MEM603 Engineering Strategy Assessment Sample
Question:
In this assessment, you are required to research, assess and compare the engineering strategies of two major automotive companies. The engineering strategies need to be current and future-oriented. You will be provided with a list of major automotive companies from which you can choose two companies. You should prepare for and approach this task by reviewing the content and readings provided in Module 1 (Strategic Business Planning), Module 2 (Innovation Strategy and Management) and Module 3 (Technology and R&D Strategy and Management) and conducting research of publicly available information. Please note that the focus of the assessment should be on the improvement of engineering operations via R&D, innovation and technology (including intellectual property).
It is suggested that you use the following as a guide to structure your assessment: 1. Introduction • Summarise the background information provided; and • Outline the backgrounds of the two global automotive companies. 2. Literature Review • Conduct a literature review of each selected automotive company and summarise the research. 3. Analysis and Findings • Discuss and compare the strategies of the selected automotive companies based on the information you gathered in your literature review. 4. Conclusions 5. References 6. Appendices
Answer:
Introduction
Summarisation of background information
The automotive industry uses modern technological development and innovation to create an established organisational structure to drive growth in its business (Slansky, 2022). Automotive organisation and their lines of products are using artificial intelligence implementation in multiple manners. Artificial intelligence will include the modern production of human-machine interaction, intelligent robots, and a substantial assurance quality process. Artificial intelligence is used fundamentally in designing cars, and manufacturers use machine learning and artificial intelligence to create their manufacturing processes. In lines of production assembly, robotics is implemented to develop that are used several times.
Background of the companies
The Jaguar Land Rover is a renowned automobile company fostering unique technological development and innovation. The computing stability of the Jaguar land rover is more excellent and more sustainable than Space Shuttle. It can handle twenty-one thousand messages alternatively and at a regular speed of about 100 MB networks of ethernet (Jaguarlandrover, 2022a). The automobile is always remained connected with Wi-Fi, 4G, and cloud computing. The car manufacturers had implemented software over the air technology to regulate updates to get delivered according to services and functions. BMW is another well-known manufacturing company regulating sustainable technologies to control high voltage batteries that are installed in the car company. Another technology implemented at Din golfing is a smartwatch that is changing along with the containers. The augmented reality glasses increased their production by twenty-seven per cent, which reduced their error rate by 34% during packing and scanning (Jones, 2022).
Literature Review
Innovation
BMW is the leading selling car manufacturing company and has always regarded creativity as an essential element to conduct success in the BMW group (Steelcase, 2022). A tidal regulated change moves between the industry to create rapid innovation within the car company. For example, they innovate autonomous driving, which is expected to develop their business model within the last thirty years. To be a leading car company, BMW has realised the vitalness of developing their innovation process to create a systematic approach.The management also recruits talented car designers that would create sustainable automobile technological development. It can be argued that, diversification can be very helpful in managing and executing innovation within the workplace. According to Markides (1997), diversification is one of the high-stake games as companies need to make a decision regarding thoughtful deliberation.
Along with the advancement of time, BMW's business model is changing along with the automated driving that is reshaping their success in the market. Digital technology has been fundamentally ubiquitous and developed, technological devices have become more interdependent and creative, teamwork and collaboration are developing as a vital aspect. The company has adopted digital location and mapping known as HERE (HERE, 2022). However, the deal was between Jaguar Land Rover and Daimler in 2015. HERE regulated services that are required by both locations and autonomous driving services. Modern technology HERE provided eminent services required for both location-driven services and autonomous driving. The windscreen wipers are integrated into the system and are shared within the management system of the company. Innovation was transforming the production process of BMW to regulate the process of production (Frangoul, 2022). The company uses robots and technology to guide employees and people working in manufacturing companies to sort out heavy lifting and transport elements. Jaguar Land Rover has worked with labs of innovation with sustainable stem to enhance organisations to develop technological developments and vehicle production. The innovation program's common goal aligns with participating industrial products and technologies into the automobile ecosystem. The engineering segment of Jaguar Land Rover has a direct association with the decision-making process. The straight path towards integrating substantial vehicles demonstrates the automated functional concept in the company. Jaguar Land Rover company is formulating digital transformation with international-based brands after their Accenture appointment. Accenture would associate forces with Land Rover's brand-named Spark 44 as an essential client automated venture to develop a modern automated model (Accenture, 2022). The venture will regulate a vital role in developing JLR to shift towards the modern, electric-based business. The company will attain advantages from various models of ownership that are designed to be fit within the individual manner of living. Accenture was selected as the sustainable technological, data generated, and experience generated approach.
Technological Advancement
During 2021 BMW Group has planned ambitious development for profitability and growth that developed immense forerunners for evaluating developed technological offensive in upcoming times. In 2014, the BMW company developed a booking option that can be done through digital services directly from automobiles through the connected drive of BMW store (BMWgroup, 2014). However, during 2018 the manufacturers maintained their vehicles up to date along with modern technological software called software up-gradation, similar to updating the modern software for mobile devices (Automotive World, 2022). The company has chosen significant powertrain from electric power to combustion engines in the second transformation phase. The subsidiaries are the moderate architecture of vehicles that enable an interchangeability network between multiple drivetrains combined closely.The eighth operating system launched in 2021 is a strong in-vehicle that processes important data within its operating system (Automotive World, 2022). The BMW I-drive is the safest and simplest concept of the operating system installed in the vehicle. The vehicles create remote up-gradation to develop sustainable installation and up-gradation.The production lab of Jaguar Land Rover is currently analysing the headset advancement of technology for creating digital applications. The designing engineers and planners can integrate the validation of products in creating process planning and factory restoration. Jaguar Land Rover also proposes technological training techniques that work with the complex technology of batteries. The solution of modular allowed the practical usage of virtual reality and augmented reality training.In the view of Li et al. (2021), virtual reality is a common substantial application to measure the implementation of virtual reality applications.However, the technological simulation adopts complex challenges that are flexible and easy to adapt to. The simulation fundamentally has made the path for an easy decision, guides to ignore waste, and thus contributes towards implementing emerging resources. Jaguar Land Rover announced that the assembly of modular aspects would have a productive increase of about twenty per cent compared with lines of production.
Analysis and Findings
Comparison between two companies’ strategies
• BMW Group has used artificial intelligence as an essential technology is a substantial element to regulate digital development. The organisation has implemented artificial intelligence throughout various aspects of the value chain, generating it as the fundamental value for processes, consumers, employees, and products. In addition, the BMW company has essential competence for encouraging data analytics and machine learning. On the other hand, Jaguar Land Rover's clear sight technologyhas regulated modern automobile generations more advanced and sustainable automobile equipment. The technology includes 5 cameras and fourteen ultrasonic sensors to generate an interactive three-hundred-and-sixty-degree view around the automobile vehicle. The clear sight allows the drivers to shift between high-definition mirrors to interior mirrors to show a good view behind the car.
• According to Kukkamalla, Bikfalvi, &Arbussa (2020), BMW Group is a well-known and leading automobile firm not regulating premium pricing on their products but also generating a good relationship with the consumer with on-demand, telematic and financial services. In 1997 the company had launched digital services. The company also has enhanced its organisational culture to increase its growth and development. On the other hand, JLR has regulated secure blockchain technologies to create proper supply chain management to generate complete transparency within a generated supply chain management. The digital technique enabled by JLR to examine the carbon footprint for its leather supply chain management.
• Qualcomm Technologies has announced its association with BMW Group, and together they will bring collaboration in the latest automobile technologies and automated driving medium. Qualcomm is a wireless technological organisation driving technological advancement by bringing 5G expansion. On the other hand, JLR has developed the application of augmented reality to create designing modern technological applications. An idle motion tracking equipment is implemented to develop the orientation and position of the reviewer's feedback around significant prototype (Mechdyne, 2022).
Innovation
• Jaguar Land Rover aims to create a sustainable business without minimising carbon emissions. The company focuses on creating zero waste that enables them to develop their zero regulation of manufacturing process. Innovation is an essential medium to create unique products in the automotive industry. For achieving innovation an organisation needs to create an appropriate integration with its R&D process and marketing channels (Cotterman et al., 2009). The company will fundamentally undergo a renaissance to evolve as the unique electric automobile industry with a substantially beautiful modern portfolio to engage modern generation and designing technologies (Jaguarlandrover, 2022b).
• The company has always focused on consumer preferences and choices regarding the specific product. The centralised medium for the company will focus on their engineering, materiality, and manufacturing financial investments. On the other hand, BMW considers itself as the automobile industry player developing modern services and substantial innovator for a successful model for business.
Conclusion
As per the above discussion, it can be concluded that both the companies focus on innovating their product line in order to capture a considerable market share. Also, it can be asserted that both the companies are dominating their markets by providing high-quality and luxurious products to their customer base. Although it can be recommended that both organisations need focus precisely on developing EVs as in the upcoming few years, the market will be captured by EVs. Moreover, BMW always has maintained its consumer-centric approach to calculate dynamic market approach and conditions in the market to develop their marketing innovation. The company also receives a substantial revenue amount from necessary services. The company also depends upon integration, technology, dynamic abilities, and collaborations to create professional activities. The BMW has enhanced the service integration method by creating collaborative programs with multiple stakeholders such as providers in communication and technological companies. Both the companies will enhance their effective standing communication to generate smart, safe, and sensitive driving experiences at BMW companies.
References
Accenture. (2022). Jaguar Land Rover transforms global marketing communications model.https://newsroom.accenture.com/news/jaguar-land-rover-transforms-global-marketing-communications-model.htm#:~:text=Accenture%20will%20join%20forces%20with,%2Dfirst%2C%20modern%20luxury%20business.
Automotive World. (2022). A New Era, a New Class: BMW Group steps up technology offensive with comprehensive realignment – uncompromisingly electric, digital, and circular | Automotive World. https://www.automotiveworld.com/news-releases/a-new-era-a-new-class-bmw-group-steps-up-technology-offensive-with-comprehensive-realignment-uncompromisingly-electric-digital-and-circular/.
BMWgroup. (2014). Sustainable value report. https://www.bmwgroup.com/content/dam/grpw/websites/bmwgroup_com/responsibility/downloads/en/2014/BMW_Group_SVR2014_EN.pdf.
Cotterman, R., Fusfeld, A., Henderson, P., Leder, J., Loweth, C., & Metoyer, A. (2009). Aligning marketing and technology to drive innovation. Research Technology Management, 52(5), 14–20.https://lesa.on.worldcat.org/oclc/7025678976
Frangoul, A. (2022).How technology is helping transform BMW’s business.https://www.cnbc.com/2018/01/18/how-technology-is-helping-transform-bmws-business-model.html.
HERE. (2022). BMW Real Time Traffic & Navigation Partnership | HERE. https://www.here.com/strategic-partners/bmw.
Jaguarlandrover. (2022a). Innovation | JLR Corporate Website. https://www.jaguarlandrover.com/innovation.
Jaguarlandrover. (2022b). Jaguar Land Rover Reimagines The Future Of Modern Luxury By Design | JLR Media Newsroom. https://media.jaguarlandrover.com/news/2021/02/jaguar-land-rover-reimagines-future-modern-luxury-design.
Jones, V. (2022). Innovation and smart tech: Why BMW is driving both. Automotive Logistics. https://www.automotivelogistics.media/innovation-and-smart-tech-why-bmw-is-driving-both/22219.article.
Kukkamalla, P. K., Bikfalvi, A., &Arbussa, A. (2020). The new BMW: business model innovation transforms an automotive leader. Journal of Business Strategy.
Li, J., George, C., Ngao, A., Holländer, K., Mayer, S., &Butz, A. (2021). Rear-Seat Productivity in Virtual Reality: Investigating VR Interaction in the Confined Space of a Car. Multimodal Technologies and Interaction, 5(4), 15.
Markides, C. C. (1997). To diversify or not to diversify. Harvard Business Review, 75(6), 93–99. https://lesa.on.worldcat.org/oclc/5232897547
Mechdyne. (2022). JLR Selects Mechdyne for Innovative Augmented Reality Software and AV Technology for Design. https://www.mechdyne.com/jlr-selects-mechdyne-for-innovative-augmented-reality-software-and-av-technology-for-design/.
Slansky, D. (2022). Before you continue to YouTube. Youtube.com. https://www.youtube.com/business-intelligence/article/21579012/manufacturing-trends-and-technologies-in-the-automotive-industry.
Steelcase. (2022). How BMW Is Driving Innovation - Steelcase. https://www.steelcase.com/asia-en/research/articles/topics/innovation/bmw-driving-innovation/.
MIS604 Requirements Engineering Assignment Help
Assignment Brief
Individual/Group - Individual
Length 1500 words (+/- 10%)
Learning Outcomes
The Subject Learning Outcomes demonstrated by successful completion of the task below include:
a) Demonstrate methods for eliciting, analyzing, documenting, and maintaining requirements in an organizational context.
b) Synthesize key principles of requirements management and communicate to stakeholders in order to solve problems.
Submission - Due by 11:55pm AEST/AEDT Sunday end of Module 2.2
Weighting - 25%
Total Marks - 100 marks
Task Summary
This Assessment requires you to respond to a case study. The same case study will be used for all three assessments so that you can develop insights into the different facets of Requirements Engineering.
For this assessment, you are required to produce an individual report of 1500 words (+/-10%) detailing a
requirements elicitation plan for the case organization. The report should contain the following:
1. A Stakeholder Engagement Plan detailing:
a. Stakeholder list
b. Areas of influence and Power mapped on a Power/Interest Grid
c. Definitions of the stakeholder’s power and interest.
2. An Elicitation Activity Plan detailing:
a. Four elicitation methods
b. An explanation of each method and why it has been selected
c. A tailored and customized example of the information gathering tool you will use for each method
d. Which stakeholders will be engaged for the elicitation activity and why?
Task Instructions for assignment help
1. Please read the attached MIS604_Assessment_Case Study.
2. Write a 1500 words (+/-10%) requirements elicitation plan for the case organization.
3. Review your subject notes to establish the relevant area of investigation that applies to the case. Re-read any relevant readings for module 1 and 2 for this subject. Perform additional research and investigation and select five additional sources in the area of elicitation methods to add depth to your explanation of method selection.
4. Plan how you will structure your ideas for your report and write a report plan before you start writing. The report does not require an executive summary or abstract.
5. Please structure the report as follows:
A professional custom title page with the subject code and subject name, assignment title, student’s name, student number and lecturer’s name an introduction (100-150 words) which will also serve as your statement of purpose for the report. This means that you will tell the reader what you are going to cover in your report. You will need to inform the reader of:
• The key concepts you will be addressing,
• What the reader can expect to find in the body of the report
The body of the report (1200-1300 words) will need to cover two specific areas:
• A Stakeholder Engagement Plan including:
i. Stakeholder list
ii. A Power/Interest Grid
iii. Definitions of each stakeholder’s power and interest
• An Elicitation Activity Plan.
i. Four elicitation methods
ii. An explanation of each method and why it has been selected
iii. A tailored and customized example of the information gathering tool you will use for each method
iv. Which stakeholders will be engaged for the elicitation activity and why?
The conclusion (100-150 words) will summarize any findings or recommendations that the report puts forward regarding the concepts covered in the report.
6. The report should use font Arial or Calibri 11 point, should be line spaced at 1.5 for ease of reading and page numbers on the bottom of each page. If diagrams or tables are used, due attention should be given to pagination to avoid loss of meaning and continuity by unnecessarily splitting information over two pages. Diagrams must carry the appropriate captioning.
7. You are strongly advised to read the rubric which is an evaluation guide with criteria for grading the assignment. This will give you a clear picture of what a successful report looks like.
Referencing
There are requirements for referencing this report using APA referencing style and it is expected that students reference any lecture notes used and five additional sources in the relevant subject area based on readings and further research. It is essential that you use the appropriate APA style for citing and referencing research. Please see more information on referencing here http://library.laureate.net.au/research_skills/referencing
Submission Instructions
Submit Assessment 1 via the Assessment link in the main navigation menu in MIS604 Requirements Engineering. The Learning Facilitator will provide feedback via the Grade Centre in the LMS portal. Feedback can be viewed in My Grades.
Academic Integrity Declaration
I declare that except where I have referenced, the work I am submitting for this assessment task is my own work. I have read and am aware of Torrens University Australia Academic Integrity Policy and Procedure
Case Study
Student Gigz Pty Ltd is a recently formed student start-up company in a university accelerator program in Adelaide. Their business focuses on ensuring that organizations can call on students, in short notice, to fulfil their short-term vacancies/ needs for specialized skills. Student Gigz Pty Ltd is building a web and mobile application combination. This application should allow organizations that require short term assistance to register for the service online to source students with the appropriate skills. The company will be funded by apro rata commission charged per hours worked by each student.
The web will be a portal for organizations s where they will be able to sign all contracts and undertakings and post listings for their short-term employment needs. They will be able to send job alters to students with the appropriate skills in their listing, who are able to work in their location via a message broadcast. The organizations will also be able to review student profile’s and send targeted message to students with the experiences in a specific area. The mobile application is designed as the primary student interface. Students will be able to create a profile where they will be able to select their skills from a pre-existing list as well as the locations where they are able to work. Typical jobs might include project support, accounting support, wireframing, high fidelity html prototyping and marketing.
Contact can be made post-matching for students to find out more about the job or the organisation to find out more about the student’s availability. Once the job is completed, payment can be made securely through the app. The organisation will also be able to rate and review the student. Your company has been engaged by Student Gigz (Pty Ltd) to help them with the requirements analysis for this project.
Solution
REQUIREMENTS ELICITATION REPORT
Introduction
The practice of researching and inventing a system’s requirements from users, customers, and other stakeholders in requirements engineering is called requirements elicitation or requirement gathering. The statement need, feasibility, statement scope, list of users participating in the requirement elicitation constitutes the work product for the system.
In order to satisfy the people’s needs of the new solution while starting a project, requirements will need to be gathered. Given that stakeholders will be affected by the project’s results, the solution that is being developed will be expected by them. It is important to understand their needs and develop a deep knowledge of their expectations, interest, influence and impact on the project for ensuring satisfactory results.
Through this study, the researcher mainly aims to identify the stakeholders for the case of Student Gigz Pty Ltd. Moreover, the study also focuses on different elicitation methods that can be used by the stakeholder for this study.
Discussion
1. Stakeholder Engagement Plan
a. Stakeholder List
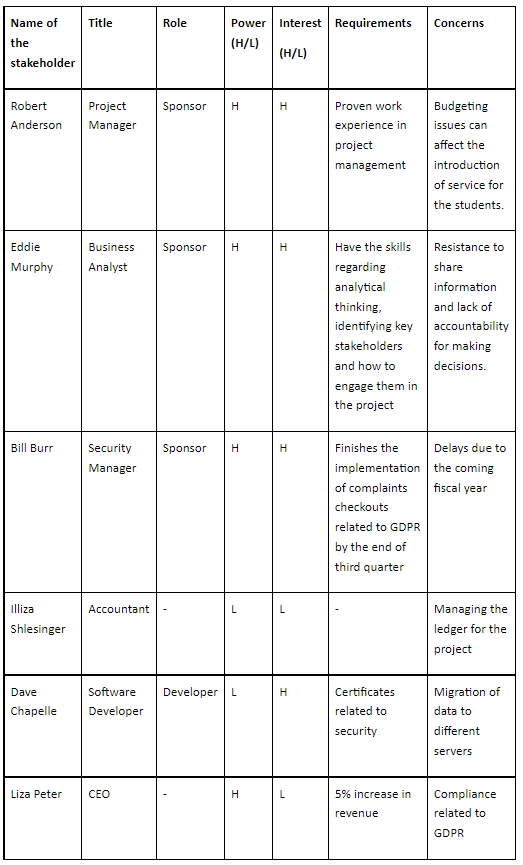
Table 1: Stakeholder List for the proposed case study
(Source: Created by the author)
b. Areas of Influence and Power/Interest Grid
In a project, the top management, team members, manager, peers, resource manager, and internal customers constitute the internal stakeholders while the external customers, government, contractors and subcontractors, and suppliers constitute the external stakeholders. The various types of stakeholder matrices are: Power interest matrix, Stakeholder analysis matrix, Stakeholder Engagement Assessment matrix. One can determine who has high or low power to affect the project, and who has high or low interest when plotting stakeholders on a power/ interest grid. It is required to keep people with high power satisfied and people with high interest informed. In stakeholder management, the simple tool that helps in categorizing project stakeholders by the power and influence they have on the project is called the Power/Influence Grid or the Power/Influence Matrix. And the technique used for categorizing stakeholders based on their power or influence and interest in a project is called the Power-Interest Grid. Stakeholders can be identified by looking at the existing documentation, organizing workshops, developing ‘as is’ business process maps and simply talking to people within the business. In this case study the name of the stakeholders is: Robert Anderson, Eddie Murphy, Bill Burr, Lliza Shlesinger, Dave Chapelle, and Liza Peter (Baernholdt et al. 2018).
c. Definitions of stakeholder’s power and interest
In any project, it is found that stakeholder management is an essential concept. Managing the stakeholders can help in successful completion of the project. In this study, the researcher focuses on the case of Student Gigz Pty Ltd. which now tries to launch a short-term assistance service for the student. Once, the stakeholders for this study have been identified, it is now important to prioritize them (Nguyen, Mohamed & Panuwatwanich, 2018). Prioritization of stakeholders becomes easy with the help of Power/Interest Grid.
From the above list formulated by the researcher for identification of the stakeholders, power and interest for different stakeholders have been highlighted. As observed from the table, the power and interest of the project manager, both are high. That means, engaging the project manager in this case would be beneficial in fulfilling the requirements. At the same time, power and influence for business analysts is also high. Managing both these stakeholders closely is quite essential. On the other hand, the CEO of this company shows high power but less interest (Campagne & Roche, 2018). That means, putting enough work in with such kind of people is required for achieving satisfaction. The software developer of this project shows low power but high interest. So, providing adequate information to such people and talking constantly with them can help in ensuring that there are no major issues. Moreover, the accountant is less powered and also less interested. Again, monitoring the accountant is important. Security manager for the same project shows high power and high interest. This shows that Engagement of the security manager will allow in securing the application and hence data breaching is not possible.
2. Elicitation Activity Plan
a. Four Elicitation Methods
An elicitation method is a collection of data that is used to gather information from people in fields related to education, knowledge engineering, management and so on. There are four elicitation methods which include interviews, user observation, use cases and prototyping.
b. Explanation of each method and selection
Interviews are used for collecting data from a small group of people on a specific topic. Generally, there are two types of interviews: they are structured and unstructured. In structure interviews the questions are placed with multiple choice answers for each subject and people are given choice to answer according to their view point (Pacheco, García & Reyes, 2018). But, in unstructured interviews questions depend on answers based on previous questions, a fixed set of answers is not possible here.
User Observation- It is based on observing a user or group of users regarding their behaviour with the product which they use in their daily life. This method can give qualitative output.
Use Case- This method is used for identifying system requirements and is used for organizing it. Moreover, this method is based on interaction between users related to a particular topic.
Prototyping- Prototype method is a method used for development in software like a prototype is built, tested and reworked. Rework is done until an acceptable prototype is attained.
For the case of Student Gigz Pty Ltd, the researcher takes the help of Use case. This is considered to be the foremost method for elicitation activity plan as it helps in explaining the system process and provides ideas accordingly. It includes four elements like Actor, Stakeholder, Primary Actor, Preconditions, Triggers, Main Success Scenarios and Alternative Paths.
c. Example of information gathering tool
The information gathering tool used for interviews is Questionnaires. In this the questions are placed with multiple choice answers for each subject and people are given choice to answer according to their view point.
On-site observation can be used as the information gathering tool for observing users’ activity. It is used in identifying people, objects and the information that is collected through this method is used for noting.
Use Case can be developed using Case studies. This method can be used in identifying and organizing system requirements which is based on interaction between users related to a particular topic (Rafiq et al. 2017).
Sketch can be referred to as the information gathering tool for prototyping. It is providing a prototype with designs and animations which is convenient for users to understand data. But, this method requires artboards in a document.
d. Stakeholders involved for elicitation activity
Project Manager is responsible for planning, procurement, and execution related to the project. Project Manager helps its team members by guiding them the right path. They show their leadership qualities by hiring employers fit for the job. In this case, the project manager is responsible for conducting interviews with business analysts to identify the key requirements for the proposed solution.
Business Analyst and security manager is responsible for conducting research and provides analysis for optimal business operations and services, they do their jobs in an efficient and productive manner. It also includes coordination with different departments to develop functional services, setting goals and budgets, managing schedules, and establishing new projects to improve organisation’s performance (Tiwari & Rathore, 2017). In this case, the business analysts and security manager are responsible for observing the behaviour of the user and then identify the best services that can be provided to them.
Software Developers will here try to design the use case for the system. Through this, it would be easier to see how different actors are associated with this system and helping to organize the requirements. Apart from that, the software developer will also try to design the prototypes for the system. With the help of a prototype, it would be easier to test the overall concept or process.
Conclusion
From the comprehensive study, it can be said that stakeholder management is vital as this is the lifeline for effective completion of the project. There must be efficient involvement of stakeholders for the fulfilment of the project. Meanwhile, requirements elicitation is also required for completing the project. The overall study has been conducted by considering the case of Student Gigz Pty Ltd. This company wishes to introduce an application for the student that will help them in getting short-term assistance. With the help of this study, the researcher tried to focus on identifying the stakeholders and prioritizing them on the basis of their job roles. For the sake of prioritization, the stakeholder took the help of Power/Interest Grid. Moreover, here different techniques of elicitation have been discussed and then applied for different involved stakeholders. Along with that, here, the researcher also mentioned different information gathering tools for the mentioned techniques.
References
Baernholdt, M., Dunton, N., Hughes, R. G., Stone, P. W., & White, K. M. (2018). Quality measures: A Stakeholder analysis. Journal of nursing care quality, 33(2), 149-156. Retrieved on 8th March 2021 from: https://journals.lww.com/jncqjournal/Fulltext/2018/04000/Quality_Measures__A_Stakeholder_Analysis.10.aspx
Campagne, C. S., & Roche, P. (2018). May the matrix be with you! Guidelines for the application of expert-based matrix approach for ecosystem services assessment and mapping. One Ecosystem, 3, e24134. Retrieved on 8th March 2021 from: https://hal.archives-ouvertes.fr/hal-01785010/
Nguyen, T. S., Mohamed, S., & Panuwatwanich, K. (2018). Stakeholder Management in Complex Project: Review of Contemporary Literature. Journal of Engineering, Project & Production Management, 8(2). Retrieved on 8th March 2021 from: https://www.researchgate.net/profile/Tuan_Son_Nguyen/publication/326801226_Stakeholder_Management_
in_Complex_Project_Review_of_Contemporary_Literature/links/5b63e5f80f7e9b00b2a25354/Stakeholder-
Management-in-Complex-Project-Review-of-Contemporary-Literature.pdf
Pacheco, C., García, I., & Reyes, M. (2018). Requirements elicitation techniques: a systematic literature review based on the maturity of the techniques. IET Software, 12(4), 365-378. Retrieved on 8th March 2021 from: https://digital-library.theiet.org/content/journals/10.1049/iet-sen.2017.0144
Rafiq, U., Bajwa, S. S., Wang, X., & Lunesu, I. (2017, August). Requirements elicitation techniques applied in software startups. In 2017 43rd Euromicro Conference on Software Engineering and Advanced Applications (SEAA) (pp. 141-144). IEEE. Retrieved on 8th March 2021 from: https://ieeexplore.ieee.org/abstract/document/8051340/
Tiwari, S., & Rathore, S. S. (2017). A methodology for the selection of requirement elicitation techniques. arXiv preprint arXiv:1709.08481. Retrieved on 8th March 2021 from: https://ieeexplore.ieee.org/abstract/document/8051340/
ENGR8762 Networks and Cybersecurity Assignment Sample
Assignment Brief
This assignment contributes 20% of your overall assessment for the topic. The grading for this assignment will be according to the University rating scheme [HD, DN, CR, P, F].
This assignment has two parts: Part A has 6% Marks, and Part B has 14% Marks.
Before you submit your assignment, you must complete the Academic Integrity module ACINT001with full marks. This is to ensure you have a good understanding of the issues of contract cheating, plagiarism, falsification, and collusion. Your submission will be automatically scanned by Turnitin for similarity. Your submission should have a similarity of less than 20%.
Submission
Due Date: Friday 29th Oct 2021 by 5 pm.
For Part A, you should provide a table (as per the example given on the next page), which addresses the threat category, controls, description, classification, and type.
For Part B, you should write a research report. The research report must have at least 1500 words but not more than 2500 words.
The assignment should be submitted as a single PDF file to the assignment space on the topic FLO page for assignment help
Late Submission
As per the official Statement of Assessments Methods (S2-2021) for this topic.
Part A: Threat classification and mitigation (6% of Total)
For the following Threat Categories, 1) Explain the threat, 2) which type of Control should be put in place for mitigation, 3) classify the controls as Process (Administrative), Product or Physical, 4) State the type of controls whether it will Prevent, Detect, Correct or Compensate. Do provide the references.
Threat Categories:
1. Impersonation attacks
2. Phishing attacks assisted with deep fake
3. Cloud Jacking
4. Ransomware attacks
5. Smishing attacks
6. DNS tunneling
Part B: Research report (14% of Total)
The topic for research is the latest security Threats. Sections on these threats include the following:
• Artificial intelligence enhanced cyber threats
• Fake news
• Ransomware attacks
• Machine learning poisoning
• Smart contract hacking
• Deep fake
• Application programming interface (API) vulnerabilities
• Internet of Things based Attacks
• Cloud vulnerabilities
• Vehicle Cyberattacks
• Threats to election
Select one of the above threats and find eight relevant papers which assist someone in developing a network threat taxonomy.
Compose an annotated bibliography of research papersthatrelate to the issue, soyour annotated bibliography will help you (and others) to have a good resource to evaluate and think about the relevance and quality of material on the topic. An example of an annotated bibliography is given at the link
https://digitalcommons.kennesaw.edu/cgi/viewcontent.cgi?referer=https://scholar.google.com/&httpsredir=1&article=1011&context=jcerp
Make sure that the information meets the topic's requirements and is from a reliable and academically respected source. Website references are not permitted unless the website is authoritative, e.g., CERT, NIST etc. You can use google scholar, IEEE Xplore digital library or ACM digital library for searching the articles.
What is an annotated bibliography?
An annotated bibliography is a list of citations to books, articles, and documents. Each citation is followed by a brief (usually about 150 - 300 words) descriptive and evaluative paragraph, the annotation. The purpose of the annotation is to inform the reader of the relevance, accuracy, and quality of the sources cited.
Annotations are NOT abstracting
Abstracts are the purely descriptive summaries often found at the beginning of scholarly journal articles or in periodical indexes. Annotations are descriptive and critical; they expose the author's point of view, clarity and appropriateness of expression, and authority.
General Instructions
The annotated bibliography is to be produced using a word processor and the EndNote reference database (or any other reference database). The submitted document must be in PDF or Word format.
The Process
Creating annotated bibliography calls for the application of a variety of intellectual skills: concise exposition, succinct analysis, and informed library research.
Solution
Part-A
The tables for threat categories along with the control and classification is shown below:
.png)
Part-B
Title
A Literature Review on Internet of Things-Based Attack
Abstract
Internet of Thing is one of the widely used platforms for transacting data. Several cloud-based applications are operated through the implication of the Internet of Things. Thus, it is one of the most demanding medium for information interchange. Millions of users are connected with this network by accessing the cloud-based application either from mobile or computer. Apart from its ease of access and platform-friendly to use, it has some security issues. As most of the users are connected with such networks for accessing the applications and services, cybercriminals obtain a feasible way to attack the connected devices and the network by penetrating malicious elements. Using this process, they use to get access to the user device and the organizational devices such as server, database etc. This causes the data and financial breach to the users and thus, it is essential to restrict the penetration of malicious elements into the network. Many researchers have proposed their methodologies and model for the prohibition or restriction to the penetration of malicious elements in the Internet of Things Network. Some of the important researches will be reviewed and discussed in this section.
Annotated Bibliography and Summarization
Annotated Bibliography
Cong, P., 2019. Spam DIS Attack Against Routing Protocol in the Internet of Things. International Conference on Computing, Networking and Communications (ICNC), pp. 198-201.
The author of this research belongs to the Department of Computer Sciences and Electrical Engineering at Marshall University, Huntington, USA. He has proposed the model to detect the DDoS attack in the Internet of Things network. They have detected that there are different types o malicious against available for DDoS attacks and one of the newest attack types is Spam DDoS. They have faced the primary challenge to detect the features of Spam DIS attack and have observed that most of this attack is subjected to the network routing protocol. So, they have researched and proposed the model through which the new type of DDoS attack that is DIS can be detected and the Internet of Things network can be protected.
Notes: This research produces a clear idea about the identification of DIS threats and the procedure of identification in the Internet of things Network.
Suryani, V., Sulistyo, S. & Widyawan, 2018. The Detection of On-Off Attacks for the Internet of Things Objects. International Conference on Control, Electronics, Renewable Energy and Communications (ICCEREC), pp. 1-4.
The authors of this research belong to the universities of Indonesia. They have researched on the Internet of Things objects that generally behave harmless while at the time of interaction with others. However, those interactions are done in a trust-based system where there is the possibility of an ON-OFF attack that can breach the user data silently. They have primarily faced challenges in the identification of trust-based and on-off attacks in the Internet of Things. They have proposed the model to detect and restrict trust-based and on-off attacks in the Internet of Things Network.
Notes: This research paper states the process of trust-based and on-off attacks in the Internet of Things Network and the procedure of detection and mitigation.
Kamaldeep, Malik, M. & Dutta, M., 2017. Contiki-based mitigation of UDP flooding attacks in the Internet of things. International Conference on Computing, Communication and Automation (ICCCA), pp. 1-5.
The authors of the research belong to India and have researched the DDoS attack that can be done by affecting User Datagram Protocol. They have emphasized the Contiki operating system and investigated the attack process. They have reviewed the previous research papers and identified that there are different types of attacks that are present in the domain of DDoS. One of the new and different types of DDoS attacks on which they have investigated was due to the effect of User Datagram Protocol in the said operating system. They have faced the primary challenge to identify the feature of that attack. Thus, they have designed and implemented the attack process using the Cooja simulator in the Contiki operating system. After that, they have proposed the solution for the mitigation process of that attach in Contiki operating system.
Notes: The researchers have demonstrated the attack type and the features of the attack on User Datagram Protocol along with the mitigation process.
Choudhary, S. & Kesswani, N., 2018. Detection and Prevention of Routing Attacks in Internet of Things. 12th IEEE International Conference On Big Data Science and Engineering (TrustCom/BigDataSE), pp. 156-159.
The authors of the research belong to India and have researched the DDoS attack on different routing protocols in the Internet of Things Network. It is to be mentioned that there are different types of routing protocols are available which are used for different purposes in the Internet of Things Network. Thus, the process of attacks is also different in these cases. Thus, they have faced challenges in identifying the procedure of attack for different protocols. They have proposed the methodology for the detection of different types of threats using Key Match Algorithm and Cluster-Based Algorithm which have been executed through Matlab Simulator.
Notes: In this research, the authors have shown and demonstrated the detection process of the threats for different types of protocols in the Internet of Things Network.
Shim, K.-A., 2019. Universal Forgery Attacks on Remote Authentication Schemes for Wireless Body Area Networks Based on Internet of Things. IEEE Internet of Things Journal, pp. 9211 - 9212.
The author of this research belongs to the University in South Korea. He had observed that wireless networks that are patched with the Internet of Things can be hacked using a DDoS agent. He had faced the challenge to detect the features of the attack so that he can propose the mitigation policy. After detecting the type of attack, he had proposed a Heterogeneous Remote Anonymous Authentication Protocol through which the attack in the Internet of Things Network can be detected.
Notes: He had demonstrated the Heterogeneous Remote Anonymous Authentication Protocol for the detection of threats in the Internet of Things Network.
Sriram, S., Vinayakumar, R., Alazab, M. & KP, S., 2020. Network Flow based IoT Botnet Attack Detection using Deep Learning.
According to the authors, administrations over the entire world are positively endorsing smart city requests to increase the superiority of daily-life actions in urban zones. Smart cities contain internet-related devices that are applied by processors such as traffic control, power grid, health care, water treatment, and many more. Each of these applications helps to improve its efficiency. The development in the number of Internet-of-things (IoT) is completely focused on botnet attacks. That is because of the rising tendency of Internet-enabled strategies. This article tries to suggest deep learning which depends upon a botnet detection system that works on network traffic movements to offer a progressive cyber-safety resolution to Internet-of-things devices as well as smart city requests.
Note: The authors of the research have demonstrated the type of attack and proposed the mitigation policy for it.
Chen, S.-C., Chen, Y.-R. & Tzeng, W.-G., 2021. Effective Botnet Detection Through Neural Networks on Convolutional Features. [Online]
The authors of the research belong to China. According to them, botnets is one of the prime threats related to internet-related cybercrimes for example spreading spam, DDoS attacks, and thefts precious information and data, according to the understanding of the research presentation it is quite evident that identifying modern botnets in recent years is becoming quite difficult to be found as well. Therefore, the project aims to present a machine learning method that can help detect the P2P botnet with the help of flow-based features.
Notes: The researchers have demonstrated the attack in the Internet of Things network that is caused by Botnet.
Wang, J., Liu, Y., Su, W. & Feng, H., 2020. A DDoS attack detection based on deep learning in software-defined Internet of things. IEEE 92nd Vehicular Technology Conference (VTC2020-Fall), pp. 1-5.
The researchers belong to the Universities in China. They have researched and emphasized different types of attacks in the software-defined Internet of Things. They have faced the primary challenges of identifying the typical attack types and behaviors. They have designed a Software-Defined Internet for Thing Network using the components like a controller, switches etc. and used a Deep Learning algorithm to detect the threats there.
Note: In this research, the authors have designed a realistic model for the detection of threats using Deep Learning.
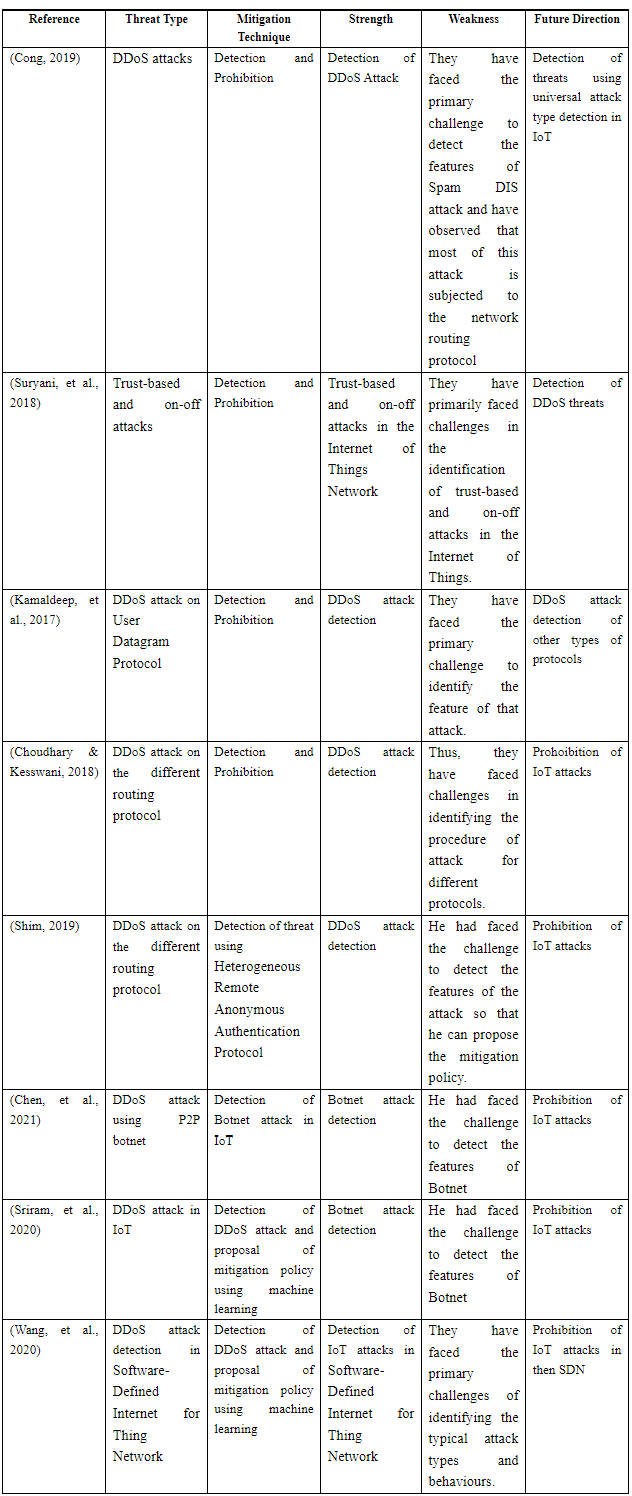
Summarization
The summarization of the reviews of the previous researches are shown below:
References
Agarkar, S. & Ghosh, S., 2020. Malware Detection & Classification using Machine Learning. IEEE International Symposium on Sustainable Energy, Signal Processing and Cyber Security (iSSSC), pp. 1-5.
Chen, S.-C., Chen, Y.-R. & Tzeng, W.-G., 2021. Effective Botnet Detection Through Neural Networks on Convolutional Features. [Online]
Available at: https://.ieee.org/document/8455930
Chen, Y., Jin, B., Yu, D. & Chen, J., 2018. Malware Variants Detection Using Behavior Destructive Features. 2018 IEEE Symposium on Privacy-Aware Computing (PAC).
Choudhary, S. & Kesswani, N., 2018. Detection and Prevention of Routing Attacks in Internet of Things. 12th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE), pp. 156-159.
Cong, P., 2019. Spam DIS Attack Against Routing Protocol in the Internet of Things. International Conference on Computing, Networking and Communications (ICNC), pp. 198-201.
Jin, X. et al., 2020. A Malware Detection Approach Using Malware Images and Autoencoders. IEEE 17th International Conference on Mobile Ad Hoc and Sensor Systems (MASS), 8(2), pp. 172-177.
Kamaldeep, Malik, M. & Dutta, M., 2017. Contiki-based mitigation of UDP flooding attacks in the Internet of things. International Conference on Computing, Communication and Automation (ICCCA), pp. 1-5.
Kuruvila, A. P. & Basu, S. K. &. K., 2020. Analyzing the Efficiency of Machine Learning Classifiers in Hardware-Based Malware Detectors. IEEE Computer Society Annual Symposium on VLSI (ISVLSI), pp. 452-457.
Murali, R., Ravi, A. & Agarwal, H., 2020. A Malware Variant Resistant To Traditional Analysis Techniques. International Conference on Emerging Trends in Information Technology and Engineering (ic-ETITE), pp. 1-6.
Nisha, D., Sivaraman, E. & Honnavalli, P. B., 2019. Predicting and Preventing Malware in Machine Learning Model. 10th International Conference on Computing, Communication and Networking Technologies (ICCCNT), pp. 1-5.
Shim, K.-A., 2019. Universal Forgery Attacks on Remote Authentication Schemes for Wireless Body Area Networks Based on Internet of Things. IEEE Internet of Things Journal, pp. 9211 - 9212.
Sriram, S., Vinayakumar, R., Alazab, M. & KP, S., 2020. Network Flow based IoT Botnet Attack Detection using Deep Learning. s.l.:s.n.
Suryani, V., Sulistyo, S. & Widyawan, 2018. The Detection of On-Off Attacks for the Internet of Things Objects. International Conference on Control, Electronics, Renewable Energy and Communications (ICCEREC), pp. 1-4.
Wang, J., Liu, Y., Su, W. & Feng, H., 2020. A DDoS attack detection based on deep learning in software-defined Internet of things. IEEE 92nd Vehicular Technology Conference (VTC2020-Fall), pp. 1-5.
ENGR9704 Engineering Management Assignment Sample
Assignment 1 - Project Specification (group project)
Title page: The title page or cover page for the project should indicate:
• The name of your group
• Group members’ names and student ID
• Date of submission
• Topic name
• Topic code.
Table of Contents
1. Executive Summary of the main work undertaken, the achievements and other significant outcomes. Executive Summaries should not be a ‘prose of Table of Contents’ and should contain information about the background, statement of objectives, proposed solution and requirements, and description of deliverables to give a complete snapshot of the project. Ideally short and to the point, able to be read quickly to judge the viability of the project in a short viewing period. E.g., it should describe what the project is about, its key milestones, stakeholders and benefits/significance.
2. Introduction / Background.
This is used to introduce the business project, describe what has happened in the past to address the problem, and what the current status is at the time of writing the Project Specification. Purpose of the Project and Problem Statement
This section should clearly establish the benefit to the organisation of proceeding with the proposed project. It should contain:
• A description of the relevant market/industry conditions that affect the project/product
• An assessment of how the business needs are currently being met or not met (e.g. customers
currently have X we will provide a better product/service).
• An analysis of the gap between the current situation and the stated objectives (what needs to change to make your project a success).
• Identify who in the organisation is sponsoring the project and why? (or what outside organisation is sponsoring).
3. Project Overview for assignment help
This should include:
• Project Title
• Vision for the project – including goals for the project and what it is expected to deliver.
• Organisational Objectives – all projects should relate to and produce results that relate to pre- defined organisational goals. The relationship between the project and the Corporate Strategic Plan should be described.
• Scope - Develop a scope statement for the project. Use the template provided on the text companion Web site and review the sample in the text. Be as specific as possible in describing product characteristics and requirements, as well as key deliverables.
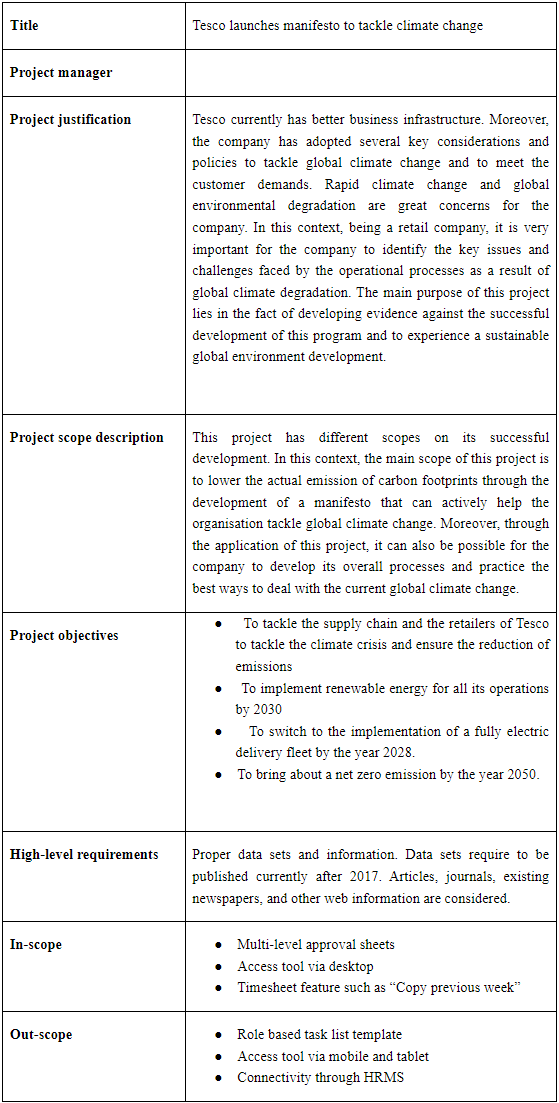
Table 1: Scope Statement
4. Critical Assumptions and Constraints
It is essential that assumptions made during the project planning process are recognised and recorded. Any requirements for specialist resources or skills should be identified here, and any dependencies that exist with other projects or initiatives.
5. Analysis of Options
This should be a high-level analysis of the possible alternatives that could be employed to bridge the gap between the current situation and what is proposed via the project.
Some options that need to be considered may include:
• Option 1 – Do nothing
• Option 2 – Undertake project
• Option 3 – Undertake alternative project
• Option 4 – The preferred option.
The advantages and disadvantages of the options can be compared in a table.
Note, that this does not necessarily need to be alternative projects (as some projects students have picked may not be suited for this type of analysis. Alternatives may also be in the form of different directions for the project to go down, such as using different materials for critical components, choosing alternative means of construction/assembly (in-house vs. outsourced), or different locations for facilities. The choice is yours for how this applies to your project.
6. Work Plan
Needs to outline project steps and phases, and major areas of work. Develop a work breakdown structure (WBS) for the project. Provide a tabular (list) version of a WBS, and a graphical version. The priority is a simple professional display of relevant information. Include a full list of tasks in the tabular version, and a condensed high-level list (if necessary) in the graphical version, to save space and make it easier to read.
7. Outputs
This needs to describe the main deliverables and outcomes that are generated by the project. Create a milestone list for this project and include at least five milestones and estimated completion dates for them.
8. Costing Section
Develop a cost estimate for the project. Estimate hours needed to complete each task (including those already completed) and the costs of any items you need to purchase for the project. Perform a Financial analysis of the intended project, include information to evaluate the potential of the project to investors (this may be included in the ‘analysis of options’ section as well in shorter detail). Use tools relevant to comparing projects such as Return on Investment, and the Net Present Value of the project.
9. Implementation Strategy
The information in this section is important. It needs to describe the main resources that will be involved as well as timelines and important milestones. Use the WBS and milestone list you previously developed to create a Gantt chart and network diagram for the project, (note that MS Project can generate both Gannt and Network Diagrams automatically from this information). Estimate task durations and enter dependencies, as appropriate. A network diagram should be included to deliver a realistic schedule. Milestones should be included as completion of major phases in the schedule and not arbitrarily defined beforehand. Once the project is well understood, the time and resources needed for its completion defined (including a realistic budget that includes the cost of the necessary contribution of time by the client, and “in-kind” cost of hours of the students. In this way, the students have a clear path to follow with sections logically dependent on each other and flowing from need to solution. Consider the resources needed for each of the tasks defined in the work plan, particularly the hours required.
10. Stakeholders
List of those to whom outputs will be delivered and a description of how each will use the benefits of the project. Related projects (or major change initiatives) that are significant for this project should be identified in this section.
11. Project Management Framework
This describes how the project will be managed, including:
? The proposed governance model (who is responsible for what?) Create a RACI chart for the main tasks and deliverables for the project.
? Quality assurance and control features of the project – consists of standards and methodology to be applied and project monitoring requirements to ensure outputs have been achieved. Create a quality checklist for ensuring that the project is completed successfully.
Also define at least two quality metrics for the project.
? Develop a communications management plan for the project. This should include:
Communication type (i.e., team meetings or project status meetings)
Objective of the communication
Medium (email, meeting, phone call)
Frequency
Audience or attendees
Who is responsible for the communication?
12. Risks
Create a probability/impact matrix and list of prioritized risks for the project. Include at least 12 risks
Solution
1. Executive Summary
The main idea behind this project is to analyse the manifesto of TESCO about climate change. In this report, a brief analysis of costing and time scale of implementation of the factors such as reducing carbon footprints, and food wastage control have been elucidated at the brief. Despite this, the report has delineated a stakeholder analysis of who is responsible for this project. Mainly three types of stakeholders have been identified in this project such as employees, local people, and government. Despite this, the impacts of the stakeholder on this project along with their roles and responsibilities have also been set forth in their report. In addition to it, the report further convened a brief idea about the RACI model where the report segmented people and their responsibilities with the help of four factors: Responsibilities, Accountability, Consultation, and Informed. At long last, the report identified two risks such as the effort to increase public awareness and climate change denial that the organisation TESCO can face during implementing their manifestation of climate change, In Addition, the report further segmented the risk as per their priority and recommended some approaches to extenuate those risks. Despite this, the report highlights other various factors such as the role of the zero deforestation soy initiative, the role of artificial intelligence in supply chain management and work plans such as project scopes, identification of the problems, and the final outcome of the project in the report.
2. Introduction or Background
2.1. Purpose of the Project
The main purpose of this project is to develop a manifesto for the purpose of tackling climate change. In this context, currently, the rapid climate change and environmental diversity loss are one of the greatest concerns of the UK government. As per the collected data, it is evident that the main sea level of the UK has risen significantly up to 1.4mm per year since 1910 due to the increasing business operations, economic activities, and the global transport system (Moore et al., 2019). Due to rapid climate change, the sea surface temperature of the UK has risen to .3 degree Celsius and 0.6-degree Celsius warmer climate. In order to mitigate this global concern and to expect more sustainable and global environment development, it is very important for the country to find the best possible options. Tesco is currently following the principle of developing the global climate through the application of developing a manifesto. In this context, through the application of this manifesto, it can be possible for the company to contribute much to the global environment development (Castle and Hendry, 2020). The main purpose of this project lies in the fact of developing evidence against the successful development of this program and to experience a sustainable global environment development.
2.2. Problem Statement
Rapid climate change and global environmental degradation are great concerns for the company. In this context, being a retail company, it is very important for the company to identify the key issues and challenges faced by the operational processes as a result of global climate degradation. In this context, the main issue is the increasing carbon emission from the manufacturing outlet of the company. Due to more emissions of carbon footprints, the company is facing several restrictions and issues in its current business operations (Raven and Wagner, 2021). Therefore, it is very important for the company to understand the current business applications and reshape the business accordingly.
The company needs to implement the latest technologies and make constant innovations in its existing system. Through the application making the entire business updated, it can be possible for the company to find the best possible ways, manage sustainable processes, and expect the minimization of carbon footprints from the manufacturing outlets (Nassaryet al., 2022). Moreover, it can also be possible for the company to expect successful ventures in their long-term and short-term goals for the development of the global environment.
Tesco currently has better business infrastructure. Moreover, the company has adopted several key considerations and policies to tackle global climate change and to meet the customer demands. As per the current marketing trends, customers are reliable on sustainable products and services with high shelf life, low cost, and eco-friendly. For this reason, Tesco has reduced carbon footprint emission significantly and it’s trying to practise zero carbon emission by 2050 to add more value to the global consumers. Tesco has also paid focus on the feedback system development for the purpose of making constant changes in the quality of the offering products for the purpose of meeting customer interests and demands.
The main gap between the current situation and the organisational objectives is the lack of proper considerations in the supply chain management and manufacturing output. As per the objectives, Tesco will bring out zero carbon emission by 2050 and to develop a sustainable supply chain. Tesco has initiated the process and adopted the implementation of a manifesto to tackle global climate change and to develop the supply chain.
The company needs to address UN goals and conduct accordingly. In order to raise more capital, the company needs effective sponsors. For this reason, it is very important for Tesco to tie up with multinational companies offering similar services in the global marketplace.
3. Project Overview
3.1. Project Title
Tesco launches manifesto to tackle climate change
3.2. Vision for the Project
The main vision of the project is to set different objectives for the purpose of maintaining the successful development of the entire project. In this context, the principal vision of the project is to tackle the rapid climate change in the UK. Therefore, through the application of maintaining a proper strategy and plan, it can be possible for the company to pay close attention to the details of the development of an effective policy to reduce the significant amount of carbon footprint reduction. Moreover, through the application of a proper plan and policy, it can also be possible for the business to bring out net zero emission of carbon footprints by the year 2050 and to effectively develop the supply chain.
3.3. Organisational Objectives
The objectives set out by the organisation are mainly to facilitate Tesco Plc to achieve climate change in a better manner. The objectives set out through the manifesto of Tesco to tackle climate change are as follows:
? To tackle the supply chain and the retailers of Tesco to tackle the climate crisis and ensure the reduction of emissions
? To implement renewable energy for all its operations by 2030
? To switch to the implementation of a fully electric delivery fleet by the year 2028.
? To bring about a net zero emission by the year 2050.
3.4. Scope Statement
This project has different scopes on its successful development. In this context, the main scope of this project is to lower the actual emission of carbon footprints through the development of a manifesto that can actively help the organisation tackle global climate change. Moreover, through the application of this project, it can also be possible for the company to develop its overall processes and practice the best ways to deal with the current global climate change.
There are several considerations included in this project that help the particular project to get successfully developed (Krogstrup and Oman, 2019). The project manager has been able to make the project accordingly through the application of identifying all the risks, timelines, and outputs. A proper digital timeline and alternative marketing operational strategies have been identified. In this way, this project can lead to the initiation of many more projects like this.
4. Critical Assumptions and Constraints
A high level of climate awareness has been implemented in the UK to help the country achieve net zero emissions. It has been observed that several companies in the country have undertaken climate control manifestos. From the studies of Gannon et al., (2022), it can be mentioned that the major constraints that can be faced in the development of a climate manifesto involve the capacity of the people to adapt to the change. From the research of Moussa et al., (2019), it has been found that the process of incorporating change on a wider basis becomes difficult since people are more comfortable with the older ways. Moreover, another important constraint of implementing a climate change manifesto involves limited knowledge of technology paired with limited awareness.
From the reports of the company, it has been observed that the critical assumptions that have been made by the company involve the following:
? A complete transition toward the use of electric vehicles would help in tackling carbon emissions.
? Creating a better basket for the customers and the planet would help in accelerating the process of climate control (Tescoplc.com, 2021).
? Improving the issues of food production would lead to preventing climate change in a better manner.
? Working with the suppliers in order to scale the technologies and target the causes of agricultural emissions would help in improving the climate manifesto.
Overall, from the identification of the constraints and the assumptions, it can be said that the planning process needs to be done in such a way that all the constraints are overcome and the assumptions are met. It needs to be mentioned that the implementation of project planning tools needs to be made so that the dependencies of the tasks can be identified in a better manner.
5. Analysis of the Options
5.1. Option 1: Zero-Deforestation Soy Initiative
Considering all the alternatives for tackling the climate change manifesto, Sainsbury’s has implemented a “Zero-deforestation soy initiative” (Sainsburys.co.uk, 2022). From the reports, it has been observed that this initiative helps in the protection of forests. It can be mentioned that the management of the financial incentives has been done by the company in such a manner that they are able to fund the Brazilian farmers. Therefore, it must be stated that choosing this option significantly contributes to environmental management. A 12-month trial phase was started, and the results have assisted in encouraging Brazilian farmers to protect the country's native Cerrado vegetation as well as the preservation of the water quality and the decline in biodiversity.
5.2. Option 2: Recyclable Packaging
The sustainability commitments of ASDA can be considered another important option for the management of the sustainability process. As per the reports of the company, it can be mentioned that the initiative undertaken by the company is to implement sustainable packaging. The company has been observed to reduce the total packaging weight by 27% (Asdasupplier.com, 2022). As one of Walmart's sustainability goals, it should be noted that the company has made a strong commitment to achieving 100% package recycling by 2025.
5.3. Option 3: Blockchain or AI in the Supply Chain
Certain small retail SMEs have been trying to comply with the “Forest Risk Rules” in order to prevent deforestation measures. From the recent reports, it has been observed that the UK government has been seen to aim at preventing deforestation rates in the country (Retail-week.com, 2021). Overall, in compliance with the UK rules and regulations, it can be mentioned that the development of agile supply chains and the implementation of technology such as blockchain and AI help in reducing waste at all levels of the supply chain. Overall, it needs to be mentioned that the implementation of these options helps in increasing the sustainability of the companies.
However, a negative aspect of the SME has been observed to be in the funding aspect. Hence, the adoption of technology has been observed to be highly difficult for companies.
5.4. Option 4: Reduction of Carbon Footprints
It has been noted that Aldi supermarket has adopted sustainable tactics like reducing operational emissions. The reports have been observed to have opted for a reduction of plastic pollution. The most innovative option implemented by the mentioned company is the implementation of smart shopping (Corporate.aldi.us, 2021). The reduction of carbon footprints has been the main aim of the mentioned company.
5.5 Advantages and Disadvantages of the options
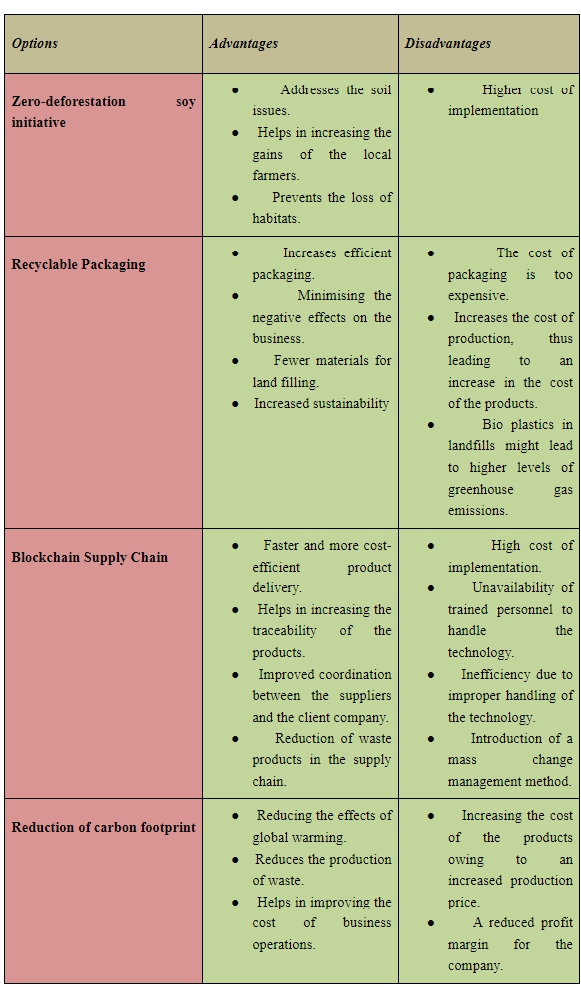
Table 2: Comparison Table for the Options Discussed
From the above table, it can be seen that the alternative options have almost similar kinds of disadvantages. Therefore, it can be said that every green or sustainable strategy raises the cost of production.
6. Work Plan
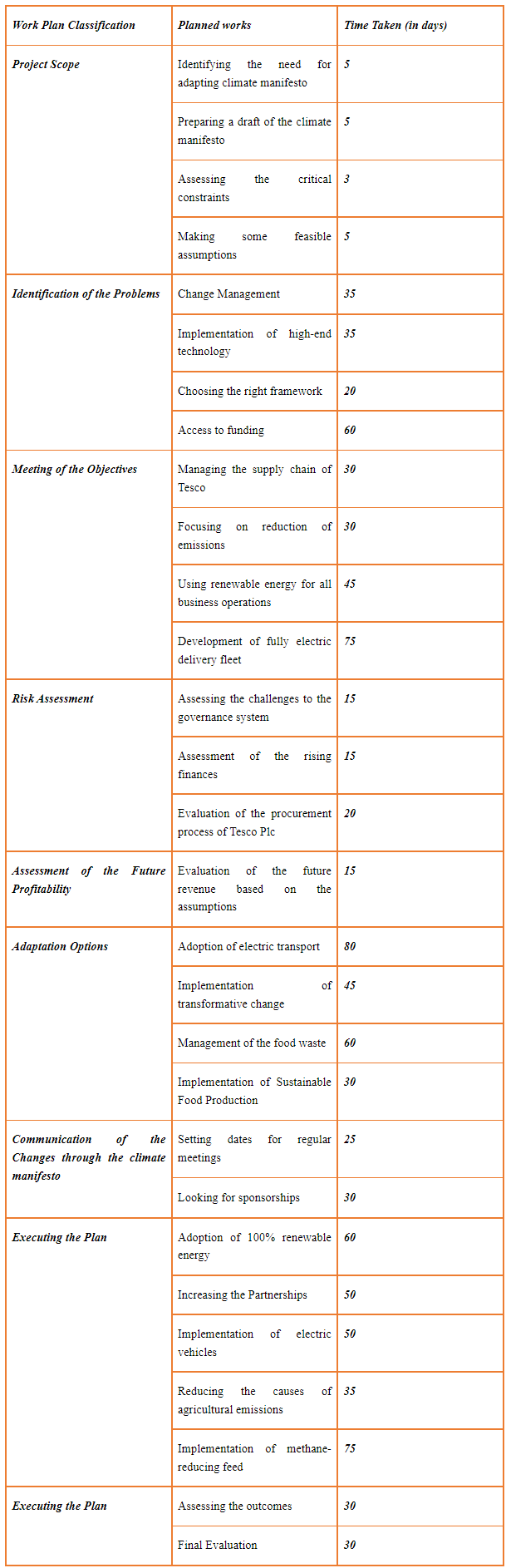
Table 2: Manual Work Plan (Tabular)
From the studies of Matheson et al., (2019), it can be mentioned that the work plan is important to identify the chronological order of undertaking a particular work. Additionally, it can be mentioned that the work plan is important as it helps in identifying the major areas of priority in a project.
The work plan, in this case, has been broadly classified under the following groups:
? Project Scope
? Identification of the problems
? Meeting the Objectives
? Risk Assessment
? Achieving Future Profitability
? Adaptation Options
? Communicating the Changes
? Executing the Plan
? Final Outcome
The work breakdown structure as derived from Project Libre has been represented in the following image.
Figure 1: Work Breakdown Structure
From the work breakdown structure, it can be seen that the priority of the tasks involves assessing the important aspects of the work breakdown structure. As seen in the present case, it can be mentioned that the process of assessing the risks and evaluating the financial aspects of implementing the changes can be considered the most important. Overall, the evaluation process of the climate manifesto needs to be considered based on these aspects.
Figure 2: Digital Work Plan (tabular)
7. Outputs
Milestones
There are 9 different milestones that are going to be achieved through the successful development of this project. In this context, there are different durations decided to meet each milestone. The entire work starts on 28.09.22 and will end on 22.07.26. Each milestone is going to be achieved through the application of dividing each task into sub-tasks. All these milestones are identified as a result of the plan and processes being set up by the project manager. It is very important to consider every step for the purpose of developing this project accordingly.
? Project Scope: 5.9.22 to 29.9.22
? Identification of the problems : 29.9.22 to 27.4.23
? Meeting the Objectives: 27.4.23 to 4.1.24
? Risk Assessment: 4.1.24 to 14.3.24
? Achieving Future Profitability: 14.3.24 to 4.4.24
? Adaptation Options: 4.4.24 to 30.1.25
? Communicating the Changes: 30.1.25 to 17.4.25
? Executing the Plan: 17.4.25 to 30.4.26
? Final Outcome: 30.4.26 to 11.6.26
8. Costing section
8.1 Cost estimate
Table 3: Cost analysis
(Source: Self-developed)
8.2 Financial analysis
In order to accomplish the project total cost has been estimated at £10,800 and the total time frame has been kept for the entire project completion is 4 months. During the entire project,
ROI or Return on investment for this project will be calculated with the help of
Where
R is the return on investment
Vf is considered as the final value which includes dividends and interest
Vi=initial value
ROI will be more than 10, which can be considered a good investment for the project by the organisation.
The calculation for NPV or Net Present value will be calculated with the help of the formula:
Where Rt stands from net cash flow at time t
And i=discount rate
t is the time frame
NPV or the Net Present value for the project is Zero which clearly indicates that TESCO can expect a profit and should move forward with the investment. NPV above zero signifies inflows are greater than outflows therefore; it will help the organisation earn a profit.
9. Implementation Strategy
Figure 2: Digital timeline
(Source: Created by the learner)
Figure 3: Digital timeline
(Source: Created by the learner)
The entire project is developed through the application of developing a digital timeline of the entire project. In this context, through the application of a digital timeline, it is possible for the project manager to include all tasks and schedules accordingly based on the desired timeline and duration. The entire project has different phases. In this context, the first phase is project scope identification. It is followed by the identification of the objectives and the meeting of the objectives. Risk management and assessment of future profitability are also done through the application of developing the digital timeline (Cullis et al., 2019). The fourth step of the Gantt chart is the adaptation options which refer to the adaptation of electric transport and other considerations. The next step is the communication plan which involves the practice of regular communication within the project management. Execution of the plan is also done through the application of considering the expected dates and times of the entire process. In this way, the outcome is determined and thus the project is developed.
Project scope: identification, preparation, Assessment of the critical constraints, and making feasible assumptions.
Identification of problems: Change management, Choosing framework, accessing funding.
Meeting the objectives: Manage the supply chain, focus on reduction of emissions. Moreover, use of renewable energy, and development of electric fleet to meet the objectives.
Risk assessment: accessing challenges, finances, governance issues, and procurement process.
Assessment of future profitability: evaluation of future revenue.
Adaptation outcomes: electric transport, management of food waste, implementation of sustainable food production.
Communication of the changes through the climate manifesto: Setting dates, looking for sponsors.
Execution of the plan: increasing partnerships, implementation of methane reducing feed, implementation of electric vehicles.
Final outcome: Assessing the outcomes, final evaluation.
Figure 4: Gantt chart
(Source: Created by the learner)
Figure 5: Network diagram
10. Stakeholders analysis
Table 4: Stakeholder’s analysis
11. Project Management framework
11.1 Governance Model (RACI model)
R= responsible
A=accountable
C=Consulted
I=informed
Table 5: RACI model
(Source: Self-Developed)
11.2 Quality assurance and checklist with two quality matrices
As per the views of Fernandes et al. (2022) quality assurance can be envisaged as a process of determining and analysing whether products or services meet with the specific requirements or not. Considering the case study, process control will be considered for the project as a part of quality assurance.
Table 6: Quality assurance
11.3 Communication management plan
Table 7: Communication management plan
12. Risks
Table 8: Risk Matrix
Table 9: Risk Register
13. Conclusion
The primary idea behind the project is to prepare a manifesto to tackle climate change and for this, the organisation has taken several approaches such as making a risk management plan, doing stakeholders analysis and preparing a budget to estimate the cost of the project implementation. The project also confabulated some developing evidence against the successful development of this program and to experience a sustainable global environment development. Despite this, the report has critically analysed various constraints that can arise during the project implementation and based on the risk proposed some mitigating strategies. Further, the report has confabulated the advantages and disadvantages of the zero-deforestation soy initiative, recyclable packaging, blockchain in the supply chain and reduction of carbon footprints with proper illustrations.
References
Asdasupplier.com, 2022. Our Sustainability Commitments. Available at: https://asdasupplier.com/responsibility/our-sustainability-commitments [Accessed on 05-09-2022]
Brock, A., Kemp, S. and Williams, I.D., 2022. Personal Carbon Budgets: A Pestle Review. Sustainability, 14(15), p.9238.
Castle, J.L. and Hendry, D.F., 2020. Climate econometrics: an overview. Foundations and trends® in econometrics, 10(3-4), pp.145-322.
Corporate.aldi.us, 2021. ALDI Tops the Sustainability Chart. Available at: https://corporate.aldi.us/en/corporate-responsibility/sustainability/#:~:text=ALDI%20achieved%20this%20 ranking%20as,recyclable%20or%20compostable%20by%202025. [Accessed on 05-09-2022]
Cullis, J.D., Horn, A., Rossouw, N., Fisher-Jeffes, L., Kunneke, M.M. and Hoffman, W., 2019. Urbanisation, climate change and its impact on water quality and economic risks in a water scarce and rapidly urbanising catchment: case study of the Berg River Catchment. H2Open Journal, 2(1), pp.146-167.
Fernandes, M.R., Donders, K. and Loisen, J., 2022. Ibermedia as a collaborative space for film co-production policy? A stakeholder analysis on decision-making processes. Communication & Society, pp.137-153.
Gannon, K.E., Castellano, E., Eskander, S., Agol, D., Diop, M., Conway, D. and Sprout, E., 2022. The triple differential vulnerability of female entrepreneurs to climate risk in sub?Saharan Africa: Gendered barriers and enablers to private sector adaptation. Wiley Interdisciplinary Reviews: Climate Change, p.e793.
Krogstrup, S. and Oman, W., 2019. Macroeconomic and financial policies for climate change mitigation: A review of the literature.
Matheson, E., Minto, R., Zampieri, E.G., Faccio, M. and Rosati, G., 2019. Human–robot collaboration in manufacturing applications: A review. Robotics, 8(4), p.100.
Moore, F.C., Obradovich, N., Lehner, F. and Baylis, P., 2019. Rapidly declining remarkability of temperature anomalies may obscure public perception of climate change. Proceedings of the National Academy of Sciences, 116(11), pp.4905-4910.
Moussa, L., Garcia-Cardenas, V. and Benrimoj, S.I., 2019. Change facilitation strategies used in the implementation of innovations in healthcare practice: a systematic review. Journal of Change Management, 19(4), pp.283-301.
Nassary, E.K., Msomba, B.H., Masele, W.E., Ndaki, P.M. and Kahangwa, C.A., 2022. Exploring urban green packages as part of Nature-based Solutions for climate change adaptation measures in rapidly growing cities of the Global South. Journal of Environmental Management, 310, p.114786.
Raven, P.H. and Wagner, D.L., 2021. Agricultural intensification and climate change are rapidly decreasing insect biodiversity. Proceedings of the National Academy of Sciences, 118(2), p.e2002548117.
Retail-week.com, 2021. Why retailers must be mindful of the impending Environment Bill. Available at: https://www.retail-week.com/retail-voice/why-retailers-must-be-mindful-of-the-impending-environment-bill/7039790.article?authent=1 [Accessed on 05-09-2022]
Sainsburys.co.uk, 2022. Zero-deforestation soy initiative underway with major UK supermarket backing. Available at: https://www.about.sainsburys.co.uk/news/latest-news/2022/02-08-2022-zero-deforestation-soy-initative [Accessed on 05-09-2022]
Schlund, D., Schulte, S. and Sprenger, T., 2022. The who’s who of a hydrogen market ramp-up: A stakeholder analysis for Germany. Renewable and Sustainable Energy Reviews, 154, p.111810.
Tescoplc.com, 2021. Tesco sets out its climate “manifesto” ahead of the crucial COP26 Conference in Glasgow. Available at: https://www.tescoplc.com/news/2021/tesco-sets-out-its-climate-manifesto-ahead-of-crucial-cop26-conference-in-glasgow/#:~:text=If%20we%20are%20to%20 safeguard,a%20net%2Dzero%20future.%E2%80%9D [Accessed on 05-09-2022]
SENG205 Software Engineering Assignment Sample
Length/Duration: 1000 Words (+/- 10%)
Unit Learning Outcomes addressed:
1) Describe compare and contrast various methodologies for software development processes
5) Be able to select an appropriate development method for a complex problem and give technical reasons for the choice
6) Be able to gather requirements, develop specifications, design, implement and test a prototype individually and in a team.
Submission Date: Week 5
Assessment Task: Initial Design – the plan and its justification
Total Mark: 15 marks
Weighting: 15 % of the units’ total marks
Assessment Description for Assignment Help
Assessment 2 will be an initial design of your project – showing your project plan and its justification. You need to write 1000 words summary on initial project information, elicit high level requirements, classify and prioritize the high level requirements, choose a software development methodology and justify its choice, initial project timeline, and preliminary budget breakdown. You need to work in groups of 4-5 students. Further details of assignment is provided on the Moodle site in “Project Outline” Document in Assessment Briefs folder. The students contribution and performance towards preparing the report will be accessed via peer review document.
Solution
Introduction
A person's education is an important factor of their life; depending on their career, it will either make or break them. Today's education is far more diverse than it was in the 1950s thanks to advancements in teaching approaches and other significant inventions that use more overt teaching methods(Hitka et al., 2021). In e-learning, students can study wherever is most convenient for them, including at home. Online resources for learning are available. Texts, audio, notes, videos, and photos may all be included in the study materials for online courses. The research methodology, though, offers both advantages and disadvantages. The "Melbourne School of Technology" aspires to convert traditional classroom instruction into an online learning environment(Öncü & Cakir, 2011). It takes a lot of work to learn in online classrooms because there is a lot of responsibility that must be handled online. I conducted an interview with the prominent stakeholders to learn about the many criteria that should be taken into account for online courses.
Requirements:
There are different expectations for various degrees of people. Approaching the university Coordinator first:
1. The lesson is only open to enrolled students, but information about the school should be available to anybody who is interested.
2. A student's enrollment is determined by the course and degree of training they are interested in.
The purpose of the online classes is to help students meet their requirements. And in their opinion:
1. In general, enrolling in a course by visiting a receptionist is quite simple, but many websites demand that you fill out extensive application forms in order to enroll online. So, they would expect that signing up for an online program would be simple and quick.
2. They should be able to choose the time slot for the class that interests them. And if they have to skip a session, they can go to another one.
Functional Requirement: required
1. Login and register – The student and tutor can register and login to the system for online class. A personal id is required to share with the students and tutors to access this system. two different portal is required to be design one for student and one for tutor. Tutor has more access to the system and student has limited access related to the class and assignment only.
2. Attendance – The system will take attendance of the student in every class as the student who join online class is marked present and it is stored in the database.
3. Assignment submission – The system must have the assignment portal in which the tutor can give the assignment related information and the students will submit the assignment on deadline.
4. modules – The modules is also required to be uploaded by the tutor in this online learning system so that the student can access the modules for completing assignment.
5. Record live class – The class recording can also be done so that the student who does not take the class can view recording.
Exam result – The student can give online exam and this system will show results on the portal.
None Functional Requirement: required
1. Security – All the information stored in the system must be secure.
3. compatibility – The system should compatible for all the devices.
4. Usability – The system should easy to use for everyone.
5. Performance – The performance of the system required to be good.
Functional Requirement Priorities (can a make a table) : required
Methodology of Software Development for the Online Classes
Applications known as e-learning systems make it possible to build learning environments, integrate training materials, documentation, and communication tools, and promote engagement, cooperation, and educational management (Mohammed et al., 2021). There are various methods for producing educational content for online learning and these methods frequently employ the same phases or stages for content generation.
Rational Unified Process has the following characteristics:
Iterative Development: This necessitates iterative development of software. With each cycle, the system evolves to incorporate new ideas and capabilities, until it is fully functional and ready for rollout to the client.
Managing requirements: To do so, it is necessary to record the user's requirement in detail and to keep track of any changes made to the original demand. It examines the system and how the changes will affect it in order to decide how much weight to give to each.
Using component-based architectures: Using a component-based architecture, the system architecture is broken down into its constituent parts.
Visual software modeling: Graphical UML is used to display both the dynamic and static perspectives of the software.
Quality assurance: As a result, you can rest assured that your software is up to par with your company's standards.
Control over changes: Using a change management system and configuration management techniques and tools, it enables effective software change management.
Data Inc’s
The e-Learning roadmap from Data Inc. uses a staged approach to content production. It has been modified for use with learning management systems as well as the creation and implementation of a variety of e-Learning modules, such as dashboards and campus gateways. It combines some project management and e-learning techniques so that the organization using it can gather requirements, turn them into tasks, distribute resources, and create and implement the program.
By transferring traditional learning methods to the Internet, DATA Inc. attempts to create an e-Learning system(Dogruer et al., 2011). Nevertheless, it makes use of the advantages of the Internet, such as chat rooms, shared resources, and flexible user role definition. The formation course is now presented by DATA Inc. using Microsoft Power Point. This method includes dashboards and campus portals, both of which are crucial for online classrooms. It is a wise decision to use this program since it provides a venue for gathering resources and putting information to use, which promotes an environment that is productive for education.
Project Timeline: required
Budget
A project's budget is the sum of money set aside to achieve the project's objectives within a given time frame. Managing a project's finances effectively means staying within a predetermined budget while still accomplishing the project's objectives.
Human or Labor Resources
Equipment and Material Resource
Conclusion
Illiteracy will be a thing of the past, students won't have to travel far for this type of education, workers, parents, and many other people will be able to attend class without feeling guilty about ignoring their duties, the bias that is sometimes present between lecturers and students in physical institutions will be reduced, students will be more motivated thanks to the excitement that comes with e-learning, and parents won't have to whine about the negative effects on their children. Online classes can therefore be successful with the help of collaboration and the information acquired from the university's various stakeholders and their priorities.
REFERENCES
Dogruer, N., Eyyam, R., & Menevis, I. (2011). The use of the internet for educational purposes. Journal of Procedia - Social and Behavioral Sciences, 28, 606–611. https://doi.org/10.1016/j.sbspro.2011.11.115
Hitka, M., Štarcho?, P., Lorincová, S., & Caha, Z. (2021). Education as a key in career building. Journal of Business Economics and Management, 22. https://doi.org/10.3846/jbem.2021.15399
Junus, K., Santoso, H., Putra, P. O. H., Gandhi, A., & Siswantining, T. (2021). Lecturer Readiness for Online Classes during the Pandemic: A Survey Research. Journal of Education Sciences, 11, 139. https://doi.org/10.3390/educsci11030139
Meyer, J., & Barefield, A. (2012). Developing and Sustaining Online Education: An Administrator’s Guide to Designing an Online Teaching Program.
Mohammed, O., Rida, N., & Chafiq, T. (2021). Overview of E-Learning Platforms for Teaching and Learning. International Journal of Recent Contributions from Engineering Science & IT (IJES), 9, 21. https://doi.org/10.3991/ijes.v9i1.21111
Öncü, S., & Cakir, H. (2011). Research in online learning environments: Priorities and methodologies. Journal of Computers & Education, 57, 1098–1108. https://doi.org/10.1016/j.compedu.2010.12.009
ENGR9742 Systems Engineering Assignment Sample
Assignment Brief:
For this assignment, you will work individually. The purpose of this assignment is for you exercise your understanding and knowledge of systems engineering principles to develop a product of your choice.
Task:
Now, imagine that you alone have been tasked with the responsibility to design a product for a customer. In your report, you must:
1. The introduction clearly explains the nature of your product. There must be a top-level system diagram, fully annotated, and referred to in the body of the introduction text.
2. Concise explanation of the application of ethics and standards throughout the testing, integration and eventual de-commissioning of the system.
3. A detailed description of the Stakeholder requirements.
4. A clear explanation of the System Requirements.
5. A clear description of the Functionality analysis.
6. A clear explanation of the development of suitable system architecture.
7. Concise application of the assignment template. Grammar, spelling, punctuation, and use of figures are appropriate. All figures are introduced in the text and their relevance is explained. Identify any safety issues and how they are addressed. Include discussion about any potential undesirable emergent system-behaviour.
Key assumptions and choices are described. There understands of the importance and necessity for feedback from testing phase that informs potential modifications to the requirements or to the functionality.
8. A well-developed architecture is presented. If appropriate, (mathematical) models should be used to explore/optimise parameter settings.
9. There is a clear appreciation and understanding of the products potential failure mode
10. Testing and Verification of the system
11. Validation of the system
12. Factory Acceptance testing and Commissioning Process
13. An informative conclusion that describes the status of the system.
Prepare a detailed report, no more than 20, on the delivery of a successful system to your very wealthy customer. Your report must comply with the template provided. Consult the information regarding the writing of a formal report, available on FLO. Identify your major contribution in the report. Have an introduction and conclusion.
Solution
INTRODUCTION
Smart health prediction system
Anyone may have experienced the frustrating reality that a doctor is needed right away yet none are accessible. The Health Prediction system is an opportunity to help that aims to provide end-user assistance and virtual medical advice. This study focuses on and suggests a method through which people may obtain immediate advice on medical matters via a smart online health care system. A variety of symptoms and the diseases or illnesses they represent are input into the system (Sapkal et al. 2020). Users are able to communicate their problems and symptoms to one another via the system. The system then analyses the user's symptoms to look for potential diseases. In this case, the system employs smart data mining algorithms to determine the most likely diagnosis that corresponds to the patient's symptoms. In the event that it is unable to do so, the system will notify the user of the illness or ailment with which it believes the user's symptoms are most strongly connected. Diseases that the user is most likely to have based on his or her symptoms are shown if there is no precise match in the database. Feedback and an administrator's dashboard are also included, as are doctors' addresses and phone numbers (Nevon Projects 2022).
System diagram
.png)
Figure 1: System diagram of health prediction system
ETHICS STANDARDS IN SYSTEM TESTING
In the development and implementation of the Smart health prediction system, many guidelines and regulations have been established for software testing that developers must adhere to in order to ensure that their products are both reliable and up to par with international norms. Moreover, testers are obligated to adhere to a variety of codes of conduct to protect the privacy and security of the data they have access to. Furthermore, they shall comply with the following code of ethics to guarantee the integrity of the works, which includes considering the safety and welfare of the public and the customer. Among the many moral compass systems are-
1. Public: The public interest and benefit should take precedence over business and personal gain throughout the health prediction system development and testing process. They should always make decisions that benefit the public (Professionalqa.com 2018).
2. Product: the software product actually is the most critical thing to think about while evaluating software. The testers' work should be carried out with the goal of assuring the highest possible quality and efficiency of the final product.
3. Employer & Client: In addition to the public interest, health care system testers need to take into account the needs of their company and the people who will be using the programme. They need to behave in a way that satisfies their customers' wants and demands.
4. Profession: the testers' team should uphold the honour of their profession by adhering to a strict code of ethics.
5. Management: team managers and leaders are tasked with taking on the responsibilities and following the ethical procedures necessary to manage the software testing, development, and maintenance process. This will enable them to thoroughly evaluate each part of the programme without causing any misunderstanding (Center for Ethical Practice 2020).
STAKEHOLDER REQUIREMENTS
In the context of a project- Smart health prediction system, the term "stakeholder requirements" is used to describe the aggregated expectations of many different stakeholders. Example stakeholder requirements for Smart health prediction system inspection are shown below.
• Operations: As an example of a capability that is essential to operations is the ability to service technological equipment. As an example, the capabilities of a production line are only one kind of limitation that might originate in the operations division.
• Business units: As an example, the capabilities of a production line are only one kind of limitation that might originate in the operations division. Depending on the nature of the project, product lines may proceed with user stories comprehensive specifications that specify the features, quality, needs, and functionality of the product.
• Customers: as the primary end-user, will provide input in the form of user stories or suggestions to enhance the Smart health prediction system initial usability, quality, and functionality.
• Subject matter expert: the requirements of specialists in fields such as architecture, engineering, layout, accessibility, technology, construction, legislation, and safety System Requirements
Functional requirements
• Creating the user account
• User must enter their authentic details
• User must enter the symptoms and select the options given for evaluation of their condition
• The application should allow the users for changing their profiles when required
• The app must retain the information and ensure top security and privacy
• The user must be able to access the previous reports and have he new one Non-functional requirements
• The app must maintain the privacy of the users and integrity
• It should have a proper database management
• The data must be quickly analysed
• The app must be easy to use and accessible anytime anywhere
DESCRIPTION OF THE FUNCTIONALITY ANALYSIS
• Patient login- Accessing the system by entering a user id and password.
• Patient registration- If one patient is a new user, the system will ask for his or her information before issuing a client ID and a secret key for entry.
• Prediction of the disease- As a consequence of his illness, the patient will exhibit the symptoms that have been predicted for him. The system will ask specific questions about his condition, analyse the answers to produce a prognosis, and then recommend doctors who specialise in treating the patient's specific sickness.
• Inquiry about Doctor- Patients may do a name, address, or specialty scan to find a doctor. Remark: Data collection: The patient will provide feedback, which will be considered by the administration. Module Position 2: Medically-Trained Expert in the Module Doctor
• Login- to enter the system, Dr. will enter his User Name and Password.
• Details of the patient- Data about the patient: When a patient registers, the specialist may access the information they provide (Reddy et al. 2019).
• Notifications- Alerts The doctor will be informed of how many patients have been admitted to the system and of the full range of symptoms to be expected from the system.
EXPLANATION OF DEVELOPMENT OF A SUITABLE SYSTEM ARCHITECTURE
To aid professionals in doing their jobs better, we have developed the Smart Health Prediction platform. An initial patient evaluation is performed within a framework that then suggests potential disorders. The process starts with the patient obtaining data about their symptoms; if the system correctly identifies their illness, it will then recommend a specialist who is conveniently located in their area. If the system isn't confident enough, it doesn't ask many questions, and if it's still not confident enough, it'll show the patient certain tests (Wang and Dong 2021). The framework will display the outcome based on the available total data. The study apply some smart mining techniques to determine the most accurate disease that may be related with the patient's outward appearance, and the study base this determination on a database of a few patients' restorative records, to which a calculation (Nave Bayes) is attached for tracing the side effects with possible diseases. Increased efficiency in the delivery of care to patients is a side benefit of this system's design (Li et al. 2021).
.png)
Figure 2: Block diagram of the system
(Source: Author 2022)
SAFETY ISSUES AND POTENTIAL UNDESIRABLE EMERGENT SYSTEM-BEHAVIOUR
• Patient data privacy concerns - With the use of Internet of Things (IoT) devices and the increasingly connected structure of the healthcare setting, doctors and nurses may provide better preventative and emergency care for their patients. The health records kept by SHSs are very private. However, SHS make individuals' health records susceptible to a wide variety of assaults. The major obstacles for intelligent medical systems are keeping patients' health information safe and private (Zeadally et al. 2019).
• Inter-realm authentication and interoperability issues- In order to build confidence for the sake of conducting digital health transactions, it is crucial that organisations operating in distinct domains be able to authenticate with one another across multiple realms. Lack of interoperability across countries planning to collaborate on ehealth Infrastructural facilities is another problem that needs attention as a prevalent digital health concern for nations. Lack of legislation for global collaboration among states on the sharing of sensitive medical information is also a contributing factor to this gap, along with insufficient ICT infrastructures and a shortage of IT professionals (Zeadally et al. 2019).
• Abuse of right to access and unauthorised access- By facilitating the safe and trustworthy electronic exchange of health-care information across a wide range of healthcare institutions, health information exchange (HIE) improves the quality of treatment provided to patients. Security and privacy concerns are major reasons why HIE systems haven't been widely used yet. The following are some problems that are experienced by contemporary HIE systems: The first is when trusted insiders misuse their position. The former may exploit their access to the HIMS to steal sensitive information, while the latter may opt to sabotage the system as a means of getting back at their former employers. Third, an outsider tries to hack into the system or pose as a member of the medical staff in order to get access (Zeadally et al. 2019).
TESTING AND VERIFICATION OF THE SYSTEM
System of test cases drawn from requirement specification to a working system is a common definition of system verification. Creating test cases that accurately represent the objectives in range and special significance after translating the requirements document is a time-consuming process. Man-in-the-loop checking with some little automated processes is the standard, even though automation (test fixtures) must be developed in most cases for engineering assignment help.
• System tests: Like the criteria that inform them, testing procedure are (mostly) transparent. But certain specifications need an amount of internal covering equal to those test cases. That means further requirements need to be added if any portion of the design or the implementation can't be confirmed by the testing process that encapsulates all the needs.
• Wafer test: Initial production testing begins with a wafer test. A wafer prober is often used to provide electrical stimulation to dies on a wafer during a wafer test. Wafer final test (WFT), circuit probe (CP), and electronic die sort are examples of assessment techniques used in this process (EDS). Wafer testing is the last step before final packaging.
• Manufacturing defects test: The second phase involves a test designed to detect problems caused by production. In order to differentiate between the right and defective behaviour of a circuit, a test engineer employs an automatic test pattern generation (ATPG) software to build test patterns. Automatic test equipment (ATE) is used to continuously administer training examples and verify replies.
• Characterisation test: The third stage aims to describe and filter chips before sending them out to consumers. Finding the optimal operational parameters of the device, such as voltage and frequency is the goal of the characterisation procedure.
• Functional test: The fourth stage, the functional test, is the process of applying functional test procedures to a chip in order to locate functional faults. To obtain the required coverage, the various components of the chip are put through their paces using functional test patterns that operate at real-world rates.
REFERENCES
.png)
ENEM28003 Fluid Power Engineering & Control Assignment Sample
Assignment Brief
1. Introduction
There are three main methods of transmitting power: mechanical, electrical and fluid power. Fluid power systems can transmit power more economically over greater distance. The work is accomplished by a pressurized fluid bearing directly on an operating fluid cylinder. A fluid cylinder produces a force resulting in linear motion. The fluid power systems are well suited in many industries because of their many advantages: easy and accuracy of control, multiplication of force, constant force or torque and simplicity, safety and economy.
Figure 1 presents a fluid power hydraulic press system. The purpose of this circuit is to control motion of the cylinder. The cylinder must extend, bottom out and hold pressure on the plates for some fixed period of time. During this time, pressure must be maintained in order to maintain the contact pressure between the plates (Figure 1b). The popular applications are bonding two pieces of metal together with an adhesive, holding a mold closed while the material is setting, etc.
.png)
Figure 1: Hydraulic press circuit (part) (Johnson, 2002)
If pressure is to be maintained, the directional control valve (DVC) must be left in the extended position even after the cylinder is fully extended (Figure 1b). Whenever the cylinder is bottomed out, the flow of oil is going over the pressure relief valve. This is a wastage of fluid power. This study should focus on how to manage the wastage of fluid power. This can be achieved by inserting additional parts into the fluid circuit diagram.
Simulation of a hydraulic circuit in Matlab is a good way to study and analyse the hydraulic circuits you design. In Matlab, you have to use SimScape (Simhydraulic). You have to go to Fluids, then Hydraulics (isothermal). From the library menu, you can draw the circuit. This menu has various
components needed to construct a fluid circuit diagram. By choosing the right components, the hydraulic symbols are assembled for analysis.
2. Aims
The aim of this project is to exercise your theoretical knowledge of fluid power systems and skills in practical applications in the area of mechanical and process engineering using Simscape in Simulink (Matlab).
3. Scope
You are required to study, analyse and assess an existing conventional hydraulic press system considering information available (you can assume some reasonable necessary data). Then design a new hydraulic press system or modify the existing design that has better performance. This is a team submission and each team must present their findings in a week 6 workshop session.
Your submission should have the following items and headings:
(1) Introduction to fluid power systems relating to hydraulic press systems
(2) Literature review on Conventional hydraulic press systems using standard papers from journals, conferences, books and reports
(3) Working principles of existing hydraulic press systems.
(4) Develop a case based on your research and develop a set of assumptions for your proposed design (operating pressure can be about 170 bars for example)
(5) Design and analysis of a new or modified hydraulic press system that gives better control: flow control, pressure control and directional control using sufficient minimum controlling devices and valves
(6) Safety check of pipes and pressure cylinders (thick-walled or thin-walled analysis)
(7) Prepare an Excel calculation sheet to put input data, standard equations, creating plots to compare
(8) Health and safety practices required for maintaining the system.
(9) Use proper drafting tools to show changes in your new design.
(10) Draw necessary fluid circuit diagrams
(11) Apply SimScape and carry out an analysis of your new design: piston positions, velocity, flow rate etc. vs time. Verify your simulation results.
(12) Preparation of team report and submit it in the Moodle link as per the due date.
Your report must include an executive summary, scope and objectives, methodology, schematic diagrams where necessary, discussions and concluding remarks, and references in the Harvard system.
4. Submission: It is a team submission. The due date is Friday midnight, week 6. The completed team charter document with signature will be with the team report (2nd page).
5. Reference: Introduction to Fluid Power, James L. Johnson, 2002.
Solution
Introduction
The hydraulic circuits you create can be studied and analysed by simulating them in Matlab. SimScape must be used with Matlab (Simhydraulic). Fluids must be selected before Hydraulics (isothermal). Construct the circuit using the library menu. The many items on this menu can be used to build a fluid schematic diagram. The hydraulic signals are put together for evaluation by picking the appropriate parts.One of the earliest types of machine tools is really the hydraulic press. is well suited for press operations in its current guise, from coining jewellery to forging aircraft parts. Today, industrial structural steel forming is frequently done with hydraulic incremental forming presses. Those machines are especially valued by small drawn component customers and manufacturers to the auto sector due to its high degree of process formability. vast variety of manufactured objects' shapes An effort is being made in the current systematic review to analyse the earlier research that has been done in the various structural design and analysis methodologies of hydraulic press(Huang, et al., 2019). One of the production processes, metal formation is primarily carried out on hydraulic presses. A compression moulding machine operates with an impact force. Some injection molds receive stress concentration and some parts experience longitudinal stress as a result of ongoing impact load. A CAD tool and a FEA tool like ANYSYS Keywords- Optimisation can be used to optimise the machinery framework, which is necessary to solve this issue(Adesina 2018).
Literature Review
Using physical processes and differential calculations, finite element analysis is the act of analysing a structural system in order to forecast its responds and behaviours. Determining internal forces, tensions, and genetic abnormalities of structures under diverse rates are high is the primary goal of structural analysis. Engineering's structural design division deals with structures made up of various structural elements. These elements, which are joined by pins or fixed joints, can be categorised as either bridge or frame components. In recent years, design approach has grown in importance as a tool for design professionals(Rani, et al. 2021). With the adoption of greater kinds of optimization by the industry, constructions are getting lighter, tougher, and more affordable. By maximising the weight of the material used to construct the building, using the best resources feasible while designing the compression moulding component can result in cost reductions. The quantity of the product, the price of the press, and its portability have all been attempted to be decreased. A 2D nonlinear magneto-mechanical study of an electrical motor using finite elements was presented by Errol et al. The proposed technique permits the accurate simulation of the whole switching cycle of a toggling, short stroke magnetic actuator(Yang, et al. 2018).
In the modern engineering sector, this kind of problem solving and product improvement is now an essential component of the system design. Since the development of mathematical analysis in the 1670s, optimizing has had a mathematical foundation. All contemporary manufacturing companies are working hard to create lighter, more outlay goods that also meet design, operational, and reliability requirements. In this situation, product design procedures that we all have researched in the literature are becoming more and more attractive thanks to structural optimization methods like topology and shape optimization. A corporation must upgrade its designs in order to compete on a worldwide scale. Additionally, saving is crucial for their upcoming endeavours(Wang and Chen 2022).
Finding the structure with both the best objective in light of a set of criteria is demonstrated in the following optimization. Design variables were entered used in the optimization. Challenging to create can be subdivided into many subfields depends on the type that the input variables are represented by. The performance parameters in form optimization are parameters that affect how the structure's boundary is shaped in part. When sizing characteristics like merge area, girder or stacking sequence are manipulated variable, we talk about size optimization. Topology optimization seems to be the structural mechanics subfield with the broadest use.A hydraulic press is a device that produces compressive stress using an air compressor(Luo, et al. 2018). The hydraulic press's major parts are its frame, hydraulic cylinder, and pressed table. In this assignment, the design technique was used to create the press frame, cylindrical, and press table. To enhance their effectiveness and quality for press operating operation, they are examined. By maximising the strength of the product used to construct the building, to use the best resources feasible while developing the hydraulic press sections can result in cost reduction. The quantity of the content has been attempted to be decreased in this way. Therefore, in this research, we take into account a mass optimization project for an H-frame hydraulic press used in industry(Du, et al. 2019).
Methodology
In addition to meeting a number of crucial requirements, this press must adjust for forces operating on the operating plates. Here, we employ implementation to analyse and improve the hydraulic press. In order to make the process of manufacturing small components in large quantities easier, this study aims to combine the hydraulic press's mechanical and hydraulic systems. Time constraints are a key factor in the current environment for the successful completion of any manufacturing operation. Therefore, with the help of automation, the manufacturing time may be cut down while also increasing accuracy because less human work is required. With the use of these tools, an effort has been made to ensure the quick and efficient operation of press work(Hua, et al. 2021). A hydraulic press is a device that generates force by pressurising fluids. These devices consist of a straightforward cylinder and piston system. A huge cylinder and a large piston make up the press, along with a smaller cylinder and a smaller piston. A pipe links the two cylinders, the huge one being larger than the smaller one. The pipe separating the two cylinders and indeed the two cylinders are both filled by liquid. At about this moment, Pascal's Principle governs how the hydraulic press works for assignment help.
In a device known as a Press, working forces are organised, directed, and managed. Thus, employing the hydraulic component in the press machine, an effort is made to two sounds the operation of press labour. The output signals of the mechanical machinery and rotary encoder are entirely electromechanical, such as spinning shafts or reciprocating plungers. The main benefit of putting this system into place is the ability to move heavy machinery. This movements can be started by hydraulic power, which can take the shape of a lever for human application or switching for automatic operation. Additionally, direction control systems have been installed to help regulate the orientations of piston motions. In a hydraulic press system, a liquid—typically crude oil—is pumped deep below under intense pressure to power a jet pump or a revolving pump. This pumping technology is very adaptable and could be used to create wells with low to high volumes. This technology has a greater fluid production capacity than the conventional lift pump. A hydraulic lift employs a pump to deliver oil under extreme pressure. The liquid is pushed to the bottom of the piston to lift it out of its seat by the pump pressure, that is typically between 300 as well as 400 kilograms per square centimeter. This lifts the load attached to the compressor assembly's head comparatively. To keep running, the necessary power oil or created water is recovered and reused(Du, et al. 2019.
Results
The hydraulic press and hydraulic system function similarly since they both rely on Pascal's Law for their operation. A hydraulic press is made up of the fundamental parts of a hydraulic system, such as a cylinders, pistons, pneumatic pipes, etc. This press operates in a fairly straightforward manner. The fluid (often oil) is pumped into the cylinder with the different radius in the system, which consists of two cylinders. The slave cylinders is the name given to this cylinder.This cylinder's piston is pushed, compressing the fluid inside it as it passes throughout a pipe and into the bigger cylinder. Master cylinder refers to the larger cylinders. The master pneumatic cylinder piston forces the fluid back to the previous reservoir as the pressure is applied to the ratio of the diameter. When the smaller cylinder is pushed into the hydraulic pump, the pressure the larger fuel tank applied to the fluids is increased. The hydraulic press is mostly employed in industries where wire mesh sheets need to be compressed under strong pressure. With both the aid of the press plates and the material being worked on, a professional hydraulic press can crush or compress the substance .
Discussion
A mechanical device used to lift or compress heavy objects is called a hydraulic press. Hydraulics is used to provide the force in order to boost the power of a basic mechanical level. The normal setting for this kind of machine is a factory setting. The NASA website has a decent explanation of "pressure vessels" and Pascal's Law, which may be the foundation of hydraulics. I have transcribed it here. In hydraulic pumps, forces are transferred from one area to another inside an incompressible viscous fluid, including water and oil.Hydraulic presses are 3-D complicated structures that are difficult and night before going to bed to analyse using a precise analytical method for stress and hyper - parameters. A reduced plane stress (PS) FEM models for a 918 kN hydraulic press architecture (welded frame) has now been chosen for investigation in order to decrease core memory requirements and computing costs. The deformation and stress characteristics are fairly consistent with those found from 3-D research. The PS model of assessment has been used to compare how the structure behaves even if it is invalid for generating actual values for complicated structures. Fillet, edge slicing, the presence of apertures, the relocation of reinforcing bars, and eccentricity loading are all taken into account.
Conclusions and Recommendations
- An oil leak is one of the most frequently reported issues; you'll see oil surrounding the ram, the hose end connectors, and the hydraulic lines. Assure all connectors are snug and you have used the hydraulic press's specified oil.
- Your press may overheat due to excessive friction & pressure as well as tainted or deteriorated hydraulic fluid. In order to prevent harming the sealing materials, hydraulic presses should never exceed a degree of 150° F. Make sure not to work overtime your presses, and make absolutely sure the filtration and oil are changed frequently(Yang, et al. 2018).
- In most cases, hydraulic presses typically reach the necessary pressure levels in about a second; if it takes longer, there is likely an issue with the pump since the fluid is not getting to the ram rapidly enough. Help ensure you inspect the pump along with related components like the pressure release valve and motor to ensure that everything was in functioning order and is clean since this could be triggered by leakage or dirt becoming stuck in the fluid.
- The produced manually operated hydraulic press was made possible by adhering to the work's specified goals. The materials used to build the produced machine came from the neighbourhood. The majority of the machine's parts were fabricated using mild steel. The interoperability of the mould and die without removing the ram assembly is a crucial component of this hydraulic press.
The produced hand operated hydraulic press was made possible by adhering to the work's specified goals. The materials used to build the produced machine came from the neighbourhood. The majority of the machine's parts were fabricated using mild steel. The tunability of the mould and die while removing the ram mechanism is a crucial component of this press machine. The machine that was created is depicted in Figure, which displays a cylinder engine compartment before having a sleeve pressed into it. Machine framework, structural parts, welds, pumps, and cylinder mechanisms were examined beforehand to look for any faults or hydraulic oil leaks before machine performance was assessed.
References
.png)
ITECH7410 Software Engineering Methodologies Assignment Sample
Final Seminar Requirements
The purpose of this assessment is to provide students with the opportunity to apply knowledge and skills developed during the semester and to demonstrate knowledge skills and expertise regarding Software Engineering Methodologies. Students must prepare their seminar content individually, but present in groups of four.
As part of the coursework and assessment in this course, students have had the opportunity to familiarize themselves with quality assurance, metrics, requirements analysis, specification, modelling, and design using formal software engineering techniques and tools. Students have also conducted research into the techniques and methods that could be applied to the software engineering tasks involved in design of a Smart City. Consistent with international standards in software engineering, it is important that software engineers take a holistic approach when considering a new project. They therefore should include processes for quality assurance, verification and validation in the methodologies adopted for a particular project.
The learning outcomes of this course require that students develop and demonstrate the following skills:
• Critically analyse and use complex decision making to research and determine the appropriate Software Engineering tools and methodologies to utilize for a given situation
• Apply professional communication skills to support and manage the engineering of a large software system
• Review, critically analyse and develop artefacts to define processes for quality assurance, risk management, and communication in large software development projects
• Implement quality assurance activities in order to verify user requirements and validate design decisions.
• Analysis of a large system development problem to decide upon the best methodological approach.
• Development of appropriate artefacts to support and manage the software engineering process such as change control and configuration management.
In this seminar, each student needs to focus on a different aspect of the Smart City software engineering development project. For their chosen aspect, they should consider the appropriate methodologies and tools that should be used to approach the engineering of a solution. Students are not asked to prepare a complete solution but are asked to describe what would be required in terms of work processes and artefacts that would be produced. The submitted report and presentation should outline how the chosen artefacts and processes would ensure quality in the final solution. For example, a student may be focused on education in a smart city. The student would need to explain the model/s that would be used relating to education in smart city.
Each student individually should prepare a professional level report in which they outline the methodology including processes, tools and modelling techniques that they recommend for their area of focus. This report should include references to appropriate literature to justify decisions made. Additionally, students should provide example artefacts to demonstrate what would be expected in the project itself.
Each group of 4 students should prepare a 20-minute seminar (5 mins each student) in which they will present their proposal to the class. This presentation should be appropriate for an audience of high-level executives who would be the stakeholders responsible for sponsoring this project. Students should include demonstration of the types of artefacts that would be created and justify how the proposed methodology is appropriate.
Each group can choose the focus area based on previous work each member has already completed. It is important that each student work on a unique aspect of the Smart City project.
Requirements
Students must record and present a seminar presentation as a panel discussion. Each student’s contribution must address their focus topic and must be based on their individual report. This content must be based on some research of recent (within 5 years) literature in academic peer reviewed journals and conferences relating to software engineering. The seminar will be presented by groups of 4 with each student taking responsibility for their particular focus topic. Each student will be individually assessed based on the material they present.
The broad topic of the seminar is What methodology is appropriate for the analysis and design of a complex Internet of Things system to be implemented to create a Smart City’s;.
Assessment Details
This assignment will be assessed by the lecturer. The assignment requires that students address the requirements outlined below.
Assessable Tasks/Requirements
Students are to provide both an individual report containing their content and reference material and the group is expected to submit a recorded seminar presentation.
Each student is expected to individually submit to Turnitin a report that they have individually prepared, particular to their specific sub-system and topic relating to Internet of Things and an implementation of a Smart City. Each group is to prepare a cohesive seminar discussion in which each student presents:
• The focus area of their seminar contribution i.e. the problems that they have focused upon
• What methodology would be appropriate to this topic. This approach must be justified and must describe the steps involved
• What artefacts would be produced in analysis and design. Examples must be provided of each artefact relating to the topic
• How the requirements would be validated
• How quality would be assured in the engineering of the system
Solution
Introduction
As part of this report, the design and analysis of a real-time money transfer system for a smart city will be carried out. This report will be a component of an assignment in which will analyse and create a control system. The construction of the control system will be the primary emphasis of the project. In conjunction with the duty of establishing a control system that has been delegated to us, this will be carried out. This examination of the real-time software system will include not only the data that is essential to the inquiry but also the control and process specifications that will be implemented into the system. (Alam, 2019)
This part of these communities is an absolute necessity due to the fact that the vast majority of the essential services that are provided to inhabitants in smart cities demand some form of payment. As a result, these communities must also have this component. These fundamental services are the engine that drives everything else, including the spending of companies on goods and services, the pay of employees, the spending of consumers, and the revenue of the government. The number of municipalities that have recently come to the realisation that the installation of cutting-edge payment technology is crucial to the notion of the intelligent city has recently increased. This realisation has come about as a result of recent events. Digital payments have the ability to facilitate a wide variety of citizen-to-government interactions (also known as C2G transactions), including toll and transit, transportation, water, education, tourism destinations, welfare care, healthcare, CFC centres, fines, and public convenience. (Wohlin C. R., 2020)
It is also feasible for it to include a wide variety of other types of payments made by the government to its residents. Some examples of these types of payments include pensions, subsidies, grants, and scholarships. These applications are causing a decrease in the need for currency, which, in turn, results in increased productivity and security. However, widespread adoption encounters obstacles not only from within but also from outside the organisation. Now that we have that out of the way, shall we take a closer look at each of these obstacles? (Digiplay Guru, 2020)
Methodology
The IoT, as has been noted, increases communication between objects with minimal human involvement. This quality is highly sought after by retailers because it simplifies the purchasing experience for customers. Internet-of-Things (IoT) payments involve the transmission of funds via a device linked to a financial account. To prepare the groundwork for the technological solution, the usage view details the user's flow through each stage of the use case. Both the human and mechanical participants in the action would be visible in this perspective. The usage view additionally provides a description of the use scenario from the user's and the system's perspectives. If this case study is applied, then every newbie has a significantly better probability of being pleased with IoT payment. As the number of people making IoT payments grows, so will the amount of data available for analysis.
Here is the process and methodology of using agile for the real time money transfer for assignment help.
.png)
The state-of-the-art method relies on a modular, end-to-end Financial Services platform that provides businesses with plug-and-play access to bank loans, personal finance management, and customer on boarding solutions via Australia's most advanced and reliable CDR Gateway, allowing for rapid deployment of Open Banking-powered use cases.
Digital payments have the ability to facilitate a wide variety of citizen-to-government interactions (also known as C2G transactions), including toll and transit, transportation, water, education, tourism destinations, welfare care, healthcare, CFC centres, fines, and public convenience. It is also feasible for it to include a wide variety of other types of payments made by the government to its residents. Some examples of these types of payments include pensions, subsidies, grants, and scholarships. These applications are causing a decrease in the need for currency, which, in turn, results in increased productivity and security. However, widespread adoption encounters obstacles not only from within but also from outside the organisation. Now that we have that out of the way, shall we take a closer look at each of these obstacles? (Hong, 2020)
Artefacts
DFD Level I (Risk Management and Quality Assurance)
In this step, there are also phases that are implemented by humans, and their purpose is to check whether or not the setup is correct before continuing. On Level 1 of the DFD, we are shown the process that is carried out by each direct entity in the RMT system. This method consists of checks at each level to ensure that the previous one was completed correctly before moving on to the next. The preceding diagram breaks the process of authentication down into its four primary steps: authenticating the user, authenticating the receiver, authenticating the OTP, and authenticating the transaction. (Park, 2019)
• Verification of User
• Verification by OTP
• Verification of Receipt
• Verification of Transaction
DFD Level II (Risk Management and Quality Assurance)
Users demonstrated each RMT scenario while doing fundamental activities at the DFD2 level. It provides a comprehensive description of the process by defining each stage in terms of the entire control, and data flow included within the system, in addition to describing the relationship between the present state and the dates that came before and after it. For example, the User verification state of the DFD 2 level compares the credentials provided by the user to those stored in the database to determine whether or not they match. If the credentials match, the RTM procedure moves on to the next stage; otherwise, it comes to an end. (Li, 2019)
• Verification of User Account
• Verification of OTP
• Verification of Transaction
Validation
Process Specifications
Login
.png)
Choose Transfer Money Option
.png)
Selecting Existing Receiver
.png)
Selecting New Receiver
.png)
Requesting Confirmation Code
.png)
Control Specifications
The "Control Specification," also known as the "CSPEC," specifies the processes that the software device is anticipated to carry out in response to an occurrence or signal. When an event occurs, the system will show the appropriate procedure that was activated as a consequence of the occurrence of the event. There are two components that are utilised when attempting to portray the overall control and data flow of the software system. (Wohlin C. R., 2020)
The Process Activation tables contain information that was gathered by directly examining the state transition diagram. This information can be accessed in those tables. This number indicates that the processes connected to the data flow model have been initiated when a given event has taken place, as demonstrated by the fact that they have begun. There is a manual that is at the designers' disposal, and they can use it to guide their work. However, it does go into detail on how the system responds to occurrences, which is included in the specification. The control specification for software does not go into depth on how the system functions or what procedures are set into motion when an incident occurs. (Peretz Shoval, 2020)
Discussion
This document also provides an overview of the fundamental procedure and entities that need to be stated and depicted in this submission. Specifically, the application is known as Draw.io, which is utilised during the process of developing such diagrams. Draw.io is a piece of open-source software that is not only uncomplicated but also straightforward and easy to understand how to use. With the assistance of the capability to drag-and-drop, we are able to get it up and running, and there are no complicated setup procedures that are required. (Li, 2019)
Data Flow Diagram
Data Flow Diagrams, often known as DFDs after their more frequent abbreviation, are graphical representations of the flow of information and data within a piece of software. It does not demonstrate where the data is located inside the system; rather, it demonstrates how the data works within the system. It does not reflect the location of the data in the system. The major objective of a DFD, which was designed specifically for the purpose of carrying out this activity, is to present the capabilities of a piece of software. The same objective can be achieved with the use of data flow diagrams (DFDs). A DFD can provide a graphical representation of all of the requirements for the system in a single, easily accessible area. This is a fantastic example that demonstrates how well-suited some software systems may be to the task of data processing. A graphic representation of the flow of information for the approach that has been suggested can be found down below. (Stankovski, 2020)
A graphical representation that can be used to describe the stages of software development cycles is known as a data flow diagram (DFD). By employing a DFD, it is possible to ascertain what subtypes of software a system and the operations it carries out must have in order to function properly. In addition to this, it formalises the architecture of the operational software as well as the flow of information throughout the system. (Stefanini, 2020)
The information that was gathered from the system that was described can be observed in the figure that can be found right after the table in this section. "Log In," "Transfer," "Identity Verification by Choosing," and "Client Payment" are the names of the three processes, with the login information being held in a third database. In order for a user to use the system, they will first need to log in with their credentials (username and password). After the customer has determined which account should receive the funds and how much money should be sent, as shown in the diagram, the client can start the process of transferring money after making those determinations. (Peretz Shoval, 2020)
Control Flow Diagram
One type of diagram that graphically depicts the control flow of a machine is known as a control flow diagram (CFD). For the very first time, engineers in the 1950s were given the opportunity to depict the processes that dictated a product visually. This development was a significant step forward in the field. Control flow diagrams have the potential to include a broad variety of different components, such as if-then-else branches, loops, and case conditions, among others. In this example, we see how a geometric diagram can not only be used to depict the various steps that are involved in a process and the details that are associated with each step but it can also be used to show how one step leads to the next step in a logical progression. This is demonstrated by the fact that a geometric diagram was used to show how one step leads to the next step in the process. Utilizing the diagram in this manner is one way to accomplish this task. The control flow that is supposed to be used for the device is illustrated in the schematic that can be found further down on this page. (Thales, 2020) The procedure that users must go through in order to access the system is depicted in the following diagram in the form of an illustration. If the user name or password is entered successfully, the user will be taken to the forwarding interface. If one of these is entered incorrectly, the user will be taken to the sign how it feels to be a user of the service. The next step in the process is for the client to begin the money transfer by either selecting a payee from their list of saved payees or manually entering the payee's account number along with the amount that they desire to send. This step marks the beginning of the second stage of the procedure. The transaction will begin as soon as the user makes their pick if the user chooses a recipient who has already enrolled for the service. Before the transaction can be executed in any other situation, the customer is needed to complete the OTP authentication process in its entirety. As evidence that the transaction was carried out correctly, the customer can be given a receipt as a confirmation that the transaction was completed successfully. (Basham, 2017)
Conclusion
Before I started my study of the anticipated needs of the system, I did some research into the effectiveness of a real-time money transmission system. This was done before I started my analysis. My work on the logical structure of the software began with me determining all of the entities and the connections that existed between them. This was the first phase of my work. In order to discover the relevant entities and their relationships, which should both be incorporated into the approach that was presented, I carried out an analysis of the system. This allowed me to determine the pertinent entities. The process of conducting research for this paper allowed me to amass a considerable amount of knowledge concerning the inner workings of real-time money channels, which I will discuss in this article. During the course of creating the data flow diagram and the control flow diagram for the proposed system, I came across certain questions concerning the anticipated operation and data flow of the proposed system. (Wohlin C. R., 2020)
Users begin the process of signing in by providing their login information, which often includes a username and a password. Once this information has been provided, the user can move on to the next step of the procedure. I made use of the approaches and the memory stick in order to characterise each function that was included within the data flow diagram. These strategies have all been gleaned from a variety of outside resources, and more especially, the internet. After that, will get some practice in by entering the information about bank account and the amount of money want to send so that may become proficient in the foundations of making a money transfer. This is taken care of by the Transfer procedure, which is in charge of executing the necessary debit and credit procedures in order to move money from the source account to the destination account. The Transfer procedure is responsible for handling this. I had a hard time not just developing the data flow diagram for the system but also the control flow diagram for the system, and during both of those processes, I was trying to figure out which system events were relevant. In the end, I went back over the system design criteria and started developing the logical architecture based on an internal vision of how the data would flow through the system. This helped me have a better understanding of what needed to be done.
The system's development shouldn't get underway until after exhaustive requirement analysis and problem specification have both been finished. In order to successfully achieve this goal, it is essential to compile streamlined descriptions of each process and sub-process that the system manages. Because of this, it is absolutely necessary to make use of the models and procedures that are associated with software engineering in order to explain and design the fundamental flow of software as well as the expected end of the process. This is because software engineering is associated with the development of computer programmes. Textual descriptions of the procedure are preferable to graphical ones because they allow for a more intuitive comprehension of the capabilities of the programme and the intended results of each operation. Graphical descriptions of the procedure are preferable because they are more time-consuming to create. One can search the internet and find graphical, great study, or pivot table descriptions of the technique. In addition to this, it directs them through the steps necessary to set up an RMT Framework that is fully functional within the new bank.
R education in the knowledge and abilities required to analyse and comprehend a real-time software programme even as it was being constructed was the primary purpose of this project. The process of reviewing real-time money transfer systems, for example, makes use of data flow diagrams and state diagrams. This helped to define the purpose of these diagrams, which was one of the objectives of the evaluation process. Because of this task, I was able to immediately put everything I had learned in my classes into practice. I found this to be an extremely beneficial experience. I've learnt a lot about control specification diagrams, including state transition diagrams and process activation tables, two of the many various types of diagrams that are.
References
.png)
MANU1381 Sustainable Engineering Systems and Environment Assignment Sample
Overview
This task evaluates your ability to understand systems approach in engineering management. You will need to select, investigate and present an engineering system, its structure, included subsystems, and examine relationships among the subsystems. You are going to identify stakeholders and their expectations. Finally, you will identify problems, or challenges, existing in the system, and propose an appropriate solution, based on selected systems approach.
Assessment details
Task 1: Systems concepts
Examine the system under study in terms of its environment, complexity and system dynamics.
Describe and examine the relationships between the sub-systems and the system as a whole.
Evaluate the role of various stakeholders, shareholders’ expectations and the measurable requirements.
b) Explore how any future actions, or changes to any of the subsystems/elements, will affect the system as a whole.
Task 2: Systems methodology
Based on the system described in Task 1:
Apply the chosen methodology to the problems and discuss its potential issues and limitations.
Solution
Subsystems objectives/purpose
There are several subsystems available in Boeing and each of them completes a predetermined task within the organization and plays an important role in the overall development of the organization. The subdivisions of Boeing are listed as follows:
Business development and strategy: The subdivision is generally tasked with the creation of a business plan or a strategy Boeing follows so that it can gain maximum profit and achieve all its objectives within the stipulated time for assignment help.
Communications: The subdivision deals with public relations so that Boeing can continue to keep its positive brand image and the subdivision also handles internal communication within the company so that all the information can be properly relayed to the required personnel.
Finance: The general task for this subdivision is to take financial decisions for both the internal and external affairs of Boeing and they are also tasked with keeping a track of all the expenditures and incomes within Boeing.
Engineering, operations and technology: Since Boeing is a company that manufactures aeroplanes it is a necessity for them to have a dedicated subdivision that deals with the technicalities of producing an aeroplane and that includes the engineers that work on the plane to the people that are working in operations and even technical associates [1].
Human resource and administration: The department focuses on recruiting new job applicants and training them and even looking into the current employees and making sure that they are working with the proper skillset within Boeing.
Internal governance: The subdivision is tasked with dealing with the business objectives of Boeing and looks into the shareholders as well as the board members and comes to a unanimous decision that would satisfy the majority.
Legal department: Every company needs a legal department and Boeing is no exception because this subdivision deals with the l matters starting from patents to cases against the company.
Public policy: The subdivision is tasked with setting up a set of standards and laws which would be implemented within Boeing and they work as regulatory measures against a particular action.
Sales: The subdivision is simply tasked with selling the services and products that are developed by Boeing and they must generate a good number of sales so that the company can stay profitable and continue to achieve its objectives.
Elements of the subsystem and their attributes
After understanding the different subsystems that are present in Boing it is necessary to understand all the attributes that the systems possess. The attributes for the individual departments are listed as follows:
Business development and strategy: The elements generally involve the usage of data driven decision making and sales funneling to implement the strategies.
Communications: The attributes include internal communication channels within the organizations and departments as well as communication channels with strategic alliances.
Finance: The attributes involve reporting financial statements, budgeting that are important for the organization [2].
Engineering, operations and technology: The attributes of the subsystem include some type of raw input that is used for the manufacture process and the staff that operate on the raw input to produce the output [4].
Human resource and administration: Generally, the attributes constitute employee recruitment, employee training and maintaining employee retention [3].
Internal governance: The attributes involve management of the overall system through monitoring and including risk assessments so that the organization can take the correct action as per that assessment.
Legal department: The attributes for this subsystem include legal documents, dispute negotiations and other tasks that represent the organization’s legal prowess.
Public policy: The attributes include implementation of policies, maintenance as well as evaluation of the said policies.
Sales: The attributes include generation of market demand for the system, collection of sales funds and procuring the clients so that the system remains profitable.
Relationships of subsystems
The subtopic covers the different dependencies that each of the subsystems of Boeing has with one another and the details are covered in detail so that an understanding can be formed about the connection of the different dependencies and the importance of each of the subsystem in the Boeing system. Some of the subsystems like the legal department or the finance department play a major role in keeping the organization functioning and therefore they are given more importance but it does not mean that the other subsystems are not important since they also play a major role in their own sector and need to be addressed as well.
.png)
.png)
Relation between the subsystems
Source: (Developed by author)
System complexity
There have been some complexities in the system of Boeing wherein they were unable to conduct proper tests on some of their 737 aeroplanes and that led to plane crashes on two different occasions and that was caused because of multiple reasons starting from lack of staffing in the engineering department and issues related to their business strategy which focused on the sale of 737 flights but they were not in the condition to be sold right away and needed much more testing. What the engineers failed to see was that the working of the aeroplane depended on the functioning of the isolated parts together and they had not given much time of testing those components in an isolated condition which may have led to the complexity. The legal department is also facing issues because of these claims and there has been a problematic situation in the Boeing system which has caused some risk for the investors and stakeholders as the company is facing issues because of different reasons. It was one of the biggest mistakes of Boeing to allow the sale of the 737 flight after which the company’s value definitely took a hit and their reputation was damaged as well.
Dynamics of systems
To understand the dynamics of the system it is important to understand the systems influence the overall complexity of the system. In the case of Boeing its stock which can be considered part of the financial part is considered as a chaotic subsystem behaviour because the value of anything in the stock market is never stable and keeps changing after regular intervals. Generally chaotic behaviour can be represented using the following equation:
The behaviour is integrated over a time to understand the change in the system through this dynamic behaviour. The feedback also affects the change in the dynamic behaviour of the system and in this case new of Boeing could have an effect on the stock market price of its shares. While compiling the chaotic behaviour of the subsystem in Boeing it can be represented in the following manner:
One of the main factors that has affected the system dynamics of the company is the launch of 737 flight which caused major issues and legal issues which made the systems behaviour chaotic and it was not following any specific pattern.
Stakeholders
The stakeholders of Boeing can be roughly divided into internal and external stakeholders. Within the internal stakeholders there are employees, management and owners and in the case of Boeing Dave Calhoun is the CEO of company and a major stakeholder for the company. Coming to the external stakeholders there are suppliers as well as some external members that hold quite a lot of shares of the company which include Newport Trust Co. with a share of 7.52% of the company and The Vanguard Group, Inc. just to name a few of the major shareholders that play a major role in the business decision-making process of the company [5].
Problem/challenge and identification
Problem/challenge description
Boeing as a company is not perfect and faces some challenges that it must overcome to fulfil its objectives. Some of the problems are given as follows:
- Constraints in the research and development department
- Inconsistencies in the delivery of 787 flights by Boeing
- $7.9 billion defence charges
- Engineering shortage as well as operational staff shortage.
- 737 market entry at high risk
- Decreased profitability
- Lack of dividend demoralizing for investors
- Unclear strategy and services
- Plunge in the market share
Problem context
The problem scope, in this case, can be divided into the individual subsystems and the problem can be identified in the case of Boeing. The first subsystem that is being affected is the business strategy and planning department which deals with the company’s business methodologies and the steps that they are willing to take to obtain their objectives. The issue lies in improper planning of strategies which has led to the current set of problems for the organization which include staffing issues as well as legal issues [6]. Since there is an issue with the business strategy department the human resource and administration department has also been affected because of this and they have been getting issues in the recruitment of required operations personnel and engineers which has led to short staffing in that particular department [7]. Since there are staffing issues, the engineers have been overworked which has led to them making some errors which could cost a lot of money to the organization. Since the engineering department was unable to do their work properly which led to the failure of one of the products the legal department had to deal with the dispute related to the faulty product in this case an aeroplane.
.png)
(Cost of Boeing shares from 2016-2022)
Selection of system methodology
After understanding the current problem, it can be said that the first issue that needs to be resolved is the procurement of capital that the company must gain to solve some of its issues. The procurement of capital would allow the company to use that capital and solve the issues that are related to the staffing of the recruits, legal disputes and even dividend issues. In this particular case, a hard system approach might be much more useful because it would handle both quantitative and qualitative issues. The methodology has its own set of benefits when compared to a soft approach but it must be kept in mind the goals that must be achieved to make an impact on the system and use that method to get the best possible output in the given scenario. When selecting the hard system approach, it must be kept in mind that the approach is rigid and does not change in accordance to the change in requirements but it should be able to cater to the immediate issue which is of the utmost importance.
Application of system methodology
The first thing to do when the capital is acquired is to find and train some recruits that can be sent to the engineering department so that the short staffing issues can be resolved. Moving onto the next step the legal disputes must be handled so that the brand image does not get hampered. Once the legal dispute is settled a focus on providing dividends to the investors can be considered which would mean that a greater number of potential investors would be interested to invest in the stock and the current investors would retain their stock [8]. When the issue of the interrelated subsystems is solved a new business strategy could be developed so that the current organizational goals can be achieved.
Conclusion
From the understanding of the above study, it can be concluded that there are several interdependent subsystems within Boeing and the performance of one department does affect the others indirectly [9]. The company has faced some issues with their profits recently and they are required to take some necessary steps to deal with those problems and increase the profitability of the company once again. The relation between the company’s subsystems was properly understood so that the effect could be mapped out properly. once the relations were identified the root cause of the problems was found based on which a recommendation was provided for the subsystem and the application of the recommendation was also explained along with it. And with that, the study was concluded.
References
.png)




.png)
~5.png)
.png)
~1.png)























































.png)






