MIS101 Information Systems for Business Assignment Sample
Assignment Brief
Length 1500 words (+/- 10%)
Learning Outcomes
The Subject Learning Outcomes demonstrated by successful completion of the task below include for assignment help
a) Identify and explain components of information system for business.
b) Demonstrate an understanding of computing related mathematics.
Submission Due - by 11:55pm AEST/AEDT Sunday end of Module 4.2 (Week 8)
Weighting - 40%
Total Marks - 100
Task Summary
Using your understanding of computer number system and logic, answer the questions provided.
Context
Computer systems only understand binary numbers. The CPU, the main component inside a computer system, makes logical decision based on binary numbers. In Modules 3 and 4, you learned about computing mathematics and logic. This assessment focuses on your understanding of the number system and logic in computers.
Task Instructions
Read the questions carefully and give clear and precise answers.
Question 1:
a) Choose a sentence of no more than 25 characters containing your name (Example: ‘Kyle is in high school.’ Identify the ASCII code for each character; identify its decimal representation and then convert it into its equivalent binary number. (10 marks).
b) Convert the binary sequence (identified in part ‘a’) back to characters (5 marks).
c) Show the hexadecimal representation of each character in the selected sentence (5 marks).
Question 2:
Select an everyday real-life problem that requires two inputs. Once selected, represent it using a truth table. Explain the possible outcomes. Represent your problem using a logic diagram (20 marks).
Question 3:
Use the internet to investigate and explain what data transfer rate or speed is (10 marks).
Question 4:
How is the concept of Set Theory applied to Relational Databases? Give two examples (10 marks).
Question 5:
Identify and explain at least two applications of hexadecimal numbers in modern computing (10 marks).
Question 6:
Consider the following scenario:
The three inputs which affect the outcome of a business are:
1. the management is good
2. employees are satisfied
3. people are hard-working
If the management is not good, the organization will be in loss. If management is good and employees are satisfied but they do not work hard, then the organization will be in loss. If the management is good but the employees are not satisfied, then the business will break-even. If all three conditions are satisfied, then the organization will be in profit.
Analyze the scenario and identify the inputs and outputs to a process which decides the success of a business. Show this in the form of a truth table and logic diagram (30 marks).
Referencing
It is essential that you use appropriate APA style for citing and referencing research. Please see more information on referencing here: http://library.laureate.net.au/research_skills/referencing
Submission Instructions
Please submit ONE Word document (.doc or .docx) via the Assessment 2 section found in the main navigation menu of the MIS101 Blackboard site.
Solution
Introduction
In the world of computing, mathematics is an important subject as this is helpful for the students to use abstract language, deal with algorithms, self-analysis of computational thinking, and accurate modeling of real-world solutions. Thus, the unit here introduces the mathematical paradigm in the context of computing. Here, the researcher shows different calculations.
Question 1
a) Sentence: Kyle is in high school
ASCII code for Each character: 075121108101 105115 105110 104105103104 115099104111111108
Decimal Representation: 75 121 108 101 32 105 115 32 105 110 32 104 105 103 104 32 115 99 104 111 111 108
Conversion to equivalent binary number: 01001011 01111001 01101100 01100101 00100000 01101001 01110011 00100000 01101001 01101110 00100000 01101000 01101001 01100111 01101000 00100000 01110011 01100011 01101000 01101111 01101111 01101100
b) Binary to character: Kyle is in high school
c) Hexadecimal representation: 4b796c6520697320696e2068696768207363686f6f6c
Question 2
Real-life problem
Premise: If an individual bought bread, then he/she went to the store
Premise: The individual bought bread
Conclusion: He/she went to the store
So, for this, the truth table will be represented as:
For the given problem, the logic problem will be represented as:
Question 3
A data transfer often talks about the movement of digital data from one place to another, from a hard drive to a USB flash drive at a specific point in time. It is commonly used for measuring how fast data is going to be transferred from one location to another. For example, ISP often provides an Internet Connection with a maximum rate of data transfer of only 1.5 Mbps. It is measured in terms of either bit per second or bytes per second. A bit is used for measuring speed, while Byte is used for measuring size (Comer, 2018).
The rate of data transfer can be tested using various online tools. Most of them are known as internet speed tests. These tools are mostly used in order to get the broadband speed promised by the Internet providers. Various speeds are measured, such as speed of downloading, uploading, and also latency. Download speed talks about the time taken to transfer a file from the Internet to the user’s home network or computer. Uploading speed is referring to as time is taken for uploading a file to the internet. At the same time, latency, also known as ping, depicts the delay in the transfer of data from a server to the user's computer.
A slow rate of data transfer is the result of the computer’s hard drive, so this can be fortunately increased. Some of the ways to enhance it are:
? Changing the file system used for formatting the drive from FAT32 to NTFS.
? Tweaking the settings of the system to perform better
? Turning off the compression of the disk
? Another method is the upgradation of USB 2.0 to USB 3.0 or new versions.
In the case of a hard drive, the data transfer rate is of two types: External rate of transfer and internal transfer rate. External is also known as curst data transfer rate or interface rate that means the speed at which the data is moving between the internal buffer and system memory. On the other hand, the internal transfer rate is also referred to as the maximum or minimum sustained rate of transfer (Bhati & Venkataram, 2017). This means the speed of data is often read and written to the hard disk. The external rate of transfer is faster than the internal just because it is purely electronic and hence not relying on the efficiency of actual physical elements.
Question 4
A set is the collection of objects. Objects in this assortment are additionally supposed to be the set components or individuals. The most important point of this is members must define it clearly and exactly. An explicit definition of the member is not able to identify the set. For example, months of the colder time of year season is indicating a set, yet a few months are not determining a set. Consequently, sets are frequently named with the assistance of capital letters (Rodionov & Zakharov, 2018). Set names are given in curly braces and separated with the help of commas. Such a representation is known as Roster or Tabular form. X= {December, January, February}
It can also be represented using a Venn Diagram.
According to the set theory, the union of two sets can be helpful to get a new set containing members of the union sets. The below example can represent this:
A= {Orange, Apple, Lemon, Avocado, Strawberry}
B= {Lemon, Avocado, Apricot, Grape}
The union will be hence depicted by A U B.
A U B= {Apple, Lemon, Avocado, Orange, Strawberry, Grapefruit, Apricot}
The Venn diagram will be hence:
In SQL Server, the UNION operator is concatenating the result sets obtained from two tables and hence eliminating the duplicated rows from the outcome. In fact, here, this is acting just like a union operator in the Set Theory. If, B and A sets are defined using SQL server’s tables then, in this context, first, create the table and then add the expressions similar to A and B.
The union of these tables will result in:
Change in the order of tables in the query will not result in any alteration.
On the other hand, the intersection of two sets is generating a set containing the common members of the intersected sets.
A∩ B = {Lemon, Avocado}
In SQL Server, the INTERSECT operator is implementing the logic of intersection in the Set Theory to tables. So, the intersection of both tables A and B can be given as:
Question 5
Hexadecimal or hex with base 16 system is mainly used for simplifying the representation of binary. This hence means that an 8-bit binary number can be written with the help of two different hex digits, one for each nibble or group of 4-bits. Hexadecimal is utilized in the following manner:
? Defining the memory location: Hex has the potential to characterize every byte as two hex digits can only be compared to eight digits at the time of using binary.
? Defining colours on the web pages: Each primary colour, such as green, blue and red, is attributed by two hex digits (Massengale, 2019). The format that is used is #RRGGBB.
? Displaying an error message: Hex is used for defining the error location in the memory. This one is hence used by the programmers to find and fix the errors.
? Representing MAC addresses: There are 12-digit hex numbers in a MAC address. The format used is either in the form MM: MM: MM: SS: SS: SS or MMMM-MMSS-SSSS. The first 6-digits of the MAC address is hence showing the adapter manufacturer's ID, while the last 6-digits represent the adapter's serial number.
Question 6
For the given scenario, it can be observed that here three inputs are present they are: employees are satisfied, management is good, and people are working hard. From the scenario, it can be said that if the management is good and employees are highly satisfied with the work environment, then automatically, the companies can foster their business. However, if the management is good, but employees are less or not satisfied, then the organization will suffer a huge loss. If all the conditions are satisfied, then, obviously, the organization will be in profit. So, the overall scenario can be presented in the truth table. Once the truth table has been created, the logic diagram can also be created easily.
So, the logic gate for this truth table would be:
In this context, the "OR" operator has been applied. It is observed that if all the inputs are false, then the output will also be false. Similarly, when two false conditions are combined with one true value, then the result will be true itself. That means that if the management is not working well and employees are not satisfied but still working with great dedication, then also the organization is gaining a huge revenue because of high productivity level. Similarly, if all three inputs are false, then the firm automatically fails to provide the best service, and there will be a huge loss in revenue.
Conclusion
Comprehensively, it can be said that binary and ASCII codes are mostly used for transmitting data. These are codes to transmit data often used by smaller and less-powerful computers for representing both textual data and also non-input device commands. So, the unit discussed these concepts profoundly. The unit also consisted of some descriptive parts related to the computing world. The study also depicted the use of a truth table and logic gates for inferring a premise. This also discussed the relationship between set theory and relational databases. In this direction, the researcher used UNION and INTERSECTION operation.
References
Bhati, B. S., & Venkataram, P. (2017). Preserving data privacy during data transfer in manets. Wireless Personal Communications : An International Journal, 97(3), 4063–4086. Retrieved from: https://doi.org/10.1007/s11277-017-4713-2
Comer, D. (2018). The internet book : everything you need to know about computer networking and how the internet works (5th ed.). Chapman & Hall/CRC Retrieved from: https://lesa.on.worldcat.org/oclc/1052459938
Massengale, L. (2019). Digital systems design: numbering systems and logical operations. Momentum Press. Retrieved from: https://lesa.on.worldcat.org/oclc/1083457871
Rodionov, T. V., & Zakharov, V. K. (2018). Fundamentals of set and number theory (Ser. De gruyter studies in mathematics ser, v. 68/1). De Gruyter Retrieved from: https://lesa.on.worldcat.org/oclc/1023551253
Information Security Assignment Sample
Value: 15%
Due Date: 23-Apr-2021
Return Date: 18-May-2021
Length: 1000-1500 words
Group Assessment: No
Submission method options: Alternative submission method
TASK
This assessment relates to Topics 1 - 6 and consists of two tasks as follows:
Task 1 : Scenario Analysis (44 Marks)
1. Identify one real-life cybersecurity breach that may have occurred in the last 2 Years. Using the vulnerability-threat-control paradigm, discuss the breach (16 Marks).
Tip: You may use any one breach from the following link for assignment help.
2. Discuss the difference between cross site scripting (XSS) attack and cross site Request forgery (XSRF). Further, explain with justification, which attack is easier to defend against (16 Marks).
3. What is buffer overflow? Studies online (e.g. statcounter ) suggest Microsoft Windows has over 70% of the OS market share. For this reason, identify and discuss a feature in Microsoft Windows that prevents attackers from using buffer overflows to execute malware (12 marks).
Task 2 : Short Answer Questions (16 Marks)
1. Discuss the notion of "security through obscurity" and its implication on modern day computer security (8 marks).
2. Discuss at least two security advantages of a host running virtualisation (8 marks).
RATIONALE
SUBJECT LEARNING OUTCOMES
This assessment task will assess the following learning outcome/s:
• be able to justify security goals and the importance of maintaining the secure computing environment against digital threats.
• be able to examine malicious activities that may affect the security of a computer Program and justify the choice of various controls to mitigate threats.
• be able to compare and contrast the security mechanisms of a trusted operating system with those used in a general purpose operating system.
• be able to compare and contrast foundational security policies and models thatdeal with integrity and confidentiality.
GRADUATE LEARNING OUTCOMES
This task also contributes to the assessment of the following CSU Graduate Learning
Outcome/s:
• Academic Literacy and Numeracy (Knowledge) - Charles Sturt Graduates understand the use and structure of appropriate language in written, oral, visual, mathematical, and multi-modal communication.
• Academic Literacy and Numeracy (Skill) - Charles Sturt Graduates demonstrate the literacy and numeracy skills necessary to understand and interpret information and communicate effectively according to the context.
• Academic Literacy and Numeracy (Application) - Charles Sturt Graduates consider the context, purpose, and audience when gathering, interpreting, constructing, and presenting information.
Solution
Task 1
1. Identify one real-life cyber security breach that may have occurred in the last 2 years. Using the vulnerability-threat-control paradigm, discuss the breach
The world has been witnessing various cases of security breaches since the last decade. One major breach of the year 2019 was reported with regards to Facebook and its loss of confidential private data belonging to over 533 social media users. The founder of Facebook, Mark Zuckerburg could not provide the committed privacy and confidentiality to its millions of loyal users. Vulnerable data like the name, location data, phone number, emails, and other biological data were leaked. The investigators further found that the privacy controls security protocols implemented in this program were weak and had loopholes. As a result data of individuals from over 106 varied nations and 32million data records related to the US was the victim of a real security breach (Jackson, Vanteeva & Fearon, 2019, p. 1277). Serious doubts and questions were raised since Facebook conserved important data like emails and data of birth users, Serious doubts came as Facebook asked all its users to make a password reset be done with urgency.
The vulnerability Threat control paradigm is referred to analyze whether this real-life data breach case fulfills the requirements of computer security (Tamrin, Norman & Hamid, 2017, p. 131). CIA triad comprising of confidentiality, integrity and availability is considered as basic needs of computer security which Facebook failed to fulfill. Confidentiality was lost since user authorization was not there and still their data got leaked. Authorised Facebook users were deceived and were manipulated and hence integrity has been filed. The users were not safeguarded by the security system applied by Facebook and hence their information was not in their hands. This breaks the availability dimension of the CIA triad as well. It can hence be considered that the Facebook data breach incident has failed to provide privacy and security to the users.
2. Discuss the difference between cross site scripting (XSS) attack and cross site request forgery (XSRF). Further, explain with justification, which attack is easier to defend against
XSS or cross-site scripting attack is a web application-centric incidence of a security breach where data or content is vulnerable. Cybercriminal often follows the web programs which the client or users are using. Scripts especially JavaScript is induced in such web pages at the code end (Rodri?guez Germa?n E, Torres, Flores & Benavides, 2020, p. 166). When the potential victim hits these specific web site on their browser these script gets injected. It is an unethical activity where no permission is taken from the victim where they use the vulnerability of the website to exploit them.
CSRF or the cross-site request forgery on the other hand is a more server kind of computer security vulnerability caused by hackers. Cybercriminals at times will send requests in the form of an email communication where the victim will be urgently asked to click open a file or install a file on their system (Kour, 2020, p. 4561). Due to the urgency if this activity request is fulfilled then cookies are detected and interaction is carried out by a hacker. The cookies sit quietly and keep sending data of the co muter system comprised to the external hacker.
So, an XSS attack is where the user will be induced for performing any action. CSRF on the other hand is dangerous as it is associated with some subset activities which users are performing. This is more like a one-way kind of attack. XSS on the other hand is a two-way attack vulnerability.
When both of these attacks are compared it is found that XSS attacks can be defended more easily than CSRF attacks. This is because the security prediction of the ber criminal cannot be made easily for the latter. As result victimisation possible more than the first kind of attack where using ample protection mechanisms one can be protected.
3. What is buffer overflow? Studies online (e.g. statcounter) suggest Microsoft Windows has over 70% of the OS market share. For this reason, identify and discuss a feature in Microsoft Windows that prevents attackers from using buffer overflows to execute malware
When the volume of information to be stored is more than the usual capacity of the stye to store data inside buffer memory the event is termed a buffer overflow (Gao, Wang, Y., Wang, Yang, Z., & Li, 2020, p. 1406). In such a circumstance, efforts are made to conduct a program overwrite over data adjacent to the buffer memory site. This is also technically termed a buffer overrun.
Microsoft, for preventing any hacking incidents or intrusions has restricted such buffer overflow processes. The potentials that applications by Microsoft being exploited is a stack that is applied over the memory spaces. Here storage space is made available. The brand dominates the market and has over 76.56%of the market shares. This is possible as Microsoft makes use of DEP or Data execution prevention programs for the operating system design Windows XP and the SP2. Here the program is given autonomous power so that they can stop any malware to get carried out with the code where there is reach for non-executable memory spaces.
DEP feature in Microsoft is enabled so that any attack upcoming can be detected. The non-explicit memory is not executed. If the buffer overflow gets used up ht DEP protection is applied so the process is carried out without the program which will restrict the security bars automatically (Wang, Huang & Chen, 2019, p. 1). This is performed in two ways by Microsoft- address the space randomization process using ASLR or using the Data Execution Prevention method.
Task 2
1. Discuss the notion of “security through obscurity” and its implication on modern day computer security. All security engineer experts use their robust design, formats, and security mechanisms to be the primary tool to execute safety to their system. In this regards a concept of security through the notion of obscurity is used as the underlying principle for such a security execution by experts (Andrew, 2018, p. 1). In modern times, however, all computer systems and mechanisms are layered by their design. Often there are gaps and loopholes which are detected by the cyber criminals and they use them to attack or hack computer systems.
Such use of security approach using obscurity as the core principle is not a positive or effective one since it is about the protection of system and data. The security mechanism is hence effective only till w nth obscurity is not explored or discovered. Hence such an approach makes the system weak or vulnerable. A modern-day example can be given here. Imagine the owner of a precious residential house uses some of the best security locking systems to give protection to the door. To give effective safety and security jiggling is made through obscurity. However, sometimes tricky ways are used by cyber criminals to get insider information about codes which can then be used to crack open the lock. So as soon as the code is discovered the system becomes vulnerable.
2. Discuss at least two security advantages of a host running virtualization
Virtualization is one of the latest technologies which has revolutionized the way business enterprises conducted their operations. Small and medium scaled business organizations today use virtualized architecture to avail their security advantages (Gavrilovska, Rakovic & Ichkov, 2018, p. 67). In using virtualization, businesses can avoid the face to face communications. Hence the first security advantage is this. The face of an individual is a vulnerable biological data that is hidden along with their other identifying information such as location, contact number of pictures using virtualization. All kinds of personally identifiable information is kept secure due to this.
The second security advantage of virtualization is that it offers centralization of all managerial operations and functions. All the operations which a business performs can run over a controlled architecture as a result. All IT-related activities are kept protected. The authorized users can only get access to such a system. These two security befits make virtualization a highly popular architectural structure.
References
Andrew, M. (2018). No security through obscurity: changing circumvention law to protect our democracy against cyberattacks. Brooklyn Law Review, 83(4).
Gavrilovska, L., Rakovic, V., & Ichkov, A. (2018). Virtualization approach for machine-type communications in multi-rat environment. Wireless Personal Communications : An International Journal, 100(1), 67–79. https://doi.org/10.1007/s11277-018-5611-y
Gao, F.-J., Wang, Y., Wang, L.-Z., Yang, Z., & Li, X.-D. (2020). Automatic buffer overflow warning validation. Journal of Computer Science and Technology, 35(6), 1406–1427. https://doi.org/10.1007/s11390-020-0525-z
Jackson, S., Vanteeva, N., & Fearon, C. (2019). An investigation of the impact of data breach severity on the readability of mandatory data breach notification letters: evidence from u.s. firms. Journal of the Association for Information Science and Technology, 70(11), 1277–1289. https://doi.org/10.1002/asi.24188
Kour, P. (2020). A study on cross-site request forgery attack and its prevention measures. International Journal of Advanced Networking and Applications, 12(02), 4561–4566. https://doi.org/10.35444/IJANA.2020.12204
Rodri?guez Germa?n E, Torres, J. G., Flores, P., & Benavides, D. E. (2020). Cross-site scripting (xss) attacks and mitigation: a survey. Computer Networks, 166. https://doi.org/10.1016/j.comnet.2019.106960
Tamrin, S. I., Norman, A. A., & Hamid, S. (2017). Information systems security practices in social software applications. Aslib Journal of Information Management, 69(2), 131–157. https://doi.org/10.1108/AJIM-08-2016-0124
Wang, X., Huang, F., & Chen, H. (2019). Dtrace: fine-grained and efficient data integrity checking with hardware instruction tracing. Cybersecurity, 2(1), 1–15. https://doi.org/10.1186/s42400-018-0018-3
ITC573 Data Knowledge and Engineering Assignment Sample
Assignment Brief
Value: 20%
Group Assessment: No
Submission method options: Alternative submission method
TASK
For this task, you are required to download the Airlines dataset which is available in the Massive Online Analysis (MOA) framework. You will need to access the airlines. arff file. Moreover, you are required to download the MOA (https://sourceforge.net/projects/moa- data stream/) software for this task.
Answer the following short answer questions based on the given dataset.
Knowledge obtained through all topics from Topic 1 to Topic 9, particularly Topic 8 and Topic 9 can be useful for assignment help to answering the questions.
Q1. Data Pre-processing [10 marks]
1. Assume that the Airlines dataset has some missing values. Out of the missing value imputation techniques (i.e. Mean Imputation, EMI and DMI) discussed in this subject, which technique do you prefer to use for the Airlines dataset? Why? [5 marks]
2. Again assume that the Airlines dataset has some missing values and some corrupt values. Do you prefer to handle the missing values before handling the corrupt values? Why? [5 marks]
Q2. Incremental Learning [10 marks]
You are required to perform a data mining task to evaluate different incremental learning algorithms. Load the airlines. arff data set into MOA and compare the performance on this data set for the following algorithms:
• HoeffdingTree
• Adaptive Random Forest
• Hoeffding Adaptive Tree
• Leveraging Bagging
Write a response that shows the performance of the different algorithms and comment on their performance using the classification accuracy and other performance metrics used in MOA. In your report consider:
• Is there a difference in performance between the algorithms?
• Which algorithm performs the best?
Your response should include the necessary screenshots, tables, graphs, etc. to make your report understandable to the reader. The recommended word length for the report is 700 to 1000 words.
SUBJECT LEARNING OUTCOMES
This assessment task will assess the following learning outcome/s:
1. be able to compare and critique various data pre-processing techniques.
2. be able to evaluate the usefulness of data cleansing and pre-processing in discovering useful knowledge necessary for critical business decision.
3. be able to evaluate and compare time series data mining approaches for business decision making.
You MUST prepare and present all text answers to the above tasks in a single document file. All images must also be embedded into the document. All files such as your response to the assignment tasks and Turnitin reports will all be in a single directory, identified by your name.
REQUIREMENTS
Your response to each of the questions such as Q1. a and Q1. b should be no longer than 500 words (excluding figures, tables and graphs). Administrative sections of your assessment such as headings, table of contents, reference list and other diagrams and figures are not included in the word count. In text citations are included as part of your word count. Please note that the length of an answer is not very important. The quality and completeness of an answer is important.
For this assessment you’re required to use APA7 referencing to acknowledge the sources that you have used in preparing your assessment. Please visit Referencing at CSU for guidance. In addition, a very useful tool for you to use that demonstrates how to correctly use in-text referencing and the correct way to cite the reference in your reference list is the Academic Referencing Tool (ART).
This assignment must be uploaded to Turnitin. Students will need to download the Turnitin report and submit it via Turnitin along with the assignment. More information on using Turnitin at CSU can be found at https://www.csu.edu.au/current-students/learning-resources/information- planning/assignments/plagiarism-checking
Solution
Introduction
The paper aims to evaluate the data mining models in incremental learning using Massive Online Analysis or MOA tool. In this context, the Airline data has been selected on which the data mining algorithms will be applied after preprocessing it.
Data Pre-processing
Primarily, the discussion about the data pre-processing will be done in this section. One of the most important data preprocessing is the missing data handling without which the data mining algorithm will not respond properly (Tahir & Loo, 2020).
Computation on Missing Values
The data has been collected in ARFF (Attribute Relational File Format) and loaded in MOA. It has not been seen that there are any missing values. However, if the data will contain missing values, there are three ways to handle this and those are as follows:
1. Replace missing values by mean
2. Replace missing values with EMI
3. Replace missing values with DMI
When the EMI (Expected Maximization Imputation) is applied to the data, the missing data will be replaced by the most occurred values in the feature. If this will be done, the central tendency of the data may be changed and for the continuous variable, it will not work properly as the mode is not a valid computation for continuous variables. On the other hand, Decision Tree-Based EMI method is used to replace the missing values by creating the decision tree model and signifying the value at each node (Beaulac & Rosenthal, 2018). So, the DMI method is time-consuming for large datasets. When the missing data is replaced by the mean value of the features, the central tendency is maintained. However, replacing missing values for categorical or nominal features, mean will not work. As airline data contain both the continuous and nominal features, both mean values (for continuous) and the EMI method (for nominal) will have to be used (Islam, 2011).
Corrupt values are not similar to missing values. In most cases, corrupt values come in the form of special characters such as “?” etc. Those characters are not traced when missing values is found as those are not the missing values and rather treated as the valid member of those features with wrong values (Zhu & Wu, 2020). If those values are not replaced, those values will produce the wrong outcome of the data analysis and finally in the application of data mining algorithms. So, those corrupt values in the data need to be removed to make the dataset cleaned and without any kind of the wrong valuation. So, before missing value treatment, the corrupt values need to be converted to missing values or NaN values so that those will be traced at the time of finding the missing values (Ghalib Ahmed Tahir, 2020). So, finally, it will be easier to trace all the missing values and can be replaced by a suitable method.
So, in view of the thought, the corrupt values need to be converted to missing values first and then the imputation of missing values should be done.
Incremental Learning
In this section, the incremental learning methods will be applied to the airline data and the performances will be observed.
Hoeffding Tree
Primarily, the Hoeffding Tree has been applied to the airline data and classified to determine the flight delay (Guo, Wang, Fan, & Li, 2019). The screenshot of the application of this algorithm in MOA is shown below:
Fig-1: Application of Hoeffding Tree
After applying the algorithm, the following outcome has been obtained graphically as follows:
Fig-2: Visualization of Performance for Hoeffding Tree
After applying the Hoeffding Tree, the classification matrics have been stored and enlisted in the following table:
Table-1: Classification Metrics for Hoeffding Tree
Adaptive Random Forest
The Adaptive Random Forest has been applied to the airline data and classified to determine the flight delay. The screenshot of the application of this algorithm in MOA is shown below:
Fig-3: Application of Adaptive Random Forest
After applying the algorithm, the following outcome has been obtained graphically as follows:
Fig-4: Visualization of Performance for Adaptive Random Forest
After applying the Hoeffding Tree, the classification matrics have been stored and enlisted in the following table:
Table-2: Classification Metrics for Adaptive Random Forest
Hoeffding Adaptive Tree
The Hoeffding Adaptive Tree has been applied to the airline data and classified to determine the flight delay (Tahir & Loo, 2020). The screenshot of the application of this algorithm in MOA is shown below:
Fig-5: Application of Hoeffding Adaptive Tree
After applying the algorithm, the following outcome has been obtained graphically as follows:
Fig-6: Visualization of Performance for Hoeffding Tree
After applying the Hoeffding Tree, the classification matrics have been stored and enlisted in the following table:
Table-3: Classification Metrics for Hoeffding Adaptive Tree
Leveraging Bagging
The Leveraging Bagging has been applied to the airline data and classified to determine the flight delay. The screenshot of the application of this algorithm in MOA is shown below:
Fig-7: Application of Leveraging Bagging
After applying the algorithm, the following outcome has been obtained graphically as follows:
Fig-8: Visualization of Performance for Leveraging Bagging
After applying the Hoeffding Tree, the classification matrics have been stored and enlisted in the following table:
Table-4: Classification Metrics for Leveraging Bagging
Finding and Conclusion
The algorithms have been applied to the airline data for the classification of flight delays. While applying the classifiers, the performance matrices have been recorded so that those can be compared to find the best one. From the overall experiment, the following finding has been obtained:
1. The performance of the chosen classifier differs from each other. The accuracy, precision, recall and f1-scores (Overall values and also by class) are different from each of the classifiers that prove the fact that the performances of classification are different from each other.
2. From the comparison of accuracy, it has been seen that the highest accuracy has been obtained from Adaptive Random Forest by 64.3% with the kappa value of 27.33% and precision by 64.04%. The execution time for Adaptive Random Forest (34 seconds) is also comparatively lower with higher accuracy.
References
Beaulac, C., & Rosenthal, J. S. (2018). BEST : A decision tree algorithm that handles missing values. University of Toronto, 1-22.
Ghalib Ahmed Tahir, C. K. (2020). Mitigating Catastrophic Forgetting In Adaptive Class Incremental Extreme Learning Machine Through Neuron Clustering. Systems Man and Cybernetics (SMC) 2020 IEEE International Conference, 3903-3910.
Guo, H., Wang, S., Fan, J., & Li, S. (2019). Learning Automata Based Incremental Learning Method for Deep Neural Networks. IEEE Access, 1-6.
Islam, M. G. (2011). A Decision Tree-based Missing Value Imputation Technique for Data Pre-processing. Proceedings of the 9-th Australasian Data Mining Confere, 41-50.
Tahir, G. A., & Loo, C. K. (2020). An Open-Ended Continual Learning for Food Recognition Using Class Incremental Extreme Learning Machines. IEEE Access, 82328 - 82346.
Zhu, H., & Wu, Y. (2020). Inverse-Free Incremental Learning Algorithms With Reduced Complexity for Regularized Extreme Learning Machine. Access IEEE, 177318-177328.
Research & Data Modelling Assignment Sample
Assessment Brief
Value: 15%
Due Date: 04-Apr-2021
Return Date: 27-Apr-2021
Group Assessment: No
Submission method options: Alternative submission method
TASK
Part A: Database Research Discussion Forum (7 Marks)
You are to conduct research about a current or a future database technology and
discuss the findings of your research in the Interact 2 Discussion forum. You should submit a minimum of two posts. You are also to comment in the Interact 2 Discussion forum on at least two posts made by other students. Copy the time, date and content of your posts and include them in a MS Word document as part of this assessment. Two discussion posts of a current or a future database technology and two comments on other students posts (4 marks) Quality of engagement: (3 marks)
Part B: Data Modelling (8 Marks)
XYZ is a company which organises conferences mainly in the computing area. Due to the success of their business, they have decided to implement a relational database for better management of the conferences. For each conference, they need to keep records of the conference code, conference dates, conference name, days duration, and venue. XYZ are required to keep track of all the past attendees identified by participant id, as they are going to send advertising materials on topics which may interest the participants to attend a conference in the future. Thus, details such as name, phone number, and address of the participants are required. XYZ needs to track details of who attended a conference in the past and the number of days attended. XYZ also keep track of all the speakers who have spoken, or are potential speakers for their conferences. Information including speaker id, name, phone number, topic id and topic name are required. For each conference, XYZ gives a rating to a speaker. XYZ also have a list of casual catering staff who can be booked to provide catering services. XYZ needs to store their id no, name, phone, position (eg. chef) and the hours worked at each conference. And lastly, XYZ has a list of the venues and other information related to a venue such as venue id, seating capacity, seating style, fax, and phone number.
Your task for assignment help.
Create an ERD for the above scenario that describe the current business rules:
Use Crow's Foot notations and make sure to include all of the following:
• All entities Attributes for each entity
• Primary key and any foreign key attributes for each entity
• The relationships between entities
• The cardinality and optionality of each relationship
For guidance on how to draw an ERD based on business rules, watch this video: https://www.youtube.com/watch?v=YvJ4t9_2SWk
To draw the diagrams, you should use a drawing tool like Draw.io, Lucidchart,
LibreOffice Draw etc. Hand-drawn diagrams are NOT acceptable.
Include your student ID and full name under the ERD then copy the whole ERD as
an image to your Word document.
Solution
PART- A
Future Database Technology
Post-1: Today, the significance of database system has increased in the implementation of diverse database applications. Database system comprises of many components which enables the development of database application according to requirement. For designing of database, numerous database models (ER model, Relational model, Object oriented mode, network model etc.) are used in respect of requirement types. In previous few years, it has observed that new database model evolved named multidimensional model which allow data representation in cubic form. Multidimensional model used in defining of data-warehousing. The integration of database technology with other information technologies results new kind of database system such as mobile database system, spatial, multimedia, Decision Support System and Distributed database system. Several information technologies used in implementation of advanced database system such as business intelligence, data warehouses, Extract Transformation & Load (ETL), OLAP, Data Mining, Grid Computing and Web Technology.
Post-2: Due to rapid evolution of computing peripherals and paradigms, database technology also require to align with this evolution. According to scalable and global access of database application over the internet require modern database approach and their implementation. For example develop distributed database application for cloud environment. Future database technology must be able to storing and analyzing diverse and high volume of heterogeneous data. It also requires revising current database approaches according to network based applications. Several data service providers such as Google, Facebook and Amazon deal with peta-bytes of data every day. This all happens by use of modern database technology. With this, implementation technology of database system is also changing over the period of time. The database implementation platforms and languages are evolved from QUEL, SQL, SQL92, OQL and XML. Apart from this, database technology research also focus on emerging field such as Big Data, Grid Computing, Web Technology and Business Intelligence.
PART- B
Entity Relationship Diagram
Based on the information provided in the case study several entities, its attributes with key constraints and relationships are identified.
All Entities
• Conference
• Attendee
• Speaker
• Catering Staff
• Venue
Attributes for each entity: Entity Name (Attribute Name [Type or Key ])
• Conference (Conference_Code [Primary Key attribute], Conference_Name, Conference_Date, Days, Duration, Venue [Foreign key referenced Venue_Id (Venue)])
• Attendee (Participant_Id [Primary Key attribute], Participant_Name, Phone_No [Multivalued Attribute] ,Address [Composite Attribute], Conference_Code [Foreign Key references Conference_Code(Conference)])
• Speaker (Speaker_Id (Primary Key attribute), Speaker_Name, Phone_No [Multivalued Attribute], topic_id,topic_name)
• Catering_Staff (Staff_Id ( Primary Key attribute), Staff_Name, Phone_No [Multivalued Attribute] , Position)
• Venue (Venue_Id (Primary Key attribute), Seating_Capacity, Seating_Style, Fax, Phone_No [Multivalued Attribute])
Relationships (Participating Entities)
• “Attended” Relationship (Attendee and Conference for each participant attended one or more conference)
• “Organized at” Relationship (Conference and Venue for each conference organized at a venue)
• “Get Rating” Relationship (Speaker and Conference where each speaker have assigned a rating for each conference)
• “Work_for” Relationship (Catering_Staff and Conference where catering staff work for each conference in number_of_hours )
Cardinality and Optionality of Each Relationship
• For “Attended” relationship, Many to Many (M:N) cardinality and optional for attending conference but mandatory for conference that means each conference has at-least one participant.
• For “Organized at” relationship, Many to One (M:1) cardinality and mandatory for conference that organized at least one venue but venue is optional it means no need of every venue used in conference.
• For “Get Rating” relationship, one to one (1:1) cardinality and mandatory for both speaker as well as conference.
• For Work_for” relationship, Many to Many (M:N) cardinality and optional both catering_staff and conference.
Entity Relationship Diagram (ER Diagram)
ICTICT426 Emerging Technologies and Practices Assignment Sample
Overview of assessment
This assessment is based on a scenario and requires you to write a response which is made up of 4 tasks. This assessment requires you to complete written tasks. You are required to complete all tasks in the order provided. You have been given a scenario based on a fictional farming business named “ASR Farms”.
You will play the role of ‘Business Analyst” for IT Works, an IT consultancy company. You are required to:
• access the sources of emerging technologies
• access practices of emerging technologies in the IT industry
• Identify and document emerging technologies to meet the requirements of ASR Farms.
Your lecturer will play the role of the Manager of ASR Farms and IT Works Project Manager.
Task/s to be assessed
1. Sources of Information
2. Overview of Emerging Technologies
3. Identification of Emerging Technologies
4. Identifying Emerging Technologies relevant to the organisation (video presentation)
4IEET – Assessment – Part 1
Identification of Emerging Technologies and Practices in IT
SCENARIO: Read the scenario carefully for assignment help then complete the assessment tasks.
Business Background
For 30 years, Mr. and Mrs. Roberts (Andrew and Suzie) have owned a 3000-acre farm far north of Adelaide. Its Registered Business name is ASR Farms. They have poultry, 250 cows as well as multiple crops on 2000 acres. They produce milk and have a team to sell their milk on open market.
There is a sales team who use computers to maintain their records electronically. Mrs Roberts uses a computer to keep track of the farm’s finances however her bookkeeping/accounting skills are self-taught, and she finds that dealing with finances is a stressful and time-consuming practice. All devices are stand alone as ASR Farms has no computer network, however they do have reasonably reliable internet access.
Andrew obtained the farm in an inheritance and is still using traditional methods of agriculture – for example most of the crop planting, picking, packing, weeding etc is done by hand. Most of their farm equipment is not modern and is at the point where it is due to be updated soon. They use chemical fertilisers and a variety of machines for various purposes, but due to their old equipment they need to hire a great amount of labour. Due to increasing labour costs, their profit margins and crop yields are reducing day by day.
A variety of different crops, primarily vegetables have grown in their greenhouses. In the last 3 years they have increasingly specialised in gourmet tomatoes - also known as heirloom or cherry tomatoes. These tomatoes can be very profitable, however maintaining the ideal environment for growth is proving to be challenging. They haven’t been able to consistently produce enough crops to ensure a profit. The owners believe that if they could perfect their greenhouse practices, this would go a long way towards seeing the farm return to profitability, but they know this won’t happen using their traditional practices.
Greenhouse environment testing is labour intensive. They manually test soil for salinity, water levels and test the temperature and humidity every 4 hours. Sometimes if there is an emergency elsewhere on the farm the greenhouse environment testing does not occur, which can result in conditions that are not ideal for crops and reduces yields.
Machinery in use is dated so repair and maintenance costs are high. They don’t really have a schedule for machinery maintenance – servicing is done on an as needs basis when malfunctions occur. The manager has a written journal where he tries to keep track of machine servicing and maintenance, but it is not 100% reliable and servicing is not always done as often as it should be.
Another issue concerning the owners is that they have had several break-ins to the 8 greenhouses on the farm. This has resulted in loss of production due to theft and vandalism. They currently have no security monitoring in place for their greenhouses.
Use of technology is minimal on the farm, and staff and management freely admit they have minimal knowledge or experience when it comes to information technology.
One of the few recent investments in technology at ASR Farms has been to install a significant number of solar panels on various farm buildings. They have also invested in battery storage solutions to complement the solar panels. Andrew and Suzie’s aim was to make the farm self-sufficient as regards electricity by sourcing solar power. Currently they appear to be achieving this with their solar energy system just supplying enough energy for their daily needs.
ASR Farms comprises of
• Owner (Director) Suzie Roberts
• Owner (Manager) Andrew Roberts
• Cowherd X 8
• Grape growers X 40
• Sales X 5
• Delivery Driver X 5
Their family friend Peter Hall lives in the USA. He works as a Manager in a Large-scale commercial Farm in Texas. He and his wife recently visited Andrew and Suzie Roberts in Adelaide.
Peter told Andrew that in the USA farmers and agricultural companies are turning to the Internet of Things (IoT), Big Data and Robotic Process Automation and other emerging technologies for analytics and greater production capabilities.
He suggested Andrew take advice from an IT company to implement emerging technologies in his farm as that may help him to resolve his problems.
Andrew Roberts contacted ITWorks and discussed their interest in using emerging technologies and latest IT practices on their farm to increase production and increase their profit margins. You work at ITWorks as a Business Analyst. You will be working with your project manager to investigate potential new emerging technologies that may be used in ASR Farms.
Task 1: Access Sources of Information on Emerging Technologies
Question 1:
Visit the following open source community website: https://github.com/open-source
Access two (2) current projects that are currently listed by Github on their “Trending” page.
For each project that you access, you must provide the following information:
• The name of the project.
• A screenshot of the project page that shows the URL. If the full URL is not visible in the screenshot due to its length, please copy and paste the full URL below the screenshot.
• A brief description of the project (minimum 30 words) that explains its purpose – i.e. what the subject of the project can be used for.
• The number of Contributors that are listed as having been involved in the project. Include a screenshot showing the number of contributors. The URL of the page must be included in your screenshot.
Question 2:
Access the following Crowd funding site: https://www.kickstarter.com/
Use the Search tool on the Kickstarter site to enter the search term “Greenhouse automation”
From the “Greenhouse automation” search results, access one project and provide the following information:
• The name of the project.
• A screenshot of the project page that shows the URL. If the full URL is not visible in the screenshot due to its length, please copy and paste the full URL below the Screenshot.
• A brief description of the project (minimum 30 words) that explains its purpose – i.e. What the subject of the project can be used for.
• The monetary target/goal of the project and the current amount pledged. Provide a
Screenshot of where you located this information.
Task 2: Identify and Evaluate Emerging Technologies
Question 1:
List 3 characteristics that would define an “emerging technology”.
i. Click or tap here to enter text.
ii. Click or tap here to enter text.
iii. Click or tap here to enter text.
Question 2:
Provide an evaluation of the following three emerging technologies (Minimum of 100 words for each):
1. Internet of Things
2. Big Data
3. Robotic Process Automation
Each evaluation must include:
• The purpose of the technology
• Two attributes of the technology. (An attribute is a characteristic or inherent part of Something)
• Two features of the technology. (A feature is a prominent or distinctive part, quality, or Characteristic)
• Advantages (minimum of two) of using this technology for ASR Farms
• Disadvantages (minimum of two) of using this technology for ASR Farms
• Evaluate how the technology could be used at ASR Farms – i.e. which processes it could be
used to enhance or replace. Refer to at least two processes.
Task 3: Identification of Emerging Technologies Features and Functions
In this task you need to review and research the technologies that the owners of the ASR farms mentioned in their initial contact with IT Works.
Question 1:
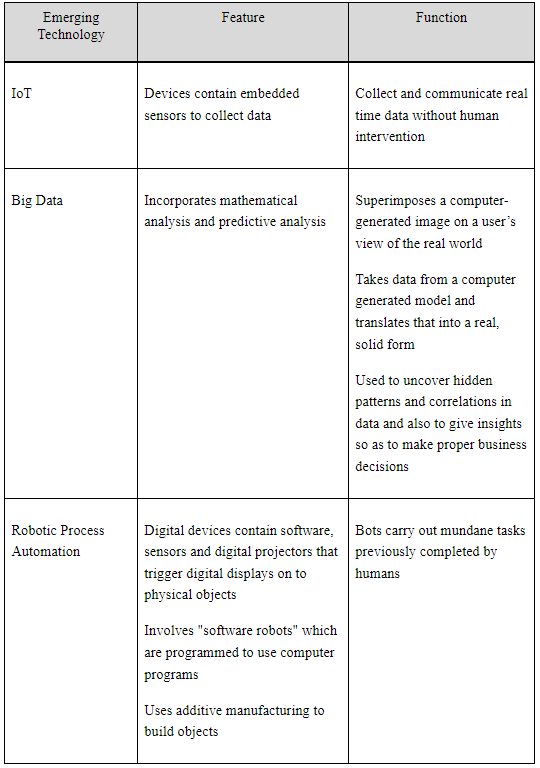
One of your co-workers has done some research on the functions and features of emerging technologies, however their notes were partially deleted. They managed to recover part of their list of functions and features, but the list does not show which function and feature belongs to which technology.
Your task is to look at the recovered list below and enter each item into the correct position in the table that follows. In the table you are only focusing on functions and features of Internet of Things (IoT), Big data, and Robotic Process Automation (RPA). The list your co- worker created also includes functions and features related to other emerging technologies – ignore these unrelated items and only select those that relate to IoT, Big Data, and RPA.
Task 4: Reporting on Emerging Technologies Relevant to the organisation
Part 1:
Your supervisor has asked you to prepare a video summary of your findings which will be viewed by the owners of ASR farms.
Content requirements of the video are:
1. Introduce yourself by name and title (Business Analyst for IT Works) at the start of the video.
2. Describe 1 example for each technology (Internet of Things, Big Data, Robotic Process Automation) of where it could be used specifically in relation to current practices used at ASR Farms. Each technology should be related to a unique practice – i.e. you will mention 3 technologies and 3 affected practices.
3. For each technology (Internet of Things, Big Data, Robotic Process Automation) describe one advantage and one possible disadvantage that may arise if it is implemented at ASR Farms.
4. In your own words, request that the owners provide you with written feedback on the following:
a. Their thoughts on your examples of how the emerging technologies could impact practices on ASR Farms.
b. ASR Farms short-term and long-term requirements/goals.
c. What they feel is the most critical need of emerging technology in ASR farms – i.e., what specific application or individual piece of technology they would like to have in place.
Solution
Task 1:
Question 1:
According to trending page in github two projects are “ErickWendel/semana-javascript-expert06” that indicates “Spotify” project and “psf/black” indicates “The uncompromising Python code formatter”.
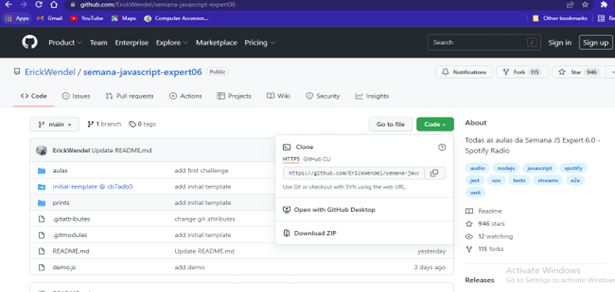
(Link- https://github.com/ErickWendel/semana-javascript-expert06.git)
Through Javascript and nodejs, a real time audio processing has been created where the stream deck is included within Spotify along with different kinds of features. In this project the full concept of Nodejs has been used for making static websites.
Contributors of this javascript project
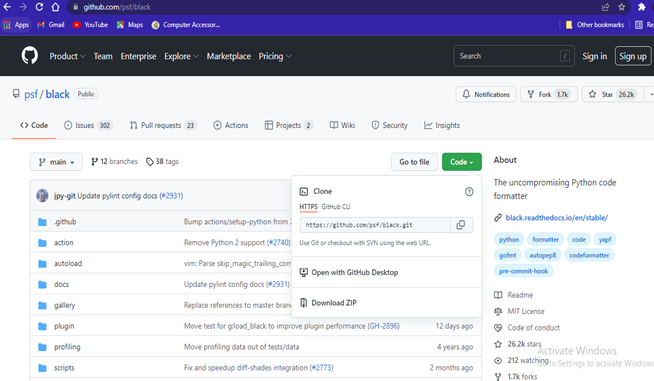
(Link- https://github.com/psf/black.git)
This project is based on “The uncompromising code formatter” and by using Black it can be controlled over minutiae of hand-formatting. Besides, Black is able to manage determinism, speed, and freedom in case of pycodestyle nagging about the exact formatting. Both mental energy and time will be saved and that makes fast code review with producing the smallest diffs possible.
Contributors of python code project
Question 2:
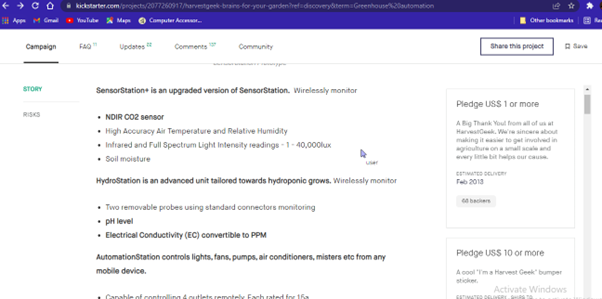
The chosen project in Kickster search tools is “HarvestGeek -- Brains for your Garden”.

Link- https://www.kickstarter.com/projects/2077260917/harvestgeek-brains-for-your-garden
The movement of local food has been effectively picking up with the special momentum. In this regard, over the country small scale agriculture is springing up in rooftops and backyards, altics, and basements, along with abandoned warehouses and lots in the vacant.
Task 2:
Three characteristics of “Emerging technologies”
? Radical novelty
? Relatively fast growth
? Coherence
Question 2:
IoT (Internet of Things):
In the current world, IoT technologies are growing rapidly along with its future trends in a significant manner. Different key technologies of IoT are like AI, 5G, blockchain, and cloud computing. All these are really meaningful to manage advancement of global connectivity with various features of this emerging technology.
Two major attributes of IoT are connectivity and intelligence.
Two features of IoT are lack of disposability or accountability, and ubiquity.
Two major advantages of Iot are cost reduction, productivity and efficiency and these are really useful for managing their farms (Spanias, 2017).
Two major disadvantages of IoT are viruses, hacking, cheating, and trolls, stalkers, bullying, and crime and these can be harmful for ARS farms.
ARS farms can manage their business production in managing electricity and solar energy systems through using IoT. These are increasing production, and increasing profit margin.
Big Data:
In order to increase the products’ market reaching speed and decrease the time and several resources for gaining the adoption of the market, target audiences and satisfying the customers.
Furthermore, the main attributes of this big data technology is volume and variety. In order to identify features of BigData, the volume of stored data is increasing day by day along with variety of data in a significant way. This is a big factor corresponding to big data to manage data varities (Kim et al., 2021).
In business operations, big data is too effective for reducing complexity by creating different types of visualisations.
In an ASR firm, big data has a great advantage in order to optimise energy production and energy distribution. Besides, unpredictable resources are notified by big data.
Moreover, the principle of privacy is violated by big data whereas for the manipulation of customers’ records, big data is utilised. Due to higher complexity, sometimes a false discovery rate is created and these are considered as disadvantages of BigData.
For business analytics, and managing various data management of ARS farms, big data can be implemented significantly.
Robotic Process Automation:
RPA (“Robotic process automation”) is a technology to manage, deploy, easily build, and control software robots to emulate human actions along with digital systems (Nguyen et al., 2021).
Two attributes of RPA are simple bot creation interface, and security.
Two features of RPA are less automation script and debugging.
Reduction of errors and increasing agility are major advantages of RPA within ARS farms (Do?uç, 2021).
Error magnification and maintenance are two disadvantages of RPA and that indicates electricity production like ARS farms.
In order to evaluate a large number of production capabilities, and smart work with sensors and robots, RPA has been used in the case of ARS farms.
Task 3:
Question 1:
Task 4:
1. Examples of different emerging technologies that suit for ARS farms:
2. Advantages and disadvantages of emerging technologies in managing ARS farms:
3.Feedback of owner in the respect of suggestions of emerging technologies
a.
As per your suggestion, all the sensors and smart technologies regarding IoT, RPA, and big Data can be effective for ARS farms to manage energy production, energy transmission as well as distribution. We will try to implement all these things to provide a better customer’ experience and achieve business development regarding electricity production.
b.
Short term goal is to provide better electricity to customers in their specific areas and long term goal is to manage a better power grid to deliver huge amounts of electricity by using IoT, BigData and RPA as per the requirements of customers.
c.
In order to achieve emerging technologies in ARS farms, specific applications of IoT will be effective for the development of smart energy production to produce electricity.
Reference list:
Do?uç, Ö. (2021). RPA in Energy and Utilities.In Strategic Approaches to Energy Management (pp. 217-230).Springer, Cham.https://link.springer.com/chapter/10.1007/978-3-030-76783-9_16
Kim, Y. S., Joo, H. Y., Kim, J. W., Jeong, S. Y., & Moon, J. H. (2021). Use of a big data analysis in regression of solar power generation on meteorological variables for a Korean solar power plant.Applied Sciences, 11(4), 1776.https://www.mdpi.com/2076-3417/11/4/1776/pdf
Nguyen, T. P., Nguyen, H., Phan, V. H., & Ngo, H. Q. T. (2021).Modelling and practical implementation of motion controllers for stable movement in a robotic solar panel dust-removal system.Energy Sources, Part A: Recovery, Utilisation, and Environmental Effects, 1-23. https://www.tandfonline.com/doi/abs/10.1080/15567036.2021.1934194
Spanias, A. S. (2017, August). Solar energy management as an Internet of Things (IoT) application.In 2017 8th International Conference on Information, Intelligence, Systems & Applications (IISA) (pp. 1-4).IEEE.https://par.nsf.gov/servlets/purl/10076703
MN623 Cyber Security and Analytics Assignment Sample
Assignment Brief
Assessment Title- Implementation and evaluation of penetration testing tools
Purpose of the assessment (with ULO Mapping)
This assignment assesses the following Unit Learning Outcomes; students should be able to demonstrate their achievements in them.
• Analyse cyber security vulnerabilities using ethical hacking methodologies.
Weight - 5%
Total Marks - 50 Marks
Word limit - 750 to 1000 words
Due Date Assignment 1- Week 3, 11:59 pm, 10/4/2022
Submission Guidelines
• Submit Assignment 1 in a word document in week3.
• All work must be submitted on Moodle by the due date
• The assignment must be in MS Word format, 1.5 spacing, 11-pt Calibri (Body) font and 2 cm margins on all four sides of your page with appropriate section headings.
• Reference sources must be cited in the text of the report and listed appropriately at the end in a reference list using IEEE Transactions on networking referencing style.
• Students must ensure before submission of final version of the assignment that the similarity percentage as computed by Turnitin must be less than 10% Assignments.
Purpose of Assignment
Assignment 1 is based on analysing cyber security vulnerabilities using ethical hacking methodologies and evaluating security testing tools. The students will explore skills in Ethical Hacking/Penetration testing by describing how weakness in the system can be exploited to hack a target system using security testing tools.
Assignment Structure and Submission Guidelines for Assignment Help
Assignment 1 is a formative assessment, and it focuses on the importance of penetration testing, industry leading tools used for penetration testing and a review of security testing tools. Students will be required to choose two security testing tools for further evaluation.
Assignment Tasks
1) Explain the different reasons and benefits of conducting penetration testing. (5 Marks)
2) What are some regulatory requirements for penetration testing? (5 Marks)
3) Present the industry leading tools used for penetration testing. (5 Marks)
4) Review three security testing tools. (10 Marks)
5) Choose two security testing tool and evaluate them. (10 Marks)
6) Describe how the two security testing tools can be used to exploit cyber security vulnerabilities and hack the system. (10 Marks)
7) References (5 Marks)
Solution
Implementation and evaluation of penetration testing tools
Introduction
Penetration testing even termed as pen testing or ethical hacking is a launch of intentional cyber-attacks that look towards vulnerabilities that is exploitable in the computer system, websites and other applications. The aim of the assignment is to focus on the utility of penetration testing, the leading tools in the industry that is used for it and the evaluation of such tools.
Different reasons and benefits of penetration testing
• Conformity to Industry Codes and Procedures - One of the most significant advantages of penetration testing is that it meets the legal and management requirements stated in business laws and standards such as FISMA, ISO 2700, PCI, and HIPAA. Pen-testing can establish how a hacker obtained sensitive information and intellectual goods [5]. Furthermore, if a corporation employs pen-testing for constant inspection and validation and ensure the privacy of credit card information.
• A Penetration reveals critical flaws - A Penetration test should be performed once a year to look for key vulnerabilities in IT assets. Various methods and technologies can test IT assets to detect which security flaws are in the system [3].
• Provide a prospect to fix vulnerabilities - Once a company has identified the vulnerabilities, security specialists can start repairing the significant problems in the networks and apps [3].
Some of the regulations that apply to penetration testing
• GDPR - The one rule that affects practically every organization. The GDPR addresses many areas of data security, but one of its many mandates is that businesses that manage private information strengthen cybersecurity and accountability. GDPR Article 32, in particular, requires firms to establish a "method for regularly testing, measuring and assessing the efficacy of technical and institutional safeguards for preserving data handling protection.
• ISO 27001- A member of the ISO/IEC set of guidelines is a global data security standard that defines a management structure for Security Management System (ISMS). Organizations must establish a suite of security protocols to prevent and resolve potential risks throughout their networking, and ensure they satisfy evolving safety needs account to get licensed.
• PCI DSS – This is a series of minimal rules created to aid businesses in safeguarding client card information. All businesses that accept or handle electronic card payments must conduct an annual PCI safety check to achieve compliance.
Industry-leading tools used for penetration testing
? Netsparker – This is a major web application for automated pen-testing. The program can catch everything, including cross-site programming to SQL injection. Programmers can use this tool on web pages, online services, and web applications.
? Wireshark - Wireshark is a network scanner that has 500 writers. Programmers can use this application to record and analyze data packets swiftly. The software is open and accessible, and it is useful for a range of computer systems, including Microsoft, Solaris, FreeBSD, and Unix [4].
? Metasploit - This assists pro players in verifying and monitoring security audits, bringing awareness, and arming and empowering attackers to keep up with the competition. It is beneficial for evaluating the safety and identifying faults, as well as for establishing a defense. The technology allows social engineers to recreate web pages [4].
Evaluation of the three security testing tools
• John The Ripper Password Cracker - Passwords are amongst the most common vulnerabilities. Username and passwords can be used by criminals to obtain identities and gain access to sensitive systems. John the Ripper should be a must tool for password protection and offers a variety of systems for this purpose [6].
• Aircrack – The tool is intended to break weaknesses in wireless connections by collecting data packets and transferring them via text files for study. This program is compatible with various operating systems, including windows, and supports WEP dos attacks. It outperforms most other penetrating tools in tracking performance and supports multiple devices and adapters.
• W3af - W3af web application exploitation and auditing modules are designed to detect security flaws in all web apps. There are three types of WordPress plugins: attacker, auditing, and detection [6]. The program then sends these to the audit tool, which checks for security concerns.
Selection of two security tools and assessment
W3af is a Web application security scanner and exploiting software. W3af is separated into two sections: the core and plugins. It delivers security vulnerability information for use in vulnerability scanning operations. The scanner has both a visual and a command-line interface. Fast HTTP queries, incorporation of web and proxies’ services into the script, injecting payloads into different kinds of HTTP requests, and so on are among its characteristics. It runs on Linux, Apple Mac OS X, and Microsoft Windows and has a command-line interface [2].
Aircrack-ng is a comprehensive set of criteria for assessing WiFi network cybersecurity. It includes a wide range of aspects of WiFi security: Attacking, Testing, Monitoring, and Cracking. All tools are command-line interface only, allowing for extensive programming. This functionality has been used by a large number of graphical user interfaces. It runs mostly on Linux and Windows, macOS, FreeBSD, OpenBSD, and Solaris. In hacking, developers can de-authenticate, create phony entry points, and launch replay assaults [1] [7]. To use AirCrack-ng correctly, programmers must catch certain packets, which must be acquired via the WiFi network adapter. Depending on whatever PC card developers have to install, guidelines for various cards and software are needed.
Utilization of the two security testing tools and the manner in which they exploit cyber security vulnerabilities
Aircrack is performed to demonstrate the existence of vulnerabilities and the potential damage that could be caused if these flaws were exploited. It also supports recording and injection, which is essential for evaluating network cards and their performance [1]. Furthermore, IT professionals can use it to assess the dependability of WPA-PSK and WEP keys. It also performs additional activities such as detecting fraudulent access points, evaluating controller capacities and WiFi cards, etc. Here's how AirCrack security testing tools could be used to attack cyber security flaws and hack the device.
On the other hand, W3af includes plugins that connect. For instance, in w3af, the identification plugin searches for various URLs to test for flaws and provides them to the auditing plugins, which further search for flaws. Through its Intuitive and Automatic requests generating features, it alleviates some of the hassles associated with manual web applications. It can also be set up to act as a MITM gateway. It also includes features for finding loopholes that it discovers. Here's how W3af security testing tools could be used to attack cyber security flaws and hack the device.
Conclusion
The aim of the assignment was to focus on the utility of penetration testing and the usage of the security tools in the industry. From the complete assignment it can be concluded that pen testing is a security exercise and have significant advantages. Moreover, security tools helps in combating the issues and attack security flaws. The selection of the same depends on the user.
References
[1]. G. Kaur and N. Kaur, "Penetration Testing - Reconnaissance with NMAP Tool," International Journal of Advanced Research in Computer Science, vol. 8, (3), 2017. Available: https://www.proquest.com/scholarly-journals/penetration-testing-reconnaissance-with-nmap-tool/docview/1901458135/se-2?accountid=30552.
[2]. J. D. Kramer and T. J. Wagner U.S.A.F., "DEVELOPMENTAL TEST and REQUIREMENTS: Best Practices of Successful INFORMATION SYSTEMS USING AGILE METHODS," Defense AR Journal, vol. 26, (2), pp. 128-150, 2019. Available: https://www.proquest.com/scholarly-journals/developmental-test-requirements-best-practices/docview/2214889819/se-2?accountid=30552. DOI: http://dx.doi.org/10.22594/dau.19-819.26.02.
[3] J. V. Olson, "Software Validation: Can an FDA-Regulated Company Use Automated Testing Tools?" Journal of Validation Technology, vol. 18, (3), pp. 49-51, 2012. Available: https://www.proquest.com/scholarly-journals/software-validation-can-fda-regulated-company-use/docview/1055111478/se-2?accountid=30552.
[4]. S. Zhou et al, "Autonomous Penetration Testing Based on Improved Deep Q-Network," Applied Sciences, vol. 11, (19), pp. 8823, 2021. Available: https://www.proquest.com/scholarly-journals/autonomous-penetration-testing-based-on-improved/docview/2580965017/se-2. DOI: http://dx.doi.org/10.3390/app11198823.
[5]. T. M. Chen, "Reinforcement Learning for Efficient Network Penetration Testing," Information, vol. 11, (1), pp. 6, 2020. Available: https://www.proquest.com/scholarly-journals/reinforcement-learning-efficient-network/docview/2548413764/se-2. DOI: http://dx.doi.org/10.3390/info11010006.
[6]. X. C. Li, D. Farson and R. Richardson, "Weld penetration control system design and testing," J. Manuf. Syst., vol. 19, (6), pp. 383-392, 2000. Available: https://www.proquest.com/scholarly-journals/weld-penetration-control-system-design-testing/docview/197657176/se-2?accountid=30552.
[7]. Z. Ren et al, "Study on practical voltage secondary loop testing tool," IOP Conference Series.Earth and Environmental Science, vol. 354, (1), 2019. Available: https://www.proquest.com/scholarly-journals/study-on-practical-voltage-secondary-loop-testing/docview/2558041287/se-2. DOI: http://dx.doi.org/10.1088/1755-1315/354/1/012090.
BIS3005 Cloud Computing Assignment Sample
Group/individual: Individual
Word count: 2000
Weighting: 30%
Answer each of the questions below for assignment help -
Describe the difference between a locally hosted school (ie. in an enterprise data centre) and a school service provided using a SaaS provider. What are the critical points, other than cost, that an enterprise would need to consider in choosing to migrate from a locally hosted service to an SaaS service?
Describe the difference between locally hosted university infrastructure (ie. In an enterprise data centre) and a university infrastructure provided using an IaaS provider. What are the critical points, other than cost, that an enterprise would need to consider in choosing to migrate from local hosted infrastructure to an IaaS service provider?
ECA, wants to investigate moving two of its educational arms to a service- based model where many of its services would be supplied to its clients as a service, in addition to its plans to move to an IaaS model. There are several infrastructure models that could possibly be used to achieve this. Some of these models are:
1. Local hosted infrastructure and applications.
2. Local hosted infrastructure with some SaaS applications.
3. Hybrid infrastructure (some locally hosted infrastructure with some IaaS) and applications.
4. Hybrid infrastructure and applications with some SaaS applications.
5. Full IaaS model with some with SaaS apps.
6. Full SaaS model.
You are required to choose an infrastructure model that you think will achieve the ECA Roadmap; Describe the benefits and drawbacks, excluding costs, of your chosen infrastructure model.
Solution
Describe the difference between a locally hosted school (ie. in an enterprise data centre) and a school service provided using a SaaS provider. What are the critical points, other than cost, that an enterprise would need to consider in choosing to migrate from a locally hosted service to an SaaS service?
Software as a Service is an internet based service which is provided and maintained by the service providers rather than in house enterprises. This is an approach to software distribution which is created by the software providers where they create and host a combination of software, database and code to create an application which can be accessed by anyone, anywhere (Palanimalai, & Paramasivam, 2015). This gives the liberty to the firms to work from anywhere around the world where there is an access to the internet. In a school there are several things that needs to be recorded as well as updated. There are several outputs that are required such as results, scores and performance in the class for both the teachers as well as the students with the help of a software. There should also be forums where students as well as the teachers can interact. Moreover, most important thing is the uploading of the class lectures that will be helpful for the students after the class. All of these things are required in a school and this required a software. Now the question arises is that there are a lot of host service providers that provides supports using SaaS which can be an option, and there are locally hosting servers can also be an option. Below are the comparison done between migrations from local server to a SaaS service provider in a school.
Time efficient: In a traditional on premise deployment it takes a lot of time to setup a particular software in a school. It is not limited to that as this requires a number of people who are expert in this field. This will make an addition to a department in a school which is absolutely unnecessary. The software will need a lot of time to build and will take time to implement it at the same time. The resources will be extra that will be required for this venture. These resources can be put to use for the school and student welfare. The extra services that will be required cannot not be shared always and the school have to compromise because of the time that it will take to be developed. In case of SaaS, the software is already installed and configured all the school have to do is to provision the server into the cloud and the system will be up and running and ready to use (Nakkeeran, et.al. 2021).
Higher Scalability: Unlike the local server the SaaS has a higher scalability which means that for an extra service the school needs to by a new SaaS and merger it with the previous one. The new SaaS will be owned by the service provider or the host as they will maintain the whole thing for them. For an instance, during the pandemic all the schools needed to conduct online classes but the schools authority did not have that feature. For the inclusion of this feature the schools authority should only have granted for a new SaaS that will be owned by the host but in case of a local server the whole thing was needed to develop first and then merge with the local server that can be accessed using a different link.
Upgrade: SaaS gets auto updated as the host will maintain the whole system for the school. The effort associated with the upgrading of the system is much less in case of SaaS and also cost efficient at the same time. In a traditional model the school will have to buy the upgrade and then install it into the system where as in SaaS the provider will do everything for the school at a very low amount of time.
Proof-of-Concept: This is a feature in SaaS where the users can see and learn about the updates prior to its launch (Kaltenecker, 2015). The functionality can also be tested to understand its functionality. In case of local server this is not an option as the software can only be tested once it is upgraded into the system.
The above differences will give an idea about the difference between and advantages of a SaaS service provider over the local enterprise system. In an enterprise like school it would be a little much to go for SaaS but a lot of things will be easier for the school. The SaaS service is more upgraded nowadays. Many a firms including schools and colleges are interested in using SaaS as their system software. Due to pandemic every institution has started to understand the usability of Software as a Service. Institutes has also started using IaaS as their new system solution which is a better solution. That is been discussed in the next question. Describe the difference between locally hosted university infrastructure (i.e., in an enterprise data center) and a university infrastructure provided using an IaaS provider. What are the critical points, other than cost, that an enterprise would need to consider in migrating from locally hosted infrastructure to an IaaS service provider?
Computing infrastructure includes hardware such as computers, modems, networking cables/wires, etc. Resources such as offices and staff are required to run a firm. To start an IT firm, one must have an infrastructure. Designing, finishing, and executing the designs and requirements need much planning (Rodriguez, 2014). It also demands a significant investment in land and other technological devices. A locally hosted infrastructure may install and deploy numerous software applications using one's hardware, networks, and storage devices. However, as cloud computing advances in the technological world, organizations may rent physical amenities such as functional connections and hardware facilities monthly. Infrastructure as a Service (IAS) is an IT infrastructure available through various cloud-based solutions. Infrastructure-as-a-Service (IaaS) providers provide hardware and other essentials in return for service. It is essential to examine and analyze the whole service details for better implications and results.
The essential idea contributing to the mobile infrastructure IaaS prototype is to employ a simulated notion that allows equipment assets to be shared by several firms for various servers held by IaaS suppliers rather than arranging for hardware and organization demands as with nearby hosted groundwork.
The Benefits and Drawbacks of IaaS Analyzing particular benefits and drawbacks can lead to better choices and implications, in a real-life scenario. On the other hand, organizations will get the highest benefit, by building the most appropriate and compatible infrastructure. Cloud technology is already hard to manage and control in an organization. In that case, the analysis will also provide better clarity and operational benefits. Several studies show that cloud storage is growing increasingly popular among enterprises. Clients can rent infrastructure and platform services in addition to software from the cloud facility. In addition to cost reductions, using Infrastructure-as-a-Service may provide several other benefits. There is no one source of dissatisfaction, no hardware venture, and so on. No need to consider where the infrastructure will be placed, regardless of location. Serve that exact are stored in the same area as the company's other business activities is a huge hassle. There is no reason to lease or rent space when infrastructure is hosted in the cloud.
Hardware safeguards
There will be no need to keep an eye on the physical apparatus to ensure security. CCTV and security staff are used by businesses to secure their physical assets (Vaquero, Rodero-Merino, & Morán, 2011). IaaS services, on the other hand, are accessed via a cloud platform, and the company that employs them is indifferent to the physical security of the equipment. The failure of one or two switches does not affect the overall performance of a cloud-hosted network. IaaS providers have the redundant infrastructure to safeguard their consumers. If a single data center fails, the infrastructure may be automatically relocated to other data centers so that users can continue accessing it.
Flexible
As needed, infrastructure may be scaled up or down. If the company expands, it won't have to acquire more equipment to meet demand, as is the case with locally hosted infrastructure. However, with IaaS, organizations need to take a few simple actions to access extra resources immediately. This functionality considerably improves IaaS scalability as compared to locally hosted infrastructure.
Cloud computing technology is also resource and cost-efficient, as all the data are saved and monitored by cloud servers. In that case, the cost of big data centers is saved. Database management, system optimization and changes also become easier and more organized. This will help in other financial investments like inventory. The project managers can also plan new system updates and categorizations that can easily connect new suppliers and other stakeholders with the system. Building financial and sales reports will also be more accurate and easier by implementing the particular technology. In that case, the business leaders and management team will be able to prepare a most market-compatible and effective strategy.
Availability
It offers round-the-clock support with access to the company's selected infrastructure to store and install the software. Because of this concern, infrastructure is always accessible. Companies and customers can access infrastructure from anywhere in the world. This also improves the networking model and connectivity between the stakeholders and organizational authorities. In a cloud environment, organizations may manage their infrastructure more efficiently. This is because they are in charge of managing and making such resources available on demand (Vaquero, Rodero-Merino, & Morán, 2011). Infrastructure Management Requires Fewer Employees because the IaaS provider collects the infrastructure. Before making arrangements to relocate from local hosting, businesses must examine many critical aspects. This is also essential for organizational and system security management. The operation will require system encryption, a developer support team, regular system checkups, system verification, etc. The project managers will also be responsible to prepare particular system policies that can satisfy the security management requirements and implementation requirements. ECA wants to investigate moving two of its educational arms to a service-based model where many of its services would be supplied to its clients as a service, in addition to its plans to move to an IaaS model. Several infrastructure models could be used to achieve this. Some of these models are:
1. Local hosted infrastructure and applications.
2. Locally hosted infrastructure with some SaaS applications.
3. Hybrid infrastructure (some locally hosted infrastructure with some IaaS) and applications.
4. Hybrid infrastructure and applications with some SaaS applications.
5. Full IaaS model with some SaaS apps.
6. Full SaaS model.
You are required to choose an infrastructure model that you think will achieve the ECA Roadmap; describe the benefits and drawbacks, excluding costs, of your infrastructure model selected.
Hybrid infrastructure (some locally hosted infrastructure with some IaaS) and applications There are various advantages of employing hybrid architecture and technologies in IaaS services. The Hybrid cloud method with special IaaS features provides several benefits. It is a strength to serve both public and private clouds. It offers round-the-clock support for access. Outline the merits and disadvantages of the hybrid approach, excluding prices. This method has a significant advantage since it can be used for both. Private and public cloud infrastructures can coexist, and sensitive and non-sensitive data can be isolated (Williams, 2013).
It offers round-the-clock help for gaining access to improved Mobility. Choosing a hybrid cloud is also helpful in terms of change or upgrade. A small testing project is planned so that infrastructure may be easily adapted to suit future demands. Increased Development/Testing Capacity contends that hybrid clouds provide the best of both worlds in terms of scalability, adaptability, elasticity, and Location independence. A hybrid cloud option is also available worldwide, making it easier to use (Williams, 2013). The accessibility of on-site servers is another advantage for the company that it may utilize its existing servers. As a result, selecting a technical model compatible with some IaaS applications that suffer from the drawbacks of hybrid infrastructure and software is a good mixture (Manvi, & Shyam, 2014). In addition to its many benefits, the chosen model has several downsides, like identification and Personal Information Protection. As previously said, hybrid clouds provide the benefits of leveraging private and public cloud resources but also require substantial administration work. When determining what is public and private, extreme caution must be exercised (Khajeh-Hosseini, Greenwood, & Sommerville, 2010).
REFERENCES
COIT20246 Networking and Cyber Security Assignment Sample
Task 1
Part 1
Read the Marr (2022) resource from Forbes:
https://www.forbes.com/sites/bernardmarr/2022/01/07/the-5-biggest-virtual-augmented-and-mixed-reality-trends-in-2022/?sh=7483c5ae4542
Write an interesting, engaging, and informative summary of the resource. You must use your own words and you should highlight aspects of the resource you think are particularly interesting. It is important that you simplify it into a common, easily understood language. You MUST NOT paraphrase the resource or any sentences or ANY parts of the resource. You MUST NOT quote from the resource (except for key metrics if relevant). Your summary MUST NOT exceed 500 words. You will not be required to use in-text citations as you are only summarizing a single prescribed resource. As such, it is not appropriate to cite any other resources.
Marr, B 2022, The 5 Biggest Virtual, Augmented and Mixed Reality Trends In 2022, Forbes, viewed 10/1/2022, https://www.forbes.com/sites/bernardmarr/2022/01/07/the-5-biggest-virtual-augmented-and- mixed-reality-trends-in-2022/?sh=7483c5ae4542
Part 2
1. Find an Internet (online) resource that provides additional information and/or a different perspective on the central theme of the resource you summarised in Part
1. The important thing is that the resource contains different information. You should be looking for a resource that contain substantial additional information that strongly relates to the resource in Part 1. The resource must be freely available online or via the CQU library. You must provide a working URL - If the URL you provide cannot be accessed by your marker, you will receive zero for this entire part (0/4). You must also provide a full Harvard reference to the resource. This includes a URL and access date.
2. Like you did in Part 1, summarise the resource, in your own words. The summary should focus on highlighting how the resource you selected expands upon and adds to the original prescribed resource. It is important that you use simple, non-technical language that is interesting, engaging and informative. You MUST NOT paraphrase the resource or any sentences or ANY parts of the resource. You MUST NOT quote from the resource (except for key metrics if relevant). Your summary MUST NOT exceed 500 words. You will not be required to use in-text citations as you are only summarising a single prescribed resource. As such, it is not appropriate to cite any other resources.
If your summary does not relate to the URL/reference you provide (i.e. you have used information from a different source), you will receive zero. You should AVOID using academic resources such as journal papers, conference papers and book chapters as these are normally very difficult to summarise in less than 500 words. Instead, try looking for online news articles, blog posts and technical How-Tos.
Part 3
Reflect on the concepts and topics discussed in the prescribed resource and the resource you found. Your task is to summarise how you think they could potentially impact on YOUR future. The “future” can range from near (a few months, a year) to far (several years, decades). Summarise these in a response of no more than 500 words, ensuring that you develop and justify arguments for the impacts that you nominate. You will not be required to use in-text citations, as such, it is not appropriate to cite any resources. Once again, use simple, easy to understand language. DO NOT re-summarise Parts 1 & 2 – your reflection must be about the impacts on YOU and YOUR future.
Task 2
Part 1
Read the MacCarthy & Propp (2021) resource from TechTank: https://www.brookings.edu/blog/techtank/2021/05/04/machines-learn-that-brussels-writes-the-rules-the-eus- new-ai-regulation/
Write an interesting, engaging and informative summary of resource. You must use your own words and you should highlight aspects of the resource you think are particularly interesting. It is important that you simplify it into common, easily understood language. You MUST NOT paraphrase the resource or any sentences or ANY parts of the resource. You MUST NOT quote from the resource (except for key metrics if relevant). Your summary MUST NOT exceed 500 words. You will not be required to use in-text citations as you are only summarising a single prescribed resource. As such, it is not appropriate to cite any other resources. MacCarthy, M & Propp, K 2021, Machines learn that Brussels writes the rules: The EU’s new AI regulation, TechTank, viewed 10/1/2022, https://www.brookings.edu/blog/techtank/2021/05/04/machines-learn-that- brussels-writes-the-rules-the-eus-new-ai-regulation/
Part 2
1. Find an Internet (online) resource that provides additional information and/or a different perspective on the central theme of the resource you summarised in Part
1. The important thing is that the resource contains different information. You should be looking for a resource that contain substantial additional information that strongly relates to the resource in Part 1. The resource must be freely available online or via the CQU library. You must provide a working URL - If the URL you provide cannot be accessed by your marker, you will receive zero for this entire part (0/4). You must also provide a full Harvard reference to the resource. This includes a URL and access date.
2. Like you did in Part 1, summarise the resource, in your own words. The summary should focus on highlighting how the resource you selected expands upon and adds to the original prescribed resource. It is important that you use simple, non-technical language that is interesting, engaging and informative. You MUST NOT paraphrase the resource or any sentences or ANY parts of the resource. You MUST NOT quote from the resource (except for key metrics if relevant). Your summary MUST NOT exceed 500 words.
You will not be required to use in-text citations as you are only summarising a single prescribed resource. As such, it is not appropriate to cite any other resources. If your summary does not relate to the URL/reference you provide (i.e. you have used information from a different source), you will receive zero. You should AVOID using academic resources such as journal papers, conference papers and book chapters as these are normally very difficult to summarise in less than 500 words. Instead, try looking for online news articles, blog posts and technical How-Tos.
Part 3
Reflect on the concepts and topics discussed in the prescribed resource and the resource you found. Your task is to summarise how you think they could potentially impact on YOUR future. The “future” can range from near (a few months, a year) to far (several years, decades). Summarise these in a response of no more than 500 words, ensuring that you develop and justify arguments for the impacts that you nominate. You will not be required to use in-text citations, as such, it is not appropriate to cite any resources. Once again, use simple, easy to understand language. DO NOT re-summarise Parts 1 & 2 – your reflection must be about the impacts on YOU and YOUR future.
Solution
Task 1
Part 1
The technology is moving around. With the fast pace change in the technology, many industries are witnessing some new trends in terms of AR, VR and Mixed reality. The time is now focusing on XR or a new trend settler that may changed the entire industry. The tech has renewed everything like gaming experience, or at the workplace so that people could think out of the box. This article has defined some of the key trends in 2022 that go beyond the expectation and also reshaped the life of every individual.
XR & Metaverse: The world will soon witness a new aspect through the technology. Metaverse a place where everything will be drafted as 3D modelling, avatar and gamification. These three are the core concepts & fit exceptionally well with the Virtual Reality Technology. The idea of metaverse is a mesh of different technologies to make a virtual world for all.
Advanced hardware and headsets: Hardware are a special and important component for any tech. Without hardware nothing is possible. It accesses the virtual reality and bring the most powerful time of the era. With the time, AR and 2 VR devices are getting lighter. One of a good example for it is California startup Mojo Vision that has demonstrated the potential of AR by making contact lens that share and transcript the information directly to the retina.
XR in retail: The most changes occur in the retail industry and it is going through the alteration everytime. There are plenty of opportunities are determined in retail industry with the application of XR. For brining the distinct shopping experience, VR is already used and provide advantage to the “brick & Mortar” system.
Although, AR technology is providing support in taking feedback and improving the system. Also, VR brings a platform where user can get new experience of shopping by putting their avatar and try some clothes, jewellery on them.
XR & 5G: Within the next few years, a new and revolutionary network will be launched around the world. 5G is already rolling out in the market and taking a mainstream proposition. Currently, some companies are working in a trial phase and provide exceptionally well speed that is 20 times more than the existing one. Moreover, a different experience is providing to the gaming as well through XR. It is not a costly element for the business and can easily set up without putting a lot of money of large infrastructure investment.
The use of technology in different businesses and processes for assignment help signify that sooner a major throwback will appear in the industries. XR is exploring its roots around every sector and provide pace to the companies to grow and maximise their operational ability. It can be also used in training and educational stream. It provides some assistance to the adult learning as after COVID, everyone shifts their paradigm of learning to the online platform. The XR technology is making things easy as visuals are more supportive than reading. It makes a learning a better place with the best idea.
Part 2
Artificial Intelligence and virtual reality are the core pillars of the future. A future is unpredictable and technology helps to predict it. Virtual reality will explore things in the next five years. The market growth is high which will benefit multiple businesses around the world. A market study shows that AR & VR market will reach 15 billion in the 2022 year. The annual growth rate (CAGR) will be 77% in 2023. AR and VR will be at the focal point of computerized change and the expenditure of various organizations and buyers will increment by 80%. The companies and buyers will prompt this development at $1.6 billion. The industries that are using the trend most by retail, manufacturing, healthcare etc. AR is supposed to overwhelm the VR market spending as soon as this year or relatively soon.Technology is an essential driver for this development will be the quick development in the reception of tablets, PCs, and cell phones, and the exorbitant grouping of significant tech players in AR and VR around the world.Presently, the equipment market drives the product market concerning income. Notwithstanding, the product market will observe a quicker development because of an expansion popular in the media and media outlets to address issues, for example, AR-based reproducing of games.The medical care and retail space of the economy will prompt the reception development of AR and VR. Between AR applications and VR applications, AR-based purchaser application has the biggest offer as per this report, more than the business, aviation and guard, venture, medical care, and others. The biggest interest in augmented reality applications is coming from business applications.Artificial Intelligence is growing and shaping the world. It makes and contributes to the success story of many companies.
A real-life experience is possible with the help of artificial intelligence and virtual reality. The future of trends involves VR headsets to check the travel locations, clothing, architecture of the home and many more. All such things are possible with the implementation of augmented reality Augmented reality are growing with the time. Augmented reality and virtual reality are sharp aspects that helps in choosing the right thing for a person. Now, everything is covered with it like clothing where an individual can try an outfit. Alongside, some more and interesting benefits derive with the use of AR and VR are:• Make your dream interior of the home. The interior designing is possible with the VR headsets. The large corporations place headsets on an individual and they can check the preferred interior and get a real home feeling.• Playing games is an exciting thing because VR headsets brings an immense experience to the user. Users can now play any game like football, cricket or anything with real world appearance. These are many things could be done with the help of Artificial Intelligence like medical operations and healthcare services. With the fast pacing world, combination of augmented reality and virtual reality would bring diversified benefits.
Harvard Reference: Future of Virtual Reality – Market Trends And Challenges, 2022. [Online] Software testing help. Available at: https://www.softwaretestinghelp.com/future-of- virtual-reality/. [Accessed on: 26th May 2022]
Part 3-
The impact of technology on our everyday life is most. It makes everything easy as we don’t need to do things manually now. We have different software that could help in doing things early and frequent. The use of technology signifies some important aspect for me and my future. It draws a positive impact on my life like improvement in communication, making more justified decisions, search things on tip and many more.
The first impact on my is predicted in terms of connectivity. The technology has connected us with our closed ones through video conferencing. After COVID, many people have put heavy investment on it and make many video call apps with distinct features. In near future, AR, VR and XR makes things more revolutionary as they might bring the closed ones so close to you in every aspect like it might be possible that we can sense them or make a look alike of them to get a sense of closeness with them. Such things are might be possible in the future.
Another aspect for me is reshaping of future experience. The technology has supported me to even try the new outfit online. It has helped in reshaping my entire shopping experience into a legitimate one. Online apps are now providing a feature where we can just try the outfit on our avatar and check that it suits the personality or not. Moreover, in future, we don’t even have any idea how it will bring more changes and make our shopping experience a unique one.
Although, I have heard a lot about the metaverse, a virtual environment place. Many people are putting their efforts to understand the terminology. Moreover, some people have already purchased land in metaverse and doing so many things. The days are not so far when we can see pregnancy and babies will be do through metaverse. The revolution of technology has put and made things so interesting. With the time, we can see many changes done through Artificial Intelligence, it makes our life easy and simple. Different technologies are providing by it that support me and others to do simple tasks. Like if we want to call someone, we can use voice assistant and make a call. Though, life is simple after the use of technology. We find these things interesting but somehow it will impact our future. We all went lazy and might be into the depression due to minimum friends, least outings. All we will get in front of us with this rapid pace and movement of the technology. Hence, it is important for us to understand the long term impact of technology and make some smart decisions so that it would not control our life completely but just can be used it as to ease it down.
Task 2
Part 1
The decision propose by the European union on 21 April was not appropriate from the future world perspective. Banning AI is not a good idea and it leave the technology alone. The certain reasons that become the core context behind the ban are:
- Data and data governance
- Documentation and record keeping
- Human oversight
- Accuracy and security
- Transparency
All the stated points should be signified by the users when they prefer high-risk AI system. It is a major innovation & many scholars believe that it helps in postmarket monitoring system. It will help in detecting the problem and also suggest some effective ways to mitigate it. With these innovation and sound based-risk structure, the regulations also unfold some interesting gaps and completely omitted them. The BigTech is not touched yet.
The article states that regulation is highly focused on provider and covered the users. The developers who are working on AI system have only two options: Sale it to the market or use it for own welfare or for the business. The tech scope is not defined properly because it only covers the EU providers and completely forget and not consider the location of the provider but also the system users who lives in the EU. The prohibition is limited to the AI system that can cause “physical or psychological” harm or promote vulnerability to the specific group people. The prohibition is stern at some places but focused on the restriction of the dark pattern use. These are certain groups that influence or put pressure on the users to take decision against their will.
The regulation is somehow working for the welfare as well because it supported the use of remote biometric identification system while looking for crime victims, missing children, impose specific threat such as terror attack, prosecute serious criminal activity, giving prior judgment. This entire regulation makes the entire team of EU members satisfy as they somehow tried to protect internal security and terrorism. While framing the regulations, some points and elements have been completely omitted by the government. The first aspect is showing the concern about algorithm bias but the text was thin. The regulation also signifies disparate impact assessment & the data governance provision support providers to use the data concerning properties such as race, gender and ethnicity to get assurance about bias monitoring, detection and correction.
Part 2
Artificial Intelligence is a new normal for the world. Many companies are using this tech to bring revolution to the mainstream and work to get a competitive edge and advantage. The AI is a new normal as it helps in resolving queries as early as possible. Chatbot, CRM and analytics everything require AI. Artificial Intelligence keeps the business ahead. Many innovation and revolutions are brining by the AI that support business in management of distinct operations like chatbot. It also provide varieties of services like CRM, analytics, reporting etc. the AI is code driven framework that spread in different parts of the world as companies are heavily relied on the data and availability. With the hacking and security of data management, AI is important to spread and helps in handling every sort of situation.
Artificial intelligence will contribute in human task management and promote adequacy in operations. It maximise the capability of an organisation and support to get the desired outcome. It helps in making things simple and support various forms of activities that are beyond human expectations like navigation, learning and exploring, visual presentation and analytics, language interpretation. A good framework is helpful in making vehicles smart, support utilities, and support business to save cash, time and aid in future by modifying the world. The system is also active in health and social care as well. Many medical service providers are using AI to diagnose and treat patients and assist senior residents to get complete information and provide better life. The artificial intelligence has added a general wellbeing program as huge information is not stored in the database. It helps in make the society about new disease, it’s diagnose that support an individual as well as the entire community. The AI would more changes soon in the schooling system as well and make an effective learning environment for the students.Artificial intelligence has contributed a significant aspect on the companies and their operations. The growth and operations of different industries are highly depend on the AI and the transforming technology. Retail industry, healthcare sector, automotive industry and many others are using AI to make their operations effective. Machines are going on another level and achieving remarkable milestones. The artificial intelligence is supporting every industry around the world like medical, legal, designing and architecture, music composition. The machines are now become highly advanced and perform every single task perform by a human. Sooner robots will do operations and provide medical medications. It brings extraordinary outcome and accelerate the growth of companies with time. There are many positive scenarios of the AI in the future context and considerations. • The machines can produce more as compared to the human. The production by robots is higher than the human beings. Thus, it will help in maximising the economic prosperity.• The labours are no longer an issue after the artificial intelligence.
Machines are more creative than humans and provide effective response. The labour market will become more flexible and appropriate as individual can make changes in the system to generate and gather more opportunities. • The robots will be used for the wars as well. On the other side, humans will be used only for performing labour intensive tasks. Using robots for wars is a major and beneficial output for the future. Artificial Intelligence and machine become an effective and most responsive part of our life. With it, many milestones can be accomplished in distinct industries.
Harvard Reference: Rainie, L. and Anderson, J., 2018. Artificial Intelligence and the Future of Humans. [Online] Pew Research Center. Available at: https://www.pewresearch.org/internet/2018/12/10/artificial-intelligence-and-the-future-of- humans/. [Accessed on: 26th May 2022].
Part 3
The use of AI is a beginning of the new era. With the time, many people are using AI just to make their life simple and easy. On the other hand, my perspective for using AI is to make the things fast moving and reduce the burden on my head. If the EU has putting law against its use is not a right thing. The Artificial Intelligence is a major backbone of the tech and innovation and it keeps the things alive.
Unlike banning it consider it as a human & provide similar rights to it. In my opinion, the technology is based on algorithm and codes and if someone tries to manipulate it we could then take some strict actions against it. But still the things are doing out of the will of the tech because it just a machine. On the other side, we can give it a right to file a case when someone manipulate it or make alterations into it. One major example is Sophia, Robot of Saudi Arabia have more than any other women in the country. The government has provided equal rights to it so that she could file a case against people. There are many countries that limit the freedom of speech, religious practices and other consider. I think it will be a big breakdown for the future because machine will run things, if we could give them an equal right. It somehow harm dignity of the human but would be great as people can do a lot of things with the tech. Using robots in the military can control a lot of damage of human life and we can put such military people on other tasks like managing borders but for fight we need to use robots only. It can control collateral damage. Using AI in crime investigation will be a great thing because it helps in checking fingerprints quickly or to find out some important evidence. Some people claim to give equal voting right as well but it seems inappropriate in today’s world. We should not give any voting right to machines. There should be some limitations set for the machines as well like we did for humans. Using of AI such as robots is a great thing and will benefit the future as well. There are some negative aspects but we should consider the positive one and need to give a little chance to machines.
COIT20261 Network Routing and Switching Term Assignment Sample
Using this information, answer Question 1 and Question 2. Show your calculations for all sub-questions.
Question 1 – Information about the block
a) How many addresses are available in the block allocated to the company, including all special addresses?
b) What is the network address of the block?
c) What is the direct broadcast address of the block?
Question 2– Allocating subnets from the block
Create five contiguous subnets from the given block beginning with the first address of the block, as follows:
i. The first subnet with 1024 addresses
ii. A second subnet with 512 addresses
iii. A third subnet with 256 addresses
iv. Two (2) subnets with 126 addresses each
For each subnet, show its prefix in CIDR format, its subnet address, and its direct broadcast address. Organize your data clearly in a table.
Question 3 – Network Tools (Windows)
Often the best way to gain an initial familiarity with network tools is to simply use them at a basic level, exploring and looking up information as you go. Some common tools you can explore include Wireshark, ipconfig, tracert, netstat, ping and arp. All but Wireshark are included in Windows, Wireshark is free to download and install. Explore these tools by researching online and trying them out yourself on your computer, then answer the following questions, using your own words. Paste screenshots of your tryouts (not downloaded/copied from the Internet!) of each tool you have chosen to answer the questions below.
a) Assume that you want to use a command-line network tool to check if you have internet connection from your computer. From your desktop what command (tool) could you try first to find out if your internet connection is functioning OK or not?
Explain the tool and its output in determining your internet connectivity status.
b) You want to find out what IPv6 address your PC is currently configured with. What command could you use to discover this? What other information could you discover from using that command? Explain your answer.
c) Assume that you want to know which TCP ports are currently open in your computer. This information is quite useful for assignment help in checking if there are malicious services running on your system that have been introduced via malware. Which command would you use to discover this information? What other information could you discover from using that command? Explain your answer.
Question 4 -- TCP
Study a diagram of a TCP segment header (for example, Figure 9.23 in your textbook), paying special attention to the header fields, then list each field (field name) along with the value in decimal that would be in that field as per the information provided below. You must briefly explain your answer for each field.
• The segment is from an Internet Relay Chat (IRC) client to an Internet Relay Chat server
• A port number of 49,600 was assigned on the client side
• There were 20 bytes of options
• The server will be instructed not to send more than 500 bytes at any one time
• The previous segment from the server had an acknowledgement number of 12,400 and a sequence number of 8,300
• The TCP checksum was calculated to equal binary zero
• The control flag fields indicate states of: not urgent; not first (sync request) or final (termination request) segment; no bypass of buffer queues required; and not a RESET.
Solution
A) 2048 addresses are available in the block allocated to the company, including all special addresses. These special addresses are network and broadcast addresses. Given the IP address is 140.66.36.120/21 it shows that the first 21 bits of this address are reserved for the network address. Out of a total of 32 bits, (32-21)11 bits are left. So, 2^11 = 2048.
B) Network address = 140.66.32.0
Given IP address = 140.66.36.120/21
Network bits are 21
Binary format = 10001100. 01000010. 00100100. 01111000
Where the network bits are first 21 bits 10001100. 01000010. 00100
Network address = 10001100. 01000010. 00100000. 00000000
In decimal = 140.66.32.0
C) Direct broadcast address of the block
Given IP address = 140.66.36.120/21
The binary form of the given IP = 10001100. 01000010. 00100100. 01111000
In the direct broadcast address of any address block, network bits are all 1 and host bits are all 0.
Direct broadcast address = 11111111.11111111.11111000.00000000
In decimal = 255.255.248.0
2)
Question 2 – Allocating subnets from the block
Organise and write your answer neatly in a table and show calculations
.png)
The given IP address here is 140.66.36.120/21 which shows that 21 bits are used for the network part and the remaining bits 32-21=11 bits are used for the subnet and host part in the network.
After applying an AND operation with a subnet mask which is 255.255.252.0, the result generated is the address of the block is 140.66.36.0/23.
These 9 bits can be used to calculate the host - 2 11 = 2048.
By using VLSM (variable length subnet masking), each subnet will be defined with a different requirement (1024+512+256+128+128=2048). The CIDR routing can be done through 2 11=2048 bits, where 1024 bits are the most significant 0 and the remaining 1024 bits are the most significant bit 1.
.png)
Figure 1 Diagram to show CIDR and subnetting
First subnet - The 140.66.0010 0100. 0000 0000
Hence its subnet address becomes
140.66.36.0 and as we can see that the subnet bit will remain the same in all host parts hence its prefix is 22 (the first 22 bits are common in all hosts)
For broadcast address - all 1’s in the host part over here host bits are the last 8 bits hence
It converts to 140.66.0010 0100. 1111 1111
Which gives 140.66.36.255/24
So, the subnet mask for 1024 addresses subnet = 255.255.252.0
Second Subnet - Now as we can see from the figure the 2nd subnet needs a 512 host for that many addresses, we need 9 bits for a host which will leave 2 it for the subnet, for subnet identification it uses 10 bits
Hence,
140.66.0010 0101. 0000 0000 which gives
140.66.37.0/23 (prefix 23 because the first 23 bits will remain the same in all host parts)
For broadcast address put 1 in all host part
140.66.0010 0101. 0111 1111
Which gives 140.66.37.127/23
So, the subnet mask for 512 addresses subnet = 255.255.254.0
The third subnet - Now the third subnet needs address 256 which will require 8 bits for the host part and that will leave 3 bits for the subnet, for its subnet we will use bit 110
140.66.0010 0101. 1000 0000 which gives
140.66.37.128/26 (prefix 24 because the first 24 bits will remain the same in all host parts)
For broadcast address put 1 in all host part
140.66.0010 0101. 1011 1111
Which gives 140.66.37.191/24
So, the subnet mask for 256 addresses subnet = 255.255.255.0
The fourth subnet - Now the fourth subnet needs address 128 which will require 7 bits for the host part and that will leave 4 bits for the subnet, for its subnet we will use bit 1110
140.66.0010 0101. 1100 0000 which gives
140.66.37.192/25 (prefix 25 because the first 25 bits will remain the same in all host parts)
For broadcast address put 1 in all host part
140.66.0010 0101. 1101 1111 which gives 140.66.37.223/25
So, the subnet mask for 128 addresses subnet = 255.255.255.218
3)
Question 3 – Network tools - Windows (5 marks)
The command tool ping will be used. A ping is a tool for checking end-to-end connectivity between two endpoints and verifying internet connectivity.
Type “cmd” to bring up the Command Prompt.
Open the Command Prompt.
Type the “ping” command.
Type the IP address to ping.
Review the results displayed
Another tool that can be used here is ‘netstat -a’ to check active connections.
.png)
Figure 2 Result of ping command that shows successful pinging means an internet connection is active
The command to get the IPV6 address of the PC is "ipconfig /all"
This command is used to show IPv4 and IPv6 addresses with subnet masks and addresses. It can also be used to show DHCP and DNS settings. It also displays the current network that can be TCP/IP without using any kind of parameters.
.png)
Figure 3 Result of ipconfig/all command
Other information includes the drivers like media state, connection type of DNS, hostname, physical address, and status of DHCP enabled or not.
Netstat command is used to know which TCP ports are currently open in the computer.
.png)
Figure 4 Output of netstat -q command
.png)
Figure 5 Output of netstat -s command
Other than these, different information can be collected by using this command like active ports, current connection, segments received, send and retransmit, and failed attempt in connection.
4)
Question 4 – TCP (5 marks)
.png)
The first Row holds the source port address and Destination port Address which is 16 bits
The second Row covers the Sequence Number which is 16 bits
The third row comprises the Acknowledgement Number which is 16 bits
The fourth Row encompasses Header Length (4 bits) and (6 bits) reserved bits with 6 functions
Six Unique bits for six functions: They are
1. First One - URG - When this is 1 means - it is urgent and When this is 0 means - the segment is not urgent
2. Second One - ACK - Whether the segment contains valid Acknowledgement or not
3. Third One - PSH - Which means the request for Push
4. Fourth One - RST Which is for resetting the segment
5. Fifth One - SYN - Synchronize the segment with the following segments.
6. The Sixth One - FIN - Is for Terminating the Connection.
Fourth Row comprehends the window size that includes segment Length which is used to carry Data
Fifth Row consist of
Checksum – It is used to check the error occurrence in the segment
Urgent Pointer - This is for telling that the segment is very urgent. So, the TCP will give priority to this segment.
The sixth Row encompasses residual information of the segment and data will be added to this place.
- The segment from Internet Relay Chat client to Internet Relay Chat server is used for chat communication over the internet through different channels and access to the servers.
- A port number of 49,600 was assigned on the client side which is used for TCP/UDP connection. The Transmission Control Protocol is used for connection-oriented infrastructure and establishing a connection between the client and server side, and exchanging data.
- There were 20 bytes of options, then, the maximum header length will be 20B+60B = 80 B and the minimum will be 20B+20B=40B.
- The server will be instructed not to send more than 500 bytes at any one time which is more than the receiving speed. In this case, if the packet is too large from the server end, then the receiver client does not accept it. This packet will be divided into multiple segments and then sent.
- The previous segment from the server had an acknowledgment number of 12,400 and a sequence number of 8,300 where 8300 is the streaming rate of data from sending and receiving TCP whereas 12400 is the next sequence number which is the receiver for the destination node.
- The TCP checksum was calculated to equal binary zero which can be calculated by the sender and it represents that an error occurred during the transmission process.
- The control flag fields indicate states of
- not urgent – URG=0
- not first (sync request) or final (termination request) segment – ACK=0
- no bypass of buffer queues required – SYN=0
- not a RESET – RST=0
SIT763 Cyber Security Management Assignment Sample
Task 1: Security Education Training and Awareness (SETA) Programme
Create a role-based SETA programme in the following three roles: real estate agents, data centre operators, and cyber security engineers. For each role, recommend the most appropriate and unique SETA element using the table shown below. Here is the description of each criterion:
Goals – identify two unique and meaningful goals. Explain why you have chosen them.
Objectives – identify one or more unique objectives for each goal. Explain why you have chosen them and how the objectives help attain the goals.
Programmes – choose from security education, security training, or security awareness the most appropriate program for the role. Justify why you choose it.
Delivery – identify a suitable SETA element delivery method. Explain and justify why the method will be effective for the role.
Value – explain what the attendees can take away from the programme that will help or advance their knowledge, skill, or awareness level.
When writing your answer for each criterion, consider the background and skill level of the staff in each role. Also, make sure you explain and provide justifications that are supported by relevant references.
Task 2: Incident Management and Response
You will use the NIST Incident Response framework to develop a cybersecurity incident response plan. Answer the following questions.
2.1 Create a visual representation (diagram) of the cybersecurity incident response plan's critical phases. Give a brief explanation of the important message conveyed by the diagram.
2.2 Using the diagram above, briefly describe the incident response steps taken by the security incident response team after a critical data breach is detected.
2.3 Explain how the information gathered during the incident response process will be used.
Your response to the above questions for assignment help must be supported by references, theory and demonstrate application of critical thinking skills.
Solution
Task 1: Security Education Training and Awareness (SETA) Programme
.png)
.png)
Task 2: Incident Management and Response
.png)
Figure 1 Cybersecurity incident response plan's phases
The important message conveyed by the diagram is that
- A process of preparation, detection/identification, analysis, containment, eradication, recovery, and post-incident review is essential for effectively and successfully responding to security incidents. These phases are the essential framework for thoroughly managing security incidents and provide a basis for achieving organizational resilience [1].
- It is also conveyed from diagram that incident response requires a structured, systematic approach in order to be successful in identifying and mitigating threats, as well as in restoring normal operations
- It also emphasizes the need for organizations to prepare and test the incident response plan and to categorize the incident types in order to be ready and prepared for such a situation.
2.2 The security incident response team (SIRT) will take the following steps when a data breach has been detected:
.png)
Validate the incident: The SIRT will verify the incident and analyze the nature of the data that has been compromised.
Contain the incident: The SIRT should identify any affected systems and isolate them to prevent further damage. They should also delete any malicious or unauthorized files and disable any affected accounts or services [4].
Gather evidence: The SIRT should collect, preserve, and analyze all necessary evidence to identify the circumstances surrounding the incident.
Investigate the incident: The SIRT should investigate the incident to identify its root cause and the extent of the damage [4].
Create a timeline: The SIRT should also create a timeline of events surrounding the incident. This includes recording the time of the incident, the time the incident was discovered, and the time each incident response action was taken.
Restore normal essential services: The SIRT should restore essential services as quickly and securely as possible to minimize the impact of the incident on the business.
Test and monitor: The SIRT should test the security measures that have been implemented to ensure that they are properly protecting the environment and are working as intended. They should also monitor systems for any suspicious activity that may indicate that the incident is still in progress.
Communicate: The SIRT should communicate their findings to stakeholders and relevant parties to ensure that any action taken to remediate the incident is understood.
Document the incident
Take preventive measures: such as implementing new security measures and implementing stricter access controls to prevent similar incidents [5].
2.3 The security incident response team will use the information gathered during the incident response process for multiple purposes.
- To Identify the Source and Impact of the Breach: The information gathered during the incident response process, such as log files, alerts, and other activities across the network/systems will help the security incident response team to identify the source of the breach and estimate the potential impact of the incident.
- To Take Steps to Contain the Breach: The security incident response team will use the information to take steps to limit any further loss or damage by isolating the affected systems and networks, halting any ongoing activities, and limiting access to the affected data/systems.
- To Identify malicious actors and Targeted Techniques: The security incident response team will use the information to investigate and identify any malicious actors, their techniques, tactics and procedures, and any malicious code or files that have been deployed.
- To Recover Data and Services: The security incident response team will use the information to take steps to recover any data or services that were compromised such as restoring any lost data and running vulnerability scans to identify any other potential threats.
- To Properly Inform Senior Management and Other Stakeholders: The security incident response team will also use the information to properly inform senior management and other stakeholders about the incident, its impact, and the steps taken to contain and remedy the breach [4].
References
.png)
MITS5003 Wireless Networks and Communication Assignment Sample
Task
The university's head of IT has recruited you as a third-party consultant to provide them with a wireless LAN solution for their network. The institution has little over 800 employees who work in a complex of seven buildings in an urban area. Employees routinely walk between buildings because they are all near enough together. Wireless technology is something that the management team wants to implement in their company's network. They've heard that, compared to the current leased line network, this type of network will save them money. They anticipate that increased mobility will result in a significant boost in production. Because the workforce moves from building to building, it appears to be a good idea to offer them with portable computer equipment and data. Figure 1 depicts the area covered by the university buildings. The assessment requires you to plan and design a wireless network for the university using any industry tool of your choice. Citation of sources is mandatory and must be in the IEEE style.
Solution
Introduction
With the rapid advancement of technology and smart devices, most organizations are enhancing their communication channels by implementing different tools and techniques. Healthcare, education, telecommunication, retails, and other industries are now implementing the ICT (Information Communication Technology) network architectures to enhance their communication system. In this task, an information communication architecture will be developed for an university. After analysing all the major requirements of the university, a wired and wireless network architecture will be developed in this paper. All the necessary networking components and devices will be identified in this report. In order to design the network design, MS Visio diagramming tool will be utilized. However, the network design will also be critically analysed in terms of different factors or usability by the university employees. Moreover, some major constraints and limitations of designed network will also be discussed in this report. Based on the university’s requirement, all the major networking components will be included into the network architecture. This network design must offer an advanced and speed communication network to the users.
Requirement analysis
In order to resolve disagreement or misunderstanding in requirements as needed by different individuals or groups of users, eliminate functionality creep, and document every step of the project creation process from beginning to end, requirements elicitation requires continuous communication with network administrators and consumer. Instead of seeking to shape consumer expectations to match the requirements, effort should be concentrated on making sure that the end product or service adheres to customer needs. In this task, all the major requirement of the university including functional and non-functional requirements have been identified [1]. The characteristics that the system must offer to its clients and end users are specified by the functional requirements. It outlines the functionality required for the system to operate. The characteristics of the technology for assignment help are the malfunctioning needs. They are made up of operational or resolution restrictions as well as outside variables like system dependability.
Functional requirements
Functional requirement for the network design can be categorized into different components including hardware, software, client device, connection media and other models. In this section, function requirements for the university has been illustrated. In order to design the network, a number of networking equipment will be required. In the below table, all the major functional requirements for network design have been illustrated.
.png)
.png)
.png)
Table 1: Hardware requirement
In the above table, all the major hardware requirements have been illustrated that could be utilized for the network design. On the other hand, some major software and protocol requirements have been identified in the below points:
• TCP and IP model that could give a standard layered internet architecture to the university [4].
• OSI model that gives raw data transmission and connection to network users.
• IP addressing approach must be adopted to provide network address to each devices and networking components.
• Windows 11 operating system must be installed into the workstations which will be accessed by the users of the university.
• Anti-malware application or programs should also be installed into each workstations to protect devices from being hacked or breached by the hackers [5].
• FTP is another vital protocol that need to be implemented by the network developers.
Therefore, a complete functional network requirement analysis need to be done before designing the network.
Non-functional requirements
There are several non-functional requirements are also associated with this project that need to be considered. These are such characteristics that helps to understand performance and reliability of the develop network design. In the below points, major non-functional requirements have been identified:
• Performance: Current network performance must be enhanced with better speed and function of the network. This will help to higher the productivity of workforce into the university.
• Usability: An advance and simple network architecture will be available to the users. A number of features and functions will be available to the users. Based on the system architecture, all the major changes into the system could be easily made by the users [6].
• Security: In order to protect data and information of the university, a secure data transmission protocol could be enabled by the users. The communication channel must be secured by using security protocols and anti-malware programs.
• Scalability: With increase in student size or university architecture, the network could be expanded with other networking components. Scalability is a major requirement of the designed network architecture.
• Reliability: The designed network must be reliable for each users of the university. During the peak hours, it must give a better communication channel to the users. This characteristic will give better networking experience to the users [7].
• Availability: Each feature of the network must be available to the users at any time. It can be defied with the request made and potential response acquired by the users.
Depending on the university infrastructure, the above functional and non-functional requirements will be fulfilled during the network design.
Network design
In this section, the network architecture design for university has been developed that includes a number of networking components. In the below figure, the network architecture design has been given. The network architecture design has been developed by using MS Visio diagramming tool. This network has been developed to fulfil all the major requirements of the university.
.png)
Figure 1: University network design
(Source: Author)
In the given figure, complete network architecture design for an university has been developed. All buildings of the university has been given with a wireless network facility. Different aspects of network architecture design has been considered during design development.
Critical Analysis
The network design task becomes critical if size of the institute or organization is larger. Depending on the IT infrastructure and industry requirement, some major actions need to be taken by the users. In order to achieve the business goal of the institute, all the possible challenges and issue must be considered and mitigated by the network engineers. Therefore, it is important to critically analyse the available network architecture after development and testing. In the developed network design, all the major considerations have been addressed for the university. Here, the star network topology has been adopted which gives a better networking facility to the users [8]. The gateway router has been installed into the main building and from gateway router other seven routers have been connected. For each building separate routers have been installed. In each building, network switches have been connected from the network router. In each building, wireless access point have been installed to provide remote networking facility.
This section includes how several sorts of needs can work together to produce the required information system, which will eventually make it easier to accomplish business objectives. The top-down technique, as shown in figure, is used in this presentation to build up the specifications beginning from the organisational objectives to the functional requirements stage, such as the necessary characteristics. With the help of wireless devices, users will be able to work from any location or building of the university. Different servers have been installed into the main building of the university. This will work as an IT support building of the campus. At the same time, firewall protection has also been given. It has been installed into the gateway router. Firewall helps to filter malicious data packets or viruses entering into the network [9]. If network applications or products are deployed without taking into account their properties and network needs, it's likely that business objectives won't be met. In this network design of contemporary educational services might offer video contact between its IT team and students in an effort to set itself apart from rival businesses. If the network administrator did not properly take into account the needs for videoconferencing as a network application, the programme is likely to fail to provide the end users with the intended experience.
Therefore, both the wired and wireless network design has been included into the network design. In order to enhance the network performance, network bandwidth could be increased by the service providers. On the other hand, high speed routers have been installed into the network which will also make the performance better. An internetworking facility has been introduced into the LAN design. This network design could be expanded in future according to the university requirement. A reliable network architecture has been developed which could give a smooth networking opportunity to the users.
Constraints and Limitations
There are several constraints and limitations are also associated with the network design that should be considered to enhance the network performance. Some major constraints have been illustrated in the below points:
• Cost is a major limitation that must be considered during the network design. In order to purchase high speed networking equipment, enough budget need to be allocated by the university authority [10]. In this context, it may become a challenging aspect for large scale network infrastructure development.
• Time is another constraint that need to be considered by the network developers as it may take unto several months to complete network design project. From the initial stage of requirement analysis to the networking device configuration, each task must be done on time.
• Expertise of staff and internal staff if also a major aspect that need to be considered by the network developers. Initially, user may not be able to use each features properly as there may be some limitations for network design. In this case, a proper training schedule need to be enabled for the network users.
• Updated cabling structure for better communication and connection need to be adopted by the users. Speed of the network may different due to the different cabling standards [11]. On the other hand, wireless communication may cause drop in network speed. Based on the system architecture of the university, proper bandwidth must be given by the service providers.
• Security infrastructure of the network must be strongest as a number of security breaches have been recorded in recent times. Each devices need to be updated and introduced with advanced version of software and anti-malware applications. Security requirement checking periodically is another major challenge in this case.
In the above points, most potential limitations and constraints associated with the network infrastructure has been identified that need to be considered by the network engineers. In order to provide a proper network infrastructure to the university authority, each requirements must be considered. However, the impact of the design limitations and constraints have also been discussed in the below points.
• The network architecture will be successfully established for the university if all the potential challenges and issues have been considered in the initial phase. The communication channel could be established by the network developers.
• The network will become fully secured form any external entities or hackers. Data and information security could be enabled by the users.
• Users will be able to communicate with each other with the help of wired or wireless network. Data and information of the university will be stored into the database server of the company.
• Usability and accessibility to the network devices and data will be increased with the successful implementation of the network architecture into the university.
The usefulness of such ICT network for each individual rises with the overall quantity of users, which is perhaps their most important feature. The value of innovations like smart phones and email is more closely tied to the number of people one can connect with through the system than it is to the services they provide consumers. As the user base expands, technologies has a tendency to gain velocity and begin expanding via a self-reinforcing mechanism into the educational institutes. The network keeps expanding on its own the more people who use it, the greater the cloud computing use value, the much more new customers who will use it, and so forth.
Conclusion
An information communication architecture has been created for a university in this project. In this paper, a wired and wireless network architecture has been built after evaluating all of the university's key requirements. This report includes every device and networking element that is required. MS Visio has been used as a diagramming tool to create the network design. But university staff members has critically evaluate the network design in terms of several elements or usefulness. This study also cover several significant design-related restrictions and limitations. All of the key networking elements have been incorporated into the network design in accordance with university requirements. Therefore the designed network architecture will give a better networking experience to both internal and external users of the university.
References
.png)
BMP4005 Information Systems and Big Data Analysis Assignment Sample
Assignment Brief
In business, good decision-making requires the effective use of information. You are hired by an organisation to examine how information systems support management decisions at different levels within organisations. You are also assigned to investigate the methods and techniques which relate to the design and development of IT solutions. Your research has been divided into different tasks. The findings from Tasks 1, 2, 3, 4 and 5 can be submitted in a portfolio format.
Introduction
Task 1: Theories, methods and techniques which relate to the design and development for TWO of the IT solutions listed here: (i) McAfee; (ii) Moodle; (iii) Canvas; (iv) MS Office
Task 2: Explanation of the systems below with relevant examples
Task 3: Globalisation and the effects of IT on globalisation
Task 4: Definition, example, advantages and disadvantages of digital infrastructure
Task 5: Risks associated with information systems outsourcing and why is IT infrastructure so critical to digital transformation!
Conclusion
References
Solution
Introduction
In this assignment, decision making procedures and effectiveness in information system execution and management. It includes different tools and models that are associated with different IT solutions or information system technology. It explains globalization and impact of IT in the development of the issue. Overall, different case studies or examples are evaluated to assess the impact into the organizational scenario. Moreover, this leads to better understanding and organizational infrastructure development.
This will lead the organizational stakeholders to better management system and organizational culture. On the other hand, risk assessment and other associated operations will help in better management planning and implementation for assignment help.
IT Solutions and Related Theories, Methods and Techniques
IT solutions are basically information system technologies or software that can be implemented effectively into different organizational requirements. This includes management systems, operational systems, etc. In this section of the assignment two IT solution software are considered to analyse. It consists different theories, methods and techniques that are associated with the project. The considered IT solutions are McAfee and Moodle.
McAfee
McAfee is a cloud computing technology-based company that develops antiviruses as their major business model. Moreover, the McAfee solution services can develop appropriate and effective antivirus encryption throughout the whole system lifecycle.
Related Theories
5 steps problem solving methodology will be most applicable and effective model of analysis for this IT solution implementation. The developer requires problem solving approach towards the system lifecycle and development. The system and the developer must identify particular areas that can be affected by cyber-attacks. This will also help in better decision making and strategic planning.
It includes five steps, where in the first phase, whole system is evaluated to define and list the problems. Then the business impact and effectiveness of the strategies will be assessed. It will lead to appropriate decision solution. The developers and project manager will be responsible for developing implementation strategy and procedure planning. This will be followed specifically for effective results. Finally, the results will be reviewed or the system will be tested in terms of effectiveness.
.png)
Image 1: 5 Steps Problem Solving Methodology
(Source: Humorthatworks, 2020)
Moodle
Moodle is a free learning IT solution or platform that operates learning management system with different courses, assignments, etc. An individual can create whole learning management structure to organize and implement learning modules and other resources. The tutor will also be able to observe student activities and progress accordingly. However, the system is effective and applicable in recent learning requirements.
Related Theories
Moodle is also associated with different framework or analysis model, that are beneficial in organizational operations and management. The business already includes a huge number of consumers and stakeholders. In that case business decisions become more significant and critical in nature. The most appropriate and effective theory, associated with Moodle will be rational decision-making model.
This is a visually structured model of project and business planning. It distributes the whole decision-making procedures into phases that can derive the most effective decision. It improves the implementation strategy and overall procedure. The process also shows different constraints and external project aspects. This will lead to better management and development.
.png)
Image 2: Rational Decision-Making Process
(Source: Biznewske, 2020)
Systems Explanation
Organizations use different information systems to operate business operations and management. In this section of the assignment , some of the systems are explained in terms of functionality and organizational uses. It shows appropriate application and impact in management and overall development.
Decision Support System (DSS)
Decision support system or DSS is an information system that provides determinations judgement and appropriate plan of action for a particular business project development (Fanti et al., 2015). It organizes and analyses a huge amount of system data and implementation strategy. There are majorly 5 types of decision support system (DSS) such as,
• Communication-driven DSS
• Data-driven DSS
• Document-driven DSS
• Knowledge-driven DSS
• Model-driven DSS
They are categorized in terms of application in different organizational requirements.
.png)
Image 3: Decision-Making Process within DSS
(Source: Indiafreenotes, 2020)
This will improve the decision-making procedures and effective implementation. Moreover, the process will develop efficient organizational culture such as flexibility.
Executive Support System (ESS)
Executive support systems are developed for the managers and higher authorities of the business that will help them to access and implement different business data. It includes both internal and external information such as management strategy.
.png)
Image 4: Executive Support Systems
(Source: Bolouereifidi, 2015)
Executive support systems provide effective IT solution for moderating all system data that can impact the whole business. It also includes the benefit of better data analysis and business management process.
Transaction Processing System (TPS)
Transaction processing system is an information system that provides the facility of collecting, evaluating and retrieving the data transactions into the business. It includes effective system response time while transaction and overall data management system as well.
.png)
Image 5: Transaction Processing System Benefits
(Source: Chegg, 2022)
The system has different business impacts such as better data integrity, performance, response time, etc. This can clearly establish the positive impact in business management and performance as well.
Management Information System (MIS)
Management information system presents the software that can operate, and manage all the business operation and management. It includes all the system stakeholders, supply chain and other functionalities. System database will store and manage all the data from the system operations and analysis.
.png)
Image 6: Management Information System Structure
(Source: Toppr, 2020)
Management information system improves management system and effectiveness into the business. Moreover, it improves different organizational cultures such as better communication and resource management.
Knowledge Management System (KMS)
Knowledge management system is also another type of information system or software that implements knowledge management principles into the organizational culture overall business procedure.
.png)
Image 7: Knowledge Management System
(Source: Kpsol, 2022)
Knowledge management system improves stakeholders’ engagement and communication. it helps the stakeholders to collect and evaluate essential business data quickly.
Globalization
Globalization is the procedure that explains trade and other exchange between different locations or nations around the world. It can establish the modern connectivity and relevant impact of communication systems.
It presents global trade and exchange around the world. It has different types and specification such as economic globalization, political globalization and cultural globalization. All of them present different globalization sectors around the world. Different internal and external business components effect this system or procedure, such as information technology.
Effects of IT in Globalization
Information technology has created new scopes and opportunities in communication systems and management. It has already created effortless system of exchanging data or information around the world. Information holds the most essential role in current business requirements or scenarios.
Information technology also improves productivity levels of the stakeholders into the organization. It implements advanced and emerging economies. Technology is the system that can reduce man power requirement and other resource supply as well. In that way, the organizational system and management become more effective and accurate.
Businesses have faced effective opportunity of reaching limitless audiences and consumers. the market reach is increased along with effective communication and marketing strategies. Visual media and social information networks have developed the system scopes of effective business implementation.
Digital Infrastructure
Digital infrastructure presents the system or resources connectivity. It includes both physical and virtual resources such as computers, data storge, network, SaaS, etc. this is essential for better and effective business process management. Project manager, finance manager, and other key organizational stakeholders are responsible to develop the digital infrastructure into an organization. Appropriate digital infrastructure will also lead to better market positioning and business growth.
In this section of the assignment, ‘cloud computing’ is considered as an example of digital infrastructure. Appropriate discussion and evaluation of the selected digital infrastructure will lead to better business procedure implementation of cloud computing technology to build effective digital infrastructure.
Overview
Cloud computing technology or system presents the digital storage and virtual processing of different organizational operations like information exchange. It includes different web-based services and hosted services. Most of the organizations are also implementing this new technology or system for better business development and management.
Image 8: Cloud Computing
(Source: Baird, 2019)
Advantages
Cloud computing is an essential digital infrastructure in any organization or business. It shows different advantages and disadvantages in organizational requirements. These are essential to evaluate for better business process management and effective decision making.
.png)
Table 1: Cloud Computing Advantages
(Source: Developed by Author)
Disadvantages
Organizational disadvantages must be discussed with appropriate evaluation. This will lead to effective business precautions and changes. It requires analytical thinking approach to evaluate these disadvantages. This may cause significant changes in system, requirement planning and designing as well.
.png)
Table 2: Cloud Computing Disadvantages
(Source: Developed by Author)
Risks Identification in Information System Outsourcing
Risk Identification is the procedure, where the potential risks are identified in a particular project development or business. In case of an information system development, the project manager is responsible to identify the potential risks into the development procedure and implementation strategy. This eventually leads to effective risk assessment and mitigation planning. This not only improves the project effectiveness but also improves the organizational culture and growth.
In most of the organizations, the information system is being outsourced by the management team. Sometimes, companies appoint and manage technical support team of developers to maintain the information system. In spite of that, it creates different project risks that can impact the overall business and information system development in a negative way. The identified risks in this case are,
• Inexperienced employees
• Data or information leak
• Dependency on the vendor
• Poor system control management
• Poor feedback management
These risks are mostly associated with different system functions and business operations. This is the responsibility of the project manager to evaluate all the identified risks in this particular project. This will eventually lead to an appropriate and effective risk-mitigation plan. This will be implemented by the business management team. Moreover, Different teams are associated with this whole risk identification and assessment process. They include. Data analysis team, database management team, etc.
Why is IT infrastructure so Critical to Digital Transformation?
IT infrastructure presents the overall development and implementation of software technology that can create appropriate IT infrastructure for effective business management procedure. It includes, cloud computing technology, security aspects, different equipment, etc.
On the other hand, digital transformation presents the transformation procedure of current business by adapting digital technology and information system (Ebert, & Duarte, 2018). It includes information management system and many other IT solutions. This is the responsibility of the supervisor to evaluate IT solution implementation into digital transformation.
Digital transformation mostly has different types in terms of transformation element and application such as,
• Process transformation
• Domain transformation
• Business framework transformation (Matt et al., 2015)
• Organizational culture transformation
Image 9: Digital Transformation
(Source: Peranzo, 2021)
IT infrastructure is critical and significant for the digital transformation. Every business requires effective IT infrastructure to implement digital transformation into the existing business structure (Reis et al., 2018). The development of any information management system, requires appropriate infrastructure that includes, efficient systems, development team, system management team, etc. Moreover, it consists different framework or analysis that are associated with the IT solutions, such as visual learning. In that way, IT infrastructure plays a significant role in digital transformation in any business or organization.
An infrastructure not only develops but also maintains a particular system. in this case of IT or information technology, the business also requires some additional features to maintain the implemented IT infrastructure. It includes data analysis team, database management team, technical support team, etc. (Berger, 2015). In this way, the IT solution implementation will be effective in long run. This will impact the digital transformation procedure as well. for example, after the system development, the first responsibility of the project manager will be to develop appropriate system policies (Baiyere et al., 2020). This will impact organizational culture and overall business system management in a positive way. This can clearly establish the significant impact of IT in digital transformation.
Conclusion
In this assignment , IT or information system technology is explained through different system types and organizational implementation. On the other hand, it discusses particular digital infrastructure, cloud computing. It includes advantages and disadvantages that can lead to appropriate evaluation into the organizational process.
The risk assessment and of IT in digital transformation, have established clear idea on information technology and real-life application. This will lead to better risk assessment strategy and impact. The business management will be able to prepare appropriate mitigation plan as well. Finally, the impact of IT or information technology is discussed into the last phase of the report. It has established the effective requirement of IT in digital transformation.
Overall, the assignment concludes, that information technology systems are effective in business management and overall management system improvement. It requires effective management and critical thinking approach to adopt this methodology or system.
References
.png)
COIT20262 Advanced Network Security Assignment Sample
Instructions
Attempt all questions.
This is an individual assignment, and it is expected students answer the questions themselves. Discussion of approaches to solving questions is allowed (and encouraged), however each student should develop and write-up their own answers. See CQUniversity resources on Referencing and Plagiarism. Guidelines for this assignment include:
• Do not exchange files (reports, captures, diagrams) with other students.
• Complete tasks with virtnet yourself – do not use results from another student.
• Draw your own diagrams. Do not use diagrams from other sources (Internet, textbooks) or from other students.
• Write your own explanations. In some cases, students may arrive at the same numerical answer; however their explanation of the answer should always be their own.
• do not copy text from websites or textbooks. During research you should read and understand what others have written, and then write in your own words.
• Perform the tasks using the correct values listed in the question and using the correct file names.
File Names and Parameters Where you see [StudentID] in the text, replace it with your actual student ID. If your student ID contains a letter (e.g. “s1234567”), make sure the letter is in lowercase.
Where you see [FirstName] in the text, replace it with your actual first name. If you do not have a first name, then use your last name. Do NOT include any spaces or other non-alphabetical characters (e.g. “-“).
Submission
Submit two files on Moodle only:
1. The report, based on the answer template, called [StudentID]-report.docx.
2. Submit the packet capture [StudentID]-https.pcap on Moodle Marking Scheme
A separate spreadsheet lists the detailed marking criteria. Virtnet Questions 1 and 3 require you to use virtnet topology 5. The questions are related, so you must use the same nodes for all three questions.
• node1: client; assumed to be external from the perspective of the firewall.
• node2: router; gateway between the internal network and external network. Also runs the firewall.
• node3: server; assumed to be internal from the perspective of the firewall. Runs a web server with HTTPS and a SSH server for external users (e.g. on node1) to login to. Will contain accounts for multiple users.
Question 1. HTTPS and Certificates [10]
For this question you must use virtnet (as used in the Tutorials) to study HTTPS and certificates. This assumes you have already setup and are familiar with virtnet. See Moodle and workshop instructions for information on setting up and using virtnet, deploying the website, and testing the website.
Your task is to setup a web server that supports HTTPS. The tasks and sub-questions are grouped into multiple phases.
Phase 1: Setup
1. Ensure your MyUni grading system, including new student user and domain of are setup. See the instructions in Assignment 1. You can continue to use the setup from
Assignment 1.
Phase 2: Certificate Creation
1. Using [StudentID]-keypair.pem from Assignment 1, create a
Certificate Signing Request called [StudentID]-csr.pem. The CSR must contain thesefield values:
o State: state of your campus
o Locality: city of your campus
o Organisation Name: your full name
o Common Name: www.[StudentID].edu
o Email address: your @cqumail address
o Other field values must be selected appropriately.
2. Now you will change role to be a CA. A different public/private key pair has been created for your CA as [StudentID]-ca-keypair.pem. As the CA you must:
3. Setup the files/directories for a demoCA
4. Create a self-signed certificate for the CA called [StudentID]-ca-cert.pem.
5. Using the CSR from step 1 issue a certificate for www.[StudentID].edu called [StudentID]-cert.pem.
Question 2. Attack Detection from Real Intrusion Dataset
For this question you need to implement three meta-classifiers to identify attack and normal behaviour from the UNSW-NB15 intrusion dataset. You are required to read the data from training set (175,341records) and test set (82,332 records).
You are required to implement it by using the publicly available machine learning software WEKA. For this task you will need two files available on Moodle:
• training.arff and test.arff.
You need to perform the following steps:
• Import training data.
• For each classifier:
- Select an appropriate classifier
- Specify test option
- Supply test data set
- Evaluate the classifier.
You need to repeat for at least 3 classifiers, and eventually select the results from the best 2 classifiers.
You need to include in your report the following:
(a) Screenshot of the performance details for 3 classifiers [1.5 marks]
(b) Compare the results of the selected best 2 classifiers, evaluating with the metrics:Accuracy, precision, recall, F1-Score and false positive rate.
Question 3. Firewalls and iptables [8]
You are tasked with designing a network upgrade for an educational institute which has a single router, referred to as the gateway router, connecting its internal network to the Internet. The institute has the public address range 100.50.0.0/17 and the gateway router has address 100.50.170.1 on its external interface (referred to as interface ifext). The internal network consists of four subnets:
A DMZ, which is attached to interface ifdmz of the gateway router and uses address range 100.50.171.0/25.
• A small network, referred to as shared, with interface ifint of the gateway router connected to three other routers, referred to as staff_router, student_router, and research_router. This network has no hosts attached (only four routers) and uses network address 10.5.0.0/18.
• A staff subnet, which is for use by staff members only, that is attached to the staff_router router and uses network address 10.5.1.0/23.
• A student subnet, which is for use by students only, that is attached to the student_router router and uses network address 10.5.2.0/23.
• A research subnet, which is for use by research staff, that is attached to the research_router router and uses network address 10.5.3.0/23.
Question 4. Wireless security [10]
Read the research article on Wi-Fi Security Analysis (2021) from the below link:
![]()
You need to perform the following tasks:
(a) Write an interesting, engaging, and informative summary of the provided article. You must use your own words and you should highlight aspects of the article you think are particularly interesting. It is important that you simplify it into common, easily understood language. Your summary MUST NOT exceed 400 words. [3 marks]
(b) Find an Internet (online) resource (e.g., research article or link) that provides additional information and/or a different perspective on the central theme of the article you summarised in (a). Like you did in (a), summarise the resource, in your own words and the summary should focus on highlighting how the resource you selected expands upon and adds to the original prescribed resource. You must also provide a full Harvard reference to the resource. This includes a URL and access date. [4 marks]
(c) Reflect on the concepts and topics discussed in the prescribed article and the resource you found and summarised and how you think they could potentially impact us in future.
Solution
Question 1- HTTPS and Certificates
HTTPS is the shorter format of Hyper Text Transfer Protocol Secure. HTTPS appears in the Uniform Resource Locator when the SSL certification barricades the website. The overall details of the credential and the website proprietor's corporate standing can be considered by clicking on the specific safety symbol on the browser streak.
Part (a)
The ala data of the student's Id and the user's details are added with the help of the MyUni system (Aas et al. 2019). Follow the basic information of Assignment 1. The setup is being processed in that way.
Part (b)
Certificate creation follows an essential process where one must send a signing request to the Certificate Authority.
1. Run the necessary Command to can make a certificate signing request (CSR) file: openssl.exe req-new-key certaname. Key-out certname. CSR.
2. The promotion time is needed information like the common name, Tableau Server name, etc.
The use of HTTPS with the specific Domain name requires an SSL certificate, which has to be installed on the website.
.png)
Figure 1: Kali Linux cmd server
(Source: Created on Kali Linux)
.png)
Figure 2: Creating CSR
(Source: Created on Kali Linux)
In this figure, a key pair file is used to construct a Certificate Signing Request (CSR). Specific field values seen in the CSR include email address, organization name, common name, state, and locale. The CSR is created with the name [StudentID]-csr.pem with the intention of getting a certificate for the student website.
.png)
Figure 3: Details of Certificate
(Source: Created on Kali Linux)
Part (c)
Write your answer here
The HTTPS on Apache is followed in several steps.
- Discover the Apache format file and unlock it with the text editor. The name of the Apache Configuration File has to depend on the system outlet.
- Demonstrate the Apache SSL structure file and save it. Open the Apache SSL layout file.
- Restart the Apache Web Server in the Linux OS System.
Part (d)
The testing process of the HTTPS certificate is done in basic simple steps. These are 1. First of all, check the Uniform Resource Locator of the specified website starting with HTTPS, where the SSL certificate has been created.2. Tab on the Padlock icon on the valuable address bar to can check all the specific details and information which is related to the Certificate.
Part (e)
The SSL is known as the Secure Sockets Layer. The SSL is a basic protocol that has the ability to can create an encipher link between the Web browser and Web Server (Gerhardt et al. 2023). Any data that can be swapped between a website and a specific visitor will be protected. Holding an SSL certificate for the WordPress website is a must for running an Ecommerce Store.
Question-2
Attack Detection from Real Intrusion Dataset
Part (a)
Training.arff
Classifier 1
Figure 1: Run Information of Rules Classifier 1
Figure 2: Rules Classifier in Test Model
Figure 3: Summary of Rules Classifier
Figure 4: Accuracy of Rules Classifier
Figure 5: Confusion Matrix of Rules Classifier
Classifier 2
Figure 6: Run Information of Bayes Classifier 2
Figure 7: Classification Model in Bayes Classifier
Figure 8: Evaluation Test and Summary of Rules Classifier
Figure 9: Accuracy of the Rules Classifier
Figure 10: Confusion Matrix in Rules Classifier
Classifier 3
Figure 11: Run Information of Trees Classifier 3
Figure 12: Classification Model in Trees Classifier
.png)
Figure 13: Summary of Trees Classifier
.png)
Figure 14: Accuracy of the Trees Classifier
.png)
Figure 15: Confusion Matrix of Trees classifier
Test.arff
Classifier 1
.png)
Figure 16: Run Information Test of Rules Classifier 1
.png)
Figure 17: Test Model in Rules Classifier
.png)
Figure 18: Summary Test of Rules Classifier
.png)
Figure 19: Accuracy of the Rules Classifier
Figure 20: Confusion Matrix of Rules Classifier
Classifier 2
.png)
Figure 21: Run Information of Bayes Classifier 2
.png)
Figure 22: Test model of Bayes Classifier
.png)
Figure 23: Build Model in Test.arff Bayes Classifier
.png)
Figure 24: Accuracy of Bayes Classifier
.png)
Figure 25: Confusion Matrix of Bayes Classifier
Classifier 3
.png)
Figure 26: Run Information of the Trees classifier 3
.png)
Figure 27: Classification Model in Trees
.png)
Figure 28: Summary of the Tress Classifier
.png)
Figure 29: Accuracy of the Trees Classifier
.png)
Figure 30: Confusion Matrix of Trees Classifier
Part (b)
Test.arff
The run information of Classification 1 is needed a shorter type scheme and very long attributes, but Classification 2 is specified a different scheme. The accuracy of classification 1 is presented in a more elaborate way but in the case of classification 2, there is a little much short about the accuracy. The F1 score and the false positive rate are better in Classification 2 than the Classification 1 (Ahmad et al. 2022).
Train.arff
The run information of the Classification 1 is very detailed in the primary part but the portion of Classification 2 is not specified in a proper way. The accuracy is less in classification 1 in the Train.arff but classification 2 is more accurate from the matrix perspective. The F1 score in the machine learning process is more specified in Classification 2 than in Classification 1 in the Train.arff (Alduailij et al. 2022).
Part (c)
Based on the specific comparison between classification1 and Classification 2, Classification 2 is better than Classification 1 because the scheme is more evaluated in Classification 2. The accuracy in Classification 1 is little much less appropriate than in Classification 1. The F1 score and the false positive rate are always better in Classification 2 than in Classification 1 of the bother test.arff and train.arff (Ceragioli et al. 2022).
Part (d)
The UNSW-NB15 is a process of the network Instruction sheets. It basically contains nine types of different attacks. The whole dataset contains ideal network packets. The number of possible records in the training set is primarily 175,341. Records. Of these nine attacks, the normal and the Generic are the most powerful. Because the training set and testing are best in these two category.
Question 3- Firewalls
Part (a)
Wireless networks utilize radio swells to transfer data into machines, similar to laptops, smartphones, and tablets, or entry points, that have attached to the “Wired Network”. “Wired Networks” utilize cables, similar to Ethernet, to secure machines, similar to routers, buttons, and wait people, to individually different or to the internet. The “Virtual Private Network” has an encrypted association up the Internet from the device to the web. The encrypted association supports guarantees that exposed data has been safely transferred. This precludes unauthorized somebody from eavesdropping on the gridlock or permits the user to execute a career remotely.
.png)
Figure 34: Diagram of wired Network
(Source: Created on Draw.io)
The network diagram in the example would show a wired network, a wireless network, and a VPN. One to three devices each would be used to represent the staff, student, and research subnets. The IP addresses of each machine and router interface would be noted. The areas of the network where data is encrypted, either by WIFI encryption or the VPN, would be prominently marked on the diagram as encrypted using red or similar easily recognizable label.
Part (b)
The firewall rules have the entry authority mechanism utilized by a firewall to protect the network from the contaminated application or unauthorized entrance. Fire3wall rules determine the variety of gridlock the firewall takes or that have rejected. The exhibition of the firewall rules creates the firewall entrance procedure. The firewall has network security that maintains getaway unauthorized users or hackers. Virtual software support saving files from viruses. Firewall support to maintain intruders by obstructing them from accessing the system in the rather residence. The firewall has a technique planned to control undesirable data from reaching and leaving the personal network. The learner will utilize either hardware or software to execute the firewall or an assortment of the two. In the company environment, or association can have an intranet that they save utilizing the network.
Part (c)
The Rules of the tables are primarily:
- Flare the concluding app or log in with the use of the sash command: $ sash user @server- name.
- List all of the IPv4 rules: $ sudo iptables -S.
- Find the valuable list of all IPv6tables -S.
- List all the special section table rules: $ sudo ip6tables -L -v -n | more.
- Lat List all the rules for the specified INPUT tables.
To add some new rule as the special section of the existing rule, merely use the index numeral of that current rule (Ruzomberka et al. 2023).
Figure 34: Network of educational institute
(Source: Created on Cisco)
The gateway router that connects the internal network to the Internet makes up the network architecture of the educational institution. The gateway router's external interface has the address 100.50.170.1, and the institute's public address range is “100.50.0.0/17”. A shared network with four routers, a DMZ subnet linked to the gateway router, a staff subnet is 10.5.1.0/23, a student subnet (10.5.2.0/23), and a research staff subnet (10.5.3.0/23) connected to their respective routers are all included in the internal network.
.png)
Figure 35: Server Configuration
(Source: Created on Cisco)
A web server that supports “HTTP” and “HTTPS”, an “SMTP” email server, and an SSH server would be included in the server setup for the educational institution's DMZ using Cisco Packet Tracer. On the gateway router, access control lists (ACLs) would be set up to permit access from the staff, student, and research subnets to the web server, staff members exclusively to the IMAP email server, and staff and research members to the SSH server from outside the network.
.png)
Figure 36: DHCP Server
(Source: Created on Cisco)
Question- 4- Wireless security
Part (a)
Advanced network security is the set of valuable technologies that have the ability to can protect the whole usability and also the goodness of the company’s framework by the process of containing the entry or the accumulation within the web of the wide range of variety of possible threats. The Hypertext Protocol Secure is a specific kind of combination of the HTTP with the Secure Socket Layer (SSL) or the Transport Layer Security which is the longer format of TLS. The TLS is an authentication and also security system that is widely connected in Web browsers and Web servers. The second portion is made on the Instruction detection system.
An instruction on the Detection of suspicious activities generates the alert when the detected system has been proceeding. Connected to the specific process of a security operation Center, the longer format of the SOC or incident responder has the capability to investigate the obstacles and also take proper actions to remediate the threat. The real instruction Database includes the classification matrix and classification them in a proper manner. The process is described on the VMware Kali Linux. The tables which are in the third section allow the specific system administrator to define the actual table and draw the diagram which can illustrate the wired network and also the firewall rules mentioned here.
Part (b)
Wireless Network Security is the stage for patterns or instruments utilized to watch WLAN infrastructure or the gridlock crosses them. Extensively communicating, wireless security of articulates that endpoints have or exist allowed on the Wi-Fi network via network entrance or security policies. Resource Allocation has given time, distance, and Commonness environment in the scope established on the technique that categorized CDMA, TDMA, SDMA, and FDMA.
Part (c)
This essential security significant to details on the internet has confidentiality, integrity, or availability. Ideas connecting to the somebody who utilized the statement have authentication, permission, or nonrepudiation. Wireless security has the precluding of unauthorized entrance and impairment to computer data utilizing wireless networks that process Wi-Fi networks. The duration can again guide to confidentiality, integrity, and availability of the web.
INFS5023 Information Systems for Business Assignment 2 Sample
OBJECTIVE
The objective of Part B of the assignment is to produce a written report addressing the question of how enterprises in the industry segment are using information and communication technologies (ICTs) to support business strategies, to seek competitive advantage (CA) or sustainable competitive advantage (SCA) and to identify opportunities for further use of these technologies by businesses in this industry segment to change or improve their businesses, or to gain CA and which of the strategies might be sustainable.
REQUIREMENT
Each group is required to:
Prepare and submit a written report on the group’s investigation to Learnonline. See below for details of the report requirements.
The report will have an executive summary.
An executive summary is a summary of a report made so that readers can rapidly become acquainted with a large body of material without having to read it all. It will usually contain a brief statement of the background information, concise analysis and main conclusions. The executive summary will be on a separate page directly before the main report and should be around half a page in length. The executive summary is in addition to the ten pages (maximum) of the main report. The report will have a title page and a contents page.
The report questions
The main written report will address the following questions/issues:
5. This part of your investigation focuses on business responses to the major forces identified in 4. (i.e. how they compete). Identify a range of the strategies that businesses have adopted to provide them with competitive advantage (CA) and which of these are sustainable competitive advantages (SCA) in response to these forces.
Your analysis should also consider issues such as cost leadership, innovation, differentiation, niche market and other strategies.
6. This part focuses on the internal arrangements within the individual businesses you have investigated — how they organise their businesses to implement their business strategies. Use Porter’s Value Chain Analysis Model to analyse organisations in the industry. The aim here is to explain how different businesses organise their processes to achieve their organisational objectives. You should choose to concentrate on at least two contrasting organisations in your segment to illustrate competitive responses. Justify your choice.
As this question requires some knowledge of internal processes, you may find it difficult to obtain specific information. Use whatever information is available to you to address this question as best you can.
7. Use Business Process Approach/ Model to identify how businesses in your industry segment are categorised as internal and external processes and how they enhance the organisation’s efficiency and effectiveness.
10. Explore the Internet and other sources to identify new and “trending” information and communication technologies, systems and applications that are becoming available or that will soon be available to businesses in this industry to assist them to gain a CA or SCA. Describe these new technologies, systems and applications..
11. Explain how the new information and communication technologies, systems, and applications identified in #10 above might be used to create a CA or SCA.
Your explanation should be in terms of some or all of the following:
effects on existing business models,
creating new business models,
supporting existing strategies,
creating new business strategies,
specific additions to a portfolio of information systems
improving the ability to compete in terms of the five forces analysis,
improving/creating new processes in terms of the value chain analysis,
improving customer relations.
12. How might these ICTs or applications create a competitive disadvantage?
13 Provide a critique of two of the analysis tools you have used. Evaluate how effective they are for exploring competitive advantage in the industry. Use a separate section with headings in your report for each analysis tool. Provide a supporting argument for your criticisms.
You are required to comment on how well they fulfil the purpose for which they were designed, not to just point to areas for which they were not designed.
Solution
Question no. 5
In response to the competitive forces in the milk segment of the dairy industry, businesses have adopted various strategies to attain a competitive advantage (CA) and sustainable competitive advantage (SCA). For Assignment Help -
1. Cost Leadership
Competitive Advantage (CA): Some companies seek to offer milk products at lower prices than their competitors to achieve economies of scale and operational efficiency (Kimiti, 2020). This can be a source of attraction for price-sensitive consumers.
Sustainable Competitive Advantage (SCA): If companies continue to invest in current technology, effective supply chain management, and maintain a robust cost control system, it may be possible to sustain the leadership of costs.
2. Product Differentiation
CA: Companies such as Nestle and Amul, aiming to create a distinct market presence and appeal to specific consumer segments, emphasize the different product characteristics of lactose-free or fortified milk.
SCA: Sustainable if the company continues to invest in research and development, introducing innovative milk products that meet changing consumer preferences and needs (Guiné et al., 2020).
3. Niche Market Focus
CA: Some companies are focused on particular niche markets, for example, organic or unique milk products that cater to a narrower but devoted customer base which will pay an additional premium in order to offer specialized services.
SCA: Sustainable if the company effectively meets the unique needs of the niche market and establishes strong brand loyalty within that segment.
4. Innovation and New Product Development
CA: Businesses invest in research and development to introduce novel dairy products or production methods, staying ahead of market trends and offering products that competitors do not.
SCA: Sustainable if the company maintains a culture of innovation, continually introduces successful new products, and adapts to changing consumer preferences.
5. Vertical Integration
CA: Vertical integration is a feature of companies like Amul, who own both dairy farms and processing facilities. This results in complete supply chain control, ensuring quality and cost advantages.
SCA: Sustainable if the company effectively manages and optimizes the integrated operations, achieving consistent quality and cost advantages over the long term.
6. Brand Equity and Recognition
CA: With solid brand recognition and consumer confidence, established brands such as Amul and Nestle can gain consumers' loyalty and market presence (Pandey et al., 2021).
SCA: Sustainable as long as the company maintains its brand reputation through consistent quality, marketing efforts, and customer satisfaction.
Question no. 6
The Porter value chain analysis model gives an overview of the internal activities that support a company's competitiveness. In the industry of dairy, firms like Amul, Nestle, and Saputo implement their business-related strategies through distinctive arrangements of value chains.
Amul
Amul, an Indian cooperative dairy firm, has a distinct value chain structure firmly ingrained in its collaborative concept (Pandey and Sahay, 2022). The joint venture includes millions of smaller milk manufacturers who share and control the company. In addition, these partnerships assist the Amul in getting the milk from the farmers directly and also ensure a steady supply of very high-quality raw materials.
Inbound Logistics: The tender procedure of Amul is exceptionally significant. They set up networks of collection points in remote areas, intending to ensure the availability of milk at a timely manner.
Operations: Amul maintains several processing factories around India. These facilities are focused on product diversification, with products ranging from milk to cheese, butter, yoghurt, and ice cream (JACKSON and JAYAPRAKASH, 2023). The cooperative concept promotes the ongoing advancement of processing technologies and procedures.
Outbound Logistics: Amul has a substantial distribution network, ensuring that its products efficiently extend urban and rural markets. However, this broad distribution extension permits them to cater towards a diverse base of customers.
Marketing and Sales: Amul is well-known for its aggressive marketing activities and has established a significant brand presence in India (Bapat, 2020). Their advertising frequently emphasises their goods' outstanding quality, low cost, and nutritious benefits.
Service: Amul places significant emphasis on customer satisfaction. They have established a robust customer service network that effectively handles inquiries, feedback, and complaints.
.png)
Figure 1: Value chain analysis model
(Source: Bruin, 2021)
Saputo
Compared to Amul, Saputo is a Canadian dairy corporation with a more centralised model. They have a global footprint with activities in many countries.
Inbound Logistics: Saputo's inbound logistics focus on procuring milk from various sources, including farms and external suppliers (Fernandes, 2021). They have established strong relationships with farmers and utilise advanced technology for milk collection.
Operations: Saputo maintains cutting-edge processing facilities outfitted with advanced technologies. In their manufacturing operations, they premium efficiency and quality control.
Outbound Logistics: Saputo has a well-organized logistics network for distributing dairy products across diverse markets. They leverage economies of scale to optimise distribution costs.
Marketing and Sales: Saputo employs a market-driven approach, tailoring their products to meet local preferences. They also engage in strategic acquisitions to expand their product portfolio and market reach.
Service: Saputo emphasises after-sales service by actively seeking customer feedback and adapting their products accordingly (Bonesteve, 2021).
Justification
A meaningful comparison in value chain strategies is provided with the analysis of Amul and Saputo. Amul's Cooperative Model also highlights the benefits of the centralised approach, and Saputo's worldwide operations show the importance of decentralised supply chains. The examination is intended to provide a detailed understanding of how different organisations organise processes to meet their objectives within the dairy sector.
Question no. 7
In the Dairy industry, businesses like Amul, Saputo, and Nestle utilise a Business Process Approach to enhance their efficiency and effectiveness through internal and external processes.
Internal Processes
Production and Processing: Amul, with over 70 processing plants in India, processes a staggering 38 million litres of milk daily (Singh, 2023). This internal operation transforms raw milk into a diverse range of dairy products.
Saputo operates 60+ manufacturing facilities globally, producing millions of pounds of dairy products yearly.
Quality Control: These companies implement rigorous quality control measures. For instance, Nestle conducts over 700,000 quality tests annually on their dairy products.
Product Development and Innovation: Amul and Nestle invest significantly in research and development. Amul's dedicated R&D centre and Nestle's global research network drive innovation and product diversification.
.png)
Figure 2: Business model of Amul
(Source: Ernie, 2019)
External Processes
Supply Chain Management: Amul's extensive network includes millions of farmers, ensuring a constant raw milk supply. Saputo balances procurement from owned farms and external sources, maintaining a flexible supply chain.
Distribution and Logistics: Amul's distribution network reaches over 3 million retail outlets in India. Saputo employs advanced logistics technology to distribute products globally (Gulati and Juneja, 2023).
Supplier Relationships: Amul's cooperative model establishes a direct and mutually beneficial connection with farmers. Nestle collaborates with a vast network of suppliers globally, ensuring a reliable supply of raw materials.
Efficiency and Effectiveness
Amul's cooperative approach reduces intermediate expenses, resulting in more cost-effective purchasing and a stronger position as India's largest dairy cooperative.
Saputo's global network and superior processing methods result in economies of scale, making it one of the world's top dairy processors.
Nestle's emphasis on innovation and product variety has enabled the company to create a significant position in the global dairy industry, boosting its overall efficacy (Kalyani and Shukla, 2022).
Question no. 10
In the dairy industry, several emerging technologies are poised to revolutionize operations and offer opportunities for competitive advantage (CA) and sustainable competitive advantage (SCA). Some significant trends are the following:
1. Internet of Things (IoT) in Dairy Farming: The Internet of Things refers to the incorporation of sensors and devices into dairy farms to monitor the health, behavioUr, and milk output of cows.
2. Block chain Technology for Traceability: The traceability of dairy products from farm to table is ensured through block chain technology (Khanna et al., 2022). Providing real-time information on the provenance and quality of dairy products will help to increase transparency and build consumer confidence.
3. Artificial Intelligence (AI) and Machine Learning for Data Analysis: In the dairy industry, AI and machine learning algorithms are used to analyze enormous data sets. They consider several facets of the dairy industry, including as milk quality, yield prediction, and resource allocation. It allows for data-driven decisions, which leads to improved product quality, resource management, and cost effectiveness.
4. Precision Agriculture for Feed Production: Precision agriculture makes use of data and technology to enhance dairy cow feed output (Monteiro, Santos and Gonçalves, 2021).
This technology has the potential to offer significant competitive advantages for enterprises like Amul, Saputo, or Nestle in the dairy sector. These companies may improve their efficiency, product quality, and sustainability through the use of these technologies within their operations to deliver both competitive advantage and long-term competitiveness.
.png)
Figure 3: Internet of Things (IoT) in Dairy Farming
(Source: Libelium, 2022)
Question no. 11
The identified information and communication technologies (ICTs) in the dairy industry can significantly impact a company's competitive advantage (CA) and sustainable competitive advantage (SCA) through various avenues:
1. Effects on Existing Business Models: ICTs like Block chain and IoT can transform existing business models by enhancing transparency and traceability. For example, Block chain can enable real-time tracking of dairy products, providing consumers with detailed information about their origin and quality (Casino et al., 2021).
2. Creating New Business Models: Robotic milking systems represent a potential shift in the dairy industry's business model. Automating milking processes increases efficiency and introduces a new paradigm in dairy farming, potentially leading to more sustainable practices.
3. Supporting Existing Strategies: AI and Machine Learning can augment existing data analysis strategies. For instance, they can optimize production schedules based on predictive analytics, aligning with cost leadership or efficiency strategies that companies may already have.
4. Creating New Business Strategies: Precision agriculture presents a new approach to feed production. This can lead to strategies focused on sustainable and efficient resource allocation, potentially reducing costs and enhancing product quality.
5. Specific Additions to Information Systems Portfolio: Implementing Blockchain and IoT systems require a specific addition to a company's information systems portfolio (Viriyasitavat et al., 2019). These technologies facilitate data collection, storage, and analysis, ensuring traceability and real-time monitoring.
6. Improving Ability to Compete (Five Forces Analysis): ICTs bolster a company's ability to compete in the five forces analysis. For instance, Block chain and IoT mitigate the threat of new entrants by establishing high barriers to entry through advanced technology adoption.
By incorporating these emerging information and communication technologies into their operation, dairy businesses can not only improve their efficiency but also distinguish themselves from the market to achieve a competitive advantage and a potential sustainable competitive advantage.
Question no. 12
Information and Communication Technologies (ICTs) and applications can potentially create a competitive disadvantage for businesses in the dairy industry if not implemented or managed effectively. In some cases, information and communication technologies may give rise to disadvantages:
1. Inadequate Data Security: If a dairy company fails to implement robust cybersecurity measures for its ICT systems, it becomes vulnerable to data breaches and cyberattacks. This may put at risk valuable confidential information, undermine customers' trust and have a significant economic and reputational impact.
2. Obsolete Technology: If the dairy business is not kept on top of technological developments, it will have a competitive disadvantage. Unupdated systems may result in inefficiencies, slow processes and an inability to satisfy customers' expectations of convenience and speed.
3. Poor Integration of Systems: ICT systems not seamlessly integrated across various departments and functions can result in data silos and inefficient workflows (Das, Gupta and Pal, 2023). This could lead to delays in decisions, reduced mobility and a lack of coherent customer experience.
4. Lack of Employee Training and Adoption: Productivity can be reduced, and available technology would be underutilised if employees do not receive adequate training on the practical application of ICT tools. This could lead to a lack of opportunities for automated processes, process optimisation and data-driven decision-making.
5. High Implementation and Maintenance Costs: Poorly planned or executed ICT projects can lead to budget overruns, tying up financial resources that could be better allocated elsewhere (Welde and Klakegg, 2022). It may result in financial strain, limiting the company's capacity to invest in others of its business.
Question no. 13
Critique of Porter’s Value Chain Analysis Model
Effectiveness for Exploring Competitive Advantage: Porter's Value Chain Analysis is an important tool to examine the internal business of a business to understand how different activities add value to its products and services (Dubey et al., 2020). It also gives information on the cost drivers and differentiators important to achieve a competitive advantage.
Strengths
Comprehensive Assessment: The model gives a formal framework for examining a company's core and support operations. This all-encompassing approach creates a clear grasp of how diverse functions contribute to the value-creation process.
Clear differentiation: It distinguishes between main activities and support activities. This distinction aids in identifying areas where a firm may have a competitive advantage or face obstacles.
Criticism
Static nature: Porter's approach is based on a static view of operations. Industries are continually changing due to technical advances, market developments, and shifting customer tastes. This approach may not represent dynamic changes in the industry landscape efficiently.
Limited Focus on External Factors: It generally focuses on internal procedures and may not sufficiently address external issues such as market developments, regulatory changes, or geopolitical effects. External variables can have a considerable influence on a company's competitive standing.
Critique of Business Process Approach/Model
Effectiveness for Exploring Competitive Advantage: The Business Process Approach takes a comprehensive look at a company's operations, focusing on the interaction of internal and external processes (Harmon, 2019). It helps find areas for efficiency and effectiveness improvement.
Strengths
Dynamic and adaptable: This strategy recognises the changing nature of industries and enterprises. It understands the necessity for processes to develop to meet shifting market needs and technology improvements.
Internal and external Process Integration: It successfully emphasises the relevance of both internal operations and exterior interactions (such as supply chain management and customer engagement) in gaining a competitive edge.
Criticism
Implementation Complexity: Implementing and administering a Business Process Approach may be time-consuming and difficult, especially for big firms (Fischer et al., 2020). It necessitates a thorough awareness of the entire value chain and practical cooperation between departments.
Data-Intensive Characteristics: This method is based on data-driven insights. Companies may struggle to obtain appropriate data or lack the requisite data management tools to effectively apply this method for competitive advantage.
References
.png)
ICTCYS608 Perform cyber security risk Assignment 1 Sample
Assessment information
Information about how you should complete this assessment can be found in Appendix
A of the IT Works Student User Guide. Refer to the appendix for information on:
- Where this task should be completed
- The maximum time allowed for completing this assessment task
- Whether or not this task is open-book.
Note: You must complete and submit an assessment cover sheet with your work. A template is provided in Appendix C of the Student User Guide. However, if your RTO has provided you with an assessment cover sheet, please ensure that you use that.
Questions
Provide answers to all of the questions below:
1. Explain why it is important for an organisation to conduct a cyber security risk assessment.
2. List typical steps that would be followed to conduct and report on a cyber security risk assessment.
3. List three ways that could be used to measure risk culture and risk appetite in relation to cyber security.
4. Identify two sources of information that that could be used to find out about cyber security legislation.
Solution
1. Importance of Conducting a Cyber Security Risk Assessment for an Organization
Cyber security risk assessment identifies and assesses the probability and severity of potential threats to an organization's information assets (Ganin et al. 2020). It is a critical part of a comprehensive security program, as it allows organizations to anticipate and plan for possible risks and to develop appropriate countermeasures. Risk assessments provide the foundation for an effective security strategy by helping organizations identify, assess and reduce their vulnerabilities. Cyber security risk assessments allow organizations to understand the risk level, the potential consequences of an attack and the necessary steps to mitigate the threat. Organizations can ensure they adequately protect their digital assets and minimize risk exposure by regularly conducting cyber security risk assessments.
Organizations need to conduct a cyber security risk assessment because it enables them to identify vulnerabilities within their systems and provides them with a comprehensive picture of the threats posed by cybercriminals (Fraser, Quail, & Simkins, 2021). By conducting a risk assessment, organizations can understand their current cyber security posture and identify areas where they may need to invest in additional measures. It also helps organizations to identify and respond to potential cyber threats, allowing them to remain one step ahead of the hackers. Furthermore, it provides a framework for developing and implementing effective policies and procedures for mitigating risks associated with cyber security threats. This helps organizations protect their valuable data, networks, and systems from malicious actors. Any organization's cyber security risk assessment is essential to protect its sensitive data, networks, and systems.
2. The procedures for Performing and Documenting a Cyber Security Risk Evaluation
The process of finding, analyzing, and evaluating risk concerning cyber security is carried out step by step. Choosing cyber security measures compatible with the risks one encounter is always beneficial. Choosing the best cyber security without the risk assessment method would be a waste of time, effort, and resources. Information assets that a cyber-attack might impact are always identified in a cyber security risk evaluation. Typically, a risk calculation and analysis are done, and then controls are chosen to address the risks that have been found.
Determining the area of responsibility of the risk assessment: The risk assessment process for the assignment help always begins with choosing the assessment's scope (Pukala, Sira, & Vavrek, 2018). It is typically a significant and difficult procedure. Additionally, it is crucial to have the full backing of all parties whose actions fall under the purview of the assessment because understanding will depend on their contributions.
Identifying the risks - The second step in the risk assessment procedure is to identify the risks. There are three sections again in this place. It must first determine the properties. The next step is to determine the threats. Threats can be tactics, techniques, or even ways. The final step is to determine which portion of the risk is incorrect.
Analyzing the risks - The third stage is to correctly analyze the risks and determine the potential effects of the threats after they have been identified. The risk potential and possibility always provide a danger that is capable of leveraging a weakness in a cybersecurity risk assessment process (Eckhart, Brenner, Ekelhart, & Weippl, 2019).
Determining and prioritizing risks - Identifying and prioritizing the risks is the fourth stage in cyber security risk assessment. It might be accomplished using a risk grid. Eliminating a task might be the optimal course for proceeding if it means not being exposed to it if the risk exceeds the benefits.
Documentation of all risks - It is crucial to record all risks related to cyber security after analysis and determination. For management to remain informed of the risks associated with cybersecurity, it must also be reviewed and updated.
3. Three Ways That Could Be Used to Measure Risk Culture and Risk Appetite Concerning Cyber Security
When assessing the risk culture and risk appetite concerning cyber security, organizations can measure and understand the risks they face in three ways.
The first is to conduct a formal risk assessment, which can provide detailed information about the company’s current level of risk and identify areas for improvement. Conducting a formal risk assessment is a vital part of ensuring the security of a business (Bayar, Sezgin, Ozturk, & Sasmaz, 2020). It should be done systematically and thoroughly to provide detailed information about the current level of risk, identify areas of weakness and potential threats, and make recommendations for improvement. It can help the business evaluate its risk management strategies, assess the adequacy of its controls, identify areas where additional controls should be implemented, and identify potential opportunities to reduce its overall risk exposure.
The second is to survey employees and stakeholders to understand their attitudes and behaviours around cyber security. Surveying employees and stakeholders is a powerful tool for understanding how they perceive and interact with cyber security in their day to day activities. Through surveys, organizations can gain insight into the attitudes, behaviours and understanding of cyber security among their staff and stakeholders, allowing them to better assess their current cyber security stance and identify improvements.
Finally, organizations should review existing policies and procedures to align with industry best practices and organizational goals (Hubbard, 2020). Doing so will help organizations keep up with the changing needs of their industry, remain competitive, and achieve their desired outcomes. By implementing this process, organizations can identify any potential risks or opportunities to be capitalized on, allowing them to stay ahead of their competitors.
4. The Resources for Learning About Cyber Security Laws
The Security of Critical Infrastructure Act 2018 is the first piece of law about cyber security. This act generally imposes obligations on particular entities concerning communications and electricity (CISC AU, 2023). Financial services, stock markets, and data handling or storage are also included. The main goals of this SOCI Act amendment were to strengthen the security and resilience of the critical infrastructure by extending the range of industries and asset classes to which it applies and by introducing new responsibilities.
The Telecommunications (Interception and Access) Act 1979 is the second source of law about cyber security. In Australia, the TIA act is a broad regulatory framework for all Internet access, including data access (Home Affairs AU, 2023). The TIA act also allows access to communications to look into the process of requesting a warrant from a judge or tribunal. Applications for warrants must consistently adhere to all stringent Act requirements. When certain conditions arise, such as a crisis, the Agencies may also view the communications despite a warrant.
References
.png)
IFN552 System Analysis and Design Assignment 1 Sample
In this Assignment, you will take what you have learnt in weeks 1, 2 and 3 and apply this to a case. You will develop a list of questions that you would ask key stakeholders to elicit requirements, distil stakeholder needs into functional requirements in a Requirements Matrix, draw a Use Case Diagram and Activity Diagram. You will also justify your designs in short descriptions accompanying each of these outputs.
1. Read the Criterion-Referenced Assessment Rubric at the end of this document.
2. Read Case 1 (below) which pertains to all elements of this assignment.
3. Develop and document a list of questions for two of the key stakeholders to specifically gather functional requirements. Aim for approximately 10 key questions for each stakeholder type (you can also choose to add follow-up sub-questions if necessary).
4. Try out your questions on the Grower, Customer and Business chatbots (available by the end of Week 1) on Slack by entering a conversation with each under the “Apps” dropdown in the IFN552 Slack channel. Note the chatbots are there to provide you with an opportunity to practice asking stakeholder questions and to provide additional ‘bonus’ information about the case; they will not be able to answer all of your questions, but can help you explore and brainstorm some of the needs for the stakeholders. Please do not rely solely on these to develop your list of requirements.
5. Develop a Requirements Matrix to show the functional requirements of the new system. Aim for:
a) 15 Essential Functional Requirements
b) 5 Desirable Functional Requirements
c) 1 Optional Functional Requirement
You should include the suggested number for each priority of requirements, totalling around 21 Functional Requirements in your matrix. A small amount less or more may be ok depending on the quality of the ones you include, but you will need to stay around the number stated above. Whilst each will have certain priority, and the list may not be comprehensive, you need to ensure that all are relevant to the case and are concise, specific, measurable and actionable.
6. In 250 words or less, justify your choices (i.e. How/why did you decide to split the system into the modules you chose? How did you decide on priorities? Is there a particularly novel or unusual requirement that you have identified – if so, how does it meet the needs of your stakeholders? etc.).
7. Draw 1 (one) Use Case Diagram representing the new integrated system described in the case.
a) Aim to include around 15-20 Use Cases in your diagram (no more than 23). Ensure that the use cases you do include are important and relevant to the process being represented.
8. In 250 words or less also introduce your use case diagram (i.e. what is it describing? At which points do users interface with the system? What is outside the scope of your diagram? Etc.).
9. Draw an Activity Diagram, representing how a grower would order a kit on the website, monitor the growth of their produce, organize a swap for their grown produce with replenishment seeds/cuttings and
a customer eventually ordering some of that produce via the website.
You can start with the following assumptions:
a) Assume that the grower and customer are already in logged in states at the beginning of their processes (i.e., no need to include activities involved in login/register)
b) The delivery process is handled by an external company. There is therefore no need to include any activities associated with the delivery process other than those that involve the system being designed and/or other actors in the process
Remember to balance detail with clarity in your diagram. Take note of the following guidelines regarding scope:
a) Use around 2-3 swimlanes to differentiate system activities initiated by different actors. For activities performed by a subsystem with no interaction with an actor, you may use a separate “system” swimlane, however, ensure all other activities performed in actor swimlanes describe system interactions.
b) Use up to 60 shapes – ideally around 50 shapes – (shapes include boxes, decision nodes, fork and join, arrows, etc.) to show the process of user activities.
c) Use decision nodes two or three times and fork and join two or three times in your model.
d) Preferably, your activity diagram will be vertical, rather than horizontal (this will make it easier when merging it into the submission PDF).
10. Write a short description of your Activity Diagram in 250 words or less. Imagine you are presenting it to a set of stakeholders and you need to introduce concisely what it is showing (~1-2 sentences) and mention a few interesting/important activities or flows, as well as parts where you have made assumptions (~3-4 sentences).
Note that it’s important to practice this skill, as you will need to contextualise designs/diagrams when you create reports/presentations.
Solution
List of questions
Stakeholder #1: Growers
1. How frequently would you like to receive updates on the growth of your plants?
2. What kind of data would you like to see about the plants' growth? (e.g. temperature, humidity, light levels)
3. How would you prefer to receive updates on the growth of your plants? (e.g. email, SMS, app notifications)
4. What information would be helpful for you to know about the exchange process with delivery personnel?
5. Would you prefer to have the option to customize the seeds/cuttings you receive in your kit?
6. What would be your preferred method for providing feedback on the Grow Kit and the plants' growth?
7. How would you like to be paid for the produce you grow? (e.g. bank transfer, PayPal)
8. What kind of support would be helpful for you during the growing process? (e.g. online tutorials, live chat support)
9. How frequently would you like to receive new seeds/cuttings?
10. Would you be willing to provide additional information about your location and growing conditions to help improve the Grow Kit and plant growth?
Stakeholder #2: Website Users
1. What kind of user account management features would you like to see on the website?
2. How would you like to receive notifications about inventory levels and forecasts?
3. What kind of analytics would be helpful for you to have access to about plant growth and inventory management?
4. What kind of user data would be helpful for the website to collect to improve the user experience?
5. How would you like to be able to communicate with growers through the website? (e.g. messaging, chat)
6. What kind of security measures would you like to see implemented on the website?
7. What kind of payment processing system would be most convenient for you to use?
8. What kind of customer service features would be helpful for you to have access to on the website?
9. What kind of reporting features would be helpful for you to have access to on the website?
10. How frequently would you like to receive updates about the website's functionality and new features?
Requirement matrix
Requirements Matrix for Micro-Farming Start-Up
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
(Rodriguez et al., 2022)
The essential functional requirements are necessary for the system to function as intended. Without the sensor data collection, display, and algorithm integration, the business cannot accurately forecast produce availability and manage inventory levels. Produce collection and replenishment, along with the delivery driver booking system, are required to manage the exchange of produce and replenishment kits between the business and Growers. The integration of Grow Predict with the online store inventory management is essential to ensure accurate stock levels and provide customers with available produce. Lastly, Growers require the ability to select grow kit size and type of produce to grow, and to receive starter kits with all necessary components (Wang et al., 2020).
The desirable functional requirements, while not critical to the system, provide additional benefits to the stakeholders. Allowing customers to customize produce boxes and providing subscription-based discounts can increase sales and customer loyalty. Nutritional information can appeal to health-conscious customers, and feedback from Growers can improve the quality of the products. Alerts to Growers can help ensure healthy plant growth. The optional functional requirement enables Growers to sell excess produce to the online store, providing an additional revenue stream for Growers and increasing the variety of available produce for customers. However, this functionality is not essential to the system and may require additional resources to implement (Rodriguez et al., 2022).
The functional requirements for the assignment help have been prioritized based on the impact on the business and the needs of the stakeholders. The system has been divided into modules to ensure efficient development and management of each aspect.
Use case diagram
.png)
.png)
Figure 1 Use case Diagram.
The use case diagram describes the interactions between the actors and the system at the various touchpoints. Growers interact with the system through the Grower Portal, where they manage their Grow Kits and sell their produce. Customers interact with the system through the Online Store, where they browse and purchase produce boxes. The GrowPredict Algorithm interacts with the system to provide inventory forecasting based on the sensor data from the Grow Kits (AL-Msie'deen et al., 2022). Outside the scope of this diagram are the technical details of the system, such as the database and server infrastructure, and the specifics of the sensor data collection and analysis. The diagram shows the relationships between the actors and the system components and illustrates the flow of data and actions between them. It is important to note that the scope of the diagram does not include specific details about the sensors or the algorithm, but rather focuses on the high-level interactions between the actors and the system components (Arifin & Siahaan, 2020).
Activity diagram
.png)
Figure 2 Activity diagram.
The Activity Diagram is a visual representation of the steps involved in the Grower portal, from purchasing a kit to harvesting produce and replenishing it with new seeds/cuttings. The diagram shows the flow of activities, including the monitoring of plant growth, the notification system for harvest, and the scheduling of pickup/delivery times. It also includes assumptions, such as the delivery driver being booked automatically and the company paying for the products based on the weight of usable produce. An interesting flow is the integration of GrowPredict, which forecasts when certain products will be available and in what numbers, and how it helps connect the online store and the Grower portal (Bakar et al., 2020).
References
.png)
![]()
CSE5CRM Cyber Security Risk Management Program Assignment Sample
Assessment Components
Component 1: Asset Evaluation and Classification
Objective: Demonstrate the ability to identify and classify organizational assets for risk assessments.
Tasks:
1. Asset Inventory Creation:
Develop a comprehensive inventory of an organization's assets (hardware, software, data, human resources). Provide a detailed description of each asset.
2. Asset Categorization:
Categorize each asset into groups (e.g., critical, sensitive, non-critical).
Justify the categorization based on the asset's role and importance to the organization.
3. CIA Triad Evaluation:
Assess each asset based on confidentiality, integrity, and availability requirements.
Assign a classification level (e.g., high, medium, low) and justify the classification.
4. Business Impact Analysis:
Conduct a Business Impact Analysis (BIA) to determine the potential impact of asset compromise on business operations.
Classify assets according to their impact on business continuity.
5. Data Sensitivity and Value Assessment:
Evaluate the sensitivity and value of data handled by each asset.
Classify assets based on the data they manage and provide justification.
Deliverable: A report documenting the asset inventory, categorization, CIA triad evaluation, business impact analysis, and data sensitivity and value assessment.
Assessment Criteria:
- Completeness and accuracy of the asset inventory.
- Justification for asset categorization and classification.
- Depth of analysis in the BIA and data sensitivity assessment.
- Clarity and organization of the report.
Component 2: Developing Methods for Evaluating and Monitoring Cyber Risk Management
Objective: Develop and apply methods for evaluating and monitoring cyber risk management.
Tasks:
1. Qualitative Risk Assessment:
Utilize qualitative methods (e.g., expert judgment, scenario analysis) to evaluate cyber risks.
Document the process and findings.
2. Quantitative Risk Assessment:
Apply quantitative methods (e.g., Annual Loss Expectancy, Monte Carlo simulations) to quantify cyber risks.
Present the results and explain the methodology used.
3. Key Risk Indicators (KRIs):
Develop a set of KRIs to monitor the organization's risk landscape.
Explain how these KRIs will be measured and monitored.
4. Continuous Monitoring Plan:
Design a plan for continuous monitoring of cyber threats, including tools and techniques to be used (e.g., SIEM, IDS, EDR).
Explain how the monitoring plan will be implemented and maintained.
5. Periodic Risk Assessment Plan:
Develop a schedule and methodology for conducting regular risk assessments.
Outline the steps for updating the risk assessment based on new threats and vulnerabilities.
Deliverable: A comprehensive document detailing the qualitative and quantitative risk assessments, KRIs, continuous monitoring plan, and periodic risk assessment plan.
Assessment Criteria:
- Appropriateness and thoroughness of the risk assessment methods.
- Justification for the selection of KRIs.
- Feasibility and effectiveness of the continuous monitoring and periodic risk assessment plans.
- Clarity and professionalism of the document.
Component 3: Determining Cost-effective Treatments to Manage Cyber Risk
Objective: Identify and justify cost-effective treatments to manage cyber risk.
Tasks:
1. Risk Treatment Options Analysis:
Identify and analyze risk treatment options (e.g., risk avoidance, risk reduction, risk transfer, risk acceptance).
Provide examples and justifications for each option.
2. Prioritization of Security Controls:
Prioritize security controls based on their effectiveness and cost.
Use the results from the risk assessments to guide prioritization.
3. Cost-benefit Analysis:
Conduct a cost-benefit analysis for each proposed security control.
Include calculations for Return on Security Investment (ROSI) and Total Cost of Ownership (TCO).
4. Implementation Plan:
Develop a plan for implementing selected security controls.
Outline the steps, resources required, and timeline for implementation.
5. Cost-effective Security Metrics:
Propose metrics to measure the cost-effectiveness of implemented security controls.
Explain how these metrics will be monitored and reported.
Solution
Component 1: Asset Evaluation and Classification
1.1 Asset Inventory Creation
.png)
.png)
Table 1: Assets inventory
(Source: Self-created)
1.2 Asset Categorization
Critical
- Web Server
- Firewall
- ERP System
Non-critical
- Workstations
Sensitive
- CRM System
- Customer Database
1.3 CIA Triad Evaluation
.png)
Table 2: CIA Triad Evaluation
(Source: Self-created)
Justification
The risk classification levels, therefore, depend on the significance of the asset to the operations, security, and data of the organization. The firewall, IT administrator, and customer database are highly classified because their loss or compromise impacts confidentiality, integrity, and availability severely by breaching customer data, shutting down operations, and attracting penalties. Enterprise resource planning and customer relationship management, as are the systems under discussion, are considered high in importance (Fraser et al. 2021).
1.4 Business Impact Analysis
Business impact analysis (BIA) is the assessment for the Assignment Help of the effect that adverse events will have on an organization’s operations in the event of the compromise of assets. In the case of the web server, firewall, CRM system, and ERP system, if compromised, it is very devastating to business continuity. For example, the web server responsible for hosting customer applications means the absence of this resource will result in a lack of access to services, loss of trust, and consequently low revenues. It safeguards the whole network and the failure of a firewall means that the organization is vulnerable to cyber-attacks and all the other systems would be at risk (Ghadge et al. 2020).
.png)
Figure 1: Risk Assessment and Business Impact Analysis
(Source: Linkedin.com, 2024)
Also, highly sensitive assets such as the customer database and financial records will cause severe legal and financial penalties as a result of data privacy laws such as GDPR. The opportunity loss would mean the inability to make sales, customer inconvenience, and delay in responding to their needs and demand but the harm is not severe as it will entail loss in potential revenue. Despite the definite usefulness of data analysts, their non-attendance does not necessarily lead to a stop of activities (Crumpler, and Lewis, 2022).
Classification
.png)
Table 3: Assets classification
(Source: Self-created)
1.5 Data Sensitivity and Value Assessment
.png)
Table 4: Data Sensitivity and Value Assessment
(Source: Self-created)
Component 2: Developing Methods for Evaluating and Monitoring Cyber Risk Management
2.1 Qualitative Risk Assessment
The qualitative risk assessment process of the anticipated scenario opened quite valuable information for the organization’s cybersecurity risks. The analysis of possible phishing attacks showed one important conclusion, though such attacks are progressing in real-world scenarios. For instance, the recent attack, the Twitter hack of the year 2020, where the attackers used phishing techniques to gain control over the executives’ accounts, indicates the risks involving negligence when it comes to the aspect of employee training on how to identify the threats (Li, and Liu, 2021). The investigation of insider threats provided more understanding of problems related to frustrated personnel becoming criminals and exploiting their privileges. Prominent examples like the Edward Snowden case of 2016 show that insider threats can have severe consequences for organizational reputation and customer loyalty.
2.2 Quantitative Risk Assessment
Annual Loss Expectancy (ALE)
The Annual Loss Expectancy (ALE) assessment enables the measurement of loss from identified threats in the assets. First, one specifies the assets and the threats that they face, for example, loss of data, or ransomware attacks. Next, every asset is given a dollar amount attached to it. There are three main types of threats, and the threat frequency, which is expressed as the Annual Rate of Occurrence (ARO), is calculated using statistical data (Kamiya et al. 2021).
“SLE=Asset Value * Exposure Factor”
“ALE= SLE * ARO”
Findings
.png)
Table 5: Findings from quantitative analysis
(Source: Self-created)
2.3 Key Risk Indicators
Key Risk Indicators (KRIs)
- Number of Security Incidents: This KRI measures the overall cumulative count of security incidents which can be within a month or within a quarter. An increasing rate of occurrence may also point to weaknesses that may require prompt action to be taken.
- Phishing Attack Rate: This represents the number of employees who have failed the phishing simulation tests. A higher rate indicates the need for enhancing the security training and awareness programs within their organizations (Zwilling et al. 2022).
- User Access Violations: This one measures the number of attempts made by unauthorized individuals to access restricted data or information systems. In user group wise use of physical access controls, an increase in violations could be from potential insiders or lack of access control (Sarker et al. 2021).
Measurement and Monitoring of KRIs
- Data Collection: Implement organizational structures for acquiring key data for each KRI. For instance, the Security Information and Event Management (SIEM) tool logs security incidents and access attempts.
- Regular Reporting: Develop KPIs and KRIs and locate or build the respective trending charts into the systems, to provide capabilities to track changes over time. In cases of monthly or quarterly reporting, there will be improved recognition of new trends and risks (Gupta et al. 2023).
- Continuous Review: Ensure that KRIs are dynamic while conducting routine reviews on such factors in relation to changes in the risk environment and business direction. This ensures that the indicators are still meaningful and in tune with the objectives that the organization seeks to put forward (Khinvasara et al. 2023).
2.4 Continuous Monitoring Plan
.png)
Table 6: Continuous Monitoring Plan
(Source: Self-created)
2.5 Periodic Risk Assessment Plan
.png)
.png)
Table 7: Continuous Monitoring Plan
(Source: Self-created)
The process of the newly updated risk assessment has included several steps that still need to be followed to ensure cybersecurity is still adequate. First, the organizations have to gather threat intelligence by either purchasing, or getting a feed that alerts them to threats, the second part is that they have to read and be aware of different industry reports and trends.
Component 3: Determining Cost-effective Treatments to Manage Cyber Risk
3.1 Risk Treatment Options Analysis
Risk Avoidance
Risk avoidance gives direction in the disposal of do in order to erase each activity that has the possibility to put the organization at risk. For example, if relatives are aware of vulnerabilities of a certain software application that cannot be fixed to a reasonable extent, they might decide not to use it in the organization.
.png)
Figure 2: Risk treatment options
(Source: Researchgate.net, 2024)
Risk Reduction
Risk minimization is centered on achieving the lowest probabilities of occurrence of risks and their severity. For instance, an organization may employ more and sophisticated firewalls and intrusion detection systems, to strengthen a network security standard (Zeadally et al. 2020). Training common employees on cybersecurity can also reduce the instances of errors which are common causes of cyber threats.
Risk Transfer
Risk transfer means the transferring of responsibility of a risk to a third party usually through contracts and or insurance. For example, an organization may invest in cyber liability insurance for protection from losses that may occur due to hacking. The said approach enables the organization to cap its resources liability while at the same time making sure that resources for dealing with such are available.
3.2 Prioritization of Security Controls
Risk control is helpful for organizations because it assists in efforts to prioritize security controls and allocate resources in a way that will be most effective in diminishing risk. Considering security controls, it is also possible to describe a risk-based approach that takes into account not only the effectiveness of the particular control but also the costs for its implementation.
.png)
Figure 3: How to implement the types of security controls
(Source: sprinto.com, 2024)
Also, the cost of controls should also be taken into consideration by organizations. It is not reasonable to use high-cost controls at workplaces when low-cost can offer almost the same level of protection.
3.3 Cost-Benefit Analysis
Firewall
- Initial Cost: $20,000
- Annual Maintenance Cost: $3,000
- Lifespan: 5 years
Total Cost (TCO) = 20,000 + (3,000*5)
=35,000
Risk Reduced (Annual Savings) = $100,000
ROSI = 10000/3500 * 100
= 285.71%
Intrusion Detection System
- Initial Cost: $15,000
- Annual Maintenance Cost: $2,500
- Lifespan: 5 years
- Risk Reduced (Annual Savings): $75,000
Total Cost (TCO) = 15000 + 2500*5
= 27500
ROSI = 75000 / 27500 * 100
= 272.73%
Employee Training
- Initial Cost: $5,000
- Annual Maintenance Cost: $1,000
- Lifespan: 3 years
- Risk Reduced (Annual Savings): $25,000
Total Cost (TCO) = 5000 + 3*1000
= 8000
ROSI = 25000/8000 *100
= 312.5%
Based on the cost-benefit analysis, the three proposed security controls have high ROSI, and the most beneficial security control is the employee training program.
3.4 Implementation Plan
.png)
.png)
Table 8: Implementation plan
(Source: Self-created)
3.5 Cost-effective Security Metrics
Proposed Metrics to Measure
Thus, the effectiveness of the security controls implemented in an organization can be represented by a set of metrics that are listed below, which can give a proper understanding of the organization’s security. One of these is Return on Security Investment (ROSI) which measures security investment dollar returns against the dollars invested.
Monitoring and Reporting of Metrics
In order to make these metrics more effective, the organization should incorporate a proper monitoring and reporting technique in order to ensure that security controls are evaluated consistently. This serves as a basis for making the correct evaluations concerning the prevailing security situation (Khando et al. 2021).

.png)



.png)
~5.png)
.png)
~1.png)























































.png)






