MIS603 Microservices Architecture Assignment Sample
Question
Assessment Task This research paper should be approximately 2500 words (+/- 10%) excluding cover page, references and appendix. In this assessment, you need to present the different issues that have been previously documented on the topic using a variety of research articles and industry examples. Please make sure your discussion matches the stated purpose of the report and include the cases study throughout. Discuss and support any conclusions that can be reached using the evidence provided by the research articles you have found. Details about the different industry cases studies should NOT be a standalone section of the paper.
Context
Microservices is one of the most rapidly expanding architectural paradigms in commercial computing today. It delivers the fundamental benefits of integrating processes, optimization and Instructions delivering efficiency across many areas. These are core benefits expected in any implementation and the MSA is primarily configured to provide the functional business needs. On-the-one-hand, MSA can be leverage to provide further benefits for a business by facilitating:
• Innovation— reflecting the creation of novel or different services or businesses processes, or even disruptive business models.
• Augmented Reality — reflecting the situation where superimposing images and data on real objects allowing people to be better informed.
• Supply chain— reflecting how the MSA enables closer communication, engagement and interactivity amongst important external or internal entities.
On-the-other-hand culture is the totality of socially transmitted behaviour patterns, attitudes, values and beliefs, and it is these predominating values and behaviours that characterize the functioning of an individual, group or organisation. Organizational culture is what makes employees feel like they belong and what encourages them to work collectively to achieve organizational goals. Extant IS implementation studies have adopted culture theory to explain how organisations respond to implement a MSA system in their workplace, and how these responses lead to successful or failed implementations. As a professional, your role will require that you understand the benefits of MSA, especially in these three areas, which are significantly becoming the preferred strategy to achieve competitive advantage for many organisations. The purpose of this report is to engage you in building knowledge about how these benefits achieve in an organisational environment with a specific focus on how and why organisational culture can influence the successful implementation of an MSA within an organisation.
Task Instructions (the scenario)
You suppose to work for your selected organization (in assessment 2) and have read reports of other organisations leveraging the MSA application in three areas (innovation, augmented reality and supply chain). Accordingly, you need to prepare a research report for management on how the MSA application can be used to deliver benefits in these areas as well as how and why organisational culture can influence the successful implementation of an MSA. Use at least 2 different case study examples for showing the benefits can be achieved by organisations.
The report should consist of the following structure: A title page with subject code and name, assignment title, student’s name, student number, and lecturer’s name.
The introduction (250–300 words) that will also serve as your statement of purpose for the proposal—this means that you will tell the reader what you are going to cover in your proposal. You will need to inform the reader of:
a) Your area of research and its context
b) The key elements you will be addressing
c) What the reader can expect to find in the body of the report
The body of the report (1900–2000 words) will need to focus on these three areas (innovation, augmented reality and supply chain) also organisational culture to develop your research paper. Particularly, you need to prepare a research report for management on how the MSA application can be used to deliver benefits in different organisational environments- cultures.
The conclusion (250–300 words) will summarise any findings or recommendations that the report puts forward regarding the concepts covered in the report.
Answer
Introduction
MSA or microservice architecture is an architectural project management approach where the services or features are micro niche-based and specific in terms of usability as well. Nowadays, all the large and small organizations are implementing this architecture to minimize their cost. With several, real-life case studies the use and implementation of MSA can be clear in this report.
The key element is MSA and real-life organizations. The connection between these two elements is essential in this competitive market. There are also some issues with the system, which can be resolved easily with this project management approach.
The report consists of project management aspects and other essential factors. Companies are implementing this concept through their niche bae projects to lower their expenses. It eventually increases the profitability and sustainability of the business as well. System issues can be solved easily with more consumer engagement. System design and use will be specific and certain teams will also be there to support the consumers. In this way, the whole customer base will experience better design and features. This is the basic reason, that companies are planning and developing microservices. In this report, two real-life case studies are taken into consideration. Amazon, a web-based company, have developed two cloud based software, such as amazon music and amazon prime video. Through cloud computing technology they are providing different microservices. The implementation procedure and benefits are discussed ad well. This will eventually show the core features, aspects and significance of MSA or microservice architectural approach through three aspects mainly. innovation, augmented reality and supply chain will be majored or considered in these two organizations with detailed discussion and risk management as well (Wang et al., 2020).
MSA Project Management Approach
MSA project management approach is basically used in small and niche-based projects. Here, all the project components are planned and built into one focus feature. Several organizations like Amazon are using or implementing this approach to build and manage their new projects or products. In this way, the projects are also micro service-based. Every stakeholder can focus on one single project development and improvement. It is also easier for project manager to handle small amount of teams. In that way, he can engage or involve every team equally with the project. The project will be come successful. On other hand, the feedback sorting and organising team can also work on specific number of issues. In this way, the team can also be trained in specific ways. Whole project will experience better efficiency and improvement. Consumers of the system will also experience the results in form of better functionality and engagement.
This management approach has significant impact, several organisational cultures. These organisational cultures are the results of specific scenarios or systems. While implementation of MSA in Amazon products, these cultures have associated with different systems and policies. Three organisational culture scenarios are mentioned here with detailed discussion on MSA implementation.
MSA in Different Organisational Cultures
Several organisations like Amazon are using or implementing this methodology or project management approach. Implementation in two amazon cloud based products will be discussed in terms of innovation, augmented reality and supply chain. Starting from the implementation procedure to the benefits or significance will be mentioned in detail. Through this part of the report, organisational culture can also be derived. Three organisational cultures are discussed here through MSA implementation.
Each of these organisational culture scenarios are made of different systems. Amazon has taken different initiatives to change the workflow and working system inside the organisation. They have developed different workplace environments and work cultures to increase work efficiency and over-all productivity. In this way, different organisational cultures are implemented on employees and other major stakeholders. Implementation results are also very specific. Whole project management becomes efficient. On other hand, time accuracy is also another benefit of these cultures. All the three cultures, which are mentioned here, are discussed through MSA or micro service architectural project management approach.
Boldness
Boldness is an organisational culture scenario, where all the employees and stakeholders are influenced and motivated to be bold with the maintenance of all the products of s certain organization. MSA is an architectural approach, where a small cloud base project is focused. The organization provides a dedicated team and project manager as well. All these things pr elements allow the stakeholders and employees to be specific and particular in objective. There they can use their specific ideas and scope of development in the project. In this way, the whole project management team becomes bold along with the team manager as well. In this way, the whole project becomes better and efficient. Eventually, the profit growth comes at place and the organizational culture becomes bold and efficient as well. The internal and external structure of the organization goes through certain changes as well. This change in the supply chain is a basic characteristic of this microservice architectural or MSA project management approach. All the organization is segregated with different products here. The boldness of the company becomes higher here with this methodology (Pacheco, 2018).
Customer-Centricity
The organization targets a separate consumer base in different parts with different services and products. One single system is not handling every objective. In this way, MSA is implemented through an organization. Small projects and niche-based software are provided by the teams. In this way, all the products satisfy particular and specific needs of targeted consumers.
All the consumers will experience better and dedicated service from one dedicated team and project managers. The project also becomes better with time. The whole project becomes more customer-centric and specific. It also influences the customer experience. The consumer gets better design in the user interface or UI. A better support system is also provided here because every project gets separate support team management. Here, all the people are experienced and trained for this particular support system (Project Management Institute, 2017).
Here the augmented reality of MSA application or implementation becomes significant. Consumers are the key-stakeholder here, who are going to experience detailed systems and features according to their small needs and requirements as well. In the end, this whole customer-centricity can be well-defined and implemented by this MSA project management approach (Meyer, 2017).
Peculiarity
It is also another organizational culture or system, where new innovations take place. From the first place, the significance of MSA implementation is very clear here. The whole concept is based on innovating a new product feature or product component. Innovation comes the basic or primary characteristic of the MSA project management approach. In that case, this character or feature will definitely influence this part of organizational culture (Project Management Institute, 2019).
With this innovative approach, the project manager can achieve so many unexpected results and develop planning accordingly. Market research and analytical reports cannot always show the required features of the consumers. It is the work of the development team and other stakeholders to develop something innovative for a better user experience. With MSA, a dedicated team will work on a specific project, which will appreciate the potential of new innovations as well. It becomes easier to make new system policies or modifications (Atesmen, 2015).
Amazon Success Stories
Amazon is one of the largest companies in the world. All the people around the world, are experiencing amazon products for a better lifestyle and exciting features. Amazon is providing best cloud-based software with exciting usability for the last decade. These products are all based on MSA or microservice architectural, project management approach. All those projects are real-life business examples of MSA approach implementation. Those project management and development teams have implemented all the characteristics and features, of the MSA project management approach or methodology. Here two of those success stories will be discussed in detail for a better understanding of MSA implementation.
Amazon Prime Video
Amazon prime video is one of the most significant software, which includes one of the major profitability factors as well. This is basically a video streaming software or platform, where web series and movies around the world are uploaded. Some own production projects are also developed here. With prime membership of amazon, this prime video account is offered. People can experience the facilities through the application as well.
This product of the project is also developed with proper implementation of the MSA project management approach. All the primary features of the MSA approach is clearly discussed here through this specific project by amazon.
Firstly, the innovation is implemented particularly in this project. There are so many other video streaming platforms, apart from amazon, such as Netflix. In that case, the project management team has to plan and develop some unique strategies to make this platform profitable and beneficial for the consumers or viewers. The system provides a new collection of contents in the first place. On other hand, the prime membership structure also makes this significant. These modifications have helped this product to stand out in the competitive market. It shows the proper use of innovation here. Another exciting feature is provided as well, which is student membership. Student membership can be bought at lower rates at amazon prime video. That also played a significant role in amazon profitability and growth (Nikolakis et al., 2020).
Innovative cost distribution or plans categorization is also very specific here along with an innovative approach. Several screens are provided by Amazon, where more than one person can enjoy the platform and contents accordingly. It makes the system more exciting and attractive to different consumers around the world.
The next feature of the microservice architectural, project management approach is augmented reality. Here, the consumers are focused. This micro product or project is based on a specific and targeted audience. In that case, the team can modify and develop all the features and modifications accordingly. Amazon prime video has uploaded a separate collection of popular movies and web series for better expenditure. Eventually, consumers get the highest benefit. This is another factor of amazon prime video success and shows the significance of MSA implementation as well (Watts, 2019).
Lastly, the supply chain takes place. Here all the external and internal structures are considered along with team engagement and efficiency. In this case, also, this MSA approach is well-implemented. This approach changes the whole working culture or the environment of the system as well. Here, all the tea is dedicated to one software which is amazon prime video. That is the reason, why team engagement is more efficient. All the stakeholders of the system are well connected through communication and management. It is also easier for the project manager to handle a small and dedicated team (Nadareishvili et al., 2016).
Amazon Prime Music
Amazon prime music is also another cloud-based amazon product that basically presents a broad collection of songs to consumers around the world. Here all the consumers can hear the music with regular ads and exciting features. On other hand, with a subscription, they can also download the songs at a certain level. There are so many music streaming platforms as well, such as YouTube Music and Spotify. In that case, also, this software stands out in this competitive market through this MSA project management method or approach. All the features of this project management approach have built this system or product in a unique way of implementation and profitability.
Firstly, the innovation part takes place, which is the most relevant feature or characteristic of MSA or microservice architectural, project management approach. In this competitive market of music streaming platforms, amazon music also provides some extra features and offerings which holds the business. In this approach, it is easier to do because the whole team is dedicated to that single software or web-based product. In that case, the whole development and management teams focus on those certain developments. For that reason, consumers are also getting bigger benefits as well (Kerzner, 2013).
The second feature is called augmented reality. Here the consumers are the key stakeholder. All these features are implemented to improve the product or the service in a particular way. All the features become better with the system and updates. In this product also, everything is being built according to the customer needs and feedbacks. In the MSA approach, the design is also considered for better user experience and engagement. In this way, all the consumers can experience better facilities along with better project management. The support team is also dedicated to specific problems and technical issues, so the consumers get the solutions easily and efficiently. This whole part shows the significance of MSA implementation in the project of amazon prime music. With a subscription, all the consumers get better plans and experiences which make the whole thing more engaging as well.
Lastly, the supply chain takes place. This is the part, where all the internal and external structure changes of the organization are being discussed according to the MSA Approach. With this approach, the team members and various stakeholders become more engaged with each other and the communication becomes stronger. When all the people are working on a single niche, then it is also easier for the project manager to coordinate with all the segregated teams. In this way, involvement of implementation of MSA or microservice architectural, project management approach, company gets better profitability and growth matrix (McLarty, 2016).
Conclusion
This whole report is based on MSA or microservice architectural, project management method or approach. In this approach, certain things are being considered and those also influence any business model especially cloud-based business. With this approach, organizations can achieve a better success rate with broad cost-efficiency and fewer issues.
All the features and implementation procedures of this approach are discussed throughout the report. After that, all the essential work cultures are mentioned and discussed. This shows certain improvements, which are done by this particular approach. This can be beneficial for any kind of scenario, in different ways. On other hand, the features of the characteristics of MSA, are used differently in different scenarios or cultures. The way of implementation is also different here.
Lastly, the real-life business example has also been taken, which is amazon product-based. Amazon prime music and amazon prime video are the two cloud-based products, where amazon has used or implemented this MSA project management method. The whole project has become more successful and significant in this way. All the three characteristics of this approach, such as innovation, augmented reality and supply chain, are implemented in a proper and particular way. Here, both of the products are discussed in terms of that characteristic implementation ad well. All the factors are majored and evaluated accordingly. This report eventually shows the whole implemented structure of this project management approach. On other hand, how other several companies can implement and use this MSA, is explained here. This also presents all the significance of the system as well. On other hand, this report also present some factors, of this approach as well, which has a large impact on cloud based business model. Every aspect of the business model is also discussed. Organization can assess the business and current situation of the business through this report as well.
References
Atesmen, M. K. (2015). Project management case studies and lessons learned : stakeholder, scope, knowledge, schedule, resource and team management. CRC Press. https://lesa.on.worldcat.org/v2/oclc/895660999
Kerzner, H. (2013). Project management : case studies (Fourth). John Wiley & Sons. https://lesa.on.worldcat.org/v2/oclc/828724601
McLarty, M. (2016). Microservice architecture is agile software architecture. Javaworld, N/a. https://lesa.on.worldcat.org/v2/oclc/6858739262
Meyer, P. (2017). Amazon.com Inc.’s Organizational Culture Characteristics (An Analysis). http://panmore.com/amazon-com-inc-organizational-culture-characteristics-analysis
Nadareishvili, I., Mitra, R., McLarty, M., Amundsen, M. (2016). Microservice architecture : aligning principles, practices, and culture (First). O'Reilly Media. https://lesa.on.worldcat.org/v2/oclc/953834176
Nikolakis, N., Marguglio, A., Veneziano, G., Greco, P., Panicucci, S., Cerquitelli, T., Macii, E., Andolina, S., Alexopoulos, K. (2020). A microservice architecture for predictive analytics in manufacturing. Procedia Manufacturing, 51, 1091–1097. https://lesa.on.worldcat.org/v2/oclc/8709224754
Pacheco, V. F. (2018). Microservice patterns and best practices : explore patterns like cqrs and event sourcing to create scalable, maintainable, and testable microservices. Packt Publishing. https://lesa.on.worldcat.org/v2/oclc/1022785200
Project Management Institute. (2017). Project manager competency development framework (Third). Project Management Institute. https://lesa.on.worldcat.org/v2/oclc/974796222
Project Management Institute. (2019). Project management institute practice standard for work breakdown structures (Third). Project Management Institute. https://lesa.on.worldcat.org/v2/oclc/1107878459
Wang, R., Imran, M., Saleem, K. (2020). A microservice recommendation mechanism based on mobile architecture. Journal of Network and Computer Applications, 152. https://lesa.on.worldcat.org/v2/oclc/8520178287
Watts, A. (2019). Modern construction case studies : emerging innovation in building techniques (2nd ed.). Birkha?user. https://lesa.on.worldcat.org/v2/oclc/1110714056
BDA601 Big Data and Analytics Assignment Sample
Task Summary
Critically analyse the online retail business case (see below) and write a 1,500-word online custom essay help report that: a) Identifies various sources of data to build an effective data pipeline; b) Identifies challenges in integrating the data from the sources and formulates a strategy to address those challenges; and c) Describes a design for a storage and retrieval system for the data lake that uses commercial and/or open-source big data tools. Please refer to the Task Instructions (below) for details on how to complete this task. Context A modern data-driven organisation must be able to collect and process large volumes of data and perform analytics at scale on that data. Thus, the establishment of a data pipeline is an essential first step in building a data-driven organisation. A data pipeline ingests data from various sources, integrates that data and stores that data in a ‘data lake’, making that data available to everyone in the organisation.
This Assessment prepares you to identify potential sources of data, address challenges in integrating data and design an efficient ‘data lake’ using the big data principles, practices and technologies covered in the learning materials. Case Study Big Retail is an online retail shop in Adelaide, Australia. Its website, at which its users can explore different products and promotions and place orders, has more than 100,000 visitors per month. During checkout, each customer has three options: 1) to login to an existing account; 2) to create a new account if they have not already registered; or 3) to checkout as a guest. Customers’ account information is maintained by both the sales and marketing departments in their separate databases. The sales department maintains records of the transactions in their database. The information technology (IT) department maintains the website. Every month, the marketing team releases a catalogue and promotions, which are made available on the website and emailed to the registered customers. The website is static; that is, all the customers see the same content, irrespective of their location, login status or purchase history. Recently, Big Retail has experienced a significant slump in sales, despite its having a cost advantage over its competitors. A significant reduction in the number of visitors to the website and the conversion rate (i.e., the percentage of visitors who ultimately buy something) has also been observed. To regain its market share and increase its sales, the management team at Big Retail has decided to adopt a data-driven strategy. Specifically, the management team wants to use big data analytics to enable a customised customer experience through targeted campaigns, a recommender system and product association. The first step in moving towards the data-driven approach is to establish a data pipeline. The essential purpose of the data pipeline is to ingest data from various sources, integrate the data and store the data in a ‘data lake’ that can be readily accessed by both the management team and the data scientists.
Task Instructions
Critically analyse the above case study and write a 1,500-word report. In your report, ensure that you:
• Identify the potential data sources that align with the objectives of the organisation’s datadriven strategy. You should consider both the internal and external data sources. For each data source identified, describe its characteristics. Make reasonable assumptions about the fields and format of the data for each of the sources;
• Identify the challenges that will arise in integrating the data from different sources and that must be resolved before the data are stored in the ‘data lake.’ Articulate the steps necessary to address these issues;
• Describe the ‘data lake’ that you designed to store the integrated data and make the data available for efficient retrieval by both the management team and data scientists. The system should be designed using a commercial and/or an open-source database, tools and frameworks. Demonstrate how the ‘data lake’ meets the big data storage and retrieval requirements; and Provide a schematic of the overall data pipeline. The schematic should clearly depict the data sources, data integration steps, the components of the ‘data lake’ and the interactions among all the entities.
Solution
Introduction
Retail industry has grown a lot in 2020-21, speciallyby the use of online store facility (Menidjel et al., 2021). Like the global retail market, Australian retail market has changed a lot. The market takes the online approach. Here customers are free to change their mind by simple mouse click. These makes this industry highly competitive.
Big Retail is a retail store situated in Adelaide,Australia. Historical data says, per month around 100000 customers visit their website and makes the purchases. The website is maintained by the IT department of Big Retail. The website is a static one. All the customers see the same content irrespective of their location and login status or purchase history. A visitor may login if he or she has an account,he or she can create an account or checkout as a guest user. These activities generate a huge amount of data every month. These raw data is unanalysed till now and a data-driven approach is not taken based on these collected data. Presently Big Retails are experiencing less sales and they are losing their revenue. Therefore, a data-driven approach has to be taken and a data pipeline needs to be made(Hussein& Kais,2021). By analysing the available dada, the possible solutions will come out and the revenue will reach its expected pick.
Data Source
The website of Big Retails is managed by the IT department of the company. Every day a large number of visitors comes in this website to see the product or to purchase. They provide their name, address, email id, phone number and other information. Customers follows a definite purchase pattern. Data are generated from this website every day.
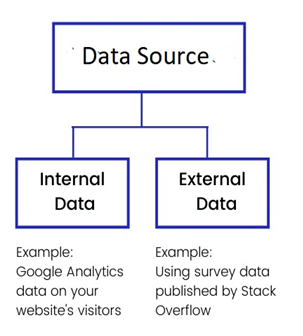
Figure 1: Data Source
Source: Created by Author
Internal Data Source
Every month around 100000 visitors visit Big Retails website. These huge number of website visitor generate a large amount of data. These website visitor data are internal data. Internal data is information which is generate within the organisation. The operations, maintenance, HR, finance, sales and marketing information within the company is also internal data (Feng, Fan & Bednarz,2019). Customer analysis, sales analysis report, cost analysis, marketing report, budget of Big Retail are internal data.
a) Internal data are reliable. These data are collected from the organisations own system. Therefore, during analysis,we can rely on these data.
b) Internal data or often unique and can be separated. Every data has unique meaning.
c) These data are operational data. Special DBMS operation is already done on these data.
d) Internal data are well defined data. The value, occurrence and event of these data are well defined. We know the exact value of each data.
External Data Source
External data are the data which is outside the current database. External data is collected from the outside source. Marketing department of Big Retail often make some market analysis and feedback collection campaign. Marketing department also does several surveys. Data which are collected from these campaign and surveys are external data.
Characteristics
a) These data are not reliable. These data are collected from external sources
b) Data operations are needed on external data.
c) We cannot use external data in DBMS.
d) External data are not well defined.
Structured data source
Structure data are those data which reside in a specific file or record. Structure data is stored in RDBMS (Anadiotis et al., 2021). In Big Retail, the data which are collected from the website visitors are identified and make unique. These data then store in a file. This file is the source of structure data.
Semi-Structured Data Source
Semi-structured data sources are emails,address of the customers who visited the website of Big Retail,XMLs,zipped files and web pages collected from different sources (Anadiotis et al., 2021).
Unstructured Data Source
Unstructured data sources are, Media information, audio and video files, surveillance data, geological data, weather data (Anadiotis et al., 2021). In Big Retail, audio and video message, email message collected form the customers are the source of unstructured data.
Challenge of Integrating Data from Different Sources
The website of Big Retail is a busy one. Everyday a large number of customers visits the website. There are internal analysis data as well. The survey data are also there. There ae structured and unstructured dada as well. Data are coming from different sources. Integrating such huge amountof data is a big challenge.
Challenges
The challenge of integrating data from different source are many. Big Retail is a large organisation. It has different types of data. All data are not structured. First challenge is to get a structured data. The integration challenge is, the data are not there where we need it(Gorji& Siami, 2020). Sometimes, the data are there but it is late. Getting data on right time, in right place itself is a challenge. The next challenge is getting an unformatted data or ill-formatted data. We get the data, but it is not formatted well i.e. the format of the data is not correct. Often the data quality is very poor. These data cannot be integrated. And again, there are duplicates of data. Throughout our pipeline, the data are duplicated (Zipkin et al., 2021). The data has to be clear. There is no clear understanding of data. These data cannot be integrated. Poor quality, duplicated and unclear data often make the situation tougher.
Solutions
The solutions of data integration problems are not many. But there are few effective solutions. We need to automate the data as much as possible. Manual data operation has to be avoided (Kalayci et al., 2021).We should opt for smallest integration first. It is advised to avoid large integration. The simplest way is to use a system integration software which will allow to integrate large amount of data from different sources. Some data integration softwareis Zapier, IFTTT, Dell Boomi etc.
Data lake
Data lake is a storage repository which stores a last amount of raw data it its own format until it is taken (Nargesian et al., 2020).
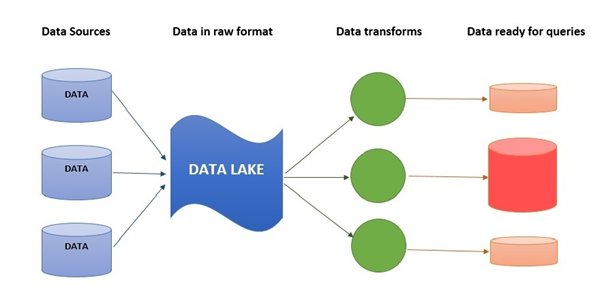
Figure 2: Data Lake
Source: Created by Author
Data lake does not use file or folder to store data, it stores data is its own flat architecture. Data lake is often a Hadoop oriented object storage. Data is first loaded in the Hadoop platform. After that, business analytics and data mining tools are used to get these data. Just like physical lake, it is a huge storage of data. The format of data is not a problem here.
Here, in Big Retail, data are coming from
1. website visitors,
2. active customers,
3. buyers,
4. feedback givers,
5. survey report,
6. sales reports
7. internal analytics report etc.
These data are structured as well as unstructured data. These data have different format. Some are integers, some are characters, some are binary data. These data are stores in data lake. Through the data pipeline these data cometothe data lake. Whenever the database administration of data scientist needs the data, some operations are done on that data and make the data available for use.
Schematic of the Overall Data Pipeline
The data pipeline is a set of actions that happen to the raw data to make them usable for the analytics purpose. There are series of data processing elements which are to be used on raw data.
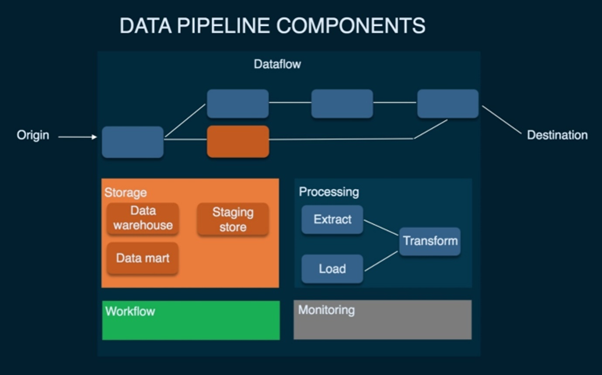
Figure 3: Data Pipeline Components
Source: (Giebler et al, 2019)
Big Retail business generate a massive amount of data which needs to be analysed to get the perfect business value and opt a business discission. Analysing data withing the system is not a wise idea. Moving data between systems requires many steps. Collecting data from one source, copping that data, upload the data to the cloud, reformatting the data, different operations on data and then joins it to other systems. This is a complex procedure. Data pipeline is the summation of all these above steps (Giebler et al, 2019).
Data from different source of Big Retails are collected first. Next part is uploading the data to the cloud. The using different software tool formatting of data is happening. Here the data goes to the data lake of Big Retail. In data lake, these data are received first and irrespective of its original format, it is stored in flat format(Quemy, 2019).
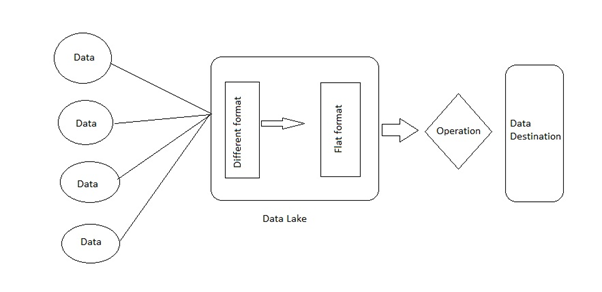
Figure 4: Data Pipeline
Source: Created by Author
Conclusion
The business scenario of today’s world is changing. Like other industry, retail in also facing a huge change due to the advancement of technology (Komagan, 2021). Big Retail of Adelaide, Australia needs to build this above-mentioned data pipeline and data lake. Being an online store, it is highly depending upon data and e-technology. It has been found that the data pipeline can help the store to get the data effectively. The proposed data lake will help to store data and can provide it when necessary. Using analytics tools, data analyst and data scientist can predict the business scenario and advice the management of Big Retail to take the necessary actions.
References
Anadiotis, A. C., Balalau, O., Conceicao, C., Galhardas, H., Haddad, M. Y., Manolescu, I., ... & You, J. (2021). Graph integration of structured, semistructured and unstructured data for data journalism. Information Systems, 101846.https://www.sciencedirect.com/science/article/abs/pii/S0306437921000806
Feng, T., Fan, F., & Bednarz, T. (2019, November). A Data-Driven Optimisation Approach to Urban Multi-Site Selection for Public Services and Retails. In The 17th International Conference on Virtual-Reality Continuum and its Applications in Industry (pp. 1-9).https://dl.acm.org/doi/abs/10.1145/3359997.3365686
Giebler, C., Gröger, C., Hoos, E., Schwarz, H., & Mitschang, B. (2019, November). Modeling data lakes with data vault: practical experiences, assessment, and lessons learned. In International Conference on Conceptual Modeling (pp. 63-77). Springer, Cham.https://link.springer.com/chapter/10.1007/978-3-030-33223-5_7
Gorji, M., & Siami, S. (2020). How sales promotion display affects customer shopping intentions in retails. International Journal of Retail & Distribution Management.https://www.emerald.com/insight/content/doi/10.1108/IJRDM-12-2019-0407/full/html
Hussein, R. S., & Kais, A. (2021). Multichannel behaviour in the retail industry: evidence from an emerging market. International Journal of Logistics Research and Applications, 24(3), 242-260.https://www.tandfonline.com/doi/abs/10.1080/13675567.2020.1749248
Kalayci, T. E., Kalayci, E. G., Lechner, G., Neuhuber, N., Spitzer, M., Westermeier, E., & Stocker, A. (2021). Triangulated investigation of trust in automated driving: Challenges and solution approaches for data integration. Journal of Industrial Information Integration, 21, 100186.https://www.sciencedirect.com/science/article/abs/pii/S2452414X20300613
Komagan, M. L. (2021). Impact of Service Environment for effective consumer behavior in Retails Industry with reference to Heritage Super Market. Turkish Journal of Computer and Mathematics Education (TURCOMAT), 12(3), 4357-4364.https://turcomat.org/index.php/turkbilmat/article/view/1727
Menidjel, C., Bilgihan, A., & Benhabib, A. (2021). Exploring the impact of personality traits on perceived relationship investment, relationship quality, and loyalty in the retail industry. The International Review of Retail, Distribution and Consumer Research, 31(1), 106-129.https://www.tandfonline.com/doi/abs/10.1080/09593969.2020.1781228
Nargesian, F., Pu, K. Q., Zhu, E., Ghadiri Bashardoost, B., & Miller, R. J. (2020, June). Organizing data lakes for navigation. In Proceedings of the 2020 ACM SIGMOD International Conference on Management of Data (pp. 1939-1950).https://dl.acm.org/doi/abs/10.1145/3318464.3380605
Quemy, A. (2019). Data Pipeline Selection and Optimization. In DOLAP.https://www.aquemy.info/static/publications/quemy2019b.pdf
Zipkin, E. F., Zylstra, E. R., Wright, A. D., Saunders, S. P., Finley, A. O., Dietze, M. C., ... & Tingley, M. W. (2021). Addressing data integration challenges to link ecological processes across scales. Frontiers in Ecology and the Environment, 19(1), 30-38.https://esajournals.onlinelibrary.wiley.com/doi/full/10.1002/fee.2290
MIS611 Information Systems Capstone Assignment Sample
Assessment Stakeholder Requirements Document
Task Summary
This capstone subject encompasses an authentic assessment strategy within a work integrated learning context that delivers a ’real life’ learning experience. You will receive a brief from a case organisation/client
which will form the basis for the three sequential assessments included in this subject. Assessment 1
Stakeholder Requirements Document is the first of three phases in which you, as a team will formulate a group
response to the case organisation/client’s brief.
1. First phase: Assessment 1: In the first phase, you as a team will determine the project approach and
framework, and the requirements of your case organisation/client and complete a 3000-word Stakeholder Requirements Document. Please see below for further details.
2. Second phase: Assessment 2: In the second phase, your group will develop and deliver a prototype solution for the case organisation/client (details as per the Assessment 2 brief).
3. Third phase: Assessment 3: In the third phase, your group will ‘demo’/ showcase your prototype solution to the case organisation/client (details as per the Assessment 3 brief).
You will be required to select a project management approach based on what you believe is the most suitable
approach for your client’s project. In doing so, you will make use of the tools and techniques that are aligned
with the chosen approach including the appropriate requirements lifecycle techniques. Part of this assessment
is also to briefly explain why the selected approach is the most appropriate to meet the needs of your client. In
alignment with your selected project approach and framework, you will need to detail and demonstrate the
requirements methods, tools and techniques that you are using with a justification as to why they have been
selected as the most appropriate.
Caveat: While this subject focuses on three phases of assessment, this does not preclude the selection of an
iterative framework. The structure of the assessment is not one of the characteristics which you should use to
define the selected approach. Also, note that the title of this report specifically does not references typical
document naming conventions within either the traditional ‘waterfall’ approach, nor the Agile approach to
offer you the freedom to make the selection you believe is the most appropriate response to the challenge.
Context
In the field of Information Systems (IS), there are several different frameworks with aligned tools and techniques that can be used to build solutions for organisations. Different frameworks are better suited to
different problems and solutions. For example, the traditional project management approach takes a linear
approach through a sequence of events, while an Agile approach is iterative.
IS leaders need to understand different philosophies and their approaches, their frameworks and the tools and
techniques which they employ. This is so that they can make discerning decisions when selecting approaches
to solve problems for the business. A key outcome of this series of sequential assessments will be for you to
demonstrate your skills in selecting an approach with reasoning and justification, and then follow through by
using the appropriate methods, tools and techniques as a simulation of a real solution delivery for a case
organisation/client.
Task Instructions
1. Team Formation and Registration
• Form teams of 5-6 members.
• The deadline for team registration is 11:45pm AEST Friday end of Module 1.2 (Week 2).
• To register your team, you are required to send your Learning Facilitator an email with “[MIS611] Team Registration” in the subject line. In the body of that email, please list the names and student ID numbers of all the members of your team.
• You are required to send the registration email to your facilitator before the registration deadline.
• After the registration deadline, those students who are not in a team will be allocated to a team by the Learning Facilitator.
2. Please read the case organisation/ client’s brief provided by the Learning Facilitator.
3. Write a 3000 words stakeholder requirements document outlining the project approach and framework, and the requirements of your case organisation/client.
4. Review your subject notes, from across the course, to establish the relevant area of investigation that applies to the case. Re-read any relevant readings for this subject. Plan how you will structure your ideas for your report and write a report plan before you start writing. You may like to start with MIS608 Agile Project Management and PROJ6000 Project Management.
5. Graphical representation of ideas and diagrams in the form of tables, graphs, diagrams and modelsare encouraged but must be anchored in the context of the material, explained, and justified for inclusion. No Executive Summary is required.
6. The stakeholder requirements document should consist of the following structure:
A title page with the subject code and subject name, assignment title, case organisation/client’s
name, student’s names and numbers and lecturer’s name.
A Table of Contents is mandatory for this assessment (Create the Table of Contents using MS Word’s
auto-generator. Instructions can be found here https://support.office.com/en-gb/article/Create- a-
table-of-contentsor-update-a-table-of-contents-eb275189-b93e-4559-8dd9-
c279457bfd72#__create_a_table).
Introduction: This must include background information about your case organisation/client as a business from quality sources, and any information about the S direction or strategies that you can gauge from the trade press or news articles. (375 words)
The brief: In this section you must describe and explain your interpretation of the case organisation/client’s brief to you. You are required to outline the following areas:
a. The problem area/scope of the project. (150 words)
b. The objectives of the project using SMART goals. (150 words)
c. The target audience for whom your solution is being defined. (225words)
d. Critical Success Factors. (75 words)
A description of the project: the approach that you will be taking and the associated framework with a justification as to what characteristics of this project informed your selection of this approach. (375 words)
A stakeholder map which identifies key stakeholders, assessing stakeholder interest and how the project will address those interests. (75 words)
The data collection strategy used to elicit requirements - both primary and secondary, quantitative, and qualitative methods and tools in alignment with the project approach. (750 words)
Appropriately documented functionality that will need to be developed in your solution prototype. These may be business and functional requirements, or user stories depending on your selected approach. (750 words)
A clear problem statement to guide the solution process. (35 words)
Next steps to be taken in progressing to your solution prototype. (40 words)
References according to the APA style. (Not part of your word count)
Appendices - if required. (Not part of your word count).
Introduction
The study has helped in understanding the ways in which money can be reinvented in 2050 in India and the target audience that has been considered is entire India. United Nations in conjunction with International Monetary Fund (IMF) have identified that by 2050 cash will not be available and IMF has thought of reinventing money for different countries (Auer, Cornelli& Frost, 2020). The study has focused on ways in which Central Bank Digital Currency (CBDC) can be implemented within India’s manufacturing industry such as automobile manufacturing. There are various ways through which CBDC can be implemented (De Lis& Sebastián, 2019). Central Bank Digital Currency (CBDC) has been referred to the virtual form of fiat currency and is considered as the digital token of a currency of a nation (Kumhof&Noone, 2018). The suggested product for development of cashless society is the designing of a mobile application through which the payment or transaction can be done digitally. It helps in making the payment in terms of digital currency that will be regulated and released by the central Bank of India. CBDC comes in the form of banknotes and coins along with being used for doing sales as well as purchasing goods. CBDCs are implied so as to present fiat currency and also according to convenience of the users. There will be presentation of security of digital along with having a well-regulated and reserve-backed circulation of the traditional banking system (Auer &Böhme,
2020). It has been observed that there are various types of Central Bank Digital Currencies (CBDCs) and they are Wholesale CBDCs in which the existing tier of banks as well as financial institutions goes for settling transactions.
Brief of the Study
Problem Statement
In the 21st century, cashless society is still a dream however, it is supported by the growth of reinvesting money. It has become difficult to access the transactions of capital in between manufacturing companies with speed (Thequint.com, 2021). There is also the threat of not been able to keep an account of the money being transferred in huge project deals in between manufacturing companies such as Tata, Bajaj. Another problem that will be solved by CBDC in India is that the reliance of the country on cash will be lowered. It has been observed that the Reserve bank of India (RBI) has thought of action plans through which CBDC is going to belaunched in phased manner (Thequint.com, 2021). It will help in solving the problems of getting efficient in international settlements and also achieve smooth functionalities. It will also help in protecting people from the volatile nature presented by cryptocurrencies. Thus, there are problems associated with uncertainties of cryptocurrencies which can be solved with the introduction of CBDC and also cashless society will take place (Thequint.com, 2021). CBDC can be considered as a virtual currency, however, is not comparable with the private virtual ones such as Ethereum or Bitcoin. In India, there is problem associated with dwindling usage of paper currency and there are various jurisdictions associated with physical cash usage (Yanagawa& Yamaoka2019). Central Banks have sought to mee the need of public for having digital currencies and reinvent money through making a cashless society. This problem can be overcome through the help of developing a mobile application through which the digital payment system can be initiated. It has to be linked with the bank account and mobile registration number.
Smart goals
Areas Goal 1: To reduce the dependency on cash
Goal 2: Decrease the settlement risks
Goal 3: To make the transactions using CBDC secure Specific This goal is specific with having a cashless society implemented through help of Central Bank Digital Currency (CBDC) This is specific since with help of CBDC in a country like India, transactions with foreign nations will be easily done This is specific as calibration of the privacy features of CBDC system can be done Measurable It is measurable by
estimating the total
number of usages of
CBDC and digital
currencies by the
population of India
It is measurable through
the help of counting the
reduction of risks that
happens
This is measurable by
estimating the efficiency
of the calibrated system
Attainable It is attainable through
the introduction of
either value-or cash-
based access and
Token-or account-
based access
It is attainable through
engaging in retail as
well as whole sale
CBDCs and also
introduce it within the
manufacturing hubs
It is attainable through
the introduction of a
calibrated privacy feature
and preserve privacy
through making the
transactions
pseudonymous
Relevant It is relevant since there
is huge pressure on
transactions using cash
It is relevant since there
are various foreign
companies with which
India does business
It is highly relevant as
disbursement happens
through third parties and
require security
Time Period By 2050 By 2050 as the project
of introduction of CBDC is happening in
phased manner
Target Audience
It is worth mentioning that all are living in a cashless society therefore it is our responsibility to contribute to the development of reinventing of money at a large platform. As per the views of Wasieleski & Weber (2017), the internal stakeholders include management, employees, shareholders, investors, and the company itself. Moreover, the management will be able to perform the manufacturing processes and other activities inside the organisation (Seiffert- Brockmann et al., 2018). The target audience consisted of the whole of India. The Digital
currencies issues by the CBDCs are also beneficial in decreasing the effort of Government functions along with ensuring the fact that distribution of benefits as well as tax collection becomes easy. Thus, with help of CBDC ai din going cashless entire India will be benefitted. An Empathy Map can be used to capture the behavior of the user and attitude towards the introduction of a new system or a product. Empathy Mapping has been observed to be beneficial at the beginning of the design process after the user research is done, however, has to be performed prior of getting the requirement as well as conceptualization done. There are certain categories in which an empathy map can be divided and they are what the user says, thinks, feels
and does. [refer to appendix 2] Persona Mapping: Persona Mapping is the process through which it is identified who are the clients and ways in which decisions are being made. The information obtained can be used in making more effective strategies. [refer to appendix 1] Critical Factors of Success
The critical factors of success are measured as follows:
? The proper identification of problem
? Development of the scope for cashless society
? Reinventment in money through CBDCs help to support the development of a cashless society which is beneficial for making the world a technologically developed place.
? The focus on serving for the good of the society and the employees by eliminating the risk of cyber-attacks as well as network vulnerabilities on the transaction of money through digitized system.
Description of the Project
The project is about developing a mobile application through which the CBDC system will ne initiated. The application will be the gateway for making the payment using digital currencies released by the Bank and Government of India. A CBDC or Central Bank Digital Currency system as a result or solution has been identified to be overcoming the issues. A CBDC is a legal tender that is issued by central Bank in digital form (Auer, Cornelli& Frost, 2020). It can be compared or is similar to fiat currency, however, the form is different. The project has been different from that of Bitcoin or any other private virtual currency as it has no issuer, however, in this case, this problem of lack of security is overcame as Central Bank of the country is the
issuer. The product prototype will be designed that will help the individuals in getting the access to digital currencies regulated by RBI. The reason behind taking participation in the project is that with help of introduction of CBDCs the implementation of the monetary policy and government functions become easy (De Lis& Sebastián, 2019). It has been identified to be automating the process of transactions that will take place in between financial institutions and wholesale CBDCs (Kumhof&Noone, 2018). The project will also consider the calibration of the CBDC system.
Therefore, the double diamond theory will be the most applicable and relevant theory.
According to the comment of Gunarathneet al., (2018), double diamond theory always provides a static structure to identify all the potential challenges with the help of four different phases. All those phrases are discovered, defined, developed and delivered. The first phase always helps to identify the exact problem. The second phase helps to determine which area should focus upon.
The third face helps to ensure the potential solutions to mitigate the challenge. The last phase
helps to implement the solution.
Figure 3: Framework of Double Diamond Theory (Source: medium, 2021)
? Discover
In the discover stage as it is stated that the problems are identified appropriately and then the solutions are defined in subsequent stages. It has been identified from the research done that there has been increase in pressure or increased dependency on cash in India. There is also theproblem of higher seigniorage due to the lower value or cost associated with transactionsKumhof&Noone, 2018). The settlement risk associated with transacting through capita is also high. It has to be minimized through the help of using cashless medium if
transactions and is possible through help of Central Bank Digital Currencies (CBDCs) in a country such as India. There is also requirement of meeting the requirements of Indian public regarding digital currencies by the Central Banks of India and this issue has increased with the increase in manifestations of private virtual currencies (Thequint.com, 2021). India has been the leasing the world in terms of digital payment innovations and the payment system has been observed to be available 24/7. Thus, the problem of increasing usage of paper currency needs to be solved with the help of using CBDCs and focus is on developing an electronic form of currency.
? Define
The prototype that will be developed will help the Indian society and the various business happening within it to go for transactions without the need of physical bank notes. The prototype that will be considered is that of making of Fiat money which are introduced by the financial institutions of India. It gets introduced in the form of banknotes and coins (Barontini& Holden, 2019). The CBDC that will be formed is the virtual form of the fiat money and also is going to have the back up support of Indian Government. The mobile application developed will be in synchronization and the digital currency can be used as long as the individual have equivalent cash or money in the bank. The prototype will be designing two variants of CBDCs and this consists of Value or cash-based access as well as Token or account-based access. The system of Value-or cash-based access will be made to pass onto the recipient through help of a pseudonymous digital wallet (Auer, Cornelli& Frost, 22020). Wallet will be made identifiable through the help of a public blockchain. Another prototype that can be designed is that of cash- based access for Indian population (Kochergin&Yangirova, 2019). The process gets initiated similar to that of the access provided by a financial institution account to its users. It has been observed that an intermediary is responsible for verification of the identity of the recipient and will also monitor the illicit activities
Stakeholders Map
Stakeholders Interest Engagement Strategy Indians High More involvement within the banking system and easy transfer of fund Employee High Accessing and utilizing all the components for keeping a track of the cashless transactions Investors Medium Maintaining all the legal and transaction ethics before
accessing the plan Shareholder Low Gather all the potential investors and influence them for corporate decision making regarding the reinvention of money Retailers, business persons and manufacturers
High They will be doing the payment using CBDCs and hence, business can be done with foreign companies
easily
Table 2: Stakeholders Map
(Source: Created by Author)
Data Collection Strategy
It is worth mentioning that the strategy of collecting data is the most crucial factor that has been taken into consideration but the results were performing the study. The strategy which has been selected for gathering the pertinent sources of data influences the factors of quality and authenticity of the report. According to the opinion of Vales (2020), there are major two sources with the help of which the data and information regarding the study can be collected and evaluated by the analyst. The researcher has to choose between these two Strategies for obtaining the relevant sources of information that can be used to make the study effective and informative. The primary strategy for collecting data has also been known as the gathering of raw data. Such
type of information and data has been collected by the research investigator for a specific study (Primary data collection, 2020). In this study, the focus of the research analysis is to obtain valuable information, data, and statistics that can define the importance of reinventing money for the development of cashless society for Tata Motors that can eliminate the negative impact of covid-19 on its manufacturing and business activities
Figure 4: Data Collection Strategy
(Source: Created by Author)
The primary strategy has also been divided into two types that are primary and quantitative primary qualitative. According to the words of Franzitta et al., (2020), it has been found that primary quantitative refers to the statistical evaluation of the data and information gathered by the researcher. Mostly the investigator performs a survey for doing the primary quantitative research. For the survey, the researcher designs a questionnaire that includes a number of questions that specifies the close-ended questions that are filled by the respondent that supports the research topic. Each of the respondents fills the question as per the best knowledge
experience. After the completion of gathering responses provided by the respondents, the researcher evaluates and analyses the result by various methods such as SPSS software or Excel sheet. As per the views of Wilson & Kim (2021), it is worth mentioning that for performing the primary qualitative study, the researcher mostly conducts an interview process which can help to gain information and knowledge regarding the research topic by interviewing the associated people with the research topic. In this study, the associated people are the employees, management, customer, investors, and shareholders.
Similarly, the secondary strategy for collecting the information and data focuses on addressing and evaluating the work of other researchers and investigators that work on a similar topic. As per the comment of Talbert (2019), this will help the researcher to understand the perspective of other analysts that can show their views regarding the importance of reinventing money. It has been identified that the secondary method of obtaining the data is more economical than the primary strategy. It has been said so because during the process of collecting the first handed information the investigator has to spend more time, effort, and money for collecting the data. It also includes the transportation cost and the survey, interview cost.
However, it has been found that for implementing the secondary strategy a researcher has to adopt the secondary qualitative study. As per the guidance of Haenssgen (2019), it has been observed that the secondary qualitative study is on developing relevant themes based on which the researcher can support their findings and evaluation in the study. After evaluating the benefits and rules of working of both the primary and secondary qualitative and quantitative data, the researcher will implement the secondary qualitative research for gathering valuable and authentic resources of the secondary database.
Documented Functionality
In this section, all the business and functional requirements that will help manufacturing companies to implement the cryptocurrency enabled cashless transaction is going to be discussed. All the potential functional requirements that the management of this organization will have to perform is to arrange some meetings with all the responsible employees and managers and discuss the comparison between the cashless modes of transactions (Auer&Böhme, 2020). It is worth mentioning that effective strategies should be implemented in order to identify the potential challenges that may impact the productivity and growth of cashless infrastructure (Kumhof& Noone,2018). After that identifying all the potential shareholders and
influencing them for this plan willbe the next functional requirement. According to the opinion of Marques et al., (2018), identifying all the investors with a proper determination regarding this plan will be one of the most important functional requirements of shareholders. There are certain examples of Central Bank Digital Currencies (CBDCs) that can be given and it has been observed that the Central Banks have initiated various pilot programs (Kumhof&Noone, 2018).
India can take inspiration from the fact that China has introduced digital yuan. Russia has also created the CryptoRuble and similar technology can be deployed within India to make the society cashless. India will require to have a digital version and the banks will be converting a part of their holdings into digital form. The digital monetary or the capital will be distributed to various business organizations and people of the country through help of mobile technology (De Lis& Sebastián, 2019). It can be observed that the largest difference in between cryptocurrencies and CBDC is that of the legal status as the later is more secured. Indian population will be benefitted as CBDC can be used as a payment mechanism and will be considered as an acceptable ledger system. In addition to this, CBDC will provide the advantage of being governed by Indian Government and is not anonymous.
There are two types of functionalities through which the CBDCs can be developed and they are Wholesale as well as Retail Central Bank Digital currencies. It can be stated that the Wholesale CBDCs uses the existing tier of banking as well as financial institutions so that transactions can be settled. This type of CBDC has been considered as traditional central bank reserves. The type of CBDC transaction that can be possible is that of interbank payment and transfer of capital takes places in between two financial institutions (De Lis& Sebastián, 2019). With help of CBDC, the process of cross-border transfer as well as automation is possible. There is also Retail CBDCs that involves transfer in between financial institution. The CBDC process that will be developed in India at first is that of retail one in which there is replacement of cash (Kumhof&Noone,2018). There must be caps imposed on the CBDC so that the banks are saved from having drainage of liquid fund. Digital tokens will be given to bearers and hence, identity verification will be conducted in an effective manner.
Conclusion
Thus, it can be concluded that this entire report has been formulated to describe a suitable reinvention plan of money by 2050. The target audience is the entire population of India and it has been observed that they will be benefitted with the help of CBDC as involvement within the banking system will get improved. It has been observed that with help of CBDC, the pressure on the use of physical notes will get decreased and also the drainage of liquid capital from banking sector will be removed. Furthermore, it can be stated with help of CBCD, there will be safer transaction of assets across borders and the system developed will be mainly token-based in the initial stage and then it can be developed in a hybrid model.
Reference List
Thequint.com, (2021), What is CBDC? Why Do We Need It in India?,https://www.thequint.com/explainers/explained-what-is-cbdc-why-do-we-need-it-in-india
Yanagawa, N., & Yamaoka, H. (2019). Digital Innovation, Data Revolution and Central Bank Digital Currency (No. 19-E-2). Bank of
Japan.https://theblockchaintest.com/uploads/resources/Bank%20of%20Japan%20-%20Central%20Bank%20Digital%20Currency%20-%202019%20-%20Feb.pdf
Auer, R. A., Cornelli, G., & Frost, J. (2020). Rise of the central bank digital currencies: drivers,approaches and technologies (No. 8655). CESifo Working Paper.https://www.econstor.eu/handle/10419/229473
De Lis, S. F., & Sebastián, J. (2019). Central Bank Digital Currencies and Distributed Ledger Technology. https://www.bbvaresearch.com/wp-content/uploads/2019/11/Banking-Lab-DLT-CBDCs_edi.pdf
Kumhof, M., &Noone, C. (2018). Central bank digital currencies-design principles and balance sheet implications. https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3180713
Auer, R., &Böhme, R. (2020). The technology of retail central bank digital currency. BIS Quarterly Review, March. https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3561198
Barontini, C., & Holden, H. (2019). Proceeding with caution-a survey on central bank digital currency. Proceeding with Caution-A Survey on Central Bank Digital Currency (January 8, 2019). BIS Paper, (101).
https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3331590
Kochergin, D. A., &Yangirova, A. I. (2019). Central bank digital currencies: key characteristics and directions of influence on monetary and credit and payment systems. Finance: theory and practice, 23(4),8098.
https://financetp.fa.ru/jour/issue/download/51/23#page=75
Desmond Dawes, G., & Davidson, A. (2019). A framework for developing justice reinvestment plans for crime prevention and offender rehabilitation in Australia’s remote indigenous communities. Journal of offender rehabilitation,58(6),520543.https://researchonline.jcu.edu.au/58765/1/A%20framework%20for%20developing%20justice%20reinvestment%20plans%20for%20crime%20prevention%20and%20offender%20rehabilitation%20in%20Australia%20s%20remote%20indigenous%20communities.pdf
Franzitta, V., Longo, S., Sollazzo, G., Cellura, M., &Celauro, C. (2020). Primary data collection and environmental/energy audit of hot mix asphalt production. Energies, 13(8), 2045–2045.
https://lesa.on.worldcat.org/v2/oclc/8582369766
Gomes, P., Mendes, S. M., & Carvalho, J. (2017). Impact of pms on organizational performance and moderating effects of context. International Journal of Productivity and Performance Management, 66(4), 517–538.
https://doi.org/10.1108/IJPPM-03-2016-0057
Gunarathne, A. N., & Senaratne, S. (2018). Country readiness in adopting Integrated Reporting:
A Diamond Theory approach from an Asian Pacific economy. In Accounting for sustainability: Asia Pacific perspectives (pp. 39-66). Springer, Cham. https://link.springer.com/chapter/10.1007/978-3-319-70899-7_3
Haenssgen, M. J. (2019). Interdisciplinary qualitative research in global development : a concise guide (Ser. Emerald points). Emerald Publishing Limited. Retrieved October 4, 2021, from INSERT-MISSING-URL. https://lesa.on.worldcat.org/v2/oclc/1128408880
Marques, T., Nguyen, J., Fioreze, G., &Petreanu, L. (2018). The functional organization of cortical feedback inputs to primary visual cortex. Nature Neuroscience, 21(5), 757–764.https://doi.org/10.1038/s41593-018-0135-z
Primary data collection (netherlands-utrecht: research and development services and related consultancy services). (2020). Mena Report, (july 15 2020): Na.https://lesa.on.worldcat.org/v2/oclc/8628905727
Rubin, H. W., &Spaht, C. (2018). Quality Dollar Cost Averaging Investing Versus Quality Index Investing. Journal of Applied Business and Economics, 20(6), 193-200.http://na-businesspress.homestead.com/JABE/JABE20-6/RubinHW_20_6.pdf
Seiffert-Brockmann, J., Weitzl, W., &Henriks, M. (2018). Stakeholder engagement through gamification. Journal of Communication Management, 22(1), 67–78.https://lesa.on.worldcat.org/v2/oclc/7294428031
Sharma, D., & Swami, S. (2018). Information Security policies Requirement in Organization. International Journal on Future Revolution in Computer Science & Communication Engineering, 4(1), 431-432.
https://www.ijfrcsce.org/index.php/ijfrcsce/article/download/1036/1036
Talbert, E. (2019). Beyond data collection: ethical issues in minority research. Ethics & Behavior, 29(7), 531–546.https://lesa.on.worldcat.org/v2/oclc/8260802315
Tata motors: wheelspin. (2018). Financial Times, 10, 10–10. https://lesa.on.worldcat.org/v2/oclc/7908714374
Vales, M. (2020). Primary data collection for language description and documentation. Etudes Romanes De Brno, 41(1), 87–98. https://lesa.on.worldcat.org/v2/oclc/8650347961
Wasieleski, D. M., & Weber, J. (Eds.). (2017). Stakeholder management (First, Ser. Business and society 360). Emerald Publishing Limited. Retrieved October 4, 2021, from INSERT-MISSING-URL.https://lesa.on.worldcat.org/v2/oclc/988757040
Wilson, C., & Kim, E. S. (2021). Qualitative data collection: considerations for people with aphasia. Aphasiology, 35(3), 314–333. https://lesa.on.worldcat.org/v2/oclc/8929382816
MITS5501 Software Quality, Change Management and Testing Assignment Sample
IT - Research Report Assignment 2
Assignment Brief
Objective(s)
This assessment item relates to the unit learning outcomes as in the unit descriptor. This assessment is designed to improve student presentation skills and to give students experience in researching a topic relevant to the Unit of Study subject matter.
INSTRUCTIONS
For assignment help, in assignment 1 you were required to do a 10-13 minutes’ presentation on a recent academic paper on on Software Quality, Software Change Management or Software Testing.
Assignment 2 requires writing a report or critique on the paper that you chose in Assignment 1 to Presentation and Participation component above.
Your report should be limited to approx. 1500 words (not including references). Use 1.5 spacing with a 12-point Times New Roman font. Though your paper will largely be based on the chosen article, you should use other sources to support your discussion or the chosen papers premises.
Citation of sources is mandatory and must be in the IEEE style.
Your report or critique must include:
Title Page: The title of the assessment, the name of the paper you are reporting on and its authors, and your name and student ID.
Introduction: Identification of the paper you are critiquing/ reviewing, a statement of the purpose for your report and a brief outline of how you will discuss the selected article (one or two paragraphs).
Body of Report: Describe the intention and content of the article. If it is a research report, discuss the research method (survey, case study, observation, experiment, or other method) and findings. Comment on problems or issues highlighted by the authors. Report on results discussed and discuss the conclusions of the article and how they are relevant to the topics of this Unit of Study.
Conclusion: A summary of the points you have made in the body of the paper. The conclusion should not introduce any ‘new’ material that was not discussed in the body of the paper. (One or two paragraphs)
References: A list of sources used in your text. They should be listed alphabetically by (first) author’s family name. Follow the IEEE style.
The footer must include your name, student ID, and page number.
Note: Reports submitted on papers that are not approved or not the approved paper registered for the student will not be graded and attract a zero (0) grades.
What to Submit
Submit your report to the Moodle drop-box for Assignment 2. Note that this will be a turn- it-in drop box and as such you will be provided with a similarity score. This will be taken into account when grading the assignment. Note that incidents of plagiarism will be penalized. If your similarity score is high you can re-submit your report, but resubmissions are only allowed up to the due date. If you submit your assignment after the due date
and time re-submissions will not be allowed.
Note: All work is due by the end of session 9. Late submissions will be penalized at the rate of 10% per day including weekends.
On Time Days Late _______Turn-it-in Similarity % _______
Solution
Introduction
The purpose of this report is to critically review the academic article identified in assessment-1. The chosen academic paper is on “AZ-model of software requirements and change management in global software development” which belongs to the course unit: “Software quality and Change Management”.
It has been possible for an individual researcher to discuss the selected article in following sections: Reviewing the Literature Survey; Critically reviewing the Proposed AZ-model; Undertaking a research method to collect data, information relevant to the topic; Discussion based upon the results and finally find the outcomes of the research report.
Literature Survey
This section is one of the major parts of this research report. Here, the researcher critically reviews the chosen academic paper and compares it with other similar papers.
Review of the Chosen Academic Paper
This paper indicates information about Requirements Change Management (RCM) and Global Software Development (GSD). Due to the lack of information communication, changes of customers’ demands, changes in management strategies might be required. With a centralised software development system, an organisation can improve its poor requirements management [7]. This literature is a proposed study of the AZ-model which has been explored through RCM & data collection process. Use of tools, technologies have been preferred here with various methods and tactics.
Comparison Literature I: Empirical investigation of barriers improvement in GSD
According to ([7]), this paper supports the chosen academic article and provides information for critical review. Capability Maturity Model Integration (CMMI) has been represented here with Initiating (I), Diagnosing (D), Establishing (E), Acting (A), and Learning (L)- IDEAL approach. During the research and review, Software Process Improvement Capability Determination (SPICE) has been recommended.
This research is a key context of supply chain management (SCM) which is a process improvement activity for GSD context. Planning, Conducting, and Reporting are the three phases of this research paper that added value to the software development model [7].
Comparison Literature II: Use of RE Tools in Global Software Engineering
As per the ideas of ([8]), this paper indicates requirements engineering (RE) tools for GSD. To support the literature survey of the chosen paper, this paper has been valued. In this study, the concept of Global Software Engineering (GSE) was also introduced. The objective of the paper is to support the chosen academic article with the concepts addressed in a different perspective. In the global software development market, the demand for changing the environment is high. Thus, evolving RE tools in GSD is an important aspect [2].
On the other hand, as per the International standard of software development, to achieve the effectiveness in requirements management, following steps to be followed which are: Change proposal, Review, Approval, Change notification. To change the market requirements as per the customers’ demand is a necessary and standard guideline for GSE [8].
Research Methodology
To continue with the research paper review, research methodology has been determined as a major section/part of the assessment [1]. In order to achieve the research problem and project objectives, it has been possible for the researcher to set research questions (RQs) and try to solve this by the end of this section.
? RQ1: How to propose the AZ-model of software requirements?
? RQ2: What is change management in GSD?
? RQ3: Which types of research methods seem suitable for this paper?
? RQ4: How to address the literature concept and analyse the data based on results?
To solve these RQs and propose the AZ-model of RCM in GSD, secondary data has been collected. The data are relevant to the research topic phase and sufficient to implement the AZ-model [2].
Collection of Data
Data collected in the form of questionnaire & survey [3]. Use of lightweight software development methodology in favour of heavyweight software development methodology has been proposed here. With the help of a project management research method, the AZ-model of RCM can be implemented. Moreover, Project manager is engaged to carry out development activities of the proposed AZ-model. Considering the Project management factor, it has been possible to set survey questions and answer accordingly.
Based on the perspective of ([7]), Software Development Methodology (SDM) refers to this AZ-model and is applied to collect data from survey respondents.
Figure 1: Sample Collected Data
Proposed Model
In this section, researchers are going to propose a model based on the empirical study and questionnaire survey [4]. Delay of one site effects in the proposed model implemented in six different areas of project management. Moreover, a six-pointed star model has been introduced here based on the guideline of Project Management Body of Knowledge (PMBoK).
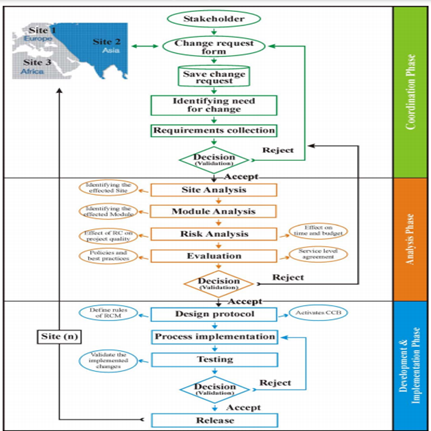
Figure 2: Proposed AZ-model of RCM
(Source: [7])
Findings and Analysis
From the collected database, it has been observed that, AZ-model can be implemented successfully if the GSD and PMBoK requirements have been fulfilled. The major findings of this academic paper are as follows:
? Workflow and Change Management
It is an important category that has been featured for global software development. In the case of GSD, high-awareness among the team is required for effective communication and model implementation [5]. However, multiple user access and collaborative life cycle management are the key approaches of software development and meeting change requirements. Regarding this, collaborative life cycle management and global stakeholder collaboration has been prioritised.
? System and Data Integration
In this case, the AZ-model framework can be implemented considering data import, data export and tool integration. System and data integration category focuses on the data collection & resources, RE and proposed AZ model [6].
? Shared Knowledge Management
The selected academic paper is useful for supporting stakeholders’ decisions, multiple user access and collaborative life cycle management. On the other end, for GSD it is necessary to introduce global stakeholders’ collaboration.
? Traceability
This is an important category featured by the GSD [1]. Flexible tracing, bi-directional tracing and traceability analysis are the key aspects of the AZ-model implementation and software development. Throughout the implemented software development lifecycle traceability seems to be a vital resource factor.
Issues addressed
While conducting systematic literature review (SLR) of the chosen article, several issues/barriers have been addressed [2]. Due to lack of organisational support and lower level of management, sometimes software development and change management has not been possible. Moreover, during the AZ-model implementation, non-availability of sufficient resources could be a major issue. Lack of client management support, lack of awareness towards the change management environment badly impacted on the GSD attributes.
Due to communication difficulties with the stakeholders the software requirements and change management may lead to misinterpretation [3]. Vital issues with the AZ-model implementation are popularly known as cross-cultural barriers among GSD organisations. Furthermore, an individual researcher faces lack of resources while reviewing this academic paper which is also a barrier. PMs were hesitant to allocate proper budget, financial support in terms of implementing the AZ-model.
Results and Discussions
This section shows the results of the proposed model and collected data in statistical form. Summarizing the data and relevant results of the six-pointed star model is the main objective of this part [4]. Researchers are prioritising the literature survey responses and evaluating the responses. To analyse the significance of the AZ-model, it is necessary to value the average, higher, and low percentage of the results from survey responses. Moreover, the evaluation criteria with the RE tool shows the performance features of the AZ-model. To analyse the results and discuss the relevant factors, a shared knowledge management and investigation method has been applied [7].
It has been possible for an individual researcher to identify and evaluate the outstanding score (CFI) from the collected database. However, in order to address the RQs, issues to be resolved on an immediate basis. On the other hand, while executing the GSD and change requirements for AZ-model, the survey data (positive/ negative/ neutral responses) are valued [5]. Significant differences observed during analysis of the results from the collected database. Categorizing the issues in a robust framework has also been valued for software process improvements. Demonstrating the Likert-scale value from the SLR exhibits in the form of results. Last, but not the least, from the proposed AZ-model and analysing the critical barriers researchers are able to modify the framework as per requirement [7].
Conclusion
After critically reviewing this academic article, how most of the software development organisations get facilities of AZ-model can be observed. Moreover, how this model can be useful in future work has also been understood from this academic paper. This paper demonstrates the key issues of AZ-model implementation and recommended for client & vendor management. How the RE tools become an advantage of GSD and AZ-model implementation has been analysed from this study [8].
In the future, global software management seems to be relevant for AZ-model implementation and featuring the gaps identified during the process improvement. Supporting features of GSD may be unsoundly obtained for the system integration part. Finally, not yet importantly, this paper provides ideas of traceability, software development, collaboration with the stakeholders and communicating with them for the next stage of change management in software industries.
References
[1] A.A. Khan, J. Keung, M. Niazi, S. Hussain and A. Ahmad, “Systematic literature review and empirical investigation of barriers to process improvement in global software development: Client–vendor perspective”, Information and Software Technology, vol. 87, pp.180-205, 2017. Accessed on: July 30, 2021. [Online]. Available: https://www.researchgate.net/profile/Arif-Khan23/publication/315382990_Systematic_Literature_Review_and_Empirical_Investigation_of_Barriers_to_Process_Improvement_in_Global_Software_Development_Client-_Vendor_Perspective/links/5b4d651ea6fdcc8dae246cc7/Systematic-Literature-Review-and-Empirical-Investigation-of-Barriers-to-Process-Improvement-in-Global-Software-Development-Client-Vendor-Perspective.pdf
[2] C. Djoweini, “The driven parameters of Software Development Projects”, 2019. Accessed on: July 31, 2021. [Online]. Available: https://www.diva-portal.org/smash/get/diva2:1371926/FULLTEXT01.pdf
[3] E. Serna, O. Bachiller and A. Serna, “Knowledge meaning and management in requirements engineering” International Journal of Information Management, vol. 37, no. 3, pp.155-161, 2017. Accessed on: July 31, 2021. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S0268401216306582
[4] J. Band and M. Katoh, Interfaces on trial: Intellectual property and interoperability in the global software industry, Routledge, 2019. Accessed on: July 31, 2021. [Online]. Available: https://www.taylorfrancis.com/books/mono/10.4324/9780429046841/interfaces-trial-jonathan-band-masanobu-katoh
[5] K. Curcio, T. Navarro, A. Malucelli and S. Reineh, “Requirements engineering: A systematic mapping study in agile software development”, Journal of Systems and Software, vol. 139, pp.32-50, 2018, Accessed on: July 30, 2021. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S0164121218300141
[6] M. El Bajta and A. Idri, “Identifying Software Cost Attributes of Software Project Management in Global Software Development: An Integrative Framework”, In Proceedings of the 13th International Conference on Intelligent Systems: Theories and Applications, pp. 1-5, 2020, September. Accessed on: July 30, 2021. [Online]. Available: https://dl.acm.org/doi/abs/10.1145/3419604.3419780
[7] M.A. Akbar, M. Shafiq, J. Ahmad, M. Mateen and M.T. Riaz, “AZ-Model of software requirements change management in global software development”, In 2018 International Conference on Computing, Electronic and Electrical Engineering (ICE Cube) (pp. 1-6), IEEE. 2018, November. Accessed on: July 28, 2021. [Online]. Available: https://www.researchgate.net/profile/Muhammad-Tanveer-Riaz/publication/330387529_AZ-Model_of_software_requirements_change_management_in_global_software_development/links/5cf4a8aa92851c4dd024128d/AZ-Model-of-software-requirements-change-management-in-global-software-development.pdf
[8] S. Yos and C. Chua, “Requirements engineering tools for global software engineering”, In Proc. 13th Int. Conf. Eval. Novel Approaches Softw. Eng.(ENASE), vol. 1, pp. 291-298, 2018, March. Accessed on: July 30, 2021. [Online]. Available: https://www.scitepress.org/Papers/2018/67601/67601.pdf
MIS609 Data Management and Analytics Assignment Sample
Assignment Brief
Individual/Group - Individual
Length - 1500 words (+/- 10%)
Learning Outcomes:
The Subject Learning Outcomes demonstrated by successful completion of the task below include:
a) Demonstrate an understanding of the broad concepts of data management.
b) Demonstrate how to manage data within organizations, teams and projects. Investigate techniques on how to collect, store, clean and manipulate data.
c) Explore data management techniques and apply when and where applicable.
e) Effectively report and communicate findings to a business audience who are not necessarily IT professionals.
Submission - Due by 11:55pm AEST/AEDT Sunday end of Module 2.2.
Weighting - 25%
Total Marks – 100
Task Summary
For this assignment, you are required to write a 1500-word report proposing data management solutions for the organization presented in the case scenario.
Context
Module 1 and 2 explored the fundamentals of data management. This assignment gives you the opportunity to make use of these concepts and propose a data management solution (a pre proposal) for the organization presented in the case scenario. This assessment is largely inspired from Data Management Maturity (DMM)SM Model by CMMI (Capability Maturity Model Integration).
Task Instructions
1. For assignment help, please read the attached case scenario.
2. Write a 1500-word data management pre-proposal for the organization.
3. The pre-proposal should not only discuss the technical but also the managerial aspects (cost, manpower, resources, etc.). Please keep in mind that you are writing a pre-proposal and not a detailed proposal.
4. Please ensure that you remain objective when writing the pre-proposal.
5. You are strongly advised to read the rubric, which is an evaluation guide with criteria for grading your assignment. This will give you a clear picture of what a successful pre-proposal looks like.
Referencing
It is essential that you use appropriate APA style for citing and referencing research. Please see more information on referencing here: http://library.laureate.net.au/research_skills/referencing
Submission Instructions
Submit Assessment 1 via the Assessment link in the main navigation menu in MIS609 Data
Management and Analytics. The Learning Facilitator will provide feedback via the Grade Centre
in the LMS portal. Feedback can be viewed in My Grades.
Case Scenario
You are a Business Development Manager in a large Information System Support organization that provides data management solution for various clients in Australia. Your organization enjoys a very good repute for its services and is rated exceptionally well in the business community.
You are tasked by your supervisor, Vince Sutter, the president of the organization, and your direct supervisor, to write a service proposal for a new client. The new client of your organization is potentially a large private school that offers online schooling services to students who are at remote locations. This school has almost 2300 registered students from all over Australia from Year 1 to 10. Like your organization, this school also enjoys a very good reputation and is ranked as one of the best online schools based on the students’ and parents’ feedback.
John Brown, the school principal, is a forward-thinking man. He wants to ensure that the school should optimize its operations and keep improving in every way possible. Given the fact that the school has a large number of students and it is continually growing as a market leader, John Brown sees an opportunity for improvement. Brown now wishes that the school staff would focus more and more on learning and teaching, which is the core function of the school. To generate better focus, he and the school’s Board of Directors opt for managed services. They plan to outsource the school’s data management function to a reputed organization that is capable of managing the school’s data. Brown searches for a data management company and comes across your organization. He meets Vince Sutter and asks him to submit a pre-proposal for the school’s complete data management.
Solution
Introduction
The Business Development Manager holds the responsibility of preparing this pre-proposal report as they need to provide optimum data management solutions. This organisation is looking forward to working with the next potential client, which is a large private school well known for its actions so that online education in the distant locations of Australia can be included as well. This pre-proposal report is going to discuss both the technical aspects as well as the managerial aspects like cost, resources etc. This paper shall state the strategy which will help in management and communication of data to meet project objectives. The data of the school that the organisation will have to handle will also need effective ways of management and that will also be discussed in the report.
Aim and Objectives
The aim of this pre-proposal report is to find and analyse certain data management solutions and decide the most effective approach towards managing the data of the large private school, which is the next potential client of the organisation.
? To promote online education in the remote areas of Australia, and thus it is in the best interest of the organisation to get into business with the school as soon as possible.
? Both the Information System Support Organisation and the large private school have quite good reputations and thus keeping the reputations intact is also an objective for the parties and must be kept in mind while planning the project.
? To discuss in detail, the solution that is best suited to the needs of the school and will also have the objective to find out and analyse what improvements can be made in the selected solution.
Project background
The project will address the organisation’s need to find an effective data management solution for the data of the large private school. This will also require the organisation to have a solid project plan which will also be addressed in this pre-proposal. Both the organisation and the school have their reputations to uphold too, so it is of utmost importance that the project be mindful of the quality of the deliverables as well as the deadline.
The Information System Support Organisation must devise a concrete project plan so that the data management system can be efficiently implemented. The school has a total of 2300 registered students from various regions of Australia, and thus the organisation needs to keep in mind the quantity of data to handle and also need to be mindful of the regulations of the various regions (Lacy-Jones et al., 2017).
The project will also need to have a brief idea of what solution the organisation wants to implement before collecting and analysing data on various systems so that they can be compared to find the best suited system to the needs of the large private school (Yang, Zheng & Tang, 2017). For ensuring transparency in the project, the data management plan needs to provide the exact methods and avoid confusion while implementation of the project.
The project plan must aim at establishing and implementing an efficient and effective data management system which will be best suited for the purposes of the large private school. The project must also analyse what are the defects in the system that can be improved further so that the systems of data management can also be improved.
Methodology
(a) The data management strategy to be used would depend on the objectives of the school and would need strong data processes to be created. It will also require to search for the best technology and to establish governance on the collected data so that privacy can be protected. Finally, it should also include the proper training of the staff of the school so that they possess basic knowledge on how to use the implemented system (Chen, Lv & Song, 2019). Only after proper training has been done can the implemented system be properly executed.
(b) One of the main methods of data communication is through parallel transmission. The parallel transmission shall prove beneficial as it can transmit multiple bits of data simultaneously through different mediums.
(c) An estimate of ten people would form a specialized team which would manage the data of this school. This team would have the staff who had the experience of installing the system thus making it easier for them to communicate with the school (Babar et al., 2019). All the team members will report to the project manager, who will in turn report everything to the president of the organisation, Vince Sutter.
(d) The organisation will manage the general personal information (like names, emergency contact numbers, blood group, date of birth, etc.) of all the 2300 registered students as well as that of the staff of the school. The organisation intends to manage the entirety of the provided data by implementing an effective data management strategy as mentioned in the former part of this subheading.
(e) The school would need to provide resources like working computers and a working and strong enough network connection in the school for administrative and database related activities.
(h) The data management policy would be set by addressing the policy of operation with its focus on managing and governing the assets of the data collected. This policy will be implemented by forming a specific team within the organisation which is filled with people experts on the policy, so that they can effectively and efficiently implement the data management policy and so that they can also communicate the necessary details to the staff of the school.
(i) Tools like Talend Metadata Manager are best examples of ways to manage the metadata.
(j) Having an efficient structure of organisation, a precise definition of what to expect in the aspect of data quality, implementation of audit processes of data profiling and finally correcting errors will help the organisation to manage the quality of the data.
(k) Questions like whether the implemented system is being used to its maximum potential can be answered effectively by implementing a data management audit. The quality of the data can be assessed by comparing it against meta-data.
(l) The organisation also needs to have an open hotline and an online customer service for their client, i.e. the large private school so that they can state any other requirements or queries that they may have.
(m) Cloud model DAMA-DMBOK 2 can be regarded as one of the best techniques that would meet the needs of the school’s data management system.
(n) Legacy data would be taken care of by evaluating the inventory of the applications provided and by identifying the redundancies in them.
Results and analysis
(f) The project aims at delivering a fully working data management system capable of handling the information of all the 2300 students plus the staff of the school. The organisation will also aim to deliver an expert team to be present on the spot to check the safe delivery of the deliverables. One of the innovative ways for better data management operations is to offer a cloud environment (Jia et al., 2019).
(g) The organisation also aims to provide an expert team to guide and train the staff of the school so that they can become self-sufficient in the general data management operations.
(q) There are many threats involved in the data management process and has to be well managed by the expert system. There are risks involved with confidentiality and privacy that has to be managed by the experts in IT (Zheng et al., 2018). (o and p) The school will get benefits like the presence of experts to guide and instruct the staff of the school and to manage any risks that may occur otherwise. The school might also face certain challenges after the installation of the system. These challenges can be the risk of losing data, the risk of technical errors which can hinder the process of education which is the primary aim of the school.
Conclusion and Recommendations
In order to conclude this pre-proposal report, it is seen that the organisation needs to provide an efficient data management system to a large private school who are hoping to increase the rates of education in the remote areas of Australia through online education. It is also seen that to provide the data management system according to the requirements of the school will require the preparation of a detailed and properly analysed project plan (Mokhtar & Eltoweissy, 2017). The project plan needs to address data quality management, legacy data and various other issues.
As seen from this pre-proposal report, certain recommendations can be made like, although the data architecture and framework can be easily decided and confirmed for the needs of the school, there are always advances in technology, which need to be kept in mind and implemented in the data management system of the school as and when required.
Reference list
Babar, M., Arif, F., Jan, M. A., Tan, Z., & Khan, F. (2019). Urban data management system: towards big data analytics for internet of things based smart urban environment using customized hadoop. Future Generation Computer Systems, 96, 398–409. https://doi.org/10.1016/j.future.2019.02.035
Chen, J., Lv, Z., & Song, H. (2019). Design of personnel big data management system based on blockchain. Future Generation Computer Systems, 101, 1122–1129. https://doi.org/10.1016/j.future.2019.07.037
Jia, K., Guo, G., Xiao, J., Zhou, H., Wang, Z., & He, G. (2019). Data compression approach for the home energy management system. Applied Energy, 247, 643–656. https://doi.org/10.1016/j.apenergy.2019.04.078
Lacy-Jones, K., Hayward, P., Andrews, S., Gledhill, I., McAllister, M., Abrahamsson, B., … Pepin, X. (2017).
Biopharmaceutics data management system for anonymised data sharing and curation: first application with orbito imi project. Computer Methods and Programs in Biomedicine, 140, 29–44. https://doi.org/10.1016/j.cmpb.2016.11.006
Mokhtar, B., & Eltoweissy, M. (2017). Big data and semantics management system for computer networks. Ad Hoc Networks, 57, 32–51. https://doi.org/10.1016/j.adhoc.2016.06.013
Yang, Y., Zheng, X., & Tang, C. (2017). Lightweight distributed secure data management system for health internet of things. Journal of Network and Computer Applications, 89, 26–37. https://doi.org/10.1016/j.jnca.2016.11.017
Zheng, W., Liu, Q., Zhang, M., Wan, K., Hu, F., & Yu, K. (2018). J-text distributed data storage and management system. Fusion Engineering and Design, 129, 207–213. https://doi.org/10.1016/j.fusengdes.2018.02.058
Link followed for format of pre proposal:
https://ethz.ch/content/dam/ethz/main/education/finanzielles/files-de/Guidelines_Preproposal.pdf
MITS4004 - IT Networking and Communication Assignment 2 Sample
Assignment Brief
Due Date: Session 9
Weightage: 10%
Individual Assignment
This assessment item relates to the unit learning outcomes as in the unit descriptors.
L01: Identify the operation of the protocols that are used inside the Internet and use the seven-layer model to classify networking topology, protocol and security needs.
LO2: Evaluate LAN technology issues, including routing and flow control. Explain the difference between switches and routers. Build and troubleshoot Ethernet, Wi-Fi and Leased line networks. Connect networks with routers.
Scenario:
You are a Network and Security Engineer for the ABC Consulting Private Limited, which is a leading network and security provider for the small and medium scaled offices.
Task 1: Your task is to propose a network design for the small scaled company and sketch a basic logical network diagram of the office with 5 departments. You are free to assume:
• Name of the Office and Departments
• Networking Hardware’s such as routers, switches, hubs, modems wireless access points, firewalls etc.
Task 2: Using your expert knowledge on TCP/IP Model and its layers, sketch the TCP/IP protocols and identify at least one protocol used by each layer.
Task 3: At each level of the TCP/IP model, there are security vulnerabilities and therefore, security prevention measures that can be taken to ensure that enterprise applications are protected. As a network and security engineer, your task is to identify the security threats and propose a solution on each layer.
The report should be prepared in Microsoft word and uploaded on to the LMS. The word limit of the report is 2000 words. The report should be a properly constructed as an academic report. The report should include references in IEEE style.
Submission Guidelines for assignment help
The report should have a consistent, professional, and well-organized appearance.
1. Your report should include the following:
? The word limit of the report is 2000 words.
? The cover page must identify student names and the ID numbers, unit details, and the assignment details.
? The assignment must use 12-point font size and at least single line spacing with appropriate section headings.
? In-text referencing in IEEE style must be cited in the text of the report and listed appropriately at the end in a reference list.
2. The report must be submitted in soft (electronic) copy as a Microsoft Word document on the LMS in Turnitin drop box. Assignments submitted on the LMS will only be accepted.
3. Late penalty applies on late submission, 10% per day would be deducted.
4. The assignments will go through Turnitin and plagiarism penalty will be applied.
The report must be submitted in soft (electronic) copy as a Microsoft Word document via the upload link available on Moodle.
Solution
Introduction
The design of the network of the company has 5 departments. The office “GLORE” situated in the US is the small Scale which has 5 departments and the designing of the network is to be done for them. This plan of the organization for the organization should have 5 offices. The workplace "GLORE" arranged in the US is a limited scale which has 5 divisions and the planning of the organization is to be accomplished for them. The report comprises of the organization name GLORE with 5 divisions that are account, innovative work, advertising, client care, and IT.
Furthermore, the availability is finished utilizing a modem, switch, LAN, frameworks, stockpiling framework, centre point, an organization switch, printers, PCs, and so on. For the organization, the requirement LAN network is required as indicated by the need. The availability was used by the utilization of different organization media such as switches, centre, switch, stockpiling worker, firewall, connector, and so on. What's more, preceding to it the managing of the organization beginning initiating from ISP moving to the client. Next, we examined the TCP/IP convention suite and the conventions of the layer along with their graph. And then we considered the security weakness at TCP/IP distinctive layer of TCP/IP, and it enforced us and then we thought of the safety efforts and answers for those weaknesses. TCP/IP convention suite that is layered engineering where every layer has its conventions which are utilized to do the usefulness of that layer. Also, at each degree of TCP/IP observations of security weaknesses were seen and they need safety efforts and afterward new layers of the suite TCP/IP convention suite aren’t secure also it has weaknesses than to have sure about them. The utilization of various controls was run which will lesson the odds of the danger of information misfortune, data spilling, and numerous different issues looked in conventions downside. This report is made in the wake of experiencing the distinctive accessible examination materials and data accessible.
Organizational network design
The planning of the organization is to be accomplished for an occasion overseeing organization "GLORE Events" which has 5 divisions, and every office requires web access for their expert. For their concern of worker's prerequisites and also for the planning of the organization, we require the availability just as the equipment and programming for its arrangement. The association needs to be established and for the installation, the introduction was initiated for receiving of an association from Internet Service Provider(ISP).
ISP provides a source that is the utilization of Modem also afterward utilizing the LAN (Local Area Network). It provides arrangement to receive the admittance to the public organization and interfacing Router along with it that requires introduction in the organization. It also posts that utilizes links, we will append an organization switch with it. And then afterward frameworks of every division will be associated with that Switch and will have the option to operate it through the data and added to the stage to speak with different frameworks. From the earliest starting point the establishment for the association is needed from the Internet Service Provider that is ISP. At that point to receive the network modem is associated utilizing the NIC and the available links which were getting the signs also the utilization of LAN installed preceding to the modem and traced with firewall. Router is also associated which is giving the availability utilizing Wi-Fi and through Ethernet is associated with switch/center also.
Router is also associated with the capacity worker for the handling of the correspondence. Also, as the organization GLORE Events has 5 offices so the Switch is associated with 6 frameworks through the link.
One for every division and one concerning the principle office sort of a worker and now the plan of the fundamental rational network association: [6]
Figure 1 NETWORK LOGIC DIAGRAM
(Source: Self-developed)
The planning of the organization for the establishment of equipment is additionally thought of where the modem requires the installation where it was being designed and initiate it as a work. The five frameworks ought to be present at divisions of the organization and the switch ought to be set halfway such that in the event of any disappointment in any associations.
The framework can admittance to Wi-Fi also the individuals who expect the portability and don't lean toward the link and wires near them so they can without much of a stretch admittance to the availability.
The additional association that is the 6th ought to be put midway and ought to be utilized to teach the wide range of various frameworks.
In the same manner with a similar order can likewise be utilized as a reinforcement framework on the off chance that any of the frameworks isn't working or confronting any issue with the network. This sort of framework will make the moving simpler and as the situations are good then representatives will have the option to work productively thus it will be at last profit the organization.
TCP/IP model
As in an examination, it was indicated that correspondence between two frameworks is conceivable with the organization through convention suits. TCP/IP is one of the most generally utilized convention suite, additionally accessible without any problem. TCP/IP is the implementation of the OSI model (open system interconnection model). TCP/IP, the substitution of the convention isn't simple. TCP/IP convention is a structure of layers, and every layer posses with a particular use which is completed by the utilization of the convention. Every layer has conventions to complete its usefulness that is clung with the layer. TCP/IP convention suite consists of four layers:
Application layer: manages every layer ought to be independent and the tools that are of the first layer can secure the application information and probably not the data of TCP/IP as it is available in the next layers. The uppermost layer is an OSI and is distributed into 2 different layers and TCP/IP is the combination of 2 OSI layers. The protocols are Telnet, SMTP (Simple mail transfer protocol), HTTP (Hypertext transfer protocol), SNMP (Simple network management protocol), FTP (File transfer protocol).
Transport layer: it is the phase or layer which will ensure the information in one meeting of correspondence among the 2 communicators. As the Information Protocol data is raised in the organization phase and the layer isn't equipped for dealing with it. The layer that works as an intermediate and is properly oriented in the connection is also known as the connectionless or no connection layer. The protocols are UDP (User Datagram Protocol) and TCP (Transmission Control Protocol).
Organization layer: It is viewed as that the specific features of the organization layer could be shared by other layers and it will not create the hurdle as they are not specific with application explicit, which implies no change is needed in the insurance application. i.e. Another connectionless layer. The formation or transferring of the data is done in small units that have an address associated with them that is an IP address. The protocols are ISMP (Inter-Switch Message Protocol) and IP (Internet Protocol).
Datalink layer: The tools or managing are operated to the wide range of various layers and their controls committed circuits among the 2 communicators of an ISP. The management of data is done from the physical links and it is said that this gives the procedural and functional attributes to the data transferring. The protocols are ARP (Address Resolution Protocol), token ring, and Ethernet.
Figure 2 TCP/IP MODEL
(Source: self-developed)
Vulnerabilities
TCP/IP utilizes the location of the gadgets which are associated which fill the two or double that need to distinguishing the gadget also. As a result of this organization weakness is made and it will entirely noticeable and not contrasted with angry clients all through the globe. TCP/IP has 4 layers, as well as security concerns, that exist at every degree of the suite TCP/IP convention suite. TCP/IP information moves from the most elevated phase which is from the first Application layer and to the fourth layer which is named the Data link layer, at every next layer data is added. Along these lines, modes fitted on a more elevated phase cannot secure the previous phase, as the usefulness of the previous-level isn't distinguished from the preceding phase. Security controlling tools that are used at different layers and phase of TCP/IP convention suite available are: [1]
Application layer: manages of every phase ought to become independent and then the tools that are of the first layer phase can secure the first application information or data and probably not only the data of TCP/IP as this is available for the next layers of phase. The answer for being utilized for it ought to be level-based which can be utilized for quite a while, for instance, the utilization of Secure Multipurpose Internet Mail Extensions(S/MIME) that is continued because of the information that will be encoded in it. [2]
Transport layer: it is that of phase which will ensure the information in a meeting of correspondence among 2 communicators. Information Protocol data which was raised in any organization phase and also the layer isn't equipped for dealing with it. The layer is utilized to deal with the commotion of traffic created by the HTTP via the Transport Layer Security (TLS) convention. For utilizing Transport Layer Security (TLS) it is required that the application can uphold Transport Layer Security (TLS). In contrast with additional insurance to the first phase that is application layer utilizing or combining with the Transport Layer Security (TLS) is favored and considered safer. Transport Layer Security (TLS) will be utilized with SSL entryway VPNs.
Organization layer: displayed as that the specific features of the organization layer could be shared by other layers and it will not create the hurdle as they are not specific with application explicit, which implies no change is needed in the insurance application. In certain cases, the controlling is done by the Network layer of the IP Security (Internet Protocol security) is favored over different controls or the controls of different layers and the layers are transport and application layer. In this layer, information is ensured in parcels and the Internet
Protocol of every bundle is secured. [5]
Datalink layer: The tools or managing are operated to the wide range of various layers and their controls committed circuits among the 2 communicators of an ISP. The utilization of information encryptors is utilized to secure it. Although it does not provide help to the insurance from numerous lines thus it is viewed as basic in contrast with the different layer controls and it is simpler to execute. These conventions are utilized for the extra assurance for some particular connections that are least relied thus the utilization of these tools are finished. [3]
Conclusion
The entire report is on Network and beginning with the planning of the organization for an organization consists of 5 divisions. All the availability and connectivity and can be given by Local Area Network that is LAN since we have 3 kinds of organization that are WAN, LAN, and MAN.
Where LAN can be utilized for the structures or organization more than one spot for some clients yet MAN is used for intercity or state organization purposes and utilization of WAN is around the world. This report is set up in the wake of examining and experiencing sites and available books with network availability and their advantages.
At long last with which we thought of the answers for security weaknesses and portrayed the conventions and planned the organization for the organization GLORE Events. TCP/IP convention suite that is layered engineering where every layer has its conventions which are utilized to do the usefulness of that layer. Also, at each degree of TCP/IP, observations of weaknesses in security was seen. There is a need of safety efforts and afterward, new layers of the suite TCP/IP convention suite aren’t secure also it has weaknesses than to make sure about them. With the utilization of various controls was run which will lesson the odds of the danger of information misfortune, data spilling, and numerous different issues looked in conventions downside.
References
[1]
M. Ji, “Designing and Planning a Campus Wireless Local Area Network,” Theseus.fi, 2017, doi: URN:NBN:fi:amk-2017053011119. [Online]. Available: https://www.theseus.fi/handle/10024/130087. [Accessed: 12-Jan-2021]
[2]
M. Ji, “Designing and Planning a Campus Wireless Local Area Network,” Theseus.fi, 2017, doi: URN:NBN:fi:amk-2017053011119. [Online]. Available: https://www.theseus.fi/handle/10024/130087. [Accessed: 12-Jan-2021]
[3]
S. Francik, N. Pedryc, T. Hebda, and B. Brzychczyk, “Use of network planning methods in designing modernization of agri-food processing enterprise to improve organization of production: example of meat processing plant,” May 2018, doi: 10.22616/erdev2018.17.n426. [Online]. Available: http://www.tf.llu.lv/conference/proceedings2018/Papers/N426.pdf. [Accessed: 12-Jan-2021]
[4]
N. Zarbakhshnia, H. Soleimani, M. Goh, and S. S. Razavi, “A novel multi-objective model for green forward and reverse logistics network design,” Journal of Cleaner Production, vol. 208, pp. 1304–1316, Jan. 2019, doi: 10.1016/j.jclepro.2018.10.138. [Online]. Available: https://www.sciencedirect.com/science/article/abs/pii/S0959652618331548. [Accessed: 12-Jan-2021]
[5]
M. Mohammadi, S.-L. Jämsä-Jounela, and I. Harjunkoski, “Optimal planning of municipal solid waste management systems in an integrated supply chain network,” Computers & Chemical Engineering, vol. 123, pp. 155–169, Apr. 2019, doi: 10.1016/j.compchemeng.2018.12.022. [Online]. Available: https://www.sciencedirect.com/science/article/abs/pii/S0098135418302813. [Accessed: 12-Jan-2021]
[6]
B. Dey, K. Khalil, A. Kumar, and M. Bayoumi, “A Reversible-Logic based Architecture for Artificial Neural Network,” 2020 IEEE 63rd International Midwest Symposium on Circuits and Systems (MWSCAS), Aug. 2020, doi: 10.1109/mwscas48704.2020.9184662. [Online]. Available: https://ieeexplore.ieee.org/abstract/document/9184662. [Accessed: 13-Jan-2021]
[7]
“US20200264901A1 - Configuring programmable logic region via programmable network - Google Patents,” Google.com, 14-Feb-2019. [Online]. Available: https://patents.google.com/patent/US20200264901A1/en. [Accessed: 13-Jan-2021]
[8]
“US20200336588A1 - Device logic enhancement for network-based robocall blocking - Google Patents,” Google.com, 19-Apr-2019. [Online]. Available: https://patents.google.com/patent/US20200336588A1/en. [Accessed: 13-Jan-2021]
[9]
“A comparative analysis of surface roughness in robot spray painting using nano paint by Taguchi – fuzzy logic-neural network methods,” Australian Journal of Mechanical Engineering, 2020. [Online]. Available: https://www.tandfonline.com/doi/abs/10.1080/14484846.2020.1842157. [Accessed: 13-Jan-2021]
MITS5001 IT Project Management Assessment 2 Sample
Assignment Brief
Objective(s)
This assessment item relates to the unit learning outcomes as in the unit descriptor. This assessment is designed to improve student presentation skills and to give students experience in researching a topic and writing a report relevant to the Unit of Study subject matter.
The following ULOs are assessed in this assessment.
LO2 Critically analyze project parameters and identify the key processes from the available project management book of knowledge in practical case scenarios.
LO5 Carry out research studies to provide expert judgement on the project progress and strategize contingency and fallback plans to ensure project deliverables are met as planned.
INSTRUCTIONS
For this component you will prepare a report or critique on an academic paper related to IT Project Management. The paper you select must be directly relevant to one of these major topics:
Project Life Cycles, Integration Management, Scope Management, Schedule Management, Cost Management, Quality Management, Resource Management, Communications Management, Risk Management, Procurement Management, Agile Project Management, Change Management, Earned Value Management, Resource Management and Stakeholder Management.
Your report should be limited to approx. 1500 words (not including references). Use 1.5 spacing with a 12 point Times New Roman font. Though your paper will largely be based on the chosen article, you can use other sources to support your discussion. Citation of sources is mandatory and must be in the IEEE style.
Your report or critique must include:
• Title Page: The title of the assessment, the name of the paper you are reviewing and its authors, and your name and student ID.
• Introduction: A statement of the purpose for your report and a brief outline of how you will discuss the selected article (one or two paragraphs). Make sure to identify the article being reviewed.
• Body of Report: Describe the intention and content of the article. If it is a research report, discuss the research method (survey, case study, observation, experiment, or other method) and findings. Comment on problems or issues highlighted by the authors. Discuss the conclusions of the article and how they are relevant to what you are studying this semester.
• Conclusion: A summary of the points you have made in the body of the paper. The conclusion should not introduce any ‘new’ material that was not discussed in the body of the paper. (One or two paragraphs)
• References: A list of sources used in your text. They should be listed alphabetically by (first) author’s family name. Follow the IEEE style.
• The footer must include your name, student ID, and page number
Submission Guidelines for assignment help
All submissions are to be submitted through turn-it-in. Drop-boxes linked to turn-it-in will be set up in the Unit of Study Moodle account. Assignments not submitted through these drop-boxes will not be considered.
Submissions must be made by the due date and time (which will be in the session detailed above) and determined by your Unit coordinator. Submissions made after the due date and time will be penalized at the rate of 10% per day (including weekend days).
Solution
Introduction
This report aims at finding out the importance of project management in terms of time, cost and quality assurance. The chosen article speaks about Agile Project Management technique, its advantage over traditional PMBOK (Project Management Body of Knowledge) when looking for innovation and change management. The use of agile technology and its effectiveness is discussed in the case study of a Brazilian Pharmaceutical Company’s IT Project. The disadvantages of using a traditional approach are analyzed, and the SCRUM framework is utilized for implanting Agile Technology in designing the new software.
Research Method
The research method used in the research paper is a qualitative exploratory research method. In this research, a case study of the pharmaceutical industry is considered [7]. The case study aims at investigating the current phenomenon where the context and phenomena are not categorized. The process of the case study includes data collection, both qualitative and quantitative.
Project Management knowledge areas
Project management knowledge areas are existing that includes risk management, change management, Human resources management, stakeholder management, quality management, time management, cost management, and many more. As per the [7] higher competition rate in the market forces various companies to consider change management in terms of project management in order to address those changes that can impact the company both positively as well as negatively. However, various studies are present which showcases other requirements for adopting the change management process during the conduction of project work. In the view of [1], the intention of the authorities of a company regarding internal change provokes companies to adopt change management principles in delivering prosperous project work. Often it is found that the requirements of project work cannot be addressed by project stakeholders by just considering the principles of project management. In this regard, it can be contradicted that the project manager of specific project work should consider a change management approach along with the project management approach in order to address the drawbacks of the ‘one-legged approach.’ On the other hand, [2] opined that the demand for global software development rise significantly due to which companies have to consider the aspects of Requirements Engineering and Change management for managing rich communication level among every stakeholder. Henceforth, it can be argued that the argument of [2], [1] and [7] is entirely different from each other. Lastly, from the concern of [4], it is found that the approach regarding Change management helps to increase the effectiveness of a project work significantly. Thus, it can be asserted that the change management approach is of utmost crucial and relevance in terms of accomplishing a project work properly. Although, every people have their own point of view regarding the utilization of change management principles.
Key Project parameter
The critical project parameters considered for any project include time, cost, quality and quantity of the products or deliverables. The project considered in the research paper was completed in 100 days (approximately about four months.) The total project cost was $US 145, 000, including the backlog changes [7]. The changes were incorporated after the completion of every Sprint, and the whole process ended in five Sprints. The information gathered, and knowledge gained in every Sprint was used to induce changes and proper decision making of the project. The traditional approach estimated seven months for completion, and the budget was Us $ 291, 000 [7]. The project team members were satisfied as the project’s testing was done in a real-time environment after subsequent phases. The changes were immediately incorporated and not waiting for the completion enhances the quantity as the products are delivered at every phase. Using SCRUM framework was helpful.
Project deliverables
A deliverable is tangible or intangible goods or services that need to be delivered. They can be documents, report, software product, a server upgrade or any other building blocks of the project [5]. The project deliverables were considered using the Product Backlogs and then estimating the items based on their priority which defines the requirement according to the Sprints of the project. The organization’s primary tangible deliverable was lowering down the need for stock as the expiration of medicines leads to loss. The XYZ project was designing an inventory module for considering the medicines with a shorter life span. It was necessary to apply filtration of medicine with batch numbers with shorter shelf life [7]. Arrange them by date, create a proper log, analyze the acquisition cost of storing and transport from inventory and total. The intangible products include the organizational reputation by meeting consumer demands and take decisions accordingly.
Project monitoring
The project was based on SCRUM framework where the stakeholders were the SCRUM team, the product owner and the Scrum master. The whole project was divided into Sprints, and the activities are described accordingly. Constant monitoring was done by meeting conducted by the Scrum Master where the report was taken from each member regarding their activities. The initial Sprint was to gather information regarding the stock of the existing drugs, their shelf life. The primary aim was to reduce damage and decrease the need for stock as the medicines were not allowed to be solved after their expiration date. The next Sprint was regarding speculation where Product Backlogs were created by the owner. From this stage, a Sprint backlog was created, which identified the product requirements that are required to be delivered in each subsequent stages of sprints. The Exploration phase covers the activities that were to be conducted in each Sprint. The meetings were held to ensure that the scope of the project is maintained. The next phase was the Adaptation Phase where the changes were incorporated according to the requirements gathered in previous stages. A retrospective approach is taken for considering the situation and how the requirements changed. But in later stages, more realistic decisions were taken.
Contingency Plan
Contingency plans are used to fight against any adverse incidences that may occur. The likelihood of risk is considered, and proactive measures are taken to combat the risk [6].
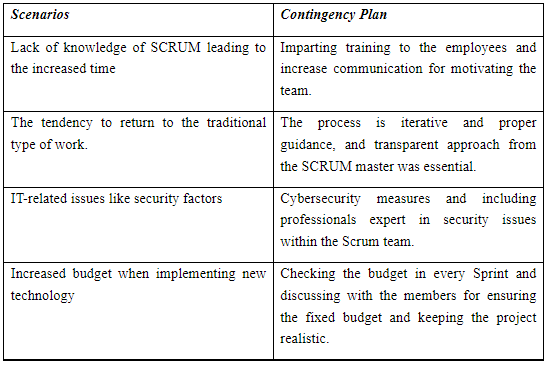
Table 1: Contingency plan
Source: (Developed by the author)
Research Findings
The research aimed to consider the positive aspects of using Agile Technology in SCRUM framework and its increased effectiveness as compared to the traditional approach. According to the research findings of the chosen paper, it is observed that a quantifiable benefit was observed in terms of time (80% increased performance as the project was completed in 100 days which was estimated to be seven months for traditional approach). In the case of cost, it got reduced by 50% [7]. The deliverables were produced after the first phase of the project life cycle, which motivated the employees as they could see the product even before the completion of the whole project. However, as per the consent of [3], every project manager needs to categorize the phases of a project work in short frequency that can provide the feeling of short-term wins to everyone associated with the project work.
However, the findings of the chosen research paper did not showcase the existence of such an aspect. Constant communication among the team members created the right working environment. The significant benefit was the project control in terms of scope. The results are analyzed, and changes were incorporated according to the requirements. According to [4], a communication plan must be deployed during the conduction of project work in order to cross-check the procedure of every step of that specific project work. However, the findings of [7] do not represent the utilization of such a communication plan. Aggregation was also initiated as the clients can instruct changes after using the products during the completion of the first phase [7]. Customer satisfaction is the major success as the change was initiated according to their demands. The major drawback of the research was to consider only a single case study of a Brazilian pharmaceutical company. It cannot be used as a generalized result, although exploratory research helped in gaining knowledge that can be used in real scenarios of business [7].
As per the above discussion, it can be argued that the project work was critically measured and delivered by the project team, although some gaps are present which could be addressed during the conduction of project work. Different authors represented different approaches for enriching the outcome of a project, which should be taken into account by authorities of project work in order to increase the effectiveness of the project. Hence, not only the aspects of Agile but also the principles of change management, appropriate communication need to considered by project stakeholders for managing change as well as to deliver a prosperous outcome by finishing the project work.
References
[1] G. O’Donovan, "Creating a culture of partnership between Project Management and Change Management", Project Management World Journal, vol. 7, no. 1, pp. 1-11, 2018. Available: https://pmworldlibrary.net/wp-content/uploads/2018/01/pmwj66-Jan2018-ODonovan-creating-culture-of-partnership-project-management-and-change-management.pdf. [Accessed 3 January 2021].
[2] M. Shafiq et al., "Effect of Project Management in Requirements Engineering and Requirements Change Management Processes for Global Software Development", IEEE Access, vol. 6, pp. 25747-25763, 2018. Available: 10.1109/access.2018.2834473 [Accessed 3 January 2021].
3] M. Fraser-Arnott, "Combining Project Management and Change Management for Project Success in Libraries", 2018. Available: https://doi.org/10.1108/S0732-067120180000038005 [Accessed 3 January 2021].
[4] F. Shirazi, H. Kazemipoor and R. Tavakkoli-Moghaddam, "Fuzzy decision analysis for project scope change management", Decision Science Letters, pp. 395-406, 2017. Available: 10.5267/j.dsl.2017.1.003 [Accessed 3 January 2021].
[5] D. Danda, "Greycampus", Greycampus.com, 2019. [Online]. Available: https://www.greycampus.com/blog/project-management/what-are-project-deliverables. [Accessed: 02- Jan- 2021].
[6] K. Hughes, "How to Make a Contingency Plan - ProjectManager.com", ProjectManager.com, 2018. [Online]. Available: https://www.projectmanager.com/blog/contingency-plan. [Accessed: 02- Jan- 2021].
[7] A. Terra, "Agile Project Management with Scrum: Case Study of a Brazilian Pharmaceutical Company IT Project", International Journal of Managing Projects in Business, vol. 10, no. 1, pp. 121-142, 2016. Available: https://www.emerald.com/insight/content/doi/10.1108/IJMPB-06-2016-0054/full/html. [Accessed 2 January 2021].
MIS607 Cybersecurity Assignment Sample
Assignment Brief
Assignment Title - MITIGATION PLAN FOR THREAT REPORT
Individual/Group - Individual
Length - 2500 words (+/- 10%)
Learning Outcomes:
The Subject Learning Outcomes demonstrated by successful completion of the task below include:
b) Explore and articulate cyber trends, threats and staying safe in cyberspace, plus protecting personal and company data.
c) Analyze issues associated with organizational data networks and security to recommend practical solutions towards their resolution.
d) Evaluate and communicate relevant technical and ethical considerations related to the design, deployment and/or the uses of secure technologies within various organizational contexts.
Submission - Due by 11:55pm AEST Sunday end of Module 6.1
Weighting - 45%
Total Marks - 100 marks
Task Summary
For this assessment, you are required to write a 2500 words mitigation plan for threat report based on knowledge you gained about threat types and key factors in Assessment 2. You are required to use the Assessment 2 case as context to write a report to address or alleviate problems faced by the business and to protect the customers. In doing so, you are required to demonstrate your ability to mitigate threat/risks identified in Assessment 2 through the strategy you recommend (STRIDE).
Context
Cybersecurity help organizations to mitigate threats/risks, reduce financial loss and safety violations, decrease unethical behaviour, improve customer satisfaction, and increase efficiency, as well as to maintain these improved results. Threats can be resolved by Risk Acceptance (doing nothing), Risk Transference (pass risk to an externality), Risk Avoidance (removing the feature/component that causes the risk) and Risk Mitigation (decrease the risk). This assessment gives you an opportunity to demonstrate your understanding of cybersecurity and your capability to explain Risk Mitigation strategies for such threats. Mitigations should be chosen according to the appropriate technology and resolution should be decided according to the risk level and cost of mitigation.
Task Instructions for assignment help
1. Read the Assessment 2 Case Scenario again to understand the concepts discussed in the case.
2. Review your subject notes to establish the relevant area of investigation that applies to the case. Re- read any relevant readings that have been recommended in the case area in modules. Plan how you will structure your ideas for the mitigation plan for threat report.
3. The mitigation plan for threat report should address the following:
• Setting priorities for risks/threats
• Analyze the case in terms of identified risk categories and scenarios
• Apply standard mitigations
• Discuss specific resolutions for improvement, and justify their significance
• Provide recommendations for mitigating risk based on an assessment of risk appetite, risk tolerance and current risk levels (Choose techniques to mitigate the threats)
• Make recommendations to the CEO on how to conduct risk management, key issues involving your process improvement model, including a road map, the identification of appropriate technologies for the identified techniques, communicating the strategy, and a suggested timeline.
4. The report should consist of the following structure:
A title page with subject code and name, assignment title, student’s name, student number, and lecturer’s name. The introduction that will also serve as your statement of purpose for the report. This means that you will tell the reader what you are going to cover in mitigation plan report. You will need to inform the reader of:
a) Your area of research and its context (how to mitigate or manage threats)
b) The key concepts you will be addressing
c) What the reader can expect to find in the body of the report
The body of the report will need to respond to the specific requirements of the case study. It is advised
that you use the case study to assist you in structuring the report. Set priorities for identified threats from assessment 2, analyze the case in terms of identified risk categories and discuss specific resolutions and recommendations for improvements in the body of the report.
The conclusion (will summarize any findings or recommendations that the report puts forward regarding the concepts covered in the report.
5. Format of the report
The report should use font Arial or Calibri 11 point, be line spaced at 1.5 for ease of reading, and have page numbers on the bottom of each page. If diagrams or tables are used, due attention should be given to pagination to avoid loss of meaning and continuity by unnecessarily splitting information over two pages. Diagrams must carry the appropriate captioning.
6. Referencing
There are requirements for referencing this report using APA referencing style for citing and referencing research. It is expected that you used 10 external references in the relevant subject area based on readings and further research. Please see more information on referencing here:https://library.torrens.edu.au/academic skills/apa/tool
7. You are strongly advised to read the rubric, which is an evaluation guide with criteria for grading the
assignment— this will give you a clear picture of what a successful report looks like.
Submission Instructions
Submit Assessment 3 via the Assessment link in the main navigation menu in MIS607 Cybersecurity. The Learning Facilitator will provide feedback via the Grade Centre in the LMS portal. Feedback can be viewed in My Grades.
Solution
Introduction
The purpose of this report is to prepare a mitigation plan for the identified threats from assessment-2 threat modelling report. The context of this report is based on the threat mitigation strategy, STRIDE which was recommended in the earlier assessment. In this threat report, it has been possible for me to address the key cybersecurity threats/risks faced by the Business & Communication (B&C) Insurance organisation and concept of risk acceptance, risk transference, risk avoidance, & risk mitigations. Moreover, in this report, recent cyber trends and relevant threats have been articulated and explored.
Readers can expect to learn about the risk mitigation strategies for critical cybersecurity threats through this assessment. Last, but not the least, this threat report helps the key stakeholders of B&C Insurance company to choose appropriate technology and resolution for the risk level. It also helps to understand the cost of mitigation and structured their own ideas for the same.
Threats Identification, Specific Resolution respond to the case study
Setting priorities for risks/threats
Table 1: Risk/Threat Prioritization (Source: Canfield & Fischhoff, 2018, p. 828)
Analysis in terms of risk categories and scenarios
Table 2: Analysis of identified threats for particular scenario (Source: Canfield & Fischhoff, 2018, p. 830)
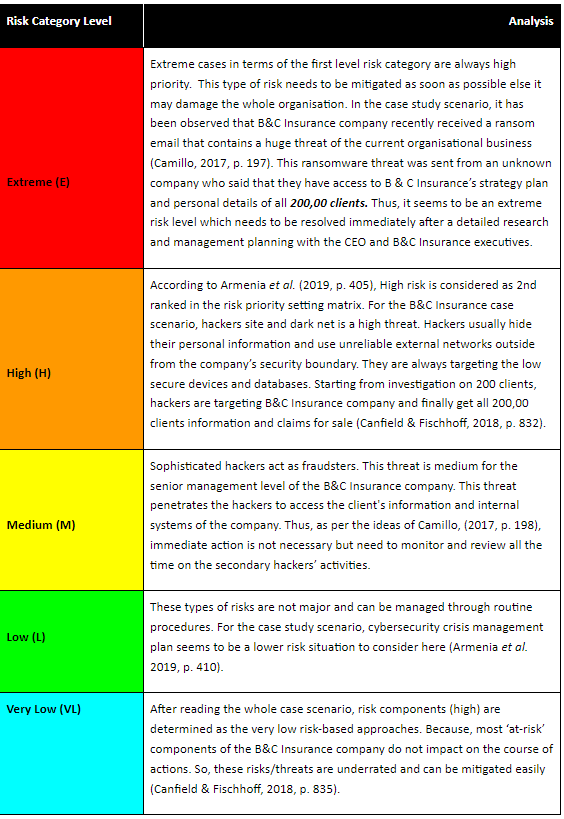
Standard Mitigations
After knowing the risk categories and relevant scenarios for this B&C Insurance case study organisation, it is necessary to identify and apply standard mitigation techniques as follows:
? Installing Firewalls to protect email/website
Firewalls are enabled to protect B&C Insurance company websites. It has been designed to create a buffer between IT systems and external networks so that it can monitor the network traffic, block anything that could damage the computers, systems, and private networks (Armenia et al. 2019, p. 405). Firewalls also prevent cyber criminals from breaking down into networks and block outgoing traffic that contains a virus.
? Installing antivirus software
Installing antivirus acts as an essential technological defence for the B&C Insurance company. Modern range of antiviruses generally provide protection against a range of malware (spam emails), key loggers, ransomware, adware, spyware, and so on (Ganin et al. 2020, p. 185).
? Patch management
For software updates, need to fix the vulnerability along with a patch management plan.
? Cybersecurity risk assessment
As per the International standard: ISO 27001, step-by-step guidance has been followed for cyber security risk assessment. It is a standard mutation applied to gain benefits (Zadeh, Jeyaraj & Biros, 2020, p. 5).
? Information security policy
It is the result of risk assessment which has been adopted by the organisation itself to prevent unauthorized access. Information security policy will review the effectiveness of the control.
? Sensitive data encryption
As suggested by Zheng & Albert, (2019, p. 2078), Under the General Data Protection Regulation (GDPR), encrypted data cannot be assessed by the criminal or hackers even if they break the systems. It only accessed by the authorized personnel i.e. CEO of the B&C Insurance with a decryption key.
? Remote working policy
Create a remote working policy for the B&C Insurance employees reshaped the organisational security services. It recommends two-factor authentication to any third-party services for personal use (Armenia et al. 2019, p. 410).
? Conduct vulnerability scans
Vulnerability scanning improves the overall cybersecurity effectiveness and security measurements.
? Create a different business continuity plan for B&C Insurance
It is also a standard mitigation that outlines the critical processes of an organisational operation in the event of a major disruption (Ganin et al. 2020, p. 188).
? Conducting penetration test
It is important to resist hacking on behalf of the B&C Insurance company. Automated scans enable the actors and leverage the weaknesses to gain a true insight. Penetration test is important to stop criminals, ethical hackers and implement defences (Zadeh, Jeyaraj & Biros, 2020, p. 12).
Specific Resolutions
After considering the cybersecurity threats for B&C Insurance company and discussing the standard mitigations, it has been possible for me to describe specific resolutions for improvement and justify their significance for the same. The following are the resolutions for B&C Insurance companies which can be implemented to ensure that the organisation does not become the victim of cyber-crime, hackers, or fraudsters (Zheng & Albert, 2019, p. 2080).
? Providing security training is a best resolution that aware the employees before clicking a malicious link or downloading fraudulent software.
? Updated strong anti-virus software is useful to protect internal organisational data (Armenia et al. 2019, p. 413).
? How to respond to the phishing threats from exploitation of software vulnerabilities has also to be considered.
? Strong password policy is a resolution to the threats and risks faced by the B&C Insurance company.
? As per the guidance of Ganin et al. (2020, p. 190), multi factor authentication is a resolution that allows B&C Insurance company to protect its compromised credentials. Attempting corporate applications, networks, and servers is also a resolution approach.
? Backing-up databases is also important. It could be the essential solution when the company lost almost its data after a cyber-attack (Zadeh, Jeyaraj & Biros, 2020, p. 20).
Recommendations for Risk Mitigation
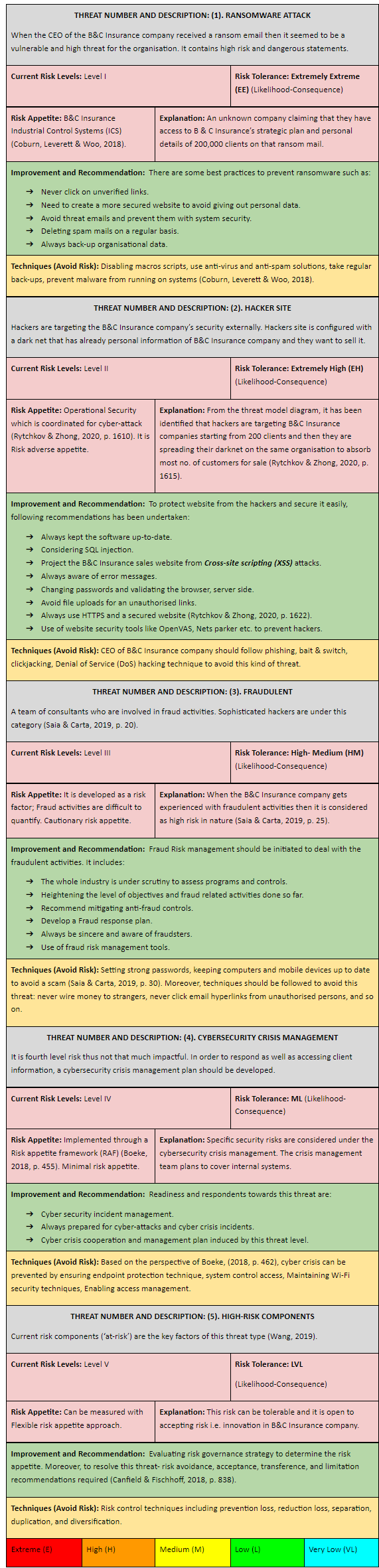
Table 3: Mitigating Risk Assessment (Source: Wang, 2019)
Risk Management Roadmap
In this stage, on the basis of risk categories and key issues involved to the threat model a risk management has been conducted. It is included in the following table.
Table 4: Risk Management approaches and relevant criterions (Source:
Figure 1: Risk Roadmap
(Source: Bahaloo-Horeh & Mousavi, 2020, p. 123186)
Identification of appropriate technologies
STRIDE elements are identified from assessment 2 which is an appropriate technique to diversify the threats. This technique is identified for the relevant threats and how to act against it.
? Spoofing is identified for Authentication security property.
? Tampering technique is for Integrity.
? Repudiation is a recommended threat key factor accessed by the CEO in a non-repudiation context (Laessoe, Jensen & Madeleine, 2017, 5).
? Information Disclosure might be considered for confidentiality.
? Denial of Service is considered for availability.
? Elevation of Privilege is an authorized technique involved in this case.
On the other hand, the DREAD model is a technique which is associated with risks/threats. NIST is also similar to these.
Conclusion
After discussing the threats, vulnerabilities in the B&C Insurance company, it is necessary to summarize those findings and outcomes that will be put forward in future cases. The course of actions must be recommended to mitigate potential threats in future are:
? Validating the threat and engaging the stakeholders.
? Conduct a proper risk management which may be beneficial and provide specific resolution to the existing threats.
? Beware of unreliable external networks, emails from the next time to prevent this kind of cybercrime scenario.
References
Armenia, S., Ferreira Franco, E., Nonino, F., Spagnoli, E., & Medaglia, C. M. (2019). Towards the definition of a dynamic and systemic assessment for cybersecurity risks. Systems Research and Behavioral Science, 36(4), 404–423. Retrieved on 18-Apr-2021 from, https://doi.org/10.1002/sres.2556
Bahaloo-Horeh, N., & Mousavi, S. M. (2020). Comprehensive characterization and environmental risk assessment of end-of-life automotive catalytic converters to arrange a sustainable roadmap for future recycling practices. Journal of Hazardous Materials, 400, 123186–123186. Retrieved on 19-Apr-2021 from, https://doi.org/10.1016/j.jhazmat.2020.123186
Boeke, S. (2018). National cyber crisis management: different European approaches. Governance, 31(3), 449–464. Retrieved on 19-Apr-2021 from, https://doi.org/10.1111/gove.12309
Camillo. (2017). Cybersecurity: risks and management of risks for global banks and financial institutions. Journal of Risk Management in Financial Institutions, 10(2), 196–200. Retrieved on 18-Apr-2021 from, https://lesa.on.worldcat.org/oclc/6998327984
Canfield, C. I., & Fischhoff, B. (2018). Setting priorities in behavioural interventions: an application to reducing phishing risk. Risk Analysis, 38(4), 826–838. Retrieved on 18-Apr-2021 from, https://doi.org/10.1111/risa.12917
Coburn, A., Leverett, E., & Woo, G. (2018). Solving cyber risk: protecting your company and society. John Wiley & Sons, Incorporated. Retrieved on 19-Apr-2021 from, https://lesa.on.worldcat.org/oclc/1080082434
Ganin, A. A., Quach, P., Panwar, M., Collier, Z. A., Keisler, J. M., Marchese, D., & Linkov, I. (2020). Multicriteria decision framework for cybersecurity risk assessment and management. Risk Analysis, 40(1), 183–199. Retrieved on 19-Apr-2021 from, https://doi.org/10.1111/risa.12891
Laessoe, U., Jensen, N. M. B., & Madeleine, P. (2017). Examination of the gait pattern based on adjusting and resulting components of the stride-to-stride variability: proof of concept. Bmc Research Notes, 10(1), 1–7. Retrieved on 19-Apr-2021 from, https://doi.org/10.1186/s13104-017-2623-8
Rytchkov, O., & Zhong, X. (2020). Information aggregation and p-hacking. Management Science, 66(4), 1605–1626. Retrieved on 19-Apr-2021 from, https://doi.org/10.1287/mnsc.2018.3259
Saia, R., & Carta, S. (2019). Evaluating the benefits of using proactive transformed-domain-based techniques in fraud detection tasks. Future Generation Computer Systems, 93, 18–32. Retrieved on 19-Apr-2021 from, https://doi.org/10.1016/j.future.2018.10.016
Wang, S. S. (2019). Integrated framework for information security investment and cyber insurance. Pacific-Basin Finance Journal, 57. Retrieved on 18-Apr-2021 from, https://doi.org/10.1016/j.pacfin.2019.101173
Zadeh, A. H., Jeyaraj, A., & Biros, D. (2020). Characterizing cybersecurity threats to organizations in support of risk mitigation decisions. E-Service Journal, 12(2), 1–34. Retrieved on 19-Apr-2021 from, https://lesa.on.worldcat.org/oclc/8978135163
Zheng, K., & Albert, L. A. (2019). A robust approach for mitigating risks in cyber supply chains. Risk Analysis, 39(9), 2076–2092. Retrieved on 19-Apr-2021 from, https://doi.org/10.1111/risa.13269
MIS500 Foundations of Information Systems Assignment Sample
Assignment Brief
Individual/Group - Individual
Length - 1500 words (+/- 10%
Learning Outcomes
The Subject Learning Outcomes demonstrated by successful completion of the task below include:
a) Effectively communicate and demonstrate understanding of the importance of ethical and professional standards in own career and professional future.
Submission - By 11:59 PM AEST Friday of Module 6.1 (Week 11)
Weighting - 35%
Total Marks - 35 marks
Task Summary
This assessment task requires you to reflect on your experiences in MIS500 this trimester by following a four-step process to gain insights into the work you have done and how it relates to your own career and life more broadly. In doing so, you will need to produce a weekly journal to record your learning and then as the trimester comes to a close reflect on these experiences and submit a final reflection of 1500 words (+/- 10%) that will include the weekly journal as an appendix.
Context
This is an individual assignment that tracks your growth as a student of Information Systems over the trimester. It is scaffolder around your weekly learning activities. Completing the activities and seeking input from your peers and the learning facilitator is essential for you to achieve a positive result in this subject. Before you start this assessment, be sure that you have completed the learning activities in all of the modules. This reflective report gives you the opportunity to communicate your understanding of how information systems relate to your career and future.
Task Instructions for assignment help
1. During Module 1 – 5, you were asking to produce a weekly journal to record your learnings each week. Based on these weekly journals, please write a 1500-word reflective report about your experience focusing on how this will support developing and planning your future career.
2. You are required to follow the four steps of Kolb’s learning cycle when writing the reflective report. You will keep a learning journal throughout the trimester. Each week as you complete the learning activities you record your experience in spreadsheet or word document.
Step 1
Concrete experience – Keep a learning journal
Step 2
Reflective observation – Summarise what happened
Step 3
Abstract conceptualization – Analyze what this means
Step 4
Active experimentation - New action
1. You are required to write this assessment in a report format using the following headings:
2. Introduction
3. Reflective Observation – Summarise what happened.
4. Abstract conceptualization – Analyze what this means for you and your career.
5. Active experimentation – What new action do you need to take to develop yourself and your career using the things you learned through your MIS 500 studies.
6. Conclusion
7. Appendix of learning journal (with evidence)
Referencing
Formal citation of sources is not required. However, specific reference to your own experiences must be made. It is essential that you use appropriate APA style for citing and referencing research if you do make reference other work. Please see more information on referencing here http://library.laureate.net.au/research_skills/referencing
Submission Instructions
Please submit ONE MSWord document (.doc or .docx) via the Assessment 3 section found in the main navigation menu of the subject’s Blackboard site. The Learning Facilitator will provide feedback via the Grade Centre in the LMS portal. Feedback can be viewed in My Grades.
Solution
Introduction
In this study, I have reflected on my learning experience related to MIS500 modules. I have described my learning experience based on Kolb’s learning cycle. This model explains that effective learning is a progressive process in which learners' knowledge develop based on the development of their understanding of a particular subject matter. Kolb's learning cycle has four phases, concrete learning, reflective observation, abstract conceptualisation and active experimentation. The learning process will help me to develop my career in the field of information technology.
Concrete Experience
Before the first module, I had little idea about the use of information systems in business. Thus, I was in the concrete experience stage of Kolb’s learning model, in which a learner has little idea about a concept. The first stage of Kolb’s model is concrete experience. In this stage, learners encounter new knowledge, concepts and ideas, or they reinterpret the ideas, concepts and knowledge that they already know (Hydrie et al., 2021). I learnt the use of information systems for making rational decisions in business is called business intelligence. I had no knowledge about business intelligence before the first module. Thus, it helped me to experience new knowledge about business intelligence. I started to think about how I can develop my career in the field of business career and the learning strategies that can help me to enhance my knowledge about the professional field.
The next modules helped me to deepen my understanding of business intelligence. I learnt that the emerging area of business intelligence is the result of a digital revolution across the world. Digital revolution refers to an increase in the number of users of tools and technologies of digital communication, such as smartphones and other types of computers, internet technology. The evidence for the digital revolution is the report "The Global State of Digital in October 2019.” The report mentions that there were around 155 billion unique users of mobile phones worldwide (Kemp, 2019). However, there were 479 billion internet users. The total number of social media users were 725 billion. The evidence has been obtained from module 1.2. Thus, there is high global penetration of digital technologies. The global penetration of digital technologies helped me to understand that I want to develop my career in the field of business intelligence. The digital revolution created thousands of career opportunities in the field. Business organisations need to use digital technologies to communicate with people or customers who use digital devices and technologies. Digital technologies are helping organisations in growth and international expansion (Hydrie et al., 2021). Businesses are expanding themselves with the help of digital technologies. Many businesses have transformed themselves from global to local with the help of digital technologies.
Reflective Observation
When I started to learn module 2, I learnt how business organisations use data to gain a competitive advantage over their competitors. In digital, the organisation which has relevant data can reach the targeted customers, improve their products and services and leverage different opportunities (Hydrie et al., 2021). Thus, data management and information management are vital for the success of an organisation. By collecting and managing data effectively, companies can obtain the knowledge that they require to achieve their business goals. I had reached the reflective observation stage by the time I learned this module because I started to reflect on new experiences by explaining why businesses need to digitise themselves. The reflection of observation is related to the second stage of Kolb’s model of learning. The reflective observation stage is related to the reflection on a new experience that a learner receives through his/her learning (Hydrie et al., 2021). It includes a comparison between the new knowledge or experience and existing knowledge or experience to identify a knowledge gap. This stage allowed me to know what I need to learn more to develop my career in the field of business intelligence or information system professional.
In the next modules, I tried to bridge the knowledge gap. In module 2.2, I learnt about the concepts of knowledge management and big data. Knowledge management is a collection of approaches that help to gather, share, create, use and manage related to management or information of an organisation (Arif et al., 2020). Knowledge management is crucial for organisations to gain meaningful insights from the collected data. However, big data refers to data in abundance which has high velocity and volume. Big data helps to identify important patterns related to events and processes and facilitates decision-making for business organisations.
These information systems are human resource information systems (HRIS), enterprise resource planning (ERP) systems and customer relationship management (CRM) systems Arif et al., 2020). This module played a vital role in shaping my knowledge by helping me to understand the practical use of information technology and information systems in business operations. I learnt how information systems help to describe and analyse the value chains of business organisations. A value chain of a business organisation is consist of main activities and supporting or auxiliary activities that help business organisations to carry out all their operations.
Module 3.1 also proved to bridge the knowledge gap. In this module, my knowledge reached to abstract conceptualisation stage of Kolb's learning model, which is related to the development of new ideas in a learner's mind or help him/her to modify existing ideas related to a concept. I started to use my learnings on how information systems can be used more effectively by business organisations. Thus, I tried to modify the knowledge related to existing applications of information systems in business.
Abstract Conceptualisation
Active conceptualisation is the stage of Kolb's learning cycle in which learners give a personal response to new experiences. In this stage, I started to think about how to use the new knowledge that I gained for the advancement of my career. I decided to learn more about ERP and CRM. If I learn about the two types of information systems, I can learn to develop them and help other organisations to learn their uses. It helped to shape my knowledge about area-specific information systems that can help organisations to meet the needs of the operations of their certain business operations. The two specific areas about which I gained knowledge in the module were ERP and CRM (Arif et al., 2020). ERP is an information system that helps to plan and manage the resources of a business organisation. It helps in managing to carry out supply chain operations. The main functions of an ERP are inventory planning and management, demand forecast and management of operations related to suppliers, wholesalers and retailers. However, CRM helps in managing relations with customers of business organisations (Hamdani & Susilawati, 2018). It helps to know and resolve customers’ grievances. CRM allows organisations to communicate with their customers to understand their needs and provide them with information about product and services offerings effectively. In module 4.2, I learnt how can help an organisation selects its business information system. The selection of a business information system by a business organisation depends on its business architecture (Hamdani & Susilawati, 2018). A business architecture refers to a holistic overview of operations, business capabilities, processes of value delivery and operational requirements. The information system that suits the business architecture of an organisation is most suitable for it. The price of information systems ascertained by vendors also influences the decisions of business organisations to use it.
Active Experiment
The active experiment is the stage in which learners decide what to do with the knowledge that they gained (Hydrie et al., 2021). I used the reflection technique to decide how to use my knowledge about information systems to develop my career. Harvard research in 2016 also explained the importance of reflection (Module 5.2). Reflecting on previous experiences helps individuals and organisations to recall what they learnt and find scopes of improvements in their existing skills and knowledge (Rigby, Sutherland & Noble, 2018). Thus, if business organisations reflect on their previous experiences related to IT operations, they can improve their knowledge about IT operations. Reflection can also help them to find a scope of improvements in their existing knowledge. As a result, they can improve their future IT strategies to achieve business goals. The improvements in the strategies can help them to ensure their future success. Thus, reflection can be an effective source of learning for organisations. The reflection of my learning helped me to know that I want to become a big data analyst because the requirements of big data analysis increasing in different fields, and I have effective knowledge about it. I will always follow ethics related to my profession to maintain professionalism because it is an ethical responsibility and professional conduct for IT professionals (McNamara et al., 2018).
Conclusion
In conclusion, my learning experience related to information systems helped me to know new concepts related to them. It helped me to bridge my knowledge gap about the use of information systems in business analytics. Based on my learning, I found that I have gained effective knowledge about big data analysis. Thus, I want to develop my career in the field of big data analysis.
References
Arif, D., Yucha, N., Setiawan, S., Oktarina, D., & Martah, V. (2020). Applications of Goods Mutation Control Form in Accounting Information System: A Case Study in Sumber Indah Perkasa Manufacturing, Indonesia. Journal of Asian Finance, Economics and Business, 7(8), 419-424. Retrieved from http://eprints.perbanas.ac.id/7166/
Di Stefano, G., Gino, F., Pisano, G. P., & Staats, B. R. (2016). Making experience count: The role of reflection in individual learning. Harvard Business School NOM Unit Working Paper, (14-093), 14-093. Retrieved from https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2414478
Hamdani, N. A., & Susilawati, W. (2018). Application of information system technology and learning organization to product innovation capability and its impact on business performance of leather tanning industry. Int. J. Eng. Techno, 7, 393-397. Retrieved from https://www.academia.edu/download/60118436/Application_of_Information20190725-106859-1v84mpn.pdf
Hydrie, M. Z. I., Naqvi, S. M. Z. H., Alam, S. N., & Jafry, S. I. A. (2021). Kolb’s Learning Style Inventory 4.0 and its association with traditional and problem based learning teaching methodologies in medical students. Pakistan Journal of Medical Sciences, 37(1), 146. Retrieved from https://www.ncbi.nlm.nih.gov/pmc/articles/pmc7794154/
Kemp, S. (2019, October 23). The Global State of Digital in October 2019. Retrieved from https://wearesocial.com/au/blog/2019/10/theglobal-state-of-digital-in-october-2019
McNamara, A., Smith, J., & Murphy-Hill, E. (2018, October). Does ACM’s code of ethics change ethical decision making in software development? In Proceedings of the 2018 26th ACM joint meeting on European software engineering conference and symposium on the foundations of software engineering (pp. 729-733). Retrieved from https://dl.acm.org/doi/abs/10.1145/3236024.3264833?casa_token=xu_JKZRcyBEAAAAA:GhNrkWmz5yEKg4TwJaWg6dfOBz8O1WWoUuOtwbJXbuo3TL623CitLoNeaEQiksit_hl5YrAcRQSQ
Rigby, D. K., Sutherland, J., & Noble, A. (2018). Agile at Scale. Harvard Business Review, 96(3), 88–96. Retrieved from http://search.ebscohost.com.ezproxy.laureate.net.au/login.aspx?direct=true&db=bsu&AN=129192576&site=ehost-live
DASE201 Data Security Assignment Sample
Assignment Brief
Length/Duration: 1000 words report (+/- 10%)
Unit Learning Outcomes addressed:
• Identify vulnerabilities for data security threat.
• Examine methods to prevent cyber-attack defences, IDS and IPS.
• Compare framework of cyber security, safety principles and guidelines of various tools to enforce data security and privacy.
• Critique the mechanisms and prominent techniques to tackle sophisticated ICT attacks.
Submission Date: Week 11
Assessment Task: Group written report
Total Mark: 20 Marks
Weighting: 20%
Students are advised that submission of an Assessment Task past the due date without a formally signed approved Assignment Extension Form (Kent Website My Kent Student Link> FORM – Assignment Extension Application Form – Student Login Required) or previously approved application for other extenuating circumstances impacting course of study, incurs a 5% penalty per calendar day, calculated by deduction from the total mark.
ASSESSMENT DESCRIPTION:
Identify two of the biggest data breaches from 2020 for assignment help and explain the vulnerabilities that lead to the attacker gaining access to the data. Also propose techniques that practices that could have helped prevented this data breach.
This is a group task with groups of 3 students
ASSESSMENT SUBMISSION:
Part 1. Group Report
This is a group activity and students are required to work with their respective group members. No individual submission will be accepted. You have to nominate someone as your group leader to coordinate the assignment submission. The report should be submitted online in Moodle by one member of the team ONLY (Group Leader) on Sunday Week 11.
You will not receive any marks for this assignment if your group members collectively report against you for non- participation or non-cooperation
GENERAL NOTES FOR ASSESSMENT TASKS
Content for Assessment Task papers should incorporate a formal introduction, main points and conclusion. Appropriate academic writing and referencing are inevitable academic skills that you must develop and demonstrate in work being presented for assessment. The content of high quality work presented by a student must be fully referenced within-text citations and a Reference List at the end. Kent strongly recommends you refer to the Academic Learning Support Workshops materials available on the Kent Learning Management System
GENERAL NOTES FOR REFERENCING
References are assessed for their quality. Students should draw on quality academic sources, such as booKs, chapters from edited booKs, journals etc. The textbooK for the Unit of study can be used as a reference, but not the Lecturer Notes. The Assessor will want to see evidence that a student is capable of conducting their own research. Also, in order to help Assessors determine a student’s understanding of the worK they cite, all in-text references (not just direct quotes) must include the specific page number(s) if shown in the original. Before preparing your Assessment TasK or own contribution, please review this ‘YouTube’ video (Avoiding Plagiarism through Referencing) by clicKing on the following linK: linK:http://moodle.Kent.edu.au/Kentmoodle/mod/folder/view.php?id=3606
A search for peer-reviewed journal articles may also assist students. These type of journal articles can be located in the online journal databases and can be accessed from the Kent Library homepage. WiKipedia, online dictionaries and online encyclopaedias are acceptable as a starting point to gain Knowledge about a topic, but should not be over-used – these should constitute no more than 10% of your total list of references/sources.
Solution
Introduction
Data security is the way of protecting organisational data and digital information from destructive forces and unwanted actions like hacking, cyber-attacks, and data breaches. Data security includes hashing, encryption, and transmission of data over a secured line (Industry2018, p. 58). In this report, two biggest data breaches are identified from 2020 and the vulnerabilities that lead to the attacker gaining access to the data has been identified. The report also talks about techniques of preventing data breaches.
Identifying the data breaches from 2020
There are two biggest data breaches identified in 2020 for Microsoft and MGM resorts.
In January 2020, Microsoft has admitted that an internal customer support database has been accidentally exposed online. Through this statement, Microsoft indirectly meant that the customer records of 250 million people spanning for 14 years has been exposed online without any password protection. A security researcher reported Microsoft about the breach when he found the database online. However, Microsoft did not take the blame on itself and said that it was a fault of misconfigured Azure security rules that was deployed in the company on 5th of December 2019. In the next year, data breach happened where email address, IP addresses of the customers, and other sensitive details like bank account number and password were exposed. This security failure made customers less confident about using Microsoft products which resulted in huge loss for the company(Bertino 2016, pp. 1-3).
In February 2020, data researchers discovered that someone in a hacking forum leaked MGM Resort hotel’s personal information about more than 10.6 million guests. The organisation was reported about this incident where it was mentioned that the formers guest list including Justin Bieber, Twitter CEO Jack Dorsey and several government officials are leaked on the internet (Palmatierand Martin 2019, pp. 133-151). The very same day, it is reported that the information started appearing in several hacking forums that are viewed publicly. In July of 2020, the data was put on sale at a bargain price of $2,900. This became a huge blow for the company in the hotel industry as customer lost interest and trust in the group. MGM suffered in maintaining reputation and stayed out of limelight after the incident.
Identifying vulnerabilities for data security threat
In the case of Microsoft’s data breach, malware and misconfigured Azure security rules are responsible. The data was breached because of the rules and standards used by Azure security that were not reliable for the company. Malware is a code or file delivered typically over a network that explores, infects, conducts, or steals any behaviours an attacker desire virtually when they get the database not protected well (Kumar,et al. 2018, pp.691-697).
In the case of MGM resort’s data breach, the attackers attempt for tricking the employee within a victim company into downloading malware or into revealing account credentials and confidential data within a phishing attack. The Internet of Things surrounds several smart devices including printers, coffee makers, and other machines (Parn and Edwards2019). The problems with those devices are that those is hijacked by attackers for forming slaved network of compromised devices for carrying out attacks further (Bertino 2016, pp. 1-3).
Methods of Cyber-attack defences, IDs and IPS
There are several methods by which defence against the cyber-attacks are possible. In the case of Microsoft, the use of Intrusion Prevention or Detection Systems (IDS/IPS) are recommended as ethical methods. IDS helps in sending alerts to the company when there is a malicious traffic network detected in the company’s server. As Microsoft was not aware of the attack until it is reported by a data researcher, it is important to develop IDS and IPS systems. In the case of MGM Resorts hotels, there is a need of using a flexible method as it protects data of celebrities and government officials. For MGM, 24*7 network monitoring is needed on the server of the company. The possible method is to change the privacy setting from time to time and keep the firewalls up to date. The software applications used by this hospitality business needs to be updated with upgradation of the operating system. In this way, any vulnerability in the network or the computing devices can be identified easily (Kumar et al. 2018, pp.691-697).
Compare framework of cyber security, safety principles and guidelines of various tools to enforce data security and privacy
There are three top-rated cybersecurity frameworks that can be used to use various tools to enforce data security and privacy. The first one is the US National Institute of Standards and Technology (NIST) Framework that helps in improving critical cybersecurity structure. The Centre for Internet Security Critical Security Control (CIS) helps in establishing safety rules for the companies. The International Standards Organisation (ISO) frameworks ISO/IEC 27001 and 27002 can be applied for data breaches. The NIST is far better for Microsoft’s data handling as it is an IT company and needs proper corporate infrastructure to handle the problems. While comparing it to the other two standards, it can be said that CIS can be used for MGM Resorts as it needs to keep cyber laws in mind(Industry 2018, p.58).
Critique the mechanisms and prominent techniques to tackle sophisticated ICT attacks
For both Microsoft and MGM Resorts, handling data security is an important organisational task. There are several tools and techniques and mechanisms that can be used to handle the data legally and ethically. Anti-malware tools are a type of software of network security developed for identifying harmful programs and preventing them from spreading. Network anomaly Detection Engine permits in analysing the network, so whenever breaches happen, it will alert quickly. Application security assists the companies in establishing the parameters of security for any applications, which is related to the network security. Data Loss Prevention policies and technologies assist in protecting employees from compromising and mis-utilising confidential data. Firewalls are utilized in managing network traffic, permitting authorized traffic during blocking access to non-authorized traffic. Web security assists in preventing web-based threat from utilizing browsers as an access point for getting into the network (Palmatier and Martin 2019, pp. 133-151).
Conclusion
The data security can be handled by Virtual Private Network tool which is utilized in authenticating communication among an endpoint device and secure networks by creating an encrypted line in handling the data breaches in companies like Microsoft and MGM. The vulnerabilities are also identified and mitigated the risk.
A few recommendations can be made in this case:
1- The companies should adopt to monitoring technologies for the detection of security threats at a priority.
2- The use of IDS should be implemented compulsorily in every company.
References
Bertino, E., 2016, March. Data Security and Privacy in the IoT. In EDBT (Vol. 2016, pp. 1-3).https://www.cs.purdue.edu/homes/bertino/paper-a.pdf0.pdf
Industry, P.C., 2018. Data security standard. Requirements and Security Assessment version, 3, p.58.https://www.mastercard.us/en-us.html
Kumar, P.R., Raj, P.H. and Jelciana, P., 2018. Exploring data security issues and solutions in cloud computing. Procedia Computer Science, 125, pp.691-697.https://doi.org/10.1016/j.procs.2017.12.089
Palmatier, R.W. and Martin, K.D., 2019. Understanding and valuing customer data. In The Intelligent Marketer’s Guide to Data Privacy (pp. 133-151). Palgrave Macmillan, Cham.https://link.springer.com/chapter/10.1007/978-3-030-03724-6_7
Parn, E.A. and Edwards, D., 2019. Cyber threats confronting the digital built environment: Common data environment vulnerabilities and block chain deterrence. Engineering, Construction and Architectural Management.https://www.emerald.com/insight/content/doi/10.1108/ECAM-03-2018-0101/full/html
MIS301 Cyber Security Assignment Sample
Individual/Group - Individual
Length - 1500 words (+/- 10%)
Completion of the task below include:
a) Investigate and analyse the tenets of cybersecurity
b) Identify and communicate a range of threats and vulnerabilities to informational assets.
Submission Due by 11:55pm AEST Sunday of Module 2.2
Weighting 25%
Total Marks 100 marks
Instructions:
In Module 1, you learnt the five types of hacker threats that are common on the internet: commodity threats, hacktivists, organised crime, espionage and cyberwar. In Assessment 1, you are required to choose any three of the five types of hacker threats and undertake some research into the cybersecurity literature and/or media coverage to find one incident for each of the chosen three types of hacker threats. For each incident, you will:
1. describe the attack and the immediate result of the attack (i.e. what was the asset that was
compromised?)
2. describe the motivation behind the attack
3. identify and describe the vulnerability (or vulnerabilities) in the organisation that made the attack possible
4. describe the short-term and long-term impact (financial, reputational or otherwise) of the attack on the organisation
5. describe the responses from the affected organisation and society as a whole.
Reflect on all the incidents, and critically discuss the factors that make the prevention of cyber-attack challenging.
The incidents should meet the following criteria:
• The attack must be a cyber-attack.
• The attack was within the last ten years.
Your report should include the following for assignment help
Title page: It should include subject code and name, assessment number, report title, assessment due date, word count (actual), student name, student ID, Torrens email address, campus learning facilitator, and subject coordinator.
Table of Contents (ToC): It should list the report topics using decimal notation. It needs to include the main headings and subheadings with corresponding page numbers, using a format that makes the hierarchy of topics clear. Because you are including a ToC, the report pages should be numbered in the footer as follows: the title page has no page number, and the main text should have Arabic numerals commencing at 1. Create the ToC using Microsoft Word’s ToC auto-generator rather than manually typing out the ToC. Instructions can be found here https://support.office.com/en-
gb/article/Create- a-table-of-contents-or-update-a-table-of-contents-eb275189-b93e-4559-8dd9-c279457bfd72#__create_a_table.
Introduction (90-110 words): It needs to provide a concise overview of the problem you have been asked to research, the main aims/purpose of the report, the objectives to be achieved by writing the report and how you investigated the problem. Provide an outline of the sections of the report.
Body of the report (use appropriate headings in the body of the report) (1170-1430 words): Ensure that you address the tasks listed above. Do NOT use generic words such as ‘Body, Body of the Report, Tasks’ as section headings. Create meaningful headings and subheadings that reflect the topic and content of your report.
The body of your report should have the following structure:
2.0 Hacker threat 1
2.1 Description of the incident (approximately 80 words)
2.2 Motivation (approximately 50 words)
2.3 Vulnerabilities (approximately 80 words)
2.4 Short-term and long-term impact (approximately 70 words)
2.5 Responses (approximately 70 words)
3.0 Hacker threat 2
3.1 Description of the incident (approximately 80 words)
3.2 Motivation (approximately 50 words)
3.3 Vulnerabilities (approximately 80 words)
3.4 Short-term and long-term impact (approximately 70 words)
3.5 Responses (approximately 70 words)
4.0 Hacker threat 3
4.1 Description of the incident (approximately 80 words)
4.2 Motivation (approximately 50 words)
4.3 Vulnerabilities (approximately 80 words)
4.4 Short-term and long-term impact (approximately 70 words)
4.5 Responses (approximately 70 words)
5.0 Factors that make the prevention of cyber-attack challenging (approximately 250 words)
Conclusion (90-110 words): Restate the purpose of the report and key issues investigated, and the related findings based on your research and analysis.
Solution
Introduction
Cyberattacks become a common threat not only for personal data security but also for government and organizational information protection. It could be considered as an assault of cybercriminals to steal data, disable computers, breaks the networks, or use a breached computer system to commit vulnerable additional attacks. The rate of cybercrime and cyberattacks are increasing day by the day and becoming a major concern to cybersecurity experts globally [Referred to appendix]
Aim
This report aims at selecting three incidents that come under different kinds of cyber-attacks and provide a brief description of their vulnerability and impact.
Objectives
? To find out the cyberattacks that occurred in the last 10 years
? To evaluate the motivation and vulnerabilities of cyber attacks
? To estimate the short-term and long-term impact of a cyberattack
? To explore the response of those cyber attacks
Body of the report
2.0 Hacktivist
2.1 Description of the incident
Scott Morrison, the Prime Minister of Australia has stated that the Australian government and institutions become the major target of being hacked by sophisticated state-based cyber hackers. It has been found that hacking attacks are happening several times and it is increasing. In fact, Prime Minister has refused to identify ant state actors. According to his opinion, government institutes, political organizations, Australian industry, educational institutes, health services in Australia, essential service providers, along with operators of several important critical infrastructures are the major target of these attacks (Bbc.com, 2020).
2.2 Motivation
The motivation behind this kind of attack is to steal government data and breach it so that political and social agendas could be fulfilled by attackers. However, the actual motivation behind this track is not specified by Mr. Morrison (9 news.com.au, 2020).
2.3 Vulnerabilities
It is easy for attackers to utilize government data in order to influence common people to motivate them against political leaders. It could be political and social activism that could breach the government data and manipulate them.
2.4 Short-term and long-term impact
Short term impact of this cyber-attack could be deleting important information or disclosing any confidential government data so that reflects directly over the impression of the Australian government. In case of long-term impact, the misuse of data to defame the Australian government in front of the world or positing any illicit or illegal content to influence people against their political leader could have occurred.
2.5 Responses
The Australian government has strengthened its cybersecurity and recruited more efficient cyber experts to prevent those attacks. In fact, the prime mister has suggested improving technical defenses, especially for emergency service providers and health infrastructure (Bbc.com, 2020). Proper awareness in the public mind reading this kind of attack is the most effective response from the end of the Australian government.
3.0 Espionage
3.1 Description of the incident
In 2016, President Trump had hired a political data firm namely Cambridge Analytica for their election campaign. The purpose of this operation was to gain access to the private information and data shared by 50 million Facebook users (Granville, 2018). In this respect, the users were asked to proceed with a personal survey in which they needed to download and installed an application that has scrapped their own private pieces of information along with available friends in their friend lists so that their political overviews and information could be generated. However, this attack was made for the welfare of the government and no data breaching of Facebook users had occurred.
3.2 Motivation
The actual motivation behind this operation was not to breach or misuse any private information of users of Facebook. It was conducted for political motivation towards the election campaign. The main aspect of this operation was to identify the personalities and political behavior of American voters so that the election campaign could proceed accordingly.
3.3 Vulnerabilities
The activity of Cambridge Analytica was vulnerable for Facebook users as Facebook prohibits data selling or data transferring to any service (Granville, 2018). In this respect, the data are used to influence political behavior and overview of American voters hence it is a vulnerable practice.
3.4 Short-term and long-term impact
The short-term impact of this kind of hacking of user profiles in Facebook could be immense as it collected the personal data of users to influence their political views. The overall election process needed to be fair and impartial enough so it could be stated as malpractice. In case of long-term impact, the users cannot rely on or trust Facebook and raise questions over the security arrangements of this application.
3.5 Responses
Increasing the security service along with protection of accounts needed to be done by Facebook. Raising awareness not to download any kind of application or participate in any survey could be effective to protect these kinds of cyberattacks. In this respect protection of user accounts could be a major concern as it contains personal photos of users which might be used for any misconduct.
4.0 Cyberwar
4.1 Description of the incident
In 2017, 3 billion Yahoo accounts have been hacked and could be stated as the biggest theft and largest data breach in history (Stempel & Finkle, 2017). In 2013, Yahoo had compromised 1 minion of user accounts and Yahoo become forced to cut down their assets price in a sale to Verizon. Yahoo has stated that all of their user's accounts could be affected but they assured that stolen information could not consist of payment data, information of bank account, or passwords in cleartext (Theguardian.com, 2017). The major concerning factors are that that information is protected through easy-to-encryption that is outdated.
4.2 Motivation
The motivation behind this hacking could be stated as defaming Yahoo for its low-category security arrangements. Another major motivation for information stealing is to use those information details for wrong purposes, terrorism, or defaming popular personalities using Yahoo.
4.3 Vulnerabilities
Yahoo accounts are vulnerable to being exposed due to its outdated security protection arrangements. Due to these two huge cyberattacks occurring in this internet company, Verizon has made their offer lower by 350 million US dollars for yahoo assets (Stempel & Finkle, 2017).
4.4 Short-term and long-term impact
In case of short-term impact, the accounts of users might be used for the wrong intention, promoting terrorism, or conducting monetary breaching through bank account details. The long-term impact of this cyberwar is that these attacks might defame the security activity of Yahoo hence the number of users of Yahoo accounts would be reduced hence it could impact the revenue generation.
4.5 Responses
Yahoo has increased its security in the data protection of users in order to maintain cybersecurity. They have hired experts so that the security of user accounts could be protected so that no data could be accessed to proceed with any kind of misconduct.
5.0 Factors that make the prevention of cyber-attack challenging
Safeguarding IoT Devices
Safeguarding IoT devices is one of the major challenges that affect the prevention procedure of cyberattacks. It is true that IoT devices are easy to access through the internet and that is the major chance undertaken by cybercriminals (Zhang et al., 2020). Maintaining safety in IoT devices becomes a major challenge for cyber experts as these devices are interconnected and getting access to one device, all of the connected devices are accessible. In the case of government data, the IoT device's safeguarding process is the major barrier.
Figure 1: Factors that make the prevention of cyber-attack challenging
(Source: Created by Learner)
Outdated Security Service
Outdated security service is one of the major barriers to preventing cyberattacks. It is true that nowadays technologies are advanced and lack of scope to update security services in websites could be effective to prevent cyberattacks. According to Lezzi, Lazoi& Corallo (2018), outdated security services are easy to encrypt and that makes hackers access easily targeted devices or websites. However, a lack of updated security service could be considered a major challenge for cyber security experts.
Outdated Hardware
In order to increase the security of software, the developers often proceed with updating their software to enhance their security practice to protect stored data. However, continuous updates of software might not be supported by old devices hence the hardware needed to be updated soon (Mashiane &Kritzinger, 2021). The major challenge has been faced while the updated software could not be supported in a backdated device version or model. However, it could be stated as a major factor for challenging the prevention of cyberattacks.
Conclusion
It could be concluded from the above discussion that cybercrimes becoming a major concern in both developed and developing countries to access the information that could be vulnerable for individuals, groups, or the whole nation. Hacktivists, espionage, and cyberwar are three major cyberattacks among cybercrime. These attacks are affecting not only personal data but also organizational aspects. The vulnerabilities and impacts of these attacks are prolonged and wide that could defame individuals or organizations, or even the whole country. However, raising awareness among people and indulging in proper response is crucial to prevent these cyberattacks by increasing security services from the end of the country, organizations, along individuals.
Reference
9 news.com.au, (2020). 'Sophisticated state-based' cyber attack hits Australian government, businesses in major breach. https://www.9news.com.au/national/cyber-attack-australia-scott-morrison-government-private-sector-breach-of-security/e621ae47-f810-4fa7-9c11-3caa3b09f4dc
Bbc.com, (2020). Australia cyber attacks: PM Morrison warns of 'sophisticated' state hack. Retrieved from https://www.bbc.com/news/world-australia-46096768
Granville, K. (2018). Facebook and Cambridge Analytica: What you need to know as fallout widens. The New York Times. Retrieved from https://www.nytimes.com/2018/03/19/technology/facebook-cambridge-analyticaexplained.html
Lezzi, M., Lazoi, M., & Corallo, A. (2018). Cybersecurity for Industry 4.0 in the current literature: A reference framework. Computers in Industry, 103, 97-110. https://www.sciencedirect.com/science/article/pii/S0166361518303658
Mashiane, T., &Kritzinger, E. (2021). Identifying behavioral constructs in relation to user cybersecurity behavior. Eurasian Journal of Social Sciences, 9(2), 98-122. https://eurasianpublications.com/wp-content/uploads/2021/07/EJSS-4.2.4.1.pdf
Stempel, J. & Finkle, J. (2017). Yahoo says all three billion accounts hacked in 2013 data theft. Reuters. Retrieved from https://www.reuters.com/article/us-yahoo-cyber/yahoo-says-allthree-billion-accounts-hacked-in-2013-data-theft-idUSKCN1C82O1
Theguardian.com, 2017. Yahoo says all of its 3bn accounts were affected by 2013 hacking. https://www.theguardian.com/technology/2017/oct/03/yahoo-says-all-of-its-3bn-accounts-were-affected-by-2013-hacking
Zhang, J., Li, G., Marshall, A., Hu, A., & Hanzo, L. (2020). A new frontier for IoT security emerging from three decades of key generation relying on wireless channels. IEEE Access, 8, 138406-138446. https://ieeexplore.ieee.org/abstract/document/9149584/
COIT11226 System Analysis Assignment Sample
Due date: Week 12 Friday (7 October 2022) 11:00am AEST
Weighting: 40%
Length: 1,200 to 1,300 words (word count includes all contents except the cover title page, table of contents, figures, and references)
Required Tasks in This Assignment Help
Assuming that the waterfall model has been chosen for implementing the new system to replace the current system. Also assuming that some programs have been written and are ready, whereas some other programs are not yet ready at the current stage of development. Complete the following tasks and document your work in your submission:
1. Testing:
a. Among unit testing, system testing, and user acceptance testing, discuss and explain which of them is/are applicable at the current stage of development.
b. Suppose the project team wants to apply white-box testing to generate test cases for testing the new system. Discuss and explain the feasibility of applying white-box testing to test the new system.
c. “Assume” that white-box testing is feasible, and it has been applied to generate test cases, do you think that the project team still needs to apply black-box testing to generate additional test cases for further testing? Why?
2. Discuss the merits and drawbacks of applying random testing to test the new system.
3. In view of the business operations of CNP, which system installation approach should be used to replace the existing system by the new system? Why? (Note: In this task, you are notallowed to select two or more installation approaches. Students who select more than one
installation approach will receive zero mark for this task.)
Solution
TESTING
a. Assuming that the waterfall model has been chosen in the Computer No Problem for implementing the new system to replace the current system. Also, assuming that some programs have been written and are ready, whereas some other programs are not yet ready at the current stage of development.
? Unit testing- It is a sort of software testing method which is achieved on a single entity, unit or module in test its modifications. This testing phase is often carried out by the developers throughout the request's expansion. Each of the unit of testing may be assumed of as a method, service, process, or object (Testim 2022). In short, this testing method tests each program individually and does not connect any other ones with it.
• The common testing methods that it uses are-
• Gorilla testing
• White box testing (Vijay 2018).
? Integration testing - software testing, the term "integration testing" refers to the practise of evaluating a programme as a whole, as opposed to its individual parts. Finding issues with module-to-module interactions, communications, and data flows is the primary goal of interoperability testing. When integrating components or sets of units into a system, either a top-down or bottom-up strategy may be used (Vijay 2018).
? System testing- the last one is system testing as it's name suggests it is referred to the software testing method of the entire system at once. System testing is a kind of testing where the entire system is examined and compared to a set of predetermined criteria (Vijay 2018).
As per the case scenario of Computer No Problem, the project follows waterfall methodology i.e. a step by step process of SDLC. Project is in the middle of development and there are still programs left to be developed and only a few have been developed, which means that it is in Integrated testing phase, where the developed programs can be integrated and tested together for the proper functioning and analysis, however it can not be in system testing because there are still undeveloped programs left, without which system can control be made and tested.
Figure 1: Testing of software
(Source: AUBERT 2020)
b. To ensure proper input-output flow in the Computer No Problem Project, enhance usefulness, and strengthen security, White Box Testing examines the software's internal structure, architecture, and code. White box testing is also known as Clear box testing, Open box testing, Transparent box testing, Code-based testing, and Glass box testing since the code is exposed to the testers. A white-box test case involves running a piece of software with known input parameters to verify known output values (ReQtest 2022). If these numbers don't add up, it's a problem. This is a theme across the whole of the program.
Figure 2: white box testing
(Source: Lemaprod 2018)
The feasibility that this technique to generate test case for testing new system are -
• Transparency- Since everything is laid out for the tester to see, they can thoroughly examine the whole structure and code base, allowing for prolonged testing.
• Less time to test case for testing new system- When all the software data is easily accessible, the tester can quickly comprehend the code and complete the tests, but huge applications without complex models might take weeks or months to test (Packetlabs 2021).
• Easy Automation of test case- Many technologies exist to facilitate automation of the test cases, therefore significantly shortens the time required to complete them.
• Detects risks and optimises code- It is useful for finding undetected bugs and removing unnecessary code. Due to the abundance of data, it should be possible to spot vulnerabilities and problems in the software (Hamilton 2020).
Figure 3: feasibility of whit box testing
(Source: Author 2022)
c. As the project aims at replacing the current system due to key operational and UI challenges. Hence, it is necessary to evaluate the end user structure of the system or the outer structure which will be presented to the user, it can evaluate with the help of Black box testing.
Black Box Testing is referred to the testing approach in the project of Computer No Problem, which does not take into account the internal structure, concept, or product implementation of the product being evaluated. In other terms, the person performing the test is unaware of its internal workings. The Black Box is focused on simply assessing the system's exterior behaviour. The program's inputs are analyzed, as are the outputs or reactions it generates (Practitest 2021).
Even after conducting thee white box testing in the Computer No Problem, it is necessary to implement the Black Box testing approach because of the reasons mentioned below-
? Black box testing examines a system end-to-end. A tester may replicate user behaviour to evaluate whether a system delivers on it's own claims, just like end-users don't care how a system is developed or designed. A black box test assesses UI/UX, web/application server, database, connections, and system integration (Imperva 2020).
? Black box testing can be used to check how certain parts or operations of the source code being tested work.
? Using the regression technique, it is possible to see if a new version of the application shows a transformation, or a loss of features from the previous version.
? Testers can simply split the independent variables in the division of groups, or panels, and appraise only one exemplar input from each group (Imperva 2020).
? With this method, one look for mistakes that development teams often make when structure similar plans. For example, developers as well as the test performers can check to see how the programmer dealt null values in a field, values of the arithmetic field or data points in a text-only field, and cleansing of input data, or if a user can enter source codes, which is important for security (Imperva 2020).
1. MERITS AND DRAWBACKS OF APPLYING RANDOM TESTING
Random testing is a kind of testing process of software in which the computer is examined using randomized and unbiased inputs & test cases. Monkey testing is another term for random testing. It is a black box evaluation framework approach wherein the tests are picked at random and the outcomes are evaluated using some software identifying to determine if the output is accurate or erroneous.
Table 1: merits and demerits of random testing
2. System Installation Approach
In the installation of Computer No Problem, for function of sales and purchasing as well as maintaining the records, it is necessary to look for the good system installation approach as it is a one time investment and it should not be further create problem. In order to look for the new system into the company, the company is going with the Web - based installation approach, that means each and every component will be operated though the web services and CRM system will be installed. Along with that, in order to maintain the data of the company, cloud infrastructure is installed and databased management system will be utilised.
REFERENCES
MIS611 Information System Capstone Assignment Sample
Individual/Group - Group (five people)
Length Part A—Report (3,500 words +/–10%)
Learning Outcomes The Subject Learning Outcomes demonstrated by successful completion of the task below include:
a) Analyse relevant industry challenges to support the development of IS solutions for addressing specific organisational problems.
b) Produce the appropriate documentation to provide evidence of project progress with project stakeholders.
c) Integrate professional and SMART skills to complete individual and team tasks in collaboration with team members to develop a robust solution that meets stakeholder needs.
d) Demonstrate professional skills to complete individual and team tasks Communicate progress and solutions to the client/representative and non-specialists and adjust according to feedback.
Submission Due by 11.55 pm AEST/AEDT, Sunday, end of Module 6.1 (Week 11)
Weighting 20%
Total Marks 100 Marks
Assessment Task for Assignment Help
In this assessment, you will finalise your report and recommendations to your client/organisation. You will incorporate all feedback provided by your lecturer throughout the trimester, including additional research or content to be completed. The final report must be structured as per the guidelines detailed in these assessment instructions. Note, you are producing an industry-level final report, not resubmitting your previous assessments.
Please refer to the Task Instructions for details on how to complete this task.
Format of the report
The report should use 11-point Arial or Calibri font, be 1.5–line spaced for ease of reading and display page numbers at the bottom of each page. If diagrams or tables are used, attention should be given to pagination to avoid the loss of meaning and continuity by unnecessarily splitting information over two pages. Any diagrams must be appropriately captioned.
Solution
Introduction
This report is conducted to define the major issues of Giverly’s current shopping platform. The customers of Giverly are facing issues while they make orders. They also get issues to individualize and make orders. Due to these issues, Giverly’s customer base came in danger and its overall sales get reduced. Giverly wants a permanent and robust solution against such issues This report aims to analyze the overall system needs, stakeholder requirements, and customer demands so, that an appropriate solution can be proposed. This report is mainly a roadmap of new planned shopping platform of Giverly so, that previous platform issues can be resolved and customers' expectations can be maintained. This report covers the stakeholder details, customer feedback & perceptions, brief research to implement the system, stakeholder needs, problems associated with new system, UX/UI elements for planned system, cyber-security considerations, prototypes, testing, and communication plan to deliver the project.
Purpose
The goal of this project is to implement a greater-designed shopping platform for Giverly so, that its customers can effectively make orders of Giverly goods as well as services on individual level. Based on this goal, the purpose of this report is to design a roadmap so, that client can analyze the scope of project and ensure everything is in right place. This report will provide an idea of how will be the project implemented including all-possible details such as stakeholder details, its user interface designs, customer needs, possible issues/problems, overall testing, etc.
Background
Giverly is an online retail company that a customer can use for shopping all-kind of products in a single system. Giverly has a large customer base as it offers multiple products with high quality, 24x7 availability, and cost suitability. The delivery facilities are also free for most of the shopping in Giverly. The customers are well satisfied with Giverly’s performance and online shopping facilities but for last 2-3 months, customers are complaining to have issues with its system while making orders (Giverly, 2022). They have also restricted to individualized orders of the products. Due to this issue, Giverly is planning to implement a new system so, that customers can easily access and make orders on that. This planned project is almost ready to be implemented as its overall planning is done including stakeholders, customer needs, resources, problems, security considerations, interface designs, and testing. Now, this time, a complete roadmap and information related to proposed Giverly platform are presented.
Scope
a) Goals and Objectives
Goal
To implement a greater-designed shopping platform for Giverly so, that its customers can effectively make orders of Giverly goods as well as services on individual level.
Objectives
• To measure the potential issues of Giverly’s shopping platform.
• To gather and understand the needs of customers to design new shopping platform.
• To develop a customer-driven Giverly shopping platform.
b) Exclusions
• The difficulties to design Giverly’s shopping platform for marketing and sales.
• The unsafe & risk-oriented resources, applications, as well as activities.
• Access of Giverly data to all-associated project members.
c) Constraints
• The participation of sales team is not approachable/active in developing this shopping platform project because of their busy schedule.
• To get customer requirements/feedback, additional time is needed.
• The development time estimation for this Giverly shopping platform is six months which can influence current customers & Giverly’s overall sales.
d) Assumptions
• Due to any new demands raised by customers, additional time requirements for research, and other changes due to market changes, the budget can be increased.
• During project implementation phase, security-based risks can occur (Giverly, 2022).
e) Deliverables
• A roadmap for Gierly’s new shopping platform.
• The user interface designs of the shopping platform.
• A customer-driven platform.
Stakeholders
(Smith, 2000)
The stakeholders that should be managed by Giverly organization are their sales team, employees, customers, and HR team. It is also necessary that they should adopt provided recommendations if they seem it will be worthy for them otherwise, they can give their suggestion, and then overall decision can be made to satisfy them and to make the system successful.
Customer Persona
Persona1
(Duda, 2018)
Persona2
(Duda, 2018)
Empathy Maps
(Melo, et.al., 202)
(Cairns, et.al., 2021)
Research
By researching both customer personas, it can be stated that they are particularly satisfied with Giverly’s shopping platform. They are using this platform largely to make any kind of orders because Giverly offers a number of orders including fashion, hotel, grocery, travel, technology, and entertainment at their single sales platform. The customers want to use this system as they found it convenient and secure. But they are facing issues related to making individual orders from this system due to some technical or other errors (Giverly, 2022). When they make orders, their order-making process is stuck in the middle and the details of orders are also inaccessible to them. Therefore, they have similar kinds of objections to using this application/system due to the order-making issues and lack of individualized ordering features. Both customers are well-educated and working in relevant positions. One customer is married woman and another customer is single male. Both are dependent upon Giverly’s platform to make most secure and fast delivery but in last few months, they are facing order-making troubles.
Therefore, they have objections to using this Giverly platform and seeking new alternatives to make orders. They found Goverly’s current platform unresponsive, time-consuming, and unapproachable. They have fears to got stuck while making orders and due to absence of notification, their order will be unconfirmed which can waste their time.
Stakeholder Requirements
To define the requirements of key stakeholders, simple method i.e. MoSCoW is used.
.png)
(Sharma, 2022)
Customer Journey Map
Figure 1: Journey map
(Source: Author)
Problem Statement
In Giverly, the stakeholders are facing issues to fix the fault of order-making process in their online shopping platform. The order-making process also faults that it does not allow the customers to individualize and make orders. The process of order-making is stuck in middle and it takes longer time to execute. The sales team and other employees identified this issue and informed the system developer (Giverly, 2022). The Giverly system is not responding to the customer’s approach and it became complex to address that issue. Thus, the major problem of Giverly belongs to their sales platform where order-making process is not working properly which causes the stoppage of platform’s overall functionality.
UX/UI
By considering the problem associated with Giverly’s platform, a new system/platform is planned to develop in which user-friendly interfaces along with transparent functionalities will be designed which effectively regulate the order-making process and individual order-making as well. The UX/UI design will be done with a very simple and visualized format so, that customers can understand and access each feature easily. The UX/UI design’s layout will be designed in such a way, that different categorized products are arranged in a systematic series so, that customers can easily reach them. The associated details will also keep in layout. Each notification will be visualized to customers and they can also put their items in their wish-list, favorites, and shopping cart for later shopping. Interactive interface, navigation bars, and menu items will be designed with proper image specification so, that customers can conveniently approach everything they want (Ho, 2021).
Accessibility Requirements
To make Giverly’s current platform highly accessible by forming it operable, perceivable, robust, and understandable. Therefore, to ensure these factors for proposed Giverly shopping platform, the accessibility requirements are maintained by keeping the balanced contrast ratio, labeling the layouts clearly, keeping consistent navigation, and keeping simple headings. Subheadings, & spacing, giving user control, designing different categories, views, and screens, not relying on colors, providing feedback for omissions & errors, and offering alternatives specifically for consuming media (DBS, 2022).
Cyber-Scurity Requirements
To resolve the issues of current Giverly shopping platform, a new system is planned and proposed so, that the order-making issues can be removed completely and a new version of Giverly platform satisfied customer needs. As discussed, due to this order-making issue, the customers are in fear of security risks. Thus, to maintain and ensure the security in new updated version of Giverly platform, security technologies and models will be implemented. Customers are needed security environment while dealing with this new application so, the whole system will be implemented by concerning the sensitive security considerations and providing automatic saving features in case of any disruptions. Other security considerations that will be implemented in this Giverly system are-
• User authentication
• Data authentication
• Cloud infrastructure
• Payment security
• Network security
• Cybersecurity features
• Accountability, privacy, & confidentiality in engagement with system
• Limited access to customers and database security
• Encryption & decryption (Adu, et.al., 2018)
Wireframes
Figure 2: Login Page
(Source: Author)
Figure 3: Home-Page
(Source: Author)
Figure 4: CategoryPage
(Source: Author)
Test
The above-specified prototypes are clearly showing how customer will be getting their new Giverly shopping platform. This new version of platform will help the customers to provide the overall shopping of all-possible products in a single system. These prototypes are designed with a user-friendly format in which the users are allowed to visualize, access, and save the products. Security is highly considered so, that each customer can rely on Giverly shopping platform without compromising their privacy and confidentiality. Each layout is designed in an effective manner and simplicity is maintained so, that customers can conveniently use the application to search, order, and cancel their needed products.
The first prototype is a simple login page in which the user can login after registering on the application. The login page is very simple and easy to understand without any additional animation or unnecessary images. Another page is home page where user can easily see the layouts i.e. menu, history, and update. The layout “menu”, is categorized into different shopping formats with different products. Customers can scroll down the categories and select particular categories of products. On history page, the customers are allowed to access the details of their previous orders, canceled orders, confirmed orders, payment details, etc. Another layout is update layout in which customers can easily update their payment-related details like bank details, phone number, address, login credentials, and many more. Therefore, they are also allowed to add the products to cart and wish-list. Consequently, another page is category page that is designed as an example to show if a customer will search for a particular product like sports watch then a list of latest & trendy sports watch will be categorized. The customer can click on particular watch and see overall details. After being satisfied with details and prices, they can make orders with free delivery facilities. Hence, customers’ order-making issues are completely solved with new version of Giverly platform. At last, the project needs to be updated time-to-time for further use.
As mentioned in above section, the proposed Giverly platform will provide effective, clear, straightforward, and convenient ways to make orders as per customers’ needs. The older version of Giverly’s platform was unable to make orders conveniently. Due to some technical or software issues, the platform stuck in the middle of order-making process which became a failure of Giverly’s online shopping system. Thus, the management team has decided to implement a new system so, that customer needs can be fulfilled quickly because customers want to use Giverly platform because it is secure and have all-possible products in single system (Giverly, 2022). The proposed solution i.e. new Giverly shopping system and this new system is highly user-friendly, secure, and convenient to make orders. Customers can directly search for a product and categorized order layouts will be helpful for them to approach needful products. They can also access the details of each product so, that they can confirm that order and add in wish-list for later purchases.
Communication Plan
This is very simple for Giverly to deliver this new solution to their large customers because Giverly has large customer base. Giverly customers are eagerly waiting to have a solution because they trust Giverly’s products, security, and service facilities. The solution will take a significant time to be implemented completely till then Giverly advertises this solution and promotes its new features using social media platforms, and its organizational website, and directly communicate with customers when they come to Giverly’s shopping centers. In addition, a survey can also be conducted to get the customer’s response on newly proposed solution.
To deliver the proposed solution to the customer, Giverly can use visual engagement tools like video chat so, that they can get aware of this system. By giving the access link or application on social media platforms and official websites, the customers can get the system on their devices. Customer metrics & chatbots are other communication alternatives to inform the customers about newly launched Giverly system (Patel, 2022).
Recommendations
With an overall experience of this Giverly project, it has been analyzed that the scope of project is very vast and profitable from the business perspective. The customers are also well satisfied with the newly-proposed system’s standards. The main issue for which, Giverly and its customers are facing issues is completely resolved by implementing new system. The previous platform had an issue with making the orders and it restricted the customers to make individualized orders. Based on the issue, Giverly’s management team has decided to implement a completely new project in which the issue will be sorted out and customers’ needs will be prioritized (Giverly, 2022). To ensure the project’s success, stakeholders are finalized to develop the system as per their interest and impact levels. The customer’s responses are also taken so, that previous mistakes can be improved and customer’s needs can be fulfilled. Giverly should understand the customers deeply and try to establish their perceptions using customer personas, empathy maps, and customer journey maps, The MoSCoW method is also supportive for Giverly to interpret the project accordingly.
Consequently, the problem statement is clearly articulated so, that relevant solutions can be planned. Based on the solution, potential UX/UI designs are proposed in which user-friendly environment, security considerations, easy order-making functionalities, and easy accessibility. However, the cyber-security considerations are well-planned using network security, encryption, decryption, and many more methods. The prototypes are designed as per mentioned solutions that customers will find more suitable to make individualized orders with other features. The testing done in this report is also ensuring that the proposed project will be highly successful.
With this new project, Giverly will get new opportunities to do business and earn trust of their customers. It will result in high productivity and future stability of Giverly. In future, based on the customer’s responses the planned project will be implemented and delivered (Zakharenkov, 2019). Consequently, its timely security and upgradation will be monitored and done so, that best online system can be provided for customer’s usability.
Referencing
.png)
MIS610 Advanced Professional Practice Assignment Sample
Individual/Group - Individual
Length - 1500 words (+/- 10%)
Learning Outcomes - The Subject Learning Outcomes demonstrated by successful completion of the task below include:
a) Investigate and reflect on the role of a Business Analyst (or chosen career path) in the contemporary business environment and society more broadly.
b) Cultivate an understanding of who the student is as a professional and what their impact should be to the enterprise, taking into consideration global ethical viewpoints.
Assessment Task
Write a 1500 words Ethics Project Report for an ethical dilemma scenario provided and make a professional decision by analysing it from a range of ethical perspectives with the aim of understanding:
a) how ethics is part of your day-to-day professional practice, and
b) how your current thinking about ethical issues influences your professional practice.
Please refer to the Instructions for details on how to complete this task.
Instructions for best assignment help
1. Read the MIS610 Ethical Dilemma that will be in the Ethics Case Study that will be provided in class in Week 3.
2. Reflect upon the incident discussed in the ethical dilemma scenario provided.
3. Write a 1500 words report that comprise of:
• A short description of the workplace event. That is your interpretation of the ethical dilemma (200 words).
• A reflection on how you would decide in response to the ethical dilemma (800 words).
The following questions need to be considered in your answer:
What do you think is the issue in this situation?
What would your response be to this issue?
Justify your answer – why would you respond in this way?
What laws, ethical codes, or personal ethical stance apply to the situation?
Why would you choose one action rather than another?
In what ways do you think your own cultural background influenced the way you would answer this situation?
• Identify two ethical frameworks or approaches (chosen from the the frameworks and approaches discussed in class), that could have helped you with your ethical decision.
• Discuss how the frameworks might have helped you reach the same decision or a different decision as you identified above. This should include reference to two relevant reliable sources that are not part of the subject resources (500 words).
The following questions will help your reflection:
What ethical framework (if any) did you use in reaching your original decision?
How do the ethical frameworks you have chosen apply to the situation?
How does a line of ethical reasoning arrive at your original decision?
How does a line of ethical reasoning arrive at a different decision?
• You need to identify and apply the two frameworks, not describe them. Descriptions of the frameworks can be found in Module 3.1 (Utilitarian approach, Rights approach, Justice approach, Common Good approach, Virtue approach, and Egoism). Additional ethics case studies will be reviewed in class.
4. You are strongly advised to read the rubric which is an evaluation guide with criteria for grading yourassignment. This will give you a clear picture of what a successful report looks like.
Solution
Description of Ethical Dilemma at Volkswagen
In September 2015, it was found out by the Environmental Protection Agency of the US that Volkswagen had installed a defeat device or software in its 11 million vehicles across the world for cheating emissions test (Pladson, 2020). It was discovered that this software enabled the vehicles to detect emissions test scenarios and accordingly change their performance for improving the results. These irregularities in tests for measuring emission levels of carbon dioxide were also detected in around 800,000 cars in Europe along with petrol vehicles (Hotten, 2020). This shows that the emissions scandal generated a huge impact in the entire automotive industry of the world. The Volkswagen scandal demonstrated a number of issues in the company culture. This is a perfect example of failure of corporate governance of the company with ineffective leadership that led to such unethical actions (Crête, 2016). It was found out that the VW engineers were unable to meet the emission standards with the given time and allocated budget, thereby pointing out to the pressure given from top executives. In addition, it also portrays the presence of a faulty corporate culture that focuses only on outcomes and ignores how employees perform their tasks.
Response to Ethical Dilemma
The Volkswagen emission scandal pointed out various internal issues present within the organization that prompted the employees to act in such a way with the knowledge of their top leaders. The fundamental issue here is the lack of proper company culture with strict codes of ethics and regulations that shape behaviors of both managers and employees. The corporate culture of VW focused on gaining the desired outcomes of passing the US emissions tests (Arora, 2017). The managers completely ignored the fact how such performance would be generated from the employees without having any ethical considerations of the same. Furthermore, the reward system of the company involves paying bonuses based on individual and team performance and productivity, which is applied to all levels of management throughout the organization (Mansouri, 2016). This might have motivated the engineers in rigging the emissions tests for meeting the unrealistic goals set by the top leaders. Besides, the boardroom controls and peculiar corporate culture resulted in this unethical action, which further demonstrated the lack of proper corporate governance and leadership in the company (Bryant & Milne, 2015). Thus, these issues were evident from the emissions scandal of Volkswagen pointing out to its ineffective company culture, leadership, governance and ethics.
The foremost response to this issue would be to improve the company culture in Volkswagen, which is the primary reason for such unethical conduct. Fostering a positive and healthy corporate culture is essential for survival and success of any organization. VW was suffering from ineffective leadership, unrealistic goals, inadequate reward system and failure of corporate governance, which all point out to its culture (Jung & Sharon, 2019). This shows that building a company culture with the help of policies, practices and people would have been beneficial for the organization. With such an ideal work environment and employees and managers being motivated and encouraged to display ethical behavior, the scandal could have been avoided (Warrick, 2017). The engineers would not have to resort to such unethical actions; instead, the company culture would have itself resulted in higher productivity, increased revenues and healthier workforce, leading to the company’s success. Here, the top executives and leaders should also have played a significant role in demonstrating ethical actions and leadership to create examples in front of managers and employees (Nelson, et al., 2020). Thus, responding in a more ethical way for passing the emissions test in the US would have been the primary focus of the organization.
From the case of VW scandal, it can be seen that the organization failed in its corporate sovereignty. It violated the US Clean Air Act, where both the State and its laws played a significant role in the later period in the different events surrounding this scandal. The International Council on Clean Technology (ICCT) discovered about the presence of defeat devices for rigging the emissions tests by undertaking independent actions (Rhodes, 2016). This helped in showing how the diesel cars of VW could have been made more environment friendly for passing the stringent US anti-emissions laws. In this regard, the automotive company not only violated these acts or laws but also their internal code of ethics available in the organization (Rhodes, 2016). Here, the engineers deliberately violated such ethical codes by installing such cheat software for passing the emissions tests in the US. This shows that managers and employees with the knowledge of their top leaders engaged in highly organized and conspiratorial efforts for defying the law, thereby disregarding corporate business ethics and harming corporate sovereignty (Rhodes, 2016). The organization resorted to great extents for admiring its own ethical values but deliberately hiding its own criminal activities. It bolstered its own sovereignty by acting above the law for increasing its corporate growth. This led to the company being held accountable for its environmental and legal transgressions, thereby questioning its corporate sovereignty.
The engineers might have faced ethical dilemma while installing the software in the vehicles for rigging the US emissions test. This unethical action was undertaken for passing the test within short time and limited budget. The excessive pressure of meeting strict deadlines and showing improved performance to get bonuses could have motivated and forced the employees to act in that way. However, lack of personal values and principles associated with ethical conduct was yet another reason that these employees resorted to such actions.
I would have chosen to act in a more ethical way without giving in to such unethical actions for gaining desired outcomes. In this regard, I would have informed my superiors and managers about how it would be impossible to pass the test in an ethical way within the stipulated time and budget. Here, cultural background would have played a significant role as it helps in shaping an individual’s principles, values, attitudes and behavior. Thus, these cultural values would have refrained me from undertaking such unethical actions.
Application of Ethical Frameworks or Approaches
Two ethical frameworks that can be used here for better understanding the VW emission scandal are Kantianism and Utilitarianism. According to Kantianism approach, the motives for corporate actions of organizations should possess a sense of duty, protect employee values and focus on undertaking moral decisions (Rendtorff, 2017). However, from the VW emission scandal, it is evident that the company made illegal and immoral choices that had negative impacts on employees, customers and general public. The engineers could not act as independent and rational agents, they had no freedom to act based on their personal judgments and their concerns were ignored for meeting the outcomes. This clearly shows that Volkswagen violated this ethical approach by treating both customers and employees as money-making commodities to increase business growth (Ameen, 2020). Furthermore, the company further opposed the principles of duty and morality for forbidding profit-based motives and rather forced the employees to defy goodwill intention. The expansion of corporate sovereignty was the main goal of VW, which motivated it to further violate moral law. This shows that basic business ethics was also ignored by the company for fulfilling its own selfish interests (Rendtorff, 2017). Besides, the company engaged in lying and fraud causing harm to different stakeholder groups by deceiving regulators and customers. This shows that it could not uphold the rights and interests of all stakeholder groups, thereby violating the deontological decisions under Kantianism. Moreover, Volkswagen’s actions were not permissible for being self-defeating and contradictory that could have generated negative results from its universal participation (Ameen, 2020). Thus, it can be said that the company resorted to unethical conduct from the Kantianism approach.
The fundamental purpose of Volkswagen for rigging the emissions test for to increase its growth and enhance shareholders’ value without considering any ethical implications. It has violated the Utilitarianism approach of producing the greatest good for the maximum number of people (Dura, 2017). This violation has been further evident from the harmful impacts caused to all stakeholders like customers, employees, general public and regulators. The emissions scandal resulted in job losses, salary deductions, revenues reduction, damaged corporate reputation, environmental pollution and stock devaluation. This shows that no greatest good was created for any of the stakeholders of the company (Ameen, 2020). VW also violated the Utilitarian principle of maximizing human good instead of only focusing on increasing profits for the company. This is evident from the fact the VW acted only on profit-motives for expanding its market share and revenues in the US by rigging the emissions tests. It did not evaluate the costs and benefits of such unethical actions, thereby harming all the stakeholders in the process. It shows that corporate and ethical policies of the company did not run in accordance with the Utilitarian ethical approach (Dura, 2017). Thus, from both the ethical frameworks, it can be said that the actions of Volkswagen were unethical and unjustified.
References
.png)
DATA4600 Business Analytics Project Management Assignment Sample
Word Count: 2000 Words (+/-10%)
Weighting: 40 %
Total Marks: 40
Report Structure:
Introduction: Introduce your two projects, identify similarities and differences.
Operational Project (700 words) based on operational case study:
Outline the scope of the project
Evaluate your natural leadership style and how you will use it to lead the project
Suggest a project management methodology and integrate it with the leadership style
Estimate the budget of project
Evaluate possible human resources involved, and associated factors, e.g. workstyles, training & cultural fit
• Discovery Project (700 words) based on an innovation case study of your choice:
Describe how you will assess the risk of the project using predictive project analytics (PPA)
Justify why this project should be undertaken given the PPA relating to its impact
Choose an optimal leadership style for the project
Suggest a project management methodology and integrate it with the leadership style
Estimate the budget of project, and why such an estimation may be difficult given the nature of innovation
Describe the team undertaking the project, or if not mentioned in the case study, suggest one that might be suitable and diverse
Explain how you would democratise the project across the business
• Reflection:
Write a short 200-word reflection of issues you may encounter when managing these projects.
Conclusion: (400 words max)
• Compare the two projects in terms of:
Characteristics
Project methodologies
Human resource requirements
Optimal leadership styles for both
Draw conclusions about how running these two projects would differ.
Solution
1. Introduction
There are two projects in consideration in this report – one operational project and another discovery project. The operational project in consideration is the implementation of location based analytics by Wendy’s. John Crouse of Wendy's has been working on developing this new system over the years that integrates geographic location mapping with demographic analytics (Burns 2014). The combination of the two helps Wendy’s to identify sites that are more likely to be successful for business. On the other hand, the discovery project being considered is the development of fully autonomous cars (Marr 2019). One of the largest business spearheads in the world, Elon Musk has already stated that Tesla will develop fully autonomous cars by the end of this year.
This report analyses these two projects from different perspectives and will compare the two using specific parameters for online assignments.
2. Operational Project
2.1 Project Scope
The scope of the project involves development of a fully working system that uses location based demographic analysis as a part of the business analytics process. The system integrates location intelligence tool with demographic analytics to determine specific new locations that are most likely favourable for business for Wendy’s food chain (Bartoletti et al. 2021). Despite the project being going on for several years, there are still lots of work to be done to perfect the system such that it can be used efficiently and effectively.
2.2 Natural Leadership Style
My natural leadership style is democratic leadership and I always believe that the opinions and ideas of all team members should always be considered with importance. If I am being assigned to lead this project, I will apply democratic leadership style in it as well. This will allow my fellow team members to apply and discuss their own ideas and inputs that I will consider before making final decisions on the project. I will conduct regular team meetings to listen to the team members’ ideas so that different perspectives can be considered while moving forward in the project.
2.3 Project Management Methodology
The most appropriate methodology for the project is Agile method. This project involves a new type of technology that combines two other different technologies to create a system that will perform different functions for the business. As such, using Waterfall method will not be suitable as the focus on quality will not be sufficient. The iterative approach in Agile means constant improvement will be made while the system is being developed throughout the project lifecycle (Huang et al. 2021). Moreover, democratic leadership style will also be suitable for this project management methodology as inputs from the team members will be utilised constantly for continuous improvement during the iterations of the project. Running multiple iterations with continuous improvements will ensure the quality aspect of the system is not compromised with.
2.4 Budget of the Project
Development of a totally accurate budget is significantly difficult in Agile projects and even more in this project that has been going on for years. The long drawn continuation of the project also means that the estimated budget amount will be significantly high and the company should be ready to invest accordingly for the project (Xanthopoulos and Xinogalos 2018). However, at the same time, the company can also expect that the project will save them millions in expenses and will increase the profit margin significantly that will also help them invest further in the project. An estimated budget for the overall project is shown in the following table.
.png)
Table 1: Budget Estimation for the Operational Project
2.5 Human Resources Involved
There are a significant number of human resources involved in the project while different types of roles and responsibilities. Each human resource will have specific roles that they must perform throughout the course of the project (Uphaus et al. 2021). The human resources in the project include the primary stakeholders who are directly involved in the project as well as the regular team members who will be involved in the execution of the project. The main human resources involved in this project are listed as follows.
.png)
Table 2: Human Resource Requirements for the Operational Project
3. Discovery Project
3.1 Predictive Project Analysis and Risk Assessment
Predictive project analysis is a relatively new tool that is very useful in assessing risks in a project, especially the large scale projects with multi-million dollar budgets. Predictive Project Analysis or PPA is a statistical analysis based tool that uses years of data from past projects to forecast possible risks for a particular project (Ondruš et al. 2020). Thus it is a very helpful tool for the project managers to assess possible risks and take early actions so that the risks do not cause the project to move towards failure.
This same tool can be used in this project as well since it will help to identify possible risks in the project. Considering the final output of the project, it can be easily seen that the overall nature of the project is significantly complex and full of various risks that may or may be not very much visible initially. Hence, PPA tool can help to identify those risks that are not well visible and early mitigation actions will be undertaken accordingly.
3.2 Justification of the Project
Analysis of the project risks using PPA may lead to the development of a long list of risks that may occur during the entire project and beyond. Moreover, the complexity of the project means there might not be any straightforward way to resolve these risks and go ahead with the project (Schneble and Shaw 2021). Additionally, the final product of the project involves transportation of human beings and even minor errors in the product may lead to severe damage or loss of lives, which is not desirable. Overall, the risk landscape generated from PPA tool suggests the project is very risky to conduct and even there is no 100% assurance that the final outcome will be flawless.
However, considering the rapid evolution of technology in the entire world and increasing demand for efficiency, this project should go ahead. Development of fully autonomous cars will reduce the need for manual drivers and at the same time, it can help in reduction of accidents through human errors like over-speeding, drink and drive, breaking signals and others (Hussain and Zeadally 2018). Hence, these autonomous cars can be a major breakthrough in transportation technology and the project should proceed but with caution.
3.3 Optimal Leadership Style
The optimal leadership style for the project is Transformational Leadership. The leader should be able to motivate the team members to constantly push their boundaries beyond their capabilities and constantly improve the product in terms of the features and performance. The complexity of the project means the leader should also be a visionary with ideas that will be beneficial for the project. Elon Musk has already set a great example of transformational leadership in his field of business and the same model needs to be followed in the project.
3.4 Project Management Methodology
The most appropriate methodology for this type of project aligned with the leadership style is Waterfall Method. Unlike the previous project, the final outcome of the project is well defined and hence, multiple iterations are not necessary. On the other hand, the most important requirements of the project include proper planning and risk analysis without which the project cannot proceed. Additionally, transformational leadership can also be aligned with this methodology as the team members can be motivated to expand their boundaries while planning and executing the project.
3.5 Budget of the Project
The development of budget for the project is relatively easier than the previous one owing the well defined final output and availability of a project roadmap. However, there are high chances of significant extra costs due to possibilities of unforeseen expenses (Yaqoob et al. 2019). An approximate budget for the project is shown in the following table.
.png)
Table 3: Budget Estimation for the Discovery Project
3.6 Team Undertaking the Project
There are a large number of teams that will be responsible for undertaking the overall project. These teams are listed in the following table.
.png)
Table 4: Human Resource Requirements for the Discovery Project
3.7 Democratising the Project
The one problem with regards to the project is that the developing company i.e. Tesla cannot keep hold of the sole development rights to itself once the project product becomes reality. Since the product has global usage value and has potential to become a standardised usage product, it will not be possible for Tesla to fulfill global commercial demands at the same time (Rajabli et al. 2020). Hence, after a certain point, the project will have to be democratised for other companies to use and develop their own autonomous cars and vehicles. However, once the project is successful, Tesla can commercialise the overall project and sell usage rights to other companies at a particular rate.
4. Reflection
If I am given to manage either of these projects, based on my understanding and knowledge, I can say that I will face many issues and problems that can arise from the project. Both the projects are significantly complex and long drawn as well as requiring constant research and development. As a result, there are number of issues expected to arise as well. Issues may be related to technical, budget, time, team conflicts and others. However, the most important challenge that I will face is creating a suitable and realistic vision that the projects will follow. Both the projects have potential to transform different types of technology and without a long term vision, it is impossible to manage and run the project till the end. If I was the manager, I would have required applying my skills, knowledge and experience to generate a realistic and sustainable vision aligned with the overall scope of the project.
5. Conclusion
Overall in this report, two different projects have been analysed and studied. The first project selected is an operational project that has involved development of a new technical system for business analytics. On the other hand, the second project is a discovery project that involves development of completely autonomous cars. The first project is recommended to follow agile methodology due to lack of clear definition of final output and the need for continuous improvement whereas the second project is recommended to follow waterfall methodology due to the presence of a clearly defined output and the need for in-depth risk analysis. The first project also requires limited number of human resources working as one team under a leader whereas for the second project, there are multiple teams involved and assigned with different responsibilities. For the first project, democratic leadership style is most optimal as it will allow the team members to apply and discuss their own ideas and inputs that will be considered before making final decisions on the project. The second project will require transformational leadership style (a model similar to Elon Musk’s style) to motivate the team members to constantly push their boundaries beyond their capabilities and constantly improve the product in terms of the features and performance. Overall, it can be seen that the projects are completely different in terms of characteristics, methodology, leadership style and resource requirements and it proves that each type of project requires different types of approach and analysis.
References
.png)
PROG2008 Computational Thinking Assignment Sample
Task: Data modelling
Weight: 50% (40 hours)
Task Description:
In assignment 2, you have helped a real estate agent to gain some understanding of the market. The agent now wants you to help them set the indicative sale price for their new properties on the market. In this assignment, you will apply your knowledge in data analysis and modelling to build a regression model to predict the indicative sale price of a given property using the previous sale data.
In particular, you will
• Apply multivariate analysis and appropriate visualization techniques to analyze the given dataset for the relationship between the sold price and other features of a property.
• Based on the analysis select one feature that can be used to predict the property indicative price. Justify your selection.
• Build a regression model to predict the indicative price from the selected feature.
• Train and validate the model using the given dataset and analyze the prediction power of the model. Discuss the result.
• Distinction students: propose a solution to improve the model accuracy.
• High Distinction students: implement the proposed solution to improve the model.
You will use Jupyter Notebook in this assignment to perform the required analyses, visualise data, and show the analysis results
Solution
Analysis Report for assignment help
The property sales prediction was done using a python programming language with Anaconda Framework using Jupyter Notebook IDE where the sales prediction dataset was explored at first. The libraries of python used for analysis and visualization were pandas, NumPy, matplotlib, seaborn, and sklearn for importing machine learning algorithms.
About data
.png)
The details about the data are thouroughly discussed in the notebook where each column details has been described about the property and sales.
.png)
The data reading was done using pandas where the information about the data was described.
Data processing including the column details, column information of data types, handling missing values and checking null values if present, and summary statistics of the data where the mean, deviation, maximum, count, etc. of the data are described.
.png)
Data visualization
The data visualizations were done using matplotlib and seaborn library which are used for creating attractive and interactive graphs, plots, and charts in python. The different graphs from the data insights are described as communicating about the data containing visuals.
.png)
The bar chart here describing the bedroom description count where the data containing 45.5% of property with bedrooms and the sales is also depended upon these factors.
.png)
Figure 5 Property sales price with bedroom availability
.png)
Figure 6 Property sales price with bathroom availability
.png)
Figure 7 Property sales price with square fit living availability
.png)
Figure 8 Property sales price with floors availability
.png)
Figure 9 Property sales price with condition availability
The sale prediction according to the property description is clearly described by the visualizations which describe the descriptive analysis of the data which represents the sales of the property according to the different infrastructure based happened in the past.
.png)
Figure 10 Property sales price with space availability
.png)
Figure 11 Property sales price with condition availability
.png)
Figure 12 Property sales price with grades availability
Data modelling
The machine learning algorithm is applied to the dataset for the predictive analysis where the future prediction based on the descriptive analysis is done to look at whether the models are accurate according to the data and the accuracy of the model describes the predictive analysis rate to predict the property sales in the future.
.png)
Figure 13 Regression model
The algorithms are applied to the dataset by training the models by splitting the dataset into train and test split and then the trained and tested values are applied to the algorithms to calculate the score of the applied data.
.png)
Figure 14 Training of the model
.png)
Figure 15 Fitting regression model
.png)
Figure 16 Creating variables
.png)
Figure 17 Decision tree regression
The predictive analysis score of the linear regression model predicted 100% accuracy whereas the decision tree regression score comes to 99% accuracy which describes the property sales prediction as mostly accurate as assumed.
.png)
Figure 18 Linear regression sales prediction with prices
.png)
Figure 19 Linearity of the model
.png)
Figure 20 Data Correlation heatmap
MIS102 Data and Networking Assignment Sample
Assignment Brief
Individual/Group assignment
Length - 1500 words
Task Summary
Create a network disaster recovery plan (portfolio) (1500 words, 10%-or 10%+) along with a full network topology diagram. This portfolio should highlight the competencies you have gained in data and networking.
Context
The aim of this assessment is to demonstrate your proficiency in data and networking. In doing so, you will design a network disaster recovery plan for a company of your choice to demonstrate your proficiency with network design.
Task Instructions
1. Create a network disaster recovery plan (portfolio) along with a full network topology diagram for a company. (the choice of a company can be a local or international company)
2. It is recommended that to investigate the same company that was researched in Assignment 1 as this created a complete portrait of the company and becomes an e- portfolio of the work complete.
3. Network disaster recovery plan (portfolio)
Write a network disaster recovery plan using of 1500 words, (10%-or 10%+) The Portfolio must include the following:
An introductory section that highlights the importance of having a recovery plan.
• What steps should the company take if:
1. There is a sudden internet outage.
2. A malware (e.g. a virus) has infected the computers in the company network.
3. There is no local area network for the entire company Is there a way to diagnose if this is a hardware failure. What communication protocol stack might be affected.
4. Only a part of the company loses internet connection.
5. There is a power outage.
6. There is a natural disaster such as an earthquake, tsunami, floods or fire.
7. There is a password security breach.
• Are there precautions and post-planning to ensure that the company will not repeat the same network disaster?
• Anticipate the likely questions about the network design that will be raised by the client (Please note that this may include both technical and non-technical staff of the organization).
4. Network topology diagram
• Create a full network topology diagram, which could ensure the business continuity of the company.
• The diagrams need to be your own work and need to be developed using Visio or Lucid chart or an approved graphic package. (Please seek the approval of the learning facilitator prior to commencing this activity).
• All diagrams need to be labelled and referenced if they are not your own.
• The full network topology will be part of the network disaster recovery plan and should be used to further enhance the understanding of the recovery plan.
Solution
Network Disaster Recovery Plan (Portfolio)
Introduction
The network infrastructure is a very crucial requirement of every business in the market for IT assignment. Many things need to be done for a successful business-like Walmart and different aspects need to be analyzed because network infrastructure is used for communication purposes daily. This study is about the network disaster recovery plan that explains what needs to be done in case any disaster occurs. This study enables us to analyze and evaluate different factors of development for Walmart and prepare an effective plan for the management of numerous activities. Walmart is an American multinational company that deals with retail operations by creating a chain of supermarkets that provide the user with goods and products at a discounted rate and serve them as department stores and grocery stores all over the world.
Network disaster recovery plan
The network disaster recovery plan is used in the market for businesses as a backup plan that can be used for any kind of disaster by recovering the entire network of a company like Walmart. The crucial part of a network disaster recovery plan is identifying the weak links and the loopholes of the network ?generating the list of vulnerabilities to risks ?planning to mitigate these risks using suitable measures and specifying the backup (Froehlich, 2019).
• Aspects of this plan
? In case of any power supply, internet failure, or system failure taking place in Walmart, the company needs to analyze what kind of response is required from the staff. The employees can use different measures in addition to handling offline customers and registering their orders. This company right now has a stable market but in case of such a situation, employees and staff need to corporate. In case of any internet outrage or downtime for a small duration, this might affect Walmart but with a low impact.
At this stage, Walmart can use the direct communication method with the employees to provide them the prior information about the opening and closing of the stores and the change in working culture for a limited period (Finucane et al., 2020).
? In case of any malware or virus affecting the devices such as the computers of Walmart, a complete shutdown takes place and the operations must be blocked. For this, Walmart needs to perform a regular scan of the viruses on their computers using the anti-virus software. They should also ensure that the current system has no malware and that updates need to be performed regularly (Pandey et al., 2018).
? In case of the absence of a local area network for the entire Walmart then there is an interruption in the communication between different devices of the Walmart network. These interruptions may take place due to poor wiring that results in weak signal strength.
? If a single part of a company loses the connections to the other network, transmission and receiving of crucial information get blocked. For such a situation companies like Walmart need to prepare by using a backup plan to protect themselves from cyber-attacks.
? Power Failure is another disaster that can take place in Walmart which brings the entire system down. Customers who are shopping offline need to take some restroom. For digital payments, some extra time needs to be provided and the transaction can take place in cash.
? In case of any natural disaster such as an earthquake, flood or fire take place, it is the crucial responsibility of Walmart to ensure the safety of one and all customers by collecting them to a safe place with the help of local bodies and relief organizations. Some food and water must be provided along with the use of anti-measures such as fire extinguishers in case of emergency.
? In case of a password security breach, the issue needs to be reported to the higher authorities as soon as possible. This might lead to the stealing of crucial and sensitive information such as customers' email addresses and payment information of debit cards or credit cards to perform fraud and ransom. This can be eliminated in avoiding by using strong passwords and using software such as firewalls and intrusion detection systems to minimize the impact on the business (Dhirani, Armstrong & Newe, 2021).
• Precautions and preventive measures
The Walmart Company has a very clear vision to provide the department item and grocery items to the customers with an extensive menu of a wide range of goods and product. The key feature of Walmart are quality products, timely delivery, healthy and fresh products, and ease in ordering and delivering items to the doorstep its chain of supermarkets are easily available in every locality. The first parameter required by Walmart firm is the internet connection which has proper bandwidth and low delay time. This is because communication is a very crucial part of any business and it needs to be analyzed carefully in the case of Walmart to record and implement the customer feedback to improve the quality of the service delivered. With the help of an effective communication technique, the negative feedback environment of the customers can be converted to positive critics (Network Disaster Recovery Plan, 2022).
The second is to use the outpouring protectors and the incessant service of power supply along with the availability of power backup to the hardware because this can save the time consumption of Walmart and protect the data by eliminating the vulnerabilities of Cyber thread by safely shutdown the system as well as the server of the Walmart.
The third is the accountability of the staff for the surrounding area and training them with this quality to take care of their task. In case of any employee of Walmart notice anything wrong or suspicious in their surrounding area, they are required to report it to the higher authorities and try to fix it faster. Communication is a critical process that needs to be implemented with the team members to understand the needs of the customers can be enhanced for a better future (Ghasempour, 2019).
The issues in the Wi-Fi internet connectivity is might be a problematic subject but such issues as low speed, poor quality, and frequent disconnections might fail Walmart to serve its customers. This requires a good and stable connection to the internet with the integration of hardware and software devices.
In case of any cyber-attack or risk that is a direct challenge to the sensitive data of the company as well as the customers the precautions required are to identify the hacking activity such as Trojan or Malware, with the need for strong network security levels, and a network monitoring tool. In case of any disaster strikes, the team members of the Walmart and customers need to analyze any evacuation plan with the regular drills required to ensure overall safety (Lin, 2019).
• Questionnaires about the network design
1. What will be the cyber threats and risks that might be faced?
Cyber threats are increasing with technological advancements. The probable cyber Threads are fishing Malware and somewhere, as well injection denial of service, a man-in-the-middle attack, butter flow, and password attack using brute force or dictionary method full stop these are the malicious attacks which are deliberately performed to steal data, breach financially sources and identity (Jaramillo, 2018).
2. What is best for me and how will I decide?
For the best network design with effective communication and high load-bearing capacity, it is understanding to evaluate the building infrastructure that provides an idea about the current networking environment. It allows us to connect with potential customers about their requirements and manage the website hosting operation. Now the business is open to search sections and Walmart might find it interesting.
3. What are your thoughts about the wireless technology of internet connection?
This can be a tricky question because the wireless technology of the internet connection is a fast-working operation facility providing methods with less complexity as no cable or wire is required to connect different devices in the network. But the wide connection provides a reliable and stable connection that is more complex but less costly than wireless. Also, the wireless network allows us to work through the obstacles like the wall with good signal strength and quality internet connection.
Network Topology Diagram
.png)
Figure 1 Network topology diagram for Walmart firm
References
.png)
7113ICT Research for IT Professionals Assignment Sample
Assignment Requirements
The Research Plan must show a clear connection between the research question and the associated focus/objectives, and the method and techniques of data collection and analysis to be used to achieve those objectives. How well this is done contributes significantly to the coherence of the work and conveys to the reader that the author of the proposal has the competence to execute the research project successfully. The body of the report should be at least 3000 words. Please note that the references, direct quotes and appendices are not included in the word count.
Required Components
• Background to the problem
• Literature review showing the relationship to previous works
• Research question (including the broad research question and the sub-questions)
• Aims and significance of the research
• Research strategy, approach and methodology
• Data gathering and analysis techniques
• Rigor, validity, reliability and ethics
• Research schedule/timeline
• References
• Clarity of the statement of the research problem (including the clarification of the underlying assumptions)
• Clarity of the research question(s) derived from the problem statement
• Rationale for conducting the study (including significance, relevance to theory and practice, relationship to previous research, own contribution)
• Review of literature and theoretical frameworks (relationship to previous research)
B. Well-reasoned and balanced choice of research methods (35%)
• Research strategy and design (including data collection and analysis) well justified given the
underlying assumptions.
• Evaluation of the methodology discussed in the relevant field with respect to the problem domain (e.g. software engineering, information systems, artificial intelligence, computer science, multimedia)
C. General Level of Scholarly Analysis (25%)
• How well the issues covered in the course have been mastered.
• How well the overall plan is developed.
• Evidence of critical reading and evaluation of relevant literature.
• Comprehensive knowledge of issues illustrated by the selection of literature.
• Evidence of explanation and analysis (not description) where appropriate.
D. Communication and Referencing (20%)
• Logical development of argument.
• Clear structure and organisation.
• Fluent writing style.
• Correct spelling, punctuation and grammar.
• At least 3000 words.
Solution
Background To The Problem
In today's marketplace, business analysis is a relatively powerful tool that assists business organizations to reduce the amount of risk which might be the result of different activities and can be short-term or long-term. Moreover, the business analysis also helps in understanding the exact requirements of a business, possibilities of organizational IT systems, development and execution of a business project etc (Žemgulien? and Valukonis, 2018). Therefore, the people who are assigned for performing such critical and in-depth analysis of a business or the business analysts have a major role in enhancing the business performance.
Modern-day business organizations have advanced and powerful IT systems that help in the collection and analysis of business operations-oriented data. But at the same time, they tend to generate enormous volumes of data that sometimes become quite difficult for the business analysts to handle, understand and interpret. Business analysts and the professionals of an IT department within an organization have a very close relationship with one another in terms of their work (Täuscher and Laudien, 2018). Precisely it can be said that their works and operations are inter-related. Therefore, it is mandatory that both professionals must work collectively to achieve the organizational aims and objectives for best assignment help.
The real problem arises when business analysts are incapable of handling the amount of data produced by the IT systems or the IT departments. This can lead to significant problems and in fact, put forward various hindrances that ultimately lead to degraded performance (Palepu et al. 2020). Some of the main hindrances faced by the business analysis in doing their daily business research are because of reasons like over-ambitious and vague business requirements, difficulty in understanding and interpreting the business requirements, generation of an enormous volume of data that are difficult to manage and interpret, allotment of inadequate time for conducting the analysis, etc.
Literature Review
Skills that business consider important for business analysts
Business analysts work with the organisation to help them to bring improvement in their system and process. Analysis and research are conducted to bring solutions to problems that arise in the business to help introduce the system to their clients and business. Indian IT sector and enterprise business analyst has emerged as the main business practice. They refer to understanding the changes that business requires along with evaluating the impact of these changes, facilitating communication and documenting among the stakeholders who are involved and analysing and identifying requirements. They contribute actively to the sustainability and profitability of an organisation. The significant role of business analysts is to guide the organisation to bring improvement in their quality and process of services and products (Pillay, 2018). Business analysts are responsible for making new models that will help in supporting the decision in the business by working closely with information technology teams and financial reporting to implement strategies and initiatives to optimise cost and improve costs. According to Robert, half technology the skills that business analysts should include defining business requirements as well as putting them to shareholders. They should have proper knowledge about reporting, variance analysis, pricing, monitoring and planning, forecasting and budgeting. According to (Shah, 2017) the role of a business analyst is to act as a link or bridge to translate, analyse and interpret between what is typically referred to as the business group in the company and the technology team (Verma et al. 2019). It is also set by them that business analysts perform driving changes and facilitates them to understand the goals and problems of the organisation and should analyse requirements and solutions.
Best place for learning specific skills for business analysts
For learning this specific skill for business analysts, a graduate or bachelor degree is an individual should have adequate knowledge about programming language and should have good negotiation and communication skills. They should create an interactive report with the help of several business intelligence tools. Individuals can have a certification that is offered by international institutes of business analysis which include certified business analysis professionals will be greatly beneficial. A bachelor’s degree is typically needed for most business analyst positions. A Master's degree in BA(business analyst) can also be useful for a more advanced position. But having a bachelor degree is the first and foremost step to become a business analyst as per the United States Bureau of labour. Individuals should have the proper background in psychology or marketing, finance, economics, a business may prove useful. For pursuing a BA position at the management level or any higher-level individual should complete an advanced degree such as masters in business administration program or masters in business analytics. A person can achieve qualification from some other industries such as the project management institute, international institute of business analyst and institute of a management consultant. These courses are offered if the individual has completed their master degree or has a working experience of BA for several years. A person can acquire or learn these skills from work experience with organisations which will help their business analyst skill. They conducted analysis and research to bring solutions to business problems.
Relationship between business analysts and IT professionals of an organization
Business analysts are professionals who analyse an organisation or business by documenting its processes and system, identifying risk, providing solutions and accessing its business model. The role of business analysts can be understood which helps to bring changes in the organisation by identifying the requirements and recommending a proper solution to those requirements for providing value to the shareholders (Ariyarathna and Peter, 2019). In a simple form, it can be said that day is the discipline that helps the company to solve the existing problem by identifying, analysing and solving them. In several organisations, the only solution to deal with issues is by altering the existing process or method or technique that is not workable. This is what BA does- identifying and solving business problems. In the IT or information technology Sector, the BA belongs to the product development team and they are responsible for identifying and analysing the abdomen of the business and documenting its processes and system. They also outline the requirements of the business and match the software that is implemented with the business model (Muntean et al. 2019). The main function of IT business analysts is to analyse and solve the issues using information technology solutions. Their role is the link to a bridge between IT and business. In this role, the business analysts may also communicate with the quality assurance and development team.
Measure that can be taken to mitigate the reason that hinders business analysts from doing accurate daily business research
? Business analysts can face several challenges such as conflict with the stakeholders when a team develops a new approach that is relevant to the present business process (Omar et al. 2019). This conflict can be solved if the team is required to understand the reason for resistance to the new solution. Business analysts should study the requirements and process to prepare a solution. They can prepare a business case document for users which demonstrates the answering users' questions and new solutions.
? The undocumented process can also be a challenge for business analyst from doing accurate daily business research. Business analysts should be familiar with the consequences of lack of documentation on the project or who documented the process and procedure (Pröllochs and Feuerriegel, 2020). For solving this business analyst should identify the decision-maker and key system users. After that, documentation with proper description is made which will demonstrate the difference and processes for users with different responsibilities. Business analysts should concentrate on the requirements of business instead of the position of the users.
? Problems can arise if stakeholders change their requirements and this problem can happen daily. The business analyst should properly understand what is the main reason for this problem (Vidgen et al. 2017). If the reason is some external company alteration in the current process of business it can be solved by accepting the new requirements while postponing the deliverables of the planned project.
Research questions
? Broad Question
What are the primary reasons that hinder business analysts from doing accurate daily business research?
? Sub-questions
1.What are the specific skill sets that business organizations consider important for business analysts?
2.What is the relationship between business analysts and IT professionals of an organization?
3.Does a disconnection exist between what business analysts consider significant and what they know?
4.What are the best places for learning or acquiring the specific skills that business organizations consider important for business analysts?
5.What can be done to reduce or eliminate the reasons that hinder business analysts from doing accurate daily business research?
Research Aims
? To depict the primary reasons that hinder business analysts from doing accurate daily business research.
? To determine the specific skill sets that business organizations consider important for business analysts.
? To understand the relationship between business analysts and IT professionals of an organization.
? To identify the disconnection existing between what business analysts consider significant and what they know.
? To recognize the best places for learning or acquiring the specific skills that business organizations consider important for business analysts.
? To determine the ways or things that can be done for reducing or eliminating the reasons that hinder business analysts from doing accurate daily business research
Significance of the Research
The business analysis finds its importance in identifying and articulating the requirements for changing the working procedures of business organizations. The role of business analysts is imperative for the growth and development of an organization. They help in identifying and defining the solutions for maximizing the value that is delivered by a business organization to its stakeholders (Aithal, 2017). There are several functions of a business analyst such as evaluating the business requirements, developing appropriate documentation, recognizing key areas for improvement, establishing organizational policies and strategic planning. Therefore, it can be easily understood that business analysis along with people who do that i.e business analysts play a crucial role in the overall development of an organization.
Any company could leverage business analysis for achieving its strategic objectives by recognizing and adopting the particular changes suggested by the business analysts. Not only does it help in the enhancement of the overall organizational performance but also helps the organisation to achieve a significant competitive advantage. However, this process is quite complex and difficult to execute in an appropriate manner. This process demands specific skill sets of the business analysts that are important for analysing the business scenarios (Yayici, 2021). Moreover, in modern times almost all business organizations have their personalised and efficient IT department that helps to collect and manage vital business data. This accumulated data is forwarded to the business analysis on the basis of which they commence the remaining procedure. But with the technical advancements at bay, it is obvious that the IT systems produce enormous volumes of data which are sometimes different to manage, handle and processed by the business analysts (Rivera et al. 2018).
The process of business analysis is considered to be a rigorous one and therefore there are certain challenges associated with it. Some of the main challenges faced by business analysts are over-ambitious and vague business requirements, difficulty in understanding and interpreting the business requirements, generation of enormous volumes of data that are difficult to manage and interpret, allotment of inadequate time for conducting the analysis, etc (Gray, 2019). Therefore, this specific research finds its significance in determining the possible reasons that obstruct business analysts from doing accurate daily business research. Moreover, it will also help in depicting the specific skill sets that a business organization demands from their analysts. Furthermore, this research will also help in finding various solutions that will help business analysts in commencing their day-to-day business research in the best possible manner and without any hindrances.
Research strategy, approach and methodology
Research Strategy
The research strategy used for this research is the quantitative survey method which is widely used in various business researches and also enables access to a significantly higher number of survey participants (Understanding different research perspectives, 2021). The research strategy requires the development of a meaningful questionnaire for getting the answers to the various research questions and the questionnaires appeal to the respondents without being too difficult to understand and the quantitative survey method had been beneficial in accurately investigating the relationships between the business analysts and the IT professionals along with the pinpointing various concerns associated to the accurate business research daily.
Research Approach
The research approach selected for this research is the inductive approach which has the objective of generating meaning from the collected data set for identifying the patterns and relationships which are required for answering the research questions as well as highlighting the various dimensions of the central issue (A General Inductive Approach for Analyzing Qualitative Evaluation Data - David R. Thomas, 2006, 2021). The approach is flexible since it has also provided the researcher with the ability to use the existing theories and previous works in the process of formulating research questions that are to be explored in the research.
Research Design
The descriptive research design is being utilised in this research since it aims at describing the present status office-specific identified variable and the research project is designed for providing structured and systematic information regarding the various problems that are being faced by the business analyst in accurately e undertaking the business research from time to time. The descriptive research design is used since it involves the development of a research hypothesis through the collected data instead of beginning with a hypothesis and the analysis of the collected data through surveys is utilised for developing the hypothesis and getting exploring the various research questions systematically.
Data gathering and analysis techniques
Data Collection
? Survey- The data collection method used in the report is a quantitative survey method which was used for determining the skills that were considered to be the most significant as well as the most essential in the engineering sector (DATA COLLECTION METHODS, 2021). The participants in the survey consisted mostly of various engineering graduates who rated the value as well as the performance of every object which was required for their appropriate professional practice. A pilot survey, which is moreover a mini-survey in which the researcher provides a questionnaire for a comparatively smaller size of sample than the total audience being targeted, was also conducted before the data collection for ensuring the reliability of the instruments of the survey (Blog, 2021). The participants of the pilot survey were six researchers, business analysts, as well as teachers and the input received from them was utilised for enhancing the sample along with identifying some attribute terms or fuzzy abilities.
Data Analysis
The data analysis approach used in the research is the mixed data analysis approach which consists of,
? Primary: The method of data analysis being used as the primary data analysis which is the analysis of the data that is collected for a specific research study and the analysis of the primary data is making sense out of the data that has been collected for answering the various research questions or critically evaluating the research hypothesis (Primary Data Analysis - SAGE Research Methods, 2021). The data collected through the quantitative survey method as well as the pilot survey analysed for understanding the various reasons involved in hindering accurate business research daily for the various business analysts.
? Interpretive case analysis approach: This approach is used by researchers for integrating the data utilizing developing various conceptual categories and supporting or challenging the various assumptions given in the case studies regarding the problems of inaccurate business research. The interpretive case analysis approach will also be beneficial in guiding the research which outlines the various problems and challenges on the way along with helping the researcher in understanding the issue through a broad range of perspective which will help in giving a better outlook towards the research questions.
Rigour, validity, reliability and ethics
The consideration of the various ethical issues is a significant part of this research while forming the evaluation plan and the various ethical considerations for this research are,
? Informed consent: This addresses the fact that the participants of the quantitative survey and pilot survey are made aware of the purpose of the research and how their response will be utilised (Ethical considerations, 2021). Appropriate informed consent has been taken from every candidate of the quantitative survey as well as the pilot survey regarding the use of the response throughout the research for exploring the research questions.
? Confidentiality: Another major ethical consideration is the confidentiality of the information that has been collected from the candidate and the data collected from the quantitative survey as well as the pilot survey for this research are being accessed by only the program coordinator which will be ensuring the identifying and collected information from being excluded from any published documents or report.
? Anonymity: The ethical consideration of anonymity has been considered since the identity of the various participants of the quantitative survey and the pilot survey are unknown to the whole research team. This has been considered necessary for the research since various candidates have insisted on this aspect while using their response during the data analysis for exploring the research questions.
? Voluntary participation: All the candidates of the quantitative survey had voluntarily participated without any external influence or force and the participants are free in withdrawing their participation whenever they want and that will not impact their involvement in future programs.
Reference List
.png)
.png)
DATA4300 Data Security and Ethics Assignment Sample
Word count: 1500-2000
Weighting: 40 %
• you have been employed as a data ethics officer by an industry board (professional body) wanting to create a code of conduct around using artificial intelligence (ai) to (a) diagnose disease in a person earlier in the progression of this disease or (b) predict the spread of community diseases, in order to inform best practice in the healthcare industry.
• you are being asked to produce a framework for a code of conduct for a medical board.
• you can choose either of the two applications above (earlier disease diagnosis or community disease prediction using ai).
• this company code of conduct framework will also address individual responsibility as well as recommended government oversight.
• your framework will be presented in a report (a suggested structure is below).
Introduction
• introduction to the use of ai in medicine as a whole and fears related to its use, e.g. “seventy-one percent of americans surveyed by gallup in early 2018 believe ai will eliminate more healthcare jobs than it creates.”
source: https://healthitanalytics.com/news/arguing-the-pros-and-cons-of-artificial- intelligence-in-healthcare
• describe how ai is being used either to (a)diagnose disease in a person earlier in the progression of this disease or (b) predict the spread of community diseases
Data ethics issues
• outline possible data security, privacy and ethical issues associated with the use of patient data in ai. for example, why it may not be a good thing as stated in the quote below.
“it’s true that adding artificial intelligence to the mix will change the way patients interact with providers, providers interact with technology, and everyone interacts with data. and that isn’t always a good thing.”
source: https://healthitanalytics.com/news/arguing-the-pros-and-cons-of-artificial- intelligence-in-healthcare applicable principles
• outline theoretical and legal principles which are relevant to the data issues identified. afterall, if the algorithm gets it wrong who is to blame?
Solution
Introduction
Use of AI in medicine
Artificial Intelligence (AI) in electronic health records may be utilized for scientific research, increased efficiency, and medical management efficiency. Despite going through the traditional road of scientific publishing, recommendation formulation, and medical support tools, AI which has been properly constructed and taught with adequate data may assist in uncovering evidence-based medical practices from electronic health information. AI may also help design new patient care patterns of healthcare provision by studying clinical practice patterns obtained from electronic health data.
A critical feature of AI-based healthcare or medical research for assignment help is the utilization of data generated for electronic health records (EHR). If the underpinning system for information technology and network do not stop the dissemination of diverse or low-quality data, this data could be difficult to utilize.
.png)
Figure 1: AI in Medical
(Source: Walls 2022)
AI is being used in Predicting the spread of community diseases
In recent days, COVID-19 has been at its peak and even a kid is aware of its impacts and the disaster it caused to the world. For overcoming its impacts, AI is being used in several ways to the prediction of the spread of this communicable disease. As the major symptoms of any communicable disease are chest pain, cold, cough, etc. AI is being combined with other technologies for tracking and flagging possible carriers of the virus (Basu et al 2020).
AI-powered glasses for checking hundreds of individuals in minutes without establishing contact. This form of the monitoring system was employed at bus and railway terminals, in addition to other public areas with a high population density. accomplishing this by merging artificial intelligence with new temperature measuring technologies using computer vision. This method allowed for the contactless measurement of body temperature, a primary indicator of COVID-19, despite interfering with people's usual behavior. Anyone whose body temperatures surpassed the limit might be promptly identified using this technique. Since physical temp measuring is time-consuming and increases the danger of cross-infection due to the required interaction with others, it proved to be a successful solution (Basu et al 2020).
.png)
Figure 2: AI models
(Source: Piccialli et al. 2021)
• Through the use of a Support vector machine algorithm, AI separates out the data and identifies the disease spread (Agrebi and Larbi 2020).
• A combination of High-resolution accuracy and a Support vector machine leads to the identification and isolation of the disease with 100% accuracy.
• It identifies the patterns of data (signs) collected from the patients and through an algorithm AI cross-checks these signs with the right disease and leads to early prediction.
• Machine learning algorithms aid in detecting the red blood cell that got infected through malaria with the use of Digital in-line holographic microscopy data (Agrebi and Larbi 2020).
.png)
Figure 3: AI in predicting covid-19
(Source: Piccialli et al. 2021)
Data Ethics Issues
It is observed that for several years, researchers and other people have expressed worries about the ethical concerns of medical data storage and information security procedures, and Artificial Intelligence is increasingly dominating the discussion. Existing regulations are insufficient to safeguard an individual's personal health data.
Indeed, according to startling research, improvements in artificial intelligence have made the Health Insurance Portability and Accountability Act of 1996 (HIPAA) obsolete, and this was before the COVID-19 pandemic. The fact is that healthcare data is very significant to AI businesses, and numerous of them appear to not mind violating a few privacy and ethical standards, and COVID-19 has just worsened the situation. This is a huge concern for the protection of security seeing the hike in cybercrimes (Lexalytics 2021).
.png)
Figure 4: ethical and legal issues of AI in healthcare
(Source: Naik et al. 2022)
Below are mentioned the most probable data privacy, security, and ethical issues concerned with patient data in AI.
1. Continuously changing environment with regular disruptions - AI in healthcare must adapt to a constantly evolving environment with regular disturbances while adhering to ethical principles to safeguard patients' well-being. Nevertheless, a simple, crucial component of determining the security of any medical software is the ability to test the program and understand how the program might fail. The pharmacological and physiological processes of drugs or mechanical components, for example, are similar to the approach for software programs. ML-HCAs, on the other hand, maybe a "black box" problem, with workings that aren't apparent to assessors, physicians, or patients (Wanbil et al. 2018).
2. Uninformed consent in order to use patient’s data - Identity, reputation, and financial loss to the patient. When it comes to data of patients and people are more concerned about it and get in stress due to this, In the online services offered by the medical industry or health care industry tend to collect it's to collect a great piece of information about the patients to feed into the system which leads to data security issues. The information of the patients can be used to manipulate them In the future, creating fake identities, conducting cyber - crimes leading to financial and reputation loss, etc. All these concerns are the major ones that every patient is concerned about (Gupta et al. 2020).
3. Algorithmic biases and impropriety - No accountability for any harm done to patients as AI is a computerized system with no strict laws. Algorithms that may function by unwritten rules and develop new patterns of behavior which come under the AI are apparently threatening the ability to trace responsibility back to the developer or operator. The claimed "ever-widening" difference is the reason for concern since it affects "both the ethical structure of the community and the basis of the accountability concept in law." The adoption of AI may leave the healthcare industry and the patients with no one to hold responsible for any harm done. The scope of the threat is unclear, and the employment of technology will significantly restrict the human capacity to assign blame and accept responsibility for decision-making (Naik et al. 2022).
.png)
Figure 5: Cons of AI Adoption in Healthcare
(Source: Ilchenko 2020)
4. Lack of transparency and traceability in the system - The lack of computational and algorithm as well as operations of the computational system in AI collecting the patient’s information transparency has influenced many legal arguments about artificial intelligence. Because of the rising use of AI in elevated circumstances, there is a greater need for responsible, egalitarian, accessible, and transparent AI design and administration. The two most fundamental characteristics of visibility are data accessibility and comprehension. Information regarding algorithm functioning is usually purposefully made difficult to get (McKeon 2021).
5. Sourcing of data and Personal Privacy violation - With the World Data Corporation forecasting that the worldwide data sphere might very well develop from 33 zettabytes (33 trillion gigabytes) in 2018 to 175 zettabytes (175 trillion gigabytes) by the year 2025, businesses will have access to enormous amounts of both structured as well as unstructured data to mine, modify, and organize. As this data sphere expands at an accelerating rate, the dangers of revealing data owners or consumers including the patients and the staff of any organization and the hospital industry rise, and protection of personal privacy becomes more difficult to secure (McKeown 2022).
.png)
Figure 6: Annual data breach
(Source: McKeown 2022)
Whenever data leaks or breaches occur, the following repercussions may drastically harm an individual as well as indicate possible legal infractions, since many legislative bodies are increasingly enacting legislation that limits how personal information can be treated. The General Data Protection Regulation (GDPR) implemented by the European Union in April 2016 is a well-known regulation instance of this, which impacted the Consumer Privacy Act approved in June 2018 (McKeown 2022).
Applicable Principles
Legal principles against the AI issues in healthcare
• HIPAA requires regulated organizations to secure health information and patient records (information or data) when it relates to Protected Health Information (PHI). Dealing with any third-party provider has concerns that must be thoroughly examined. Whenever committing confidential material to an Artificial Intelligence vendor, healthcare institutions must create Business Associate Agreements (BAAs) to subject suppliers accountable for the same stringent data security requirements. As Artificial Intelligence technologies develop and healthcare businesses adopt AI into everyday activities, regulation loopholes remain to keep this technology in the shadows.
• Another principle that the healthcare industry must follow while implementing AI is that they need to offer full transparency to the system and the data information accountability of the patients in order to maintain their trust. In such cases, the placement and ownership of the computers and servers which keep and access patients' medical data for healthcare AI usage are critical. Without notable exceptions, laws must mandate that patient information be kept in the jurisdiction from where it was collected.
• Developing and applying artificial intelligence (AI) in order to strengthen national security & defense as well as strengthen the trusted collaborations by softening science and technology guidelines with the application of human judgment, particularly whenever an activity has the possibility to deprive people of civil liberties or intrude with one‘s fundamental freedoms of civil rights.
• Creating and implementing the best practices to increase the dependability, privacy, and precision of Artificial intelligence design, implementation, and usage. this will use best practices in cybersecurity to promote sustainable development and reduce the possibility of adversary impact.
• Legal principles shall offer adequate openness to the community and corporate clients about our AI methodologies, implementations, and uses, within the constraints of privacy, innovation, and reliability as defined by law and regulation, and in accordance with the IC's Principles of Information Visibility. it will create and implement systems to define roles and hold people accountable for the usage of AI and its results.
REFERENCES
.png)
CTEC104 Communication and Technology Assignment Sample
Assessment Task:
Formal reports are practical learning tasks where students apply the theories they have been studying to real world situations.
Given a scenario the students are required to collect information (primary and/or secondary) and prepare a report applying their research to make recommendations that address the business scenario.
This report should consist of the following parts: Executive Summary, Introduction, Objectives, Methodologies, Information Analysis, Findings, Recommendations, References, and Appendices (optional).
ASSESSMENT DESCRIPTION:
From paper to internet Luca, your team leader, has asked one of your colleagues, Imran, to develop and post on the internet information about how to lead a ‘greener’ life. Imran realised he needs to write scannable text and blend various models of presentation (text, graphic, design, pictures, sound, video and animation) but is uncertain about the mode(s) of presentation to use and asks your advice. Imran has requested you to think about the scenario and prepare a long report answering the following questions:
Questions:
1. Why web writers do more than just write.
2. Include a list of suggestions and discussion of activities to be undertaken in the initial planning.
3. Benefits of using the mosaic form of design for web pages rather than the traditional linear form.
Solution
Introduction
The study will focus on the real life situation and explore theory in order to relate with the issue of responsibility of web writers and also include suggestion and discussion for the initial planning. It will also explore the web pages traditional linear form and also identify the engagement with his audience. The focus of the study for assignment help is to explore the method of improving and discovering the website using the search optimization engine. It will also manage the web content importance.
Aims and Objectives
The study is to describe the importance of writers for their activity more than just right design.
? To identify the different activities of the writers.
? To explore the designs and methods used by the web writers.
? To identify the way the audience is addressed.
1. Methodologies
The study will focus on identifying the secondary qualitative study. It will provide appropriate evidence. The use of secondary data will be highly effective and efficient in the context of current study as it will provide resources and potential outcome within the context of the writing environment. The use of the philosophy of positivism will ensure a proper management of resources and perception of the reader.
2. Information Analysis
4.1 Activities of web writers
A writer of the web has to compose a written document in the blogs or the pages that are available on the web. They have no chance to use a notebook or pen to write their content, just like a formal writer. They have to use the artificial techniques of the internet to capture the attention of their viewers and encourage them to visit the new vlogs or the new pages on the web made by them. For the attraction, they always try to use some graphical representation like the graphics of the flash, which don’t need any formal writer. So they always needed wisdom in the field of the techniques of the internet. In some cases, the web pages have been used the SEO (search engine optimization), which helps them to organize their content in the system to get higher rank and also help them to make more efficient in the engine of the search that is web-based (Himmelstein et al 2019). So those things have not needed for a just writer.
The web writer those who have this job need to be good writers with a strong understanding of language and grammar, but also have an understanding of how the words they will compose will be exploited and presented in the online space. Depending on the job of the writer of the web, they need a great knowledge of the coding of the web, and they are also aware of the knowledge of building a language. There are several different ways to get this type of job, but people who have experience working in a company with blogging or a strong web presence may be the most attractive candidates for the recruiter. The work is often preferred by many people because it is often really flexible, and a huge amount of the work can be done from their home or on the basis of the freelance. Web writers always try to provide the content of articles and pages on the website to give the visitors something which is meaningful and interesting both. So this means that there is a huge difference between a normal writer and a writer of the web pages or a blog writer. A writer on the web needs a lot more knowledge than a normal writer.
4.2 Planning requirements
4.3 Create Objectives
The first move that is taken in planning is deciding the goal to be achieved during the planning term. The strategic plan made on a long-term basis may prioritise particular market share gains in the coming years (Hussain et al 2022, p. 69). In contrast, the division operating plan may prioritise the application of a new technique of monitoring orders and sales in the next quarter.
Mark is concerned with yearly goals for the department of sales, so he starts by defining goals which are concerned with the sales in the next year, as well as a job he would like to apply for that helps in automating the sales order process.
4.4 Task creation to achieve these goals
The further move is to create a checklist of tasks that must be executed to meet the defined objectives. For example, Mark determines the sales taking place on monthly basis required to meet the goal of sales he is aiming for, as well as chief tasks linked to the automation process, like tool selection, as well as training for the team on its use.
4.5 Required resources for completing the task
For fulfilling an objective some resources are required which should be identified at first. In this case, the term "resources" refers to both the human resource required to fulfil the plan and the supplies required to give support to those human resource (Hussain et al 2022, p. 69). This could include a sales administrator, salespeople, various supplies such as funds, and brochures for an advertisement propaganda which is intended to increase the number of prospects in the funnel of the team of sales.
4.6 Timeline
Now the identified resources must be allocated according to the need. For example, Mark decides that the campaigning of the marketing will start during the first quarter of this financial year, this will increase the marketing of the company in the second quarter of the following financial year. Based on Mark can easily calculate that how much resources is required to complete the task. If there is any shortage of salesperson it can be filled in the second half of the financial year.
4.7 Plan Implementation
This is the point at which other managerial functions enter the picture. Managers communicate the plan to employees clearly in this step to help turn plans into action. This step entails allocating resources, organising labour, and purchasing machinery.
4.8 Follow-Up Action
Follow-up refers to the process of constantly monitoring the plan and soliciting feedback at regular intervals. Monitoring plans are critical to ensuring that they are carried out according to schedule. It is to ensure that objectives are met. The regular checks and comparisons of results with set standards are performed.
3. Benefits of mosaic form
Creating a good design is very much important. When the audience visits the website, it gives them the first impression of one’s business. They will judge the business in a few seconds and in these seconds only a good design can make a positive impression in the minds of audiences. A good design aids one’s search engine optimization strategy.
When a website is designed with a traditional linear form it is organized with a middle, beginning, and end, more like a printed book would look. These days linear design is not used to design most websites, but it is very helpful in the presentation of long-form content, such as online texts and manuals. These days the mosaic form of web page designing has become a favourite free architecture portfolio website template to most designers. The mosaic form of web design is minimal, sophisticated, and minimal, the overall implementation is excellent, and its flexibility goes beyond the roof. It doesn’t matter what device a person is using. They can experience magnificent designs and creations; mosaic adapts to it fluently and instantly. It is like one will be having a lot of fun while creating their architecture website and so anyone could enjoy it while browsing. A website when designed in linear form, the website will usually present a table of content, like a book and it will have “next and “previous” buttons which allow paging through the whole site. It becomes monotonous (Sane 2020, p.58). For this reason, creating a good and strong impression with a striking and unique split-screen slider with a call-to-action button. Additionally, the Mosaic features scroll content load, animated statistics, sticky navigation, categorized portfolio section, and parallax effect. It also provides recommendations and logo sliders for clients, a contact section with full form, a full-page blog and Google maps as well as a newsletter subscription box. Anyone can create and design a web page using the Mosaic form of web design. It doesn’t require one should know the programming language. It can be created easily just by learning HTML. It is important to create a responsive web design to have a better visual experience, the experience of the user, and create a good impression from the user. Websites that were designed using the traditional linear form are monotonous like books, having an index, title bar, content, and “previous and next” buttons. The design created with the Mosaic form has a charming appearance that encourages the user to engage more with the website and also enhances their experience during surfing.
4. Conclusion
It can be said that the writers of the website have more responsibility to perform when it comes to the different environments. Initial planning requires a complex web of experience and managing to overcome the issue of design and traditional linear form. It has been noted that the planning of the writing and design provide a significant direction and control over the management of the organization.
5. Recommendations for improvement of the website
It is necessary for the web writer to play a crucial role in the management of the services in a significant and effective way. It is necessary for the writer to make the website more optimized and accessible to the user.
References
.png)
COIT20248 Information System Analysis and Design Assignment Sample
REQUIREMENTS
Required tasks in this assignment assuming that the waterfall model has been chosen for implementing the new system. also, assuming that some parts of programs have been written/implemented and are ready, whereas some other parts/programs are not yet ready. complete the following tasks and document your work in your submission:
1. Testing:
a. list and discuss the various types of testing.
b. identify (and explain why) which types of testing are applicable to the new nqac.
c. for each applicable type of testing identified in (b) above, discuss in detail the following:
• when (i.e., in what phase(s) of the software development life cycle) should this type of testing be conducted?
• the procedures for applying this type of testing.
• the follow-up procedures in testing after checking the testing results.
• who are the main stakeholders involved in this type of testing?
2. as stated in the nqac business case, the current system is a primitive and manual. on the other hand, the new system should be more sophisticated and should be run on a web platform. it implies that the new system will need the historical data to be transformed in to new data files and a new database must be created to support the operation of the new system. in view of this requirement, what task/activity must be done to create these data files (or the database)?
how should this task/activity be conducted? please note you are not asked to create a data file or data base you only need to describe where how and by whom the new data will be prepared.
3. because the new system is running on a platform which is different from the existing system, the design of the new system will be largely different from the existing system. in view of this, describe in detail what techniques the project team can implement to help end users familiar coit20248 assessment 3 term 1, 2022 with the operation of the new system. for each of these techniques, discuss its advantages and disadvantages.
4. in view of the business operations of nqac, which system deployment option should be used? why? how to apply this option in nqac? (note: in this task, select the most appropriate option. in other words, you are not allowed to select two or more options.)
layout of your report your report should be organized using the following headings and guidelines: a “separate” cover title page
• should include the word count of your report in this cover page. if the word count of your report falls outside the range “1,500 words” (word count includes all contents except the cover title page and references), marks may be deducted from your submission.
an introduction
• briefly discuss the overall content of this report.
task 1
• discuss in detail all the questions and sub-questions of this task.
task 2
• discuss in detail all the questions and sub-questions of this task.
task 3
• discuss in detail all the questions and sub-questions of this task.
task 4
• discuss in detail all the questions and sub-questions of this task.
Note: in tasks 1 to 4 above, you may include figures to illustrate/support your answers, if you think that this is appropriate.
Solution
Introduction
Noac is an organization performing changes in the management system. the organization is shifting to digital mode of marketing. in this case, the staff members and the technicians impart significance in the research report. the technician involves various tasks in terms of customer handling and system functionalities. the website must include details of the ac, their types, installation methods, and testing types. moreover, it must include few more details about the facilities and benefits.
This report consists of several information regarding the testing background of ac such as cooling, heating, and humidity control. moreover, the various types testing methods, identification of the appropriate testing method, their application and performance. on the other hand, it also includes the activities performed to create a new data base and familiarity of the system with the traditional system. The overall reports for assignment help provides an idea of testing methods of the ac and how to conduct it.
Task 1
various types of testing in terms of nqac, they provides a various types of testing methods, it includes,
• air enthalpy calorimetric
• temperature testing
• variable capacity testing discussion air enthalpy calorimetric air enthalpy calorimetric is required for testing the temperature such as cooling and heating. it includes the two methods such as the calorimeter room method and indoor air enthalpy or psychometrics methods.The measurement in terms of energy input to a room is done by calorie metric room method.
Moreover, it controls the temperature by an ac unit (job, & lidar, 2018). on the other hand, it maintains the air temperature inside the room at a constant value. whereas, the constant value is equivalent to the cooling capacity of the ac.
Indoor air enthalpy method it measures the air enthalpy such as air moving in and out of the ac indoor unit. in the case in changing the air enthalpy, it is multiplied by the rate of air flowing is equal to the cooling capacity of the indoor ac unit. test temperature in this case of ac installation, testing the temperature is essential for the identification of outdoor air temperature. moreover, it also includes testing the loading system, and average weight of the outdoor air temperature (mohanraj et al, 2012). these are used to measure the performance of the load system and also in calculating the efficiency metrics. it is divided into two segments, such as full load test conditions.
It is the method that includes the testing of air cooling condensers that works by evaporating the condensate. part load test conditions in this case, the capacity of humidification falls off. it is also termed as seasonal efficiencies that are required to measure the efficiency. the measurements are particularly done in part-load and full- load capacity. it controls the cooling and heating load by using the relative cooling and heating load hours.
Variable capacity testing in the case of variable capacity testing, it includes the demands of heating and cooling loads of an ac. it maintains proper cooling inside the room. moreover, it has the ability to dehumidifying. it also includes the compressor speed. the main purpose of ac compressor is to control the refrigerant under the pressure in the system. In this case, change in pressure takes place. the low pressure has converts to high pressure gas (prabakaran et al., 2022). on the other hand, the compressor speed determines the rate of refrigerant flow. the motor capacity and frequency varies in this case. the motor speed decreases with increase in capacity output. identification on the type of testing the type of testing which is applicable for the new nqac is temperature testing. in this case, temperature testing is essential for better maintenance of ac performance and servicing. it includes the loading system and weight of the outdoor air temperature. it overviews the overall performance and efficiency of the system. in terms, nqac includes the methods in their installation techniques to improve their service towards their potential customers and new customers as well. as the organization has shifted to digital mode it is necessary to provide temperature testing (dias et al., 2016). it is one of the unique features that nqac must include their management system. it deals with the loading system such as cooling and heating procedures. moreover, it is one of the servicing methods that include checking the performance and efficiency of the system. moreover, it supports the organization in getting a separate customer base. by providing the necessary facilities and meeting the customers’ demand will lead the organizational development digitally.
Task 2
Activities performed to create the database the responsible technician, users, and analysts are required to prepare the new database. The databases are mainly collected from the organizational growth report, feedback report, and other organizational data resources (zhang et al., 2014). in the end, the database is stored in the cloud system database. it is a significant way to store, secure, and protect the data. the website must be encrypted with the cloud computing systems.
Task 3
The similarity in the new system there are still some features and functionalities in the existing system, that are similar to the new proposed system. however, these are essential to evaluate and document to determine all the appropriate system features that are effective and sustainable in nature (blum et al., 2019).
however, this is the responsibility of the project manager, to document and supervise all the system similarities, which must be unchanged in further development procedures as well. the previous system was manual with different business process complexities such as poor cost and time effective
time management.the particular similarities are,
• core supply chain system and management process
• billing and packaging
• team culture and team distribution
• research and development system
Advantages
All of these similarities come with particular business advantages. these advantages can be implemented through effective management and critical analysis of the current business scenario
with the proposed system technology. the advantages are,
• better business management and documentation
• better finance management and resource supply maintenance
• shorter processing time
• advanced database management and analysis
• better market analysis and report evaluation
• effective business process improvement with digital technology implementation
Disadvantages
organizational disadvantages are also associated with these business system similarities. these must be considered and evaluated accordingly, to avoid the negative consequences. this is the responsibility of the project manager, to document and evaluate these disadvantages accordingly. this will not only lead to effective precaution but also will improve the business system and management.
Task 4
System deployment options
The system development can also be categorised into different system development options such as agile development, lean development, etc. these two are the major development methods or options available for the project. this depends on the compatibility and effectiveness of the business model.
Agile management or development option has the idea of equal and effective work distribution between the teams with effective engagement. it also provides better flexibility and innovation in the development phase (shah et al., 2013). though, it also causes different complexities such as poor time and resource management for continuous system changes with feedback analysis. in spite of that, the lean development option will be the most effective and appropriate in this case, as the system should follow the appropriate development strategy and planning. this is only the developer to call site band quantity analysis of different business requirements and system analysis.
this is also effective for resource management and eventual results (goetzler et al., 2016). overall, this analysis can establish that the lean management option will be most effective as a development option for the information system technology of the organisation. application of the option in the application phase, the project manager is responsible to develop appropriate and most effective planning that can develop the proposed system technology. in the next phase, open analysis and different reports who is implemented and the development phase will be started. The management authority and project manager will motivate and supervise the whole department for better analysis and further changes (if required). finally, the system will go through a proper testing procedure and feedback analysis that can improve the quality and service in a real-life business scenario.
Conclusion
To conclude, the testing method impacts a major significance in ac installation. the organization nqac provides a unique feature of temperature testing methods that can gradually increase the market demands. the facilities provided by the organization support gaining potential customers in the future. it helps in maximum registration and booking of products gradually. as the organization is recently shifting to a digital mode of marketing, it is essential to analyze the advantages and disadvantages of the conduction of the new system. developing the testing method leads the organization to follow the market trends, market demands, and customers’ requirements.
References
.png)
ITECH5402 Enterprise Systems Assignment Sample
Objective:
This assessment task has been designed to help you deepen your understanding of ERP/Enterprise Systems. It comprises both team and individual components.
Aim:
You have to produce a clearly articulated and well-researched enterprise system evaluation report to be given to the Board of Directors of GBI to successfully assist the organisation with choosing the correct software product to implement for their enterprise. Please refer to the GBI Case Document.
Learning Outcomes:
Evaluate and compare various types of enterprise resource planning (ERP) software solutions and their application in global business contexts.
Identify the main suppliers, products, and application domains of enterprise-wide packages.
Demonstrate communication skills to present a coordinated, coherent, and independent exposition of knowledge and ideas in dealing with enterprise systems.
Structure:
• Introduction
• Case Context, establishing the need for enterprise systems
• ERP Selection, indicating identification and comparison of several ERP systems
• Benefits to be gained from the ERP package proposed
• 3-4 additional technology required to meet the needs of the organisation. Ideally, each team member must identify one (1) technology to be included in the team report. This makes up the individual component.
• Concluding remarks, summarising the content of the report Demonstrate depth and breadth of reading to include a comprehensive reference list
• Use APA referencing style for all references in the body of text and in reference list
• Include readings from: Journals, Conference proceedings, presentations, books/book chapters, or any other significant sources.
Solution
Introduction
Enterprise resource planning defines a process used by the companies to combine and manage the importance of their business. ERP software is important for companies as they help them to execute resource planning by combining all the processes to run a company with a single system. ERP software combines human resources, marketing, finance, sales, planning, purchasing inventory, etc. This report aims to do a study analysis on the company ‘Bike Global Group’ as to how they work with their resources and how it manages distribution, selling, partnership, etc. The objective of the company was to manage the company with new resources and make bikes for both the genders males and females and to do work within the collaboration. Another objective of this report is to emphasize the benefits of implementing an ERP system for the Global Bike Groups for every management. This report highlights the background of Global Biker Groups and the various problems faced by them during the expansion of the company. This report throws light on how ERP systems allow the company to overcome these obstacles. This report also includes additional technologies that can be implemented in the company for the development of this company.
Case Context, establishing the need for enterprise systems:
Background
The Global Bike Group manufacture bike for long-distance and off-trail racing. Its founders designed their first bike, nearly 20 years ago as they had to win races and the bikes that were available at that time were not of high standards. So, they started the company named ‘Global Bike’ and started to deliver high-performance bicycles to the world’s most demanding riders. John Davis started it’s making his bike when he realized that the mass-produced bike was not fit for racing and rebuilt from other bikes into a single ‘Frankenstein’ bike that lead him to victory in the national championship. This made him famous and started his own company at a slow pace. At the nearly same time, Peter Schwarz designed their bike and slowly his bike turned into a small company which he, later on, get partnered with local companies. Fortunately, Peter and John met each other in 2000 and realizes their passion for business models, and collaborated and distributed their work for best assignment help.
Problems in the Global Bike Group
During the expansion phase, the Global Bike Group was being subjected to more workload. This workload leads to the various problem that has to be faced by the Global Bike Group. The process of management of these company become more tangible and dealing with the demands of the bikes according to the customer become their primary objective. This leads the company to lower its management process and handling such a huge company without a proper management plan was a tough job to achieve (Gallego, Mejia & Calderon, 2020). In the case study, it was seen that working after the collaboration and working together as a whole new company that comprises different departments needed a whole new management system. Sticking to outdated management techniques leads to ineffective and lesser productivity (Anatolievna & Anatolievna, 2018). But this did not keep them back from producing more products at that time.
Another problem faced by the company was that they were not achieving the required demands at that moment. After seeing lesser sales of the finished product they soon came to know that they need modifications on the bikes to fulfill new demands according to the changing requirements of the bike. Very less customer interaction was one of the biggest problems faced by any company (Goodman, 2019). On the other hand, this growing expansion of market and distribution demanded a more accurate management system to handle and supervise such a big network that includes the marketing department, sales department, research and development department, and production department.
Solution
Requirements and needs are the factors responsible for the alteration in product quality. Changing product manufacturing needs alteration in the manufacturing process and working of departments. To manage everyday changes in a company irrespective of the intensity of the change, a company needs to have a proper management technique through which effective management of various departments can be possible. The ERP system software provides the same requirement that can handle everyday work and processes of different departments in a single place. As in the case study, various problems related to the management of different departments include the manufacturing department, production department, sales department, distributor department, and many more. This ERP system software provides a proper management platform and smooth function of different departments. Handling of the distributer through ERP can be achieved in a simple way (Costa, Aparico & Raposo, 2020). The company can easily supervise the over the working through this system software.
Another biggest problem of customer interaction can also be solved by ERP system software. ERP system allows the company to store previous interactions with the same customer and can continue with conversation from where they left off. This enables the company to understand the customer and requirements of the customer more accurately which will eventually help the company to provide better customer service. This also makes the company more responsive to the requirement of the customer (Khan, Asim & Manzoor, 2020). This ERP can reduce the burden of expansion which results in more susceptibility to tangible network management and allows the company for further extension. In this way, ERP system software can overcome the problems faced by the company.
ERP Selection, indicating identification and comparison of several ERP systems
Different ERP:
SAP ERP System:
Since System Analysis Program has been started in 1992. This system is good for all types of businesses. Broad scope challenges of business data solutions are provided by ERPs (Al-Sabri, Al-Mashari & Chikh, 2018). To choose any software from this system, the company provides a free trial offer so that users can experience a product.
Oracle ERP System:
This resource planning is the leader in the computing space. It provides its own data management to the various industries. In keeping the view of business, it is designed at small, medium, and global levels. The companies who need to transfer and share large amounts of data or merge several companies can use this system (Amini & Abukari, 2020). It is very beneficial for them to use this ERP system.
Microsoft ERP System
Microsoft is one of the most wide-ranging software companies in the world that are selling an ERP called Dynamics 365. Their ERPs are cloud-based. This can be used by every business of every size, but it depends upon the varying price (Zadeh etal., 2020). Dynamics 365 can be used for human resources, customer service, retail operations, marketing, project automation, and so on.
IFS ERP System
Industrial and Financial systems are the leading source of enterprise-level software. It is a Sweden-based company that is providing services and solutions to manufacturers and organizations since 1983 (Grobler-Debska et al., 2021). This ERP highlights its software programs in terms of coordination and flexibility.
Comparison
.png)
.png)
Selection
Oracle ERP is best for the organization as it is designed in such a way that it can deal with every level of the business whether it is medium, large, or global. This ERP is the leader in the cloud computing space. It covers database management for a variety of industries in sales, marketing, manufacturing, and distribution. This software is too ideal for Global Bike Company as it can help get efficient in a large amount of data (Kakkar, 2021). Oracle ERP can help them in the merging of several companies. As management is very much necessary in the company in every part. As Global Bike company needs management as well as advanced capabilities that can be gained through this ERP. It can help the company to quickly react to market changes and shifts. Oracle ERP provides a space for the company to be updated always in the current situation and can get an advantage in the market as per their competition (Elbahri et al., 2019). This ERP is the best for the management of marketing, manufacturing, sales, and the distribution sector. Oracle ERP is the modern, complete, cloud ERP. The global company should have this ERP to be in this competitive market, to manage their database, to have a look over the shifts in the market, and to get updates on the current market. As of this ERP, Global Company can make the best use of it. This ERP helps to reduce business costs too and make companies’ analytics accurate too.
Benefits of ERP system
ERP system enhances business management models and functions that include preparation, inventory management, planning, order processing, production, financing, and many more. The most advantageous point which can be seen over the system is the capabilities to check and update in real-time and also enables to supervise the organization management (Rouhani & Mehri, 2018). Some other benefits of the ERP system can be brought up as key points as follows:
Data Integrated information across various departments.
Data integration refers to the process of gathering data in one place from the different departments which provides a single room for organizing data and data management. This also frames a base platform for the data analysis and production overview. For example, the data collected may originate from many sources like marketing software, customer application, CRM system, etc. All this information is required to be collected in one place for analysis for further action (Tarigan, Siagian, & Jie, 2020). The data integration task is managed by the developer and data engineers of the Company. All branches of Global Bike Groups are situated in different geographic locations, this company is required to deliver the data and services across their different branches. For these types of situations, the ERP system provides data integration which enables the organization to manage the data of different branches and different departments in one place.
Reduced data redundancy and processes
Another problem of data redundancy can be solved through an ERP system. With a data integration service facilitated by an ERP system, the same data kept in different places can be eliminated. After the foundation of Global Bike Group, expansion become the most significant part and it was seen more often in that case study. With the expansion of the company, handling of the data became more strenuous (Kumar, 2018). ERP system will ensure consistency in the work and required information can be received whenever needed in the company. Reliability of the data can be achieved with this system which was the biggest advantage of data redundancy to confirm the correctness of data while avoiding data redundancy at the same time (Chopra et at., 2022). Data redundancy enables the employee to get quick access to information as it was available on multiple platforms but this advantage is also covered by the ERP system.
Data security for the organization
Technology is the key to this globalization. Technology and globalization bring us close to the importance of data in digital platforms and its security. Dealing with a huge amount of data is the primary responsibility of any organization. All organization keeps their confidential as well as personal information along with their marketing information in a computer-based program for management purpose. Accidently losing such data can distort the organization’s work (Trunia et al., 2018). For any company, data are the most important aspect to record and maintain safety. These data can be very useful in the further decision-making process which will allow the company to generate higher revenue. ERP system will allow more security for the data of any organization or company.
Effective communication across different departments
With the foundation and expansion of the Global Bike Group in the case study from a single individual to a world-class company, many departments were set up within the company, and also many branches were set up at different locations across the globe. Effective communication is the key to proper working and managing a vast company. Proper channels of communication are required for smooth functioning (Aboabdo, Aldhoiena & AI-Amrib, 2019). Data sharing across the different department are equally important through effective communication. This effective communication of data sharing in Global Bikes Group can be achieved through ERS system. This ERS system also avoids conflicts in the department as the data is properly managed and organized in a single place in a computer-based program.
Additional technologies required by the organization
New technologies are emerging every day. To fulfill the demands and survival in the competitive market, companies and organizations need to keep themselves up to date with the upcoming new technologies. These technologies allow them to channel their work properly and increase the production of products with better quality (Biswas & Visell, 2019). Apart from the ERP system, Global Bikes Group is required to implement many new technologies to fulfill the need of the company. Some of them are listed below:
AI
The traditional methods for maintaining and running an organization can no longer keep up with these fast pace evolving requirements and complex demands of the customers. This drive organization to utilize technologies based on AI for interpretation and fulfillment of the demand of customers. AI is a computer-based software that performs given tasks close to human mind capabilities (De Cremer, 2021). AI generate more revenue and perform better in completing complex task which ultimately promotes the organization’s growth.
In the Case study, it was seen that after the establishment of Global Bikes Group became a vast company, managing such a big company was stressful. The tasks became more complex due to the demand of the customer (Wamba-Taguimdje, 2020). In these situations, AI can be very helpful in completing complex tasks and analyzing the demands of the customer to come up with a better result.
CRM
CRM is the abbreviation of Customer Relationship Management. CRM software is a tool that can be used to store data like marketing, sales, and customer services together with policies and customers in one place. When the business model on expanding, it became difficult to handle so the need for a remote CRM also increased (Kampani & Jhamb, 2020). This remote CRM enables them to manage sales productivity and also provide the proper platform to work with their staff and customer together.
CRM software is modifiable and it can be easily modified according to the customer and the organization’s needs. Many enterprises are already using CRM software for increasing marketing, customer support, and sales. Established companies use CRM software to increase the interaction of customers with the company which helps them find out the flaws in the product (Boulton, 2019). CRM can be modified by Global Bikes Group to respond to their customer requirements.
Cloud Management Platform
With technological advancement, the organization also needs to upgrade itself. This includes using various online services to be offered by the organizations. Cloud computing platform offers a variety of services (Lv et al., 2018). In the cloud, third-party service providers develop applications that can be accessed by users.
Features of Clouds
• It can handle multiple clouds.
• It allows controlling cost.
• User-friendly interface.
• It also reduces complexity in infrastructure.
Cloud is a fundamental part of the process of digitalizing of organization. However, as clouds become more and more complex cloud management platforms become the need for the organization to fully exploit the benefits of clouds. These cloud management platforms are important components that can be used to manage these clouds. Global Bike Group can implement a cloud management platform to enable various services over the internet through clouds.
Blockchain
Blockchain work on a shared network with a decentralized authority. It can benefit the organization in the following ways:
Public
Organizations always try to interact with their customers. Organizations create a network of federation Blockchain merging public and private networks. They keep their professional data on the private network and use the public network to connect with their customer (Bodkhe et al., 2020).
Transaction Cost
Organizations are always concerned about their security. Blockchain has an intense level of security and secure transaction through this network using cryptocurrency that cannot be easily tracked. This enables organizations to make their trading more confidential.
No intermediates
Intermediates service providers are always subjected to trust issues. Most of the fraud cases are linked through these intermediaries. In Blockchain, organizations do not have intermediaries so it saves the extra charges for providing their services and also reduces the chances of fraudulent cases (Morkunas, Paschen & Boon, 2019).
Conclusion
Expansion of an organization or a company makes the company more complex and management of such a big organization becomes a challenge. The load of work for each sector and department becomes complex and increases and becomes harder to manage. For a huge company as seen in the case study, the growing demands of the customer pressurize the company to the production of more and better products. This makes the workspace more crowded and the process more tangible. Here comes the need for proper management techniques for the organization. The ERP system is more of a management technique achieved through computer software. This allows the organization to handle everyday work like project management, supply of goods, project progress, accounting, sales, etc. From the report, it was seen that Global Bike Group faces many problems during the early stage and after the expansion of the Company. Problems like handling the expanded market situated in different geographical locations, dealing with the demand of increased customers through customer interaction, etc. From both perspectives of John Davis and Peter Schwarz, managing individual departments like VIP marketing, Chief Financial Official, VIP Human Resources, Chief Information Officer, VIP operations, and VIP Research and Development become tangible and they had to involve on the ground level with the staff to manage. All of these problems faced by the company can be solved through computer software based on the ERP system. Apart from solving the problem faced by the company, ERP based software system offers many benefits that include data integration, data security, and effective communications and also reduces data redundancy. Many additional technologies can also benefit the Global Bikes Group like AI, Cloud Management Platforms, CRM, and Blockchain for the development of the company in the era of technologies. Benefits like confidentiality of trading, Cloud management, user-friendly customer interactions, etc. will lead the company to achieve greater heights in the long run.
References
.png)
.png)
TITP105 The IT Professional Assignment Sample
ASSESSMENT DESCRIPTION:
Students are required to analyse the weekly lecture material of weeks 1 to 11 and create concise content analysis summaries (reflective journal report) of the theoretical concepts contained in the course lecture slides.
Where the lab content or information contained in technical articles from the Internet or books helps to fully describe the lecture slide content, discussion of such theoretical articles or discussion of the lab material should be included in the content analysis.
The document structure is as follows (3500 Words):
1. Title Page
2. Introduction (100 words)
3. Background (100 words)
4. Content analysis (reflective journals) for each week from 1 to 11 (3200 words; approx. 300 words per week):
a. Theoretical Discussion
i. Important topics covered
ii. Definitions
b. Interpretations of the contents
i. What are the most important/useful/relevant information about the content?
c. Outcome
i. What have I learned from this?
5. Conclusion (100 words)
Your report must include:
• At least five references, out of which, three references must be from academic resources.
• Harvard Australian referencing for any sources you use.
• Refer to the Academic Learning Skills student guide on Referencing.
GENERAL NOTES FOR ASSESSMENT TASKS
Content for Assessment Task papers should incorporate a formal introduction, main points and conclusion.
Appropriate academic writing and referencing are inevitable academic skills that you must develop and demonstrate in work being presented for assessment. The content of high quality work presented by a student must be fully referenced within-text citations and a Reference List at the end.
Solution
1. Introduction
The main aim to write this reflective journal report is to analyse the lectures of weeks 1 to 11 regarding ethics in information technology. This reflective journal will describe various roles for IT professionals and social, personal, legal and ethical impacts arising from their work. The role of the professional associations which are available to IT professionals will also be described in this reflective journal. It will assess the relationship between IT professionals and the issues of governance, ethics and corporate citizenship. I will critically analyse and review the IT professional Codes of Conduct and Codes of Ethics in this reflective journal report. This will help to develop a personal ethical framework for best assignment help.
2. Background
Technology offers various opportunities and benefits to people worldwide. However, it also gives the risk of abolishing one's privacy. Information technology must conduct business or transfer Information from one place to another in today's era. With the development of Information Technology, the ethics in information technology has become important as information technology can harm one's Intellectual property rights. Ethics among IT professionals can be defined as their attitude in order to complete something base on their behaviour. IT professionals need to have high ethics to process the data to control, manage, analyse, maintain, control, design, store and implement. Information Technology professionals face several challenges in their profession. It is their role and responsibility to solve these issues. The ethics of information technology professionals guide them to handle these issues in their work.
3. Content analysis
Week 1
a. Theoretical discussion
i. Important topics covered
In week 1, an overview of Ethics was discussed. Ethical behaviours generally accepted norms that evolve according to the evolving needs of the society or social group who share similar values, traditions and laws. Morals are the personal principles that guide an individual to make decisions about right and wrong (Reynolds, 2018). On the other hand, the law is considered as a system of rules which guide and control an individual to do work.
ii. Definitions
Corporate Social Responsibility: Corporate social responsibility adheres to organisational ethics. It is a concept of management that aims to integrate social and environmental concerns for promoting well-being through business operations (Carroll and Brown, 2018, p. 39). Organisational ethics and employee morale lead to greater productivity for managing corporate social responsibility.
b. Interpretation
The complex work environment in today's era makes it difficult to implement Codes of Ethics and principles regarding this in the workplace. In this context, the idea of Corporate Social Responsibility comes. CSR is the continuing commitment by a business that guides them to contribute in the economic development and in ethical behaviour which have the potentiality to improve the life quality and living of the employees and local people (Kumar, 2017,p. 5). CSR and good business ethics must create an organisation that operates consistently and fosters well-structured business practices.
c. Outcome
From these lectures in the 1st week, I have learned the basic concepts of ethics and their role and importance in business and organisation. There are several ways to improve business ethics in an organisation by establishing a corporate code of ethics, establishing a board of directors to set high ethical standards, conducting social audits and including ethical quality criteria in their organisation's employee appraisal. I have also learned the five-step model of ethical decision making by defining the problem, identifying alternatives, choosing an alternative, implementing the final decisions and monitoring the outcomes.
Week 2
a. Theoretical discussion
i. Important topics covered
In the 2nd week, the ethics for IT professionals and IT users were discussed. IT workers are involved in several work relationships with employers, clients, suppliers, and other professionals. The key issues in the relationship between the IT workers and the employer are setting and implementing policies related to the ethical use of
IT, whistleblowing and safeguarding trade secrets. The BSA |The Software Alliance and Software and Information Industry Association (SIIA) trade groups represent the world's largest hardware and software manufacturers. Their main aim is to prevent unauthorised copying of software produced by their members.
ii. Definition
Whistle-blowing refers to the release of information unethically by a member or a former member of an organisation which can cause harm to the public interest(Reynolds, 2018). For example, it occurs when an employee reveals that their company is undergoing inappropriate activities (Whistleblowing: balancing on a tight rope, 2021).
b. Interpretation
The key issues in the relationship between IT workers and clients are preventing fraud, misinterpretation, the conflict between client's interests and IT workers' interests. The key issues in the relationship between the IT workers and the suppliers are bribery, separation of duties and internal control. IT professionals need to monitor inexperienced colleagues, prevent inappropriate information sharing and demonstrate professional loyalty in their workplace. IT workers also need to safeguard against software piracy, inappropriate information sharing, and inappropriate use of IT resources to secure the IT users' privacy and Intellectual property rights and ethically practice their professions so that their activities do not harm society and provide benefits to society.
c. Outcome
I have learnt the various work relationships that IT workers share with suppliers, clients, IT users, employers and other IT professionals.
Week 3
a. Theoretical discussion
i. Important topics covered
In week 3, the ethics for IT professionals and IT users further discussed extensively, and the solutions to solve several issues that IT professionals’ faces were discussed. IT professionals need to have several characteristics to face these issues and to solve them effectively. These characteristics are the ability to produce high-quality results, effective communication skills, adhere to high moral and ethical standards and have expertise in skills and tools.
ii. Definition
A professional code of ethics is the set of principles that guide the behaviour of the employees in a business (Professional code of ethics [Ready to use Example] | Workable, 2021). It helps make ethical decisions with high standards of ethical behaviour, access to an evaluation benchmark for self-assessment, and trust and respect with the general public in business organisations.
b. Interpretation
Licensing and certification increase the effectiveness and reliability of information systems. IT professionals face several ethical issues in their jobs like inappropriate sharing of information, software piracy and inappropriate use of computing resources.
c. Outcome
I have learned several ways that organisations use to encourage the professionalism of IT workers. A professional code of ethics is used for the improvement of the professionalism of IT workers. I have learnt several ways to improve their ethical behaviour by maintaining a firewall, establishing guidelines for using technology, structuring information systems to protect data and defining an AUP.
Week 4
a. Theoretical discussion
i. Important topics covered
In week 4, the discussion was focused on the intellectual property and the measurements of the organisations to take care of their intellectual properties. Intellectual property is the creations of the mind, like artistic and literary work, inventions, symbols and designs used in an organisation. There are several ways to safeguard an organisation's intellectual property by using patents, copyright, trademark and trade secret law.
ii. Definition
A patent is an exclusive right to the owner of the invention about the invention, and with the help of that the owner have the full power to decide that the how the inventios will be used in future(Reynolds, 2018). Due to the presence of Digital Millennium Copyright Act, the access of technology protected works has become illegal.. It limits the liability of ISPs for copyright violation by their consumers. Trademarks are the signs which distinguish the goods and services of an organisation from that of other organisations. There are several acts that protect Trademarks secrets, such as the Economic Espionage Act and Uniform Trade Secrets Acts.
b. Interpretation
Open-source code can be defined by any program which have the available source code for modification or use. Competitive intelligence refers to a systematic process initiated by an organisation to gather and analyse information about the economic and socio-political environment and the other competitors of the organisation (Shujahat et al. 2017, p. 4). Competitive intelligence analysts must avoid unethical behaviours like misinterpretation, lying, bribery or theft. Cybercasters register domain names for famous company names or trademarks with no connection, which is completely illegal.
c. Outcome
I have learnt several current issues related to the protection of intellectual property, such asreverse engineering,competitive intelligence,cybersquatting, and open-source code. For example, reverse engineering breaks something down to build a copy or understand it or make improvements. Plagiarism refers to stealing someone's ideas or words without giving them credits.
Week 5
a. Theoretical Discussion
i. Important topics covered
The ethics of IT organisations include legal and ethical issues associated with contingent workers. Overview of whistleblowing and ethical issues associated with whistleblowing is being addressed (Reynolds, 2018). Green computing is the environmental and eco-friendly use of resources and technology(Reynolds, 2018). In this topic, there is the definition of green computing and what is initially the organisations are taking to adopt this method.
ii. Definition
Offshore Outsourcing: This is a process of outsourcing that provides services to employees currently operating in a foreign country(Reynolds, 2018). Sometimes the service is provided to different continents. In the case of information technology, the offshore outsourcing process is common and effective. It generally takes place when the company shifts some parts or all of its business operation into another country for lowering cost and improving profit.
b. Interpretation
The most relevant information about the context is whistleblowing and green computing. Whistleblowing is the method of drawing public attention to understand unethical activity and misconduct behaviour within private, public, and third sector organisations (HRZone. 2021).
c. Outcome
After reading the book, I have learned that green computing and whistleblowing are vital factors for the organisation's work. I have also learned about the diverse workforce in tech firms and the factors behind the trend towards independent contractors—the need and effect of H1-B workers in the organisation. Furthermore, the legal and ethical issues associated with green computing and whistleblowing have also been made.
Week 6
a. Theoretical discussion
i. Important topics covered
In this chapter, the importance of software quality and important strategies to develop a quality system. Software quality is defined as the desirable qualities of software products. Software quality consists of two main essential approaches include quality attributes and defect management. Furthermore, the poor-quality software also caused a huge problem in the organisation (Reynolds, 2018). The development model including waterfall and agile development methodology. Lastly, the capability maturity model integration which is a process to improve the process.
ii. Definition
System-human interface: The system-human interface helps improve user experience by designing proper interfaces within the system(Reynolds, 2018). The process facilitates better interaction between users and machines. It is among the critical areas of system safety. The system performance depends largely upon the system-human interface. The interaction between humans and the system takes place through an interaction process. Better interaction improves UX.
b. Interpretation
The useful information about the context is the software quality and the important strategies to improve the quality of software. The Capability Maturity Model Integration is the next generation of CMM, and it is the more involved model incorporating the individual disciplines of CMM like system engineering CMM and people CMM (GeeksforGeeks. 2021).
c. Outcome
After reading the context, I have concluded that software quality is one of the essential elements for the development of business. The software derives predictability from improving productivity in the business. The software quality decreases the rework, and the product and services are delivered on time. The theories and facts that are involved in developing the strategies that are involved in developing the software quality in the organisation.
Week 7
a. Theoretical discussion
i. Important topics covered
In this context, it will discuss privacy, which is one of the most important features for the growth and development of individuals and organisations. The right, laws, and various strategies to mitigate ethical issues are adopted (Reynolds, 2018). The e-discovery can be defined as the electronic aspect ofidentifying, collecting, and producing electronically stored information for the production of investigation and lawsuit.
ii. Definition
Right of Privacy: The privacy of information and confidentiality of vital information comes under the right of privacy(Reynolds, 2018). In information technology, the privacy right helps in managing the access control and provides proper security to the user and system information. This also concerns the right not to disclose an individual's personal information to the public.
b. Interpretation
The most relevant in the context are privacy laws that are responsible for the protection of individual and organisation's rights. The protection laws include the European Union data protection directive, organisation for economic cooperation and development, and general data protection regulation that protect the data and information of the individual and company (Reynolds, 2018). Furthermore, the key and anonymity issues that exist in the workplace like cyberloafing. The employees exercised the practice to use the internet access for personal use without doing their work.
c. Outcome
I have learned from this context that privacy is required for every organisation to protect the private information about the personal information and credentials that are present in the company—privacy along with developed technology that secures the data and information about the organisation. I have also got information about the ways and technological development to protect the data.
Week 8
a. Theoretical discussion
i. Important topics covered
In this context, it is discussed freedom of expression, meaning the right to hold information and share decisions without any interference. Some of the vital issues of freedom of expression include controlling access to information on the internet, censorship to certain videos on the internet, hate speech,anonymity on the internet, pornography, and eradication of fake news often relevant on the internet (Reynolds, 2018).
ii. Definition
Freedom of Expression: Freedom of expression denotes the ability to express the thoughts, beliefs, ideas, and emotions of an individual or a group (Scanlon, 2018, p. 24). It is under the government censorship which promotes the right to express and impart information regardless of communication borders which include oral, written, the art of any other form.
b. Interpretation
The most important information regarding the context is John Doe Lawsuits. It is a law that helps to identify the anonymous person who is exercising malicious behaviour like online harassment and extortion. Fake news about any information that is irrelevant, which are however removed by several networking websites. However, the fake news sites and social media websites are shared by several videos and images cause confusion and misinterpretation regarding a particular subject (Reynolds, 2018).
c. Outcome
After reading the book, I have concluded that the internet is a wide platform where several malicious practices are carried out, like fake news, hate speech, and many other practices practised on the internet. I have also gained information about several laws and regulations to protect the right and regulations on the internet, including the telecommunication act 1996 and the communication decency act 1997.
Week 9
a. Theoretical discission
i. Important topics covered
In this context, it will be discussed about cyberattacks and cybersecurity. Cyberattacks are an assault launched by an anonymous individual from one or more computers using several network chains (Reynolds, 2018). A cyber-attack can steal personal information a can disable the computer. On the other hand, cybersecurity is the practice of protecting information from cyberattacks. There are several methods to protect the internet from malware, viruses and threats.
ii. Definition
Cyber espionage: This is the process of using computer networks for gaining illicit access to confidential information(Reynolds, 2018). The malicious practice increases the risk of data breaching. It steals sensitive data or intellectual property, typically preserved by a government entity or an organisation (Herrmann, 2019, p. 94). Cyber espionage is a threat to IT companies, especially as it targets the digital networks for information hacking.
b. Interpretation
The most important aspect in this context is intrusion detection system, proxy servers like a virtual private network. The intrusion detection system is the software that alerts the servers during the detection of network traffic issues. The proxy servers act as an intermediator between the web browser and another web server on the internet. The virtual private network enables the user to access the organisation's server and use the server to share data by transmitting and encryption over the Internet (Reynolds, 2018).
c. Outcome
After reading the entire context, I have gained information about several cyberattacks and cybersecurity. Cyber attackers like crackers, black hat hackers, malicious insiders, cyberterrorists, and industrial spies (Reynolds, 2018). Cybersecurity like CIA security trial. Department of homeland security, an agency for safer and secure America against cyber threats and cyberterrorism. The transport layer security is the organisation to secure the internet from cyber threats between the communicating application and other users on the Internet (Reynolds, 2018).
Week 10
a. Theoretical discussion
i. Important topics covered
In this context, it is discussed about social media and essential elements associated with social media. Social media can be defined as modern technology that enhances the sharing of thoughts, ideas, and information after establishing various networks and communities (Reynolds, 2018). Several companies adopt social media marketing to sell their services and products on the internet by creating several websites across the Internet.
ii. Definition
Earned Media: It is observed in brand promotions in organisations where media awareness awarded through promotion(Reynolds, 2018). It is also considered the organic media, which may include television interviews, online articles, and consumer-generated videos. It is not a paid media; rather, it is voluntarily awarded to any organisation. The earned media value is calculated through website referrals, message resonance, mentions, and article quality scores.
b. Interpretation
The most important aspect of social media marketing where the internet is used to promote products and services. As per the sources, global social media marketing spends nearly doubled from 2014 to 2016, increasing from 15$ billion to 30$ billion—organic media marketing and viral marketing as one important aspect of social media marketing.
c. Outcome
I have gained much information about social media and elements of social media marketing, which encourages marketers to sell their products and services to another individual across the internet. Social media is a vast platform that has both advantages and disadvantages aspect. The issues regarding social media including social networking ethical issues that are causing harmful threats and emotional distress on the individual. There is a solution to these issues, which is adopted by several organisations like fighter cyberstalking, stalking risk profile, and many more.
Week 11
a. Theoretical discussion
i. Important topics covered
This context will eventually discuss the impact of information technology on society. The information impacts the gross domestic product and standard of living of people residing in developed countries. Information technology has made the education system more productive and effective. The process of e-learning has allowed the students to study from their homes. The health care system is also affected by information technology.
ii. Definition
Robotics: It is the design and construction of machines (robots) for performing tasks done by human beings (Malik and Bilberg, 2018, p. 282). It promotes autonomous machine operating systems for easing the burden and complexity of human labour. In this case, artificial intelligence helps to improve the development process of machines by incorporating the machine learning process. Automobile manufacturing industries use robotics design for safeguarding humans from environmental hazards.
b. Interpretation
The most information aspect of the topic is the artificial intelligence and machine learning have impacted the growth of IT. Artificial intelligence includes data and human intelligence processes that include activities like learning, reasoning, and self-correction. Machine learning is the process to talk with the technology through machine languages.
c. Outcome
I have gained much information about information technology and its impact on the organisation and people. The innovation and development occurred vastly due to the effect of social media.
4. Conclusion
It is to be concluded that this reflective journal report describes all the aspects of ethics in information technology by providing an understanding of the ethical, legal and social implications of information technology that IT professionals need to nurture in their professional work. Critical analysis of the privacy, freedom of expression, common issues of IT professionals, solutions of these issues are reflected in this journal report. The journal report also attempts to address the ethical issues in the IT workplace. An understanding of IT and ethics needed in IT professionals to achieve success is reflected in this journal report.
References
.png)
SYSS202 System Software Assignment Sample
ASSESSMENT DESCRIPTION:
Students are required to write a Reflective Journal in which they reflect on unit content and learning experiences between weeks x and y. In this assignment you should describe an interesting or important aspect of each week’s content/experiences, analyse this aspect of the week critically by incorporating and discussing academic or professional sources, and then discuss your personal learning outcomes.
The document structure is as follows (3000 words):
1. Title page
2. Introduction (~150 words)
a. Introduce the focus of the unit and the importance of the unit to your chosen professional area. Provide a preview of the main experiences and outcomes you discuss in the body of the assignment.
3. Body: Reflective paragraphs for each week from week x to week y (1 paragraph per week, ~250 words per paragraph). In each reflective paragraph:
a. DESCRIPTION (~50 words): Describe the week
• Generally, what was the focus of this week’s lecture and tutorial?
• What is one specific aspect of the week’s learning content that was interesting for you? (e.g. a theory, a task, a tool, a concept, a principle, a strategy, an experience etc.)? Describe it and explain why you chose to focus on it in this paragraph. (*Note: a lecture slide is not an acceptable choice, but an idea or concept on it is)
b. ANALYSIS (~100 words): Analyse one experience from the week
• Analyse the one specific aspect of the week you identified above
• How did you feel or react when you experienced it? Explain.
• What do other academic publications or professional resources that you find in your own research say about this? (Include at least 1 reliable academic or professional source from your own research). Critically analyse your experience in the context of these sources.
c. OUTCOMES (~100 words): Identify your own personal learning outcomes
• What have you learned about this aspect of the unit?
• What have you learned about yourself?
• What do you still need to learn or get better at?
• Do you have any questions that still need to be answered?
• How can you use this experience in the future when you become a professional?
4. Conclusion (~100 words): Summarise the most important learning outcomes you experienced in this unit and how you will apply them professionally or academically in the future.
5. Reference List
Your report must include:
• At least 10 references, 5 of which must be academic resources, 5 of which can be reliable, high-quality professional resources.
• Use Harvard referencing for any sources you use
Solution
Introduction
System software, various operating systems, and the functions of key parts of the system are needed to be understood inevitably to operate the systems effectively. Operating systems and storage systems are the key parts of a system. The functions of these parts are essential to be understood to manage the operations through the systems effectively. Furthermore, the networking system, file manager, and many more key resources are described properly through the weekly materials to make the learners understand the complex operational functions of the computer systems. A learner can understand the importance of every key function of the computer system with proper and in-depth knowledge. Memory, security systems, and ethical operations of the computer systems are also described in this report for assignment help. User interfaces, Graphical user Interfaces (GUI) are also described in the report. Reflective analysis of my learning about the use of different functions and operating systems of computers has been portrayed in this report.
Week 1: Functions of various operating systems
The week 1 lecture provides knowledge regarding the functions of various operating systems and their roles in the systems. I have gained in-depth knowledge about operating systems and software, and hardware. Planning design of the software in the computer system through this lecture material provides a detailed analysis of computer operations and management (Fakhimuddin et al. 2021, p-24). Programs, tangible electronic machines, and many more parts and their operational activities guide the proper management of a computer system.
File manager, main memory, and many more functional parts are inevitable for operating the computer system. I have gained knowledge regarding the classification of various software and hardware operations of a computer system. Operating systems coordinate many systems to work together for better productivity. Memory, storage devices, different applications, and many more roles and responsibilities of various key parts of a system have been taught. RAM and ROM and their functions based on volatile and nonvolatile nature are inevitable to understand the storage and memory of a system (Ayadi et al., 2021, p-20). Input and output devices as well as peripheral devices such as "mouse," "keyboard," "printer," "scanner" and many more perform various necessary key operations of the computer systems.
As I have gained major knowledge about the parts and operating system, it would be very beneficial to perform all the functions effectively. The use of input and output devices helps to perform various necessary tasks with one system. Software applications help perform the core operational activities of the system and maintain the coding and database of the system. The database manages important information of any application and system also (Shukla et al. 2018, p.16). I understand using these key operating functions for mastering the system for any complex work. I have also learned about the data manipulation and retrieval of deleted data in the system in any emergency.
Week 2:memory and space allocation and de-allocation of the computer system
Week 2 describes the knowledge about the memory and space allocation and deallocation of the computer system. The concept of the replacement of pages, allocation of pages, and the function of paging in the system are provided in this session. I have also gained knowledge regarding using various memories such as cache memory and many more, which is essential to be understood for operating a system. I am very glad to know the operational activities of various paging operational activities of the system. The paging operations provide me with detailed knowledge regarding the page setup and various designs of the pages (Shukla et al. 2018, p-30). Page frames for various programmable key factors help understand the design of pages for different operations in a system. I am very glad to know about these kinds of interesting facts about the system's different major paging operations. I can use this knowledge to understand the system's operational activities for designing various pages for programs. The knowledge I gained has helped in completing the operational activities of the computer system for better management. As this basic knowledge is essential for me to understand the system in detail, the functions assist me to perform all kinds of important operations for my career growth. Page setup is quite an important factor for the system to create documents and programs (Youssef et al. 2018, p-20). Thus, I have understood the page framing and important operational performance of this page replacing and allocation for the system, which has made the system's functions easier for me.
Week 3:Device management system
Description
The device management system is one of the most important parts of the computer system (Kaluarachchilage et al. 2020, p-1). The session has provided me with knowledge about device management systems to understand the use of computer systems better. Advantages and disadvantages of various devices of the computer system have been a part of this session so that I can understand the operational management of various functions and malfunctions of the system. I am very excited to implement the knowledge of many devices that can easily make various operational performances of the system. Operations of various devices help to perform many works simultaneously. DSD (Direct Action of Storage Devices) helps to perform all the data storing operations effectively (Prakoso et al. 2020, p.157). Furthermore, the knowledge assists me in using the proper timing of implementing many functions of the key parts of the computer operations. Various devices such as "printer," "plotter," "drive," and much more help in performing various activities in computer systems. Detailed understanding of the storage and functions of many devices makes the user operational process for the computer system easier. The input and output of various data storage of the system make the system perform well and effectively (Prakoso et al. 2020). The session has provided me with such knowledge, which is essential for performing various operations. The use of this knowledge also makes me an expert at the performance of different complex problems of the systems.
Week 4:Different processors
The week 4 sessions has depicted a clear understanding of different processors and their detection process in the system. Processors are the key part of a system that performs the core operations for the system (Scalfani 2020, p.428). The performance regarding providing instructions for operating different programmable languages and software applications is inevitable to understand. I have understood the core functional areas of the computer system with the application of different programmable languages. Furthermore, the operating system is based on "deadlock," "real-time systems," "resources," and many more for better knowledge. “Modelling deadlock” for the operations of programmable languages is quite interesting to understand while understanding the graph cycle of data process to resources (Syuhada 2021, p.1335). This graph cycle of process data as resources helps to complete the operations of computer systems effectively. I have also learned the procedures of allocating multiple devices at a time with a single system with the use of proper databases. Knowledge of databases and multiple processors helps to persist the knowledge regarding managing various job operations. Furthermore, access to different file requests provides me with in-depth knowledge of different programs and files. The computer operating systems understand locking levels and data integrity (Li et al. 2021, p.522). Locking and accessing processes of different files have also been understood. Thus, this session has made me understand properly to learn the proper locking and data management effectively.
Week 5:System management
Week 5 provided me with complete and detailed knowledge of system management of the computers. Monitoring of systems and the protection of database management in the system have made me understand computers' complete functions (Wang and Lu, 2019). Evaluation of operating systems and strengths and weaknesses of the system based on hardware and other devices and software applications also. I have gained immense pleasure by learning the application of database protection and system management. As system management is one of the most important parts of a computer system, the session has helped me understand it. However, I realize that I need more detailed and in-depth knowledge regarding the practice of database management. More clarity will help me to perform the hardest operational activities also. Algorithms and the use of the CPU (Central Processing Unit) have also been discussed in this particular session (Wang and Lu 2019). I need more clarity in understanding algorithms as it is a difficult part and one of the most important parts of the system. The knowledge regarding system management and algorithms is not quite satisfactory for me to perform any important task effectively. Operations of multi programs are one of the most beneficial factors of the system, which makes the operational activities of computers easier (Wang and Lu 2019). Furthermore, I have also gained immense knowledge about patch management and operational accounting activities. However, a clearer understanding and in-depth knowledge of algorithms are essential for better management.
Week 6:File management
The session has mainly focused on operations and clarity regarding file management which is inevitable to store the data in computer systems. Furthermore, the role of various extensions for various file formats in the system has provided me with knowledge regarding the storage and management of databases. Furthermore, access to different files and data protection control are very important for different functions of computer systems. I have understood that a complete knowledge of file management systems is essential for storing important information in computers. Furthermore, the compression process of data for file storage and procedures of controlling data is quite important for the systems (Ayoubi et al. 2018). The knowledge is very beneficial for me to manage the data of different files with different extensions. As the file manager operates the functions of different files, the organisation of different files is quite important for the effective use of the storage and memory space of the system. Collaboration of data management and the functions of different software in modifying and controlling data is quite important for the system. Management of files and control and access to data are essential parts of the computer's system (Ayoubi et al. 2018). I have gained immense knowledge about the management of different files in the system so that the access of the files can be handled properly. Functions of different files help me understand the access of different parts effectively so that program libraries can be operated effectively.
Week 7:Network functioning
Session of week 7 refers to a basic knowledge of network functioning for the computer system. This session has highlighted the introduction of various networking systems and their responsibilities. Furthermore, the comparison between NOS (Network Operating Systems) and DOS (Distributor Operating system) has been discussed in this session (Ayoubi et al. 2018, p.23). The performance of this network management system has been described in this session which is very beneficial for me to understand. Network management is one of the most important computer system factors (Saadon et al. 2019). I have understood the complete and detailed knowledge of network management with a properly explained session this week. The variance of local operating systems and their relation to NOS has made me understand how to allocate file management and data computing for a particular system. I have also understood the various functions of local operating systems and the distribution of different files based on different data. Application servers and many other user interfacing systems have been explained effectively to better understand the chapter of networking management. Server running systems and application running of computers help operate different functions in a single system effectively (Saadon et al. 2019). This session has helped me understand the clear knowledge of network management and the relation to operating systems of the computer. This exercise has helped me to manage the clients in my workplace, which has been very beneficial for me. Furthermore, I have gained some effective knowledge that has helped me start my new career regarding new business related to software applications based on networking management.
Week 8: Basic structure of security
Week 8 sessions has outlined a basic structure of security of computer systems effectively. Furthermore, data security is one of the major concerns in the cyber world. Different viruses often break the security chain of the computer system so that the appropriate advanced technologies can be implemented to maintain the security thread of the system (Saadon et al. 2019). The role of various OS (Operating Systems) in managing data security has also been depicted in this session. Ethical practices have also been discussed in the session while maintaining the system's security. Systems operational activities and key functional areas are discussed in the system, which has helped me learn to maintain computer systems' security. I am very excited to understand the relations of operating systems with the security and ethical practices of the computer. My knowledge regarding the maintenance of the system's security has helped me understand the proper implementation of protection to protect important data. Viruses, worms, and many other cyber threats often break the security chain (Muslihah and Nastura 2020). Proper ethical practices are needed for better management of computer operations effectively.
Outcomes
The knowledge of security maintenance has helped me pursue my career in the data security management of computers. As this chapter is quite interesting for me, it has provided me with a curiosity to know the advanced level of technology that helps maintain computer security (Muslihah and Nastura 2020). I have learned about data backups, retrieval of data, and advanced level technology to manage the system's security.
Week 9:Data operating systems
Description
Session 9 has provided me with great knowledge regarding data operating systems and data survival management. I have experienced data management by implementing proper server technologies in the system. Furthermore, the operating system has managed to operate the system's important functions, which can run the software and hardware operations effectively (Muslihah and Nastura 2020). Network and security management are major key operational functions of the system. The operating systems have the responsibility regarding the management of operating systems. Furthermore, I have learned the implementation of different operational functions to manage better important data and resources, which is quite beneficial for me to make data confidential. The session has also depicted the advanced level technology while performing the tasks and managing different operations (Talha et al. 2019, p.72). Various operating systems have performed the key functions in the computer system while performing the knowledge. Data management knowledge and theories based on advanced technologies have helped me pursue my career in data security management systems. Deallocation and reallocation of data and knowledge based on the practices of various software and hardware applications have provided me with immense knowledge about computer operational activities and their progress. Furthermore, the data management system has helped me perform all the database and code practices activities, which help me understand computers' functions (Muslihah and Nastura 2020).
Week 10:Different windows operating systems
This session has mainly described the functions of different windows operating systems and the management activities of the computer. File drives and customisation of different software of the systems are the core parts of the computer systems. Furthermore, memory management and virtual memory space-based learnings have been provided to better design windows systems. Security-based challenges and various computer processors are depicted in this session (Talha et al. 2019). I feel the knowledge I learned through this session is quite important to understand the core functions. Furthermore, communication of interprocess management and different versions of windows have provided me knowledge regarding the implementation of various important tasks. From the initiation of “Windows XP" to “windows version 10.0” have seen the progress of development of different processes of computer systems in the recent era (Talha et al. 2019). Newest versions have helped to perform various incredible tasks within a very short period of time. I have gained a great deal of knowledge regarding various operating systems from DOS to the upgradation of newest software applications. This kind of knowledge has helped me to pursue my career in a better way so that the operations of different tasks can be maintained effectively. Furthermore, I have also understood a detailed practice of many operating systems and programmable languages along with networking based products.
Week 11:Linux operating systems
Session 11 has focused on the practice of Linux operating systems and the management of different software interrelated to these operating systems of computer. Role of different memory, devices and file management to the operational activities of computer systems have been provided in this session (Wang et al. 2020). Responsibilities of different software applications interlinked to “Linus Torvalds” are depicted in this week to understand the basic operational functions of “Linux Operating System”. I am quite excited by learning the operational practises of computer systems and the management of different machine languages. Role and functions of different software applications for operating “Linux” based systems (Wang et al. 2020). Portability of programs and system software are quite important parts of the systems. I have experienced better practice regarding the knowledge of main memory as well as user interface systems. The knowledge is quite effective for managing any difficult tasks with proper clarity. Various roles and responsibilities of the computer system are quite important for me to perform any kind of task effectively. The basic knowledge of operating systems especially “Linux” has helped me to understand the effectiveness of the management based functions (Wang et al. 2020). Various functions such as different software and hardware applications are quite essential for me to perform different tasks of the computer in a greater way.
Conclusion
Various management and operational functions of computer systems are the major focus areas of the sessions. The sessions have provided me with great knowledge regarding the management of different functions and roles as well as responsibilities. Furthermore, implementations of different advanced technologies have been provided for a clear understanding of the system. Protections of important data and data manipulation have become one of the most important highlighted areas of the systems. Security management and server management based knowledge have also been provided for better practise of the computer system so that the operations have been performed well in the systems. System software and hardware based knowledge have also been provided for my better career in this field and performing any complicated tasks in this field.
References
.png)
ITBO201 IT for Business Organisations Assignment Sample
ASSESSMENT DESCRIPTION:
Students are required to write a Reflective Journal in which they reflect on unit content and learning experiences between weeks x and y. In this assignment, you should describe an interesting or important aspect of each week’s content/experiences, analyse this aspect of the week critically by incorporating and discussing academic or professional sources, and then discuss your personal learning outcomes.
The document structure is as follows (2500 words):
1. Title page
2. Introduction (~150 words)
a. Introduce the focus of the unit and the importance of the unit to your chosen professional area. Provide a preview of the main experiences and outcomes you discuss in the body of the assignment.
3. Body: Reflective paragraphs for each week from week x to week y (1 paragraph per week, ~200 words per paragraph). In each reflective paragraph:
a. DESCRIPTION (~50 words): Describe the week
o Generally, what was the focus of this week’s lecture and tutorial?
o What is one specific aspect of the week’s learning content that was interesting for you? (e.g. a theory, a task, a tool, a concept, a principle, a strategy, an experience etc.)? Describe it and explain why you chose to focus on it in this paragraph.
b. ANALYSIS (~75 words): Analyse one experience from the week
o Analyse the one specific aspect of the week you identified above.
o How did you feel or react when you experienced it? Explain.
o What do other academic publications or professional resources that you find in your own research say about this? (Include at least 1 reliable academic or professional source from your own research). Critically analyse your experience in the context of these sources.
c. OUTCOMES (~75 words): Identify your own personal learning outcomes
o What have you learned about this aspect of the unit?
o What have you learned about yourself?
o What do you still need to learn or get better at?
o Do you have any questions that still need to be answered?
o How can you use this experience in the future when you become a professional?
4. Conclusion (~100 words): Summarise the most important learning outcomes you experienced in this unit and how you will apply them professionally or academically in the future.
5. Reference List
Your report must include:
• At least 10 references, 5 of which must be academic resources, 5 of which can be reliable, high-quality professional resources.
• Use Harvard referencing for any sources you use
• Refer to the Academic Learning Support student guide on Reflective Writing and how to structure reflective paragraphs
Solution
Introduction
In this report all the weekly summaries are present. In the different week, we study the different types of technologies, management techniques, and many more which is very helpful in both type of organizations that is big and small. We research with the different types of study material and weekly lectures and find out the best technologies from every week and discussed in the report. In this paper the reflecting summary of every week is discussed. This paper is important in the terms of information security and information technologies. From the development of the computer to the emerging technologies development all the things are described in the report. As we have seen that the rising in technologies also raises some risks, attacks, phishing, and many more. So in this paper different type of risk management techniques is also discussed. The report is consisting of the overall summary of how the computer is developed to how we manage all the information technology and security for assignment help.
Week 1 –
Chapter 1 Information Security
In week 1 we are focused on the learning of Information security. After successfully learning in week 1 the student is familiar with some concepts of information security which are described as below:-
• The information security concept.
• The history of information security
• How information security is important in the system development cycles.
The main thing that is very interesting in week 1 is merging information security with the system development life cycle. In my opinion including the system security in the system, the development life cycle is much beneficial in the terms of security because if our system is secure then we will secure for the cyberattacks and many unwanted things that are occurred in today’s era. As we see that software development life cycle is generally considered with the 6 phases but if we add one more phase which is system security then we protect all the things from attack in development itself. I learned how system security is important in our day-to-day life and how we manage both the system and security at a low cost. I learned the most important thing from this week's lecture is that “As we have seen the technology is increased day by day so we also look into the security and modified ourselves to protect from the data breaches and cyber-attacks.” (Bidgoli, 2019, p. 12)
Week2-
Chapter 2 Machine Based Computing
In week 2 we are focused on the learning of Machines behind Computing. After the successful learning in week 2 the student is familiar with some concepts of Machine Behind Computing which are described as below:-
• The computer hardware and software
• Understand the computer operations
• Understand the different input, output, and memory devices.
Job management, resource allocation, data management, and communication-related thing are present in the week 2 lecture. In my opinion, the main thing which is very interesting in the overall week 1 lecture is the memory device because in this era the need for memory is a high priority. The thing or the topic which is very much interesting and the helpful is the Operation that is performed by the Computers there are three basic operations of the computer which are arithmetic, logical and storage. I learned that without memory management all the function we have done is waste. Without memory we have not correctly organized things so for this purpose memory management in the computer or the software is a must. I chose memory management because in my opinion if we correctly manage memory then after this management of the entire task is very easy.
Week 3-
Chapter 3 Database System
In week 3 we are focused on the learning of Database systems, Data warehouses, and Data Marts. After successfully learning in week 3 the student is familiar with some concepts of Database System, Data Warehouse, Data Marts which are described as below:-
• Understand the database and the database management system, data warehouse.
• Understand how the logical database and the relational database are designed.
• Understand the full lifecycle of the database management system, data warehouse.
• Understand the database uses and design.
• Understand Big data and their different application
The main thing which is very much interesting in week 3 is the big data and its various business applications. I chose this topic for the discussion because the big data is everywhere for example:-social media, entertainment, financial services, government, manufacturing, healthcare, and many more things are depends on big data. I chose this topic because there is vast scope in the field of big data also it is famous in the today’s era. It is said that people or users depending on the social network or technology for their daily activities and both generate a lot of data in a single day so in the future the world depends on big data. (Bidgoli, 2019, p. 31)
Week 4 –
Chapter 5 -Protecting Information Resources
In week 4 we are focused on protecting information resources. After successful learning in week 4 students are familiar with some concept of how to protect the information system or resource which is mentioned below:-
• Understand the different types of technologies that are used in the computer system/.
• Understand the basic safeguard in the computer and network security
• Understand the major security threats
• The Security and enforcement measure is understood.
In week 4 the very interesting topic is the risk associated with information technologies. In a big organization, risk management is a very interesting topic. How they handle the risk is very important in a large-sized organization. It is seen that in the future as the technologies are increasing so the cyberattack, phishing through email, D-Dos attacks is also increased. So in this way, risk management in every type of organization is a must. By preparing the risk management plan we can protect our organization and ourselves from the various attacks that is held today or in the future. In the future cyberattack which is very common is phishing, email attack, D-Dos Attack and many more. The attacker always catches to the weak point of organization so we need to change our risk management policy and make it strong. (Bidgoli, 2019, p. 21)
Week 5 –
Chapter 14 Emerging Technologies, Trends and Application
In week 5 we are focused on emerging technologies, trends, and their application. After successful learning in the week, the student is familiar with some concepts of an emerging trend, technologies, and application which are described below:-
• Understand the new trends in the software
• Understand the virtual reality components and applications.
• Understand cloud computing, nanotechnologies, blockchain technologies.
In week 5 the most interesting topic according to me is blockchain technology. In simple words block technologies means the decentralized and distributed network. The blockchain is used to record transactions across connected devices as blocks of data that cannot be altered after being recorded. In week 5 we study different case studies of the company for the blockchain technology we understand the Wal-Mart case study. I chose this topic for discussion because due to the high security in blockchain management or development the transaction is proceeding at a faster rate. (Bidgoli, 2019, p. 31) In the future the application which depends on the blockchain are described as below:-
• For the tracking foods and the goods.
• In the security of the software development
• The management of digital content
• To improve the healthcare record
• In the audit Trial
Week 6 –
Chapter 11 Enterprises System
In week 6, we are focused on the learning of the Enterprise Systems. After successful learning in week, 6 students are familiar with some concept of enterprise system which is described as below:-
• Understand supply chain management.
• The customer relationship management and the management systems.
• An understanding of the enterprise resources planning system is gained.
In week 6, we understand different type of application that is used in the management of the technology and the business. In week 6, the topic which is most interesting is the supply chain. In simple word, the Supply chain means the network which is consisting of an organization, supplier, transportation companies, and brokers. Supply chain management is used the delivery goods and services to customers. This topic excites me most because in the era of online supply management is a must. As we have seen that people purchase the goods, product, service, and essential materials of daily lives online. So in this way, the management of the supply chain is a must in the future. A healthy relationship is made between the suppliers, organizations, transportation companies, and brokers. Due to this healthy relationship, the supply chain is managed perfectly. To ensure the business or organization growth we manage supply chain perfectly. (Bidgoli, 2019, p. 52)
Week 7 –
Chapter 8 E-Commerce
In week 7 we are focused on E-commerce. After successfully learning in week 7 the student is familiar with some concepts of E-commerce and the E-commerce platform which is described as below:-
• Understand the concept of e-commerce, its advantages, disadvantage, and also business models.
• The different categories of e-commerce and the lifecycle of the e-commerce cycle.
• Understand the social media, mobile-based, and voice-based e-commerce in the market.
In simple words, e-commerce means all the activities like selling and buying that are performed using computers and communication techniques. In week 7 we focused on the many case studies like star bucks company, coca-cola, and many more by which we can easily be familiar with the e-commerce business models. In my opinion, the thing that is more interesting in week 7 is the online service delivered by e-commerce. The e-commerce service helps the youth and old age to provide them good services. In the future, the e-commerce sector is on the boom. With the increase in technology, people used mobile in many modes like for shopping, for bill payment and many more. So in this way, the e-commerce sector is on boom in the upcoming generation. E-commerce provides many facilities to make it easy for everyone to use mobile services like voice assistance, direct messaging system, and many more. The boom of technology also made payment services very easy in an e-commerce application. (Bidgoli, 2019, p. 67)
Week 8 –
Chapter 10 Building Successful Information System
In week 8 we are focused on building a successful information system. After successfully learning in week 8 the student is familiar with some concepts of how to build the information systems which are described as below:-
• Understand the system development life cycle in the building of successful software.
• The different type of phase that is involved in the software development life cycle that is the planning phase, requirement gathering phase, analysis phase, design phase, implementation phase, and maintenance phase.
• The new trends in the system design are also introduced in this lecture.
The most interesting part of week 8 is the new phase that is involved in the software development life cycle. It seems that the procedure is very much important in software development but choosing the right one is difficult. So in this week all the phases and models are clearly described. The model which I suggest is an agile methodology, in this week I studied different case studies and I recommended that agile methodology is very much beneficial. In the future, the agile methodology is at its peak because it follows the weekly or we can say that time sprint. In a particular time sprint, the task is to be done so in this way project is delivered on the given time. That is the reason big company follows the agile methodology in the software development life cycle. (Bidgoli, 2019, p. 90)
Week 9-
Chapter 12 Management Support System
In week 9 we are focused on the management support systems. After successful learning in week 9, the student is familiar with some concept of management support system which is described as below:-
• Understand how the big organization makes decisions and maintain those decisions.
• Understand how the decision support system works.
• How the geographic information is important.
• Guideline for designing a management support system.
In week 9 we understand the concept of decision making also means how the big organization takes decisions. The Decision is also taken in the three-phase which are structured decision, semi-structured decision, and unstructured decisions. In this week 9, the most interesting topic is decision making in the organization or we can say that in the big organization. In the process of decision making every type of decision like payroll, inventory problem, record keeping, budget preparation, and sales forecasting are involved in it. In the future, this type of decision is taken with the help of artificial intelligence and we know how artificial intelligence is on the peek in the future. It is seen that every industry depends on the decision process. So the process of decision-making in week 11 excites me most. (Bidgoli, 2019, p. 103)
Week 10 –
Chapter 13 Intelligent Information System
In week 10 we are focused on the Intelligent Information System. After successfully learning in week 10 the student is familiar with some concepts of how the intelligent information system which is described as below:-
• Understand artificial intelligence and how AI technologies support decision-making.
• The expert system and the application or the components.
• The case-based reasoning
• Different types of logic like fuzzy, case-based logic, genetic algorithm, natural processing, and many more.
In week 10 the most interesting topic according to me is artificial intelligence. In simple words, artificial intelligence is a technology that is try to simulate and reproduce human behavior. This technology is applicable in different sectors that as perception, reasoning, cognitive abilities, and many more. It is seen that artificial intelligence have a great impact on both industries and human being. In the future, artificial intelligence is everywhere like robot techniques, Internet of things techniques. In every field, artificial intelligence is used. It is seen that in the future artificial intelligence is on the boom because in many fields artificial intelligence works in the field of marketing, in the field of medicine, in the field of management, and the field of safety. Artificial Intelligence also developed the automated car and we see that the car and medical sector is a very large sector so in this way we can say that the artificial intelligence sector is on boom in the future. (Bidgoli, 2019, p. 120)
Week 11 –
Chapter 7 -Internet, intranets and extranets
In week 11 we are focused on the internet, intranets, and extranets. After successful learning in week 11 the student is familiar with some concepts of the internet, intranets, and extranets in the information security system which is described as below:-
• Understand common internet service
• The purpose of intranets, extranets.
• Understand the Internet of everything
• The navigation tools, search engines, and directories.
In this week 11, there are many concepts which I have learned that is a different type of browser for more security like Google, Chrome, brave and Mozilla Firefox. The most interesting thing that is in week 11 is the new concept that is the internet of things which means it is web-based development in which people process the data which is connected with the internet and other various things like OR Codes, barcodes, and many other devices. The future of the IoT is very bright. It is estimated that 30.9 billion IoT projects are developed in the year 2025. In 2025 by the use of the Internet of things, more cities become very smart. To save the most of company and cities are using smart technologies and these smart technologies are generally made with the Internet of things. (Bidgoli, 2019, p. 78)
Conclusion –
In this report, we learned the different technologies that are very emerging and in the future, these technologies are on the boom like nanotechnologies, big data, and artificial intelligence and robot techniques. As a student after researching and learning all the week's concepts, we are familiar with the topic and find out that every technology depends on others so we have to try to use this technology and maintain the risk that is present in the technologies. As we see that different technologies are mentioned in the report so as a student the very interesting technology is risk management because we see that as an increase in the technology the risk is also increased so that risk management is a must.
References List
.png)
.png)
COMP1001 Data Communications and Networks Assignment Sample
Task Description:
Your task is to create a technical report of your home network and propose a plan for its improvement. Your work must demonstrate your learning over the six modules of this unit. The format of the report with requirements that you have to fulfil are detailed in the template provided with this assignment description.
In summary, your report will have to provide the following technical details:
• R1: Network topology
• R2: Network devices
• R3: Communication technologies
• R4: Addressing scheme
• R5: Network protocols and analysis
• R6: Network services
• R7: Network security and analysis
• R8: Performance parameters and analysis
Finally, your report will also provide your own analysis and assessment regarding role of computer networks in your life and study. Support your analysis and assessments with evidences.
Solution
R1: Network Topology
For network topology considering the home network two different topologies are defined in the section one is physical topology and another is logical topology. Both network topologies are described below as:
Physical Topology
.png)
As home network is a wireless network where a single router is used for internet connection and that router connected to an access point. There are four systems for assignment help which are connected to the wireless network in Star pattern that can be observed in the above figure. The physical topology shows the wireless connectivity from router to the client system. It can also be observed in the above diagram that router is directly connected with access point.
Logical Topology
The above figure define logical topology of home network that is based on data flow connection and connected client devices to the network. It can be observed how data is transfer from router to the and devices where this router is directly connected with access point. Here the data flow pattern can be changed according to the requirement and structure of the system. The installed router is able to cover a defined range where the router can provide internet connectivity to all systems which comes under this defined range.
Difference between Physical and Logical topologies
Physical topology is based on network devices which are used in selected network that consist of connection cables and network devices. As it can be seen in the above physical topology that connections cable are not used because home network is a wireless network. Instead of connection cable the wireless connectivity has shown in physical topology for home network. The router which is used is wirelessly connected to the access point that allow data communication for data flow to router and then connected devices. The physical topology for wireless network is not that complex as wire-based network contains.
The logical topology define data flow among the network devices which are used in selected network that is home network. The logical topology consist of data flow connection or representation of data flow and network devices such as router and client devices. Here home network is considered that is based on wireless network so data flow can be observed between router and devices were the main router is connected to access point for data communication. The major differences between physical and logical network topology of home network is physical topology represent cable as connection and logical topology represent data flow as connection.
R2: Network Devices
This section discusses different network devices which are used in home network. As the home network is a wireless network that consists of router-modem client devices, mobile phones and tablets.
Client Devices
Laptops
1. Model: The model of the laptop can be considered as latest model of 3rd generation. The laptop is able to connect wirelessly to any network.
2. Technical specification: The laptops are based on the 3rd generation and 5th generation that are able to connect with any wireless network. The network driver are installed in all the laptops that allow data transfer from external sources. Each laptop have feature to act as router so that other devices can connect with laptop as a wireless connection.
3. Physical Network Interface: The physical network interface consist of network adaptor that is a small integrated chip install in network devices. The laptop which are connected to the homemade work contains network adaptor that allow to connect with the wireless network for data transfer.
Router
Router is a main network device in home network that allow a wireless connection to more than one IP address for data communication. The router installed in home network allow multiple connections that can connect wirelessly such as laptops, mobile phones, tablets and desktop. Further this router is wirelessly connected to the access point.
1. Model: The model of the router connected in the Home wireless network is TP-Link Archer AX6000.
2. Technical specification: This is based on new technology such as 802.11ax with OFDM that allow to provide high speed for data communication. The speed of router is considered as 1148 Mbps with 2.4GHz and can perform up to 4804 in case of 5GHz band. This Router allows multiple Ips for wireless connection in-home network.
3. Physical Network interface: The physical network interface can be measured by using the network analyser as the speed of the router can be observed on screen.
Wireless Access Point
In computer networks wireless access point is a type of device that allow various wireless cards that can connect to all and devices without physical cables. Access points are also able to connect with LAN and create a wireless network. This is the only device that is able to connect from wired network environment to wireless network environment. Generally it is also use to transform network type at workplace or for home purpose. Wireless access point can physically connect with LAN and transform into a wireless network to all of more than two IP addresses for data communication in wireless network environment.
1. Model: The model of the Access point is Wi-Fi 6/6E (802.11ax) Catalyst
2. Technical specification: This is considered as most reliable that contains top speed of 9.6Gbps with 6TH generation 802.11 ax.
3. Physical Interface: The physical interface of this network device is reliable and strong with high speed.
R3: Data Communication Technologies and Standards
Generally, four type of wireless data communication technology are found such as wireless LAN wireless man wireless pan and wireless van. The only difference among all these four wireless data communication technologies is size or range including with connectivity requirements.
The data communication technology which is used in home network is Wi-Fi technology that is considered as one of the most common wireless data communication technology for small range connectivity requirements. Wi-Fi basically stands for wireless fidelity initiated by NCR corporation. This technology simply allows data transfer among more than one devices that is actually based on mobile computing. This technology allow devices to be mobile in nature through which devices can move from one place to another while connecting with her particular network for data transfer. Wi-Fi is basically a wireless LAN model that used for small range or size with minimum connectivity requirements. By using Wi-Fi a small wireless network can be construct from one end to another end that highly considered for home network
Technical Specification
This section discuss this about technical specification of Wi-Fi data communication technology where the most important specification is frequency band of Wi-Fi data communication technology that is 2.4GHz ISM. The bandwidth of channel for Wi-Fi data communication technology is 25 Mhz. Wi-Fi technology have half duplex with all kind of bandwidth. The technology which is used in Wi-Fi data communication is direct sequence spread spectrum.
Application of wi-fi Technology
This section discusses about application of Wi-Fi technology as Wi-Fi technology have multiple applications.
The very first and important application of Wi-Fi technology is any wireless devices which are capable to connect wirelessly can connect with internet. Wi-Fi technology is able to provide access to the internet for more than one device.
The second most important application of Wi-Fi technology is that video, as well as audio streaming, can be done wirelessly with any devices for the purpose of entertainment.
The important files and data can be shared from one system to another system through wireless connection easily. There is another important application where Wi-Fi can be used as hotspot that will allow other devices to get access for the internet. That actors which are installed in Wi-Fi are non for spreading radio signals by using the owner network for providing hotspot to other devices. Wi-Fi data communication technology can also be used for poisoning system.
Wi-Fi standard
The Wi-Fi standard which is used for home network is IEEE standard 802.11g that provides a frequency of 2.4 GHz with a maximum speed of 54 mbps. This is standard is considered as quite common for the home network.
R4: Addressing Schemes
This section discusses the addressing schemes of home networks where each network devices has IP addresses for data communication. The physical and logical addresses for the connected devices in home network is defined considering the data transfer. The IPv4 Address is 192.0.2.1 where IPv6 Address is 2001:db8::1. The IP address of the Router is 192.168.1.1.
IP address is considered as logical address which is actually assigned by the software application in system or in router for data communication with other devices. In home network IP address is assigned to all the connected devices such as router laptops and other devices.
R5: Network Protocols
The wireless network protocols which is used in home network is 802.11g that generally a combination of 802.11a and 802.1 b. In this section wire Shark network analyser is used to analyse the technical specification of used wireless network protocol that is 80 2.11 g.
The above 2 pictures define status of package transfer and network traffic identified by the wireshark network analyser. Network protocol is basically basic guidelines which are made for data communication. The wireless network protocol called 802.11 g is considered as family network protocol standard that allow connection of multiple devices. The collection of protocols that contains multiple protocols for different purpose and functions is TCP /IP. This version of the network protocol is derived from the previous version where generally one version of the network protocol is transform in another updated version based on the requirements of connectivity and innovation in networking technology. As it can be absorb in the above figure that logical addresses of connected devices are shown while packet transfer.
R6: Network Services
In this section of the report network services will be discussed that allow to provide different type of services to client system. They are two important network services which are discussed in this section such as DHCP service and DNS service. Here DHCP services define dynamic host configuration protocol and DNS service define domain name system.
DHCP service
DHCP is a type of protocol that is used for network management where DHCP is responsible for assigning IP addresses to all the connected network devices so that they can communicate over a network utilising the allotted IP address. By using this service IP address can be assigned to any network devices which are connected or going to connect within a wireless network. The device with mobile nature IP addresses are changed while moving from one place to another so DHCP assign IP addresses to each location.
The DHCP server address is 192.168.29.122 and the DHCP client address is 10.1.1.100/24. The scope of IP address is defined and checked using command prompt.
The the DHCP service can be found almost every network in infrastructure that is based on wireless or wire based network because for every wireless network wireless devices are used that are mobile in nature. For sach devices which are mobile in nature required temporary IP addresses and these temporary IP addresses assign by the DHCP service.
DNS service
Domain name system or DNS service is considered as phone book over the internet where humans while using the internet utilise domain names for assessing any information. Suppose a user typed isko.com then isko.com is a domain name that is used by user for assessing information. Here the browser use IP address and DNS service change domain name into IP address so that browser can find the relevant information by using the IP address from the server. DNS service simply reduce the complexity of remembering IP address that is actually difficult to remember by humans. So human can use website name or domain name for searching any information and DNS service translates these domain name into IP address through which required information can be access by browser easily. There is a simple purpose of DNS that is converting the horse name to IP address that is actually a system friendly.
The DNS IP address is 192.168.29.122.
R7: Network Security
Network security is one of the major concern that are discussed by many exports in literatures and articles. The network security exports continuously working on innovation in network security field so that numerous of attack and losses due to the attacks can be minimised. This section discusses about network security measures and the possible attacks on home network.
The common types of network security measures are intrusion prevention system, firewalls and intrusion detection system. These three are the common parameters based on which network security can be analysed where intrusion prevention system help in preventing home network from external attacks and intrusion detection system help in detecting the possible attacks from external sources over home network. Firewalls are the another important network security measures that will help in filtering out the malicious link and data from open source platforms
Top three Attacks
1. Malware: Malware attack is a very common type of attack where malicious link or file downloads automatically while using the internet or downloading any files from the internet. This attack include is stealing information or data from the system with the help of malware downloaded while using internet.
2. DoS attack: Daniel of service attack is another common type of attack where the network gets shut down and unable to access by the user. This can cause network flooding or high traffic on home network.
3. Phishing Attack: In this type of attack malicious link or email sent to the target system where user click on that link unknowingly and convert into a victim of attack.
R8: Performance Parameters
This section discusses about the performance parameter of home network with some basic parameters such as:
Bandwidth = 2.4Ghz
High speed = 54Mbps
Coverage area = More then 802.11a and 802.11b
ITECH1103 Big Data and Analytics Assignment Sample
IT - Report
You will use an analytical tool (i.e. WEKA) to explore, analyse and visualize a dataset of your choosing. An important part of this work is preparing a good quality report, which details your choices, content, and analysis, and that is of an appropriate style.
The dataset should be chosen from the following repository:
UC Irvine Machine Learning Repository https://archive.ics.uci.edu/ml/index.php
The aim is to use the data set allocated to provide interesting insights, trends and patterns amongst the data. Your intended audience is the CEO and middle management of the Company for whom you are employed, and who have tasked you with this analysis.
Tasks
Task 1 – Data choice. Choose any dataset from the repository that has at least five attributes, and for which the default task is classification. Transform this dataset into the ARFF format required by WEKA.
Task 2 – Background information. Write a description of the dataset and project, and its importance for the organization. Provide an overview of what the dataset is about, including from where and how it has been gathered, and for what purpose. Discuss the main benefits of using data mining to explore datasets such as this. This discussion should be suitable for a general audience. Information must come from at least two appropriate sources be appropriately referenced.
Task 3 – Data description. Describe how many instances does the dataset contain, how many attributes there are in the dataset, their names, and include which is the class attribute. Include in your description details of any missing values, and any other relevant characteristics. For at least 5 attributes, describe what is the range of possible values of the attributes, and visualise these in a graphical format.
Task 4 – Data preprocessing. Preprocess the dataset attributes using WEKA's filters. Useful techniques will include remove certain attributes, exploring different ways of discretizing continuous attributes and replacing missing values. Discretizing is the conversion of numeric attributes into "nominal" ones by binning numeric values into intervals 2 . Missing values in ARFF files are represented with the character "?" 3 . If you replaced missing values explain what strategy you used to select a replacement of the missing values. Use and describe at least three different preprocessing techniques.
Task 5 – Data mining. Compare and contrast at least three different data mining algorithms on your data, for instance:. k-nearest neighbour, Apriori association rules, decision tree induction. For each experiment you ran describe: the data you used for the experiments, that is, did you use the entire dataset of just a subset of it. You must include screenshots and results from the techniques you employ.
Task 6 – Discussion of findings. Explain your results and include the usefulness of the approaches for the purpose of the analysis. Include any assumptions that you may have made about the analysis. In this discussion you should explain what each algorithm provides to the overall analysis task. Summarize your main findings.
Task 7 – Report writing. Present your work in the form of an analytics report.
Solution
Data choice
In order to perform the brief analysis on the selected data set, it is important to make the data suitable for analysis using WEKA tool. This tool for assignment help support only ARFF format of data and arff viewer in this tool helps to view and transfer data set into appropriate form of data (Bharati, Rahman & Podder, 2018). In this task, a data set has been downloaded which is related to the phone call campaign of Portuguese banking institution. The data set was initially in the csv format which is imported into the analytical platform. In the below figure, the csv file has been shown which was initially imported into the analytical tool. Based on the tool requirement, this data file need to be transformed into arff format.
.png)
Figure 1: Original csv data
After importing the csv file into the arff viewer, the file has been saved as arff data format to convert the data set type.
.png)
Figure 2: Transformed ARFF data
In the above figure, it has been seen that the data set has been transformed into arff format and all the attributes of the data frame is present into the dataset. The data set conversion has been successfully done to do further analysis on the selected data set.
Background information
In this project, a data set has been chosen which is related to the bank customer details. Data has been generated after getting information from clients through phone calls to predict if they are interested to invest into term policies. There are several attributes are available into the data frame. Here, the data types and other information related to the client are given. On the other hand, a brief analysis on the data frame could be conducted into the WEKA data mining tool. There are different analytical algorithms have been associated that could be utilized to classify data by considering a particular class variable. The data set has been downloaded from UCI machine learning repository. A large number of data sets are available into this website that consist of variety of topics and categories. The data set is mainly about the client details and based on the attributes present into the data frame, all the necessary analysis could be done.
In order to get proper insights and findings from the analysis, clients could be classified into two categories. Persons who are interested to invest in term policies and who are not interested in investment are the two major categories. In this project, a bank market analysis will be done to get knowledge on the investment pattern by the clients. The project is mainly focused on the data analysis by using WEKA analytical tool. Based on the given data and statistic, several essential insights could be extracted by using the analytical platform. Here, the Portuguese banking institute will be able to make crucial decision on the client engagement and investment issues. Based on the client data analysis, attractive offers and terms could be given to the potential investors. On the other hand, a complete statistics of the pervious campaign and their output could also be achieved by the analysts. In order to enhance the subscription rate into the organization, this analysis will help the organization through statistical analysis. All the major findings will be documented into this report.
In order to fulfil the project aim and objectives, WEKA data mining tool will be used that gives major features to pre-process and analysis data set. There are several benefits could be achieved by the users by using the data mining tool. Based on the data types and project objective, data mining tools could be used for multiple purposes. Business managers can obtain information from a variety of reputable sources using data mining tools and methodologies. After conducting a brief study on the selected large dataset, industry professionals can gain a number of important observations. On the other side, with analytics solutions like WEKA, a significant volume of data and information may be readily handled and controlled. Furthermore, the policy maker could make a variety of critical judgments after evaluating the information utilizing data mining methods, which could lead to positive outcomes business expansion.
Data description
A bank campaign data has been selected in this project and it will be analyzed to get vital information on the clients. It is important to understand the data set properly to make better analysis on the analytical platform. The data set consist all the major attributes related to the clients including age, marital status, loan details, campaign details, campaign outcome and some other indexes. However, all the attributes are categorized into client data, campaign data, social and economic attributes. All the attributes could be pre-processed to conduct the analysis after considering the class attribute and categories. The last attribute of the data frame is desired_target that will be considered as the target class. If the clients are interested to invest in the bank on term policies is the main focus of the entire analysis. Here, a major concern of the project is to make a brief analysis on the given data frame. On the other hand, some data pre-processing will also be done to prepare the data frame suitable for the analysis. There are several filtering features have been given by the analytical platform.
There are 19 attributes are available into the data frame and all the necessary attributes will be considered for this analysis. Here, five major attributes have been evaluated based on the importance for this analysis:
• Job: This is a major attribute that gives overview on the work filed of the client. Income level of the client could also be assumed through the job profile which could play a vital role on investments strategy of the client. In terms of business perspective, job profile of the client could play a better role to customize offers and policies of the client.
• Marital status: Based on the marital status of the client, investment tendency could be assumed. For each relationship, different financial investments are sometime done by the consumers. One the other hand, expenses of the clients also varies on the relationship status.
• Loan: Previous loan consumption or financial transaction of the client should also be considered by the business analysts of the banking institutes. This attribute tells if the client has consumed any previous loans or not.
• Poutcome: This feature is another vital thing that should also be considered to predict if the client is interested to invest or not. After each campaign, output is considered as success or failure. This would play a vital role in this analysis.
• Cons.conf.idx: On the other hand, consumer confidence index is another essential aspect that must be analyzed to predict if the client in interested in investment or not.
The above five attributes are the most essential aspects that must be analyzed to get insights on the campaign data and its possibilities. However, the campaign strategy could be changed based on the previous results and outcomes.
Data pre-processing
Data pre-processing is the primary stage that must be performed by the analysts to prepare data suitable for the analysis. During the analysis, some of the major issues are faced that must be mitigated by using different pre-processing techniques. Data cleaning, transformation and other some other operations are performed during the data pre-processing. In this task, different data processing steps have been followed to make the data frame suitable for the analysis.
Removing attribute from the data frame
.png)
Figure 3: Unnecessary attributes removed
In the above figure, two attributes including euribor3m and nr.employes have been removed from the data frame. These are the two attributes that will not provide any vital insights on campaign data.
Discretizing attributes
.png)
Figure 4: Discretizing attributes
In the above figure, four attributes have been selected that have been transformed from numeric to nominal data type. This will make the analysis easier by selecting the class data type. On the other hand, the selected analytical tool is not comfortable with the numeric data types and it gives betted visualization on the nominal values.
Removing duplicated values
Duplicated values gives wrong analytical result on the data frame. For this reason, it is important to remove the duplicated values from the data frame. In the below figure, all the attributes have been selected and then a filters has been applied to remove duplicated values from the data frame.
.png)
Figure 5: Removing duplicated values
After removing duplicated values, it has been seen that the count of each columns or categories have been reduced. After removing duplicated value, only distinct type data are present into the data frame.
These three data pre-processing steps have been introduced in this project to make the data set appropriate for the analysis. After preparing data with some pre-processing steps, all the necessary analysis and insights have been built.
Data mining
There are several data mining techniques are there that could be introduced into the data set to get proper insights and visualization on current business operations and activities. Based on the business requirement, classification algorithm could be implemented into the data frame. On the other hand, a brief analysis on the given problem context could be introduced by the users after successfully implementing the algorithms. In this task, three different algorithms have been selected and executed on the data frame.
Random Forest algorithm
Random Forest algorithm is a major type of classification algorithm that take decision on the given data set by classifying data frame into different categories. By selection random data from the data frame, decision tree is created and then based on the accuracy of each branch, decision tree gives result. In this project, decision tree has been implemented into the data frame to classify clients into potential subscribers or non-subscribers. In order to improve the accuracy of the model, average of sub samples are calculated by this algorithm.
.png)
In the above figure, a random forest algorithm has been executed on the campaign data set in order to classify the clients. All the attributes have been included in this execution and based on the cross-validation, 10 folds have been tested.
.png)
Figure 7: Output of RandomForest model
After implementing the classification algorithm, a complete statistic of the model performance have been given in the above figure. All the necessary parameters have been given in the given statistic. The developed model given about 85% of accuracy. The model has been built within 5.66 seconds. A confusion matrix on the selected model has also been created that classifies the data frame into two categories.
Naive Bayes algorithm
Naïve Bayes classification algorithm is a supervised algorithm that is simple and effective for the classification and prediction of a particular feature. It's termed Nave because it considers that the appearance of one feature is unrelated to the appearance of others. As a result, each aspect helps to identifying that it is a fetaure without relying on the others. In order to classify the identified features from the data frame, the naïve bayes classifier algorithm will set some pre-defined identifications (Hawari & Sinaga, 2019). However, this algorithm has some independences variable on the given data frame and prediction of feature is made with some probabilistic assumptions.
.png)
Figure 8: Naïve Bayes classifier
In the above figure, a naive bayse algorithm has been executed into the given data frame. The data frame has been classified into two categories that are yes and no. 10 fold cross validation has been selected as testing option. Based on some particular features, this model will classify the data frame into class variables.
.png)
Figure 9: Output of Naive Bayes model
After the implementation of the naive bayes algorithm, the above statistic has been achieved that shows all the essential parameters of the model. However, this model is able to classify the data frame with more than 83% of accuracy. Here, the confusion matrix has also been demonstrated that gives overview on the classification capability of the model.
K-nearest neighbor
In this model, new data are classified after checking the similarity with the previous data. Knn algorithm can easily classify the given data into categories based in the previous data records. Both the regression and classification models could be developed by using knn algorithm. Assumption on the underlying data are not triggered in this algorithm. However, the action performed in the training data are not quickly implemented into the test data set.
.png)
Figure 10: K-nearest neighbor
In the above figure, a lazy classifies algorithm has been executed into the data frame. The nearest neighbor will be identified based on some per-defined characteristics. Here, 10 fold cross validation process has been used.
.png)
Figure 11: Output of K-nearest neighbor
In the above figure, several performance parameters have been illustrated as output of the model. On the other hand, the confusion matrix of the model has also been introduced in the above figure.
Discussion of findings
After conducting brief analysis on the given data set, a number of vital insights have been achieved that have been discussed in this section with proper evidences.
.png)
(Figure 12: Age variable vs. desired_target)
In the above figure, it has been seen that the clients with age between 33 to 41 are highly interested to invest in term policies. The rate of investment is decreasing with increase in age of the clients.
.png)
Figure 13: Job variable vs. desired_target
On the other hand, clients with job profile in administration have maximum probability of getting subscription or non-subscription.
.png)
Figure 14: Marital status variable vs. desired_target
Here, the analysis has been done based on the marital status of the client. This shows that the married persons are highly interested to make investments.
.png)
Figure 15: Loan variable vs. desired_target
Those clients who have already taken any loans are interested to make investments. On the other hand, percentage of non-subscribers is lower who have not taken any loan.
.png)
Figure 16: Poutcome variable vs. desired_target
However, the output of the phone campaign gives a statistic that most of the campaign have not given any particular result or assumption.
.png)
Figure 17: Cons.conf.idx variable vs. desired_target
The confidence index of the consumers is another essential aspect that has also been analyzed in the above figure.
.png)
Figure 18: Cons.price.idx variable vs. desired_target
Consumer price index has been illustrated in the above figure. After categorizing the feature in terms of desired_target, some vital insights have been introduced.
References
.png)
.png)
ITECH7407 Real Time Analytics Assignment Sample
Learning Outcomes Assessed
The following course learning outcomes are assessed by completing this assessment task:
• S1. Integrate data warehouse and business intelligence techniques when using big data.
• S2. Create flexible analytical models based on real time data, and use connectivity interfaces and tools for reporting purposes.
• S3. Use real time performance analysis techniques to monitor data, and identify shifts or events occurring in data, as a basis for organisational decision making.
• S4. Use real time mobile tracking techniques to utilise mobile-specific usage data.
• K3. Communicate the key drivers for big data in terms of efficiency, productivity, revenue and profitability to global organisations.
• K4. Identify and describe types of big data, and analyse its differences from other types of data.
• A1. Communicate security, compliance, auditing and protection of real time big data systems.
• A2. Adopt problem solving and decision making strategies, to communicate solutions to organisational problems with key stakeholders, based on analysis of big data, in real time settings.
Deliverable 1. Analysis Report (30%)
Task 1- Background information
Write a description of the selected dataset and project, and its importance for your chosen company. Information must be appropriately referenced.
Task 2 – Perform Data Mining on data view Upload the selected dataset on SAP Predictive Analysis. For your dataset, perform the relevant data analysis tasks on data uploaded using data mining techniques such as classification/association/time series/clustering and identify the BI reporting solution (e.g., diagrams, charts, tables, etc.) and/or dashboards you need to develop for the operational manager (or a relevant role) of the chosen organisation.
Task 3 – Research
Justify why you chose the BI reporting solution, dashboards and data mining technique in Task 2 and why those data sets attributes are present and laid out in the fashion you proposed (feel free to include all other relevant justifications).
Note: To ensure that you discuss this task properly, you must include visual samples of the reports you produce (i.e. the screenshots of the BI report/dashboard must be presented and explained in the written report; use ‘Snipping tool’), and also include any assumptions that you may have made about the analysis in your assignment report (i.e. the report to the operational team of the company). A BI dashboard is an integrated and interactive tool to display key performance indicators (KPIs) and other important business metrics and data points on one screen, but not a static diagram or graph. To ensure that you discuss this task properly, you must include visual samples of the reports you have produced (i.e. the screenshots of the BI report/dashboard must be presented and explained in the written report; use ‘Snipping tool’), and also include any assumptions that you may have made about the analysis from Task 3.
Task 4 – Recommendations for CEO
The CEO of the chosen company would like to improve their operations. Based on your BI analysis and the insights gained from your “Dataset” in the lights of analysis performed in previous tasks, make some logical recommendations to the CEO, and justify why/how your proposal could assist in achieving operational/strategic objectives with the help of appropriate references from peer-reviewed sources.
Task 5 – Cover letter
Write a cover letter to the CEO of the chosen firm with the important data insights and recommendations to achieve operational/strategic objectives.
Other Tasks –
At least 5 references in your report must be from peer-reviewed sources. Include any and all sources of information including any person(s) you interviewed for this project. Please refer to the marking scheme at the end of the assignment for other tasks and expectations.
Deliverable 2. Personal Reflection
This deliverable for assignment help is an individual work and can be attached to your data analytics report. In this part, each student will write a one-page-long reflection report covering the following points:
• Personal understanding of course content, and personal insights into the importance and value of the course topics.
• Three most useful things you have learned from the course and explain how they could help your current learning and future professional career.
• Personal feeling of SAP products (or other equivalent tools) used in lab exercises and assignments.
All discussion is expected to be well backed with real examples.
Solution
Deliverable 1. Analysis Report
Task1- Background Information
Australian Institute of health and welfare is recognized as a freely statutory institute generating accessible and authoritative statistics as well as information in order to inform and help better service delivery & policy decisions, leading towards effective wellbeing as well as health for entire Australians. Australian Institute of health & welfare/AIHW has high experience of over 30 years with welfare and health data records. This is also known at both national and international levels for their statistical expertise and ensured track the records in facilitating the independent evidence and high quality. To facilitate statistical information for community and governments to utilize in order to promote discussion & inform the relevant decisions based on health, community services, as well as housing is the mission of AIHW. On the other hand, facilitating robust evidence in terms of information and data for better decisions as well as improvements in health & welfare is the vision of AIHW. AIHW supports releasing various health solutions for community so, they need a good expenditure to continue progress in this field (Health Direct, 2022).
In this manner, the dataset selected for this agency is related to the area of expenditure, broad sources of funding, and detailed sources of funding for AIHW including corresponding states and financial years. This selected dataset is varying from the financial year 1997 to 2012 respectively. This dataset is very essential and helpful for AIHW executive dashboard review for health expenditure with a long duration (1997 to 2012). Hence, the dashboard will help the CEO of AIHW to recognize the entire business expenditure, total resources, and broad/detailed contributors so, that the CEO can make the decisions appropriately and plan further expenditures more accurately by analyzing and tracking this expenditure dashboard. According to the selected datasets, the main areas of expenditure are administration, aids & appliances, other medications, benefit-paid pharmaceuticals, capital expenditure, dental services, community health, medical expense tax rebate, health practitioners, medical services, patient transport service, private hospitals, public health, research, and public healthcare.
The main importance of this project and selected dataset is listed below-
• To reduce the unnecessary expenses.
• To increase the revenue
• To increase market promotions
• To ensure public health and welfare programs (Burgmayr, 2021).
Task2- Data Mining
The selected datasets from the given source and relevant AIHH teams such as CEO, Director, Finance Director, and Operational Director are identified to prepare the high-level dashboard accordingly. So, the selected datasets can be proposed as-
.png)
.png)
Therefore, the data analysis is done based on such expenditure review for AIHW from 1997 to 2012. To analyze the defined datasets, some major data mining techniques have been used including classification analysis, cluster analysis, and regression analysis which are systematically mentioned below-
• Classification Analysis: This data mining technique is used to extract the most relevant and required datasets for the financial years 1997 to 2012 for reviewing total expenditure of AIHW agency. Using this analysis method, the different datasets have been classified into different classes. The classification is done based on the six corresponding classes such as financial year, state, area of expenditure, broad sources of funding, detailed sources of funding, and real expenditure in millions. This classification helped to analyze the data using creating the appropriate graphs and charts accurately.
• Cluster Analysis: Cluster analysis is a series of data variables; these variables are equivalent within the same cluster. This method is used to discover the clusters in data according to the range of association between two variables. This is used to get help in customizing the dashboards for CEO and Finance manager specifically.
• Regression Analysis: Regression analysis is also used for the expenditure review in order to identify and evaluate the relationships among such classes or variables. This analysis technique helped to understand the feature values of each dependent class change if any of available independent variables vary. In other words, it helped in prediction of total expenditure and revenue growth of AIHW (Souri, & Hosseini, 2018).
Task3- Research
Assumptions
Before mining the datasets, it is essential to disclose the main assumptions made for analysis of these datasets, and these assumptions are mentioned in the following points-
• Total of 15 expenditure areas is covered throughout the datasets review.
• Financial year is concerned as per the calendar year from 1997 to 2012.
• Broad source funds and detailed source funds are centralized to calculate the total expenses and revenue.
• A total of 8 states are covered to make the data model.
CEO Dashboard
The dashboard of CEO is outlined below with particular analysis as the main purpose of this dashboard is to review the real expenditure in millions by state as well as area of expenditure. The dashboard comprises major financial years of highest expenses, real expenditure in millions, main states, and the major areas of highest expenditure.
.png)
Figure 1: CEO Dashboard
The structure of above-mentioned dashboard is classified into four main classes in order to support the business outcomes. Major descriptions of expenses, areas, states, financial year, and real expenditure amount are calculated and plotted using graphs to highlight the revenue and expense ratios.
In case of CEO dashboard, entire information is at broad level including Australian level rather than only one or two particular cities in order to give major snapshots of this large AIHW business.
Supporting Charts
.png)
Figure 2: Expenditure Charts
These supportive bar charts are used in the estimation of total expenses and revenue forecasting by state and area of expenditure as it gives a foundation line view of the details concisely. The other views include the total real expenditure using all measures. On the other hand, top 4 real expenditure is investigated by state and these states are NSW, VIC, QLD, and WA. Similarly, the top 4 expenditure areas are identified including public hospitals, private hospitals, benefit-paid pharmaceuticals, and all other medical services. Thus, the result is clearly outlining the main sources of highest expenditure in AIHW in terms of these four states and areas of expenditure.
.png)
Figure 3: Broad source-based expenditure charts
The above-illustrated charts are reflecting following observations-
• The real expenditure graph is estimated mostly for the years 1998 and 1999 where 1997 has no value for highest expenditure.
• For detailed source funding, the real estimated expenditure has constant value based on all measures.
• On the other hand, the main broad sources of funding including government and non-government sources have real expenditure value as shown in right-side designed top and down charts.
.png)
Figure 4: expenditure in million
This chart is defining the real expenditure in millions to estimate the total expenses and most sensitive states. Thus, the graph is not static as per financial years.
Finance Director Dashboard
.png)
Figure 5: Finance Director Dashboard
The layout of finance director dashboard illustrated above is customized based on a similar approach to previous chairman’s dashboard. Review the real expenditure in millions by state as well as area of expenditure is the main purpose of this dashboard. The high-level dimension’s performance is outlined based on four main classes including the most expensive financial years, most expenses raised state, and most expenses raised areas of AIHW to measure the expense history and plan further financial strategies accordingly. The objective of this finance dashboard is to facilitate more stable information in order to track the financial performance on previous record basis. It is reflected in the developed graphical evidence that is showing the financial performances in terms of real expenditure in millions as per the highest expensive financial years. Supporting this graph, corresponding charts are also generated to show the main expenditure areas and states.
Supportive Charts
These chats and bars are systematically listed below with brief analysis-
.png)
Figure 6: Expenditure charts
The overall designed or generated charts articulated above are showing the financial director’s dashboard results in which the review of expenditure is done on the basis of state and area of expenditure. Top four real expenditure areas are discovered with top four real expenditure states based on the financial years. The real expenditure in million is also proposed using static graphic view.
.png)
Figure 7: Total value in million
These charts are very specific as these help in estimating the historical expenditure values using reviews and tracks of such selected AIHW records including a possibility to calculate the total revenue according to financial years of 1997 to 2012. This has been estimated that the value of expenditure in previous financial years is majorly higher than 200 million as the graph rate is constantly increasing as represented in above chart. So, it has been estimated that AIHW has higher revenue growth based on total expenditure values. The highest expenditure is the highest revenue so, the result is positive for AIHW as they increased their revenue per year.
Task4- Recommendations for CEO
To enable the AIHW CEO for improving their business operations based on the business intelligence analysis done previously some recommendations are suggested. The perceptions obtained from the selected and analyzed datasets, and some logical solutions in terms of recommendations will be guided to the CEO of AIHW so, that CEO can achieve the strategic and operational objectives of their agency using different BI models. Big data is one of the most effective solutions that can help CEOs to understand the previous records and current data status of their agency so, that appropriate planning and decisions can be made.
To make AIWS a data-driven agency, CEO has to identify the business and strategic values of big data instead of focusing on technological understanding. To transform this health and welfare agency, the appropriate strategies are required to formulate. So, to leverage the benefits and improvement strategies of Big data analytics effectively, five key strategies are recommended below-
Deployment of big data governance
Governance of big data is an upgraded version of IT governance that concentrates on benefitting the organizational large data resources to build business values. Big data analytics will help AIHW CEO in expenditure management, IT investment, financial planning, and healthcare data governance. The organizational heterogeneous knowledge, information, and data can be easily governed internally by CEO by changing the business processes in more accessible, secure, and understandable manner. To govern the data firstly it is required to frame the mission with clear goals, governance matrices, execution procedures, as well as performance measures. Then, the data is required to review for making decisions. Finally, integration of information is essential to lead big data deployment to encounter issues and develop robust business values.
Building information distribution culture
The importance of big data analytical implementation is to target the AIHW goals to foster the information transformation culture. This involves collection of data and delivery to address the challenges and develop policies to meet business achievements. This will improve data quality, accuracy, and prediction as well.
Training
CEO is responsible to understand, evaluate, and make the decisions accordingly. Thus, CEO needs to conduct training programs to use the outputs of big data effectively in order to interpret the results. In this manner, CEO of AIHW should arrange training for personnel to utilize big data analytics (Tamers, et. al., 2019).
Incorporation of Cloud Computing
To improve the cost as well as storage issues in AIHW, it will be a better solution to integrate cloud computing into big data analytics. This will make data-driven decisions more accurate, fast, and operable. CEO will also enable to visualize the organizational different information sets including different areas, expenditures, and factors. Thus, CEO can balance between protection of patient information and cost-effectiveness by integrating both these technologies.
Creating new business insights
New insights can be created using big data analytics By CEO which leads to updating the business functions that increase competitive advantages and productivity. The AIHW CEO will also allow leveraging the outputs such as alerting KPIs, reports, market opportunities, interactive visualization, and feasible ideas (Grover, et. al., 2018).
Other strategies that can be recommended in improving AIHW operations are-
Accessibility- CEO should understand the entire organizational operations and datasets so, that the database can be designed accordingly. Different information can be accessed separately which will help CEO to access, update, and make decisions more quickly.
Utilization- This is also an essential factor that utilization of any database should be done more attentively so, that the data can be interpreted in knowledge for business decisions.
Validation- Validation is another factor that ensures security so, CEO should focus on robust security system. This will help CEO to protect sensitive information of entire AIHW assets including patients, staff members, equipment, machines, details, records, etc. (Hsieh, et. al., 2019).
The main reasons for using the suggested solutions for achieving the strategic/operational objectives for AIHW CEO are-
• Cost-effectiveness
• Accurate decision-making strategies
• Automatic data processing (accessibility, update, delete, transformation)
• Rapid data delivery
• Robust integration
• High-level security
• Marketing & competitive advantages
Task5- Cover Letter
To,
XYZ
CEO
Australian Institute of Health & Welfare Agency,
Australia
Dear Mr. XYZ,
With overall description and analysis, the Australian Institute of health and welfare agency has specific goal to review the expenditure for financial years 1997 to 2012. To achieve this specific mission of AIHW, CEO should focus on leveraging their business operations using the in-depth analysis of their corresponding business datasets. According to the analysis, AIHW has been identified with higher expenditure values. This signifies that the revenue is also good but still, the increasing market structure and competitiveness, this is a possibility of higher expenditure but less revenue growth. In this manner, it is essential for CEO to take responsibility and enhance the scope of their business using strategic objectives. Some relevant recommendations are outlined in the following section that encourages
CEO to understand and apply the business objectives for better results specifically. These recommendations are-
To understand and develop big data strategic values
Big data analytics play a vital role in incorporating strategic business values so, CEO of AIHW can also lead these strategic values as shown in below figure-
.png)
Figure 8: Strategic Values of Big Data Analytics
(Source: Grover, et. al., 2018)
The functional value leads to financial performance, market share, and many more as it defines to improve the performance by adopting big data analytics. On the other hand, symbolic value refers to a broadly derived value via signaling effects of investment in big data analytics. Symbolic value comprises mitigation of environment load, organizational reputation, brand, and many more.
To strategically fit the business needs of AIHW, CEO should rely on functional value to balance organizational operations and technological awareness. In this manner, CEO will enable to ensure organizational business efficiency, coordination in operations and personnel, and decision-making features (Grover, et. al., 2018).
To implement innovative E-health record/system
CEO should take an initiative to develop an innovative e-health system to record the datasets and manage the organizational operations more effectively, accurately, securely, and flexibly. The CEO can use this system to conduct the business transparently and achieve business goals more quickly as multiple advantages can be leveraged for CEO including predictive data values, cost and smarter business decision-making capabilities, data storage, management, and improved outcomes as shown below-
.png)
Figure 9: E-Heath System
(Source: Dash, et. al., 2019)
References
ITECH3001 Evaluating a System Assignment Sample
Assignment objectives
• Investigate the techniques for evaluating systems as described in the literature
• Design and conduct usability evaluation for a chosen system
• Analyse and interpret the data and results from the evaluation
• Report on the results and recommend for improvement of the evaluated system
Details of written components
Assignment
You will select one of the websites from the list of charities provided on Moodle. The assignment involves conducting a usability test on that website, interpreting the results and writing recommendations in the form of a report on any changes needed. Your report should be presented clearly enough so that it will be ready to be submitted to the charity.
Each of the charities listed have requested a usability evaluation of their website. The written component of the assignment must be based on your ACTUAL usability test on REAL users and should contain the following:
• A discussion, based on the literature, of the different approaches for assessing or testing usability with more detail on the use of usability testing for evaluating systems or websites.
• A brief description of the website selected for the usability evaluation. This should include the purpose of the website, the audience and the objectives of the organisation with respect to their website as determined by the charity.
• For the usability test you must:
o Describe how the usability testing was conducted, and rationale for the approach. You may use the usability instrument provided on Moodle or a similar version (but improved version). The description should include a justification of the number of users, selection of users, the instrument you used for your test (the survey questions), the task you designed for the test etc.
o Design one practical scenario and test its usability
• A critical discussion of the method (good or useful aspects, difficult or poor aspects).
• A page to summarize and list your recommendations for changes to the website with supporting evidence. Think about what you think key personnel in the charity will want to know about how well their website is performing.
Your report must be written for scanning rather than for reading. Use dot lists, numbered lists, tables and levelled headings to organize your ideas and content as demonstrated in this document.To support your arguments, use screenshots, graphs and actual data from your test and cite references across your document.
Solution
Introduction
Usability Test
It is the technique of analysing the use of the service in the market. The organization releases a few features in the market to gather information about the user experience and analysis. It is essential to test the service before launching it in the market. It also includes analysing the requirements of the consumers in terms of features and management systems (Barnum, 2020). Moreover, it is important to understand the effectiveness of the service in the market and how much it is user-friendly. The entire procedure includes an analysis of the features required to be developed in the system, the features that are used mostly, and the features that are not required. The testing relies on feedback analysis of the customer. It is a long-term process and after the completion of the process, the organization finally launches the features into the market. Is procedure followed in terms of an agile project management system that improves the organization in terms of development and improvement?
Benefits
The implementation process benefits the organization in several ways, they are as follows:
• Product Validity
In terms of a better understanding of the market analysis and demands, the organization is required to follow an agile project management system and its implementation procedures. It helps the organization to analyze the needs of features in the market by liberating a few features. The entire process supports the organization in understanding the problems, needs, and demands of the consumer regarding the service or product. As it follows an agile project management system, it prefers feedback analysis for better implementation of the system. The feedback from the consumers helps the organization better understand the requirements. The feedback analysis procedure is followed in every stage of the implementation procedure. A better understanding of the problems and requirements can be evaluated through the process. Moreover, it results in better organizational development.
• Meeting the demand
Meeting the demand is the main aim of the organization. Due to the feedback analysis system, the organization is capable to understand the demands of the consumer. Due to the purpose, the organization can improve the implementation process significantly. The organization can be able to meet the demand by understanding the requirements and problems in their service. Through the procedure, the organization analyzes the customers’ expectations regarding the service. After a complete analysis, the company finally launches the website without any errors. It results in the accuracy and appropriateness of the system launched.
• Trouble identification
The customer accessibility to the website must be smooth. The system must be developed with appropriate features and a loading system. It must be easily accessible in terms to check and analyze the user accessibility. The developing team within the organization should focus on the customer’s user interface. The system handling must not be complex and the website prefers multitasking such as purchasing and donating. In this case, observing is essential to identify the user story. If any issue is discovered by the following system, it must be revised and recovered immediately.
• Appropriate analysis
The internal design of the website attracts the customer in terms of the appropriate arrangement of the features updated into the system. The analysis is based on the user handling such as the features that the customer is using the most and the features the customer is not using. From this point of view, the user analyzes why the customer is not using the features? It results in a better understanding of the system.
• Minimum source of error
As the organization follows the agile project management system, the organization has the least chance of causing errors. According to the feedback analysis, after feedback collection, the stakeholders of the organization set meetings for selecting the relevant ideas or feedback provided by the consumers. By following the ideas, the developer updates the features based on the customer’s requirements. Better implementation procedures and management systems are required for error minimization.
• Better understanding and development
Through the feedback analysis, the organization understands the demands of the market, the techniques to develop the system, and business procedures. Through the process, the organization also understands the effectiveness of the project management system. The organization analyzes the needs of the customers in terms of system development. In this way, the organization results in effective development through usability testing.
• Changes for improvement
After releasing a few features, the organization promotes feedback analysis. The change completely relies on the customer’s feedback such as updating new features and removal of the features that are not necessary. The development team requires focusing on the feedback of the customer and working accordingly. It results in better development and improvement of the system and management system.
• Efficient user experience and satisfaction
User experience and satisfaction are essential in terms of a usability test. It supports the company during the launch of the website; it results in smooth functioning of the system and is user-friendly.
Literature Review
Breast Cancer Network Australia
The organization is associated to promote support for people suffering from Breast cancer. The founder of Breast Cancer Network Australia is Lyn Swinburne that believes in serving humanity. It is a group of fewer people that connects women facing breast cancer. They are already connected with 70 % of Australian women battling breast cancer (O’Brien et al., 2020). The organization provides hope to maximum Australian families in terms of managing funds for treatment and positivity. Today, BCNA is known as the largest consumer organization for the last 22 years in terms of providing support to women who are diagnosed with breast cancer. At present, the organization has taken the initiative in terms of providing maximum facilities to families suffering from breast cancer (Beatty et al., 2021). To reach the destination, the organization needs innovative ideas and progressive thinking to increase the maximum funds of the organization and promote help to them.
To increase the maximum fund, the organization has introduced a website for easy funding for women diagnosed with breast cancer. it also facilitates the implementation procedure by providing a better understanding of the steps that must be taken by the women suffering from breast cancer. It provides several information and updates that are essential for people to know about breast cancer (Riihiaho, 2018). It provides a better innovation for a better management system. BCNA also provides a better understanding of the treatments best for women battling breast cancer. Moreover, they provide support to the patients by supplying facilities such as
• Quick access to the website
• Providing better tests and treatments.
• By lower the budget.
• By providing the best nurse and care facilities.
• By providing public health service
• Provides effective treatment for lymphodema.
• Better clinical practices
Different Approaches of Usability Testing
Common and General Usability Testing
It is the most common and moderate usability testing that is required to collect data in-depth and provides better information for best assignment help .
Lab Testing
In this case, lab testing is important in terms of analyzing the stage, issues, and problems of cancer. The testing period is conducted through mobile or website (Lyles et al., 2014). The stakeholders and the moderators of the organizations focus on the movements of the patient to analyze ad detect the complications.
Advantages
- Provides full observation of the patient's behavior
- Assurance for providing efficient service
Disadvantages
- Requires high expenses
- Consumers time
- Fewer people agree to do the test.
Guerilla Testing
The test is generally conducted in public places. It supports the organization in collecting bulk data in a shorter period. In this case, the procedure is not efficient enough to meet the organizational demand as most peoples are not curious about the result (Kendler, & Strochlic, 2015). Mostly, the person participates due to the purpose of collecting gift coupons.
Advantages
- Provides appropriate and free testing period
- Provide gift coupons
- Do not consume time
Disadvantages
- People do not have the time to collect the result.
Common and most used usability tests
In this case, the entire procedure works digitally and significantly. Interaction with the patients is meant to be possible through questions and query solving approaches.
Interviews via phones
The women suffering from breast cancer require appropriate counseling. The counseling period is generally conducted through phones. The modulators analyze the movements of the patients and focus on identifying their thinking and problems by promoting an appropriate discussion session (Wagner et al., 2020). It results in better understanding and data collection in a shorter period.
There are more approaches such as unmodified and remote and immoderate-in-person. In this case, unmodified and remote focuses on the insight performance of the website such as session recording and online testing tools (Lifford et al., 2019). on the other hand, the immoderate and in-person approach testing session is conducted by the participant itself but does not allow the moderator to involve. These approaches are also very significant in terms of better support provided by providing usability testing sessions to the patients.
Usability Evaluation
The steps of usability testing are inspection, testing, and inquiry. In this scenario, we are performing usability testing. The testing period is conducted mainly to detect the movements and behavior of the patients. Moreover, to identify the thinking and problems of the patient the testing session is conducted to promote support to them (Ginossar et al., 2017). On the other hand, it is also analyzed that it requires improvements in terms of strategic planning, visual analysis, and remote testing system.
The performance of the website can be evaluated by providing multiple questions. In this case, the answer if the finding must be appropriate and informative in terms of better understanding and evaluation. It will support the participants in finding the answer that is not present on the website so that handles the system accurately. Better stakeholder analysis and engagement are required for better system understanding and evaluation.
Purpose
• To promote better website accessibility and performance to the patients.
• To promote help in terms of usability testing to breast cancer patients.
• Provides effective counseling sessions.
• To improve the management system.
• To promote a better engagement between the modulator and patients.
• Results in effective testing analysis and understanding.
Objectives
• Better implementation procedure in terms of usability testing.
• To promote support and facilities for the women battling breast cancer.
Methodology
In this report, the particular methodology or process steps are followed to conduct the overall research or usability testing. However, the methodology was started by motivating the participants to buy the BCNA merchandise from the online portal. After that, they will conduct in detail testing of the products. The management team will prepare an appropriate discussion or seminar that can derive proper analysis and evaluation of the personal experiences (Maramba et al., 2019). The participants will also share their issues and the reasons that make the product more useful in a practical scenario. However, this overall discussion or evaluation will be documented in the company database that can further be implemented in organizational strategy and sustainability.
Participants’ Responsibilities
• Buying Projects and different categories of merchandise and products.
• Conduct in detail testing by using the products.
• Discussion with critical thinking and a flexible approach.
• Personal experience evaluation.
• Active engagement in group discussion.
Training of the Participants
All the participants required appropriate training modules and program designing to conduct the overall testing effectively. It is the responsibility of the management team to design the overall training structure for the organization (Li et al., 2012). This will include engaging seminars, online conferences, team projects, etc. In this way, the participants will be more effective in the overall testing procedure and documentation. Moreover, the test results will be implemented efficiently in a real-life scenario.
Procedure
The testing is the most significant and essential process of the overall report. In this case, the overall evaluation leads to two different procedures of testing. There are differences in nature, specification, and implementation (Lin et al., 2021). In this section of the report, both of those usability testing procedures are explained with potential results.
.png)
Table 1: Different Procedures of Usability Testing
(Source: Developed by Author)
Questioner System
A questionnaire system is a part of a remote usability testing procedure. This can also be conducted in the usability Lab testing. Despite that, it is the most efficient remote procedure. All the participants will be able to share their opinion and different evaluation along with personal experiences through the online portal system. This will also efficiently categorize and document them into the system. Moreover, the valuation and testing results will be effectively implemented by considering all the opinions of the participants.
.png)
.png)
.png)
.png)
.png)
Figure 1: Participant 5
Usability Matrix
Usability metrics are an analytical procedure for evaluating the overall testing procedure and results. In every organization, usability testing requires appropriate criteria and metrics for constant evaluation of the project progress (Maramba et al., 2019). In this section of the report, different usability metrics components will be discussed in terms of description and significance.
.png)
Table 2: Description and Significance of Usability Matrix
(Source: Developed by the Author)
Usability Goals
Usability goals present different objectives of the overall usability testing procedure. This is conducted to collect data and feedback from different participants (Tiong et al., 2016). However, these usability goals must be specific and tested by the management team for further organizational implementation. This includes,
• Error-free testing method and usability results
• Appropriate and effective operations
• Effective time management
• Efficient usability testing and operations
• Effective management structure and planning
It is the responsibility of the management team and participants to meet all the usability goals with active contribution and analysis.
Classification
Problem Sensitivity
Problem sensitivity presents the significant impact of the particular problem in any usability scenario. Appropriate classification will help in the identification of the severity of the problems in the procedure and overall results implementation process as well (Lo et al., 2018). In this section of the report, some of the problem categories are explained in terms of effective solution strategies.
.png)
Table 3: Description and Problem Sensitivity
(Source: Developed by the Author)
Observation
In this section of the Report, the overall observation of the whole usability testing procedure is discussed in terms of impact and organizational significance. This observation will be effective for the management team to develop appropriate planning and strategy for further improvement and implementation. This will lead to effective recommendations as well. The report or whole testing procedure includes problem analysis, participant analysis, testing procedure, and different framework evaluations. In that case, the observations are,
• The most effective and efficient system for this usability project will be a remote testing model
• The management team has already implemented effective teamwork and management
• Problem analysis has shown the appropriate strategies that can resolve different problem categories
• The participants are the key stakeholder in the overall process and evaluation.
This is the responsibility of the management team to evaluate or analyze all the documented observations to list the most effective recommendations for the project.
Conclusion and Recommendation
The report concludes that the overall usability of the system is already efficient enough to conduct real-life business implementation. Despite that, some of the system and strategic changes will improve the usability experience and other beneficial features. This will also require active observation and engagement of the participants and managerial stakeholders. However, the strategic implementation will effectively conduct the whole process in the assigned time frame.
The final observations and whole analysis can also lead to the most effective and applicable recommendations that must be documented and analyzed for further requirements. It includes,
• The management must improve the remote usability testing system
• The appropriate and effective participant training program must be designed
• The process must include regular feedback analysis into the system
• The appropriate and efficient team must be prepared to moderate and manage the system regularly
This requires effective leadership and analytical skills to implement these recommendations, which can lead to further organizational growth and sustainability in the market.
References
.png)
CSE2HUM Ethical Issue on Current Cyber Context Assignment Sample
In this assignment, you will be provided with two context briefs. You will be required to select one for your analysis and complete the tasks below (1 & 2). As much as possible, focus on the details provided in the brief. Where information is not provided but integral to your analysis, make reasonable assumptions (which should be clearly stated and explained). (Note: You must clearly specify the selected context brief in your report,
Risk Assessment Report
Objectives:
Identify and discuss at least three cyber security risks faced by the organization. Since the organizations are based in Australia, the discussion must identify;
1. Where these threats are most likely to originate (outside Australia and within)?
2. Who those threat actors might be?
3. What are the key drivers, or motivations behind those threats?
4. Do ideological, cultural, political, social, economic factors influence those motivations?
5. What kind of vulnerabilities they might exploit?
Please note as this is an important part: The course is “Human Factors in Cyber Security” , therefore you must relate the vulnerabilities to the concepts taught during week 3,4,5, and 6, including but not limited to; personality types, limitations of human cognition, types of learning – associative and non- associative, conditioning – operant and classical, Pierre Bourdieus theory of practice (capital; habitus; field; practice).
2. Cyber Security Awareness Plans
Objectives:
Once you have identified the risks in part one.
1. Describe detailed steps to counter those threats by designing a cyber security awareness plan.
2. The plan must contain a general cyber security awareness campaign for all the participants of the organization.
3. The plan must also identify awareness campaigns for specific groups of people with specific job roles (These are for people in the job roles that are either privy to important assets/data or manage key operations).
4. You must think and address the following aspects while designing the plan:
a. Tools, and mechanisms to ensure maximum impact?
b. Cultural, economic, social, ideological, or political factors which you think might impact the content and/or communications.
c. Can techniques such as personality type identification, conditioning (operant and classical), habitus, learning types (associative and non- associative), be used to deliver an effective plan?
d. Can ethnography be used for developing such plans?
Solution
Introduction
The following study will aim to identify three potential cyber security threats that might occur with the Australian-based hospital. A cyber security awareness plan will also be developed in order to address the identified threats.
Risk assessment report for assignment help -
Cyber security risks and origination of the risk
Malware attack: Attackers make use of different types of methods to input malware into a device and this is mainly done by social engineers (Gunduz and Das, 2020). In order to input malware into a device, the attacker might develop a link containing malware and as the operator of the device click on that link.
Denial-of-service: The main objective of a denial-of-service attack is mainly to overwhelm a target system’s resources and make its functions and operations stop and also deny access to the system to the user.
Password attacks: A hacker can obtain an individual's user credentials by monitoring the network connection, employing social engineering, guessing, or gaining access to a password database (Coventry and Branley, 2018). A hacker can 'predict' a password in a systematic or random manner.
The attack might originate within Australia and also outside Australia since most hackers do not require the actual system to hack it, they can also do it remotely.
Identification of threat actors
Lack of proper security: Cyber security risks often occur when there is a lack of security assurance (Happa, Glencross and Steed, 2019). People handling passwords and storing data in the hospital’s cloud system need to have the proper knowledge regarding how they can assure the security of the system and the files stored in the system. In the hospital, there are various patients who ask for passwords and one among them might have the skills to hack the system using the password.
Vulnerabilities in systems: Cybercriminals often hack systems that have a weak spot. It makes it easy for hackers to attack a system that has weak cyber security systems installed or when the cyber security system is out of date (Happa, Glencross and Steed, 2019). If the password of the operating system is weak, hackers can easily predict the password and attack the system. Hence, it is important to keep cyber security up to date.
Key motivations and drivers behind the threat
The hospital contains the data and information of many patients and hackers who want to hack the system might have a certain purpose in mind before hacking the system (King et al., 2018). Hacking the operating system of a hospital will provide a hacker with all the data regarding the patients and also the hacker will get access to raw data and information about the hospital. If the hacker has the motivation of leaking sensitive data regarding patients or the hospital, this might act as a key driver or motivator behind the attack.
Influencing factors in motivation
There is a huge cache that economic, political, social, ideologically and cultural factors might be one of the prime influencing factors behind the motivations. Hackers hacking the system might be culturally or ideologically influenced to do so. The influence of any political party or social group also might influence the hacker to attack the system (Nurse, 2018). Accessing data about the hospital and selling the data will also bring in some money which might be an economical factor behind the attack.
Potential vulnerabilities
The potential vulnerabilities referring to Bourdieu's theory of practice that might occur include the influence of habitus which indicates that individuals with their resources and nature react differently in different situations (Nurse, 2018). Bourdieu also talks about misrecognition as a potential vulnerability in this case.
Cyber security awareness plan
Modern society is much more technologically dependent than ever before, and numerous areas of our being, such as power, businesses, rule of law, security, and so on, are highly influenced by technology (Mashiane, Dlamini and Mahlangu, 2019). As a result, cyber security becomes critical for preventing the misuse of these sources of data and IT infrastructure.
The steps that will be included in the cyber security awareness plan of the hospital in order to address the threats that the organisation might face include:
- No employee of the hospital should click on any link before verifying its authenticity of the link.
- The password of the Wi-fi must be changed from time to time.
- The installed cyber security must be up-to-date (Zwilling et al., 2022).
- If any suspicious cyber activity is witnessed, it must be reported immediately.
- The networks used by the staff must be protected using well-developed cyber security since staff mainly input the data of patients.
- The desktop and iPads given to the doctors and nurses must be protected by strong passwords and the web activity must be checked from time to time.
- The cloud storage of the hospital also needs to be protected using well-developed cyber-security (Sabillon, 2018).
The behaviour modification theory can also be referred to for enhancing the knowledge of the employees of the hospital regarding cyber security. The behaviour modification theory will help in enhancing the behaviour and develop the actions of the employees and make them more aware regarding cuber security. If the entire workforce becomes more aware and alert regarding the importance of cyber security, the organisation will be able to achieve good outcomes with respect to cyber security.
The receptionists and other staff must have basic knowledge regarding cyber security so that they can identify and report any suspicious activity to the higher authority. The doctor and the nurses must keep their devices with them all the time in order to prevent the device from being stolen or used without consent (Hepfer and Powell, 2020). The staff involved with data entry must be well-aware of how to protect the data files so that the data can be prevented from being manipulated or stolen.
The tools and techniques that will be mostly included in this plan include the installation of antivirus software, firewall tools, penetration testing technique, packet sniffers and encryption tools. Conditioning, personality type identification, learning types and habitus techniques can also be used. Ethnography can be used to address economic, political, social, ideologically and cultural factors.
Conclusion
It can hence be concluded from the above study that the cyber security threats identified in the study might negatively affect the organisation and sensitive patient data and data of the hospital can be accessed by the hacker if there is an abuse of proper cyber security. The cyber security plan will be quite helpful in addressing the identified threats.
Reference list
.png)
COIT20256 Data Structure and Algorithms Assignment Sample
Objectives
In this assignment you will develop an application which uses inheritance, polymorphism, interfaces and exception handling. This assignment must be implemented:
1. incrementally according to the phases specified in this documentation. If you do not submit a complete working and tested phase you may not be awarded marks.
2. according to the design given in these specifications. Make sure your assignment corresponds to the class diagram and description of the methods and classes given in this document. You must use the interface and inheritance relationships specified in this document. You must implement all the public methods shown. Do not change the signature for the methods shown in the class diagram. Do not introduce additional public methods unless you have discussed this with the unit coordinator - they should not be required. You may introduce your own private methods if you need them. Make sure your trace statements display the data according to the format shown in the example trace statements. This will be important for markers checking your work.
3. Using the versions of the software and development tools specified in the unit profile and on the unit website.
Phase 1
Description
In phase 1, you are to simulate customer groups of two people arriving every two time units for 20 time units. The only event types that will be processed in this initial phase are Arrival Events. There will be no limit to the number of customers in the shop in this phase. However, this phase for assignment help will require you to set up most of the framework needed to develop the rest of the simulation. At the end of the phase 1 simulation you are to display all the customer groups currently in the shop and all the customer groups that have ever arrived at the shop (this will be a history/log of customers that could be used for future analysis). Given that leave events will not be implemented in this phase, the customer groups in the shop will correspond to the customer groups in the log/history.
Phase 2
In phase 2 we will now have the groups get their coffee order after they arrive. This will be achieved by introducing a new Event type (an OrderEvent) to be scheduled and processed. To do this we have to:
1. Add a serveOrder() method to the ShopModel class.
This method is to print out a message to indicate the time that the group involved has been given their coffee (i.e. print out the following message:
“t = time: Order served for Group groupId”
where the words in italics and bold are to be the actual group id and time. The signature for the serveOrder () method is: public void serveOrder(int time, CustomerGroup g)
2. Add an OrderEvent class
The OrderEvent extends the abstract Event class and must implement its own process() method.
The OrderEvent’s process() method must use the shop model’s serveOrder() method to get a coffee order filled for the group (i.e. print out the message). (In a later phase the process model will also schedule the “LeaveEvent” for the group.)
The OrderEvent must also have an instance variable that is a reference to the customer group associated with the order so that it knows which group is being served their coffee.
This means the signature for the OrderEvent’s constructor will be: public OrderEvent(int time, CustomerGroup group)
3. Have the ArrivalEvent’s process() method schedule the new OrderEvent one time unit after the group arrives
4. What should be output by the program at this point? Run and test it.
Phase 3
In phase 3 we will have people leave after they have finished their coffee. To achieve this, we need to:
1. Implement a leave() method in the shop model, which is to:
print a message when a group leaves the shop as follows:
“t = time: Group groupId leaves”
where the words in italics and bold are to be the actual group id and time remove the group from the ArrayList and decrement the number of groups (numGroups) in the shop.
2. Introduce a LeaveEvent class. The LeaveEvent class must:
Extend the abstract Event class
Have a reference to the “customer group” that is about to leave
Implement its own process() method which is to invoke the shop model’s leave method.
3. Have the OrderEvent schedule a LeaveEvent for the group 10 time units after they receive their coffee.
4. What should be output by the program at this point? Run and test it.
Phase 4
Now there are restrictions on the number of customers allowed in the shop. This will correspond to the number of seats made available in the shop. *** For the purpose of testing and to allow the markers to check your output, make the number of seats in the shop 8.
Extend the ShopModel class as follows:
1. Add a ShopModel constructor that has one parameter that is to be passed the number of seats available in the shop when the ShopModel object is created.
2. Include an instance variable in the ShopModel class that records the number of seats available.
The number of seats available is to be passed into the ShopModel constructor. (The UML diagram in Fig 2 now includes this constructor.)
3. When customers arrive in the shop, if there are enough seats available for all the people in the group, then they can enter the shop and get coffee (i.e. schedule an OrderEvent) as normal.
4. If there are sufficient seats to seat all members of the group, print a message as follows:
“t = time : Group groupId (number in group) seated”
where the words in italics and bold are to be the actual group id and time.
In that case, if new customers are seated, the number of seats available in the shop should be decremented. If there are insufficient seats for the group, then these customers cannot enter the shop. In that case, print a message saying: “t = time : Group groupId leaves as there are insufficient seats for the group”
where the words in italics and bold are to be the actual group id and time.
Assume that if there are insufficient seats the group just “goes away” (i.e. does not get added to the ArrayList of Customer Groups in the shop) and are considered lost business. They should still be recorded in the log/history.
Keep track of how many customers are lost business during the simulation and print that information as part of the statistics at the end of the simulation. In both cases (seated or not seated), the process method should schedule the next arrival.
5. Don’t forget to increase the number of seats available when a customer group leaves the shop.
6. At the end of the simulation, print the following statistics:
How many customers were served (requires an instance variable to track this)
How many customers were lost business (requires an instance variable to track this)
Display the groups still in the shop at the end of the simulation
Display the log/history of customer groups that “arrived” in the simulation.
Phase 6
In a simulation you do not normally use the same values for arrival times, times to be served etc. As explained earlier, in practice these values are normally selected from an appropriate statistical distribution. To model this type of variability we are going to use a simple random number generator in a second version of your program. Copy your version 1 program to Assignment1V2. Now add a random number generator to your abstract Event class as follows:static Random generator = new Random(1);//use a seed of 1 Note that we have seeded the random number generator with 1. This is to ensure that we will always generate the same output each time we run the code. This will help you to test your code more easily and will also allow the markers to check your work for this version of the program.
Your concrete event classes must now use this random number generator to:
1. Determine how long after an arrival before the OrderEvent is to be scheduled (values to be between 1 and 5 time units).
2. Determine the number of people in a group (to be between 1 and 4 people in a group).
3. Determine how long after getting their coffee the group stayed in the shop, i.e. how long after the OrderEvent before the LeaveEvent is to be scheduled to occur (values to be between 5 and 12 time units).
Questions
Regardless of which phase you have completed, Include the answers to the following questions in your report.
Question 1: Why does the random number generator in phase 6 need to be static?
Question 2: What is the default access modifier for an instance variable if we don’t specify an access modifier and what does it mean in terms of what other classes can access the instance variable?
Question 3: How could you restrict the instance variables in Event to only the subclasses of Event?
Solution
Instructions
A description of what is required in each section is shown in italics. Please remove all the instructions from your final report.
Description of the Program and Phase Completed
Phase 1 has been completed
In this phase we have define the all classes given in the class diagram.
Phase 2 has been completed
Added serveOrder method to ShopModal class and defined ServeEvent so that customer can get coffee served by stipulated time interval.
Phase 3 has been completed
In this phase we have define leave method in to shop modal class and defined a new LeaveEvent class to track the customer group leaving time
Phase 4 has been completed
We have fixed the total number of seats available at the shop in the beginning so that after arriving of each customer group we can see whether the customer group will got seat or leave the coffee house with out placing order
Phase 5 has been completed
Define the working of statistics file so that simulator can writhe the details of program as per given in the format.
Phase 6 has been completed
Created the random class instance into event class so that the automatic random number will be generated and tested the program accordingly.
Testing
Testing of scheduling of events
.png)
Testing of group of people in each customer group
.png)
Sample Output
Simulation trace to the standard output:
.png)
Statistics written to the statistics.txt file
.png)
.png)
Bugs and Limitations
Bugs
“No known bugs”
Limitations
I don’t think any limitations
Additional Future Work
We can add multithreading to simulate the same project
Answers to Questions
Question 1
The event class can use directly because we are unable to create object of abstract class.
Question 2
The default access modifier of any reference variable of class is called default. That reference variable can be access by anywhere within the same package with the help of object.
Question 3
We can use private access modifier so that it can be used in subclass but not with the help of object in anywhere of the program.
DATA4900 Innovation and Creativity in Business Analytics Assignment Sample
Assessment Description
- This assessment is to be done individually.
- Students are to write a 2,000-word report using on Complexity Science principles and AI in business and submit it as a Microsoft word file via the Turnitin portal at the end of week 9.
- You will receive marks for content, appropriate structure and referencing.
In this assessment, you will be writing an individual report that encourages you to be creative with business analytics, whilst also developing a response to brief containing a “wicked problem”, to be addressed using Complexity Science principles and Artificial Intelligence.
Assessment Instructions
This assessment is set in the year 2023. Assessment Title- Report: Complexity Science and AI. Imagine that you are an expert in complexity science and manage staff using artificial intelligence. Land in your area has become scarce, however the populations is ever growing. There’s a housing shortage and also evolving demand for many types of services, such as childcare centres, public parks, shops and recreation centres, and car parking. You have been asked to write a report on
1. how this issue can be viewed in terms of complexity science
2. how artificial intelligence can be used in urban planning, re-developing and design of facilities and infrastructure.
Your report should have
- an introduction (250 words)
- a section discussing urban planning and design in the context of complexity science (600 words)
- a section on the role of artificial intelligence in business (100)
- a section on how artificial intelligence is being used in urban planning and design (600 words)
- a section recommending how artificial intelligence can be used in conjunction with complexity science in the future for urban planning and design (250 words)
- a summary (200 words)
- At least ten references in Harvard format
Solution
Introduction
The world is rapidly changing with the increasing population and land scarcity. It is becoming a challenge for urban planners and developers to design and redevelop the infrastructure for the growing population. The traditional methods of urban planning are no longer sufficient to meet the growing demand for various services. In order to address this issue, complexity science and artificial intelligence (AI) are increasingly being used to design and develop urban infrastructure.
Complexity science is an interdisciplinary field of study that focuses on the analysis of complex systems, including social, ecological, and technological systems, and seeks to identify patterns, trends, and correlations among the different components of a system. By understanding these patterns, trends, and correlations, complexity science can help urban planners and developers to better understand the needs of the population and the environment and to plan and design urban infrastructure accordingly.
AI is an emerging technology that is being used in a variety of industries and fields, including urban planning and design. AI is a powerful tool that can be used to develop intelligent systems that can automate tasks and make decisions based on data. This can help urban planners and developers to identify the needs of the population and the environment and to develop urban infrastructure that meets these needs.
In this report, the use of complexity science and AI in urban planning and design will be discussed for assignment help. The report will also explore the role of AI in businesses. Further, recommendations will also be provided about how AI can be used in conjunction with complexity science in the future for urban planning and design.
Urban Planning and Design in the Context of Complexity Science
.png)
Figure 1 Urban Planning Life Cycle
(Source: Moreira 2020)
The global population is expected to exceed 8 billion by 2050, and rise to about 9.5 billion by 2100. It is projected that nearly 1.5 billion people will live in megacities by 2030, up from 500 million in 1990. As per the 2030 Population Reference Bureau, China and India will account for more than 50% of the global population growth and will continue to exert great influence on the global population and its urbanization patterns. Urbanization also brings with it concerns over infrastructure development and management. Urbanization-related issues such as housing, transportation, environmental pollution, congestion, and general urban congestion are affecting the quality of life, as well as causing social and economic distress. This becomes more acute in megacities with a population of more than 10 million and rapid growth, such as London, Shanghai, or Guangzhou.
Urban planning and design are often associated with a range of complex issues, such as the distribution of resources, the planning of natural resources and ecosystems, and the design of governance systems and institutions, and society. These problems require the application of a range of specialized knowledge in urban planning, such as biology, mathematics, economics, physics, and engineering. The complex factors and underlying processes that interact with each other to produce these factors require highly developed knowledge of complex systems, and the application of advanced mathematical methods, such as graph theory and complexity theory. As a result, planning and designing megacities involves a significant degree of complexity (Ai Ain't disruptive: Complexity Science is! 2019).
Complexity science is a study of complex systems and their behaviour, with the goal of understanding how different elements interact with each other and how these interactions can affect the overall functioning of a system (Artificial Intelligence and Smart Cities 2018). In the context of urban planning and design, complexity science can be used to model and understand the behaviour of different elements within a city, such as traffic patterns, population density, and the environment.
The concept of complexity science, or complex adaptive systems (CAS), is based on the idea that complex systems can be better understood by studying their smaller components, and understanding how they interact with each other. This type of science is particularly applicable to urban planning and design, as cities and towns are composed of many different components that must work together in order to create a functioning, livable environment.
Complexity science can be used to analyse the needs of the population and the environment and to create models that can be used to plan and design urban infrastructure. For example, complexity science can be used to analyse traffic patterns and identify areas of inefficiency in the existing urban environment. This can help to optimize traffic flow and reduce congestion. Complexity science can also be used to identify population density trends, as well as anticipate changes in population density over time. This can help urban planners to plan for the future population growth of a city (Relationality 2019).
Complexity science can also be used to identify patterns and trends in urban data, as well as understand the dynamics of urban systems (NERC Open Research 2019). For example, in order to create a livable city, planners must consider how different services, such as childcare centres, public parks, and shops, interact with each other and with the environment. If one service is poorly designed or sited, it can have a negative impact on the other services and the environment. Additionally, complexity science recognizes that urban planning and design is an ongoing process, as the needs of a city or town can change over time. In order to keep up with these changes, planners must be able to quickly adapt to new demands and find creative solutions.
The Role of Artificial Intelligence in Business
AI is a field of computer science that focuses on giving machines the ability to learn and make decisions (Sustainable smart cities 2017). AI has numerous applications in the business world, such as predicting customer behaviour, automating tasks, and optimising processes. AI can also be used to improve customer service, as machines can be programmed to respond to customer queries and provide recommendations. AI can also be used to analyse large amounts of data to generate insights and identify trends which can help in automating business processes such as customer segmentation, customer analytics, and marketing campaigns (Coe-Edp 2021). This can help businesses to develop more effective strategies for targeting customers and improving customer service.
How Artificial Intelligence is used in Urban Planning & Design Now
(Source: Sustainable smart cities 2017)
Artificial intelligence (AI) technologies are advancing rapidly, and smart city development is widely viewed as an area of technological convergence and innovation. AI-based systems can be used to analyse data, identify patterns, and make decisions quickly and accurately. This can help urban planners and developers to identify the needs of the population and the environment and to develop urban infrastructure that meets these needs.
AI has a number of potential applications in urban planning and design. AI can be used to simulate and optimize different aspects of urban planning, such as traffic patterns, population density, and the environment. AI can also be used to identify patterns in urban data, such as traffic flow, to create more efficient and effective urban designs. AI can also be used to develop predictive models of potential urban developments, and to identify areas of risk in urban development projects (Moreira 2020). In addition, AI can be used to automate urban analysis and modelling processes (AI in Urban Planning 2021). AI-based systems can be used to create detailed simulations of cities and analyze the impact of different interventions on the urban environment.
Artificial Intelligence is being used in various areas of urban planning, namely:
1. Green Land Planning
Green land planning is related to the management and protection of land resources for human use. In the study, the participants were asked to look at ways of making their city greener.
2. Traffic Management
Traffic management is basically planning ways that can help manage traffic congestion. These include things like identifying possible bottlenecks in the road network and other ways to make a better traffic plan for the future.
3. Sustainability Planning
Sustainability is something that looks at the role that humans can play in making a city sustainable in a sustainable way. The study involved looking at how artificial intelligence can be used in helping planners develop a sustainable city.
4. Economic Determinism
This refers to the idea that an economic system drives all the changes in society. The study looked at how artificial intelligence can be used in improving the economic development in a city.
5. City Planning
This refers to the planning of where cities should go and the planning of the future of cities. The study looked at artificial intelligence applied to the planning of cities and other urban areas.
6. Smart City Design
This is related to the idea that urban areas can be made more efficient and safer using a mix of human and artificial intelligence. One of the advantages of a smart city design is that there's a greater integration between human and artificial intelligence to make sure that their work is more efficient (Yigitcanlar et al. 2020).
.png)
Figure 3 Smart Wastebin
(Source: Mahendra 2022)
AI can also be used to optimize the urban environment. By using AI-based systems, urban planners and designers can develop algorithms that can identify areas of inefficiency in the existing urban environment and suggest ways to optimize it. For instance, It has been observed urban areas often produce a lot of waste, making it hard to manage it efficiently. Fortunately, AI-based tools are available to help. There are cameras that can recognize the type of trash that has been thrown on the ground. Additionally, some waste bins have sensors that can tell when they are almost full, allowing authorities to only come and empty them when needed, saving money in the process (Mahendra 2022). AI can also be used to create virtual models of urban environments in order to simulate and test different interventions, such as changes to traffic flows or the introduction of new infrastructure and services (Artificial Intelligence in smart cities and urban mobility 2021). This could help urban planners to identify the most efficient and effective solutions for urban problems.
Recommendations for the Future
The use of Artificial Intelligence (AI) and complexity science in urban planning and design is likely to become increasingly relevant in the near future. AI can be used to identify patterns, trends, and relationships in the complexity of urban systems, helping to create more efficient and effective solutions tailored to the needs of the city's residents
Complexity science is the study of complex systems that involve the interaction of multiple components, often in nonlinear ways. By understanding the complexity of urban systems, it is possible to develop better solutions for urban planning and design. AI can be used to identify patterns and relationships in the complexity of urban systems and help to develop solutions that are tailored to the needs of the city's residents.
For example, AI can be used to analyze the mobility patterns of citizens and identify areas where public transportation is needed. This could be used to create more efficient and effective transportation networks within cities. AI could also be used to analyze the existing urban environment and provide insights into how to improve it, such as by creating green spaces and providing access to parks, playgrounds, and other recreation areas. In addition, AI can be used to identify areas of potential risk and provide solutions to mitigate these risks.
By investing in the infrastructure and training necessary to make use of AI and complexity science, cities can ensure that their citizens benefit from the most efficient and effective urban planning solutions.
This report explored the use of complexity science and artificial intelligence (AI) in urban planning and design. It discussed how complexity science can be used to analyse the needs of the population and the environment and to create models that can be used to plan and design urban infrastructure. It also explored the role of AI in businesses and how it can be used to automate tasks, analyse data, and optimise processes. Additionally, the report discussed how AI can be used in urban planning and design, such as green land planning, traffic management, sustainability planning, economic determinism, city planning, and smart city design. Finally, the report provided recommendations for the future, such as investing in infrastructure and training, creating public-private partnerships, and establishing ethical frameworks and guidelines. By making use of the advances in AI and complexity science, cities can ensure that their citizens benefit from efficient and effective urban planning solutions.
In conclusion, complexity science and AI are powerful tools that can be used to inform urban planning and design. By leveraging these technologies, cities can become more efficient and sustainable, and ensure that their citizens have access to the services and infrastructure they need. Additionally, cities should invest in the necessary infrastructure and training to make use of AI and complexity science. By investing in these technologies and taking the necessary steps, cities can ensure that their citizens benefit from efficient and effective urban planning solutions.
References
.png)
DBFN212 Database Fundamentals Assignment Sample
ASSESSMENT DESCRIPTION:
Students are required to write a Reflective Journal in which they reflect on unit content and learning experiences between weeks 1 and 11. In this assignment you should describe an interesting or important aspect of each week’s content/experiences, analyse this aspect of the week critically by incorporating and discussing academic or professional sources, and then discuss your personal learning outcomes.
The document structure is as follows (2500 words):
1. Title page
2. Introduction (~150 words)
a. Introduce the focus of the unit and the importance of the unit to your chosen professional area. Provide a preview of the main experiences and outcomes you discuss in the body of the assignment.
3. Body: Reflective paragraphs for each week from week 1 to week 11 (1 paragraph per week, ~200 words per paragraph). In each reflective paragraph:
a. DESCRIPTION (~50 words): Describe the week
- Generally, what was the focus of this week’s lecture and tutorial?
- What is one specific aspect of the week’s learning content that was interesting for you? (e.g. a theory, a task, a tool, a concept, a principle, a strategy, an experience etc.)? Describe it and explain why you chose to focus on it in this paragraph. (*Note: a lecture slide is not an acceptable choice, but an idea or concept on it is)
b. ANALYSIS (~75 words): Analyse one experience from the week
- Analyse the one specific aspect of the week you identified above.
- How did you feel or react when you experienced it? Explain.
- What do other academic publications or professional resources that you find in your own research say about this? (include at least 1 reliable academic or professional source from your own research). Critically analyse your experience in the context of these sources.
c. OUTCOMES (~75 words): Identify your own personal learning outcomes
- What have you learned about this aspect of the unit?
- What have you learned about yourself?
- What do you still need to learn or get better at?
- Do you have any questions that still need to be answered?
- How can you use this experience in the future when you become a professional?
4. Conclusion (~100 words): Summarise the most important learning outcomes you experienced in this unit and how you will apply them professionally or academically in the future.
5. Reference List
Your report must include:
- At least 10 references, 5 of which must be academic resources, 5 of which can be reliable, high-quality professional resources.
- Use Harvard referencing for any sources you use.
- Refer to the Academic Learning Support student guide on Reflective Writing and how to structure reflective paragraphs.
Solution
Introduction
A database management system is essential because it properly manages data and allows individuals to do a variety of tasks with ease. A database management system (DBMS) is a software application that stores, organizes and manages large amounts of data (Yunus et al. 2017, pp.192-194). The application of this technology enhances the efficiency of business operations while cutting overall costs. In this course, we learned about relational databases, SQL statements to extract information to meet business reporting demands, creating entity relationship diagrams (ERDs) to construct databases, and analysing table designs for unnecessary redundancy (Astrova 2009, pp. 415-424).
Hence, we mainly learn about the main aspects of Database Management Systems and alongside we will also get to know how the Databases are managed, built, their types and how they are integrated with different web services for best assignment help.
Week 1: Databases
The focus of this week was mainly on Database Systems. Out of all the topics discussed this week I mainly learned that a database is a structured data or information collection procedure which is typically stored digitally in a computing device. A database management system (DBMS) mainly consists of a database and its handling in particular. Through this learning process, I have analysed that DBMS are mainly the link between a user and a database as it allows a user to share and receive data, allows the user to view their data in an integrated manner, and provides efficient management of data. Though DBMS provides us with a lot of enhancements, it brings along elevated costs, complex management, and dependency on the vendors and much more. This week, I have learned that Databases hold a large amount of data for users and allow them to View and manage the data. I used to wonder how the data that we enter or see is being managed or stored. It is clear to me that DBMS manages everything related to data. I still need to learn how the data manipulation (Yunus et al. 2017, pp.192-194.) is being done and stored. In future, this would help me in understanding the basic concept of the data that is being managed by the businesses.
Week 2: Data Models
This week we have mainly targeted the Data models. Data models define how well the schematic representation of a database is portrayed. Models are fundamental components of a DBMS for adding abstractions. These models describe ways data is related to each other and how it is managed and kept within the system. The below analysis can be made that to manage data as a resource, data modelling methods and approaches are used to represent information in a standard, stable, and precinct manner. The data modelling (Liyanage 2017, pp. 432-435) mainly deals with the building blocks like Entity, Relationships and Constraints. I have learnt through data models that data modelling may be done during many sorts of projects and at various stages of a project. Data models are iterative; there is no such thing as a definitive data model for all corporations or applications. It follows no free lunch theorem. The data models should preferably be saved in a repository so that they may be accessed, extended, and updated over time.
Week 3: Relational Database Model
This week’s main focus is on Relational Database. A relational database is an organized collection of data components connected by established connections. These objects are generally stored as a series of tables. In a database, a column maintains the actual value of an attribute and the rows represent a collection of links. A primary key is allocated to each item in a database, and entries from different tables can be connected via foreign keys. According to my analysis, when working with big, complicated datasets, relational databases are ideal. A relational database is a form of database that stores and makes data points that are connected available. Every row in a relational database is a transaction with a unique identifier known as the key. The table's columns include data attributes, and each record typically contains a value for each feature, making it simple to construct links between data points. This has taught me that a relational database (Astrova 2009, pp. 415-424) is a subtype of a database. It employs a framework that enables us to identify and access data in the database. I've also learned about relational databases, and how data in a relational database is structured into tables. Relational databases, as I have understood, eliminate data redundancy. To me, relational databases have been a completely new and interesting concept. I will incorporate it to enhance my work.
Week 4: ER Modelling
This week’s focus is on ER Modelling. Modelling of ER (or Entity-Relationship Modelling) are sometimes referred to as ERDs or ER Models. The ER model is a traditional and completely normalised relational schema that is utilised in many OLTP systems. Typically, these applications do query tiny units of information at a time, such as a customer record, an order record, or a shipping record. I have mainly focused on and found that Entity Relationship Modelling (ER Modelling) (Weilbach et al. 2021, pp. 228-238) is a graphical method which helps in representing real-world objects. It also resolves the difficulties in developing a database is that designers, developers, and end users all have different perspectives on data and its application. A combination of attributes characterizes an entity and values can be assigned to entity properties. During this process, I discovered that one of the pitfalls while developing an efficient database comes from the fact that designers, developers, and end-users all have different visualisations and necessities of data (Schulz et al. 2020, pp.150-169). Developers will find it simple to use, manage, and maintain. I have learned a new way to generalize database entity structure. I will surely incorporate this technique to make thing more professional in future.
Week 5: Advanced Data Modelling
This week we mainly discussed Advanced Data Modelling. It refers to data patterns that enable users to rapidly discover and effectively evaluate complicated cross-enterprise data-focused business rules and validate complex requirements. Techniques for generalisation and abstraction allow for flexible data structures that can adapt to quickly changing business norms and needs. I have analysed and suggested the five data model dimensions as the most important (Liyanage 2017, pp. 432-435).Clarity implies the ability of the Data Model to be comprehended by those who look at it. Flexibility means a model's capacity to adapt without having a significant influence on our code. Performance describes performance advantages solely based on how we represent the data. Productivity implies a model that is simple to work with without wasting a lot of time. Lastly, Traceability means information that is essential to the system as well as data that is valuable to our consumers. As a result, I've learned that the Data Model of each programme is its heart. In essence, it's all about data: data enters via the user's computer or from an external source, data is processed according to certain business rules, and data is eventually displayed to the user (or external apps) in some convenient manner. In future I would need this Data Model knowledge as every component of DBMS relies on data to make sense of the entire system.
Week 6: Normalisation
This week's focus is on Normalization. The act of structuring database tables in such a way that the outcomes of utilising the database are always clear and as intended is known as database Normalisation. It has the potential to duplicate data inside the database and frequently leads in the development of new tables. According to My Analysis, for many years, database normalisation has been an important element of the database developer's arsenal due to its capacity to minimise or decrease replication while increasing data integrity (Sahatqija et. al. 2018, pp. 0216-0221). The relational approach developed during a time when corporate records were primarily kept on paper. Other reasons have also contributed to the challenge to database normalization's supremacy. Hence, I have mainly learned that Normalization helps in reducing Data redundancy and for my future work, Normalization will play a very important role. Normalization is among the most significant features of Database Management Systems that I have studied about. If data is updated, removed, or entered, it does not affect database tables and helps to enhance the integrity and performance of relational tables. Some believe that normalisation will improve performance. It avoids data abnormalities. Hence I have mainly learned that Normalization helps in reducing Data redundancy and for my future work, Normalization will play a very important role.
Week 7: SQL
This week, we will be learning about SQL. For excellent purposes, database systems and SQL are immensely prevalent in the industry. SQL, as a language, enables you to query these databases effectively. SQL is a declaratory language of programming, which implies that when we write SQL code, we understand what it is doing but not how it works. In Analysis, though SQL is often used by software programmers, it is also popular among data analysts for several reasons (Taipalus 2019, pp.160-166). It's simple to grasp and learn from a semantic standpoint, analysts do not have to copy data into other programs since they can access enormous volumes of data immediately where it is kept and when compared to spreadsheet technologies, SQL data analysis is simple to audit and reproduce. I didn't believe SQL would be beneficial for my day-to-day job as a graduate student researching computational cognitive neuroscience when I initially learned about it. I realised that because SQL is so widely used in the industry, I would also have to study it, but I had no intention of using SQL as a student. After thinking about how SQL could be utilized in my profession a little more, I discovered that attempting to create and handle relational databases may be quite valuable in my job.
Week 8: More SQL
SQL is a strong language because it operates entirely behind the scenes, allowing it to query databases with extraordinary performance. Because it is a sequence of instructions, if one is acquainted with imperative programming languages (for example, Python), he/ she will consider it quite straightforward to learn. Again, with SQL, organisations of people committed to understanding how and whento effectively search databases have gone through the process for us and developed our techniques to query databases. With SQL, we simply tell the machine whatever we want to be accomplished (Astrova 2009, pp. 415-424). Analyzing this week’s learnings, SQL mainly focuses on three areas. Data Definition Language(DDL) encompasses starting a Database Model, Creating a Table, Identifying Database Schema and Defining data Types.Data Manipulation Language (DML) involves tasks to insert Rows to a table, Delete Rows From table, Update data in table, Select(View) data from table, Rollback changes on a table, Commit(save) data from a table (Taipalus 2019, pp.160-166).Procedural language extensions to SQL(PL/SQL) create Procedures and batch processes to handle bulk query statements in the form of Code. Hence, this week I learned about SQL and how it is implemented. I have also learned about DDL, DML and PL/SQL and their importance in SQL and DBMS.
Week 9: Database Design
Focus of this week has been Database Design. Database design is vital for developing scalable, elevated applications. Everything else is simply a minor detail. If a database is well-designed, pieces of relevant material are immediately filed and details may be extracted as needed. There is endless diversity under that simple notion. Small actions made early on have a large cumulative influence. After Analysis, there are few factors to consider, and some of the most important (at least in the beginning) for me is to question what is the 'appearance' of the data that can be retained? How is it divided into logical entities, and how many of those entities are expected to exist throughout time? How will the information be used? Is it primarily transaction (OLTP) or primarily used to generate analytical views (OLAP)?Is there any redundancy that may (fairly) be avoided, or anything that should be considered to avoid this in the future? Are there any potentially huge or complicated links (Santosa et al. 2020, p. 012179) that may need particular consideration? I've discovered that the generic aim of database design is to create logical and physical modelling techniques for the suggested database system. To explain, the logical model is largely focused on data needs, and judgments whereas the physical database modelling approach involves a conversion of the database's logical design model by maintaining control over physical media through the use of hardware resources and software systems such as DBMS. I would really be using database design as a key learning for my future.
Week 10: Transaction and Concurrency
This week’s focus is on transactions and concurrency, Database concepts such as transactions and concurrency management techniques are frequently encountered in real-world scenarios (Yu et al. 2018, pp.192-194). Concurrency control is the management of many transactions that are running at the same time. A transaction is a set of activities, generally read and write operations, which is carried out from beginning to end to access and update multiple data elements. In analysis, concurrency control isolates each transaction while it is completed, allowing data to stay consistent long after the transaction has ended, which is very important in multi-user systems. Concurrency control is essential for preventing this. A good transaction has the ACID (Atomicity, Consistency, Isolation, Durability) properties. After being exposed to SQL databases, I got curious about the fundamental ideas that describe how databases work, which prompted me to research transactions and concurrency control. Before starting new transactions on the same object, one transaction should finish its cycle. However, there are drawbacks to this method, such as poor resource use and general inefficiency. This is going to help me while implementing transactions and concurrency in my future work.
Week 11: Database and Web
Today’s topic is on Databases and Web. An intermediate application server or gateway in between Web application and the DBMS is necessary for a Web server to obtain information from a database (DBMS). CGI is the abbreviation for the most widely used Web server interface. A Web server gets a URL, corresponds to a CGI resource, launches a CGI programme, connects to the DBMS, searches the database, and produces the result to the Web server. I have analysed today's learning and found out that web database apps can be free or cost money, generally in the form of monthly subscriptions. Almost any device may access the information. Web database programmes are typically accompanied by their technical support team (Zhao 2022, pp. 1053-1057). They enable users to update information, so all we need to do is design basic web forms. Databases are a commonly utilised technology in the corporate sector, and their importance, attractiveness, and profitability have already expanded. I feel that connecting middleware or the user interface to the application's back-end database still needs a lot of research. There are certain technologies available that connect the user interface to the database at the backend. Some systems consist primarily of a front-end integrated with several levels of middleware and database back-ends.
Conclusion
In Conclusion, I have learned that DBMS mainly manages the Data to/From a user. Data management becomes increasingly complicated as applications become more sophisticated. File-based solutions are inextricably linked to the initial implementation specifications and are exceedingly difficult to redefine and update. It is useful for any coder since practically every application will have to persist its data to a database at some time. With the help of other features like Normalization, Data Modelling ER Modelling etc. we can easily enhance the performance of DBMS by reducing Data redundancy, Scalability and flexibility of the managed data making it more reliable and efficient to use. In this entire learning process, I have learned how data management is done and how we can store and manipulate data without any complexity.
References
.png)
ICT80008 Professional Issues in IT Assignment Sample
Assignment Brief
Purpose or Overview
Your task in Assignment 1 is to write a Briefing Paper on ONE of the following topics. Note that you can look at an aspect of one of the following topics if you so wish. For example you may look at machine learning as an aspect of AI, take a deep dive into the ACS’s professional code of conduct as an aspect of the first topic etc. If you are unsure that what you want to look is a viable aspect of a topic, speak to the unit convenor:
- Professional Codes of Conduct for ICT professionals
- Privacy or Surveillance or Uberveillance
- Cybercrime or Cybersecurity
- Emerging Technologies
- Diversity in the IT Workplace
- Green IT
- Artificial Intelligence (AI)
- Technology 4 Good
- A topic of YOUR choosing to be agreed with your Convenor.
Note that several topics could well be researched from a technical or from an application/societal context perspective. In this unit, it is not appropriate to take the technical perspective, except where technical issues impact on the application of the technology in context. For example, if your topic is ‘AI’, you should focus on how organisations use or are impacted by AI, what are the key issues and challenges faced by ICT professionals, where the impediments to using the technology are (legal, regulatory), etc., rather than on the detailed hardware and software technologies needed to implement the technology.
In essence, a literature review identifies, evaluates, and synthesises the relevant literature within a particular field of research. It illuminates how knowledge has evolved within the field, highlighting what has already been done, what is generally accepted, what is emerging and what is the current state of thinking on the topic
Submission Requirements
- Assessments must be submitted via the Canvas unit site through the Turnitin submission link.
- Do NOT email the assessment to your Convenor or tutor unless requested to do so.
- Keep a backup of your submission. If your assessment goes astray, whether your fault or ours, you will be required to reproduce it.
- The assessment should be in one single Microsoft Word document and as a general guide, should be written in 12-point font size and should use 1.5-line spacing between each line.
- Pages of the assessment should have footers which include your name, student ID, unit code, and assessment title and page numbers.
- It is expected that all work submitted, will have been edited for spelling, grammar and clarity.
- Standard procedure is that assessments will be marked up to the specified word count only.
- The word count does not include the reference list and/or appendices
Solution
Introduction
The use of the information technology has increased in the recentyears but the professional issues in IT has also increased. The IT operations are increased so the issues related to cyber-attacks, threats and security have the major concerned so Green IT aims to minimizes the negative impacts of those IT operations with the practice of environmentally sustainable computing. In this paper, the major focus will be made on Green IT, issues andchallenges faced by the professionals in Green IT and how the Green computing helps in creating the sustainable environment(Bai, et al., 2017).ICT professional’s faces many issues related to ethical or socio technical so they need regulatory obligations, codes of conduct and proper standards for the effective work life balance.
Literature review
Green IT
Green Technology is the important practice in IT as it is the study of the environmentally sustainable computing which believes in creating the environmentally friendly products which have low negative impact on IT operations. Green IT are used by the organizations these days so reduce the human impacts on the natural environment. ICT professional uses the scienceand technology for saving the cost and energy, improving the culture, reducing the environmental waste and their impacts, etc.(Kansal and Chana, 2012). The main motive behind the use of Green Computing is that it helps in maximizing the energy efficiency, reducing the use of the hazardous materials, promoting the biodegradability of the products of the outdated and unused things, etc.
The concept of Green IT has emerged in the year 1992 which helps the organization in saving the money and also improving the energyefficiency. The major relationship of Green IT is with green networking, virtualization, green cloud computing, green washing, redesigning of data centers, etc.(Anthony Jr, 2020).The pattern of green IT includes server virtualization, data centers, energy efficient hardware’s and monitoring systems.All the products related to the IT technology such as manufacturing, designing, disposing, operating products, etc. are made of the green IT practices so that greenhouse gas emissions can be reduced by the professionals for best assignment help.
Why organizations use Green IT
In the recent years, the use of the Green IT has increased among the organizations as it helps in reducing the maxim sing the energyefficiency, reducing the use of the hazardous materialsandalso helps in promoting the products of biodegradability(Dalvi-Esfahani, et al., 2020).The strength of Green computing are reducing the energy usages from the green techniques which helps in reduction of the fossil fuels, lowering the emission of the carbon dioxide and also helps in conserving the resources so IT professional use such technology.
The IT professional also uses the Green IT as they have strength which includesecofriendly, environmental responsible and also use the resources and computers in the effective manner(Molla, et al., 2008).One of the biggest example is that green computing has done simple practices where the computers shut down when it has not been used so it helps in saving the energy and reducing the waste of energy. The green computing techniques are so effective it adjust the power settings which consumes less energy while operating the functions of the computers.
According to the (Dezdar, 2017), Green computing are also used so that less usage of energy can be used, produced and even disposed of the products. IT professionals use to run and compute the software on the regular basis so green computing helps in saving the money, energy resources and also give more efficient results in turning of the monitor, adjusting the brightness, leaving the printer off, turn off peripherals and even don’t use the screen saver. It has also been stated by the author that the major goal of green computing in the companies is to attain the economic viability by improving the computer devices with energy efficient manners, sustainable production practices and even with the recycling procedures.
Challenges faced by the professionals in Green IT
As per the author, there are several issues and problems in Green IT such as lack of expertise, competition priorities, misaligned incentives, need an expert of IT energy efficiency, etc. Green computing weakness has determined by the author such as disposal of electronic wastes, power consuming, educating the stakeholders with the return on investments, new optimization techniques are required and even the energy requirements are higher.
The IT Professionals need higher cost for implementing this. In the long term it is cost effective but for the short term, it is quite expensive so it was one of the major issue. There are manyorganizations who has refrain the green computing and switch to other technologies as there is high upfront cost. The IT professionalsalso need high knowledge and education to implement this and there is lack of IT knowledge experts in the companies so it created the issue (Zheng, 2014).There are many other issues are also found with the green computing such as adaption, performance, maintenance, security leaks, system support, etc. which creates challenges for the IT professionals. As per the reports, to produce the desktop computer it takes about 1.8 tons of the chemicals which produces fossil fuels. There are billions of PCs sold over the year so green computing are required to reduce the impact of carbon emission, fossil fuel and even to save the energy consumption (Bai, et al., 2017).
Impact of Green IT on the work of ICT professional
According to the(Chuang and Huang, 2018), the major impact of Green IT on the work of ICT professional users is to save the energy opportunitiesand even conserve the energy by installing the computers with low energy devices. One of the greatest example of such device is energy efficient logo which helps in adjusting the behavior to save the energy. Green ICT has the great impact on the working professional as they can save the sufficient energy cost and helps in reducing the impacts of the carbon emissions (Jenkin, et al., 2011).The professionals used to adopt the modern IT systems which reduces the greenhouse impact from the environment.
There is no gaps in the research has been found as such but this green IT requires huge investment so small and medium companies could not afford this easily. The human life is in the trouble as the e-wastes are increased and environment is getting affected badly which is also one of the major research gap.
The brand reputation of the companies also get enhancedwhich used to adopt the green computing system as it helps in reducing, reusing and recycling the environmental impact and helps in saving the cost andenergy consumption. Green IT also created environmental sustainability which not only improved the culture of ICT professional but also helps in retention and customer attractions.
There is also the certification of “Green IT Professional” which are offered globally by IFGICT. The professional who have such certification or course then it helps in doing the management and designing of IT infrastructure and system more effectively and even created great impact on the work as the professional (Bai, et al., 2017).Green IT professional courseandcertification also gets higher salaries so they get high level of motivation to associate with ecofriendly products and also conserves the energy.
Regulations behind Green IT
The regulations and the standards of green IT is based on the computing of environmentalsustainability so green IT services should be recur in the IT departments (Jenkin, et al., 2011).According to the law of the public procurements, the public authorities are allowed to demand the IT providers for using the technology and products which are energy efficient. The law of Green IT has to be establish by the large organization’s and considered as voluntary for long time as it focused on the legal framework on energy efficiency of IT products. There are many legal bodies which give the right to the public procurement to demand sustainable development and market mechanism using the eco criteria (Mishra, et al., 2014).
There are variety off technologies which has been introduced in the recentyearsso the laws and regulations put the major focus on green IT andsustainability measures which helps in detecting, mitigating and suppression the hazardous environmentalimpactsand also helps in setting up the requirements for manufacturing, designing and the sale of energy related products.
Conclusion
From the above discussion, it was concluded that Green IT has created the great impact on the environmentsustainabilityand development as it helps in saving the energy consumption with the effective use of IT products. It was also analyzed that Green IT reduces the negative impact of IT operations and helps in saving the cost and energy consumption. Green IT should be adopted by the IT professional in the work but there are certain issues andchallenges while implemented this which has stated above. The major issues and challenges are related to high cost, lack of guidance and knowledge, maintenance, security leaks, system support, etc. The major goal of green computing is to attain the economic viability by improving the computer devices with energy efficient manners, sustainable production practices and even with the recycling procedures.
References
.png)
COIT20250 Emerging Technologies in E-business Assignment Sample
Corematic Engineering is an engineering consultancy company providing an externalised research and development (R&D) service. According to the organisation’s website, Corematic Engineering provides R&D services to businesses that want to de-risk innovation and automate their operations, keeping full control of their IP.
As per the Corematic’s website, “in 2018, Scott Hansen and Jonathan Legault established Corematic Engineering with the vision of bringing a different R&D approach to the Australian business landscape with savoir-faire and strong knowledge focusing on an agnostic approach to technology. Happy clients equal a successful business - this success story of two senior industry leaders who live and breathe client success led Corematic to reach two million dollars in two years.” As a self-funded company, they are fully funded by their customers - not investors, subsidies, or government grants. Corematic has offices in Brisbane and Bundaberg, both cities located in Queensland.
Corematic website states “bringing a proven engineering process that combines state-of-the-art R&D practices with a return-on-investment approach, Corematic’s new-generation mechatronics engineer tailor solutions in robotics, artificial intelligence, computer vision, and machine learning to empower businesses to lead Industry 4.0.” In particular, they specialise in vision, vision system, 3D camera, LiDAR, Industry 4.0, Internet of Things (IoT), Smart Factory, Intelligent Technology, Artificial Intelligence (AI), Sensor, Monitoring Platform, Proximity warning system, Anti- collision system, innovation, and automation.
“At Corematic, we never push a particular technology or brand. We are unbiased in our role as consultants, presenting options and giving clients the freedom and control to choose what they want to do.” Scott Hansen & Jonathan Legault, Founders of Corematic. Even though, the field of expertise of Corematic Engineering revolves around robotics, computer vision and machine learning, they also specialise in lean manufacturing and business improvement by placing long term consultants with their clients. Corematic applies a Lean Six Sigma Approach to analyse the current processes for both operation and business, define a performance baseline, and identify opportunities for improvement before proposing and implementing innovative solutions. To leverage this expertise, Corematic uses and resells one of the best business process mapping tools available on the market: PRIME BPM. Corematic is also mapping processes and defining procedures for its own internal activities with an ISO9001 certification in mind. Corematic also runs a Digital Marketing Agency specialising in B2B activities, preferably in engineering where marketing is relatively unexplored.
According to their website, “Corematic Engineering is now referred to as a disruptor in the robotic and business intelligence industry, providing turnkey solutions for complex problems that made black box solutions obsolete.” Because of their establishment in robotics and automation, they have been awarded referrals to different organisations including their award for Harvester.
Mounted Vision System ‘TallyOp’ that allows farmers to optimise efficiency and boost yield performance to simplify and enhance farm management decisions through detailed insight.
“Corematic Engineering’s expertise in robotics, artificial vision, and machine learning has been applied to multiple projects, revolutionising the power of business intelligence in the Australian landscape.” Corematic has worked on multiple projects with many esteemed leaders in the Australian agriculture, smelting and pharmaceutical industries so far!
Please Note: Corematic Engineering official website (https://corematic.com.au) was the main source to prepare this Case Study with minimal change in order to protect the original information provided by the organisation. The Case Study provides a short business story about Corematic Engineering, however accessing their website and other internal/external sources for more detailed information about this organisation is necessary to complete the assessment as required.
WHAT YOU ARE EXPECTED TO DO :
Pretend that you have been appointed as an Emerging Technologies consultant by Corematic
Engineering (https://corematic.com.au) to advise them on their next e-business strategic direction (2023-2027) in terms of adopting emerging technologies in their current and other potential business operations. This is because Corematic Engineering would like to expand their businesses nationally and internationally in the next 1-5 years and become one of the most advanced technology consultancy companies in Australia, and build a national and global brand name. Furthermore, they recently realised that they are facing fierce competitive pressure from a number of national and international companies as well. Corematic’s business has been growing significantly since their establishment in 2018, however they fear that they cannot sustain this growth after the next few years unless they take some serious action, invest in variety of emerging technologies, and expand their business operation fields (in addition to what they have and do currently). They think the solution could be using appropriate emerging technologies effectively in their many business fields and operations. To help them achieve this, first you will need to read all the information given to you about this case study including accessing the Corematic Engineering website and other relevant sources to understand the organisation’s business, growth strategies, operations, and processes better.
You then need to read the Assessment-3 details to find out how you can help Corematic Engineering business by advising about emerging technologies to allow them to achieve their business strategic goals and provide much better and diversified products and services, not only on a national scale, but also to become a truly international company, build a global brand name, and gain and sustain competitive advantages in their business operations. When you are suggesting appropriate emerging technologies for your chosen three e-business use cases of Corematic Engineering, apply your innovative thinking, imagination, long visionary skills, and e-business knowledge and experience in an effective way.
Each of you will analyse a given case study and identify the issues arising from the case study. Based on the issues found in the case study, you will identify three e-business use cases (for example, Predictive Maintenance). You will then choose as many emerging technologies as appropriate to address those use cases. You can choose any emerging technologies that fit the use cases, even the ones not covered in the lectures.
You will write a report illustrating how the chosen emerging technologies would fit into and address the requirements of the identified e-business use cases.
In the main body of the report, you will include the following topics.
1. A list of identified three e-business use cases and chosen emerging technologies including a brief background study of those emerging technologies. You need to first list identified three e-business use cases and chosen emerging technologies to address those use cases (as per the given Case Study) then describe how the chosen emerging technologies evolved, their underlying designs, working principles, functions, and capabilities (in general).
2. A brief description of the future potentials of the chosen emerging technologies. You need to discuss the future applications of the chosen emerging technologies in e-business in general.
3. An illustration of how the chosen emerging technologies would fit into the identified e-business use cases
You need to illustrate what issues of the identified use cases would be resolved by the chosen emerging technologies as per the given Case Study.
4. Details of how the chosen emerging technologies would address the requirements of the identified use cases
You need to elaborate how the chosen emerging technologies would interoperate to fulfill the requirements of the identified use cases as per the given Case Study.
Solution
Introduction
The company of Corematic Engineering offers an externalised research and development (R&D) service. As per Corematic Engineering's website it has been discovered that the respective company is offering R&D service to companies that are looking to automate and re-disk Innovation while maintaining total control of their business as well as their IP. It has been found from the case study that the respective company is aiming for creating a different R&D approach within the Australian business market landscape. The services of the company mainly centre around various robotic technologies such as AI and IoT. It has been visible in the provided case study for assignment help that the respective company is trying to expand their business internationally. However, they found a barrier to competitiveness. So, the management department of the respective company needs some specialized solutions for improving its business strategy internationally. The respective study is going to discuss the essential technologies that the company should adopt to grow their international market.
Identifying three use cases and chosen emerging technologies
Predictive maintenance is one of the important use cases of e-business that has been identified. Going with the view of Carvalho et al. (2019), predictive maintenance can be termed as a design that helps in monitoring tools along with techniques. With the help of Monitoring the tools as well as techniques, predictive maintenance plays a vital role in monitoring the structural performance of the company. Based on the view of Nasution et al. (2020), this case can be used by the companies to determine the issues within their structural performance. There are five major technologies that the company can adopt to improve their predictive maintenance. The technologies are PdM Tools and Technology, Vibration analysis, Ultrasonic analysis, Oil analysis techniques and Motor circuit analysis. These are some of the essential technologies that can be used by the Corematic Engineering company to increase its business strategy within the international market. Based on the view of Rong et al. (2018), it can be stated that these technologies can help a company effectively maintain its business fields as well as operations. These technologies can help a company in allowing their safety compliance. As per the view of Gouda et al. (2020), these predictive technologies are mainly used for a variety of tasks, including establishing credit risk models, managing resources as well as anticipating inventory. These technologies in predictive maintenance support businesses in lowering risks, streamlining processes, and boosting earnings.
Aside from predictive maintenance, Sales-Profitability & Demand Forecasting is another important case. Based on the view of Bhimani et al. (2019), sales profitability helps in keeping an accurate map of the profit status of an industry. In other words, it can be stated that this case is mainly used for measuring the sales dollar of a company to map their profits after maintaining all of the costs along with taxes. The sales profitability of a company can be identified by performing a subtraction between total revenue and total expenses. According to the view of Lei et al. (2021), demand forecasting helps in predicting future customers as well as future demands. Few technologies can be used by a company to maintain sales profitability and demand forecasting. The technologies are big data analysis, Cloud storage technology, Internet of things or IoT. These technologies are highly associated with the development of Sales-Profitability & Demand Forecasting. These technologies can help a company in identifying its net profit. Aside from this, the pre-mentioned technologies can be also used in determining the future of an industry.
Besides all of this, trend Identification to Drive the Pricing & Promotion Plan can be termed as one of the major cases that have been used by the e-business. Based on the view of Bhimani et al. (2019), a trend can refer to the overall direction of a market. Trend identification can help a business identify how the business is performing in a market. This also helps in finding various issues related to the business. The trend identification process of comparing the business data with marketing trends. Going with the view of Huang et al. (2019), four important technologies are highly associated with the development of trend Identification to Drive the Pricing & Promotion Plan. The technologies are Machine learning, 3D printing, computing power, smarter devices and datafication. This technology plays a vital role in analysing the service and supply demand of a product on a market.
Describing future potential and application of the chosen emerging technologies
Technology is growing at an intense level. As per the view of Biswal and Gouda (2020), good technology can prove to be a boon to a company. The Corematics Engineering company must adopt the latest technologies so that it can lead itself ahead of any other technological consultancies present in the market. To perform predictive maintenance the use of PdM tools and techniques is very much essential to identify the risks, assess the data from core to core and predict if there are any flaws or not. It does not only reduce the time of the experts but also the costs get reduced. The company can rely on this technique to perform quality-based work that can assure high-quality results. The Corematics Engineering implementation of predictive maintenance can take the company to a whole new level. Apart from that, the application of big data analysis and cloud storage can help in increasing sales profitability and demand forecasting. The future of these technological advancements can not only take the company to another level but create a global name worldwide. The profit could be calculated and the demand of the customers could be identified very easily. The demands can be met by the company very easily and the company can earn good profits through that. The future of these technologies is very crucial and their implementation can bring a revolution in the e-business market. The Corematics Engineering consultancy company can prove to sustain in its future activities if the business of the company goes at par with the technological advancement going on everywhere and between a lot of companies that are trying to create a revolution in the e-business industry.
As far as going with the trend is concerned any company that does not understand the dynamics of the market generally suffers a lot in future. The potential e-business company must adhere to the latest smart computing techniques, 3D printing, smarter devices and machine learning so that it can fix proper pricing and bring a revolution in the market. The implementation of these technologies can help Corematics Engineering to maintain a proper e-business as well as earn profitability without any hesitation and gain a strong competitive advantage over any other company on a global scale.
Application of the chosen emerging technologies in the identified use cases
Cinematic engineering being one of the reputed engineering consultancies has been facing a lot of issues that need to be resolved. As mentioned by Lei et al. (2021), the advancement of technology can help an organisation in improving its activities and achieve heights. Similarly, as far as Corematic Engineering is concerned it must adhere to the latest technologies to sustain its business as well as its operations for the later future. Even if the idea of predictive maintenance has improved downtime and decreased long-term expenses since its inception, it still leaves open the chance of those unforeseen surprises and the cost of downtime that goes along with them. This situation was real because the mechanic's skills, intuition, and experience were all that were relied upon to keep the machine operating at its best. The preventive component of the maintenance programme was also left to the mechanic's "fingers crossed" optimism. Therefore, Corematic Engineering must adapt to using PdM tools and techniques for predictive maintenance. As stated by Ran et al. (2019), the idea of conditions-based predictive maintenance aims to close the gap between the limitations of relying on human experience and intuition for repair and the capacity to not only prevent failure but also predict it and optimize maintenance and repair to reduce time and cost. It can be of vital essence to the company to sustain its business and the application of the various PdM tools and techniques can be used to do proper predictive maintenance. According to Sony et al. (2020), the application of AI is an essential ingredient that has the power to not only change the business reality but take the company to the next level. Not only can it satisfy the goals of the company but also develop the latest in-hand facilities that can give quick solutions to harder tasks or problems. Being an R&D company, Corematics Engineering aims to solve the issues of competition that are developing in the market and that can be sorted with the implementation of the latest AI facilities. Sales profitability and demand forecasting play an important role in an organisation. The application of big data analysis, IoT and Cloud storage can help benefit organisations at a huge level. The ascertainment of net profit could be made with the execution of these advanced mechanisms. Finding the right data for execution at the right time becomes very much easy with the application of AI that builds a friendly tech-savvy atmosphere. Lastly, building a promotion plan and pricing through trend identification is of essential need by an e-business company like the Corematics Engineering company. The application of machine learning, 3D printing, smarter devices, and computing power can help the company in locating the trend and fix the promotion and pricing. Corematics Engineering must adhere to these innovative techniques.
Application of the chosen emerging technologies in addressing the requirements of the identified use cases
Emerging digital technologies can help the Corematic Engineering company in spreading its business within an international range. It has been assumed that after adopting the technologies the company would be able to solve the arising business-related issues. Aside from this, the selected technologies can also help the company in identifying the essential requirements of the pre-mentioned identified cases. There are almost twelve digital technologies have been identified in the previous sections of the respective study. Therefore, it can be stated that adopting the identified technologies may help the R&D organisation in spreading their business within w worldwide range.
PdM Tools and Technology:
This technology plays a vital role in monitoring the predictive maintenance of the industry. In other words, it can be stated that this technology plays an important role in addressing the case of predictive maintenance. As it has been found in the case study the respective company is trying to spread their business internationally. Based on the view of Rashid et al. (2019), before conducting any business in an international market it is important to have proper maintenance of the tools and techniques. This respective technology mainly helps in maintaining the pre-mentioned factor and increasing the capacity of the business. Thus, this technology helps in identifying the requirement of the identified use cases.
Vibration analysis:
Aside from the pre-mentioned technology, vibration analysis is another important technology that plays an important role in monitoring predictive maintenance. It can be stated that the technology is mainly used for maintaining machines. It can be assumed that with the help of this technology the respective industry can identify the issues within their machines. To spread the business within a new market it is essential to identify the potential failures. In other words, it can be described that it helps in increasing the safety levels of the employees.
Ultrasonic analysis:
Along with the pre-mentioned technologies, Ultrasonic analysis also plays a vital role in developing the maintenance of monitoring predictivity. Going with the view of Yang et al. (2020), ultrasonic analysis of a product is mainly done for detecting the flaws and issues of the product. Detecting the flaws and issues provide a chance of finding a perfect solution to solve the problems. With the help of this technology, the respective company can investigate how sound waves move through the materials under test, allowing us to find significant faults. This will also help the company in examining the potential of ultrasonic analysis as a condition monitoring tool and a preventive maintenance technique throughout this paper.
Oil analysis techniques:
Oil analysis techniques are an important technique that helps in analysing the oil volume within a machine. Based on the view of Hanga et al. (2019), Oil analysis is a routine analysis that helps in analysing the level and the health of oil within a machine. Understanding the coordination of the oil can be termed as one of the major reasons behind performing oil analysis. With the help of this oil, analysis is the respective R&D company can be able to read as well as check the data on the machine type. Thus, this technique of oil analysis can help in identifying the requirement of the identified use cases.
Motor circuit analysis:
Motor circuit analysis can be termed another important part of predictive maintenance. Along with the pre-mentioned technologies, motor circuit analysis techniques also play a vital role in analysing the machines and the production system within an industry. Based on the view of Choudhary et al. (2019), motor circuit analysis is a method that helps in identifying the health condition of a motor. The respective company has been suggested to adopt this technology to understand the health of their electronic motor circuits. In this way, this technology can help in addressing the requirements of the case of predictive maintenance.
Big data analysis:
The pre-mentioned technologies are for addressing predictive maintenance, whereas this technology helps in addressing the requirements of the case of Sales-Profitability & Demand Forecasting. Based on the view of Mikalef et al. (2020), big data analysis can be defined as a complex process. This complex is used in identifying necessary information within a huge amount of data. It has been suggested to the respective company to adopt the technology of big data analysis. This will help the company in spreading its business internationally. Along with this, big data analysis can help the organisation in analysing data for making data-driven decisions. Eventually, it will lead to improving business-related outcomes.
Cloud storage technology:
Along with the previous technology, cloud storage technology also plays an important role in addressing the requirements of the Sales-Profitability & Demand Forecasting case. Going with the view of Gur (2018), cloud storage technology is not only safe as well as secure but also it is budget-friendly. Corematic Engineering can easily adopt this technology to increase the growth of the business. Using cloud storage technology can provide the access to companies to view their files from anywhere with the help of an internet connection.
Internet of things or IoT:
IoT is another vital technology that has been used in addressing the requirements of the Sales-Profitability & Demand Forecasting case. Based on the view of Alam et al. (2021), IoT is all about using sensors, devices, gateways, and platforms to improve business processes and solutions. With the help of this technology, the respective company would be able to gather data efficiently for improving the capacity of the business. Moreover, IoT can help in increasing the connectivity between the stakeholders of the company.
Machine learning:
Machine learning technologies can be termed as a bunch of AI or compute learning technologies. Based on the view of Hair et al. (2021), machine learning plays a vital role in identifying customer behaviour as well as the patterns of business operations. It can be assumed that with the help of technology the respective company can identify the situation of the company within a market. Which eventually can provide a greater opportunity of understanding the needs of the business as well as customer needs.
3D printing
Along with the pre-mentioned technologies, 3D printing can be termed as another important technology that helps in addressing the requirements of the trend Identification To Drive The Pricing & Promotion Plan case. Based on the view of Rong et al. (2018), 3D printing can help a business by having a 3D look at their plans and projects. With the help of this technology, the respective company would be able to manufacture perfect products.
Adoption of Smarter devices:
With the help of smarter devices, the respective industry would be able to conduct an efficient management system of operations. Besides this, the respective technology can help the respective industry in receiving real-time data.
Conclusion
As studied in the report, it can clearly be stated that the Corematics Engineering consultancy company must adapt to its latest technologies. It is very much clear that to sustain itself in the market the company must implement new technological aspects that can benefit the company. As far as the long run is concerned, with the emergence of the latest technologies like the PdM tools and techniques, vibration analysis, motor circuit analysis, and ultrasonic analysis, the latest AI implementation in the business can help Coremetrics Engineering in flourishing in their business. With the three use cases as explained in the above report, it is very clear that every technology has its relevance and its adaptation can not only create a huge success but help the company grow in the long run. With the competition in the market being very high, the Corematics Engineering consultancy needs to rely on its technology and must continuously upgrade its internal activities so that the business does not perish as well as the customers do not complain about their work. As quoted by Roman-Belmonte et al. (2018), technology can bring revolution. Similarly, the Corematics Engineering consultancy with the proper execution of the latest technologies and creating a tech-savvy environment can prove to be a leader in the global market and establish itself as one of the main names internationally.
Reference
.png)
.png)
INF60007 Business Information System Assignment Sample
ASSIGNMENT TASK
1) Process Diagram
This assignment requires you to read the given Incident Management Procedures. From these procedures you are required to complete the partially completed swim lane process diagram.
Recommendation: Use the swim lane template (.ppt) provided on the third assignment page. This template includes the partially completed swim lane diagram – it will save you recreating the model.
2) Description of Incident Management Roles and Responsibilities
You are also required to derive a description of the roles and responsibilities for the following actors:
• Customer /End User,
• First Line Analyst,
• Incident Response Team Manager, and
• Incident Response Team.
This represents the written part of the assignment. You have up to 1000 words to complete this part of the assignment.
3) Critical Reflection on the Formalization of Organisational Processes
Based on your reading of the Incident Management process model (swim lane), answer the following question for assignment help: What is the motivation for organizations to formalize business processes for managing IT incidents?
Solution
1) Process Diagram
.png)
2) Description of Incident Management Roles and Responsibilities
2.1) Customer/ End User
End users or customers are responsible for protecting all kinds of information resources of an organisation that they can access. The role and responsibility of an end user according to incident management is to ensure non-computerized and computerised information security practices. The roles and responsibilities of an end user according to its management include the following:
• An end-user is responsible for understanding the participation in the BYOD program which is supposed to be voluntary and unless agreed to otherwise, it is their responsibility to assume carrier service cost, accessories, and devices (Hayes et al., 2021).
• End users are also responsible for maintaining the physical security of the information technology devices and also providing a high level of protection for sensitive information against unauthorized access. It is their responsibility to apply the TSC standards and make sure that the encryption is consistent with those standards that are required to be complied with for storing sensitive information.
• The responsibility of end users also extends to the appropriate protection of sensitive information that is transferred physically or electronically from unauthorized interception. It is also their role to enter appropriate encryption of sensitive information that is transmitted over public networks (Fuada, 2019).
• The end users have the role to consult with IT professionals to ensure that electronic information is properly disposed of in accordance with the guidelines and regulations provided in InfoSec 3.0.
2.2) First Line Analyst
The role and responsibility of a first-line analyst are to conduct investigations and resolve issues for users and is also responsible for the effective delivery of IT support services to external and internal customers. The role and responsibility of a first-line analyst are to gather facts, conduct research regarding issues, analyse and frame potential solutions for the problems and submit the information obtained to higher-level technical staff for further review. They also have the responsibility of assisting in the development and implementation of application systems and maintaining the establishment of applications using specifically defined procedures (Ahmad, 2018). Therefore, the first-line incident management analyst has the role and responsibilities in an IT organisation as follows:
• Accept or reject assigned incidents after reviewing them with precision.
• Conduct an investigation and identify the incident.
• Documents the entire incident resolution or workaround in the service management application to resolve it.
• The implementation of incident resolution which is an important activity is also the responsibility of the first line as an analyst.
• Verify the proper resolution of the incident identified and close the incident.
As a member of an IT team, the first-line analyst is responsible for solving organisational problems by analysing workflows, processes, and systems so that strong opportunities can be identified for automation or improvement of the IT processes within the organisation (Palilingan & Batmetan, 2018, February).
2.3) Incident Response Team Manager
The incident response team manager manages all technical aspects of incident response from the beginning to the end. He is also responsible for assessing the nature of the incident and determining what resources are required for the proper resolution and restoration of the service (Wolf et al., 2022). An incident response team manager will be supervising a team of IT professionals who in turn are responsible for attending to computer crimes, network intrusions, and cyberattacks. They also include direct involvement with security personnel as they are required to investigate security breaches and implement countermeasures for them. The responsibility of an incident Response team manager is to be proactive and carry out the following roles:
1. The incident manager should ensure that policies and processes are being followed with precision and that standard compliance is maintained so that best practices such as COBIT or ITIL are maintained. They require to identify gaps, assess data, inaccuracies, and trends so that actionable outcomes and opportunities can be identified (Son et al., 2020).
2. Since the incident manager is the front-line manager during incident management and requires to handle the incident or issue calmly and should have proficient working knowledge of how to resolve identified incidents and restore the business service.
3. Incident managers should use a systematic methodology to analyse, evaluate, design, and implement technology or processes to achieve measurable benefits for the business. They are required to make suitable recommendations based on recent arguments and have a clear idea of the problem or issue identified.
4. An incident management team manager should be a good communicator and problem solver because he is required to find a resolution to restore business functions and translate the messages for the entire incident response team so that they are able to carry out their individual in identifying and resolving the issue. Hence the responsibilities of an incident response team manager include being a good listener, critical thinker, and problem solver so that an incident is managed by him effectively and resolved with suitable methodologies and applications (Christensen & Madsen, 2020).
2.4) Incident Response Team
The role and responsibilities of an incident response team are to respond to different cyber security incidents or issues which include cyberattacks, data breaches, and system failure. This team is composed of different other roles and responsibilities which are delegated to other IT personnel who has specific skills. Therefore, the composition of an incident response team includes a team leader, team investigator, first-line analysts, researchers, communication liaison, and legal representatives. There can be three main types of incident response teams which are CERT (Computer Emergency Response Teams), CSIRT (Computer Security Incident Response Team), and SOC (Security Operations Centre) (Sarnovsky & Surma, 2018). The roles and responsibilities of the different incident response teams are discussed below:
1. CERT- They focus on partnerships with law enforcement, industry, and government for academic institutions. These professionals are responsible for prioritizing the development of threat intelligence and implementing best practices according to security responses.
2. CSIRT- This team has an assorted collection of IT professionals who are responsible for preventing, detecting, and responding to incident response cybersecurity incidents or events (Owen et al., 2018).
3. SOC- This incident management team covers a broad scope of the concept of cyber security and is responsible for directing incident response in addition to defending and monitoring systems, overseeing general operations, and configuring controls.
3) Critical Reflection on the Formalization of Organisational Processes
3.1) Types of Business Processes and How to Recognize Them
Since businesses are built on complicated interrelated processes and networks it is important to formalize the process so that the goals and objectives can be effectively managed and achieved. I think that incident management team managers should understand the different types of business processes and the unique roles they play in the overall business success so that they get the required motivation to undertake the process. In any organisation, business processes can be of three types, and the methods to recognize them are as follows:
• Core Processes: These are responsible for creating value for customers in a business and generating the required revenue. Also, core processes are sometimes known as primary processes because they consist of the main activities of the business organisation such as customer service, distribution, production, sales, and marketing. Common core business processes are structured processes that are managed by CRM, ERP, or vertical SaaS. Several businesses are implementing a system of engagement for optimizing the primary business processes and making them more efficient (Dorofee et al., 2018). Therefore, I think that core business processes should be formalized so that the structured process can be managed effectively and the IT functions of the business are carried out without any issues.
• Support Processes: Support processes are the activities that make it possible for the business functions to be carried out in contradiction to the core processes which provide value to customers and generate revenue. I think that support processes play a critical role in helping businesses to achieve the desired value and generate revenue by helping to carry out the business processes smoothly. I have also evaluated that the motivation during incident management regarding the support process is to service the internal customers in the organisation rather than the internal customers. I have also analysed that the formalization of business processes is to formalize the support processes with a department-specific SaaS platform.
• Long-tail Processes: These processes include the category of processes in process management strategies that are unique and emerge as a response to increasing stack complexities and evolving business needs (Cadena et al., 2020). I think that the motivation to formalize this business process is because it will help address a gap between apps, systems, or workflows.
3.2) Motivation of Business Formalization
It is important to formalize business functions because formalization comprises compliance with existing procedures and applying them to the business functions so that these functions are carried out according to the established standards and regulations required by legal laws and regulations (Bryant et al., 2019). I think that the formalization of business processes for managing it incidents can be a daunting task because it involves conformance to standards such as OSHAS 18001, ISO 14001, ISO 9001, and so on so that the documentation of the IT incidence is effective for the management system of the organisation. I have also analysed that the necessary documentation for proper incident management is quite complex and ranges between a variety of job descriptions and policies. Therefore, it is required to formalize business processes for managing IT incidents because important resources for employees when training new employees or implementing new systems can be smooth and effective (Mustapha et al., 2020). It is regarded that the formalization of business processes can be an effective tool for ensuring that all levels of the organisation are working efficiently to meet the organisational goals while managing incidents by identifying them and framing suitable solutions.
Often, I have regarded that the application of a business process modelling will help improve IT incident management as part of formalizing the business functions to manage IT incidents. Business processes should be formalized so that it is possible to communicate the business processes and procedures in a standardized manner and also understand the internal business processes with clarity. Whenever there is inadequate monitoring of incidents that prevents the proper mitigation or resolution of such issues, a formalized business process will help in better management and resolution of these escalations so that the business functions are restored. It is also possible to manage change within the organisation if the business processes are formalized and control automated for proper customization, documentation, monitoring, measurement, execution, and improvement of the business processes (Ray et al., 2020, April). I have analysed that at the global level organisations are required to formalize their processes so that IT incidents can be managed by individuals who are specialized in managing incidents by aligning themselves with the business objectives and goals. It is required to optimize the business processes so that incidents get better attention and IT professionals can increase user satisfaction through the normal functionality of a service.
The IT incident process management is generally operated by a user help desk that consists of technological and human resources with the primary objective of resolving the intimations of the service that require more attention. In large IT organisations, they have their own user help desk, for instance, SUNARP which is a public organisation in Peru has its own user help desk that is responsible for receiving different requests for user attention either through emails, in-person requests, or phone calls (Turell et al., 2020). Hence, I have evaluated that if the business processes are formalized for incident management, then it will prevent the organisation to become inefficient and prevent it from working in a disorderly manner by preventing users from communicating with the organisation and complaining that they have not been attended to yet. Through the formalization of organisational processes, it is also possible to reduce the wait time and a solution can be framed that is causing user dissatisfaction. Therefore, I think that it is important to have motivation for business formalization so that undefined procedures can be mitigated and limitations of available IT tools for managing incidents can be overcome by the incident response team.
References
.png)
.png)
ISYS6008 IT Entrepreneurship and Innovation Assignment Sample
Task description:
Your initial task in completing this report is to find a subject for your case study. that is either an entrepreneur or a corporation that uses emerging technologies such as robotics, drones, artificial intelligence (ai), machine learning, online media streaming, iot, real-time processing, rendering or applications, augmented reality (ar) virtual reality (vr) hardware or applications, etc.; and has successfully done one of the following:
- Started a new business, or
- Improved an existing organisation, or
- Had a global impact from using the emerging technologies. your next task is to evaluate his/her/its entrepreneurship journey and its relevance to what you learned so far from this unit’s contents and recommended reading and activities, and write a report which includes the following:
- An introductory paragraph to describe an entrepreneur (or corporation/business) and its associated products or services.
- A discussion on entrepreneurial mindsets applied in to establish the business.
- A discussion on how the business was initialised, including how the initial marketing and/or legal challenges were addressed. it is recommended that you search and include information about the capital sources used to grow the successful venture.
- A description of the latest capabilities of this business and how it has been used by people and its own and/or other companies to improve or transform their activities.
- Finally, provide a conclusion on whether you see any gap that can be addressed or if this case study has inspired you to think of a new idea. you should be concise in your report as you will be required to write no more than 1500 words.
Solution
Introduction
A brief description of the business and its products – Nike
The selected organization for the study is nike, it is a globally recognized brand for sneakers in the footwear industry. the brand was founded in the year 1964 by phil knight and bill bowerman, however, it was earlier recognized as blue ribbon sports. the brand established its first store in the year 1966 and after a 6years, it relaunched the company with a new name "nike". the key products of nike are casual and athletic footwear with sustainable manufacturing and designs, accessories, and apparel.
.png)
Figure 1: nike
(source: oyibotha, 2022)
Use of online media streaming at Nike
Being in the footwear industry, it was hard for nike to get global success and spread awareness of its name, products, and services all across the world. this is when online media streaming came into the role and nike adopted this service and further implemented it in its marketing strategy. Streaming media is referred to the audio or video content for assignment help sent in the compressed format on the internet and played by the users on several media streaming platforms, commonly on youtube. nike has an engaging channel presence on youtube which posts its new launches, products, services, and about r&d. that is how nike uses the online media streaming services to grow its brand reputation.
The entrepreneurial mindset of Nike
Name of the mind-set to be an entrepreneur, a strong entrepreneurial mindset is necessary. phil and bill both faced challenges at the initial level of their business start-up which is nike, however, they both fought that phase with a strong head. entrepreneur mindset refers to the mode of thought process which helps in achieving the desired success and goals. successful entrepreneurs have the capacity of embracing failures, challenges, and mistakes as new opportunities and develop new skills for their business success.
.png)
Figure 2: entrepreneurial mindset
(source: eli mindset 2021)
3 Key mindsets that nike follows are-
- A growth mindset: refers to believing that if the right amount of effort and time is put into learning and intelligence then a certain level of success leads to the continuous growth of business as well as personal development.
- Intrinsic motivation: refers to doing something for its own sake instead of greed for external rewards because intrinsic motivation thrives the idea generation and turns it into reality. this mindset involves a high level of engagement and psychological well-being (eli mindset 2021).
- Resiliency: it is referred to the ability to be recovered from challenges and issues quickly. entrepreneurs who are resilient in nature tend to pursue an explanatory style referring to a positive attitude to every situation.
Mind-set demonstration
There are two situations in which nike showed these three entrepreneurial mindsets. phil had an entirely different background from his study to professional life, however, his passion calling never stopped. in the 90s, he believed that sports shoes can be manufactured and sold at cheaper prices and compete with the japanese market, with this idea his crazy insanely flipped the market and revolutionized the sporting world. that's when he showed his intrinsic motivation and growth mindset.
further, in 1962, bill and phil were broke, inexperienced guys, and had no resources with a business idea, however, they refused to let the idea go and crazily presented his idea to the japanese managers supposing to turn the million-dollar american sports market (valuepenguin 2019). even after so many legal challenges, rejections, and setbacks, nike never lost faith and showed a resilience mindset.
Nike’s initialisation, marketing strategies, & legal challenges INITIALIZATION
.png)
Table 1: initialisation
Marketing strategies
- The very first marketing strategy of nike is selling its slogan “just do it” on its online platforms to connect with the world
- The compelling tagline for attracting the audiences
- Using the power of social media and collaborating with celebrities for marketing
- Empowering the targeted market such as women for social causes marketing
- Selling stories, not the product (pride, 2022).
.png)
Figure 3: instagram page of nike
(source: instagram 2022)
Legal Challenges
The key 5 legal challenges that nike faced due to its unethical actions are -
1. Racial discrimination- ahmer inam joined worked as senior director and claimed he faced racial discrimination as he was treated poorly as compared to his white teammates. this impacted his physical and mental health (young 2019).
2. Environment protection act- environmental pollution and use and discharge of toxic chemicals- in their production, nike was observed to use toxic chemicals in their development causing health issues and leading to the killing of sea animals. it is against the csr of the manufacturing industry and business.
3. Labour law act challenge- employed manual workers are very underpaid and are forced to work at low wages and long work hours, nike went against the labor protection act, not only that it employs child labor.
4. Copyright law challenge- the jumpman logo of nike brand jordan worth billion is copied, life magazine claimed that it is their true publishing that nike took and violated the copyright act (bain 2022).
5. Traded secrets- nike filed a 10million lawsuit against the three best designers of the company who broke the non-compete agreement and traded their designs with adidas and violated their privacy.
Capital resources
Capital plays an important role in the development of the business, however, nike makes huge amount of profit by itself that it does not worry about getting a loan from any bank and expect other companies to invest in it. yet, the key capital shareholders of nike are-
- philip knight- 0.9& class a and 2.6 class b shares
- mark parker- 0.09 shares
- andrew campion- 0.01% shares
- swoosh llc- 16.5%
- vanguard group- 7.0%
- blackrock- 5.9% (reiff 2022).
.png)
Figure 4: capital shares
(source: author 2022)
NIKE’S LATEST CAPABILITIES AND IT UTILISATION
CAPABILITIES
Nike has started to develop the eco-friendly and sustainable shoes through the use of the supergases technology. as the environment has started to get impacted in sever manner these days, which is why nike decided to initiate the sustainability program and also attract the new audiences to their brands. nike's corporate social responsibility and initiatives are largely focused on the company's fundamental idea that "sports have the capacity to impact the world for the better." nike leverages its sports prowess to fulfil csr goals in three key areas diversity and access, civic engagement, and environmental balance. nike fulfils their csr obligations by initiating these initiatives-
- Covid-19 response program
- Environment friendly branding
- Inclusion & diversity
- Community support programs
This capability of nike is considered in the r&d aspect of the brand.
.png)
Figure 5: figure 2: nike eco-friendly brand
(source: mahirova, 2021)
Example of company’s demonstration and succeeded in marketing
the idea of sustainable production and eco-friendly development has appealed a lot of people specially the younger generation. it is noticed that too many of the influencers who are very much active on social media platforms such as twitter, instagram, facebook, & youtube, who uses the online media streaming recognizing this capability of nike and approach the brand to collaborate with them (ravi 2018). this not only helped the brand to gain a huge recognition but also gave nike a new marketing strategy.
Nike started to make engaging videos and audio contents for its social media pages, as well as the collaborators having millions of followers also made the streaming content with the iconic slogan “just do it” and posted it on their accounts. this way nike not only got benefit and recognition of their new launches from their pages but also from the collaborators influencing the minds of billions of users just through one click. in short nike used the sustainability research and development as its leading marketing strategy.
.png)
Figure 6: twitter of nike
(source: ravi 2018)
CONCLUSION
The report demonstrated the online media streaming through the example of nike brand, being a sports brand nike had a few choices in the past era to promote their products. however, with the introduction of the social media marketing and streaming services, nike took advantage of it and promoted their products through engaging video and audio contents. the report has successfully analysed the emergence of new technology through discussion on entrepreneur mindsets, nike's marketing strategies and legal challenges, and it's capabilities through the demonstration.
Inspiration for a new idea the study has pushed entrepreneur mindset into the student and led to the new generation of ideas. as nike is a sports brand, and it has direct link with the health and fitness leading to the idea of introducing a fitness app with a health monitoring wearable device (band). this will create a new source of income into the company and also allow the company to put its leg into the information technology industry.
References
.png)
MITS5002 Software Engineering Methodology Assignment Sample
INSTRUCTIONS:
In this assessment students will work individually to develop Software Specification document. Carefully read the associated CASE STUDY for this assessment contained in the document MITS5002CaseStudy.pdf. From this Case Study you are to prepare the following:
1. Given the MITS5002CaseStudy.pdf, what SDLC Model would you use to develop the associated software. You will need to justify your answer. Outline the advantages and disadvantages your SDLC model would have over other SDLC models that could be utilized in developing the software.
2. Discuss the techniques from the case study that you would use to gather the requirements.
3. Develop a Specification Document based on the given case study. The document should have the following sections. However, you could add other topics based on your assumptions.
Your report must include a Title Page with the title of the assessment and your name and ID number. A contents page showing page numbers and titles of all major sections of the report. All Figures included must have captions and Figure numbers and be referenced within the document. Captions for figures placed below the figure, captions for tables placed above the table. Include a footer with the page number. Your report should use 1.5 spacing with a 12-point Times New Roman font. Include references where appropriate. Citation of sources is mandatory and must be in the IEEE style.
Solution
Introduction
In order to manage all the learning related activities and documents, XYZ company has decided to develop an e-learning platform. After a successful development and implementation of the, the platform will be able to perform a number of activities including course management, system administration, videoconferencing and collaboration. In this report, all the major aspects of the system development including scope identification, feasibility analysis, stakeholder identification, requirement specification, use case modelling and context modelling will be illustrated. Based on the company requirements, all the necessary documentations will be done in this paper. A comprehensive software engineering methodology will be conducted in this task. However, the use case and context models will be developed by using visio diagramming tool.
Technical discussion
SDLC
Within a software company, the SDLC is a method used for software projects. It comprises of a thorough plan outlining how to create, maintain, update, and modify or improve particular software. The life cycle outlines an approach for assignment help enhancing both the general process of creating software and the final product in terms of quality. In this task, the initial phase of SDLC will be illustrated including requirement gathering, use case modelling, context modelling, stakeholder identification and others [4]. Based on the planning phase of any software project, the complete project is conducted by the project team members. In this task, SDLC methods for e-learning platform building will be illustrated.
Requirement Gathering Strategy
In order to build a particular system, all the major requirements must be gathers in the planning phase. This task is about the development of e-learning platform by XYZ company. In the given case study, all the major requirements including functional, technical, or non-functional have been given. On the other hand, a brief qualitative research on the given problem context will also be conducted from different secondary sources [1]. In this context, few assumptions on the system development will also be done. After gathering all the major requirements, further planning will be conducted.
Specification document
a. Executive summary
In this task, a brief analysis on requirement specification of an e-learning platform development has been conducted. The system will be able to perform multiple activities including enrolment, course management, communication, data storage and others. There are five major modules will be available into the system including system admin, course management, collaboration and video conferencing, electronic register and anti-plagiarism. In this paper, all the major requirement of the system have been identified. Depending on the system requirements, few assumptions and feasibility study have been done.
b. Scope and feasibility analysis
Scope
Few scope for the system have been identified that are given in the below points:
- The system would to be able to establish user groups for collaboration, communication, and content sharing.
- Administrators can choose the look and feel of the websites for various campuses, as well as from a variety of graphical user interfaces.
- A opportunity to provide users alternative roles and permissions, as well as control access to diverse e-resources inside the system [2].
- Plagiarism checking could also be included for both the students and institutions on the platform.
Feasibility analysis
Feasibility analysis for the system has been conducted in terms of below aspects:
- Technical feasibility: Few new technologies for system development could be easily implemented by the developed team. JAVA, C++, DBMS, SQL, and many other techniques could be easily utilized [5].
- Operational feasibility: The goal of the project is quite clear. Therefore, the operational tasks and activities can be easily scheduled by the team members. However, a variety of operations could be done through this platform which is quite feasible.
- Legal feasibility: In terms of legal feasibility, all the necessary documents and papers can be developed by the project team members.
This system development project if quite feasible in terms of the above three aspects.
c. Stakeholders
In this section, all the major stakeholders of the e-learning platform have been identified in the below table:
In the above table, all the major stakeholders for this project have been identified.
d. Requirement specification
In this section, all the major requirements of the system have been discussed:
- Functional Requirements
1. Students should be able to access materials from other webpages using the interface.
2. Restrictions on disc space ought to be capable of being set by system administrators for particular individuals, organisations, and courses.
3. The system should enable for the posting of notices that are open to all students or by giving relevant individuals particular access permissions [3].
4. Accessibility of included tools for encouraging student involvement in the educational process, such as platform for developing and managing comment sections, podcasts, content sharing, and notebooks.
- Non-functional Requirements
1. Productivity increasing for both the students and employees of the institutions is a major non-functional requirement.
2. Up to a million active users must become able to access the system concurrently, and more options should be available.
3. It should be possible to reach the platform over the network using HTTP or https, and it should be distributed remotely on one or more machines [6].
4. For accessible and secured areas, it should feature an internet user and management interfaces.
5. To make it simpler for them to access and utilise, the system should be modified for those who have visual impairments.
- Others
1. An advanced learning environment should be available to the users.
2. All the users will be able to build a proper communication channel through the learning platform.
3. Future improvement must be enabled into the system.
e. Assumptions
In order to develop the system, few assumptions have been made that are given below:
- The system will be used by the students, teaching staffs, admin, university management, third party service providers.
- All the data and information of the system will be stored into the cloud based storage devices.
- In terms of security checking for new websites, automatic virus scanning facility will be included into the platform.
- The system will be cost effective for both the XYZ company and third party service providers.
f. Use cases
Diagram
.png)
(Source: Author)
In the above figure, the use case diagram of e-learning platform has been developed. All the major actors and use cases have been shown in the above figure [7].
Description of the use cases are given below:
Description
Description of each use case has been given in this section:
- Registration: Through this use case, users will be able to logged in into the system. Details of the users will be given during registration phase through this module.
- Course tracker: All the course related activities could be done by the users through this module. Submission of documents or marks checking could be done through this section.
- Interface: This is the main use case which will give access to each of the actors. The system admin will be able to manage each activities through this portal.
- Reward management: Students will be able to handle their financial rewards through this module. Any kind of fees or dues could be paid through the use case.
- Communication: In order to establish communication through video calling or messaging, this portal could be used by the users. By using their user name, students will be able to make communication with administration.
- Plagiarism Checker: In order to check similarity score of any assignment, both teaching staff and students will be able to use the plagiarism checker.
In this section, all the major description of use cases have been given. The system will be developed based on the users requirement and actors specification.
g. Context model
A context model gives the complete overview on the activities performed by the actors and system. All the necessary process and activities are identified in the context model. In this section, the context model of e-learning platform has been developed. This gives a brief description of each activities and operations performed into the learning platform.
.png)
Figure 2: Context modelling
(Source: Author)
In the above figure, a context diagram of e-learning platform has been created. All the major activities and process have been identified. Relation between different process and system has also been illustrated [8]. Based on the system requirement, this context diagram has been developed. A cloud based data storage devices has also been installed into the figure. Institute management and service providers will have direct access to the cloud based storage.
References
.png)
ISYS5003 Principles of UX Design Assignment Sample
Task Description:
Your task is to evaluate an existing augmented reality (AR) application and write a report demonstrating your understanding of UX concepts from the perspective of a developer in relation to your chosen AR application.
In your report, you should pay particular attention to the concepts learned in Modules 1 and 2 and how these might affect design choices. You should be concise in your report as you will be required to write approximately 500 words.
Solution
Introduction
A simple bunch of data that comes to life when is scanned through any of the smart device lenses or cameras gives the human psyche an endless horizon to chase. Many games in the modern world are the primary source from where the augmented reality concept is flourishing. Many technology giants for assignment help are prepping their infrastructure and investing more and more into this promising market also keeping in mind the importance of the data that comes from the user end also known as the user experience feedback which ultimately helps in enhancing the quality of the concept as polished, real and efficient as possible (Xiong et al., 2021).
Analysis and evaluation
Many companies in the gaming arena and the furniture business are turning their focus to the augmented reality technology since this helps in eliminating the need for a middleman. One such example can be taken as “Pokemon go” which is a real time game played by the users with the use of augmented reality. This boosted the implementation of AR idea onto a large scale. The UX i.e. the user experience enables the app developers to efficiently manage and enhance the quality of the product that they have created so as to attract more and more customers.
Principles and implementation
The gaming app Pokemon go used the principles of UX design when the data is being managed and manipulated such as the proper following of the Hicks law which tells that the measure of time that a customer or end user takes to make a decision is proportional to the corresponding level of the number of complexities of the choices they have (Bottani and Vignali, 2019).
The data set obtained through the large number of distinct users help the developers in generalising the process like what areas the so called Pokemon entities will the users find and how to remove errors through statistical analysis on a large scale so that the impact of errors on the individual level can be mitigated to a minimum. If the user is experiencing some kind of a problem in the interface then that data is collected and stored with all the other similar types of data set.
On the managerial level the company resolves the issues with the help and feedback of user experience. The user experience plays a very keen part in the app. When the users scan the geographical area in-front of them through a smartphone camera lens, a 3-D image of an entity called Pokemon appears on the screen which gives the information to the user and then the user has to take a real time decision and so on to continue in the game. An app that has such a high amount of customer query management needs to be updated with the newest data set at a very frequent rate since all the improvements for future references can only be done through the regular updating process (Han et al., 2018).
Conclusion
The customers or the end users are the key source of data which is needed to facilitate the quality of the environment and fulfil the requirements of the end users. The concept of augmented reality is based upon the very fact that the random data that is generated in an interval of seconds can be used for improving the results and experience at a very regular and short span of time so as to minimise the occurrence of errors and improve the accuracy of augmented reality for the customers and end users and make the everyday experience more efficient and at ease. Even technology giants around the world are now focusing on big data analysis which refers to the concept of handling big sets of data for research purposes and for improving the everyday interaction between users and technology efficient and easy. (Nguyen et al., 2021).
References
.png)
MIS603 Microservices Architecture Research Report Sample
Assessment Task
This research paper should be approximately 2500 words (+/- 10%) excluding cover page, references and appendix. In this assessment, you need to present the different issues that have been previously documented on the topic using a variety of research articles and industry examples. Please make sure your discussion matches the stated purpose of the report and include the cases study throughout. Discuss and support any conclusions that can be reached using the evidence provided by the research articles you have found. Details about the different industry cases studies should NOT be a standalone section of the paper.
Task Instructions (the scenario)
You suppose to work for your selected organization (in assessment 2) and have read reports of other organisations leveraging the MSA application in three areas (innovation, augmented reality and supply chain). Accordingly, you need to prepare a research report for management on how the MSA application can be used to deliver benefits in these areas as well as how and why organisational culture can influence the successful implementation of an MSA. Use at least 2 different case study examples for showing the benefits can be achieved by organisations.
The report should consist of the following structure:
A title page with subject code and name, assignment title, student’s name, student number, and lecturer’s name.
The introduction (250–300 words) that will also serve as your statement of purpose for the proposal—this means that you will tell the reader what you are going to cover in your proposal.
You will need to inform the reader of:
a) Your area of research and its context
b) The key elements you will be addressing
c) What the reader can expect to find in the body of the report
The body of the report (1900–2000 words) will need to focus on these three areas (innovation, augmented reality and supply chain) also organisational culture to develop your research paper. Particularly, you need to prepare a research report for management on how the MSA application can be used to deliver benefits in different organisational environments- cultures.
The conclusion (250–300 words) will summarise any findings or recommendations
Solution
Introduction
The study is going to introduce the underdosing of microservices that develop better business processes in Netflix. In this study, Netflix is considered in this proposal to present an implementation plan of MSA for the business processes. Netflix is the online Network platform that is presenting digital entertainment. For Assignment Help, It also increases productivity with developing the business processes. The study also demonstrated the important undressing of developing customer satisfaction and productivity. A different model of business also develops the innovation system of Netflix like the Subscription-based business model. Moreover, the real-life data also presents a better understanding of this business process with the development of the MSA.
The Proposal also focused on the development of the revolution and the transformation which involved developing the research properly. The use of MSA also helps for developing closer communication. The culture of the organization also interacts with the internal and external context. In this context, the MSA application helps to develop the entire study on a current business operation to develop the organization's growth. Moreover, the implantation of a data management system and the infrastructure of the cloud also develop future studies.
The area of the study also highlighted the important key elements which will also address proper research on the selection of an organization. Moreover, the global concept also recognizes that Netflix is a total entertainment company which is also demonstrated with the micro services of global media cloud-based streaming services. Netflix is also improving the technologies by developing machine learning, artificial intelligence and IoT. It is a software-based technology that also helps improve the performance of Netflix. Moreover, it is increasing the business capacity with developing the business productivity including the use of modern technology. On the other hand, Netflix is the storage management system that is exposed with open source on the data management.
Main body
Innovation
Reflecting the creation with innovation in business processes or business model
Subscription-based Business Model
Netflix also introduced a subscription-based business model which makes money with a different simple plan including basic standard and the premium. This plan is getting access to the streaming series, shows and movies (Kukkamallaet al. 2021). The company also gains profit from this plan that is slow with a positive cash flow with growth in the content of original production. The streaming content is also specialized with the entertainment of subscribers in July 2021 with 72 million users from the Canada and United States. Netflix has their own offices in Brazil, France, the United Kingdom, Japan and South Korea.
.png)
Figure 1: Subscription business model
(Source:Duggan nMurphy&Dabalsa, 2021)
It is the member of the motion association picture that is distributed and produces the content from different countries over glow. In order to think of this company, it was founded in 1997 by Marc Rudolph and Reed Hastings (Martinez, 2014). It is also known for providing our best services that are used by people for renting some movies which they wanted to see in DVD format. It is the service of the internet that is making a sure journey with the business model.
The business model develops with a profitable run with the original content of productivity by the organization of Netflix. These models also described that they are the subscribers who are also able for Internet services where the company rents the movies and the online shows. The subscription is the base that is incorporated with the company that is considered huge that is also helpful when it comes through the Netflix business model.
The work of Netflix business model
To define Netflix, it has been stated that it is the basic provider of content that is used online for properly developing online TV shows and movies along with some documentaries. Online streaming is the site that is an application that is mood applicable for the connection of devices (). So, it has been stated that it is providing a better service to the people with their needs.
Netflix also defines the business model as subscription-based which is the opposite of a generating model revenue in the specific level of title(DuggannMurphy&Dabalsa, 2021). The continent assets are likely produced and licensed with the review that has an operating segment on the circumstances. It is also indicating all changes with expected usefulness.
.png)
Figure 2: Netflix business model
(Source:Ulin,, 2013)
American media services are the provider as well as and production company where the business model of Netflix revolves with the subscription base of learning. It consists of online streaming with the library forms and the TV programs which are also included with the films and produced in the house (Ulin,, 2013). The user also has a surety about monthly subscription where the services are used by paying money e that is provided by the people with the name-based online process. What different content also provides online streaming with the site and access of clients that make a better platform.
Transformation of The Organization Internal Environments
The transformation of Netflix also developed the internal environment of organization business by modifying the business tools, strategy, policy, infrastructure structure and culture. They are the most relevant reasons also included with changing the organization technology, new market conditions and the customer demand (Hinssen,, 2015). Moreover, the organizational changes also enable the Netflix component to develop a scope in the digital platform. Thereafter the organization also embraced the technological changes to adjust the digital concept (Braun& Latham, 2012). The organizational changes also assist with the development company which is replacing the old system with new strategies to achieve a competitive advantage in the marketplace.
The Changes Example in Netflix
Netflix is an important example of the change of an organization that has the best scope in the new context. As an example, the Netflix organization also changed with real-life examples including changes in the business model of Lewin's (McDonald& Smith-Rowsey, 2016). The organization also changes with a different stage that is completing the whole process including the significant factors of culture, the environment and technology. It is also simulated with the organizational change including the new strategies in the current situation (De Oliveira, 2018). So, it is always proved that Netflix is the best example for an organization and change where the different software companies accept the organizational changes as Netflix to achieve all the competitive advantage.
Augmented Reality
Reflecting the superimposing images in the revolution of Netflix
Netflix has great goals to help the members with developing the context to enjoy the discovering. Personalization is the important pillar that allows Netflix to help each member with the different content views. The adapt has the best interest on the content which is present over time expands on this (Curtin,Holt &Sanson, 2014). Each kind of experience is personalized with the different dimensions where the videos have suggested the ranking. The videos are the way that the all-advanced work plays that have a unique address on the member's needs.
.png)
Figure 3: Revolution of Netflix
(Source: Stawski& Brown, 2019)
Personalization is the start with the homepage which is extended with the products beyond. It is keeping an informed engagement on the reality that is picking a growing form of development in the original content. Netflix also uses the multimedia mechanism in the learning and the recommended algorithm which has a running scale on the personalization. It presents better research on personalization with developing the all-continuous improvements of the online experiments (Stawski& Brown, 2019). The organization also works through all improvements in the development areas by looking through the new opportunities for making better-personalized experiences. Revolution is the best part for developing online context with improving the personalized homepage experiences.
Netflix also seeks the offering of TV shows and movies that also shows the relevant concept with joy. The artwork of personalization also represents each video where machine learning is the crucial piece. Including the new alignments of collaboration, natural and online. The movements also recognize the best concept with developing the best connectivity in the online processes. It is presenting a great watch on the development of online series and movies with proper opportunities.
The real object for developing the study
Search of Algorithm
Search leverages the combination of the processing of natural languages, machine learning, text analytics and collaborative filtering. It is the member of Netflix to discover a new connection between the textual queries and the titles of the catalogue (McDonald& Smith-Rowsey , 2016)It is also struck with simplicity with the Netflix members by minimizing all the numbers including the interactions of member needs for making a search interface.
.png)
Figure 4: Netflix algorithm
(Source:Springer, 2014)
Moreover, it is present a search interface to look for the algorithms which also handle the catalogue and queries to span with the languages including many countries. The search also develops with good coverage what each title and each query get the best shot (Springer, 2014). Whenever the little title appears with the member homepage, the search algorithm also ensures that every title has a chance to lead a play surface.
Marketing Personalization
It is the main site of the product interface where Netflix applies the personalization algorithm with many types of critical areas in order to provide a base experience to the member. Moreover, the different areas also provide the best future for the members to connect with the personalized algorithm (Ulin,2013). For achieving this Netflix also reaches the members with new recommendations with notification and emails. The delivery of a billion messages in a year also worked with a personalized algorithm. On the other hand, this algorithm aims to optimize the member's joy by creating a mind full volume on the messages. Additionally, it is invested with a heavy growth that is retaining the members with the base of programmatic advertising.
.png)
Figure 5: Marketing personalization
(Source: Weinman, 2015)
In order to promote the services in the original contract, Netflix also developed the budget system allocation algorithm which decides the advertisement. Both also determine the algorithm's delicate balance with the incremental and cost to reward (Weinman, 2015). Different types of machine learning algorithms as well as statistical techniques like natural networks, casual models and collaboration are also diverse with the set of a product and business. These business patterns also solve the business need and the complex product with the use of Netflix expertise.
Supply Chain
Effectiveness of MSA in Closer Communication
MSA also defines the experimental and the mathematical methods that determine a variation of the amount which exist with the measurement process. A variation in the development of the measurement process has directly contributed to the overall variability. So, MSA is also used for certifying the system of measurement with evaluating the development accuracy, stability and precision (FarmakiSpanou, & Christou,2021). Fortunately, they are the different adaptation of micro services also sharing all expertise that has an open spirit on the different sources. Netflix is the best example where the transition form of Netflix has a traditional model plan on the development of DVD rental applications.
It is the micro service architecture that is responsible with a small team to create an end-to-end development on the micro services. It is developing the communication with streaming the digital entertainment for millions of Netflix customers (López Jiménez&Ouariachi, 2021). Now the technology is fellow on the Cockcroft which is prominent for micro services as well as the architecture of cloud-native.
Effectiveness of MSA application in the benefits of organization environments and culture
The revolution of Netflix also presents an effective application of MSA that has benefited the organizational culture and the environment that is using radical data. At the same time, the Netflix business including innovating and old fashion is transport with the town-to-town country. The postal services of the governments in the oldest departments also apply with the rental distribution of video. It is presenting an innovative approach to the Netflix industry which is entirely based on a brick-and-mortar concept.
The balance between old fashion and innovation is the master of influence in the culture of organization Netflix. The necklace is successful in the evolution of pre-existing content elements which has a distribution on the medical advancement. Netflix also took a pre-existing DVD in the film as well as the television that also gives the customer a new way for receiving them with television all storytelling distribution method (Shaughnessy,, 2018). It is the part of an innovation that maintains the structure of pre-existing whenever it has a comprehension with the usability of different models.
Engagement and Interactivity Among the Important external or internal entities
The transition of multi challenge places an engagement and interactivity with the internal and external concept of Netflix. It is the type of field that is involved in the technological innovation that increases the control, programs office taxation and the viewer’s choice. In the internal and external concept, the changes of the technology have also measured the technique that is capable of developing the revolution with viewing the television including distribution of narrative structure. The translation of this multichannel also drives channel proliferation. In the year of 1986, it premiered with the complete concept of the broadcast network (Olivier, 2020). All through the presentation of cables is specialized with the offerings of different formats of economics including the outstanding status of FCC regulation.
It has an important concept in the long-lasting television industry which is important to develop the technologies. This technology is also helping to remove the control of normalized concepts where the drivers also increase the control program. On the other hand, the VCR also gives the viewers control over the recording program(Olivier, 2020). The advanced concept of the audience is also presented in measurement technique which allows for determining the concept of television including specification and accuracy.
Conclusion and recommendation
Netflix is the company that is presenting a constant flow which is made with the streaming product that is corporate with the philosophy. Netflix also uses the analytic tool which is recommended for the videos. Netflix is the 90-second window that helps the weavers to find TV shows or movies. It is also presenting an understanding of the customer needs which is belonging through the movies, web series, advertisements and videos. The researcher also finds the best creation of the innovation in this business process through the subscription business model. And the supply chain processes will present a close communication including the MSA application. This application is also highlighted within this study for developing the organization culture and the environment as well as engaging the interactivity e with important entities of external and internal.
This proposal also creates a developed understanding of the implementation and the benefits of MSA business operation. Moreover, it is present in top scope to create a strong network on the MSA data center which helps the Netflix organization for gaining a better market criterion. The organization also helps to improve the work performance issues by developing the understanding of company capacity. In this context, the management system of data is presented as a based action on the business operation which is used for developing customer data with a proper demand. Moreover, the data management system also in Hindi company productivity with the working capacity. It is presenting a transformation in the structure of MSA that is led with the proper changes which increase the satisfaction of the customer. MSA also developed opportunities for the company to expand their market system with the development of continuous improvement in Netflix.
References
.png)
.png)
MITS5004 IT Security Research Report 2 Sample
Objective(s)
This assessment item relates to the unit learning outcomes as in the unit descriptor. This assessment is designed to improve student presentation skills and to give students experience in researching a topic and writing a report relevant to the Unit of Study subject matter.
INSTRUCTIONS
Assignment 2 - Research Study - 10% (Due Session 9) Individual Assignment For this component you will write a report or critique on the paper you chose from Assignment
1. Your report should be limited to approx. 1500 words (not including references). Use 1.5 spacing with a 12 point Times New Roman font. Though your paper will largely be based on the chosen article, you should use other sources to support your discussion or the chosen papers premises.
Citation of sources is mandatory and must be in the IEEE style.
Your report or critique must include:
Title Page: The title of the assessment, the name of the paper you are reporting on and its authors, and your name and student ID.
Introduction: Identification of the paper you are critiquing/ reviewing, a statement of the purpose for your report and a brief outline of how you will discuss the selected article (one or two paragraphs).
Body of Report: Describe the intention and content of the article. If it is a research report, discuss the research method (survey, case study, observation, experiment, or other method) and findings. Comment on problems or issues highlighted by the authors. Report on results discussed and discuss the conclusions of the article and how they are relevant to the topics of this Unit of Study.
Conclusion: A summary of the points you have made in the body of the paper. The conclusion should not introduce any ‘new’ material that was not discussed in the body of the paper. (One or two paragraphs)
References: A list of sources used in your text. They should be listed alphabetically by (first) author’s family name. Follow the IEEE style.
The footer must include your name, student ID, and page number.
Note: reports submitted on papers which are not approved or not the approved paper registered for the student will not be graded and attract a zero (0) grade.
Solution
Introduction
The exciting improvements of the upcoming Microsoft Windows 11 operating system are disclosed in an insightful essay from eMazzanti Technologies, a reputable IT consultant and Microsoft cloud services provider with offices in NYC. Windows 11 is expected to revolutionise PC users' productivity and security when it launches in October. For Assignment Help, The article goes in-depth on the main improvements, like faster access to Microsoft Teams and a better Snap tool for window management. The criteria for Microsoft Azure Attestation (MAA) and the Trusted Platform Module (TPM) 2.0 further emphasise the importance of security. Windows 11 offers consumers a better, safer future with less frequent upgrades, improved tablet compatibility, and simplified system requirements.
Critique of the paper
The impending Windows 11 operating system is described in detail, along with some of its anticipated features, in the article titled "Windows 11 Set to Deliver Security and Productivity Improvements." The work does, however, have a few features that call for criticism and more investigation. In its review of the new features in Windows 11, the article, to start, lacks depth. It highlights improvements like quicker access to Microsoft Teams and a better Snap feature, but it does not go into detail about these or discuss any possible repercussions [1]. The readership would profit from a more thorough investigation of the potential effects of these features on user experience and output.
Second, a critical viewpoint on the system requirements for Windows 11 is absent from the essay. Although it acknowledges the necessity of Trusted Platform Module (TPM) 2.0, it does not address any potential difficulties or worries that consumers or organisations might encounter in order to comply with these standards. It would have been instructive to look more closely at the hardware requirements for upgrades and compatibility problems. The article also does not cover any potential downsides or compromises related to Windows 11 in any detail [2]. The new operating system is portrayed in a mainly positive light, but a fair analysis should take into account any drawbacks or restrictions that users might experience.
Strengths and Weaknesses
Strengths
The article outlines numerous advantages that Windows 11 is expected to offer. First and foremost, the improved security measures are a big plus. A proactive approach to tackling changing cybersecurity risks is demonstrated by the release of Trusted Platform Module (TPM) 2.0 and support for Microsoft Azure Attestation (MAA). By providing physical security against malicious software, these methods safeguard critical data. Second, Windows 11 offers some notable productivity improvements [3]. The taskbar's quicker access to Microsoft Teams makes it easier to collaborate and communicate with clients and colleagues. Multitasking is facilitated by the enhanced Snap window management capability, increasing overall efficiency. The disruption and annoyance brought on by lengthy update processes are reduced by smaller annual feature upgrades and monthly security updates.
Weaknesses
Windows 11 does, however, have some shortcomings. The heightened system requirements are a significant obstacle. Although these improvements are intended to increase security, they could be difficult for users with outdated gear to use. Compatibility problems could result from this, necessitating expensive hardware upgrades. The article also mentions that most customers would not be able to upgrade from Windows 10 until early 2022. For individuals who cannot upgrade right once, this staggered release schedule could lead to differences in the user experience and even impair corporate operations [4]. However, organisations and people will need to take into account potential limitations while planning their transition to the new operating system, such as the increased system requirements and the delayed availability for some users.
Problems or issues identified by the Author
Despite discussing a number of different features of Windows 11 in this essay, the author falls short in properly addressing a number of significant difficulties and problems.
Absence of Critical Analysis: This is a significant problem. This essay, which was authored by a Microsoft partner, seems to be a marketing piece for Windows 11 [5]. As a result, it is biased and skips over any potential negative aspects or shortcomings of the new operating system. Both the advantages and disadvantages should be discussed in a fair manner.
Limited Hardware Compatibility: Despite mentioning Windows 11's system requirements, the page does not go into great detail about the difficulties that users with older hardware may encounter. Many consumers can discover that their current devices do not satisfy these standards, needing expensive upgrades or new
Dependence on the Microsoft Ecosystem: The article highlights elements like direct access to Microsoft Teams and interaction with Microsoft Azure [6]. This, however, raises questions about vendor lock-in because consumers may become more and more reliant on the Microsoft environment, reducing their flexibility and options.
Security Issues: Despite the article's mention of improved security measures, it fails to address any potential privacy issues brought on by these adjustments. Users may be concerned about how Microsoft uses and collects personal data.
Transition Challenges: Although it makes a passing reference of the necessity for users and companies to get ready for the switch to Windows 11, it offers no specific advice on how to do so in an efficient manner. There should be more focus on this topic because switching to a new operating system might be a difficult procedure.
Relationship with the first assignment
The previous paper highlighting the value of operating system security and the paper outlining the security and productivity aspects of Windows 11 are related in the context of IT security and technological breakthroughs. The previous assignment offers understanding into crucial elements of operating system security, including vulnerabilities, exploitation strategies, and security mechanisms [7]. It emphasises how important it is to protect operating systems so that data and programmes are shielded from potential dangers. The article regarding Windows 11, in contrast, emphasises the enhancements and novel features in the future operating system update. The need of Trusted Platform Module (TPM) 2.0 is expressly mentioned as one of the improved security measures that must be in place to safeguard sensitive data.
The bigger picture of IT security is what connects these pieces. While the academic paper concentrates on the theoretical and practical elements of operating system security, the article about Windows 11 shows how operating system developers, like Microsoft, are actively addressing security concerns by incorporating new features and requirements. In the ever-evolving field of IT security, both publications emphasise the significance of strong operating system security mechanisms.
Components of the assignment
The upcoming release of Microsoft Windows 11 is examined in-depth in a new essay from eMazzanti Technologies by a well-known IT expert in the NYC region, who emphasises the significant gains in security and productivity. The rumour claims that an operating system for PCs that is extensively used will be released in October 2021. The focus is on the enhanced security capabilities of Windows 11, which include support for Microsoft Azure Attestation (MAA) and a requirement for the Trusted Platform Module (TPM) 2.0 [8]. These components make the system more robust to fend against threats that are always changing. Data security is enhanced by TPM 2.0's physical defence against malicious software.
The article also emphasises productivity upgrades that promote efficient multitasking and collaboration, such as easy access to Microsoft Teams directly from the taskbar and an improved Snap tool for window organising. By committing to monthly security updates that are 40% shorter than Windows 10's cumulative updates and annual feature upgrades rather to semi-annual ones, Windows 11 promises a more streamlined experience and addresses the continuing issue of lengthy Windows updates. While the transition to Windows 11 is expected to begin in October, the majority of customers will likely upgrade from Windows 10 to Windows 11 in the early months of 2022 [9]. During this transitional period, people and companies can assess their hardware compatibility and prepare for a seamless move.
Comparison and Analysis
This particular article from eMazzanti Technologies differs from other articles on Windows 11 in a number of ways:
Vendor Perspective: The author of this post is a Microsoft cloud services provider, in contrast to numerous articles that offer a more impartial and objective perspective on Windows 11. As a result, it has a more sales-oriented tenor and places greater emphasis on the operating system's advantages and good points. It differs from more unbiased evaluations due to the vendor-specific perspective.
Emphasis on Security and Productivity: The focus of this article is on security and productivity improvements rather than Windows 11's features, which are generally only mentioned in passing in other articles. It goes into detail about Microsoft Teams integration and the need for Trusted Platform Module (TPM) 2.0 [10]. Compared to articles that might cover a wider range of topics, it stands out because of its narrow emphasis.
Highlighting Vendor Knowledge: The article highlights eMazzanti Technologies' knowledge as a Microsoft Gold Partner and its preparedness to help with Windows 11 upgrades. Unlike posts that primarily try to enlighten readers without endorsing any particular service providers, this one promotes itself.
Specific Release Information: The article indicates that Windows 11 is scheduled to be released in October 2021 and offers a plan for upgrading from Windows 10 to Windows 11 in early 2022. It distinguishes itself from articles that might offer more general information without definite periods thanks to its temporal context.
Limited Criticism: This article tends to emphasise Windows 11's advantages rather than its potential disadvantages or difficulties, in contrast to other articles that might critically analyse those issues [11]. The advantages are emphasised rather than a thorough evaluation.
Conclusion
In conclusion, the eMazzanti Technologies paper discusses important features of Windows 11, with a focus on security, productivity, and system requirements. It forecasts a release date of October and highlights the advantages of greater productivity tools including Microsoft Teams integration, smaller monthly upgrades, and an annual update cycle. The article recognises that individuals and companies must get ready for the switch to Windows 11 because of the higher system requirements. It also emphasises how ready eMazzanti Technologies is to help with this shift. However, it's crucial to highlight that the essay lacks a critical viewpoint and is written from a promotional perspective, concentrating mostly on the positive elements of Windows 11.
References
COIT20251 Knowledge Audit for Business Analysis Report Sample
Task Description
In this assessment, you will demonstrate understanding of the core competencies and skills required for a Business Analyst. You will also demonstrate your knowledge in the use of tools and techniques for requirements elicitation and reporting.
The assessment has two parts – Part A: Reflections and Part B: Case Studies.
To construct this part of the assessment, you are required to a write a reflection on each of the three topics mentioned below.
1. The Business Analysis Maturity Model (BAMM)
2. Prototyping
3. Gap Analysis
In each reflection, you will provide a brief introduction of the topic (method/process/model), how the method/process/model works, stakeholders involved, inputs and outputs, how it helps business analysis and its benefits. You also need to include figures, diagrams and illustrations to improve the quality of presentation.
Each portfolio should contain approximately 400 words. You need to include at least three references (including at least two academic references) for each reflection. You also need to make sure that the references are cited in the text and the reflections are free from any grammatical and spelling errors.
Part B: Case Studies
In this part, you will analyse two short case studies and answer questions for The Assignment helpline given with each case study. The case studies will be made available on the Moodle unit website. The answer to each case study question should not contain more than 400 words.
You should include at least four references (including at least two academic references) in this part.
Solution
Part A: Reflections
1. The Business Analysis Maturity Model (BAMM)
The Business Analysis Maturity Model (BAMM) is a framework that helps organizations evaluate and improve their business analysis practices. It is based on the idea that organizations can progress through different levels of maturity in their business analysis practices, and that by understanding where they are currently, they can take steps to improve. BAMM is a process that allows organizations to measure and evaluate their current business analysis practices in order to identify areas for improvement and align their business analysis strategy with their overall organizational goals (Jayapalan, 2020).
Five levels of maturity:
BAMM consists of five levels of maturity: Initial, Managed, Defined, Quantitatively Managed, and Optimizing. Each level describes a different stage in the development of business analysis practices and includes specific characteristics and capabilities that organizations at that level are expected to possess (Nilsson & Dahlgren, 2019).
.png)
Figure 1 Characteristics of the maturity levels
(Source: Nilsson & Dahlgren, 2019)
- At the Initial level, business analysis is ad-hoc and reactive, with no clear processes or standards in place.
- At the Managed level, processes and standards are established, but they are not consistently followed.
- At the Defined level, processes and standards are consistently followed and there is a clear understanding of the business analysis role within the organization.
- At the Quantitatively Managed level, metrics are used to measure the effectiveness of business analysis practices.
- At the Optimizing level, business analysis practices are continuously improved (Nilsson & Dahlgren, 2019).
Stakeholders involved in BAMM and input and output to BAMM
The stakeholders involved in BAMM include business analysts, project managers, business leaders, and other stakeholders that are impacted by the business analysis process. The inputs to BAMM include data on the organization's current business analysis practices and the outputs are a report that describes the organization's level of maturity and recommendations for improvement (Terry Ramabulana et al., 2020).
The stakeholders involved in BAMM include business analysts, project managers, business leaders, and other stakeholders that are impacted by the business analysis process. The inputs to BAMM include data on the organization's current business analysis practices and the outputs are a report that describes the organization's level of maturity and recommendations for improvement (Terry Ramabulana et al., 2020).
BAMM process
The BAMM process typically includes the following steps:
• Define the scope of the assessment: Determine which business analysis practices will be evaluated and which stakeholders will be involved.
• Gather data: Collect data on the organization's current business analysis practices through interviews, surveys, and document reviews.
• Analyze data: Review the data and evaluate the organization's level of maturity in each of the five BAMM levels.
• Report results: Prepare a report that describes the organization's level of maturity and provides recommendations for improvement.
• Implement improvements: Develop and implement a plan to address any identified areas for improvement.
BAMM helps business analysis by providing a clear and objective way to assess the organization's current practices and identify areas for improvement. It also helps to align business analysis practices with the organization's overall strategy and goals. By using BAMM, organizations can improve the effectiveness and efficiency of their business analysis practices, which in turn can lead to better decision-making, improved project outcomes, and increased business value.
Benefits of BAMM:
• Provides a clear and objective way to assess the organization's current practices and identify areas for improvement.
• Helps to align business analysis practices with the organization's overall strategy and goals.
• Improves the effectiveness and efficiency of business analysis practices.
• Leads to better decision-making, improved project outcomes and increased business value
2. Prototyping
Prototyping is a process of creating a model or simulation of a system or product, which is used to test and evaluate the design before it is built. Prototyping is an iterative process, which means that the prototype is continually refined and improved until it meets the requirements of the stakeholders.
Prototyping is a process that involves creating a preliminary version of a product or system to test and evaluate its design and functionality. The prototype is typically a simplified version of the final product and is used to gather feedback and make improvements before the final product is developed. The process of prototyping allows stakeholders to test and evaluate the product or system's design and functionality before it is developed, which can help identify any problems or issues early on and ultimately save time and money in the long run.
Different types of prototypes
There are different types of prototypes, such as paper prototypes, wireframes, and functional prototypes. Paper prototypes are simple mockups of the product or system created using paper and pencil, while wireframes are digital mockups that show the layout and functionality of the product or system. Functional prototypes are more advanced and can be used to test the product or system's functionality (BA,2021).
.png)
Figure 2 Prototype
(Source: BA,2021)
Stakeholders involved in prototyping and input and output to prototyping
The stakeholders involved in prototyping include project managers, designers, developers, and users. The inputs to prototyping include the product or system's requirements, design, and any constraints. The outputs are the prototype itself, feedback from stakeholders and any improvements that need to be made (Lauff et al.,2020).
Process of prototyping
.png)
(Source: BA,2021)
The process of prototyping typically includes the following steps:
• Define the scope of the prototype: Determine the purpose of the prototype and what features and functionality need to be included.
• Create the prototype: Use various tools and techniques to create a preliminary version of the product or system.
• Test and evaluate the prototype: Gather feedback from stakeholders and use it to make improvements to the prototype.
• Refine and improve the prototype: Make any necessary changes to the prototype based on feedback and testing (BA,2021).
Prototyping in business analysis
Prototyping helps business analysis by allowing stakeholders to test and evaluate the product or system's design and functionality before it is developed. This can help to identify any problems or issues early on, which can save time and money in the long run. It also helps to ensure that the final product or system meets the user's needs and is fit for purpose (Baldassarre et al., 2020).
Benefits of prototyping
• Allows stakeholders to test and evaluate the product or system's design and functionality before it is developed (Lauff et al.,2020).
• Helps to identify problems or issues early on and save time and money in the long run.
• Ensures that the final product or system meets the user's needs and is fit for purpose.
3. Gap analysis
Gap analysis is a process that involves identifying the differences between the current state of an organization and its desired future state. It is used to identify areas where the organization needs to improve in order to achieve its goals and objectives. The process of gap analysis helps organizations to identify areas of weakness and prioritize areas for improvement (Robin, & Robin, 2021).
The process of gap analysis typically includes the following steps:
.png)
Figure 4 Gap Analysis Process
(Source: Santhosh & II MBA, n.d.))
• Define the scope of the gap analysis: Determine the goals and objectives of the organization and what areas will be evaluated.
• Collect data on the current state: Gather information on the organization's current processes, systems, and performance metrics.
• Define the desired future state: Identify the goals and objectives of the organization and what the desired state should be.
• Compare the current and desired states: Identify the differences between the current and desired states and document any gaps or areas of weakness.
• Prioritize the gaps: Determine which gaps have the most impact on the organization's goals and objectives and prioritize them for improvement.
• Develop recommendations: Develop a plan to address the identified gaps and improve the organization's processes and systems (Santhosh & II MBA, n.d.).
Stakeholders involved in gap analysis and input and output to gap analysis
The stakeholders involved in gap analysis include business analysts, project managers, business leaders, and other stakeholders that are impacted by the organization's goals and objectives. The inputs to gap analysis include data on the organization's current state, goals and objectives, and any constraints. The outputs are a report that describes the gap between the current and desired state, and recommendations for improvement (Suklan, 2019).
Gap analysis role in business analysis
Gap analysis helps business analysis by providing a clear and objective way to identify areas where the organization needs to improve in order to achieve its goals and objectives. It allows the organization to understand the gap between their current and desired state, and prioritize areas for improvement. By using gap analysis, organizations can improve their performance and achieve their goals more efficiently. It also allows organizations to identify the gap between the current state and desired state in the areas of operations, processes, systems, and performance, in order to make informed decisions about how to improve and move forward (Robin, & Robin, 2021).
Benefits of Gap Analysis:
• Provides a clear and objective way to identify areas where the organization needs to improve
• Helps organizations to understand the gap between their current and desired state
• Prioritize areas for improvement
• Improves the organization's performance and achieve their goals more efficiently.
• Allows to identify the gap between current state and desired state in the area of operations, processes, systems, and performance (Suklan, 2019).
Part-B
Case Study-1: A Manufacturing Company
1. Position of current users of the Case study organisation on the Power/Influence/Interest Diagram.
In the Power/Influence/Interest Diagram, the current users of the Case study organization would likely be located in the lower right quadrant, as they have minimal power and influence within the organization, but a high level of interest in the current system they are using. They are the ones who are directly impacted by the system and have a high level of interest in it, since they have been using it for a long time and are familiar with its capabilities and limitations. They have developed a sense of trust and comfort with the system, have established a workflow that is efficient for them and they don't want to change it (Reed, 2022).
.png)
Figure 5 Power/Influence/Interest Diagram
(Source: Paula, 2022)
The users may have some resistance to changing the system they are used to, and they do not want to spend time and effort learning a new system or dealing with the trauma of change that comes with it. They might not see the need for a new system, since the current one is working for them. They are not the problem owners, they are not the ones who have the problem with the old system, they are just the ones who have to work with it.
On the other hand, upper-level management is located in the upper left quadrant. They have the power and influence to make decisions for the organization, but their interest in the current system may not be as high as that of the users. They are concerned about the two people who are maintaining the system, and the potential consequences of not having anyone to maintain it. They are worried that the company will not be able to sell any new products if the system is not updated. They see the need for a new system written in a modern language with more modern technology (Mints & Kamyshnykova, 2019).
The Upper-level management are aware that the technology is outdated and that it is hard to find people who can maintain it. They are aware that the system is not meeting the current regulatory compliance standards, and they are worried that the company will be penalized if the system is not updated. They are the problem owners in this situation, they are the ones who have the problem with the old system and they are the ones who have to find a solution for it. Upper-level management is in a position of power and influence, and they have the responsibility to make decisions that will benefit the organization as a whole. They must weigh the concerns of the users with the needs of the organization, and find a solution that will work for both parties.
2. Strategies to effectively manage the stockholders in an "uncooperative users" situation
• Communicate the urgency and importance of the situation to upper management and gain their support in communicating the need for change to the users: The support of upper management is crucial to overcome resistance from the users. Upper management should be involved in the process of selecting and designing the new system, allowing them to provide input and feedback on how it will impact their work processes. They should be able to communicate the urgency of the situation and the potential risks if the system is not updated (Gupta et al., 2020).
• Involve the users in the process of selecting and designing the new system: By involving the users in the process, they will feel more invested in the new system, and their resistance to change may decrease. It is essential to understand their concerns and address them in the design of the new system. The users should be able to provide feedback on the system design and they should be able to test the new system before it is implemented. The users should be able to provide feedback on the system's ease of use and they should be able to provide feedback on the system's compliance with their workflow.
• Provide training and support for the new system: To mitigate the users' resistance to change, it is essential to provide training and support for the new system. This will help them understand how the new system works and how it will benefit them. The users should be able to attend training sessions and they should be able to receive support from the system's developers. The users should be able to receive support during the transition period and after the new system is implemented (Mints & Kamyshnykova, 2019).
• Communicate the benefits of the new system: It is essential to communicate the benefits of the new system to the users, such as increased efficiency, improved compliance, and better reporting capabilities. This will help the users understand why the new system is necessary and how it will improve their work processes. It is important to show the users how the new system will make their job easier, more efficient and how it will help them to meet the regulatory compliance (Gupta et al., 2020).
• Be flexible and open to feedback: It is essential to be flexible and open to feedback from the users throughout the process. The users should be able to provide feedback on the new system, and the system developers should be able to make changes based on the feedback. The system should be flexible enough to adapt to the users' needs.
• Have a plan in place for the transition: It is essential to have a plan in place for the transition from the old system to the new system. This will help ensure a smooth transition and minimize disruption to the users' work processes. The plan should include a timeline for the transition, a training schedule for the users, and a support plan for the users during and after the transition.
Case Study-2: Smart Solar Systems (3S)
1. Tangible and Intangible costs that would be involved in the business improvement options.
The business improvement options proposed for the 3S company that would involve both tangible and intangible costs.
Tangible costs
• Tangible costs include the cost of implementing cloud-based ERP and KM systems, as well as the cost of training front-line staff to become generalists (Chofreh et al., 2020).
• The cost of purchasing and implementing new software systems can be substantial, as well as the cost of training employees on how to use them.
• Additionally, there may be additional costs such as hardware upgrades or IT support that would need to be considered.
• These costs may include the purchase, installation and maintenance of the software, the cost of data migration, the cost of employee training, the cost of IT support and the cost of hardware upgrades (Velenturf & Jopson, 2019).
Intangible costs
• Intangible costs include the costs of changing the company organizational structure and culture. This may involve significant changes in how the company operates, which can be disruptive to employees and may require significant time and effort to implement.
Additionally, there may be a loss of experienced employees who are not comfortable with the new organizational structure or who may not possess the necessary skills to adapt to new roles. This can lead to a loss of institutional knowledge, which can be difficult to replace, and a loss of employee engagement, which can lead to a decrease in productivity (Andersson et al., 2019).
• Another intangible cost would be the time taken to implement these changes. The change process may take a while and might also face resistance from employees and managers who might be uncomfortable with the new ways of working.
This may lead to a decrease in productivity and may also lead to delays in completion of tasks and projects. This can also lead to a loss of customer trust and business opportunities (Carlsson Wall et al., 2022).
• Finally, the cost of flattening the organization hierarchy would be that managers may lose some of their decision-making power, and that front-line staff may not be prepared to take on more responsibility, which could lead to confusion and mistakes.
This may also lead to a loss of accountability and a lack of direction in the organization, which can lead to a lack of progress in achieving company goals (Andersson et al., 2019).
The business improvement options would involve significant tangible costs such as implementation of new software systems and training of employees, as well as intangible costs such as changes in organizational structure and culture, loss of experienced employees, and resistance from employees. Additionally, it can also lead to a loss of time and delay in achieving company goals
2. Tangible and Intangible benefits that business improvement options deliver once implemented successfully
The business improvement options proposed for the 3S company would deliver both tangible and intangible benefits once implemented successfully.
Tangible benefits
• Tangible benefits include improved efficiency and productivity, as well as cost savings resulting from the streamlined business processes. The implementation of cloud-based ERP and KM systems would allow for better collaboration, communication and sharing of knowledge among the teams, leading to improved workflow, faster decision making and reduced errors. This would lead to faster completion of projects, improved customer service and increased revenue for the company (Chofreh et al., 2020).
Flattening the organizational hierarchy would give front line staff more autonomy in decision making, which can lead to increased job satisfaction, higher employee engagement and improved performance. This can also lead to improved customer service as front line staff would be more empowered to make decisions that are in the best interest of the customer, which would lead to increased customer loyalty and repeat business (Andersson et al., 2019).
• Integrating business units would allow customer service, engineering & design, logistics, installation, marketing, and sales teams to collaborate and share information more easily without needing the approval of their managers. This would allow teams to work more efficiently and effectively, and would lead to faster completion of projects and increased customer satisfaction. This would also lead to increased revenue and improved company reputation (Velenturf & Jopson, 2019).
• Re skilling front line staff to become generalists would make them more versatile and adaptable to different roles, which would allow the company to respond more quickly to changing market conditions. This would also lead to better employee retention, as employees would be more likely to stay with the company if they were given the opportunity to learn new skills and take on new roles. This would lead to reduced recruitment and training costs for the company (Carlsson Wall et al., 2022).
Intangible benefits
Intangible benefits include improved company culture, increased employee engagement and improved customer satisfaction. A more collaborative and communicative culture would improve employee morale, and the ability to adapt to changing market conditions would lead to improved:
• Customer satisfaction
• Brand reputation and Customer loyalty.
• Employee engagement and motivation
• Performance and Productivity (Andersson et al., 2019).
The business improvement options would provide a range of tangible and intangible benefits once implemented successfully. These benefits include improved efficiency, productivity and cost savings, increased employee engagement and satisfaction, improved customer service and satisfaction, improved company culture and brand reputation, and the ability to adapt to changing market conditions. These improvements would ultimately lead to a more successful and profitable company.
The company will have better coordination, collaboration and information sharing among the teams across departments, leading to faster completion of projects and increased customer satisfaction. The company would be able to respond more quickly to changing market conditions, which would lead to increased revenue and improved company reputation. The company will also have reduced recruitment and training costs and improved employee retention, which would lead to improved performance and productivity.
References
.png)

.png)
.png)
.png)
.png)
.png)



.png)
~5.png)
.png)
~1.png)























































.png)






