Order Now
- Home
- About Us
-
Services
-
Assignment Writing
-
Academic Writing Services
- HND Assignment Help
- SPSS Assignment Help
- College Assignment Help
- Writing Assignment for University
- Urgent Assignment Help
- Architecture Assignment Help
- Total Assignment Help
- All Assignment Help
- My Assignment Help
- Student Assignment Help
- Instant Assignment Help
- Cheap Assignment Help
- Global Assignment Help
- Write My Assignment
- Do My Assignment
- Solve My Assignment
- Make My Assignment
- Pay for Assignment Help
-
Management
- Management Assignment Help
- Business Management Assignment Help
- Financial Management Assignment Help
- Project Management Assignment Help
- Supply Chain Management Assignment Help
- Operations Management Assignment Help
- Risk Management Assignment Help
- Strategic Management Assignment Help
- Logistics Management Assignment Help
- Global Business Strategy Assignment Help
- Consumer Behavior Assignment Help
- MBA Assignment Help
- Portfolio Management Assignment Help
- Change Management Assignment Help
- Hospitality Management Assignment Help
- Healthcare Management Assignment Help
- Investment Management Assignment Help
- Market Analysis Assignment Help
- Corporate Strategy Assignment Help
- Conflict Management Assignment Help
- Marketing Management Assignment Help
- Strategic Marketing Assignment Help
- CRM Assignment Help
- Marketing Research Assignment Help
- Human Resource Assignment Help
- Business Assignment Help
- Business Development Assignment Help
- Business Statistics Assignment Help
- Business Ethics Assignment Help
- 4p of Marketing Assignment Help
- Pricing Strategy Assignment Help
- Nursing
-
Finance
- Finance Assignment Help
- Do My Finance Assignment For Me
- Financial Accounting Assignment Help
- Behavioral Finance Assignment Help
- Finance Planning Assignment Help
- Personal Finance Assignment Help
- Financial Services Assignment Help
- Forex Assignment Help
- Financial Statement Analysis Assignment Help
- Capital Budgeting Assignment Help
- Financial Reporting Assignment Help
- International Finance Assignment Help
- Business Finance Assignment Help
- Corporate Finance Assignment Help
-
Accounting
- Accounting Assignment Help
- Managerial Accounting Assignment Help
- Taxation Accounting Assignment Help
- Perdisco Assignment Help
- Solve My Accounting Paper
- Business Accounting Assignment Help
- Cost Accounting Assignment Help
- Taxation Assignment Help
- Activity Based Accounting Assignment Help
- Tax Accounting Assignment Help
- Financial Accounting Theory Assignment Help
-
Computer Science and IT
- Operating System Assignment Help
- Data mining Assignment Help
- Robotics Assignment Help
- Computer Network Assignment Help
- Database Assignment Help
- IT Management Assignment Help
- Network Topology Assignment Help
- Data Structure Assignment Help
- Business Intelligence Assignment Help
- Data Flow Diagram Assignment Help
- UML Diagram Assignment Help
- R Studio Assignment Help
-
Law
- Law Assignment Help
- Business Law Assignment Help
- Contract Law Assignment Help
- Tort Law Assignment Help
- Social Media Law Assignment Help
- Criminal Law Assignment Help
- Employment Law Assignment Help
- Taxation Law Assignment Help
- Commercial Law Assignment Help
- Constitutional Law Assignment Help
- Corporate Governance Law Assignment Help
- Environmental Law Assignment Help
- Criminology Assignment Help
- Company Law Assignment Help
- Human Rights Law Assignment Help
- Evidence Law Assignment Help
- Administrative Law Assignment Help
- Enterprise Law Assignment Help
- Migration Law Assignment Help
- Communication Law Assignment Help
- Law and Ethics Assignment Help
- Consumer Law Assignment Help
- Science
- Biology
- Engineering
-
Humanities
- Humanities Assignment Help
- Sociology Assignment Help
- Philosophy Assignment Help
- English Assignment Help
- Geography Assignment Help
- Agroecology Assignment Help
- Psychology Assignment Help
- Social Science Assignment Help
- Public Relations Assignment Help
- Political Science Assignment Help
- Mass Communication Assignment Help
- History Assignment Help
- Cookery Assignment Help
- Auditing
- Mathematics
-
Economics
- Economics Assignment Help
- Managerial Economics Assignment Help
- Econometrics Assignment Help
- Microeconomics Assignment Help
- Business Economics Assignment Help
- Marketing Plan Assignment Help
- Demand Supply Assignment Help
- Comparative Analysis Assignment Help
- Health Economics Assignment Help
- Macroeconomics Assignment Help
- Political Economics Assignment Help
- International Economics Assignments Help
-
Academic Writing Services
-
Essay Writing
- Essay Help
- Essay Writing Help
- Essay Help Online
- Online Custom Essay Help
- Descriptive Essay Help
- Help With MBA Essays
- Essay Writing Service
- Essay Writer For Australia
- Essay Outline Help
- illustration Essay Help
- Response Essay Writing Help
- Professional Essay Writers
- Custom Essay Help
- English Essay Writing Help
- Essay Homework Help
- Literature Essay Help
- Scholarship Essay Help
- Research Essay Help
- History Essay Help
- MBA Essay Help
- Plagiarism Free Essays
- Writing Essay Papers
- Write My Essay Help
- Need Help Writing Essay
- Help Writing Scholarship Essay
- Help Writing a Narrative Essay
- Best Essay Writing Service Canada
-
Dissertation
- Biology Dissertation Help
- Academic Dissertation Help
- Nursing Dissertation Help
- Dissertation Help Online
- MATLAB Dissertation Help
- Doctoral Dissertation Help
- Geography Dissertation Help
- Architecture Dissertation Help
- Statistics Dissertation Help
- Sociology Dissertation Help
- English Dissertation Help
- Law Dissertation Help
- Dissertation Proofreading Services
- Cheap Dissertation Help
- Dissertation Writing Help
- Marketing Dissertation Help
- Programming
-
Case Study
- Write Case Study For Me
- Business Law Case Study Help
- Civil Law Case Study Help
- Marketing Case Study Help
- Nursing Case Study Help
- Case Study Writing Services
- History Case Study help
- Amazon Case Study Help
- Apple Case Study Help
- Case Study Assignment Help
- ZARA Case Study Assignment Help
- IKEA Case Study Assignment Help
- Zappos Case Study Assignment Help
- Tesla Case Study Assignment Help
- Flipkart Case Study Assignment Help
- Contract Law Case Study Assignments Help
- Business Ethics Case Study Assignment Help
- Nike SWOT Analysis Case Study Assignment Help
- Coursework
- Thesis Writing
- CDR
- Research
-
Assignment Writing
-
Resources
- Referencing Guidelines
-
Universities
-
Australia
- Asia Pacific International College Assignment Help
- Macquarie University Assignment Help
- Rhodes College Assignment Help
- APIC University Assignment Help
- Torrens University Assignment Help
- Kaplan University Assignment Help
- Holmes University Assignment Help
- Griffith University Assignment Help
- VIT University Assignment Help
- CQ University Assignment Help
-
Australia
- Experts
- Free Sample
- Testimonial
ENGR8762 Networks and Cybersecurity Assignment Sample
Assignment Brief
This assignment contributes 20% of your overall assessment for the topic. The grading for this assignment will be according to the University rating scheme [HD, DN, CR, P, F].
This assignment has two parts: Part A has 6% Marks, and Part B has 14% Marks.
Before you submit your assignment, you must complete the Academic Integrity module ACINT001with full marks. This is to ensure you have a good understanding of the issues of contract cheating, plagiarism, falsification, and collusion. Your submission will be automatically scanned by Turnitin for similarity. Your submission should have a similarity of less than 20%.
Submission
Due Date: Friday 29th Oct 2021 by 5 pm.
For Part A, you should provide a table (as per the example given on the next page), which addresses the threat category, controls, description, classification, and type.
For Part B, you should write a research report. The research report must have at least 1500 words but not more than 2500 words.
The assignment should be submitted as a single PDF file to the assignment space on the topic FLO page for assignment help
Late Submission
As per the official Statement of Assessments Methods (S2-2021) for this topic.
Part A: Threat classification and mitigation (6% of Total)
For the following Threat Categories, 1) Explain the threat, 2) which type of Control should be put in place for mitigation, 3) classify the controls as Process (Administrative), Product or Physical, 4) State the type of controls whether it will Prevent, Detect, Correct or Compensate. Do provide the references.
Threat Categories:
1. Impersonation attacks
2. Phishing attacks assisted with deep fake
3. Cloud Jacking
4. Ransomware attacks
5. Smishing attacks
6. DNS tunneling
Part B: Research report (14% of Total)
The topic for research is the latest security Threats. Sections on these threats include the following:
• Artificial intelligence enhanced cyber threats
• Fake news
• Ransomware attacks
• Machine learning poisoning
• Smart contract hacking
• Deep fake
• Application programming interface (API) vulnerabilities
• Internet of Things based Attacks
• Cloud vulnerabilities
• Vehicle Cyberattacks
• Threats to election
Select one of the above threats and find eight relevant papers which assist someone in developing a network threat taxonomy.
Compose an annotated bibliography of research papersthatrelate to the issue, soyour annotated bibliography will help you (and others) to have a good resource to evaluate and think about the relevance and quality of material on the topic. An example of an annotated bibliography is given at the link
https://digitalcommons.kennesaw.edu/cgi/viewcontent.cgi?referer=https://scholar.google.com/&httpsredir=1&article=1011&context=jcerp
Make sure that the information meets the topic's requirements and is from a reliable and academically respected source. Website references are not permitted unless the website is authoritative, e.g., CERT, NIST etc. You can use google scholar, IEEE Xplore digital library or ACM digital library for searching the articles.
What is an annotated bibliography?
An annotated bibliography is a list of citations to books, articles, and documents. Each citation is followed by a brief (usually about 150 - 300 words) descriptive and evaluative paragraph, the annotation. The purpose of the annotation is to inform the reader of the relevance, accuracy, and quality of the sources cited.
Annotations are NOT abstracting
Abstracts are the purely descriptive summaries often found at the beginning of scholarly journal articles or in periodical indexes. Annotations are descriptive and critical; they expose the author's point of view, clarity and appropriateness of expression, and authority.
General Instructions
The annotated bibliography is to be produced using a word processor and the EndNote reference database (or any other reference database). The submitted document must be in PDF or Word format.
The Process
Creating annotated bibliography calls for the application of a variety of intellectual skills: concise exposition, succinct analysis, and informed library research.
Solution
Part-A
The tables for threat categories along with the control and classification is shown below:
.png)
Part-B
Title
A Literature Review on Internet of Things-Based Attack
Abstract
Internet of Thing is one of the widely used platforms for transacting data. Several cloud-based applications are operated through the implication of the Internet of Things. Thus, it is one of the most demanding medium for information interchange. Millions of users are connected with this network by accessing the cloud-based application either from mobile or computer. Apart from its ease of access and platform-friendly to use, it has some security issues. As most of the users are connected with such networks for accessing the applications and services, cybercriminals obtain a feasible way to attack the connected devices and the network by penetrating malicious elements. Using this process, they use to get access to the user device and the organizational devices such as server, database etc. This causes the data and financial breach to the users and thus, it is essential to restrict the penetration of malicious elements into the network. Many researchers have proposed their methodologies and model for the prohibition or restriction to the penetration of malicious elements in the Internet of Things Network. Some of the important researches will be reviewed and discussed in this section.
Annotated Bibliography and Summarization
Annotated Bibliography
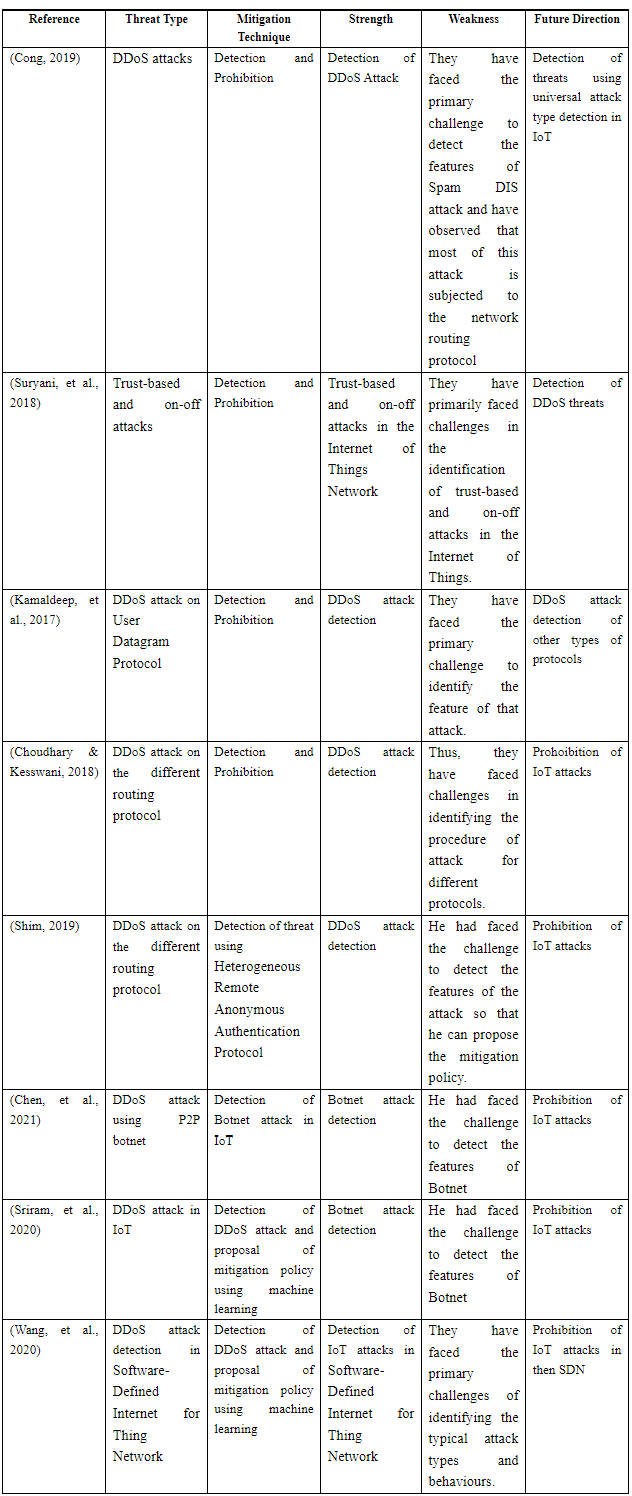
Cong, P., 2019. Spam DIS Attack Against Routing Protocol in the Internet of Things. International Conference on Computing, Networking and Communications (ICNC), pp. 198-201.
The author of this research belongs to the Department of Computer Sciences and Electrical Engineering at Marshall University, Huntington, USA. He has proposed the model to detect the DDoS attack in the Internet of Things network. They have detected that there are different types o malicious against available for DDoS attacks and one of the newest attack types is Spam DDoS. They have faced the primary challenge to detect the features of Spam DIS attack and have observed that most of this attack is subjected to the network routing protocol. So, they have researched and proposed the model through which the new type of DDoS attack that is DIS can be detected and the Internet of Things network can be protected.
Notes: This research produces a clear idea about the identification of DIS threats and the procedure of identification in the Internet of things Network.
Suryani, V., Sulistyo, S. & Widyawan, 2018. The Detection of On-Off Attacks for the Internet of Things Objects. International Conference on Control, Electronics, Renewable Energy and Communications (ICCEREC), pp. 1-4.
The authors of this research belong to the universities of Indonesia. They have researched on the Internet of Things objects that generally behave harmless while at the time of interaction with others. However, those interactions are done in a trust-based system where there is the possibility of an ON-OFF attack that can breach the user data silently. They have primarily faced challenges in the identification of trust-based and on-off attacks in the Internet of Things. They have proposed the model to detect and restrict trust-based and on-off attacks in the Internet of Things Network.
Notes: This research paper states the process of trust-based and on-off attacks in the Internet of Things Network and the procedure of detection and mitigation.
Kamaldeep, Malik, M. & Dutta, M., 2017. Contiki-based mitigation of UDP flooding attacks in the Internet of things. International Conference on Computing, Communication and Automation (ICCCA), pp. 1-5.
The authors of the research belong to India and have researched the DDoS attack that can be done by affecting User Datagram Protocol. They have emphasized the Contiki operating system and investigated the attack process. They have reviewed the previous research papers and identified that there are different types of attacks that are present in the domain of DDoS. One of the new and different types of DDoS attacks on which they have investigated was due to the effect of User Datagram Protocol in the said operating system. They have faced the primary challenge to identify the feature of that attack. Thus, they have designed and implemented the attack process using the Cooja simulator in the Contiki operating system. After that, they have proposed the solution for the mitigation process of that attach in Contiki operating system.
Notes: The researchers have demonstrated the attack type and the features of the attack on User Datagram Protocol along with the mitigation process.
Choudhary, S. & Kesswani, N., 2018. Detection and Prevention of Routing Attacks in Internet of Things. 12th IEEE International Conference On Big Data Science and Engineering (TrustCom/BigDataSE), pp. 156-159.
The authors of the research belong to India and have researched the DDoS attack on different routing protocols in the Internet of Things Network. It is to be mentioned that there are different types of routing protocols are available which are used for different purposes in the Internet of Things Network. Thus, the process of attacks is also different in these cases. Thus, they have faced challenges in identifying the procedure of attack for different protocols. They have proposed the methodology for the detection of different types of threats using Key Match Algorithm and Cluster-Based Algorithm which have been executed through Matlab Simulator.
Notes: In this research, the authors have shown and demonstrated the detection process of the threats for different types of protocols in the Internet of Things Network.
Shim, K.-A., 2019. Universal Forgery Attacks on Remote Authentication Schemes for Wireless Body Area Networks Based on Internet of Things. IEEE Internet of Things Journal, pp. 9211 - 9212.
The author of this research belongs to the University in South Korea. He had observed that wireless networks that are patched with the Internet of Things can be hacked using a DDoS agent. He had faced the challenge to detect the features of the attack so that he can propose the mitigation policy. After detecting the type of attack, he had proposed a Heterogeneous Remote Anonymous Authentication Protocol through which the attack in the Internet of Things Network can be detected.
Notes: He had demonstrated the Heterogeneous Remote Anonymous Authentication Protocol for the detection of threats in the Internet of Things Network.
Sriram, S., Vinayakumar, R., Alazab, M. & KP, S., 2020. Network Flow based IoT Botnet Attack Detection using Deep Learning.
According to the authors, administrations over the entire world are positively endorsing smart city requests to increase the superiority of daily-life actions in urban zones. Smart cities contain internet-related devices that are applied by processors such as traffic control, power grid, health care, water treatment, and many more. Each of these applications helps to improve its efficiency. The development in the number of Internet-of-things (IoT) is completely focused on botnet attacks. That is because of the rising tendency of Internet-enabled strategies. This article tries to suggest deep learning which depends upon a botnet detection system that works on network traffic movements to offer a progressive cyber-safety resolution to Internet-of-things devices as well as smart city requests.
Note: The authors of the research have demonstrated the type of attack and proposed the mitigation policy for it.
Chen, S.-C., Chen, Y.-R. & Tzeng, W.-G., 2021. Effective Botnet Detection Through Neural Networks on Convolutional Features. [Online]
The authors of the research belong to China. According to them, botnets is one of the prime threats related to internet-related cybercrimes for example spreading spam, DDoS attacks, and thefts precious information and data, according to the understanding of the research presentation it is quite evident that identifying modern botnets in recent years is becoming quite difficult to be found as well. Therefore, the project aims to present a machine learning method that can help detect the P2P botnet with the help of flow-based features.
Notes: The researchers have demonstrated the attack in the Internet of Things network that is caused by Botnet.
Wang, J., Liu, Y., Su, W. & Feng, H., 2020. A DDoS attack detection based on deep learning in software-defined Internet of things. IEEE 92nd Vehicular Technology Conference (VTC2020-Fall), pp. 1-5.
The researchers belong to the Universities in China. They have researched and emphasized different types of attacks in the software-defined Internet of Things. They have faced the primary challenges of identifying the typical attack types and behaviors. They have designed a Software-Defined Internet for Thing Network using the components like a controller, switches etc. and used a Deep Learning algorithm to detect the threats there.
Note: In this research, the authors have designed a realistic model for the detection of threats using Deep Learning.
Summarization
The summarization of the reviews of the previous researches are shown below:
References
Agarkar, S. & Ghosh, S., 2020. Malware Detection & Classification using Machine Learning. IEEE International Symposium on Sustainable Energy, Signal Processing and Cyber Security (iSSSC), pp. 1-5.
Chen, S.-C., Chen, Y.-R. & Tzeng, W.-G., 2021. Effective Botnet Detection Through Neural Networks on Convolutional Features. [Online]
Available at: https://.ieee.org/document/8455930
Chen, Y., Jin, B., Yu, D. & Chen, J., 2018. Malware Variants Detection Using Behavior Destructive Features. 2018 IEEE Symposium on Privacy-Aware Computing (PAC).
Choudhary, S. & Kesswani, N., 2018. Detection and Prevention of Routing Attacks in Internet of Things. 12th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE), pp. 156-159.
Cong, P., 2019. Spam DIS Attack Against Routing Protocol in the Internet of Things. International Conference on Computing, Networking and Communications (ICNC), pp. 198-201.
Jin, X. et al., 2020. A Malware Detection Approach Using Malware Images and Autoencoders. IEEE 17th International Conference on Mobile Ad Hoc and Sensor Systems (MASS), 8(2), pp. 172-177.
Kamaldeep, Malik, M. & Dutta, M., 2017. Contiki-based mitigation of UDP flooding attacks in the Internet of things. International Conference on Computing, Communication and Automation (ICCCA), pp. 1-5.
Kuruvila, A. P. & Basu, S. K. &. K., 2020. Analyzing the Efficiency of Machine Learning Classifiers in Hardware-Based Malware Detectors. IEEE Computer Society Annual Symposium on VLSI (ISVLSI), pp. 452-457.
Murali, R., Ravi, A. & Agarwal, H., 2020. A Malware Variant Resistant To Traditional Analysis Techniques. International Conference on Emerging Trends in Information Technology and Engineering (ic-ETITE), pp. 1-6.
Nisha, D., Sivaraman, E. & Honnavalli, P. B., 2019. Predicting and Preventing Malware in Machine Learning Model. 10th International Conference on Computing, Communication and Networking Technologies (ICCCNT), pp. 1-5.
Shim, K.-A., 2019. Universal Forgery Attacks on Remote Authentication Schemes for Wireless Body Area Networks Based on Internet of Things. IEEE Internet of Things Journal, pp. 9211 - 9212.
Sriram, S., Vinayakumar, R., Alazab, M. & KP, S., 2020. Network Flow based IoT Botnet Attack Detection using Deep Learning. s.l.:s.n.
Suryani, V., Sulistyo, S. & Widyawan, 2018. The Detection of On-Off Attacks for the Internet of Things Objects. International Conference on Control, Electronics, Renewable Energy and Communications (ICCEREC), pp. 1-4.
Wang, J., Liu, Y., Su, W. & Feng, H., 2020. A DDoS attack detection based on deep learning in software-defined Internet of things. IEEE 92nd Vehicular Technology Conference (VTC2020-Fall), pp. 1-5.

Download Samples PDF
Related Sample
- SENG205 Software Engineering Assignment
- NSG3NCI Chronic Illness Management Plan Assignment
- DATA4300 Data Security and Ethics Case Study Sample
- The Independent Director and Effective Corporate Governance
- BUS6101 Business Information Systems Case Study 2
- EBP107 Evidence Based Practice Assignment
- PPMP20009 Project Management Report
- MGT608 Business Law and International Contexts Case Study
- AHS205 The Australian Healthcare System within a Global Report 1
- PRJ5108 Project Delivery and Procurement Assignment
- COIT20263 Information Security Management Report 1
- BUS3004 Corporations Law T1 2023 Essay 1
- IM501 Agricultural Data and Information Management Report 2
- HI5017 Managerial Accounting Assignment
- MIS610 Advanced Professional Practice
- 96331 Planning and Evaluating Health Services Report
- HCT343 Research Methods and Data Analysis in Healthcare Assignment
- MBA600 Capstone Strategy Assignment
- PUBH6004 Assignment 2
- MBA504 Data Analytics for Business Assignment

Assignment Services
-
Assignment Writing
-
Academic Writing Services
- HND Assignment Help
- SPSS Assignment Help
- College Assignment Help
- Writing Assignment for University
- Urgent Assignment Help
- Architecture Assignment Help
- Total Assignment Help
- All Assignment Help
- My Assignment Help
- Student Assignment Help
- Instant Assignment Help
- Cheap Assignment Help
- Global Assignment Help
- Write My Assignment
- Do My Assignment
- Solve My Assignment
- Make My Assignment
- Pay for Assignment Help
-
Management
- Management Assignment Help
- Business Management Assignment Help
- Financial Management Assignment Help
- Project Management Assignment Help
- Supply Chain Management Assignment Help
- Operations Management Assignment Help
- Risk Management Assignment Help
- Strategic Management Assignment Help
- Logistics Management Assignment Help
- Global Business Strategy Assignment Help
- Consumer Behavior Assignment Help
- MBA Assignment Help
- Portfolio Management Assignment Help
- Change Management Assignment Help
- Hospitality Management Assignment Help
- Healthcare Management Assignment Help
- Investment Management Assignment Help
- Market Analysis Assignment Help
- Corporate Strategy Assignment Help
- Conflict Management Assignment Help
- Marketing Management Assignment Help
- Strategic Marketing Assignment Help
- CRM Assignment Help
- Marketing Research Assignment Help
- Human Resource Assignment Help
- Business Assignment Help
- Business Development Assignment Help
- Business Statistics Assignment Help
- Business Ethics Assignment Help
- 4p of Marketing Assignment Help
- Pricing Strategy Assignment Help
- Nursing
-
Finance
- Finance Assignment Help
- Do My Finance Assignment For Me
- Financial Accounting Assignment Help
- Behavioral Finance Assignment Help
- Finance Planning Assignment Help
- Personal Finance Assignment Help
- Financial Services Assignment Help
- Forex Assignment Help
- Financial Statement Analysis Assignment Help
- Capital Budgeting Assignment Help
- Financial Reporting Assignment Help
- International Finance Assignment Help
- Business Finance Assignment Help
- Corporate Finance Assignment Help
-
Accounting
- Accounting Assignment Help
- Managerial Accounting Assignment Help
- Taxation Accounting Assignment Help
- Perdisco Assignment Help
- Solve My Accounting Paper
- Business Accounting Assignment Help
- Cost Accounting Assignment Help
- Taxation Assignment Help
- Activity Based Accounting Assignment Help
- Tax Accounting Assignment Help
- Financial Accounting Theory Assignment Help
-
Computer Science and IT
- Operating System Assignment Help
- Data mining Assignment Help
- Robotics Assignment Help
- Computer Network Assignment Help
- Database Assignment Help
- IT Management Assignment Help
- Network Topology Assignment Help
- Data Structure Assignment Help
- Business Intelligence Assignment Help
- Data Flow Diagram Assignment Help
- UML Diagram Assignment Help
- R Studio Assignment Help
-
Law
- Law Assignment Help
- Business Law Assignment Help
- Contract Law Assignment Help
- Tort Law Assignment Help
- Social Media Law Assignment Help
- Criminal Law Assignment Help
- Employment Law Assignment Help
- Taxation Law Assignment Help
- Commercial Law Assignment Help
- Constitutional Law Assignment Help
- Corporate Governance Law Assignment Help
- Environmental Law Assignment Help
- Criminology Assignment Help
- Company Law Assignment Help
- Human Rights Law Assignment Help
- Evidence Law Assignment Help
- Administrative Law Assignment Help
- Enterprise Law Assignment Help
- Migration Law Assignment Help
- Communication Law Assignment Help
- Law and Ethics Assignment Help
- Consumer Law Assignment Help
- Science
- Biology
- Engineering
-
Humanities
- Humanities Assignment Help
- Sociology Assignment Help
- Philosophy Assignment Help
- English Assignment Help
- Geography Assignment Help
- Agroecology Assignment Help
- Psychology Assignment Help
- Social Science Assignment Help
- Public Relations Assignment Help
- Political Science Assignment Help
- Mass Communication Assignment Help
- History Assignment Help
- Cookery Assignment Help
- Auditing
- Mathematics
-
Economics
- Economics Assignment Help
- Managerial Economics Assignment Help
- Econometrics Assignment Help
- Microeconomics Assignment Help
- Business Economics Assignment Help
- Marketing Plan Assignment Help
- Demand Supply Assignment Help
- Comparative Analysis Assignment Help
- Health Economics Assignment Help
- Macroeconomics Assignment Help
- Political Economics Assignment Help
- International Economics Assignments Help
-
Academic Writing Services
-
Essay Writing
- Essay Help
- Essay Writing Help
- Essay Help Online
- Online Custom Essay Help
- Descriptive Essay Help
- Help With MBA Essays
- Essay Writing Service
- Essay Writer For Australia
- Essay Outline Help
- illustration Essay Help
- Response Essay Writing Help
- Professional Essay Writers
- Custom Essay Help
- English Essay Writing Help
- Essay Homework Help
- Literature Essay Help
- Scholarship Essay Help
- Research Essay Help
- History Essay Help
- MBA Essay Help
- Plagiarism Free Essays
- Writing Essay Papers
- Write My Essay Help
- Need Help Writing Essay
- Help Writing Scholarship Essay
- Help Writing a Narrative Essay
- Best Essay Writing Service Canada
-
Dissertation
- Biology Dissertation Help
- Academic Dissertation Help
- Nursing Dissertation Help
- Dissertation Help Online
- MATLAB Dissertation Help
- Doctoral Dissertation Help
- Geography Dissertation Help
- Architecture Dissertation Help
- Statistics Dissertation Help
- Sociology Dissertation Help
- English Dissertation Help
- Law Dissertation Help
- Dissertation Proofreading Services
- Cheap Dissertation Help
- Dissertation Writing Help
- Marketing Dissertation Help
- Programming
-
Case Study
- Write Case Study For Me
- Business Law Case Study Help
- Civil Law Case Study Help
- Marketing Case Study Help
- Nursing Case Study Help
- Case Study Writing Services
- History Case Study help
- Amazon Case Study Help
- Apple Case Study Help
- Case Study Assignment Help
- ZARA Case Study Assignment Help
- IKEA Case Study Assignment Help
- Zappos Case Study Assignment Help
- Tesla Case Study Assignment Help
- Flipkart Case Study Assignment Help
- Contract Law Case Study Assignments Help
- Business Ethics Case Study Assignment Help
- Nike SWOT Analysis Case Study Assignment Help
- Coursework
- Thesis Writing
- CDR
- Research


.png)
~5.png)
.png)
~1.png)























































.png)






