MIS605 Systems Analysis and Design Assignment Sample
Scenario (The Case) Book reading is an extremely healthy activity. It has many benefits and above all, it is exciting, entertaining and a great way to release stress, anxiety and depression. These are not the only benefits. Above everything; book reading helps in mental stimulation; improvement of memory and it also helps in improving language skills. It also certainly allows an individual to help concentrate better. In short, the benefits are enormous. In recent times we have been introduced to technologies such as laptops, cell phones, tablets and other technologies but to date, the conventional book reading is something that people cherish and enjoy in its own way. It is believed that a “book has no substitute” and book readers from all over the world firmly agree to this. Cynthia, a young technopreneur and a book lover; plans to open an online lifestyle substitute business named ‘bookedbook.com’. This online business is Cynthia’s dream. Cynthia has formally registered her new company, everything is in place from a legal perspective and the company now has ample funds to develop an online website that would support Cynthia’s business idea. bookedbook.com would be an extremely interesting website. This website will require user registration. Children would also be able to register but their registration would be accompanied with some details of parents and their contacts. The website would only offer individual registrations and proof of ID would be a must when registering. bookedbook.com will offer quarterly, biannual and annual memberships. The whole idea is very simple. Registered book readers would be able to launch the books that they own and which they would want to give away to other registered members. A book launch would require complete details of the book. It would also require the user to provide the address where the book is available. Once the book details are provided by the subscriber (registered book reader) the company’s content manager would approve the book launch request. Once approved, the book would be available for all users for them to review and/or acquire. The review process would allow all users to provide feedback and comments about the book and would also allow users to rate the book. The acquisition process would allow book readers to acquire the book from the book owner. The users planning on acquiring the book, would make a request for book acquisition. This request would help facilitate book reader meetup and exchange books. Once the book would be acquired the book owner would have the option of removing the book. bookedbook.com will also allow users to interact with one another via messaging and chat rooms. Users will be given an option to decide the mode of communication that they would prefer. Off course all chat request, messages and acquisition request and all other messages are also provided to the user via email that is provided at the time of subscription. The website would also provide a portal to the administrator for data analytics. Cynthia is keen to observe and analyse every type of data that is obtained at this website. For example, she wants to know which book is being exchanged mostly, she wants complete customer analytics, book exchange analytics, analysis of book reviews and rating and other similar portals for data analysis. As soon as the user registration would expire, all book launch requests would be halted by the system and the users interested in acquiring the book(s) placed by the user whose registration is about to expire would be sent an email that these book(s) are no longer available. Users would be asked to renew their subscription 15 days before the registration expiry date to ensure continuity of services. Cynthia does not want this website to be a book exchange platform only. She also wants the website to provide a platform for all the users to arrange for an online and face to face meetup. She wants to ensure that any book meetup events that bookedbook.com plans should be available to its users. Users should be able to register for these events which may be paid or unpaid. She feels that these meetups would be a great source of fun for book lovers and also a source of marketing for the company. In order to ensure this website stays profitable Cynthia also wants this website to allow book authors from all around the world to advertise their books on bookedbook.com. This functionality, however, would not require book authors to register with bookedbook.com formally. Book authors would be able to just fill in a ‘book show request form’, provide their details, provide the details of their book and a credit/debit card number. They would also provide information about the time period for which they want their book to be advertised on the website. Advertisement requests would also be approved by the content manager. Once approved, the book authors would be charged and the advertisement would go live. The ad would be removed by the system automatically once it reaches the end date. bookedbook.com will only allow advertisement of up to 5 books at a time. All advertisement requests would be entertained by the system on a first come first serve basis. The advertisement functionality is also available for subscribers. In this case the fee for advertisement is very minimal. Cynthia wants this website to be upgradable and secure. She wants simple and modern interfaces and also wants a mobile application version of this website.
Assignment brief:
In response to the case study provided, identify the functional and the non-functional requirement for the required information system and then build a Use Case Diagram and document set of use cases. Context System analysis methods and skills are of fundamental importance for a Business Analyst. This online assignment help allows you to enhance your system analysis skills by capturing the business and then functional and non-functional requirement of a system. It helps you in identifying “what” the proposed system will do and “how”?
Instructions 1. Please read the attached MIS605_ Assessment 1_Case Study. Note that every piece of information provided in the following case serves a purpose. 2. Once you have completed reading the case study. Please answer the following questions for essay help online:
Question 1 (10 mark). Identify all the human and non-human actors within the system. Provide brief description against every actor.
Question 2 (30 marks). Using the information provided in the case study, build a Use Case Diagram using any diagramming software. Note: Please make assumptions where needed.
Question 3 (60 marks). Document all use cases (use case methods). All use cases identified in the Use Case Diagram in Question 2 must be elaborated in detail. Please document each use case using the following template: Use Case Number Use Case Type Base/Abstract (Extends or Includes) Use Case Name Priority Actor Involved Associated Data Sources Associated User Interfaces Pre-Condition(s) Post Condition(s) Detailed Description Normal Course of Events Using a Flow Chart Diagram Alternate Course(s)
SOLUTION
Question-1:
Human Actors:
Management: The management of the bookedbook.com will handle all the process that is going to happen inside the system or outside this. The management will solve the query of the users who will find any difficulty or have any doubts in the system. They are going to generate the subscription and giving approvals to the users to enter the system. The management will maintain the system for the user. The management will decide the price structure and schedule to design the system. The financial approval is must for the management from the client (Hopkins, 2017).
Authors: The author will have a chance to add their books in the system and they can sell their book through it. The author can also generate the advertisement for the books they want to get popular. The author has an interest in different types of book writing and they will be able to get a good book reader from the system so this is helpful for them.
Readers: The readers have an interest to read the different types of books. This system will give them many options to read the books or acquire the books they like. The readers can also exchange the books which they have completed and someone else will require. They will buy a membership from the system to make the book reading and exchanging easy.
Book Sellers: The book sellers are the one who has so many books with them or doing business of the book selling. The book sellers will add the available books and try to sell or exchange it with someone else. The readers who require the book will send the request for book acquiring or exchanging. The book sellers will also organize the event through the system so the readers can attend it and more selling can be possible of their book.
Publications: The publication will print the books for the writers who writes the book. The publication will do contract with the book writers and provide the printing of the books to the different book sellers. The publication house is required to the book writers or authors to let their book gets selling.
Non-human Actors:
Email notification: If the book seller or readers membership is about to get ended then the system should let them know by giving some kind of warning. This is possible by sending the email notifications to them. The email API will ask the system about the users details and send the mail directly to them.
Reminder: The book sellers will arrange the different events in the system. The book readers will take part in such events. Once the book reader registers themselves in the events then it is required to send them the reminder. The system will automatically generate the reminder for the book readers and send it to them through email or SMS(Bron, 2020).
Question-2:
Admin Use case:
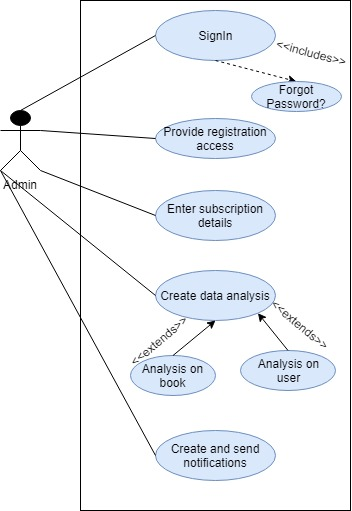
Content Manager Use Case:
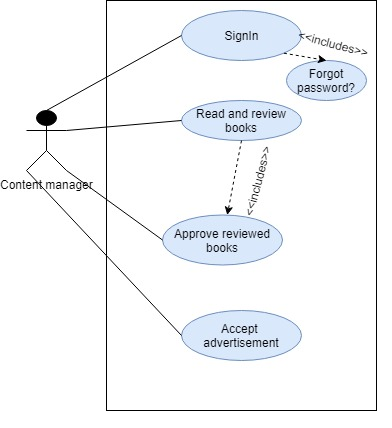
Book User Use Case:
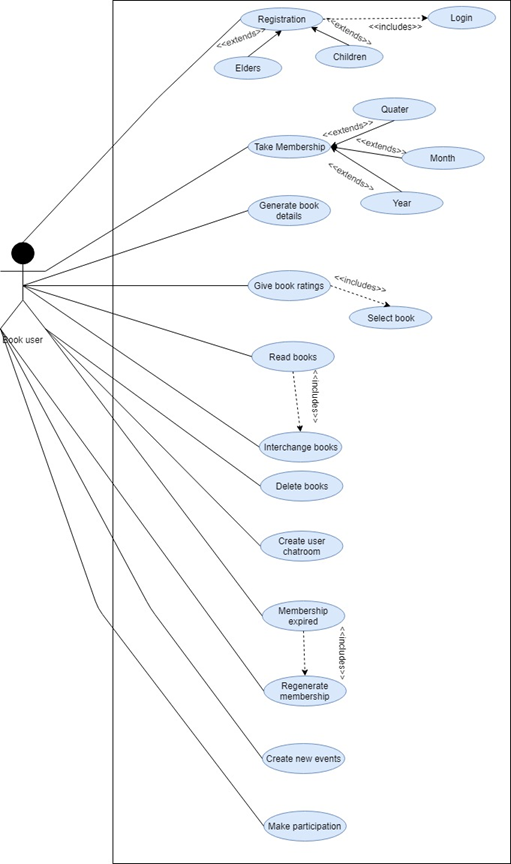
Author Use Case:
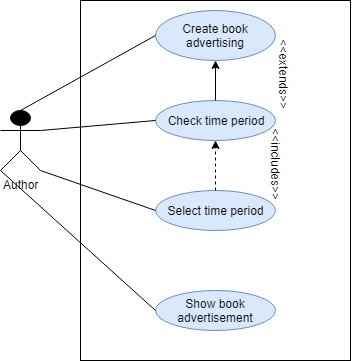
Question-3:
Sign in:
.png)
Provide Registration Access:
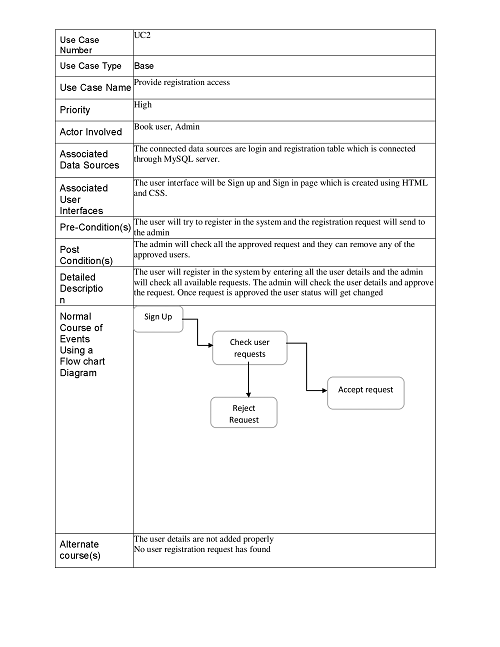
Enter Subscription Details:
.png)
Create Book Advertising:
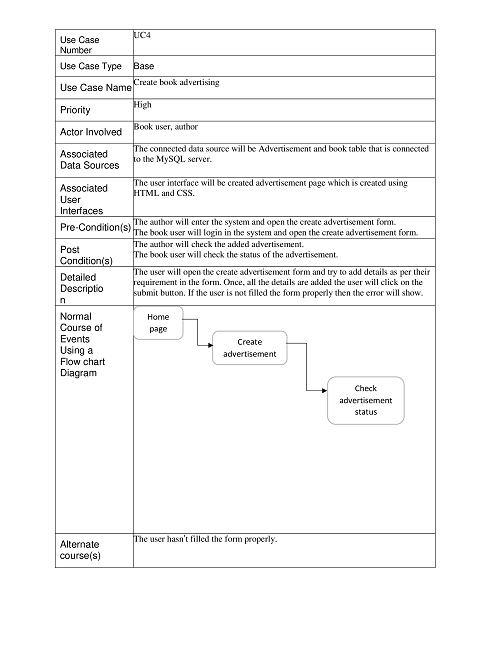
Show Book Advertisement:
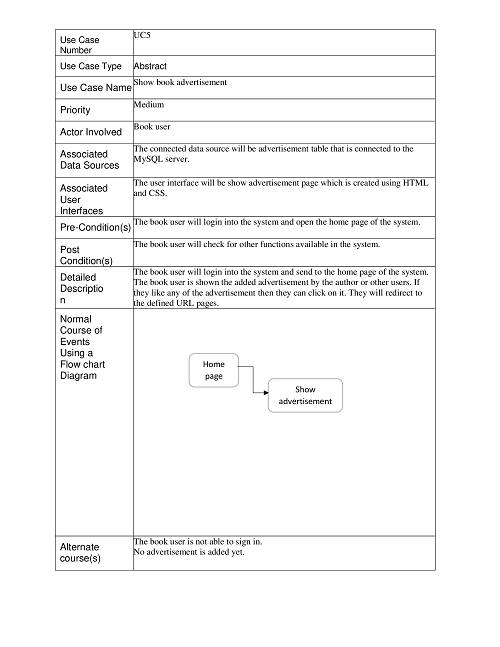
Generate Book Details:
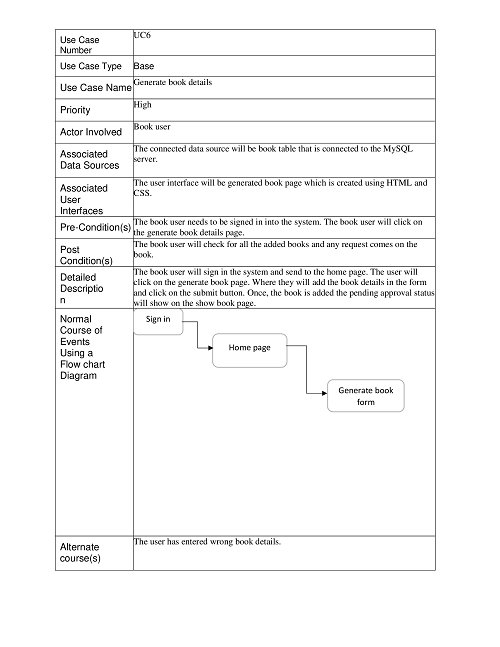
Take Membership:
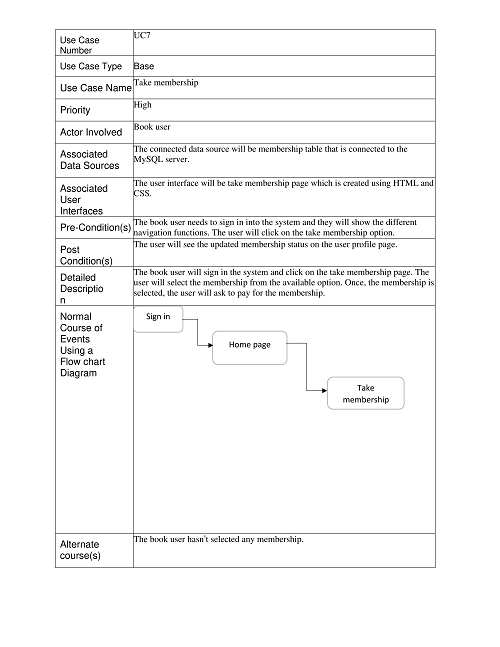
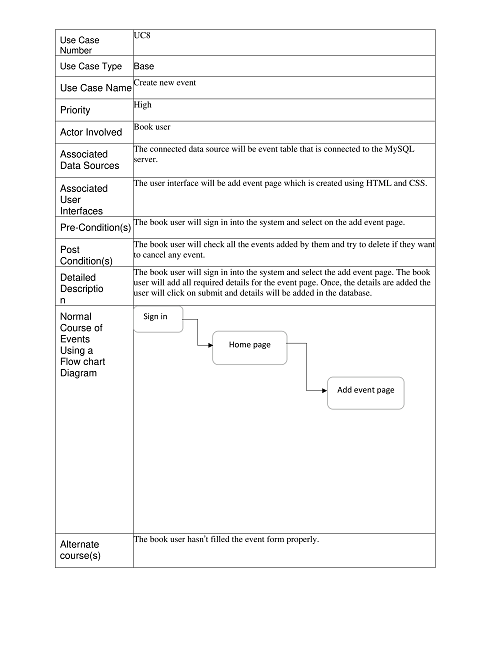
Create New Event:
References
Bron, J.Y., (2020). System requirements engineering : a SysML supported requirements engineering method. Hoboken,NJ: s.n.
Hopkins, M., (2017). Systems engineering : concepts, tools and applications. s.l.:Novinka.
Szabo, P. W., (2017). User experience mapping : get closer to your users and create better products for them. s.l.:Packt Publishing.
MIS101 Information Systems for Business Assignment Sample
Question
Task Summary Using your understanding of the components of Information systems, propose a assignment help technical solution for another organization. Please refer to the Task Instructions for details on how to complete this task. Context In Module 1, you learned about Information Systems and its components. In Module 2, you learned about Information Technology and Data Management in relation to Information Systems. You now have the opportunity to apply these concepts and propose a solution for the scenario given to you by your Learning Facilitator.
Task Instructions Read the scenario in the file MIS101_Assessment_1_Scenario to complete the task of writing a technical proposal. Deliverables Required Write a technical proposal for the organization identified in the scenario. The proposal should only discuss the technical aspects of the project. Do not focus on the managerial aspects such as cost, human and technical resources, etc.
Important Notes
• You must ensure that the technical proposal essay help online is relevant to the scenario given.
• Your technical proposal should ideally answer the following questions (but not limited to):
1. What would be the hardware requirements?
2. What would be the software requirements?
3. What would the communication and network for the scenario look like?
4. What would be the data needs and the data storage needs?
5. What would be the structure of the data layout plan?
6. How would the technical proposal being put forth be beneficial for the management and other stakeholders?
7. How would the proposed solution improve operations?
8. What would the limitations of the proposed solution be?
9. Other questions When writing your technical proposal, make sure that you write in a systematic way (the questions above are not given in a systematic manner). Make use of the internet to find out the structure/format of a technical proposal. When writing the technical proposal, assume that this would be submitted to your potential customer (as identified in the scenario given to you).
MIS101 - Assessment Task 1 Scenario B: HealthWay is a privately-owned healthcare facility that has been in business for 10 years and has a good reputation. It is a small hospital that is equipped to treat 20 inpatients at one time. In addition to inpatient care, it provides medical care service to outpatients via clinics specialising in family medicine, gynaecology, and paediatrics. HealthWay’s mission is to provide quality and personalised medical care to the patients. The organisation relies on a traditional file management system for all its business operations and patient record keeping. The management feels that the current system affects the performance of the business and makes patient record maintenance a slow process, thus affecting the quality of patient care. Josh, the President of HealthWay, believes that it is time to review the business and introduce information systems in the organisation to improve overall performance and gain competitive advantage. Josh wants to automate and optimise business operations including human resources, accounting and finance, supply chain management, and administration (although it is not limited to just these areas). He also wants the patients’ data to be arranged in such a way that it can be easily accessed and updated by the hospital staff. As HealthWay is a growing business and expects an increase in the number of patients, Josh sees this as an opportunity for improvement. He also wants the system to help the management in decision-making and planning. He wants an information system that can support all core and support operations of the hospital. Josh has requested your organisation, KSoft, to provide a technical proposal to be further discussed with Healthway’s Chief Technology Officer.
Solution
1. Abstract
In business (e.g. healthcare), Management Information Systems (MIS) is introduced to support the organisational processes, intelligence, operations. To improve business operations related to IT, outpatients and impatiens via clinics, automated business operations in the healthcare organisation, information system is required. The criteria of a technical proposal are to identify the core technical problems first, then evaluating it or justifying it with the base requirements, and later providing proposed solutions for these. MIS tools helped to manage information and move data associated with the patients. MIS is a formal, sociotechnical, as well as organisational system designed to control performance of HealthWay business processes.
Keywords: MIS, Healthcare system, Data management, Proposed Solution, Technical requirements, Technical proposal, HealthWay.
2. Introduction
In this technical proposal, Information Technology (IT) and Data management with relation to Business Information systems is taken into consideration. Based on the case scenario of HealthWay privately-owned healthcare facility, it has been possible for me to propose solutions and meet the organisational needs. This technical proposal is prepared by KSoft organisation considering the HealthWay’s Chief Technical Officer's perspective. Here, a basic structure of technical proposal has been followed and all the technical aspects, factors related to this project have been elaborated with a systematic manner and submitted to HealthWay’s potential customers.
3. Statement of Need
3.1. Hardware Requirements
Based on the understanding of the case scenario, hardware requirements for HealthWay Information System (HIS) are:
• Keyboard (s)
• Monitor (s).
• Mouse (s)
• Central Processing Unit (CPU) as Microprocessor (Carvalho Joa?o et al., 2019, p. 390).
• Hard disk drive (HDD) to store patient’s data and records.
• Optical disc drives
• Expansion cards
• Motherboard
• Power supply unit to every healthcare departments’ system
• Main Memory (Random Access Memory- RAM).
As per the ideas of Beverungen, Matzner & Janiesch, 2017, p. 783), hardware requirements for HIS can also be managed by the Clinical management, Supplies management, Support services, patient management, and also by information management.
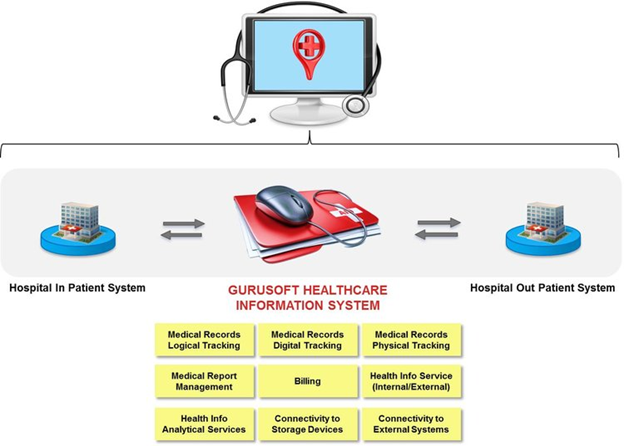
Figure 1: Inpatient & Outpatient requirements
(Source: Carvalho Joa?o et al., 2019, p. 393)
3.2. Software Requirements
In the case of the HealthWay Healthcare and Hospitality management system, to gather the patients’ data, software is required. Software is divided into two-part requirements: i). Functional, ii). Non-functional.
Under the functional requirements, Software Requirements Specification (SRS) is measured which is a complete configuration of different software requirements for registration process, report generation, database management etc (Beverungen, Matzner & Janiesch, 2017, p. 785). On the other hand, non-functional requirements of the HealthWay management system are for security, performance, reliability, and maintainability purposes.
3.3. Communication and Network scenario
On the basis of patients’ information and decision support tools, delivery of quality care, some technical factors are considered which are important for planning as well as implementation of healthcare communication networks:
• Transmission latency throughout the wide healthcare network.
• Ubiquity of network access (Carvalho Joa?o et al., 2019, p. 395)
• Bandwidth requirements and availability inside HealthWay
• Data security and confidentiality
• Continuous availability of the network.
3.4. Data & Data Storage Needs
As per the guidance of Daneshvar Kakhki & Gargeya, (2019, p. 5325), most of the HealthWay datasets are related to individual patients’ data, patients’ records, inpatients and outpatient’s data via clinics. Data storage options recommended for the same HealthWay organisation are:
• Cloud Computing is ideal to store healthcare information. Here, data stored online and considered for both security with latency and privacy for HealthWay.
• Storage Area Network (SAN) to the gynaecology, paediatrics, family medicine departments. SAN option is also applicable to measure the diagnostic data.
• External Storage Devices as Electronic Medical Records (EMR), External hard-disks or SSDs (Graybeal et al., 2018, p. 3276).
• Network Attached Storage System (NAS) stored humongous data churned out by HealthWay organisation. It is one of preferred storage options for HealthWay networks.
4. Evaluation
4.1. Data Layout Plan
With response to the raw data, and data storage, a layout plan has been recommended for the HealthWay information system. This data layout plan has been created by maintaining World Health Organisation (WHO) guidelines.
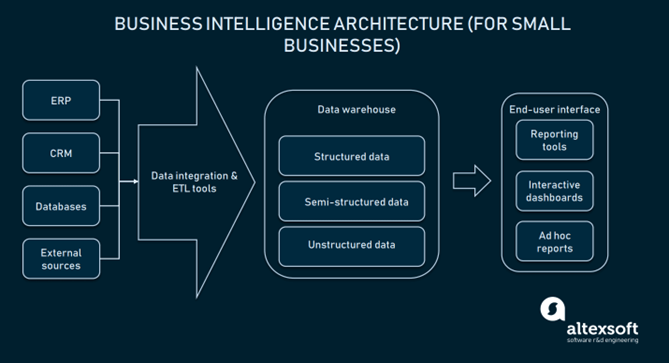
Figure 2: Basic Data structure of HealthWay Hospitality Management System (HMS)
(Source: Carvalho Joa?o et al., 2019, p. 398)
4.2. How it can be Beneficial for Stakeholders
This technical proposal put forth benefits for the HealthWay stakeholders and helps the higher managerial authority, Josh in following way:
• KSoft’s technical proposal is better for project planning, which often meets the dire need of the local communities.
• This proposal is recommended to solve the current healthcare issues.
• It builds with consensus (Beverungen, Matzner & Janiesch, 2017, p. 787).
• This technical proposal gives a plan for monitoring & evaluation
• It helps the researchers, experts to do more research and gives them ideas to move forward within the healthcare industry.
• Both Internal and External stakeholders are able to improve their business operations and marketing with HealthWay.
5. Solution
Understanding the scenario, this proposal provides technical solutions for all the major HealthWay attributes. This solution also created a link between the Case Scenario B and the technical proposal.
5.1. Proposed Solutions
Table 1: Detailed proposed solution for all the key aspects (Source: Jørgensen et al., 2019, p. 155)
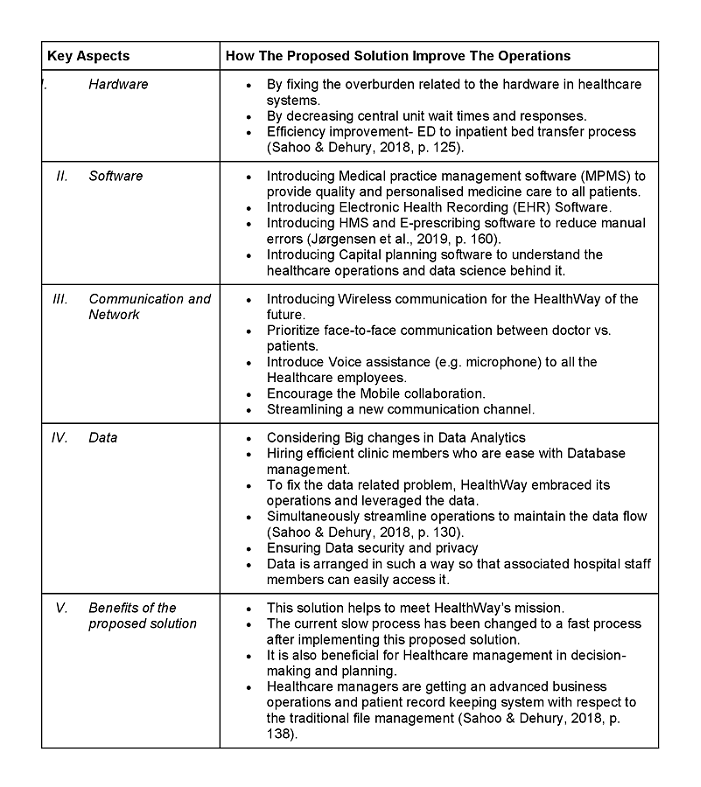
6. Conclusion
After addressing all the HealthWay requirements in a systematic manner, it can be concluded that the proposed solution recommended for the business scenario is appropriate and it provides further ideas to the learner.
6.1. Limitations
Limitations of the proposed solution would be:
• This technical proposal not focusing the managerial problems
• Solutions for cost breakdown, budgeting, human, and other technical resources have not been recommended here.
• This proposed solution is only limited to technical problems.
• Though it is an individual work but sometimes to find the exact solution for an appropriate MIS problem, more than one person is required.
7. References
Beverungen, D., Matzner, M., & Janiesch, C. (2017). Information systems for smart services. Information Systems and E-Business Management, 15(4), 781–787. https://doi.org/10.1007/s10257-017-0365-8
Carvalho Joa?o Vidal, Rocha A?lvaro, van de Wetering, R., & Abreu Anto?nio. (2019). A maturity model for hospital information systems. Journal of Business Research, 94, 388–399. https://lesa.on.worldcat.org/oclc/8089318423
Daneshvar Kakhki, M., & Gargeya, V. B. (2019). Information systems for supply chain management: a systematic literature analysis. International Journal of Production Research, 57(15-16), 5318–5339. https://doi.org/10.1080/00207543.2019.1570376
Graybeal, C., DeSantis, B., Duncan, B. L., Reese, R. J., Brandt, K., & Bohanske, R. T. (2018). Health-related quality of life and the physician-patient alliance: a preliminary investigation of ultra-brief, real-time measures for primary care. Quality of Life Research : An International Journal of Quality of Life Aspects of Treatment, Care and Rehabilitation - an Official Journal of the International Society of Quality of Life Research, 27(12), 3275–3279. https://doi.org/10.1007/s11136-018-1967-4
Jørgensen, R., Scarso, E., Edwards, K., & Ipsen, C. (2019). Communities of practice in healthcare: a framework for managing knowledge sharing in operations. Knowledge and Process Management, 26(2), 152–162. https://doi.org/10.1002/kpm.1590
Sahoo, P. K., & Dehury, C. K. (2018). Efficient data and cpu-intensive job scheduling algorithms for healthcare cloud. Computers and Electrical Engineering, 68, 119–139. https://doi.org/10.1016/j.compeleceng.2018.04.001
MN621 Advanced Network Design Assignment Sample
Students are required to use an industry case study of your PBL exercise to complete the assignment. It is to note that this assignment consists of two parts a) Assignment 1a and b) Assignment 1b. You have to discuss your chosen case study with tutor in week 1 and 2. Make sure to design your own case study if possible to avoid Academic Misconduct.
Assignment 1A
1. Project Scope and Report Requirements
The project scope and requirement should have a detail explanation of the planning and designing of a network. It is recommended that bullet points are included whenever necessary. Use your Problem Based Learning (PBL) tutorial findings.
The Following is The Scope for Assignment 1a.
• Attach your chosen real world business case study with reference as an appendix A.
• Include points that you have gathered from your chosen case study on their existing network.
• Discuss in a tabular form how the information obtained will be useful in designing the network.
• Discuss the approach you will be taking (include bullet points whenever necessary) to redesign the network.
Assignment 1B
The Following is The Scope for Assignment 1b.
2. Response to Assignment 1a
• It is mandatory that students should demonstrate how they have incorporated the feedback given in assignment 1a. You may use a tabular form whenever necessary.
3. Network design and justification
• Draw a network design that you think will be useful in the future for the industry that you have visited. Network should include the following requirements:
o 3 routers
o 4 switches
o 10 PCs
o 4 VLANs.
• Suitable IP addressing scheme in tabular form (assume as many hosts as necessary for each department). Use your MIT student ID to come up with your own IP addressing scheme (to avoid Academic Misconduct). Justify the choice of IP address.
• Indicate where do you use static routing, dynamic routing protocols (name the protocols, RIP, EIGRP, OSPF, etc.), Access Control List (ACL) as per the network preferences. Justify your choices.
4. Network Configuration
Configure your network using Packet Tracer. Write a report on
• Packet Tracer Network diagram- Copy diagram from your simulator
• Switch configuration
• Router configuration
• Host configuration
• Access point and server configuration guidelines.
5. Timeline and Budget Estimation
This section should include the followings:
• Hardware requirements with the specification with costs
• Human resources and logistics
• Tentative timeline specifications.
Solution
1. Project Scope and Reporting Requirements
Crystal Point is a luxury building. It has 69 units, 24-hour security, a concierge, facility of fitness, & a year-round heated pool & all with 360-degree the mountains & city's views. Despite that, HOA (Homeowners Association) of Crystal Point discovered that one crucial amenity, Internet & Wi-Fi services, was falling short of residents' expectations. As a result of such problem, the residents receive an unsettling WIFI service, & the surveillance system is malfunctioning. As a result of these hassles, resident’s complaints are on the rise, as is the risk to security. Crystal Point needed a strong and dependable Internet & Wi-Fi solution since homeowners were complaining on a daily basis. Company wanted a high-end, Internet solution & fully managed Wi-Fi that was perceptibly superior in terms of dependability & quality than service provided by regular service provider.
The requirements of the crystal point are as follows:
• A network that could grow to handle rising demand from an increased number of people & devices
• Ensure secure & high-bandwidth internet connection is provided to the residents.
• Safe & secure connections in any area within the facility's footprint.
• A wireless & wired solution that was convenient to use.
Network configuration & system network up-gradation are critical for fixing the problem. For resolving the inadequate connectivity's issue, the system's each components, such as switches & host routers, must be upgraded. Changing the entire network system is not straightforward for the crystal point[1].To resolve all these issues, the solutions are as follows
• SmartZone controller was utilized for managing the APs & ease network management as well as set-up.
• Installed an R510 indoor AP in each condo unit.
• ICX switches were utilized to create a dependable wired & wireless network.
The benefits of redesign network are as follows:
• During boosting signal strength & wireless reliability, enhanced the several concurrent clients assisted per access points.
• Flexible & quick-to-respond service of customer.
• A complete controlled, actively controlled solution.
• Simplified network set-up and management, boosted security, minimized troubleshooting, & made updates simple Reliable, trouble-free Internet service fit for a high-end, luxury establishment
Useful Information To Redesign The Network
|
Current Status |
Status of network |
Bandwidth |
|
|
Email communication |
inadequate |
Up gradation needed (old) |
The AP's firmware is outdated. |
|
Voice chat for conference |
inadequate |
Up gradation needed (old) |
Old ADSL connection |
|
Video chat for conference |
inadequate |
Up gradation needed (old) |
Old ADSL connection |
|
Residence |
inadequate |
Up gradation needed (old) |
Old ADSL connection |
|
Working conditions |
inadequate |
Up gradation needed (old) |
Old ADSL connection |
|
Safety measures |
inadequate |
Up gradation needed (old) |
Don’t set a security policy. |
Approach To Redesign
The above issues in the network of crystal point are solved by Ruckus’ ICX switching & wireless access points (APs) through reconstructing the system network and for good performance:
• Using wireless access points (APs) & ICX switching of Ruckus, It allows giving residents of Crystal Point with consistent Wi-Fi reliability & greatly increased services.
• The Dual Path suggested a Cat6 & fibre infrastructure to provide Crystal Point residents with a much enhanced Internet experience.
• In each condo unit R510 AP & ICX switches installed, & a SmartZone 100 that manages & controls the Wi-Fi network makes up the solution.
• The SmartZone Wireless LAN controller & Ruckus ICX switches work together for making network management & setup easier, improve security, reduce troubleshooting, and make upgrades simple.
• Continuous Wi-Fi coverage is provided by the Ruckus R510. The exceptional RF (Radio Frequency) performance is provided by the APs provide.
• Automatic interference mitigation & a two-stream MIMO 2x2:2 are included in the Ruckus R510 APs, ensuring constant, predictable performance.
• The R510 is ideal for crowded device situations, with data rates up to 1200 Mbps.
References
[1] "Network Design and Management Overview", Copyright 2000–2014, [online] Available: http://www.bitpipe.com/netmgmt/netmgmt_overview.isn
[2] "Putting Technology to Work Providing Business Solutions", Valley Network Solutions, 2014, [online] Available: http://www.vns.net/services/infrastructure/index.htm.
[3] Cisco design model of a network, [online] Available: http://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Campus/Hcampus_DG/hacampusdg.html.
[4] J L Marzo, C Vaz de Carvalho, L Schoofs, R Van Steenberghe, S Knockaert, J Salonen, et al., "European Study Programme for Advanced Networking Technologies (ESPANT) EDULEARN" in , Barcelona, July 2009.
[5] CRYSTAL POINT. Luxury Living Condos Receives Top Technology Amenity 2012.
DATA4000 Introduction to Business Analytics Assignment Sample
Assignment Brief
Word Count - 2000 Words (+/-10%)
Weighting - 30 %
Total Marks - 30
Submission: via Turnitin
Due Date - Monday Week 5, 23:55pm AEDT
Your Task
Complete Parts A to C below by the due date. Consider the rubric at the end of the assignment guidance on structure and content.
Assessment Description
• You are to read case studies provided and answer questions in relation to the content, analytics theory and potential analytics professionals required for solving the business problems at hand.
• Learning outcomes 1 and 2 are addressed.
Assessment Instructions for assignment help
Part A: Case Study Analysis (700 words, 10 marks)
Instructions: Read the following two case studies. For each case study, briefly describe:
a) The industry to which analytics has been applied
b) A potential and meaningful business problem to be solved
c) The type of analytics used, and how it was used to address that potential and meaningful business problem
d) The main challenge(s) of using this type of analytics to achieve your business objective (from part b)
e) Recommendations regarding how to be assist stakeholders with adapting these applications
for their business.
1. Artificial Intelligence in Germany: Reinventing Engines of Growth
https://www.bernardmarr.com/default.asp?contentID=2141
2. GE Power: Big Data, Machine learning and ‘The Internet of Energy’
https://www.bernardmarr.com/default.asp?contentID=1226
Part B: The Role of Analytics in Solving Business Problems (500 words, 8 marks)
Instructions: Describe two different types of analytics (from Workshop 1) and evaluate how each could be used as part of a solution to a business problem with reference to ONE real-world case study of your own choosing. You will need to conduct independent research and consult resources provided in the subject.
Part C: Developing and Sourcing Analytics Capabilities (800 words, 12 marks)
Instructions: You are the Chief Analytics Officer for a large multinational corporation in the communications sector with operations that span South East Asia and Latin America. The organization is undergoing significant transformations; it is scaling back operations in existing low revenue segments and ramping up investments in next generation products and services - 5G, cloud computing and Software as a Service (SaaS). The business is keen to develop its data and analytics capabilities. This includes using technology for product innovation and for developing a large contingent of knowledge workers.
To prepare management for these changes, you have been asked review Accenture’s report
(see link below) and publish a short report of your own that addresses the following key points:
1. How do we best ingrain analytics into our decision-making processes?
2. How do we organize and coordinate analytics capabilities across the organization?
3. How should we source, train and deploy analytics talent?
To help you draft this report, you should review the following working paper from Accenture:
https://www.accenture.com/us-en/~/media/accenture/conversion-
assets/dotcom/documents/global/pdf/industries_2/accenture-building-analytics-driven-
organization.pdf
The report is prepared for senior management and the board of directors. It must reflect the needs of your organization and the sector you operate in (communications).
Solution
Part A: Case Study Analysis
A. The industry in which analytics has been used
The case studies concern themselves in two different aspects of analytics. The case study named 'Artificial Intelligence in Germany: Reinventing Engines of Growth' deals with the artificial intelligence analytic. Another case study named GE Power: Big Data, Machine learning, and 'The Internet of Energy' is related to block chain analytic. In the case study concerning artificial intelligence, several industries are introduced to use artificial intelligence analytics. Germany introduced AI in its traditional businesses at first. Company Otto, a giant E-commerce company, uses AI for analytics implementation (Marr 2020a). Another company Zalando, an E-tailer organization, uses AI for the performance management of the machines. Germany's largest railway infrastructure provider company Siemens AG uses AI for its railway infrastructure analysis (Marr 2020a).
Moreover, the automobile companies such as BMW and Daimler also use AI technology in their autonomous vehicles. Allianz Insurance company utilizes AI analytics (Marr 2020a). Also, Braun uses AI in its digital toothbrush making, where the AI technology will help to implement proper ways to brush the teeth. Media Conglomerate Bertelsmann hosted AI for solving data and AI challenges in business (Marr 2020a). Another case study related to block chain analytics targets the health care industry to solve the issues in operational management (Marr 2020b). MedRec uses block chains to improve electronic medical records, allowing patients' information to be accessed securely (Marr 2020b).
B. The potential and meaningful business problem to be solved
The possible and potential issues can be solved through strengthening AI research, using a competitive market to drive innovation for encouraging SMEs to use AI in business structure. The e-commerce company Otto has the problem of product returns in its online commerce market (Marr 2020a). Zalando has been facing the issue of fraudulence in the e-tailer system. Siemens AG wants to avoid the issues of delay in trains arrival. To promote reliability and accuracy is the target. BMW and Daimler are facing issues in traditional man-driven vehicles. For operational efficacy improvement, Allianz Insurance uses AI (Marr 2020a). Bruan targets healthy habit which is reasonably related to clinical activities to prevent teeth problems. Bertelsmann has faced challenges in business. The case study concerning block chain analytics corresponds to various issues related to health information. The case study shows around 140 million patient's records have been breached between 2015 to 2016 as per the report of the Protenus Breach Barometer (Marr 2020b). IT architecture is struggling to secure systems. It becomes an issue to generate and record data in disparate systems through any human. Medicare fraud is also an issue. They reduce the counterfeit drug application costs high to pharmaceutical companies, which have created a loss of $200 million (Marr 2020b). The issues such as waste of time, duplication in process, money, confusion, and life-threatening are related to MediRec.
C. The type of analytics used and how it was used to address that potential and meaningful business problem
Artificial intelligence and blockchains are the analytics used. Germany introduced AI to solve the operational issues related to products and services (Marr 2020a). The government wants to become one of the leaders of global technology. For that, business organisations in Germany focus on quality over quantity as the competition relating to AI technology is high in the global market. AI can benefit the citizens in Germany to experience a high level of IT security. For that, AI technology must be implemented legally and ethically. Otto uses algorithm processes in online activities to decrease product returns (Marr 2020a). Zalando uses AI to prevent fraud in the e-tailer system. The automobile vehicle companies BMW and Daimler use AI to produce autonomous vehicles to solve the prevalent issue. Bertelsmann uses AI to develop intelligent solutions to avoid possible issues in business (Marr 2020a). The teams focused on various tasks such as voice-controlled search functions, automated podcasts, listening recommendations. Higher privacy and security provision are agendas to use block chain analytics (Marr 2020b). Block chain infrastructure can be a possible solution to minimize the risk of patient record breaching. Block chain helps to disparate the systems for future treatment. Reducing the counterfeit drug application costs high to pharmaceutical companies can be managed through block chain (Marr 2020b). To deal with the issues such as waste of time, duplication in process, money, confusion, and life-threatening issue, MediRec applied block chain (Marr 2020b).
D. The main challenges in using the analytics to achieve business objective
The challenges concerning utilizing analytics such as artificial intelligence and block chain to achieve the business goal can be customer dissatisfaction, driver downtime, and reducing maintenance costs. Moreover, the issues regarding data security and privacy are a significant concern in both AI and Block chain. Artificial intelligence helps in securing the system from fraudulent transactions, but the barrier is to handle the system. For that, organisations need to hire IT experts, which will make the organisations bear additional costs. Kroger, while using artificial intelligence to Restock Krogers, can face significant challenges. Among them, data security while the transaction is a significant issue.
Furthermore, record tracking, sharing, assigning, and linking can be faced while using the blockchain analytic. For instance, Meta Capital has been facing challenges while implementing the blockchain technology in partnership channel with ConsenSys Config. Blockchain is used to reduce delay in banking sectors, but the cost of blockchain operation is high.
E. Recommendations regarding stakeholders’ assistance
Managing the business objective through using analytics needs to assist the stakeholders about application adaptation.
• Training regarding analytics such as artificial intelligence and blockchain is a must for the stakeholders.
• The stakeholders need to engage themselves with IT experts to know the system management through analytics.
• Discussion regarding the aim or objective with the stakeholders through meetings and conferences can be practical.
• The stakeholders need to know about the transformations after implementing the analytics in the system.
• Awareness must be created regarding the need for innovation to achieve organizational success.
• Training regarding privacy and security maintenance must be given to the stakeholders while operating through analytics.
Part B: The Role of Analytics in solving Business Problem
Analytics has immense contribution to business due to its ability in identifying problems and providing new opportunities to solve these problems. Analytics not only help in making business decisions but also in identifying opportunities to engage a more significant number of customers. In the case of Artificial intelligence, it is used to make a market survey and identify customer requirements by trend analysis. The critical business decisions regarding the product that needs to be more highlighted or updated and suggesting the products according to customer needs are made through artificial intelligence. Business analytics is also helpful in dealing with logistics issues where several shipping companies use analytics to keep track of their fleet. The sensor devices will help diagnose the problem in parts of the ship, which will reduce maintenance cost, driver downtime and customer dissatisfaction. Predictions related to internal problems within the organization can be solved through predictive analytics that helps in identifying the issues, predict what will happen in future through past data and make suggestions or recommendations accordingly (Michigan state university online 2020). Artificial Intelligence is making its mark in business organizations for dealing with issues like data security and fraudulent transactions for giving more safe and secured solutions in the business.
Nowadays, many online transactions occur through mobile phones using the internet, where personal data is shared constantly. Kroger using Artificial Intelligence in their initiative Restock Kroger where the shoppers are allowed to scan groceries through their smartphone using AI. They have also planned for an autonomous vehicle for delivery in partnership with Nuro, Silicon Valley Company. They are also planning to have robotics in their operations to design an automated warehouse where robots using Machine learning algorithm can select products for delivery from warehouses. Using smart shelves technology, customers will be given suggestions based on their choice and price demands. Machine learning will help in the deployment of several models without human interventions (Bernardmarr 2020). The data transfer process is speedy, and companies face a massive challenge in dealing with the security problem. Using Artificial Intelligence, the process of transaction scanning for potential fraud detection takes place at a fast rate, making the system more secure. Block chain technology is used in supply chain management where asset recording, tracking, sharing, assigning and linking makes it efficient, giving more transparency and better protection at every step. For example, Mata Capital has partnered with ConsenSys Config to leverage its assets by introducing security tokens using block chain technology. It has helped in better dealing with customer requirements, cost befits, more security in transactions, and business expansion to a new class of investors (Consensys 2020). block chain is used in several banking sectors to assist in cross-border transactions and reduce delay. The processing taking place in real-time ensures more security and restricts any securing them from any modifications. Data security is also a significant issue in the business where the personal data of customers and sensitive information of organizations are stored in large databases, which is prone to any security breach and malicious attack. Blockchain-enabled security systems are more effective as any attack has done to blockchain-based data storage will be fatal, and there is no way of tampering or stealing the data (Goodfirms 2021).
Part C: Developing and Sourcing Analytics Capabilities
1. As a chief analytics officer in the communication sector, it can be asserted that including analytics in the decision-making process is significant, which helps to manage the service changes. For infusing analytics in the decision-making process, CPG leaders addressed the business issues initially and then defined the data (Hernandez, Berkey & Bhattacharya 2013). After this process, they reengineer decisions for result analysis and insight. CPG focuses upon rare skill development for ingraining analytics into decision-making processes. The cross-functional process is also effective as it helps the business produces a greater return to analytics capabilities. It also enhances the price, promotion, and assortment efficiency. CPG enhances speed and end-to-end process assessment in decision making, which helps to infuse analytics in business decision making. In the decision-making process, changes for enhanced performance need fact-based discussion and action in brand marketing, field sales, supply chain, and sales planning. Reengineering the decision-making process in business will help to function the analytics-driven process in business. Analytics promote quicker decision-making abilities. Also, the organisations have to analyze their ability to manage the reengineering process. For example, P&G company uses data-driven culture and innovative tools like the business sphere to infuse analytics in the decision-making process (Hernandez, Berkey & Bhattacharya 2013).
Conducting an analytics diagnosis process will help to identify the type of insight needed and also determines who and when will develop the insight so that timely delivery can be possible. Organizational changes that enhance the value of Analytics and visibility are also required. Consistent and deliberate typing strategies and tactics will generate insights from Analytics. Analytics services aim to reach enterprise business goals which involve the prioritizing process.
2. Managing transformation in business due to technological inclusion needs to have organization and coordination analytics capabilities across the organization. The closest positioning to decision making and delivering the most value includes analytics insight development. Organisations construct and allocate resources based on business needs and maturity. Managing supply and demand for analytics services across the business is crucial. The fundamental organizational issues such as sponsorship, leadership, funding, and governance are addressed to extract value from analytics (Hernandez, Berkey & Bhattacharya 2013). For maintaining the balance of demand and supply, sponsorship helps to create benefits of analytics to whip up energy and confidence. The view of enterprise helps in making required decisions that benefit the organization. The ultimate objective of the sponsor is to accelerate adoption and buy-in within the organization. Sponsors need to be an astute leader in breaking the cultural barriers to disseminate data widely.
The leadership in organisations creates a considerable impact on the coordination of analytics capabilities. Analytics leaders encourage vision regarding the capabilities of them the organization in holding people accountable for the result. The leader has to build analytics capability in culture and improves the decision-making process. Funding comes from various sources or functions. In proportion, function puts on priority upon Analytics. The funding promotes the capabilities of analytics. It increases simultaneously with the proportion of analytics in the organization. Funding in organisations would signify the strategic value of Analytics which generates, preserving the point of migrating to a pay-to-play model (Hernandez, Berkey & Bhattacharya 2013). The pay-to-play model creates the ability for the functional executives for integrating Analytics insight development into business decisions. Due to the increment in adoption, resources become more appropriate.
Governance involves the ownership of analytics and the capability to manage demand and supply. Different roles and responsibilities correlate with the governance structure. The initial considerations involve the maturity of analytics capabilities, priorities of the organization, and the need to balance demand and supply. The centralizing model helps to grow demands for analytics. The Federated model also works when there is high demand in analytics, including the SWAT team to manage complex cross-functional decisions. (Hernandez, Berkey & Bhattacharya 2013) Governance reduced duplication KPIs establishment is done for the central and dispersed teams. Finally, Analytics resources provide capability development opportunities. Stakeholders' engagement in the analytics process is also significant for supply and demand management. Management of demand helps to identify, prioritise and service the highest value opportunities.
3. Sourcing, training, and deploying analytics talent includes several aspects regarding talent management. The seven components used to shape an appropriate operating model are sponsorship and governance, organizational structure and talent management, data of insights, capability development, Insight-driven decision, outcome measurements, and information and data management. Organisations for understanding the talent needs will use analytical skills. In that case, an analyst is needed who will understand the distribution network. CPG companies tend to have talent in descriptive Analytics (Hernandez, Berkey & Bhattacharya 2013). The company needs to generate predictive and prescriptive insights. Talent sourcing is another aspect that can be done in a variety of ways. The public-private partnership is effective in resourcing as universities like MIT invest in data science degree programs for talent sourcing. Even Google, Microsoft, and Amazon are supporting the programs related to Analytics for talent sourcing. Alternative arrangements can provide a dedicated capacity of analytics talent (Hernandez, Berkey & Bhattacharya 2013). Flexibility and capacity promote lower costs in comparison to the internal hiring process. Capacity development involves business skills to remain relevant with strategic management. It also includes executive-level skills. Ability to manipulate, find and interpret and manage the data help in developing capacity. Talent management requires a new approach beyond the standard career improvement. For instance, CGP needs to work hard to create a path that will retain the analytics talent.
References
Bernardmarr 2020, Kroger: How This U.S. Retail Giant Is Using AI And Robots To Prepare For The 4th Industrial Revolution, viewed 19 April 2021, <https://bernardmarr.com/default.asp?contentID=1537>.
Consensys 2020, Codefi Case Study Download: Mata Capital, viewed 19 April 2021, <https://pages.consensys.net/codefi-mata-capital-case-study>.
Goodfirms 2021, ‘Top 10 Problems that Blockchain Solves’, viewed 19 April 2021, <https://www.goodfirms.co/blog/problems-blockchain-solves#:~:text=One%20thing%20is%20certain%20now,charity%2C%20voting%2C%20and%20crowdfunding>.
Hernandez, J, Berkey, B & Bhattacharya, R 2013, Building-analytics-driven-organization. viewed 19 April 2021, <https://www.accenture.com/us-en/~/media/accenture/conversion-assets/dotcom/documents/global/pdf/industries_2/accenture-building-analytics-driven-organization.pdf>.
Marr, B 2020a, Artificial Intelligence In Germany, viewed 19 April 2021, <https://www.bernardmarr.com/default.asp?contentID=2141>.
Marr, B 2020b, This Is Why Blockchains Will Transform Healthcare, viewed 19 April 2021, <https://www.bernardmarr.com/default.asp?contentID=1226>.
Michigan state university online 2020, How Business Analytics Can Help Your Business, viewed 19 April 2021, <https://www.michiganstateuniversityonline.com/resources/business-analytics/how-business-analytics-can-help-your-business/>.
MIS300 Systems Analysis & Design Assignment Sample
MIS300 The Assignment Help Case Study
Online Restaurant Pre-order System
Rajesh’s Roti Kitchen has always done a roaring trade in tasty treats. Not only do people drive across the cityfor their roti but their sweet meats are highly prized, especially the burfi and jalebi. The Roti Kitchen has a CRM system and customer loyalty program with discounts and special offers, but at peak times it is too busy to sign the customer up at the till and staff make typos on mobile phone numbers and email addresses. Rajesh is seeking to develop an online ordering system (the system). He has seen several pre-order applications from established fast food chains and has some ideas about what he wants from this system. You have been engaged as the Business Analyst on this project. The system should allow Rajesh and his team to create, edit and remove menu items based on festivals and seasonal ingredient availability. Customers should be able to sign up, review the menu, place an order, and pay. Pre-ordering online will allow customers to take advantage of special offers and receive discounts. Customers should be able to access the system from a device of their choice, whether it be their PC at home, a tablet, or their phone. This will allow Rajesh to take the pressure off the queue and get more staff into the kitchen. Customers should be able to create, edit or remove items from their order up until completion of the order. At completion of the order, the system must generate on invoice and prompt the customer to a secure payment process, after which it confirms the order. Confirmation of the order must trigger an SMS to the customer’s phone indicating when the order will be ready for pick-up. Rajesh is very eager to have the capability to report on various aspects of his business and in particular would like to understand how popular various items are on the menu and whether there are times where some items are more popular than others.
For this assignment, students need to individually write a 1500-word business report in response to the provided case study. There are two components:
1. Conceptual questions about the role of business analysts and the tasks they undertake to support the systems analysis and design process.
2. Practical questions in response to the provided case study: MIS300 AssessmentCase Study. Please refer to the Task Instructions for details on how to complete this task. Context Requirements analysis is one of the primary roles of a business analyst; the business analyst helps stakeholders identify their needs. You will be expected to support users by eliciting their requirements of a system that is being built or modified and document these requirements in a way that is clear to stakeholders, ensuring user needs can be understood and met.
Task Instructions To complete this task, you must:
1. Carefully review the attached MIS300_ Assessment _Case Study.
2. Review your subject notes, essential readings and learning activities to ensure that you are well prepared for the assignment.
3. Create a report plan and identify all the key components required in your report. 4. Follow the outlined report structure: Note: The report is brief and therefore will not require an executive summary or abstract.
Title page: should include subject ID, subject name, assignment title, student’s name, student number and lecturer’s name.
Table of contents: include all key components of this assessment. Introduction (75–100 words): This serves as your statement of purpose. You will tell the reader what you are going to cover in your report. You will need to inform the reader about:
• your area of research and its context
• the key concepts you will be addressing
• what the reader can expect to find in the body of the report.
Body of the report (800–850 words):
Conceptual questions: • What is your understanding of the role of a business analyst?
• Why is requirements analysis important for the success of a system build or modification?
Practical tasks:
• Identify the stakeholders for this project
• Identify the actors in this system?
• Identify and list 2 major functional requirements for the system
Identify and list 4 non-functional requirements of the system. Include the reasons why you identified these particular requirements.
• Build a set of use case diagrams for the system using Lucidchart or any other diagramming app, such as app.diagrams.net.
• Based on the use case diagrams, develop and document two elaborated use cases. Each use case documentation must include: – use case name – ID – priority – actor – description – trigger – precondition – normal course – alternative courses – post conditions – exceptions. Layout: • The report should use Arial or Calibri 11-point font and should have 1.5 line spacing for ease of reading. A page number must be inserted on the bottom of each page.
• With the required diagrams, due attention should be given to pagination to avoid loss of meaning and continuity by unnecessarily splitting information over two pages. Diagrams must carry the appropriate captioning. Conclusion (75–100 words): summarise any findings or recommendations that the report puts forward regarding the concepts covered in the report.
SOLUTION
Introduction
According to Keller Andre? (2019), requirement analysis or requirement engineering is the process of defining user expectations for a new software being created or changed. It is also called requirements gathering or requirements capturing in software engineering. It identifies, analyses, and models the functionality of a prospective software system the requirements are modelled after analysis with the help of Unified Modeling Language Diagrams, Entity-Relationship Diagrams, Data Flow Diagrams, or formal methods. Through this case study, the researcher aims to analyze and discuss the techniques of systems analysis for enhancing the ability of Rajesh’s Kitchen to address their needs for the information systems. Also, the requirements for a variety of Rajesh’s kitchen’s information systems’ needs are being developed through this study.
Discussion
Conceptual Questions
Role of Business analysts
Business analysts mainly work with different organizations for getting assistance to improve the processes and systems. In other words, they hold a huge responsibility of bridging the gap between IT and business with the help of data analytics for assessing processes, determining the requirements and delivering recommendations driven by data. Moreover, on a regular basis, business analysts are responsible for knowing the change required in any business and finding out the implications of those changes (Gordon, 2017).
Thus, in the concerned case study, it has been observed that the role of a business analyst is quite essential. In order to introduce an online ordering system for Rajesh’s kitchen, the BA would analyze the structure of the business, involved processes and determine the key areas in which technology can help in adding value. Here, BA would work along with System analysts and hence find out the key challenges and their solutions (Paul & Lovelock, 2019). Furthermore, Business analysts would also help Rajesh to suggest the best technology and software tools for improving the operations of the business.
Importance of Requirement analysis
Requirement analysis is said to be an important aspect for organizations to determine the exact requirements of stakeholders. Meanwhile, it also helps the development team establish effective communication with the stakeholders in the easiest form. Therefore, it can be said that the main aim of such analysis is analyzing, validating, documenting and hence managing the requirements of the system. Requirements of high-quality are often documented, traceable, testable for identifying the opportunities within a business and hence facilitates the design for the same (Dick, Hull & Jackson, 2017).
In the concerned case study, requirements analysis will help Rajesh’s kitchen to introduce an online ordering system efficiently. Hence, it would be easier for Rajesh to identify the need of stakeholders in the entire lifecycle of an online ordering system.
Practical Tasks
Stakeholders for the project
?Figure 1: USE CASE for Online Ordering system
(Source: Created by the author)
Actors in this system
An actor in the system is responsible for specifying the role played by a user or other system interacting with the system. Hence, an actor can be a person, outside a system or sometimes an organization. In the given case study, the actors are customers, admin and payment gateways (Voirin, 2018). Customers here are responsible for creating an account, adding food items to the cart and then finally placing the order. Admin authenticates the entire operation carried out by the customer whereas payment gateways are responsible for making transactions.
Two major functional requirements
Two major functional requirements for the online food ordering system are registration and adding food items to the cart. Without registering the account, the user/customer may fail to order the food. Hence, at the initial stage, registration is important. Once, the process is over, the customer can add food items to the cart. Apart from these, other functional requirements are displaying the menu, modifying it, changing the order, reviewing the order before final processing and payment.
Four non-functional requirements
Four non-functional requirements are portability, reliability, availability and security. With the portability feature, the customer can use this application either on computer/PC/Laptops or mobiles (Garci?a-Lo?pez Dennys et al. 2020). Reliability will allow the system to behave consistently in a user-acceptable manner at the time of operating with the environment for which the system is mainly developed. Availability requirements allows the system to be available at all times. This means that customers can access the application with the help of a web browser. Security with help in ensuring the confidentiality of the user’s bank details.
Use Case Diagram
Here, a use case for the online food ordering system for Rajesh’s kitchen has been developed. With the help of this design, the researcher tried to show the interaction of various users with the proposed system. From the diagram, it can be observed that there are three actors actively involved in the system. Each one of them plays a significant role.
.png)
Figure 1: USE CASE for Online Ordering system
(Source: Created by the Author)
Use Case Documentation
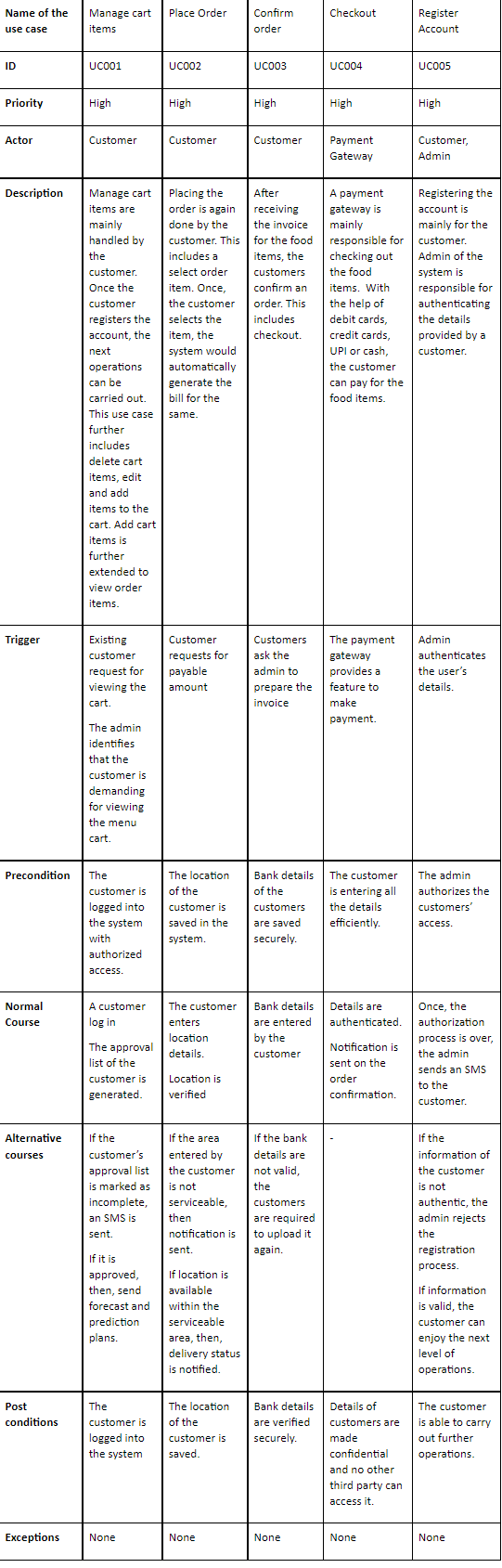
Table 2: Use Case Documentation
(Source: Created by the author)
Conclusion
From the comprehensive study, it can be concluded that requirement analysis has helped Rajesh’s kitchen to determine the actual requirements of the stakeholders of the organization. Moreover, it can be seen that requirement analysis enabled the development team of Rajesh’s kitchen to communicate with its stakeholders in a language they understand like charts, models, flow charts instead of text pages. The overall study focused on identification of stakeholders and their role in the system. In this study, the researcher designed a use case for showing the interaction of various users with the system. Moreover, the researcher also presented a brief documentation for the use case designed in this context.
References
Dick, J., Hull, E., & Jackson, K. (2017). Requirements engineering (4th ed.). Springer. Retrieved on 7th March 2021 from: https://doi.org/10.1007/978-3-319-61073-3
Garci?a-Lo?pez Dennys, Segura-Morales, M., & Loza-Aguirre, E. (2020). Improving the quality and quantity of functional and non?functional requirements obtained during requirements elicitation stage for the development of e?commerce mobile applications: an alternative reference process model. Iet Software, 14(2), 148–158. Retrieved on 7th March 2021 from:
Gordon, K. (2017). Modelling business information : entity relationship and class modelling for business analysts. BCS, The Chartered Institute for IT. Retrieved on 7th March 2021 from: https://lesa.on.worldcat.org/oclc/1004319314
https://doi.org/10.1049/iet-sen.2018.5443
Keller Andre? A. (2019). Multi-objective optimization in theory and practice ii : metaheuristic algorithms. Bentham Science. Retrieved on 7th March 2021 from: https://lesa.on.worldcat.org/oclc/1097974294
Paul, D., & Lovelock, C. (2019). Delivering business analysis : the ba service handbook. BCS Learning & Development Limited. Retrieved on 7th March 2021 from: https://lesa.on.worldcat.org/oclc/1119617420
Voirin, J.-L. (2018). Model-based system and architecture engineering with the arcadia method (Ser. Implementation of model based system engineering set). ISTE Press.Retrieved on 7th March 2021 from: https://lesa.on.worldcat.org/oclc/1013462528
ITC508 Information Technology Assignment Sample
Assessment 2 - Inception and Elaboration Phase
Value: 25%
Due Date: 04-Apr-2021
Return Date: 27-Apr-2021
Length: 1500 - 2000 words
Group Assessment: No
Submission method options: Alternative submission method
TASK
You are provided with a case study about a business that needs the development of a modern information system to support its day to day operations. In your role as System Analyst, you will help the business in the development of the new information system. Please refer to the Interact2 Resources for the Case study; Read the detailed document and then complete the following task. You will use the same case study to complete assignment 2 and assignment 3.
Inception phase: 10 marks
In the inception phase of the project, your goal is to investigate the scope of proposed business information system in the given case study. To present your understanding of the project, you are required to submit a System Vision Document which includes the following sections
• Project Introduction
• Important system capabilities
• Perceived business benefits
• Resources required
• Stakeholder map
Elaboration phase: 15 Marks
In the elaboration phase of the project, you are required to prepare a report that elaborates the project requirements in detail and illustrate those requirements using UML models. For this purpose, you should attempt the following tasks:
• Identify use cases and draw use case diagram(s) for the new information system that shows major use cases and actors.
• Write one fully developed use case description for one of the important use cases identified. Select an important use case that is a key part of the system, not a basic simple one.
• Draw the UML domain model class diagram(s) for the new information system. Be as specific and accurate as possible, given the information provided. If needed information is not provided, make realistic assumptions.
RATIONALE
This assessment task will assess the following learning outcome/s:
• be able to explain and apply the concepts of object orientation methodology.
• be able to describe the relationship of analysis and design activities to the System Development Life Cycle (SDLC).
• be able to analyse a case study and construct a business proposal to argue the feasibility of a client software proposal.
• be able to analyse system requirements to determine the use cases for the creation of a domain model of the problem domain.
• be able to create analysis and design diagrams with UML notation.
• be able to model various aspects of systems to construct quality diagrams for use in a system development project.
Case study for assignment help
Vallée de Goût’ is a French cuisine restaurant located in outer suburbs Sydney, offering a luxurious and contemporary fine dining experience. Thanks to maintaining their quality standards, their business has been growing steadily. But for the past few months their venue has been getting overcrowded during weekends.
This has impacted the customer service quality, for example, due to delays in order preparation, mistakes in orders or bills etc. The management firmly believes that an existing customer is worth more to a businessthan a new customer, because the cost to attract a new customer can be multiple times higher than the cost to retain an old customer. A customer is likely to return to a restaurant, if they receive an excellent customer service as well as appetising food. However, the restaurant would easily loose the customers if they have to wait for an unreasonable amount of time or there was a mistake in their order.
To solve these problems, firstly the management has convinced ownersto relocate to a bigger venue nearby. Secondly, the management would like to upgrade to a sophisticated information system at the same time. Their current information system has become a hurdle in smooth business operations because of very limited features. For the past two weeks, the business manager has been evaluating multiple off-the-shelf systems for Vallée. But he came to the conclusion that all of those systems are quite generic; those will require excessive
customization to adapt to some of the Vallée requirements, while lacking some important features. Therefore the restaurant manager have decided to get a custom integrated system developed that better fits their business needs. Your company ‘Hospitality Innovations’ has won the contract Vallée’s software on the basis of extensive experience in developing restaurant related softwares. You and your team have had several meetings with restaurant staff and they have communicated to you their system requirements. You were provided an opportunity to observe day to day restaurant operations, and then interviewed all the potential users of the proposed system (managers, cooks, waiters etc.) in order to get as clear idea of the requirements as possible.
Once you got a clear idea of the system requirements, you propose the new information system to be named iDine. The management liked your name and asked you to describe how the system would work. You wrote a detailed description as below, providing a vision of system working in full capability. Your team will now help Vallée convert this vision into reality. Getting inspiration from touchscreen self-ordering kiosks used by fast food restaurants, Vallée wantsto apply a similar concept (to some extent) in the fine dining. For this purpose, all tables in restaurant are to be equipped with tabletop tablets. These tablets display their detailed digital menu and allow customers to place and send their orders directly to the kitchen. This potentially saves time because customers do not have to wait for a server, especially during lunch or dinner rush hours. Furthermore, while enjoying their meals, customers can use this system to quickly order an extra drink or an additional plate. Plus, since customers can dig deeper into the menu to discover more add-ons and extras than any waiter could recite, orders can be customized as per customer wishes. As an added bonus, some tabletop tablets come loaded with games and entertainment to keep kids busy while their parents are chatting waiting for the order.
Customers who are not tech savvy enough to use those tablets, can just tap the “Call waiter” button to order the old school way. There is main terminal located in the dining room that is overseen by the head waiter. This machine would display a prominent notification of which table is requesting the waiter visit. The head waiter can then direct one of the available waiters to that table to collect the order. The waiter keys-in the order details into the system via a handheld tablet. The table number is also recorded in the system along with the order details. Whichever way an order is placed (customer self-order or through waiter), the system
categorizes the individual items in the order according to the section where they are prepared, and then route the suborders to printers in the appropriate preparation area. For example, to the printer in cold section if ordered item is a salad, to the cafe printer if it is a coffee or sandwich, or to the main kitchen if order is from the main course menu. This ordering system eliminates any problems caused by a waiter’s handwriting. In each
preparation area, the cooks have access to a large touch screen display that shows all orders that are yet to be served. Once an order is ready, a cook will mark the order as ready, which will send a notification to dining room terminal along with the table number. The head waiter then instructs one of the waiters to pick up the order from kitchen and serve to customers.
After the customer have finished with their meal, they can see their final bill on the same tabletop tablet. Alternatively the waiter can print out the bill from the main terminal for any given table number. Other than customer order management, iDine is also composed of several other subsystems like pantry and fresh produce inventory management, and supplies ordering management. Although the inventory system provides a lot of benefits as described later, but it doesimpose a strict data entry requirement. Every item added to inventory must be keyed in to the system. Similarly every item used up from inventory must be recorded. To simplify these tedioustasks, the inventory system is linked together with customer ordering system and
supplies ordering system. A workflow is designed like this: All the supplies are ordered through the supplies ordering system. When those supplies are delivered to the restaurant, a staff member keys- in the details of everything added to inventory. Most of it is same as the supply order, so the information is automatically copied over using the supply order number, but staff can adjust the details if the delivery does not exactly match supplies order.
To keep track of supplies consumption, the iDine estimates how much inventory the restaurant should have on-hand based on the items sold. This is possible because ahead of time when the restaurant menu is designed, the chefs provide a list of ingredients (fresh produce or grocery items) required for every single item on the menu. Therefore, as soon as customer orders are served, the inventory system uses to recipe to record an approximate deduction for every ingredient present in the order. This way the system keepstrack of actual
product counts, and also monitors theoretical inventory levels. The inventory system therefore provides a clear information of stock availability for every asset. Management can view inventory counts any time for greater efficiency and accuracy. Because the system can only estimate stock consumption (based on recipes), real stock counts need to be verified by the staff at the end of the day. A comparison of the estimated vs actual stock counts can alert managers to discrepancies from over-portioning, waste, and theft so that they can be
resolved immediately.
Another benefit of linking inventory management and customer ordering is that when the kitchen runs out of a food item, the cooks will use the kitchen terminal to record an ‘out of stock’ status. This will be helpful for waiters when taking orders. If an item can’t be prepared because one or more of the ingredients are out of stock, the waiters can immediately apologize to customers, enabling them to provide a better customer service. Similarly the customer tabletop tablets will disable ordering of such items, indicating the same reason on the screen.
An automated stock control is done by the inventory system and a report is readily available showing which items are currently available in stock and which of them need to be ordered from suppliers. This greatly reduces the chances of mistakes by staff members and they do not have to remember what is to be ordered. Previously staff had to handwrite a list of all ingredients that were out of stock at the end of every night shift. It was always not that productive as there was a very big possibility on missing out some of the ingredients. Using the automated reports, managers can manually place an order of supplies to be delivered the next day before the restaurant opens. But manually preparing the orders is seldom needed because an even better automated purchasing system works most of the time. Linked directly to the inventory system, this subsystem notifies and alerts the managers about low product levels. This system intelligently suggests purchasing recommendations based on supplies (expected) delivery time, forecasted sales quantities, and predefined stock level thresholds. Managers can also enable automatic orders to placed whenever inventory reaches a certain threshold.
Sales analytics is part and parcel of every modern business and Vallée is no exception. To this end, the new information system provides up-to-the-minute reports on the food items ordered and breaks out percentages showing sales of each item versus total sales. This helps management understand which food items are popular in customers. This data isthen shared with chefs so that can tweak the recipes of unpopular items. In this way, menu is tweaked according to customers’ tastes. The system also compares the weekly sales revenue versus food costs, allowing planning for tighter cost controls. In addition, whenever an order is voided, the reasons for the void are keyed in by waiters. This may help later in management decisions, especially if the voids are consistently related to food or service. iDine is capable of generating different types of charts for sales information so that management can view statistics in numerous diagrams.
Another crucial business requirement fulfilled by iDine is managing customer feedback. This subsystem works in two ways. First, at the restaurant exit door, a special purpose computer is installed that provides five buttons and a small display. The goal of this device is to ask the customers a simple ‘How did we do today?’ question. The five buttons are labelled with emoji faces from ‘sad’ to ‘smiling’. Customers will only need to push one button which is acknowledged with a thank you displayed on screen. iDine collects all such feedback and
presents in the form of charts as needed. In case customers wish to offer a detailed feedback with comments, that option is also available. The bill receipts have a QR-code at the bottom which customer can scan with a smartphone camera. The QR code is unique to each customer, linked to their order information. Scanning it leadsto an online feedback form where user can leave detailed rating and comments. Later when management reviewsthe feedback, they will have access to order details as well so it is easy to understand and act upon customer complaints (if any).
Another convenience Vallée is proud to offer its customers is the real time space availability and wait time estimation. As soon a customer places an order, iDine records their table as busy and that way remaining space available in restaurant can be worked out and displayed on the company website, updated in real time. Similarly, based on the actual order placed, system can provide an estimate of preparation time which is intimated to customers via tabletop tablet or waiter. Furthermore this information is also to estimate how long queuing time is, for those arriving when the restaurant is full. To get a proper estimate of queuing time, iDine keepstrack of the average time customersspend from order to payment (because most customers leave right after payment). When restaurant is full, these average values are used to work out when the next table will get free.
Ever since iDine has been installed at Vallée, it has vastly improved the workers organization and teamwork. Management is happy with the post-sales analysis reports. The system itself is designed with a very user friendly, touch driven GUI. The system response time is incredibly fast; the staff do not come across any noticeable lags or delays when using it. All customer orders are logged in an archive for record keeping and analytics purposes.
Solution
Introduction
The following project is carried out to develop an information system for a restaurant, named as Vallée de Goût’. It is a French cuisine restaurant, located in outer suburb area of Sydney which serves both the contemporary and luxury dining experience. In order to cope with the rising business, the business needs adequate space which can be solved by developing the system management. Due to the long waiting time or getting delayed order, the existing venue gets overcrowded. So, the staffs feel difficulty in handling the loads of the customers. As a result, they serve delayed order and also make mistakes on orders and bills out of pressure. This type of mistake will impact on the reputation on the customer service of the restaurant and they will start losing the customers. Beside the quality food, they also want to improve the customer service by enabling a better information system.
The existing information system management of the restaurant has very generic features which needs to be customized in the new system. It will help the business to involve multiple touchpoints from customers to the staffs which removes the mistakes occur in the manual orders. The customers will be given with a tablet on the top of every table and they can book the orders by themselves from the list of a digital menu. The order will be sent directly to the kitchen and the cook can access it. It will make a clear communication between the customer and the restaurant by avoiding the mistakes of writing made by the waiter. The waiter gets the notification of serving the dishes from the head the supervision of head waiter who oversees the process and makes decision. It will also allow an old school way of order taking through the ‘call waiter’ button. The new system will be named as ‘idine’. Apart from these basic features, it will have several add-on features to engage the customers.
Key System Features
The ‘idine’ will have an automation system with the below listed functionalities:
Customer Service
• The system will have the functionalities of showing the current menu of the day and changing the menu digitally.
• The system will enable the customers to have both the self-ordering and order taking by the waiter.
• The system will enable the customer to change the order and adjust the bill.
• The system will be able to adjust with the changing price of the cuisine every day and also show the new offer as per the entry of the back-end staff (Salen, Gresalfi, Peppler & Santo, 2014).
• The system will have a customer registration which records the name and phone numbers of the customers along with their billing details.
• The system will have cashless online payment system which the accepts the online pay and tips of the waiters via net banking or payment apps.
• The system adds the extra requirement of the customers apart from the digitally saved menus which directly will be sent to the cooks.
• The system will have the feedback options where the customers can rate the service and also give their review.
• The system will ask the customer is their any service or feature they want changes.
• The system will offer many video games which will engage the customers and their kids until the dish is served.
Inventory Management
• The system will be able to provide the real time inventory stock to the kitchen manager as per every order.
• The stock information will be updated with the data entry requirement. Whenever a new order is placed, it shows the available ingredients for the recipe of a booked order.
• The system will automate a report concerning the used goods, leftovers and what needs to be filled up as per the recipe manager (Zhao Guibas, 2004).
• The system will also update the out-of-stock status.
Supplies ordering management
• The system will have a supply ordering management which sends orders to the suppliers by tracking the stock availability and the system automation has the ability to decide which stocks is required or need to be ordered. This reduces the chance of manual mistakes (Cassell & Hiremath, 2018).
• The automation purchasing system will enable the restaurant to buy the products at any point of time. It omits the night shift of the staffs who tracks the required supplies and orders. This automation process enables the restaurant to have the supplies on the next day morning. Also, the lists are free of manual error.
Perceived business benefits
• The idine will avoid the chance of data loss by the digital booking. So, the accuracy in the ordering, billing and inventory management will be perceived (Taylor, 2017).
• It will automate the process and saves the time of customers and the staffs. As a result, there will be no delayed orders or long queue in the booking. By delivering quick service, the restaurant will get rid of the problem of over-crowding.
• it will improve the efficiency of delivery and the overall process. So, the customer will be satisfied and customer retention is ensured.
• It will deliver a better customer service experience through the booking, billing and entertainment. So, customer attraction will be increased.
• The cashless payment system will deliver customer convenience with an assured paying with taxes.
• The finance management of the restaurant will be improved by calculating the total sales, purchase in supply management and leftover in the inventory.
Required Resources
The required resources of idine are:
Project manager
The project manager will select the roles and responsibilities of the team members; also ensure the essential items and tracks the required changes.
Software developer
The software developer will be responsible for writing the codes and develops the programme for idine.
UX designer
The UX designer will be responsible for designing the visual representation of the idine, including the branding of the web page.
UI designer
The UI designer is responsible for designing the functionalities based on the user interfaces and the user applications (Alencar, 2015).
Protype test team
The prototype test team will send the raw product of idine IS system to the test users. Based on their reviews the prototype of idine will be moderated.
Technical writer
The technical writer will write the uses of the idine system based on the description of the test users.
Stakeholder map
Vallée de Goût’ : this stakeholder is the client of this project who will send requirements and give approvals of idine.
Customer service team: the customer service team consists of the waiter, cooks, inventory staffs who are allocated for checking the booking details.
Admins: the admins are the head waiters, inventory manager, supply chain manager and kutchen manager who oversees the overall process in each domain, by the help of idine system and instructs their subordinate.
Customers
Customers are the active participants who uses the booking system in idine and enjoy the amusements.
Suppliers
The suppliers are the stakeholders who sells raw ingredients for the cuisines by the system generated process. They are also paid by this automated system.
Project team
The project team receives the requirements from Vallée de Goût’. They design, develop and deploy the iDine.
Stakeholder Map
Stakeholder Map
Elaboration phase
Use case diagram
Use case description
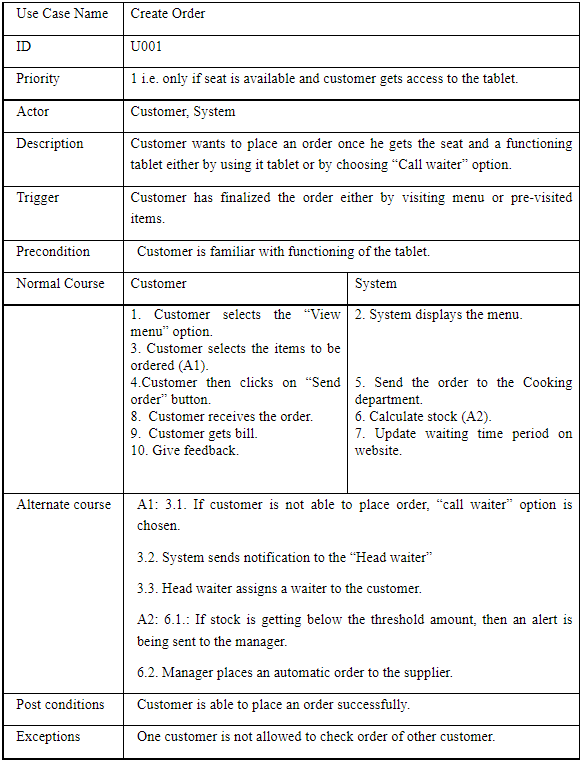
Domain model class diagram
The diagram has key classes: CUSTOMER, FEEDBACK, BILL, ORDER, ORDER_DETAILS, ITEMS, SUPPLIER, STAFF and REPORT. All the many-to-many relationships have been resolved using associative classes such as ORDER_DETAILS and SUPPLIER_ORDER.
References
Alencar, M. S. (2015). Information theory (Ser. Communications and signal processing collection). Momentum Press.
Cassell, K. A., & Hiremath, U. (2018). Reference and information services : an introduction (Fourth). ALA Neal-Schuman, an imprint of the American Library Association.
Taylor, M. (2017). Information system research : :fundamentals of scientific research for the consumer. Momentum Press.
Tekinbas? Katie Salen, Gresalfi, M., Peppler, K. A., & Santo, R. (2014). Gaming the system : designing with gamestar mechanic (Ser. Interconnections : understanding systems through digital design). MIT Press.
Zhao, F., & Guibas, L. J. (2004). Wireless sensor networks : an information processing approach (Ser. The morgan kaufmann series in networking). Morgan Kaufmann.
COMP2003 Securing Networks Assignment Sample
Assignment Brief
Learning Outcomes LO1, 2, 3
Weight - 40% of overall unit assessment
Suggestion
This assignment is developmental and cumulative. You are strongly advised to start doing this assignment from Week-1 in your study. Leaving your starting date to the week before the due date is a very poor strategy for success in the unit. For assignment help follow the provided guidelines to help you successfully direct your efforts.
Task Description
You need to complete the following tasks:
• Task 1: Advice appropriate security strategies to the organisation.
• Task 2: Scanning and Report on Network Vulnerabilities.
Scenario
You are a consultant at one of the Big 4 consulting firms. You have been recently assigned your first new client and you need to provide them services to help secure their network. A short time ago their network was breached, and they would like your assistance on ensuring this does not happen again.
They have provided a network diagram of their current network which you can use in your analysis.
You must provide a report to the Chief Information Security Officer of your recommendations to combat the current trend of security threats and the strategies that may assist them to combat them.
Task 1: Network Security Solutions
The client would like you to provide them with a brief report (max 1000 words) of what you believe is the greatest threats to their organisation, why you think that and what they can do to combat this.
For this task you must consider some suitable network security solutions for the network and justify the selection.
Advise how each option you suggest provides an improvement to the security and how it will mitigate the threat.
Provide any references or statistics to support your analysis.
Task 2: Network Vulnerability Scanning
Part 1
Provide a detailed solution (max 300 words) of what vulnerability analysis methods you recommend the customer to complete based on their network and advise why those are appropriate.
Part 2
Complete a vulnerability scan on the breached server that has been provided.
• Provide a copy of the OpenVAS report (screenshot or PDF) with the results for the server.
• Determine the possible server that had the breach and what you believe was the attack vector. Explain why you think that was the attack vector and provide any references or statistics to support your analysis. (Max 300 words)
Submission Format
When you have completed the assignment, you are required to submit the following:
1. Your assignment in the PDF/DOC format. The file will be named using the following convention:
Filename = FirstInitialYourLastName_COMP2003_A1.pdf
(i.e. FJones_COMP2003_A1.pdf)
Getting Help:
This assignment, which is to be completed individually, is your chance to gain an understanding of the fundamental concepts of network security which later learning will be based. It is important that you master these concepts yourself.
Marks and Feedback
All assessment materials submitted during the semester will normally be marked and returned within 7 days of the required date of submission (provided that the assessment materials have been submitted by the due date). Marks will be made available to each student via the MySCU Grade book.
Solution
Task 1: Network Security Solutions
NETWORK SECURITY Solutions
Association is where many individuals work to seek after the objective of the organization or association. There is tremendous measure of information which is utilized in the working of an association. Web is a one of the main element of an association to work in light of the fact that without organization availability it is difficult to move information or to speak with clients by means of Emails. So as a result of this colossal measure of information move which is occurring on the organization, the organization should be gotten. While making an association there are different dangers which are kept in focuses to forestall issues in future. There are different dangers to an association, for example, various assaults that are phishing assault, Ransomware, a few different dangers are network break.
Perhaps the most hazardous danger is the organization break since, in such a case that any outsider breaks into the organization they can without much of stretch gain admittance to the information that is moved on the organization. In associations the information that is moved on the organization should be classified since it is connected with the association or the company. So to make an association secure the organization security ought to be of exceptionally great.
Network security implies getting the organization so some other individual or any assailant can't go into the organization. When the organization security is of great then the organizations information and data will be protected and forestall a simple admittance to the aggressors. The method involved with building an organization security is that first and foremost the organization ought to be all around planned and every one of the parts of going after ought to be forestalled by that network design. Network security will order admittance to an organization by keeping an alternate assortment of dangers from entering and spreading through a framework.
Benefits of Organization Security
Prior to building or planning any organization security the association would see the upsides of the organization security which will be planned. Following are key benefits of the organization security are:-
- The trust between the clients, clients and association will increment in light of the fact that once the security will expand the information can be moved effectively with next to no issues.
- The touchy data of the clients, clients won't get spilled.
- Digital assault can be forestalled as a result of organization security.
- Network manager controls organization and watches out for the organization that assuming any assault is occurring on the organization and it will likewise forestall it.
Kinds of Network Security
1) Access control network security: - In this kind of organization security just that guests can go into the organization that approach the organization. The Access is given by the organization administrator. The word access control implies the administrator can conclude whom the entrance ought to be permitted and for whom the entrance is obstructed. This sort of organization security is generally excellent.
2) Cloud security: - It implies giving security to the distributed storage of the association which comprise of the multitude of information and data, for example, pictures, records and so on. Distributed storage increments proficiency.
3) DDoS Network security:-DDoS implies Distributed refusal of administration which implies that this instruments forestall the DOS assault which are most normal now a days. In this assaults there is an uneven organization demand and due to this assault the organization crashes.
FIREWALLS ought to be utilized to build the organization security since it comprises of the greater part of the security devices which will make the organization more solid and secure.
Measurements:
As the information is expanding information breaks are additionally expanding each year in the year 2021 the information breaks which occurred were around 1862 and in the rush hour of Coronavirus in the year 2020 the information breaks were 1108.
Around 2200 digital assault occurred in year 2020 which intends that after like clockwork a cyber-attacks happens.
Ransomware assaults that occurred in half year in 2021 were 2084 assaults.
In the present time around after every 39 seconds there is an attack taking place of different types on different computers or networks or organization.
Firewall
Firewalls control drawing closer and dynamic traffic on networks, with fated security rules. Firewalls keep out offensive traffic and are a significant piece of everyday enrolling. Network Security relies strongly upon Firewalls,
Network Segmentation
Network division describes limits between network segments where assets inside the social event have a regular limit, peril or occupation inside an affiliation. For instance, the edge section pieces an association network from the Internet.
Access Control
Access control characterizes access to the authenticated resources by 3rd party.
Remote Access VPN
Remote access VPN gives remote and secure permission to individual such as long-distance workers, portable clients and other external customers
Zero Trust Network
The zero trust security models communicates that a client should simply have the entry and assents that they need to fulfil their work. This is a very surprising procedure from that given by standard security plans, as VPNs, that grant a client full induction to the objective association
Email Security
Email security suggests any cycles, things, and organizations expected to defend your email records and email content shielded from outside risks. Most email expert associations have certain email security features expected to keep you secure,
Data Loss Prevention
Data setback evasion is an internet based insurance method that joins advancement and best practices to thwart the transparency of sensitive information outside of an affiliation, especially coordinated data like eventually conspicuous information (PII) and consistence related data: HIPAA, SOX, PCI DSS, etc.
Assessment of Risks
This progression is thusly critical, as it emergencies the weaknesses. It is at this progression that network safety faculty should settle on the accompanying: How basic the vulnerabilities found; How pragmatic it could be for a programmer to take advantage of the weakness. Whether any current security controls could diminish the gamble?
Task 2: Network Vulnerability Scanning
Vulnerability Analysis Methods
For the most part, it is important to complete two unmistakable kinds of outputs:
Inner: This output is done from inside an association's edge protections. Design is to distinguish weaknesses could be taken advantage of by programmers who effectively enter the edge safeguards, or similarly by "insider dangers" like workers for hire or disappointed representatives.
Outer: This sweep is an outer output is completed from outside an association's organization, and its chief intention is to recognize weaknesses in the border guards like open ports in the organization firewall or specific web application firewall.
Then again, there are other two ways to deal with weakness filtering:
Verified Scans: In these sweeps, the analyser signs in as an organization client, and gives weakness scanners different special qualifications. Validated filters consider the scanner to straightforwardly get to organize based resources utilizing distant managerial conventions like secure shell (SSH) or far off work area convention (RDP) and confirm utilizing gave framework qualifications.
Unauthenticated checks: These sweeps look for shortcomings in the organization border and uncover weaknesses that can be gotten to without signing into the organization. Unauthenticated examines is a strategy that can bring about countless misleading up-sides and can't give nitty gritty data about the resources working framework and introduced programming.
Vulnerability the board cycle incorporates four stages:
• Recognizing evidence of shortcomings
• Evaluation of the bet introduced by any shortcomings perceived
• Treatment of any recognized shortcomings
• Giving insights about shortcomings and how they have been dealt with
• Unmistakable evidence of Vulnerabilities
A scanner's reasonability depends upon two things:
• The limit of the scanner to find and perceive devices, programming and open ports, and collect other structure data
• The ability to relate this data with known shortcoming information from somewhere around one shortcoming informational collections
There is a strong idea that shortcoming checks ought to be performed during business hours.
Scan Results
Conclusion
An assault vector is a way or means by which an attacker or developer can draw near enough to a PC or association server to convey a payload or malignant outcome. Attack vectors enable developers to exploit system shortcomings, including the human part.
Typical computerized attack vectors consolidate contaminations and malware, email associations, pages, spring up windows, texts (IMs), chat rooms and cheating. Except for confusion, these techniques incorporate programming or, in a few cases, hardware. Precariousness is the place where a human overseer is fooled into disposing of or incapacitating system assurances.
To some degree, firewalls and antivirus programming can discourage attack vectors. In any case, no confirmation technique is totally impervious to attack. A gatekeeper procedure can promptly become outdated, as developers are ceaselessly invigorating attack vectors and searching for new ones in their excursion to secure unapproved induction to PCs and servers. A security opening can be found in a piece of programming or in a PC working framework (OS). Once in a while, a security weakness can open up due to a programming mistake in an application or a defective security design. Hacks could in fact be low-tech, for example, acquiring a worker's security certifications or breaking into a structure.
Programmers are continually filtering organizations and people to recognize all potential passage focuses into frameworks, applications and organizations. At times, they might even objective actual offices or observe weak clients and inside workers who will purposely or coincidentally share their data innovation (IT) access certifications.
References
McClure, S., Scambray, J., and Kurtz, G. Hacking Exposed, Seventh Edition (McGraw-Hill Professional, 2012).
NIST SP 800-27 Rev A, Engineering Principles for Information Technology Security.
NIST SP 800-42, Guidelines on Network Security Testing.
NIST SP 800-64 Rev. A, Security Considerations in the Information System Development Life Cycle.
Richardson, R. 2010-2011 CSI Computer Crime and Security Survey (http://gocsi.com/survey).
Wood, C. Information Security Policies Made Easy, Version 11 (Information Shield, 2009).
RFC 2401 (1998) Security Architecture for the Internet Protocol, Kent, S., Atkinson, R.
Schneier, B. (1996) Applied Cryptography, 2nd edn, Wiley.
Stallings, W (1999) Cryptography and Network Security, Prentice Hall.
Stallings, W (2001) SNMP, SNMPv2, SNMPv3, and RMON 1 and 2, 3rd edn, Addison Wesley.
Ellis, J. and Speed, T. (2001) The Internet Security Guidebook, Academic Press.
ISO/IEC 17799 (2000) Information Technology – Code of Practice for Information Security Management , International Organization for Standardization.
Tanenbaum, A. S. (1996) Computer Networks, 3rd edn, Prentice Hall.
CSC214 Computer and Network Security Assignment Sample
Case Study for Assignment Help
Figura Leisure Centre (FLC) was established in 1989 by converting an old hospital. FLC provides a room space for the community which is visited by nearly 100, 000 people every year. Centre contains a fitness gym, school nursery and several offices for local charities and is visited by several groups who runs their personal or activities for the community.
Centre is run by a small management committee which is formed of volunteer trustees of the association and works directly with the local city council. Management volunteers are drawn from the local community and are responsible for the development of the centre. FLC mission is to provide affordable high-quality comfort to the visitors and their customers are from the different sections of the society. The centre has been enjoying an enviable reputation for the quality and comfort of its rooms and customer service support due to the dedication of its staff. The FLC competitive strategy has been to ensure the utmost satisfaction of their customers from a policy of continuous monitoring by management staff. This has not gone unnoticed by customers wishing to have an excellent place to organise their activities i.e. birthday parties, wedding receptions, yoga and Pilates classes, karate, basketball and football games, etc, and there has been no problem in attracting customers.
The centre, having no website, promotes itself by way of flyers, local newspaper and magazine advertising, and ‘word-of-mouth’. Most of their work is still taken manually and the management committee have felt that most of their rooms and facilities were not in use throughout the day, thus, they are loosing revenue. Several people works in the centre on the rota basis and the staff don’t get to see each other unless there is a social gathering or a staff meeting. Due to the lack of communication between the staff several problems arises in the centre to deal with the customers queries. At the same time centre staff having a problem to chase the customers to make the payment.
Management committee have heard about new innovative technology ‘cloud’ which is helping the traditional business world. They have find out that cloud computing is the fastest growing form of computing and according to Gartner the worldwide public cloud service market will grow from $182 billion in 2018 to $331.2 billion in 2022.
Management has realised that with the cloud technology the centre can solve their problems and provide better service to their customers and improve the occupancy rate to increase the revenue.
Management have decided to use cloud-based SaaS (Software as a Service) based business information system, for example, management information system, customer management system, accounting information system, etc, which can be used to analyse their customers patterns to offer them better deals and attract more customers in the off peak time.
Management have approached a number of consultants, to find out the right SaaS system for the centre and identify the benefits, challenges for adopting the SaaS based system with the approaches to minimise the impact of challenges you have identified.
Solution
Introduction
SaaS (Software as a Service) is mainly considered as a software distribution model that is included with cloud providers and different hosts applications. This makes a more appropriate selection of end-users within the internet, and the SaaS application is used as a compatible device for the login of users. This study is mainly based on a case analysis of FLC ("Figura Leisure Centre"), provides an active room space community and contains a school nursery, gym, and several offices for particular local charities with more than 100,000 people per annum. Customer services and support of their room services are major priorities for FLC. The management of FLC has no proper website, and due to this, they decided to use a SaaS-based system for developing business and its information management. Several processes can be managed by the cloud-based SaaS, and these are customer management systems, management information systems, and accounting information systems. These all are useful to analyse the pattern of customer’s patterns and offer them an attractive deal at an off-peak time.
On the basis of cloud computing, the definition of SaaS ("Software as a Service") with appropriate research
As a software distribution model, SaaS is a cloud provider that hosts applications by making all of these available for end-users across the internet. Besides, an ISV ("independent software vendor") can contract with a third-party cloud provider for hosting the application. Additionally, in the case of large companies like Microsoft, cloud providers are sometimes referred to as software vendors, and SaaS is a major category within three activities of cloud computing. IaaS ("Infrastructure as a Service") and PaaS ("platform as a service") are also included within cloud computing, and a range of IT personnel, business, and professional users use SaaS applications in an active way (Huang & Li, 2020). Apart from that, FLC has a mission of providing affordable as well as high-quality visitors with comfort and customers who come from various sections of the society, along with a good reputation and effective dedication to this.
Figure 1: Effective framework for SaaS provisioning and selection
A better framework is figured out in this section, and the selection manager helps to implement SP management operations by managing various policies with suitable SaaS providers. This is mainly based on the QoS consumer's requirements and QoS offerings SaaS providers (Badidi, 2013). SLA manager implements SLAM operations by carrying out the negotiation process between SaaS providers and consumers. After that, CSV selects different SaaS providers and looks into the negotiation process. In addition, in managing IAM operations, a Profile manager is used by including different preferences on the basis of required QoS as well as personalised services. As depicted by Hadi et al., (2021), another feature is policy manager for managing PM management and is responsible for meeting QoS aware selection as well as authorisation policies on the basis of service providers. This entire working principle and architecture are really effective to manage better services to FLC in order to develop the better activity of customer support and their services.
Discussion of two to four benefits for Figura Leisure Centre to adopt cloud-based SaaS model in managing Information systems such as accounting information system, CRM, and management information systems
Cloud-based SaaS models are too effective in order to manage different kinds of information systems such as accounting information systems, CRM and Management Information systems. Along with that accounting information system is mainly a system structure, which is generally utilised for the business for storing, managing, processing, retrieving and reporting several financial data. Furthermore, for accountants, business analysts, managers, consultants, financial officers, regulators, auditors and several tax agencies, this accounting information system plays an important role (Al-Somali & Baghabra, 2019). Through SaaS accounting, accounting software is provided, which is generally hosted by the service provider. On the other hand, SaaS software can be securely accessed through mobile or computer. In such correspondence, this kind of software is called cloud accounting software. Along with that, for the data centres of the organisations, this software's are installed by the companies. Hence, for Figura Leisure Centre (FLC), this cloud accounting software is too significant for managing several activities regarding accounting (Malik et al., 2018). On the other hand, for accessing various services and features, the SaaS accounting information system is too efficient. Along with that, automatic updates are also processed in the case of SaaS. In such correspondence, management is patched and updated.
In addition, SaaS CRM is mainly Cloud-based software by which permanent access is given to the CRM functionality. Furthermore, any kind of investing is not required for the installation and maintenance. On the other hand, transparency corresponding to the relationships among the customers is brought by the SaaS-based CRM. Besides, business automation is helped where marketing, sales and customer service are personalised through this process (Nayar & Kumar, 2018). Moreover, for operating the Figura Leisure Centre (FLC), a CRM is required in order to manage the customers of this company. Along with that, different kinds of data and information corresponding to the customers are maintained through this CRM software where several kinds of features such as attendance, payments, different rules and regulations of the company and other features are provided. Through the Cloud, all the information is stored in the database, which is too significant for the business. Along with that, business data and services are provided through the CRM system. As opined by Saa et al., (2017), service providers can host the SaaS CRM, which is available to all the customers of the company. In such circumstances, SAAS has great importance for managing the CRM in order to operate the company. As per the case study for Figura Leisure Centre (FLC), SaaS is too effective for operating the CRM information system of this company.
For management information systems, SaaS is a significant distribution model by which multiple applications can be hosted by the cloud provider, and these applications are available to the users online over the internet. On the other hand, the portfolio regarding the technology of the company is provided through the SaaS management system. Besides, the cost of the SaaS applications is contained in the SaaS management system (Jayasimha & Nargundkar, 2020). In addition, vendors and the contracts are managed through the SaaS management system, whereas several SaaS applications are secured through this management system. For Customer service support of FLC, this SaaS management system is too effective for the visitors and the customers. In such accordance, the collaboration of the information technology is developed through the SaaS management system, whereas the shadow IT is reduced and prevented (Rath et al., 2019). As per the case study writing, this FLC organisation has no website for managing its customers and visitors. In such correspondence, a SaaS management system is required for the development of the organisation in a digital way.
Identification of two challenges associated with introducing cloud-based information system in regard to a business information system that has been identified in the previous section
In order to introduce cloud-based information systems in regard to business information systems, various challenges are involved in this. These are such as reliability and high availability, hybrid cloud complexity, portability and interoperability, migration, creating of private Cloud, migration, compliance, control of governance, internet connectivity, lack of expertise, and password security as well as cost management. These all are involved with managing various business information systems like CRM, accounting, and management information systems (Al Hadwer et al., 2021). As per the case study, it is seen that management has realised and approached a number of consultants for better identification of SaaS systems within the centre. Additionally, the management of FLC has also identified that cloud technology is the key success of their business information system that solves problems and provides better customer services on the occupancy rate of increasing the annual revenue of FLC.
Two major challenges are discussed on the basis of the previous discussion of the benefits of using Cloud-based SaaS for small to medium-sized companies like FLC.
Password security:
Using cloud accounts by various users can be harmful to getting network threatening and vulnerable threats. The specific password is known by all, and anyone can change the password at any time. This indicates a big issue for managing the password and can be hacked with cloud access with confidential information. In order to manage the financial information system, business information, as well as management systems, can also be secured by using an effective one known password within the organisation (Ferreira et al., 2017). After that, a big initiative can be measured through organisations like FLC for protecting their password to get secure and safe access to cloud computing and SaaS operations. After that, the password must be modified on a daily basis to access passwords and usernames in a judicial manner.
Cost management:
Cloud computing is able to access fast software internet connection, and that requires high valued software, hardware, maintenance, and management. Besides, high and affordable prices can make it more difficult to achieve a better business information system in medium-sized organisations (Malik et al., 2018). Another issue is transferring of data and its cost within a small business project in a public cloud.
Developing of supporting evidence for identified key challenges in the previous section and analysis of three major approaches that help to minimise the impact of these challenges that have been identified
As per several key challenges corresponding to the previous point, password security and cost management are big factors. In such circumstances, Cloud-based security, network protection, identity security and visibility have to be improved. In such correspondence, cloud cyber security has to be increased for preventing different types of attacks (Nayar & Kumar, 2018). Besides, the growth of agile development has to be increased, and scalability has to be improved. Along with that, firewall, tokenisation VPN, penetration testing should be utilised where the public internet connection should have to be avoided.
Figure 2: Worldwide public cloud service revenue forecast, 2018-2022
(Source: Gartner, 2019)
According to the Gartner report of 2019, the worldwide public cloud services market has been projected to grow 17.5%, and that is $214.3 billion in 2019 (Gartner, 2019). Apart from that, Cloud system infrastructure services have grown 27.5% by 2019, and these large evaluations in cloud computing indicate big cost management in organisations like FLC.
Many companies trying to adopt cloud computing activities must have a firm that understands the major three deployment models such as private, public, and hybrid (Saa et al., 2017). In this regard, the case of personal entertainment and managing advanced IT tools, Netflix is a great example of this activity, and for B2B and B2C users, IaaS (“Infrastructure as a Service”), SaaS (“Software as a service”), and PaaS (“Platform as a Service”) are three approaches frequently used in the market. Furthermore, all the SaaS tools should be discovered for prioritising the application at a low cost. In such correspondence, Platform as a service and infrastructure as a service can be utilised in order to minimise the challenges as it is low costing and it is provided by the third party provided, where the software is utilised over the internet. Moreover, IaaS is owned by the service provider where the security is too strong.
Conclusion
From the above discussion of the entire Cloud-based SaaS for business information management, it can be concluded that the SaaS management information system is mainly the business practice. This includes several factors like purchasing, different licensing; on boarding, renewals and multiple off boarding are managed and monitored through the SaaS management. Besides, cloud system infrastructure services have grown 27.5% by 2019, and this indicates a large evaluation in cloud computing along with big cost management in the organisations like FLC. Therefore, CRM, accounting information systems, and management information systems can be managed effectively by using Cloud-based SaaS in FLC.
Reference:
Al Hadwer, A., Tavana, M., Gillis, D., & Rezania, D. (2021). A systematic review organisational factors impacting cloud-based technology adoption using Technology-organisation-environment framework. Internet of Things, 15, 100407. https://www.researchgate.net/profile/Madjid-Tavana/publication/351443429_A_Systematic_Review_of_Organizational_Factors_Impacting_Cloud-based_Technology_Adoption_Using_Technology-Organization-Environment_Framework/links/60983b51a6fdccaebd1d6091/A-Systematic-Review-of-Organizational-Factors-Impacting-Cloud-based-Technology-Adoption-Using-Technology-Organization-Environment-Framework.pdf
Al-Somali, S. A., & Baghabra, H. (2019). Investigating the determinants of it professionals' intention to use cloud-based applications and solutions: an extension of the technology acceptance. In Cloud Security: Concepts, Methodologies, Tools, and Applications (pp. 2039-2058). IGI Global. https://scholar.archive.org/work/cfnbn4purfbjrhk75mockd6lyy/access/wayback/http://pdfs.semanticscholar.org/
3bf2/dbe862f0eb240800297d5f350f578a43c32e.pdf
Badidi, E. (2013). A framework for software-as-a-service selection and provisioning. arXiv preprint arXiv:1306.1888. https://arxiv.org/pdf/1306.1888
Ferreira, L., Putnik, G., Cunha, M. M. C., Putnik, Z., Castro, H., Alves, C., ... & Varela, L. (2017). A cloud-based architecture with embedded pragmatics renderer for ubiquitous and Cloud manufacturing. International Journal of Computer Integrated Manufacturing, 30(4-5), 483-500. https://repositorium.sdum.uminho.pt/bitstream/1822/51375/1/0951192X.2017.pdf
Gartner, (2019). Gartner Forecasts Worldwide Public Cloud Revenue to Grow 17.5 Percent in 2019. Retrieved from https://www.gartner.com/en/newsroom/press-releases/2019-04-02-gartner-forecasts-worldwide-public-cloud-revenue-to-g. [Retrieved on 16 March 2022]
Hadi, H. J., Omar, M. A., & Osman, W. R. S. (2021). Investigating the determinants of CC-SaaS adoption in Iraqi’s public organisations from the perspective of IT professionals. International Journal of Engineering Research and Technology, 14(2), 130-143. https://www.researchgate.net/profile/Hiba-Hadi/publication/351093867_Investigating_the_Determinants_of_CC-
SaaS_Adoption_in_Iraqi's_Public_Organisations_From_the_Perspective_of_IT_Professionals/links/6085b409
881fa114b42b0966/Investigating-the-Determinants-of-CC-SaaS-Adoption-in-Iraqis-Public-Organisations-From-the-Perspective-of-IT-Professionals.pdf
Huang, W., & Li, J. (2020, August). Using agent solutions and visualisation techniques to manage the cloud-based education system. In 2020 IEEE Intl Conf on Dependable, Autonomic and Secure Computing, Intl Conf on Pervasive Intelligence and Computing, Intl Conf on Cloud and Big Data Computing, Intl Conf on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech) (pp. 375-379). IEEE. https://westminsterresearch.westminster.ac.uk/download/4e28ebe530f0e91acd90292bd000cbec0926b0def48b
eca232b64f4c4e2063c7/1779663/ICETA%202016.pdf
Jayasimha, K. R., & Nargundkar, R. V. (2020). Impact of software as a service (SaaS) on software acquisition process. Journal of Business & Industrial Marketing. https://www.iimidr.ac.in/wp-content/uploads/Impact-of-software-as-a-service-SaaS-on-software-acquisition-process-FPMI-Theses.pdf
Malik, M. I., Wani, S. H., & Rashid, A. (2018). Cloud computing-technologies. International Journal of Advanced Research in Computer Science, 9(2). https://www.researchgate.net/profile/Mohammad-Ilyas-Malik/publication/324863629_CLOUD_COMPUTING-TECHNOLOGIES/links/5af45452aca2720af9c57086/CLOUD-COMPUTING-TECHNOLOGIES.pdf
Nayar, K. B., & Kumar, V. (2018). Cost benefit analysis of cloud computing in education. International Journal of Business Information Systems, 27(2), 205-221. https://www.researchgate.net/profile/Vikas-Kumar-122/publication/321753986_Cost_benefit_analysis_of_cloud_computing_in_education/links/5af94354a6fdcc0
c033450cb/Cost-benefit-analysis-of-cloud-computing-in-education.pdf
Rath, A., Spasic, B., Boucart, N., & Thiran, P. (2019). Security Pattern for Cloud SaaS: From System and Data Security to Privacy Case Study in AWS and Azure. Computers, 8(2), 34. https://www.mdpi.com/2073-431X/8/2/34/pdf
Saa, P., Cueva Costales, A., Moscoso-Zea, O., & Luján-Mora, S. (2017). Moving ERP systems to the cloud-data security issues. http://rua.ua.es/dspace/bitstream/10045/69990/1/2017_Saa_etal_JISEM.pdf
MITS4001 Business Information System Assignment Sample
Read the following case study and answer the questions below in the form of a report.
You are expected to answer each question within approximately 250-300 words.
Case Study: Cutting out paper speeds up the process
The Chinese are credited with inventing paper nearly two millennia ago, and in spite of more recent inventions, such as the integrated circuit, computerised storage, and networking, it is still heavily used. So is the world moving closer to ushering out the old in favour of the new?
The paperless office has long been a dream, but can it be achieved?
Liverpool Direct is doing its best. The company is a partnership between BT and Liverpool City Council, which at the turn of the decade was seen as one of the worst councils in the UK at revenue collection and benefit payments. ‘The service was deemed to be failing’, says David McElhinney, chief executive of Liverpool Direct, which was formed in 2001 to help modernise the council's operations. ‘The average time to turn around a benefit claim was 140 days, and there was a backlog of 50,000 cases.’ The paper was holding everything up. Each week, 20,000 pieces of mail would arrive at the benefit office, including everything from benefit claims to notifications that an individual's circumstances had changed. The mail would be stamped, and filtered through different teams depending on what information it held until it reached a file.
It would then be sent to more people for manual assessment. Bottlenecks would delay the paperwork, and files would be buried on someone's desk when they were needed most. 'A claimant might pay a personal visit, and we wouldn't be able to locate their file', Mr McElhinney says. 'The average wait was about two hours.' Not only did the paper cause significant delays, but also took up £750,000-worth of office space a year. Ridding the office of paper began with refocusing the system around the end-user. A series of 'one stop shop' contact centres was set up to handle customer queries and visits, and the organisation opted for what Mr McElhinney calls a 'single version of the truth' - a single electronic document that can be referred to by all parties at any time. Now, when a document is received, it is scanned and put into a digital file. Data can be attached to the documents, which is archived into different folders by a dedicated team, based on the content. Software-based flags can then be set for the document that can trigger actions necessary for that letter. One trigger might cause a letter with a particular response to be generated, for example.
One of the biggest challenges when re-engineering a paper-based system is to minimise disruption, but some interruption is inevitable. ‘It’s one of those systems where you can’t run things in parallel’, explains Mr McElhinney. The systems were turned off for six weeks, and buildings including 15 post rooms where closed; one post room was retained to scan all incoming correspondence; the paper storage building was sold in March 2006, generating £4.5m for the city. Stripping away old ways of working was an important part of the project's benefits: ‘Know your processes, and challenge them to make them more efficient’, says Roddy Horton, central systems manager at the Hyde Group, a housing association with 1,200 employees serving more than 75,000 people. This month, the Hyde Group computerised its recruitment process, stripping 58,000 sheets of paper a year out of the system.
Before the recruitment process was digitised, candidates would receive an information pack and application form in the post. They filled in and returned the form and copies were sent to the recruiting manager and up to five people on the review panel. The recruiting manager would then fill out various forms following the interview and return them to human resources, which would then send a decision letter to the candidate. 'Now, all the details are on the website', explains Mr Horton. An online application form is logged in a database and sent to the recruitment manager, who then electronically forwards it to the interviewing panel. Once the decision is reported to human resources, the candidate receives an e-mail.
The recruitment application is built on a database from Northgate HR that the company had bought in 2001 to manage some human resources information. It then purchased ePeople, a human resources application from Northgate that enables the company to provide a self- service front end to the database. The developers built workflow rules into the system that coordinated these communications electronically. The recruitment applications join an already-deployed paperless expense claims and training request application, also designed to strip paper from the system. Before the introduction of that system, paper-based expense claims and time sheets needed to be signed by a manager, who would often be out surveying sites, dealing with housing issues, or visiting other offices. 'It might be weeks before you saw your manager', says Mr Horton. 'Staff were not being paid on time, and they were also going to huge amounts of effort to claim those payments.’
The electronic system handles those communications digitally, so staff enter their expenses claims directly into the computer. The Hyde group also refined the expenses process by making it possible within the system to request that another person sign a document, if the first choice of manager was absent, for example. Both Liverpool Direct and Hyde’s projects had a common challenge in getting people to change the way they work – especially senior staff used to do things a certain way. Mr Horton found that electronically signing documents was counterintuitive for many staff: ‘I had problems proving that an electronic signature is just as sound as a paper one’, he says, explaining that employees ‘sign’ an e-mail in the workflow system by e-mailing it to the server, which then e-mails the next person in the workflow chain.
‘Sometimes, people can also be nervous of introducing efficiencies because they see it as a job threat', Mr Horton warns. He had to reassure several people as systems were roiled out. But how much paper do such projects really get rid of? Neither of these organisations are yet paperless. Liverpool Direct has achieved the greatest success, having stripped about 70 percent of the paper from the process. None of the paper that is personally bought into the one-stop shop centres and scanned is retained, but any postal correspondence is retained for 30 days after being digitised. The Hyde Group's attempt at digital deforestation has been more muted. Since the recruitment system was digitised, about one-third of its paper has been eliminated. It hopes to increase that to 80 percent by digitising supplier invoices, tenancy agreements, and possibly tenancy repair requests, Mr Horton says. Nevertheless, even though an entirely paperless office may not be plausible, stripping even this much paper out of the system can have positive effects. For example, in Liverpool the caseload backlog has been reduced from 50,000 to zero, while the average processing time for benefit claims has dropped from 133 days to 19. Abandoned call rates to its contact centre have dropped from 50 percent to just 5 percent, and the waiting time for personal visits concerning benefit claims has been reduced from the original two hours to four minutes.
Hyde will always have some paper, even if it is not strictly speaking in the office. The company is reluctant to get rid of paper-based tenancy agreements altogether, and keeps them stored in an off-site location for legal purposes. Nevertheless, with the paperless recruitment system now in place, and with its previous paper saving efforts, it has eradicated 153,000 sheets of paper a year from its operations. In reality, the totally paperless office may still be as far off as the paperless newsagent – but organisations can go a long way towards reducing what they use and increasing the efficiency of their work along the way.
Questions
1- Why is it important to strip away old ways of working when introducing systems such as those brought in by Liverpool Direct and Hyde?
2- Using the Internet as a resource, locate information regarding a simple document management system, such as Scansoft's PaperPort Office. How useful is such a product likely to be within a department of a large company or a small business?
3- What is the likelihood that the paperless office will ever be achieved?
Solution
Introduction
In this study research the business information system is discussed on the achievement of paperless office by Liverpool Direct in mitigating different in old ways of working and its evaluation to better business profit. In such accordance several issues regarding the old models have been discussed and the utilization of paperless documents has been proposed as per the case study for business development.
The way of striping away of old working process by Liverpool Direct and Hyde
It is too important to strip away various old ways of working in order to increase the business profit, by replacing different kinds of systems brought by the Liverpool Direct. For the development of business, different kinds of new strategies are implemented as smart work is more effective and efficient than hard work. In such circumstances, the striping away of the old ways has different effects in business (Oliveira et al. 2021). In addition, “Wise Acre Frozen Treats” has been bankrupted whereas the 180s (clothing) has been recovered.
Adapting of information system to achieve strategically organizational goals by Liverpool Direct and Hyde
On the other hand, in 2013, Crumbs Bake Shop topped in the business whereas in 2014 it was bankrupted. Along with that, a gaming company Zynga tried new development, but it did not work out well. Besides, KIND Snacks tried to develop its business while later it stuck to the quality of the products. In such circumstances, it is too significant to strip away the old methods. Actually, all the old methods will not be stripped away whereas many new methods will be implemented for a better future (Kim et al. 2021). As per the case study, total benefit claim is 140 days where total backlogs have been seen for 50000 cases. On the other hand, personal visit time is 2 hours for this company. Additionally, office space corresponding to a year is £750,000. Hence, a single electronics document is referred for the customer handling through the one stop shop.
Time management and the reduction of the effective process are the main factors regarding several management activities. In the case of Hyde, 153000 sheets of the paper have been wasted for its operation and for recruiting 58000 sheets have been wasted. Various data are saved in the database and after receiving the documents, these are changed into a digital file.
Utilization of simple document management system such as Scansoft’s Paper Port office
In order to manage simple documentation management systems like Scansoft’sPaper Port office, Facts and reality checking are most important for product development and that must be included in this. While the paperless office is not to be plausible and stripping paper out from the system, a positive impact can occur in this regard (Wantaniaet al. 2021). According to this case study sample, caseload backlog has reduced to 0 from 50,000 and average processing of this system has dropped from 133 days to 19. Various management activities depend on managing time and reducing effective processes within a suitable way. Apart from that, contact center has also reduced to 5% and personal visiting as well as waiting times have also decreased to 4 minutes.
Development of IT plans casestudy for assignment help to maintain Document management system within Liverpool Direct and Hyde
Hyde can focus on managing papers and is not maintaining strict decision making within the company and that results in reluctance to get rid of tenancy agreements along with a paper-based process. This keeps all the data stored within a location for off-site legal purposes. Moreover, by managing requirement systems of paperless documents along with its previous paper saving efforts, it is seen that more than 153,000 sheets of paper have been eradicated in a year with an appropriate operation. After that, in reality, a paperless office can be still far off as the “paperless newsagent” and the organization can be forwarded to reduce the usages and manage efficiency the long way (AbdulKareemet al. 2020).
Various difficulties can also be faced by Liverpool Direct to manage “Cutting out paper speeds up the process”. These are as follows:
Upgrading from paper-based system to IS
Analyzing the value of an original document
Managing parallel work and its completion within exact time
After that, management of documentation is a process for maintaining the information as well as its organizing, sharing, and storing, creating as appropriate manner. It is important for managing documentation for businesses from large enterprises to small. As per the case study, Hyde can deal with high-stake information for managing the activities in documentation.
Achievement of paperless office and its justification
This is a modern thing to do paperless office for small to medium size enterprises and for better productivity and growth in business management various companies are trying to achieve paperless office. Besides, paperless office can be achieved by the company, Liverpool Direct by using best management in their organization. In order to identify conflict and success, parallel office can be achieved along with the major three activities and these are cost of IS memories, comfort, and cyber safety. As per the case study analysis, it is seen that Liverpool Direct has a partnership between Liverpool City Council and BT, and that is considered as one of the worst councils within the UK on the basis of benefit payments and revenue collection. For managing council’s operations along with modernization of Liverpool Direct along with average time for claiming of 140 days. Apart from that, a backlog was there with 50000 cases and more than 20000 pieces arrived through mail in the betterment of the office.
Identification and synthesisation of different functions corresponding to the database management system within Liverpool Direct and Hyde
Major difficulties must be maintained through Liverpool Direct by implementing someIS (Information System) activities and that will be beneficial for paperless offices (Udendeet al. 2018). On the other hand, no proper company can achieve new methods with initiating effective firewalls, and can afford memories. Additionally, “Wise Acre Frozen Treats” has been bankrupted while clothing has recovered and in 2014, an appropriate business management has been shown by Crumbs Bake Shop whereas 2014 was bankrupted. Some issues are also there in using papers in office and these are paper not also causing significant delays but also worth £750,000 office space per year. For managing end users with reinforcing of ridding the office and “one stop shop” is involved to set by handling customers visiting, and queries. This is managed through a single electronic document and that is really effective for Liverpool Direct in evaluating paperless offices. Therefore, yes, paperless office has been achieved with various regards along with customer services by Liverpool Direct.
Conclusion
From the above discussion of entire section in this study, it can be concluded that paperless office can be achieved on the basis of proper business and exact documentation of effective information by using database. In this respect, Liverpool Direct proposed the paperless office through single electronic document and reinforcing office as “one stop shop” to handle customer visit and different queries.
Reference list:
.png)
SAM11486 System Analysis and Modeling Assignment Sample
Assignment Case Study – L-Mart
Disclaimer: The situation described in the following case study for assignment help is fictional, and bears no resemblance to any persons, businesses, or organisations, living or dead. Any such resemblance, if exists, is merely co-incidental in nature, and is not intentional.
L-mart is a national business that sells all kinds of varied goods directly to consumers through its physical retail stores and growing online presence. It is looking to upgrade and improve its inventory management system, as its current system is old, outdated, slow, and difficult to use – not suitable for a growing company with rapidly increasing online sales.
L-mart’s inventory management system needs to keep a record of all of the products that are sold at L-mart and the suppliers of those products. It also keeps records of all sales and inventory at both individual physical retail stores, and at regional warehouses.
In the online web store, products are displayed to consumer with their name, retail price, a short description, current stock at each location, and an image. The wholesale price (the price that L-mart paid to a supplier for the product) and barcode are also recorded for each product.
The system also prints shelf labels for in-store use (for staff to put on shelves or individual items). These shelf labels only include the name, retail price, and barcode of the product.
L-mart’s physical retail stores are named after their suburb and state (e.g. “Bruce, ACT”, “Queanbeyan, NSW”), along with their street address, email address, phone number, and a store manager (a person with a phone number).
Regional warehouses are named after the city/area they serve and state (e.g. “Canberra, ACT”, “Western Sydney, NSW”), and have the same information except that they do not have a store manager. The inventory management system keeps a record of all sales. In-store purchases are obviously recorded against the store they are purchased from (and reduce the inventory held by that store accordingly). At the moment, online purchases are always shipped from a regional warehouse directly to the customer (there is no click-and-collect functionality at present, although L-mart is currently investigating the feasibility of this for the future). The time, sale location, product, and quantity are recorded for all sales, and online purchases also record customer name, address, and payment details. Each location can mark individual products as ‘active’ or ‘inactive’. An ‘active’ product is for popular, regularly-ordered products, where stock should automatically be reordered. An ‘inactive’ product is for products that are seasonal or infrequently ordered.
For ‘active’ products, when stock of a product at a particular location reaches a critical threshold (this is different for each product and each location, due to varying stocking and sale rates for each product at each location), the inventory management system should automatically create a purchase order, to be approved (or rejected) by store or warehouse staff. If an order is approved, the staff will specify the amount of new stock to order. Each month, all of the approved purchase orders for each store go out to each supplier for processing. ‘Inactive’ products are never automatically ordered but still have critical thresholds - store or warehouse staff are still alerted when stock drops below these levels and they can manually create purchase orders for these (or other products) if needed.
Each supplier provides multiple products for L-mart, but L-mart only orders a product from a single supplier at any given time. As an ICT business analyst, you will be tasked with analysing and modelling L-mart’s current business practices in order to better understand the current situation of the business, with a view towards creating a single, updated ICT system to manage their inventory management system.
Solution
Introduction
L–mart is regarded as a national business organization that provides its customers with various goods sold directly through the physical retailing stores of the company to their customers. The L-mart company is currently following their outdated and slow system for inventory management, which is becoming old and is thereby increasing the company's difficulties in maintaining proper efficiency. Hence, L-mart company is focusing on developing an advanced inventory management system to manage customers' growing demand effectively and to impart its online presence. Hence this report will provide the context diagram, the data flow diagram and the use case diagram. The company will also focus on the data dictionary, reflecting on the data presented within the context and flow diagrams.
1. Additional research and assumption
From the given case study, it is seen that the L-mart company will be looking to update and improve its inventory management system, for which the company will be focusing on enhancing the features of the online site (Ahmadi et al., 2019). Therefore for bringing the changes to the website, the technical department of the L-mart company will be basing their inventory modelling on some of the basic assumptions. The most important assumption that the L-mart company will be making will be that the customers' demand is constant and continuous. Apart from this, the case of product shortage is not permitted within the company, which indicates that the inventory should consist of an adequate amount of products that will meet the customers' needs (Wautelet et al., 2018). Apart from this, the inventory system should be formed by integrating 3 factors: frequency, order size and timing, and the company's ability to track its inventory. After in-depth research, it is seen that the system must contain proper lead time knowledge and, at the same time, contain variability.
2. Context diagram
.png)
Figure-1: Context Diagram of L-mart
(Source: Self-made)
Through the help of the context diagram, the L-mart company will be able to gain a conceptual view of the inventory management system. Therefore through the help of the context diagram, the L-mart Company will be able to show the overall data flow for inventory management and thereby enable data management.
3. Data dictionary
.png)
.png)
.png)
.png)
.png)
4. Data flow diagram
A data flow diagram is considered one of the most influential graphical representations of the data flow process associated with the flow of information system management design process. Here in this context, it has been identified that the aspects of data items flowing through the data flow diagram are initiated from the external data sources towards internal data sources effectively (Fauzan et al., 2019). In the following section, a top level of DFD has been produced, which effectively incorporates an effective detailed model design for the organisation's L mart inventory management system. Based on this data flow diagram, a structured accomplishment of system mechanism and how the entire retailing operations are done through web process effectively. Based on the smooth flow of information, effective mode of order stocks and inventory control, the possibilities of overstocking and higher inventory costs can be reduced effectively.
.png)
Figure 2: Data flow diagram
(Source: self-made)
Level 2
.png)
Figure 3: Data flow diagram level 2
(Source: self-made)
5. Process specifications
In response to the case scenario, it has been identified that the approached inventory management system can keep all the sales records for the organisation L marts effectively, including in-store and online purchases. It has been identified that the entire process includes direct shipping operations from the company's regional warehouses to the customers to maintain better feasibility (Irhamn and Siahaan, 2019). Here in this context, it has been identified that the inventory management system specifications include details such as the time, sale location, product, and quantity effectively. In addition to that, the online process also incorporates recording customer names, addresses, and payment details. Hence in this context, critical specifications involved in this process are storing process, organisation, management and inventory data analysis. To maintain efficiency and accuracy of the entire system specifications to deliver better inventory control and management support documentation, and in addition to that, employee training at an advanced level is also required.
Hence as retail operations, including in-store and online retail, ensure vast process flexibility, that is why the process being described is one of the most exciting and complex processes of the system in response to having the support of employee training and support documentation.
6. Use-case diagram
Figure 3: Use a case diagram
(Source: self-made)
7. Use case description
In response to the entire information system operations for the company inventory management process, it has been identified that product marking has been taken under consideration as it is identified to be one of the most compelling use cases of the entire inventory management system.
Product marking:
As this product marking helps the system to ensure a better product threshold, it is considered a fascinating and complex use case of the system in context with warehousing operations and stocking management of the organisation L mart.
Conclusion
This report has developed a new inventory management system for the L-mart company, for which the additional assumptions needed are being described. The context diagram, along with the data flow diagram and the use cases for this case, has been provided through which the L-mart company will be able to enhance their data management regarding their product inventory and will be able to handle their increasing demand more effectively.
8. Reference List
.png)
DATA4300 Data Security and Ethics
IT – Case Study
Your Task -
• This assessment is to be done individually.
• Students are to write a 1000-word report on the monetisation of data and submit it as a Microsoft word file via Turnitin on Tuesday week 3 at 23:55pm (AEST).
• You will receive marks for content, appropriate structure and referencing.
Part A: Introduction and use on monetisation
• Introduce the idea of monetisation.
• Describe how it is being used in by the company you chose.
• Explain how it is providing benefit for the business you chose.
Part B: Ethical, privacy and legal issues
• Research and highlight possible threats to customer privacy and possible ethical and legal issues arising from the monetisation process.
• Provide one organisation which could provide legal or ethical advice.
Part C: GVV and code of conduct
• Now suppose that you are working for the company you chose as your case study for assignment help. You observe that one of your colleagues is doing something novel for the company, however at the same time taking advantage of the monetisation for themself. You want to report the misconduct. Describe how giving voice to values can help you in this situation.
• Research the idea of a code of conduct and explain how it could provide clarity in this situation.
Part D: References and structure
• Include a minimum of five references
• Use the Harvard referencing style
• Use appropriate headings and paragraphs
Solution
Part A: Introduction and use of monetization
The idea of monetization
The most popular method of using information to increase revenue is data monetization. The highest performing and fastest growing businesses have embraced data monetization and integrated it into their operations. Offering direct access to your information to outsiders is part of direct information monetization. One can sell it in its original, unsophisticated form or in a structure that has been modified to include research and knowledge titbits (Tucci and Viscusi, 2022.). Common models include contact configurations for new commercial opportunities or discoveries that have an impact on the businesses and organizations of purchasers, where things become interesting is with aberrant information monetization. Information-based improvement comes first and foremost. This involves dissecting your data to find experiences that can improve how your association does business. Information may help you understand how to approach clients and how to interpret client behaviour so one can move your transactions forward. Information might also include where and how to cut expenses, avoid risks, and simplify procedures.
Use of monetization in Telstra
The last several years have seen activity in the field of big data monetization in telecoms. But telecoms' competitiveness has changed over time because of the complexity of delivering and selling such a wide variety of goods, as well as because different verticals have distinct income potential opportunities. The success of other new telco products, particularly IoT, as implied by the connection between various Telstra information and examination items and IoT arrangements, has also significantly impacted Telstra's desire to pursue information monetization approaches (Cunneen and Mullins, 2019.). In many cases, IoT information monetization is the main system, as shown in the scenario above, but in other cases telecommunications administrators can handle opportunities independently of IoT administrations.
The benefit of monetization in Telstra
The arrangement of understanding distraction/wearing scenarios is a fairly typical use case in today's world that makes use of sensor data and client development expertise. Also available for examination are crucial areas like client division and behaviour. For Telstra, it is harder to find various open doorways around pleased usage designs. Although it is a mature market used to consuming various types of information, and it doesn't seem to be a well-known use case, Telstra may well know about its set-top boxes and various stages that will be important to content suppliers.
Part B: Ethical, privacy, and legal issues
Threats to customer privacy and possible ethical and legal issues arising from the monetization process
Big Data, artificial intelligence, and information-driven advancements provide enormous benefits for society as a whole and numerous fields. On the other hand, their abuse might cause information work procedures to ignore moral obligations, security expectations, and information insurance regulations (Al Falasi Jr, 2019). If using big data effectively inside a framework that is ethically sound and culturally focused is capable of acting as an empowering agent of favourable outcomes, using big data for money outside of such a structure poses several risks, potential issues, and ethical dilemmas. A few examples of the impact modern reconnaissance tools and information collecting techniques have on security include group protection, advanced profiling, automated guidance, and biased rehearsals.
Everything in modern society can be scored, and fundamentally innovative opportunities are still up in the air thanks to such scoring systems, which are typically obtained by opaque predictive equations applied to data to determine who is valuable. Therefore, it is essential to guarantee the decency and accuracy of such scoring frameworks and that the decisions based on them are acknowledged legally and morally, avoiding the risk of defamation suited to affect people's chances (Kumar et al. 2020). In a similar vein, it's critical to prevent the alleged "social cooling." This deals with the long-lasting undesirable effects of information-driven improvement, particularly those caused by such scoring frameworks and the standing economy. It may be seen, for instance, in the phrasing of self-awareness, danger avoidance, and the absence of free speech activity in large information works that are conducted without a moral foundation.
The human-information interaction under Internet of Things (IoT) settings, which is boosting the amount of information acquired, the speed of the cycle, and the variety of information sources, is another crucial morality issue (Rantala et al. 2021). Researching new viewpoints such as "responsibility for" and other barriers is important, especially because the administrative landscape is developing much more slowly than the Internet of Things and the advancement of Big Data technologies.
The organization which could provide legal or ethical advice
The Office of Legal Services Coordination works to guarantee that Australian Government entities get trustworthy and well-written legal services. This group might offer advice on the impact of modern observation tools and information gathering techniques on security, including group security, advanced profiling, computerized direction, and unfair practices.
Part C: GVV and code of conduct
Report the misconduct
The GVV framework including Values, Choice, Normalization, Purpose, Self-Knowledge & Alignment, Voice, and Reasons & Rationalizations can be noted to be denied in the abuse of the monetization frameworks may result in disruptions and extraordinary results. The weaponization of monetization poses the most obvious risk. The projected risk of computerizing protection engineering is that it would lead to widespread obliteration that is not reversible (Truong et al. 2019). The tactical application of adaptability, such as the use of independent weapons, might result in a different and more destructive style of combat.
It should also be taken into consideration because a study on the corrupt use of money found that adaptation might make already existing threats like cybercrime worse and the deliberate misuse of the GVV framework should be reported. The advancement of adaptability may also herald the appearance of novel threats. They might easily sabotage current safety initiatives, interfere with a system's operation, or damage any stored information. Additionally, futurists warn that money might be misused in a variety of ways, like as:
• Through the propagation of false ideologies, the majority is subjugated and subject to social control.
• The increase of automated systems that can spread fake news and change public opinion
• Attacks against the fundamental pillars of the economy, such as banks, media communications, utilities, and so on, can be launched by cybercriminals using money.
• Large businesses can use adaption-controlled techniques for adaptation to mine confidential customer information.
Code of conduct and its usage
A code of conduct is essential in this case because it provides employees with clear guidance on how to behave and operate while carrying out their jobs. While some businesses want their employees to abide by a code with many requirements, others keep things simple. An aspiring employee may determine whether they can work in a certain organization by learning about the standards, methods, and assumptions, and a current representative can excel at their job by doing so (Dagg et al. 2022). The new legislation for information protection and other moral concerns requires that businesses manage their internal information operations following these new rules, which is the importance of the code of conduct. Additionally, even if change at large firms is dramatic, information pioneers should seriously assess such changes as business opportunities rather than burdens.
Part D: References
.png)
SYAD310 Systems Analysis and Design Assignment Sample
ASSESSMENT DESCRIPTION:
Case Study
Case Study: ‘Sydney Gifts’
‘Sydney Gifts’ run a store selling good quality antiques and have been in operation for twenty years. They currently maintain details of every piece they sell in a manual system.
‘Sydney Gifts’ has always been run by the same owner/ manager Mr Smith. Mr Smith's son has just joined the business and thinks that using a computerised system would make managing their orders, stock levels and records management easier. Currently they divide their stock into three categories furniture, china art and paintings.
For furniture they store the following details current owner, approximate age, type, style, construction material, finish, condition, notes and price. For paintings they store current owner, approximate age, style, condition, notes, price, artist and medium. For china they store current owner, approximate age, style, and condition, notes, manufacturer and construction material. The managers also want to be able to run sales reports at the end of every month.
‘Sydney Gifts’ also sell antiques on behalf of some of their existing customers so that they may sell the same item more than once. When this happens, they go back to the original record of that piece and record the details of the new sale price, owner etc. This is done so they can maintain the provenance of the item. It is very important to both Mr Smith's that this system is very accurate and quick to use.
They would also like a better way of maintaining customer details so that a customer could tell Sydney Gifts that they are looking for a particular item. That item could be placed on a "wish list" and the customer notified when the item is located. As well as the standard attributes for an item the wish list will store the date the customer registered the item on their wish list and the top price they are willing to pay. ‘Sydney Gifts’ have many customers so that sometimes more than one customer may register that they are looking for a particular item. When at least two customers are looking for the same item it has been decided to offer the item to the customer who registered the item on their wish list first.
Tasks
Write answers on the following questions
1. What types of system requirements will you focus on for Sydney Gifts System? Explain each one in detail.
2. What fact-finding methods could you use to collect information from employees at Sydney Gifts? Suggest at least three methods and explain the pros and cons of each.
3. Describe two systems development tools and two development methods you can used for system development for Sydney Gifts.
Modelling Exercise
1. Create a use case diagram for Sydney Gifts System.
2. Prepare a context diagram for Sydney Gifts System.
3. Prepare a diagram level 0 DFD for Sydney Gifts System. Be sure to show numbered processes for handling order processing, payment, report processing, and records maintenance.
4. Create an initial ERD for the new system that contains at least four entities.
5. Analyse each relationship to determine if it is 1:1, 1: M, or M: N.
Solution
1. Introduction
The present report examines 'Sydney Gifts', a significant store that has been selling high-quality antique products to consumers for twenty long years. In recent times the company has been maintaining the information of the items that would be sold in a manual system. In the Case study report, two types of system requirements are mentioned to operate the operation of the 'Sydney Gifts' system. Furthermore, fact-finding methods are explained that are implemented to collect information from the workers. The advantages and disadvantages of the methods are also explained in the report. Two development methods and two systems development tools are implemented to analyse the development of Sydney Gifts.
2. System requirements by focusing on Sydney Gifts System
Functional Requirements
Functional requirements are signified as the description of the particular service offered by the particular software. It determines the system of the software and its component in dealing with the changes in the software requirements (Martin 2022). On the other hand, the function inputs to the operating system, outputs, and behaviour. The functional requirement is also determined by manipulating data, calculation, user interaction, business management, and specific usage that defines the systematic element to run the functional performance. ‘Sydney Gifts’ regulates the system requirements while determining the requirements that are needed to store the details of the consumer. The store ought to maintain each significant piece sold in a manual system. The store sells antique products such as furniture, paintings, and China art.
On the other hand, the organisation wants to maintain its business while implementing a computerised system such as stock levels, records management, and stock levels. It can be asserted that ‘Sydney Gifts’ uses the functional requirements from the higher aspect of the abstract statement to the specific mathematical requirements. The company will use the functional requirements in conducting the data analysis needed in the operating screen. Consumer data handling needs to be entered into the main system. While entering the specific data, complete information about the stocks, records and orders are put into the system. The system's value is used to analyse the recommendation sets required to design the functional characteristics (Miller et al. 2018). The design is evaluated along with the human factors engineering can result in improvement of their stock maintenance for assignment help.
Performance Requirement
Performance requirement determines the elements of criteria that are needed to stimulate the elements that are used to perform the stock management in a specific code of standards (Designing buildings 2022). On the other hand, performance requirement is signified as the process through the software system would accomplish specific functions under significant conditions. Performance requirements are important to execute the performance that is needed in guiding the end-users (Gorman 2022). In-store management, gathering important information is an important element of software development in determining the software requirements. Requirements are implemented to fully concentrate on the capabilities, goals, and limitations of the project management. Sydney Gifts' consumers, users, and stakeholders need to understand the performance requirement in project management. Sydney Gifts are also looking to maintain the consumer details for the required amount of item. The wish list is the place in the software system where all the information about the products is kept.
3. Fact-finding methods to collect information from employees at Sydney Gifts
The fact-finding method is the important process of implementing techniques such as questionnaires to gather information about requirements, preferences, and systems. Fact-finding techniques are used by Sydney Gifts to find out the changing preferences of the consumer regarding the antique products sold by them. The organisation will use the questionnaire to find out the responses of the consumer that might reveal their preferences and choices on buying the products manufactured by the specific organisation. The fact-finding methods include interviewing, examining documentation, questionnaires, and research.
Interviewing
Interviewing is the eminent fact-finding method to collect information from the consumers buying their products from their store and online platform. The interviews will be conducted properly to find out the best results that are relevant for finding the changing choices of the consumers. Interviews have several advantages, and the most striking aspect is questioning people who can relatively write their responses. This significant category can include the illiterate subjects and infrequent subjects that are unimportant while they speak during the interview. Oral responses play an important part in determining the individuals with a greater number of information than their written responses. The pros of interviewing are the capability to find pertinent information and increase knowledge. The cons of interviewing are a major time-consuming process.
Examining documentation
Examining documentation signifies the project's development required to execute the requirements needed in the project management. Here Sydney Gifts wanted to manage the information about the consumers that have been buying their products for many years. Important approaches are regulated for eliciting requirements to understand the whole inventory system among the stakeholders (Aslam et al. 2021). It is advantageous in recognising the data flow needed to understand the new system. It is disadvantageous because it does not store the document that is important for the system.
Questionnaire
Sydney Gifts are incorporating a questionnaire in the primary survey that will be conducted by them to know about the preferences and choices of the consumers. Questionnaires are the eminent form of fact-finding method that permits facts to be collected from a significant number of individuals while regulating control over the responses. It can be asserted that Sydney Gifts are implementing the survey questions to extract information from the consumers who participated in the survey. Questionnaires are designed with important questions that are mentioned in the questionnaire. The consumers have to answer the questions one by one in a serial number to gather responses from the consumer about the products sold and manufactured by the organisation. The pros are that it is a cost savings process and reaches a wide number of people in a certain region. On the other hand, it can also determine unanswered questions about the company and a lack of personalisation.
Research
Research is an important feature finding method in analysing the techniques and methods used in the survey. Proper research can guide the organisation to implement the suitable management required to maintain the manual system. The organisation stores information about the products sold by them to the consumer. The computerised system makes the development of the product management while properly storing the inventory. Proper research will help the Sydney Gifts in assessing the requirements that are needed in the organisation to foster innovation and project management. It regulates critical thinking and also drives analytical skills through on learning process in determining factual knowledge.
4. Systems development tools and methods
System development methods are signified as the eminent process regulated in the organisation to analyse several steps important to design, implement, maintain and analyse the information systems (Saravanan et al. 2017). It is fundamentally important for the systems that are used by Sydney Gifts to maintain the stock for maintaining and gathering the manufactured products. Two systems development methods are the system development life cycle and the agile approach.
System development life cycle
The significant methodology is the product life cycle that includes important steps such as the development of the information systems. The life cycle includes steps such as planning, analysis, maintenance, implementation, and design. In planning, necessary problems of Sydney Gifts are acknowledged to determine the common scope of the traditional system. The problems are analysed to determine the extent to which the management will analyse the modern system (Tutorials point 2022). During the planning phase, challenges, integration, and system security exercised by the Sydney Gifts are considered. In the specification, the information that is collected during the survey is analysed, gathered and validate the relevant information. Furthermore, all the reports are prepared under implementation, which is important to execute the maintenance of the inventory system required to store the modern system.
Agile approach
In recent times the integration of the agile approach in the organisation has developed significantly among highly successful companies (Xu & Koivumäki 2019). The agile approach provides benefits to the organisation in managing important development around the project life cycle. The agile approach is a fundamental process in the project management process to implement an important process in regulating successful business. In user stories, the agile team can develop a fundamental estimation of the activities operated to accomplish the project management done by Sydney Gifts. Sprints are the amount of work that is done by the project members that are discussed in the project planning sessions. The organisation will hold a stand-up meeting to arrange all the members together to ensure the informed details are regulated by the people. Furthermore, in the agile approach, the agile board plays an important role in assessing the tasks that are implemented by the organisation in determining the agile movement.
5. Use case diagram
The use case diagram is signified as the process of determining the changing behaviour of the operating system (Javatpoint 2022). It determines the functionality of the systems while regulating actors, use cases, and their communication with the operating system. The common objective of the use case diagram is to determine the changing aspect of the system. The use case diagram will analyse the requirements necessary in the system that includes external as well as internal influences. The system requirements drive the use cases, persons, and multiple elements that drive the elements and actors that are needed for the implementation of the important use case diagram. Sydney Gifts uses this diagram to understand the changing demands, production of new products, and inventory management are used for analysing through the use case diagram. With the use case system, the Sydney Gifts gather the needs and preferences of consumers present in the operating system. The significant diagram also acknowledges the external and internal factors needed to influence the whole system. While implementing the use case diagram, the organisation needs to analyse the whole operating system of the company to find out the functionalities in the organisation. It can be asserted that the diagram has influenced the integration of the system incorporated by Sydney Gifts.
.png)
6. Context diagram
A context diagram signifies the system incorporated under consideration as a significant process to develop the process. It then determines the relationship between the system and the external aspects, including organisational groups, systems, and external data stores (Modernanalyst 2022). The context diagrams are developed to exercise the components important to structure the whole system of the organisation. Sydney Gifts arranges the context diagram that is important to regulate the synchronisation required in the organisation. The boundaries and scope are the relevant information needed to execute the important information. With the context diagram, the Sydney Gifts will use the technical systems to interface the system important for the organisation.
.png)
7. Level-0 Diagram
The data flow diagram determines the information flow in the system and process (Lucidchart 2022). It fundamentally uses symbols like circles, rectangles, and arrows, to provide storage points and outputs between the destination in the project management. The data flow diagram is an extensive process determined to regulate the diagrams needed in the organisation. Sydney Gifts will use DFD to encourage sustainable information to determine real-time, interactive, and database-regulated systems. The data flow diagrams regulate the fundamental integration while encouraging captivating criteria needed in the system.
.png)
8. Entity-relationship diagram
ERD is the significant element of the flowchart that determines how elements such as objects, people, and concepts link with each other in a confined system. ER diagrams are the fundamental element in determining the debugging and designing of the elements present in the business and research.
.png)
9. Conclusion
Based on the above research, it can be concluded that Sydney Gifts are operating a store that will run the products, including the chair, furniture, and paintings. The organisation implements the two system requirements, functional and performance requirements, to encourage the project management process. Diagrams like use case diagram, context diagram, diagram level, and an entity-relationship diagram are used to implement the project management.
References
SBD403 Security By Design Assignment Sample
Individual/Group - Individual
Length - 3,000 Words +/- 10%
Learning Outcomes-
The Subject Learning Outcomes demonstrated by successful completion of the task below include:
b) Administer implementation of security controls, security risk mitigation approaches, and secure design architecture principles.
c) Explain Secure Development Lifecycle models and identify an appropriate model for a given situation.
e) Apply security by Design industry standard principles in systems development.
Assessment Task
Create a document that advises on how to create a complete cyber security environment in an enterprise. Criticially analyse the basic requirements in conjunction with available technical and organizational cyber security methods and align them with adequate user experience. This has to be aligned with relevant industry or international standards, such as OWASP or ISO270xx. Please refer to the Instructions for details on how to complete this task.
Scenario
Consider you being the member of the CISO-Team (Chief Information Security Officer Team) of an enterprise with approx. 300 employees. The business of this company is
• performing data analysis for hospitals (i.e. how many diagnosises of what type)
• performing data analysis for retailers (i.e. how many products of what type). This data contains no personal data from shoppers such as credit cards. In both instances the data is provided by the respective client. All clients and all client data is from Australia only.
Because of the sensitive nature of the hospital data, the data is stored on premise while the retail data, because of sheer size, is stored in a cloud storage. The cloud provider fulfills all necessary security standards and resides in Australia. About 100 staff is working with the hospital data, this group is called “Doctors” and 200 with the retail data, group called “Retailers”. Every group is organised into a “support”-team, consisting of personal assistants, group head and group vice head and then the analysts. Every 20 analysts work on the same client, there is no one working on two or more clients’ data. The software that is being used for both groups is capable of having individual usernames and group roles. Access control for data can be set by username, group or both. The executives of the company (CEO, CFO and CMO) as well as their PA should not have any access to the data, the IT staff only when required for troubleshooting the application or storage.
Instructions
You will be asked to write a design guide how to create a secure environment for the enterprise since the client demand information about the safety of their data. This includes addressing the following topics:
• What kind of user training is required and explain why this suggested training is required to achieve a better cyber security?
• Perform a risk assessment to identify at least 5 major risks?
• What technical and/or organisational methods can be deployed to mitigate assessed risks? Name at least four technical and two organisational methods and indicate on how to deploy them. Describe the impact on the users ability to work for each method.
• If applicable identify mandatory methods out of the list created.
• Describe if user groups and user rights need to be implemented in the analysis application and the basic IT system (E-Mail, PC-Login etc.)
• Create an appropriate password rule for user accounts both in the application and for general IT and administration accounts (administrator, root, etc.). Explain why you chose this rule or those rules and align that with current standards (such as NIST)
• Define the required security measures for the storage and align them with current standards
• A recommendation for a plan of action for creating and maintaining proper information security.
• A recommendation for a plan to sustain business availabilities.
• A reference to relevant security and governance standards.
• A brief discussion on service quality vs security assurance trade-off (less than 500 words).
You will be assessed on the justification and understanding of security methods, as well as how well your recommendations follow Secure by Design principles, and how well they are argued. The quality of your research will also be assessed, you may include references relating to the case, as well as non-academic references. You need to follow the relevant standards and reference them. If you chose to not follow a standard a detailed explanation of why not is required. The content of the outlined chapters/books and discussion with the lecturer in the modules 1 – 12 should be reviewed. Further search in the library and/or internet about the relevant topic is requested as well.
Solution
Introduction
This case study for assignment help will construct client data security to make insight and potential protected IT controllable conditions and proposals as little hardship to real users and necessary to keep while retaining the top security standard possible. Here, anticipate the user’s participant of CISO-Team (Chief Information Security Officer Team) of such a company with approximately 300 staff. Therefore, the organization's main line of work is data analysis for health facilities. After that, this dataset includes no private information about customers, including credit card information. The data is made by the consistent user in both cases. On the other hand, training for the user will be required for analysis in the data security. There are identify the risk assessment and technical methods to mitigate the assessed risk will be evaluated. However, creating an appropriate rule for user accounts for software and General IT system will be illustrated to measure the security in this report.
Discussion
Required training for user
In order to, user training is necessary to able for enhanced a cyber-security to analyze the aims of user training regarding potential IT vulnerabilities and threats. It enables the users to recognize potential security risks when functioning online and sometimes with their software applications. Cybercriminals inject malicious into devices by using a wide range of effective methods, with newly developed techniques being advanced all the time. Users must be instructed in fixing issues, securing sensitive data, and reducing the likelihood of criminals obtaining personal details and records (Decay, 2022). The main cause for cyber-security training is to prevent business from malicious hackers who could harm the organization.
? A malicious actor is searching for aspects to gain entry to an organization's funds and personal user data, as well as extract money from enterprises.
? Therefore, choice to invest in information security is critical for all organizations, and their employees must have admin rights to an appropriate training scheme for work with potential malicious cyber risks, their data security training must be kept updated.
? User training is includes to evaluating the training information and keeping the data updated.
? There are various training tools available, such as simulating threats, increasing understanding and awareness as well as unusual threats, and providing detailed monitoring (Gathercole et al., 2019).
? The most fundamental type of cyber security training relies on increasing user insight into potential threats.
? There are several options for user training, which is included: Cyber security awareness, Antimalware training, and techniques for communicating data training.
On the other hand, more innovative systems are offered that may be perfect for the IT group as well as roles including cyber analysts. This learning is relevant to OWASP, the more Dangerous Application Errors According to CWE/SANS, DevOps training for protected server and delivery transactions. Some employees could be given training in a variety of risk management measures by transferring them to interactive or in-person basic training. Risk assessments, data protection, as well as intrusion detection systems are all part of cyber security. These systems are intended to teach technology scientific techniques while also providing users with hands-on knowledge in communicating with cyber threats. However, the General IT group can participate in the basic training course, whereas IT and information security professionals can sign up for enhanced programs.
Risk assessment identification
In order to, recognize and assess the five major risks against every type of attack that are mitigating by the following risk matrix table implemented for user training are as follows:
Risk matrix
.png)
To reduce the threats, a recognizing and prioritization table has been illustrated with the assistance of a risk assessment table, as shown below:
.png)
.png)
In the above table, Ransomware, Email phishing, DDoS attack, Trojan Malware and Network Failure are examples of security threats that demonstrate the impact of each threat on an organization. As a result, attacks on each threat priority are infrequently high, medium, and low. This table represented a priority to analyze threats in order to mitigate organizational assets in terms of network and application security.
Technical methods to mitigate the assessed risks
Organizational strategies can be used to prevent or reduce identified risks for users. Users might be effectively capable to implement, evaluate, and mitigate by using risk management solutions as well as risk assessment models (Lyu et al., 2019). There are a few strategies to evaluate to preventing the identified risks as follows:
? Risk Acceptance: Once the risk is low or unlikely to succeed, risk acceptance seems to be the right method. Whenever the price of minimizing or risk avoidance is greater than the amount of simply acknowledging it as well as exiting it to opportunity, it makes understanding to keep it.
? Risk Avoidance: Risk avoidance indicates refraining from engaging in the task that poses the risk. This approach to risk management is most similar to how individuals deal with specific risks (Arshad, & Ibrahim 2019). Although some individuals are much more risk-averse than others, the entire team has a critical threshold beyond which items become far too dangerous to undertake.
? Risk Mitigation: After threats are assessed, a few risks have been better avoided or accepted than others. The approaches and technologies of managing risks are referred to as risk reduction. Because once users identify potential risks as well as their likelihood, users can assign organizational resources.
? Risk Reduction: A most popular method is risk reduction since there is generally a method to at least minimize costs. It entails having to take preventive actions to lessen the severity of the influence (Freddi etal., 2021).
? Risk Transfer: Risk transfer entails transferring the risk to a different third entity and organization. Risk transfers could be delegated, transferred to an insurance firm, or transferred to a new organization, as when borrowing assets. Transferring risk does not always lead to reduced costs.
The four technological and two managerial strategies that are indicated to implement the threat are as follows:
? Agile development approach: All agile processes entail groups to make apps in phases that consist of micro of novel structures. The agile development process approaches in many flavours, such as scrum, crystal, extreme programming (XP), as well as feature-driven development (FDD).
.png)
Figure 1: Agile Development Methodology
(Source: Dhir, Kumar & Singh 2019)
? DevOps deployment methods: DevOps deployment focuses on managerial transformation that improves partnership among depts. responsible for many phases of the progress life span, including innovation, feature control, and actions.
.png)
Figure 2: DevOps Deployment Methodology
(Source: Battina, (2019)
? Waterfall development method: The waterfall development technique is broadly regarded as the maximum agile and out-dated technique. The waterfall approaches are indeed an inflexible linear model, comprised with various steps (needs, layout, application, confirmation, and preservation).
.png)
Figure 3: Waterfall Development Method
(Source: Firzatullah, (2021)
? Rapid application development (RAD): Rapid application development enables our teams to rapidly adapt to changing specifications in a fast-paced, ever-changing market. The user procurement and build phases are repeated until the consumer is satisfied that the design satisfies all specifications.
.png)
Figure 4: Rapid Application Development
(Source: Sagala, 2018)
Furthermore, the influence on the users' capability to work for each method for user training to get the major purpose of the agile software approach is that it enables apps to be issued in different versions. Sequential updates increase performance by enabling players to recognize and accurate defects although also supporting the potentials in the initial period. There are similarly allowing the users to gain the rewards of software as soon, appreciations to frequent gradual enhancements. DevOps is anxious with decreasing time to business, reducing the malfunction frequency of novel updates, reducing the time among repairs, as well as reducing interruption while optimizing trustworthiness. DevOps entities try to obtain this by programing agile methodologies to ensure that everything runs properly and smoothly. After that, the waterfalls advance strategy is modest to recognize as well as maintain due to its sequential environment. The waterfall technique tasks better to get initiatives with clearly defined goals and security criteria. However, the rapid application progress that ensure well- defined company goals as well as a defined group of users and aren’t difficult to salve. RAD is incredibly beneficial for time-sensitive tiny to medium- sized development.
Analysis of the application and basic IT system for user groups and user rights
User groups and user rights are essential to implement for application analysis to enable the generation of a ranking of all rational and reasonable application user groups. Some Systems can be controlled in the software platform just on the "Users" section. It is critical because each login user to understand to that which users he or she is appointed. On the other hand, application reliability is focused on multiple users (rather than particular users), novel users can be provided and eliminated (even in executable mode) without changing the software (Garzón, Pavón & Baldiris 2019). It enables the application's essential components to be recommended to ensure software user access. The basic IT system set up for user login on every user at such a web is indeed a basic framework organization task.
After that, a normal user email address contains all of the data required for such a consumer to sign in and then use a framework without knowing the platform's root user. In the user account aspects are to be defines the elements of the user account number. When individuals create a user email address, individuals could add its user to preselected user groups. A common use group would be to assign group approvals to a file system, providing access to certain members of that organization (Young, Kitchin & Naji 2022). A user could have a database with secret data that only a few users must have full rights to. However, users have create a highly classified group consisting of users who are functioning on the highly confidential task. Users could also give an extra highly classified group read access to the top confidential documents
Create an appropriate rule for user accounts both in the application and for general IT
In order to, develop a suitable password policy for user accounts in the assessment as well as general IT or government accounts to keep the accounts inside the software up to date. The following are the appropriate password rules for recognizing the accounts:
? Never, ever share their password with anybody: Username and password must not be distributed to everyone, such as educators, users, and employees. When someone needs full rights to another person's providing security, project of permission choices must be considered.
? Reset their password if users suspect a negotiated settlement: reset their username from such a computer user don't normally use. After that, reset their password, and notify the local users with various sections in management as well as the Data Security Executive (Wiessner, 2020).
? Rather than a password, take into account using a password: A password is a login composed of a series of words interspersed with data type as well as representational actors. A passcode can be verified or a preferred cite. Passwords generally have advantages including being higher and simple to understand.
Structures are not just a recent idea to cyber security experts, as well as the advantages are enormous - and individuals don't have to be advanced to be efficient. In this section, users look at the NIST Information Security Program but it must be a core component of their security plan. The NIST Cyber security Framework seems to be a consensual method that signifies millions of data security experts' combined experience. This is largely viewed as standards and specifications as well as the most extensive and in-depth set of safeguards available in any guideline. The CSF is indeed the result of a risk-based strategy that managers are very familiar with. This system allows for an interconnected risk management strategy to cyber security planning that is linked to the business objectives.
However, the company's interaction and decision-making would be expanding. The resources for security will be effectively acceptable and circulated. Considering its risk-based, outcome-driven strategy, the CSF is perhaps the most adaptable framework. There are Several businesses have effectively implemented it, reaching from big data security businesses in electricity, logistics, as well as funding to minor and midsize companies. It is strongly configurable because it is a consensual framework (Krumay, Bernroider, & Walser 2018). The NIST CSF is by far the most dependable form of security for developing and refining a security infrastructure in anticipation of new features to developed rules and requirements.
Security measures
A sufficient database security measures as well as track up them to today's standards to analyze security protocols and describe policy-based restrictions used for every data level of security when measured by standardized data; high-risk information needs more sophisticated protection. Users can incorporate cyber security depending on the dangers associated if users comprehend what information individuals have or what requires to be defended are as follows:
? Implement Successful Data Storage Safety Regulations: Every organization must develop, implement, and maintain an extensive data storage security policy. To be efficient, digital storage safety measures are needed everywhere, including the workplace, portable apps, storage systems, on-premise facilities, as well as online.
? Safeguard Their Managerial Configurations: Companies frequently set measures to safeguard data as well as documents storage devices from illegal access whereas ignoring management connectivity security. This might enable the user to gain elevated special rights or an attacking player to create their roots in cultural qualifications, in addition to providing data they must not have direct exposure to.
? Install Data Loss Prevention (DLP) System: Implementing a data loss prevention (DLP) is a key of the most efficient data security standards. A data loss prevention system (DLP) recognizes, provides protection, as well as displays information over the internet and information stored in their storage facilities, including computers, laptops, tablets, smartphones, as well as other equipment (Hussain, & Hussain 2021).
? Measure User Data Authentication and authorization: In this case, another excellent way to improve data security would be to measure user data security controls. It aids in providing secure users ’ access even while retaining user rights to make sure that people only obtain information required to finish their tasks.
Recommendation of maintaining proper information security
The maintaining proper information Security and privacy protections are intended to prevent the unauthorized release of data. Here, the privacy and security mentioned principle's objective is to ensure that individual data is secured and that it can only be viewed or acquired by people who need help that training to perform their job tasks. Therefore, data security requires protection against unauthorized access (e.g., addition, deletion, or modification) (Srinivas, Das & Kumar 2019). The consistency concept is intended to confirm that info can be respected to be reliable as well as hasn’t been improperly altered. A security availability in relevant data is the prevention of structural systems with their characteristics as well as the acknowledgment, that information is entirely available and affordable during the time period or when it is needed by its participants. The objective of convenience is to assure people which data exists and use it when making a decision.
Recommendation for a plan to sustain business
In this section, Recommended for a plan to sustain the business because every organization wants to expand their business, but few recognize how and where to sustain it all in the long run or take a glance at the upcoming monthly or annual survey. Business expansion necessitates the right knowledge assets, carefully chosen partnership opportunities, and goods or both products and services that are in high supply in the business. Aside from these basics, supporting the business necessitates an allowing organization's framework in order to minimize the incidence to the long-term strategy.
? Top Skill: Without such an appropriate person, a company can develop and will struggle to maintain acceleration over time. Users are at the heart of the company because without the appropriate person, it cannot grow as well as advanced.
? Operational Efficiencies: Efficiency improvements drive down costs as well as incorporate an attitude inside the worksite community that creates cost society consciousness, as well as methods to improve how well the organization responds, performs, and integrates the data points of possibilities.
? Prospecting the Right Users: Being a businessman is more than just a job title; it was a lifestyle. To get together and detain the best opportunity - particularly ones previously unheard of or that someone doesn't see behind - users should always adopt an innovative business mind-set (Østergaard, Andersen & Sorknæs, 2022).
? Sound Decision-making process: The significance of what maximum advantage to do was to resolve issues. The primary objective of representatives is to prevent the risk of issues, which also indicates users should be brave enough then to confront them head-on.
? Excellent Leadership: The most effective people end up making impulse decisions and, as a result, have a rotating vision that observes opportunity in everything.
A brief discussion on service quality vs. security assurance
A brief overview of the service quality vs. security assurance has been analyzed into the specific framework of software, all these words are important. Service quality software implies it will perform under its characteristics and functions. Security implies that the framework would not allow confidentiality of data as well as computational capabilities. Whereas quality appears to be simpler to understand, both are slightly contextual in their evaluation. Service quality and service assurance concerns are both considered defects from those who begin taking a comprehensive approach to designing and development. A problem can be described as a "frailty as well as insufficiencies that restricts a product from becoming comprehensive, attractive, efficient, secure, or of significance, or causes it to breakdowns or underperform in its intent" by security research to improve (Obsie, Woldeamanuel & Woldetensae 2020). This procedure may pressure the application to give a response that is outside of the implementation flow's standard parameters. According to the concept of "defect," this same operating system stopped functioning or underperformed its activity. This is a flaw and falls under the classification of satisfaction. On either side, more investigation will be required to determine whether the deficiency does have a security aspect. When a user can show that manipulating this flaw in some manner to obtain unauthorized access to confidential or the system falls under the classification of privacy, this will also come under the segment of security.
On the other hand, service assurance and service quality is such a flaw is easily a logical flaw that, whereas feasibly inconvenient, doesn't generate a hack able vulnerability. The programmer can password the operating systems under the demands while still making it susceptible to Injection attacks. The linked malfunction would've been security-related, but it does represent a quality deficiency. There are most would make the argument that such a security flaw is a quality issue. A user could comfortably accommodate that type of thinking, and others would take a structure to achieve. This proves that protection is not a subsection of quality. The fact that quality and security have been operationally divided in conventional development shops contributed to the confusion. The quality assurance department, which was usually located somewhere within the management framework, had been in charge of quality (Shankar et al., 2020). This aids the programmers with quality assurance as well as testing. IT security personnel were in charge of security. There are several organizations' connections with advancement were badly described and even worse implemented. IT Security, as well as QA, might have occurred in different worlds and not recognized it. The conventional quality and security storage facilities have to come back down by necessity as development programmers have developed and agile methodologies keep taking root. Security has been incorporated into the development phase so that designers can incorporate security best practices into their code. Accordingly, designers are now jointly responsible for quality.
Conclusion
A brief analysis has been built on client data security to consider making insight and potential secured IT manageable conditions and proposals as painless for real users as possible while maintaining the highest security standard possible. Consider the user as a member of the CISO-Team (Chief Information Security Officer Team) of an organization with assessed 300 employees. As a result, the organization's primary focus is data analysis for health care facilities. Following that, no sensitive data regarding users, including account information, is included in this dataset. On the other hand, training for the user has been required for analysis for data security. There are recognize the risk assessment and technical methods to mitigate the assessed risk have been demonstrated. However, creating an appropriate rule for user accounts for software and the General IT system has been illustrated to measure the security in this report.
Reference
.png)
.png)
BUS5PB Principles of Business Analytics Assignment Sample
Task 1
Read and analyses the following case study to provide answers to the given questions.
Chelsea is a lead consultant in a top-level consulting firm that provides consultant services including how to set up secure corporate networks, designing database management systems, and implementing security hardening strategies. She has provided award winning solutions to several corporate customers in Australia.
In a recent project, Chelsea worked on an enterprise level operations and database management solution for a medium scale retail company. Chelsea has directly communicated with the Chief Technology Officer (CTO) and the IT Manager to understand the existing systems and provide progress updates of the system design. Chelsea determined that the stored data is extremely sensitive which requires extra protection. Sensitive information such as employee salaries, annual performance evaluations, customer information including credit card details are stored in the database. She also uncovered several security vulnerabilities in the existing systems. Drawing on both findings, she proposed an advanced IT security solution, which was also expensive due to several new features. However, citing cost, the client chose a less secure solution. This low level of security means employees and external stakeholders alike may breach security protocols to gain access to sensitive data. It also increases the risk of external threats from online hackers. Chelsea strongly advised that the system should have the highest level of security. She has explained the risks of having low security, but the CTO and IT Manager have been vocal that the selected solution is secure enough and will not lead to any breaches, hacks or leaks.
a) Discuss and review how the decision taken by the CTO and IT Manager impacted the data privacy and ethical considerations specified in the Australia Privacy Act and ACS Code of Professional Conduct and Ethics
b) Should Chelsea agree or refuse to implement the proposed solution? Provide your recommendations and suggestions with appropriate references to handle the conflict.
c) Suppose you are a member of Chelsea’s IT security team. She has asked you to perform a k-anonymity evaluation for the below dataset. The quasi-identifiers are {Sex, Age, Postcode} and the sensitive attribute is Income.
In the context of k-anonymity: Is this data 1-anonymous? Is it 2-anonymous? Is it 3-anonymous? Is it 4- anonymous? Is it 5-anonymous? Is it 6-anonymous? Explain your answer.
Task 2
There is a case study provided and you are required to analyse and provide answers to the questions outlined below.
Josh and Hannah, a married couple in their 40’s, are applying for a business loan to help them realise their long-held dream of owning and operating their own fashion boutique. Hannah is a highly promising graduate of a prestigious fashion school, and Josh is an accomplished accountant. They share a strong entrepreneurial desire to be ‘their own bosses’ and to bring something new and wonderful to their local fashion scene. The outside consultants have reviewed their business plan and assured them that they have a very promising and creative fashion concept and the skills needed to implement it successfully. The consultants tell them they should have no problem getting a loan to get the business off the ground.
For evaluating loan applications, Josh and Hannah’s local bank loan officer relies on an off-the-shelf software package that synthesizes a wide range of data profiles purchased from hundreds of private data brokers. As a result, it has access to information about Josh and Hannah’s lives that goes well beyond what they were asked to disclose on their loan application. Some of this information is clearly relevant to the application, such as their on-time bill payment history. But a lot of the data used by the system’s algorithms is of the kind that no human loan officers would normally think to look at, or have access to —including inferences from their drugstore purchases about their likely medical histories, information from online genetic registries about health risk factors in their extended families, data about the books they read and the movies they watch, and inferences about their racial background. Much of the information is accurate, but some of it is not.
A few days after they apply, Josh and Hannah get a call from the loan officer saying their loan was not approved. When they ask why, they are told simply that the loan system rated them as ‘moderate-to-high risk.’ When they ask for more information, the loan officer says he does not have any, and that the software company that built their loan system will not reveal any specifics about the proprietary algorithm or the data sources it draws from, or whether that data was even validated. In fact, they are told, not even the developers of the system know how the data led it to reach any particular result; all they can say is that statistically speaking, the system is ‘generally’ reliable. Josh and Hannah ask if they can appeal the decision, but they are told that there is no means of appeal, since the system will simply process their application again using the same algorithm and data, and will reach the same result.
Provide answers to the following questions based on what we have studied in the lectures. You may also need to conduct research on literature to explain and support your points.
a) What sort of ethically significant benefits could come from banks using a big-data driven system to evaluate loan applications?
b) What ethically significant harms might Josh and Hannah have suffered as a result of their loan denial? Discuss at least three possible ethically significant harms that you think are most important to their significant life interests.
c) Beyond the impacts on Josh and Hannah’s lives, what broader harms to society could result from the widespread use of this loan evaluation process?
d) Describe three measures or best practices that you think are most important and/or effective to lessen or prevent those harms. Provide justification of your choices and the potential challenges of implementing these measures.
Guidelines
1. The case study report should consist of a ‘table of contents’, an ‘introduction’, logically organized sections or topics, a ‘conclusion’ and a ‘list of references’.
2. You may choose a fitting sequence of sections for the body of the report. Two main sections for the two tasks are essential, and the subsections will be based on each of the questions given for each task (label them accordingly).
3. Your answers should be presented in the order given in the assignment specifications.
4. The report should be written in Microsoft Word (font size 11) and submitted as a Word or PDF file.
5. You should use either APA or Harvard reference style and be consistent with the reference style throughout your report.
6. You should also ensure that you have used paraphrasing and in-text citations correctly.
7. Word limit: 2000-2500 words (should not exceed 2500 words).
Solution
Task 1
1a)
The consideration of the ethical aspect is quite important in ascertaining the implementation of the different research strategies and approaches for attaining goals related to the Australia Privacy Act and ACS Code of Professional Conduct and Ethics. The Australian privacy act implements the protection of the personal data in any given condition. It has been observed that CTO and IT Manager is trying to implement the strategies that relies on the low security of the organization. This low security can be quite fatal to the organization since it is quite prone to be hacked by the cyber-crime experts. The Australian Privacy Act is trying to implement the strategies which can provide the guaranteed security to the information which is available to the organization.
The different types of the strategies are a major contributor to influencing changes in behavior, attitudes, and accuracy and directing them towards improved performance. These can serve as a tool for the organization to develop the strategies that could aid in improving the current scenario regarding the improvement of the data security (Riaz et al. 2020). Data security is a powerful tool for improving the authenticity of the organization and their ability to manage their information over time for best assignment help.
Data security of the Australian government promotes an increased, continuous, and strategic improvement of the existing information about the data. The policy of the government has focused on the upsurge in the implementation of the different types of data of the customers. The data security has the attribute in safeguarding any kind of the vulnerable security to the customers by the implementation of the strategies that could help in augmenting the security of the organizations (Ferdousi, 2020)
In recent years, the modern data encryption strategy is usually implemented for determining the safety requirements of the data which is available to the company for example the salary of the employees and the customer’s details of the organization. This model is commonly referred to as advanced data security. In the event of a stable environment regarding the safe guarded data of the organization this will enable the improvement of the confidence level of the persons towards the organization.
The rise of the utilization of the strategies due to their technological advancements gives them an advantage over the traditional models of data security with the aid of the suitable strategies. It has investigated the impact of the data security technique of the government would improve the current scenario of the data security and would help to improve the current scenario. The information regarding the different modes of the data security strategy has to be considered for relevant fields of any project of the organization (Zulifqar, Anayat, and Kharal, 2021).
Various factors with varying degrees of influence were identified that mediate the implementation of the advanced data security technique. The tools to envisage the impact of the implementation of the data security techniques and the current performance deliverables through the adoption of the innovative data security strategy are all considered in this context. In this context, it is essential to identify the suitable strategies that are doctrine by the government.
However, in the current context the company is trying to implement the low security strategies to protect the privacy of the data which is available to the company. In this regard it can be suggested that the company has given more priority in saving the operational cost of the company by retaining the existing mode of low security technique. However, in this case this strategy is in utter contrast to the existing policies of then government. This strategy will have a negative impact in the current scenario and would also encourage the competing agencies to adopt the similar strategies that partly compromise the security of the information which is available to the company. In this context, it must be noted that the company must ensure the safety of the organization and this should be held in high priority over all the existing conditions.
1b)
The company is resorting to the techniques which are not conducive to the current scenario when the government is endorsing the high security of the personal information. In the current scenario, according to me Chelsea is correct in her arguments. Chelsea is endorsing the high security for protecting the data of the company and to prevent the breach of the vulnerable data that could hamper the credibility of the company. Hence according to my opinion Chelsea has an edge in this argument. However, the company is correct in its justification that the high security system is quite expensive. It is to be noted that the advanced encryption system is undoubtedly quite expensive and the company is prone to suffer from huge operational cost in the case of implementation of this expensive strategies. In this case it is also to be noted that the company can implement the less expensive strategies that can give moderate security and improve the existing security system of the organization. The k anonymization strategy would be helpful in safeguarding the data of the customers and the employees. In this connection it is essential to de-identify the available dataset and this could further improve the security of the concerned organization. The k anonymization helps in removing the identities of the several categories and after the removal of the identities the appropriate codes are given to the data so that the breaching of the information can be effectively controlled (Sai Kumar et al., 2022)
Hence the conflict that is existing between Chelsea and the management of the company can be resolved by the implementation of the cost effective strategies by the company. However, the proper strategies must be implemented for safeguarding the privacy of the company as this would help in improving the reliability of the organization. The confidence of the customers and the employees can be improved significantly by the incorporation of the suitable de-identification techniques that could protect the vulnerable data of the organization (Madan, and Goswami, 2018). Thus I highly support the opinion of Chelsea keeping in mind the interest of the company. Thus the amalgamation of cost effectiveness and the data security of the organization aids in the improvement of the present condition of the company.
1c)
In this case 2 anonymous systems have been followed. This system is involved in the anonymising or hiding the details of the two categories of the members in the company. These two categories are identity and the post code of the employees. The income of the employee is a very sensitive topic and the proper de identification of the data should be done for ensuring that there is no such breach of vulnerable information that can disturb the reputation of the company. Here in this case the ID of the employees has been denoted with the aid of the codes like1, 2, 3, 4, etc. The post code has also been denoted with the aid of the codes like 308 and 318.There must be some distinctions in the codes that have been applied in this respect. However, all the post codes have not been revealed in this context and this denotes that this data has also been de-identified. However, the other categories like the age, gender and the income of the employees has been mentioned in details. Thus the k anonymization strategy has followed the 2 anonymous systems.
Task 2
2a)
The big data driven system of loan approval system is a rapid system of loan approval and it helps in envisaging the loan applications quite quickly and on time (Hung, He, and Shen, 2020.) The credit risk assessment is done in a programme driven manner and this enables the system to handle a lot of application in one given point. Thus this type of computerized big-data driven system helps to reduce a lot of manual labor and this also helps to perform the work in a shorter span. Hence both the time and labor of work is reduced in this type of loan approval system that employs the big data system.
2b)
In the case of the big data driven rejection of the loan application there are certain hazards that are associated with this type of rejection. In this case Josh and Hannah were denied of the loans due to the evaluation by the big data and this type of rejection was computerized. In this context the ethical issues are as follows
Creation of confusion-In this case of big data driven rejection of loans the loans are rejected or accepted according to the computer programming. The applications which lack the key requirements are usually rejected in this type of loan approval system. On the other hand, in the case of the manual loan approval, the person responsible for evaluating the loan applications had the duty to explain to the applicants the reason of their failure. However in the case of a computerized system there is no such opportunity to get the required clarifications from the system. This causes a great deal of confusion in the minds of the applicants like Josh and Hannah about the reason for their failure. This lack of knowledge also prevents the applicants to reapply for the loan by fulfilling all the required criteria. Thus this creates a lot of doubt and confusion in the minds of the applicants regarding the rejection.
Lack of transparency and Confidence-As discussed earlier the big data driven loan approval system is devoid of the capability to inform about the exact reason for the failure of the loan application. This creates of confusion and thus this depletes the transparency related to the loan approval system of the bank. The applicants are confused regarding the process and often doubt the unbiased nature of the selection process. The lack of knowledge also heavily contributes to the absence of adequate confidence regarding the loan approval system of the bank.
Doubt regarding discrimination-The lack of knowledge about the existing loan approval system contributes to the development of the doubt in the minds of the loan applicants. The loan applicants are not sure about the unbiased nature of the system since the system is not providing bthe adequate justification of their loan rejection. This instills a belief in the minds of the applicants that they might be the victims of various types of discriminations. This discrimination can be due to the social status r their economic status. The applicants often believe that they have been subjected to discriminatory behaviour due to their existing social or economic conditions. This can be a very disturbing issue since the people rely solely on the banking system for getting loans during their crisis period.
2c)
The people of the society heavily rely on the banking system to obtain the required loans during their financial crisis. The loan rejection like Josh and Hannah can have a deep rooted impact on the society since this type of loan rejection does not provide the necessary reasons for the rejection of the loan. This creates a lot of confusion and doubts in the minds of the loan applicants. In such case there is depletion in the transparency and unbiased nature of the banking system. The transparency of the banking system is quite necessary in the society and this damage to the transparency of the banking system disrupts the confidence levels of the people. Furthermore, it has been observed that due to the lack of adequate knowledge about the reasons for the loan of denial, the people might think that the bank is exhibiting a discriminatory approach towards them and this can be quite fatal top the brand image of the bank or the organization which is providing loans.
2d)
The big data analysis should not be solely implemented for the selection of the loan application. The applications must not be contingent upon the database and the data analytics of the concerned system (Agarwal et al., 2020). This type of system cannot be applied in all categories of the loan application and the methods should be properly checked before the application. According to my opinion the methods that should be implemented to reduce the cases of discontent regarding the rejection of the loan application are as follows
Current Income-The current income of the individuals must be checked beforehand in order to know whether that concerned person would be able to repay the debt on time. The current income of the individual must be given priority since the person would be able to repay the debt on time only when the person has a steady flow of cash.
Occupation-The occupation of the individual is quite crucial in estimating whether the person can repay the debt on time. The occupation must be stable in nature for determining whether the concerned person would be able to pay off the debt and would be eligible for the lo0an application
Repayment History-It is essential to denote the intention of the people to repay the debt on time. It is essential to prioritize the willingness of the people to repay the debt and in this case it becomes quite imperative to consider the repayment history of the individuals. This indicates that the concerned individuals will be able to repay the debts on time by considering the repayment history of the individuals.
Thus according to my opinion, it is essential to consider the above mentioned parameters since this parameter appropriately estimates the ability of the individuals to repay the debts on time. Thus these parameters must be given more importance than the existent big data driven loan approval system.
References
.png)
COIT12208 Duplicate Bridge Scoring Program Assignment Sample
Case Study: A Not-for-Profit Medical Research Center
You are Alexis, the director of external affairs for a national not-for-profit medical research center that researches diseases related to aging. The center’s work depends on funding from multiple sources, including the general public, individual estates, and grants from corporations, foundations, and the federal government.
Your department prepares an annual report of the center’s accomplishments and financial status for the board of directors. It is mostly text with a few charts and tables, all black and white, with a simple cover. It is voluminous and pretty dry reading. It is inexpensive to produce other than the effort to pull together the content, which requires time to request and expedite information from the center’s other departments. At the last boarding meeting, the board members suggested the annual report be “upscaled” into a document that could be used for marketing and promotional purposes. They want you to mail the next annual report to the center’s various stakeholders, past donors and targeted high-potential future donors. The board feels that such a document is needed to get the center “in the same league” with other large non-for-profit organizations with which it feels it competes for donations and funds. The board feels that report could be used to inform these stakeholders about the advances the center is making in its research efforts and its strong fiscal management for effectively using the funding and donations it receives.
You will need to produce a shorter, simpler, easy-to-read annual report that shows the benefits of the center’s research and the impact on people’s lives. You will include pictures from various hospitals, clinics, and long-term care facilities that are the results of the center’s research. You also will include testimonials from patients and families who have benefited from the center's research. The report must be “eye-catching”. It needs to be multicolor, contains a lot of pictures and easy-to-understand graphics and be written in a style that can be understood by the average adult potential donor. This is a significant undertaking for your department, which includes three other staff members. You will have to contract out some of the activities and may have to travel to several medical facilities around the country to take photos and get testimonials. You will also need to put the design, printing, and distribution out to bid to various contractors to submit proposals and prices to you. You estimate that approximately 5 million copies need to be printed and mailed.
It is now April 1. The board asks you to come to its next meeting on May 15 to present a detailed plan, schedule, and budget for how you will complete the project. The board wants the annual report “in the mail” by November 15, so potential donors will receive it around the holiday season when they may be in a “giving mood”. The center’s fiscal year ends September 30, and its financial statements should be available by October 15. However, the non-financial information for the report can start to be pulled together right after the May 15 board meeting. Fortunately, you are taking a project management course in the evenings at the local university and see this is an opportunity to apply what you have been learning. You know that this is a big project and that the board has high expectations. You want to be sure you meet their expectations and get them to approve the budget that you will need for this project. However, they will only do that if they are confident that you have a detailed plan for how you will get it all done. You and your staff have six weeks to prepare a plan to present to the board on May 15. If approved, you will have six months, from May 15 to November 15, to implement the plan and complete the project. Your staff consists of Grace, a marketing specialist; Levi, a writer/editor; and Lakysha, a staff assistant whose hobby is photography (she is going to college part-time in the evenings to earn a degree in photojournalism and has won several local photography contests).
Case Study Questions for assignment help -
Question 1
Establish the project objective and make a list of assumptions about the project.
Question 2
Develop a Work Breakdown Structure (WBS) for the project.
Question 3
Prepare a list of the specific activities that need to be performed to accomplish the project objective. For each activity, assign the person who will be responsible for seeing that the activity is accomplished and develop an estimated duration for each activity.
Question 4
Create a network diagram that shows the sequence and dependent relationships of all the activities.
Question 5
Using a project start time of 0 (or May 15) and a required project completion time of 180 days (or November 15), calculate the Earliest Start (ES), Earliest Finish (EF), Latest Start (LS), and Latest Finish (LF) times and Total Slack (TS) for each activity.
If your calculations result in a project schedule with negative TS, revise the project scope, activity estimated durations, and/or sequence or dependent relationships among activities to arrive at an acceptable baseline schedule for completing the project within 180 days (or by November 15). Describe the revisions you made.
Question 6
Determine the critical path, and identify the activities that make up the critical path.
Solution
Project Objectives and Assumptions
The primary objective of this project is to prepare the annual report for the company within a specified date. In order to achieve this objective, several requirements must be followed that are listed below.
To collect sufficient data regarding the organisation’s services and performance
To collect financial data of the company for the current fiscal year
To visit various facilities of the company around the country and collect photographs, testimonials and interviews of patients and their families
To create the documentation contents in the form of the annual report
To add the collected pictures and data to the report
To hire a contractor for design, printing and distribution of the annual report
To get the report approved by the management
The assumptions made for this particular project are as follows.
- The entire project work can be completed within the 6 months window, working 5 days a week.
- The current group of staff is sufficient and skilled enough to handle all the necessary actions during the project execution.
Work Breakdown Structure
Work breakdown structure is a representation of the list of tasks within a project that can be shown in the form of a table or diagram. The purpose of the diagram is to break down the entire project into smaller individual activities and work packages that help the team members to better understand the work requirements and their duties in the project.
The work breakdown structure for the project in focus is shown in the following diagram.
.png)
Figure 1: Work Breakdown Structure of the Project
(Source: Created by Author)
Activities, Duration and Resources
The list of activities along with estimated duration and resources attached is given in the following table.
.png)
.png)
The overall list above contains the entire cycle of the project that starts right after the kick off meeting of April 1. However, the main part of the project (execution) starts on 15th May and the durations for the work packages have been allocated in such a way that the execution phase ends on 15th November with the submission of the fully prepared annual report to the board, as per the necessary requirement and agreement. The detailed schedule based on the allocated dates and duration can be shown in the form of a Gantt chart as follows.
.png)
Figure 2: Gantt Chart of the Project
(Source: Created by Author)
Network Diagram
The purpose of a network diagram is similar to a Gantt chart i.e. exhibiting the project schedule but in much more detail. The network diagram shows details of each activity including project duration, start and end dates, allocated resource within each single box representing a work package. While Gantt chart can also exhibit the same, it can become very confusing to view the details of a particular activity / work package when the project is very complex and there are vast numbers of activities.
.png)
.png)
Figure 3: Network Diagram (Shown part by part in chronological order)
(Source: Created by Author)
ES, EF, LS, LF, TS
.png)
Figure 4: ES, EF, LS, LF and TS for the Execution Phase of the Project
(Source: Created by Author)
The diagram above depicts a PERT chart that shows the sequence of tasks in the project. Since actual part of the project is considered to be the execution phase that starts on 15th May and ends on 15th November, only the execution phase in drawn in the diagram rather than the entire project that has been shown in the WBS. In the legend added to the top left of diagram, the meanings of the abbreviations are as follows.
ES – Early Start
EF – Early Finish
DUR – Duration
LS – Late Start
LF – Late Finish
TS – Total Slack
For this part of the project, the total duration has been considered to be 6 months (May 15 = day 0 and November 15 = ending date).
Critical Path
Based on the diagram shown above and the calculations the critical path of the project can be stated as (using WBS IDs):
3.1 > 3.2 > 3.3 > 3.7 > 3.8 > 3.9 > 3.10 > 3.13 > 3.14
The critical path itself has been already highlighted in the above diagram itself, in the form of red arrows whereas non-critical paths are shown with blue arrows.
DSAA204 Data Structure and Algorithms Assignment Sample
ASSESSMENT DESCRIPTION:
This assessment is an individual report about the design of an OOP system using Data Structures and Algorithms. The report should follow the following structure
1. Title Page
2. Executive Summary
3. Introduction
4. Background
5. Case Study and the Design
5.1 Variables, Ranges and Keys
5.2 Operations and the Justification
5.3 Algorithms and the Justification
5.4 Modifications
6. Conclusion
7. References
Case Study:
You are required to design a health system for a small medical partitioning centre with information about doctors and patients. Assume that there are: 50 Doctors 100 Nursing staff
Around 1000 patients. You need to decide how would you like to represent the doctors, nursing staff and patients. For each of these decide what variables should be there (think in terms of OOP design). Also provide ranges for these variables. You will need to specify keys as well to carry out some essential operations related to this health system. Identify and list down potential keys for given entities.
Use your knowledge of real world and think about operations that will be needed for the health system. Keep in mind that it is not a complete hospital management system but should support the main/basic operations. Mainly, we are interested in locating the records of doctors, nursing staff and patients, but should support all basic operations of any information system. For each of these operations, discuss the most suitable algorithms that can implement these operations efficiently. Use your knowledge of various algorithms to suggest why your chosen algorithm for each operation is the most appropriate one. Your justification should talk about the different properties/characteristics of algorithms and explain as to why your chosen algorithm is best suited to the problem in question.
Now, a public hospital wants to adopt your system for computerizing their records of staff and patients. The hospital has a total of 1000 doctors, 4000 nurses and around 10,000 patients. Do you think your previously suggested algorithms would be able to handle this volume of data efficiently? If yes, justify and if not, suggest the new set of algorithms (and change in data structures, if needed) that will ensure that system will work smoothly and efficiently.
Solution
Executive Summary
A database was built for the health-care system. It makes it easier to maintain track of all of the patients' and physicians' information. It stores all databases in a secure manner for future usage. More than 100 nurses and 50 doctors have been assigned to this new system. They will be responsible for roughly 1000 patients. This detail will aid in the storage of all information pertaining to each and every member of the nursing staff, as well as doctors and patients. The database integrity restrictions are being rechecked for all data by system developers. Keys such as foreign keys and main keys will be stored in certain data. All database developers are concentrating on using enough variables. This new information system has a large amount of data.
Introduction
The purpose of this paper is to explore the fundamentals of implementation. All data formats and their algorithms will contribute to the development of a contemporary health information system. In comparison to other manuals, this one, or the conventional one, is not as effective. Currently, however, this storage technique is making this massive dataset more time-consuming. The efficient application of sorting and searching algorithms will improve all of these data management and storage activities. Healthcare for assignment help is a collaborative endeavour. Each healthcare professional is treated as a valuable part of the team who plays a specific function. Some members of the team are doctors or technicians who assist in illness diagnosis. Others are specialists who cure diseases or look after the physical and emotional requirements of patients. Administrative staff members plan the appointment, locate the medical record, phone the patient for a reminder, meet the patient, and check insurance details. A nurse or medical assistant takes the patient's weight and vital signs, leads them to an exam room, and documents the purpose for their appointment. Each health system's primary goal is to improve people's health, but it isn't the only one. The goal of excellent health is twofold: the highest possible average level – goodness – and the lowest possible disparities between individuals and groups – fairness. Fairness indicates that a health system reacts equally well to everyone, without prejudice, and goodness means that it responds well to what people expect of it. Each national health system should be oriented to accomplish three overarching goals, according to the World Health Organization (WHO): excellent health, responsiveness to community expectations, and financial contribution equity.
Background
This new health information system was created as a result of the previous system's inability to handle such large amounts of data. However, the engineers are striving to improve this new system by enabling all of these new sorting and searching approaches to be considered. Developers are always attempting to improve the contemporary system. Allowing all of these approaches for searching and sorting reasons, as well as providing some attention, will be beneficial. However, because health systems lack the ability to offer access to high-quality treatment, private health-care systems have evolved at the same time, with a steady and progressive development of private health-care services. Healthcare is a highly fragmented sector, with different healthcare systems in different countries. In the United States, insurance coverage is mostly the responsibility of the individual; however, new legislation will make it more universal. Other industrialised countries, such as the United Kingdom, Canada, Australia, and Italy, give free healthcare to all residents. During the previous decade, technological advancements have dominated healthcare activities, resulting in enhanced techniques of detecting and treating diseases and injuries. Infection control, less invasive surgical procedures, advancements in reproductive technology, and cancer gene therapy have all emerged as clinical developments
Case Study and Design
Variables, Ranges and Keys
In object-oriented programming, the program modules are broken down into classes and objects. The classes and known as the user-defined variables in this programming concept. The classes in general consist of member variables and member functions. When a program creates objects of these classes which are also known as instance variables, several instances of the class type are created (Varga et al. 2017,p. 7). These objects are then be stored into respective data structures such as arrays or lists, which can be accessed and modified as necessary. In the case of this health system, a similar object-oriented programming design would be constructed and the classes, variables, function, and data structures would be listed with their respective ranges and required justification. Each of these classes will also consist of a member variable that will be unique for each of the created objects.
Using the right Data Structure is also very important in information system development. There are various data structures that allow static insertion and modification of data while there are other more convenient and efficient data structures that allow the dynamic handling of data (Weise et al. 2019,p. 344). In an information system such as this, a dynamic Data Structure would be preferred that would allow easy insertion, deletion, and modification of data.
This variable would be called the key data member for the entities with his help in unique identification. The identified class variables, objects and Data Structures are as follows:
The Classes: Doctor, Nurse, Patient, MedicalCentreSystem
Doctor Class Variables:
.png)
Nurse Class variables:
.png)
Patient Class variables:
.png)
MedicalCareSystem Class variables:
.png)
.png)
Operations and the Justification
Insert new Doctors, Nurses or Patients: This operation will help the system administrators to add new doctors, nurses and patients into the system. This process will include the session of data that includes all the required details and variables mentioned for the respective classes (Kleine and Simos 2018,p. 54). On validation of these inputs, respective doctor, nurse, or patient class objects will be created and will be stored in their respective data structure. On the creation of each of these objects, a unique ID would be created and set into the object variables.
Search available Doctors, Nurses or Patients: Searching is another very important operation that is performed frequently on any information system. In this medical centre system, the searching can be performed due to the need for accessing user data or in order to modify respective data models (Lafore 2017,p. 242). Searching can be performed based on the criteria of searching doctors, nurses, and or patients.
Sort current patients on the basis of their net_bills: This functional feature would allow the system administrator has to look for patients who are admitted currently in the order of the highest to lowest medical bills. This will allow the administrators to offer certain amenities or in other financial and taxation utilities.
Algorithms and the Justification
There are two major algorithms that can be primarily used for a smaller data storage system that has been identified in the initial case study. One of these algorithms would allow easy operations for searching while the other will allow the operation for sorting the required data elements. These respective searching and sorting algorithms are as follows:
- Linear search: Through this technique a data structure is linearly search from top to bottom in order to find the required data element. The complexity of this algorithm is O(n).
- Bubble sort: This is one of the most commonly used sorting techniques. In this program, the sorting technique can be used to arrange the patient in order of their medical bills. This sorting technique can be used to arrange both alphabetical and numerical data on the basis of ascending or descending order as required (Priyankara 2020,p. 317). In this algorithm, the sorting is done on the basis of the general swapping of two elements in a linear manner. The entire data structure is traversed having swapped through all the different elements in the required order that is ascending or descending, the list would be sorted in general. This algorithm can also be used with objects stored. The time complexity of bubble sort is O(n2).
.png)
Modifications
Considering that the data requirements for this system would be rising in recent years, certain modifications will be required in terms of performing the various operations using the given algorithms. The above-mentioned algorithms are suitable when the data set is fairly low. However, in a larger data storage system, it is better to use algorithms that will perform this task in a more efficient manner in terms of time and resources (Chawdhuri 2017,p. 324). The following algorithms should be applied in order to search and sort on a system with a larger data set:
- Binary search: The time complexity of this algorithm is O(log n). This algorithm divides the data set into two halves in a particular sorted order and then makes it easier to search for the data.
.png)
- Merge sort: The time complexity of MergeSort is O(n*log n). This, therefore, helps in a very efficient manner of sorting on the larger accumulation of data. Merge sort is considered to be one of the most important and efficient sorting algorithms in computer programming (Teresco 2017,p. 3857). In this particular system, it can be used in terms of objects are taken as well on the respective data structures. Merge sort works on the concept of divide and conquer. It breaks down the list into various smaller sublists in such a manner that at the end when all the elements are broken down into single sub-lists, the result would be sorted.
Conclusion
The importance of searching and sorting algorithms in managing all information related to the health information system has been demonstrated. They also specified the keys, variables, and all ranges that this new system employs. Finally, the binary search algorithm has been demonstrated to be the most essential algorithm employed in this system. To sort all data, randomised quicksort and insertion sort are quite useful. The health-care delivery system is a society's structured response to the population's health issues and demands. Countries differ significantly in terms of their levels of income and economic potential, the diversity of health problems and needs, the way they arrange their responses, and the degree of central management, funding, and control of their health-care system in terms of coordination, planning, and organisation.
References
.png)
MIS609 Data Management and Analytics Case Study Sample
Task Summary
Using the concepts covered in Module 3 and 4, write a 2000 words case study report for a real scenario faced by an organisation of your choice.
Context
This assessment gives you the opportunity to demonstrate your understanding of concepts covered in Module 3 and 4 including Business Intelligence, Big Data, Business Analytics, Data Warehousing, Data Mining, AI, Machine Learning. In doing so, you are required to select an organisation and then analyse and evaluate how the above-mentioned concepts can be used to solve a real-life problem.
Task Instructions
Step 1: Select an organisation that you would like to investigate. When choosing the organisation, make sure that you are able to access data from the organisation easily, or the data is available on the web.
Step 2: Write a case study report outlining how the selected organisation has used the concepts covered in Module 3 and 4 to successfully solve a problem faced by the organisation.
Solution
Section 1
Introduction
Westpac was formed in 1817 and is Australia's oldest bank and corporation. With its current market capitalization, Commonwealth Bank of Australia as well as New Zealand has become one of the world's top banks, including one of the the top ten global publicly traded enterprises (WestPac, 2021). For Assignment Help, Financial services offered by Westpac include retail, business & institutional financing, as well as a high-growth wealth advisory business. In terms of corporate governance and sustainability, Westpac seems to be a worldwide powerhouse. For the past six years, they have been placed top in the Dow Jones Sustainability Index (WestPac, 2021).
Reason for Selection
Considering Westpac Group been around for a long period of time, it was a logical choice. Big customer-related knowledge has been a problem for the organisation in its efforts to use big data analytics to make better business decisions. Since the organisation faced hurdles and gained outcomes, it's best if one learn about how they used big data analytics techniques to overcome those obstacles given their massive database.
Business of Westpac
Westpac Group is a multinational corporation that operates in a number of countries throughout the world. Four customer-focused deals make up the banking group, all of which play a critical role in the company's operations. A wide variety of financial and banking services are offered by Westpac, encompassing wealth management, consumer banking, & institutional banking. Over the course of its global activities, Westpac Group employs about 40,000 people and serves approximately 14 million clients (Li & Wang 2019). Large retail franchise comprising 825 locations and 1,666 ATMs throughout Australia, offering mortgage & credit card and short-long-term deposits.
Section 2
Concepts of Big Data
Unstructured, structured, & semi-organized real-time data are all part of the "big data" idea, which encompasses all types of data. It has to cope with massive, complex data sets which are too large or complex for standard application software to handle. To begin with, it's designed to collect, store, analyse, and then distribute and show data. Professionals and commercial organisations gather useful information from a vast amount of data. Businesses utilise this information to help them make better decisions (Agarwal, 2016). Many major organisations use data to produce real-time improvements in business outcomes and to build a competitive edge in the marketplace among multiple firms. Analyzing data helps to establish frameworks for information management during decision-making. Consequently, company owners will be able to make more informed choices regarding their enterprises.
Business Intelligence
The term "business intelligence" refers to a wide range of technologies that provide quick and simple access to information about an organization's present state based on the available data. BI uses services and tools to translate data into actionable information and help a firm make operational and strategic decisions. Tools for business intelligence access and analyse data sets and show analytical results or breakthroughs in dashboards, charts, reports, graphs, highlights and infographics in order to give users detailed information about the company situation to users (Chandrashekar et al., 2017). The term "business intelligence" refers to a wide range of techniques and concepts that are used to address business-related problems that are beyond the capabilities of human people. An specialist in business intelligence, on the other hand, should be well-versed in the methods, procedures, and technology used to collect and analyse business data. In order to use business intelligence to address problems, those in this position need analytical talents as well (Schoneveld et al., 2021).
Data Warehousing
In the data warehousing idea, there are huge reservoirs of data for combining data from one or many sources into a single location. In a data warehouse, there are specific structures for data storage, processes, and tools that support data quality (Palanivinayagam & Nagarajan, 2020). Deduplication, data extraction, feature extraction, and data integration are only few of the techniques used to assure the integrity of data in the warehouse (Morgan, 2019). Data warehousing has several advantages in terms of technology. An organization's strategic vision and operational efficiency can be improved with the use of these technological advantages.
Data Mining Concept
Patterns may be discovered in enormous databases using the data mining idea. Knowledge of data management, database, and large data is required for data mining. It mostly aids in spotting anomalies in large datasets. It also aids in the understanding of relationships between variables using primary data. Furthermore, data mining aids in the finding of previously unnoticed patterns in large datasets. Data summaries and regression analysis also benefit from this tool (Hussain & Roy, 2016).
Section 3
Data Sources
A wide variety of external data sources were explored to gather the information needed for such an evaluation. The term "secondary data" refers to data gathered by anyone other than the recipient of the information. This material comes from a variety of sources, including the official site of the firm, journal papers, books, and lectures that are available throughout the web. A simpler overview is described below:
.png)
Problems Faced
There were a number of issues faced by Westpac Group when it came to collecting and storing data, managing marketing, goods, and services delivery, embezzlement and risk mitigation, absence of appropriate multiple channel experiences, inability to design adequate usage of information strategy, and sharing of data schemes (Cameron, 2014). There wasn't enough assistance from key players for the sector, particularly in terms of finance and board approval for initiatives. In addition to the foregoing, the following critical concerns were discovered:
- Report production or ad hoc queries were typically delayed since data generated by several programmes would have to be manually cleaned, reconciled, and manually coded. Owing to the duplication of work and data, there were also inefficiencies (Cameron, 2014).
- Inconsistent methods for data integration were employed (e.g., push of data into flat files, hand code,. This is also not future-proof because no concepts or approaches were employed to handle emerging Big Data prospects, such as data services as well as service-oriented architecture (SOA).
- There was an error in data handling and data security categories, which resulted in unwarranted risks and possible consequences.
Implementation of the Solution
The Westpac Group was aware that financial services businesses needed to advertise their services and products as a banking sector. When it came to serving consumers and managing customer data across numerous channels, the corporation realised that it had an obligation toward becoming a true, customer-centric organisation. That which was just stated implies that seamless multichannel experiences are available. It was only with the emergence or introduction of big data, notably in the realm of social media, that the bank was able to discover that channel strategies were not restricted to traditional banking channels alone. Before anything else, Westpac set out to establish an information management strategy that would assist them navigate the path of big data (Cameron, 2014). However, achieving such a feat was not without difficulty (WestPac, 2016).
It was determined that the Westpac bank needed better visibility into its data assets. Data warehouse senior System Manager, Mr. Torrance Mayberry recommended Informatica's solution. Torrance Mayberry, a specialist in the field, worked with the bank to help break down organisational barriers and foster a more open and collaborative environment for new ideas. Customer focus was still far off, but Westpac didn't stop exploring the vast possibilities data held, particularly on social media. There was a further increase in the bank's desire to understand its customers in depth. The bank included sentiment analysis within big data analytics as well.
Quddus (2020) said that IBM Banking DW (BDW) was used by Westpac for data warehousing, and that IBM changed the BDW model hybridized version, that was implemented in an Oracle RDBMS, to include the bank's best practises into its DW. As a result, IBM's BDW came to provide a fully standardised and comprehensive representation of the data requirements of said financial services sector. Informatica was the platform of choice for integrating and accessing data. Informatica Metadata Manager was also included in the implementation of Informatica PowerExchange. Informatica platform variant 8.6.1 was used by Westpac until it was updated to edition 9.1 (Quddus, 2020).
An EDW was used as the principal data warehouse architecture, serving as a central hub from which data was fed into a number of smaller data marts that were dependent on it. Analytical solutions for enabling and maximizing economic gain, marketing, including pricing were part of the supply of these data marts. As an example, financial products' price history was saved and managed in the DW, and then sent to the data mart in order to fulfil the analysis requirements for pricing rationalization. Informatica's platform gathered data from the bank's PRM system, that allowed this same bank to quickly refresh its knowledge of fraud and reduce individual risk. Data-driven decision-making at Westpac developed as a result of increased trust in the information provided by the DW, as well as the creation of new business links.
Section 4
Problems Faced in Implementation
Data warehousing (DW) was the first step in Westpac's road to Big Data. Similarly to other large corporations with data-intensive tasks, the Westpac Group has a large number of unconnected apps that were not meant to share information.
- There was a lack of data strategy. The lack of a single version of Westpac's products and clients because critical data was gathered and stored in silos, and dissimilar information utilisation and definitions were the norm; and the inability to obtain a single version of Westpac's products and clients because critical data was gathered and stored in silos, and dissimilar information utilisation and definitions were the norm (Cameron, 2014).
- Due to the laborious scrubbing, validation, and hand-coding of data from several systems, the response time for ad hoc or reporting production requests was sometimes delayed. In addition, there was a lack of efficiency due to the duplication of data and labour
- To integrate data, many methods were used, including pushing information into flat files and manually coding.
- Soa (service-oriented architecture) as well as data services didn't exist at the time; and there were no methodologies or ideas that might be used to handle new big data opportunities; Information security and data handling were classified wrongly, resulting in potentially harmful complications and hazards.
Benefits Realization to WestPac
According to Quddus (2020), Westpac has reaped the benefits of the big data revolution in a variety of ways. According to Westpac's data warehouse, a large number of its business units (LOBs) are now able to get information as well as reports from it (DW). Westpac said that the bank's core business stakeholders started to realise the strategic importance of the bank's data assets therefore began to embrace Westpac DW acceleration. Financing, retail and commercial banking departments in both New Zealand and Australia as well as an insight team for risk analytics as well as customer service were all part of it. It was possible for Westpac to invest in the development of a comprehensive data strategy to guide business decisions by delivering relevant, accurate, comprehensive, on-time managed information and data through the implementation of this plan. Impacted quantifiable goals and results for securing top-level management help as a result of change. In Westpac's view, the project's goals and outcomes were viewed as data-driven. The chance of obtaining funds and board approval for such ventures grew in respect of profit and productivity.
Conclusion
Big data analytics have just placed the company in a functioning stage thanks to the potential future gains or expansions that may be derived from the examination of enormous amounts of data. The Westpac Group anticipates the big data analysis journey to help the banking industry obtain insights according to what clients are saying, what they are seeking for, or what kinds of issues they are facing. The bank will be able to create, advertise, and sell more effective services, programmes, and products as a result of this.
Recommendations
The following recommendations can be sought for
- These early victories are vital.
DW team at Westpac was able to leverage this accomplishment to involve key stakeholders as well as the (LOBS) or line of businesses, thereby increasing awareness of the problem for the company's data strategy by leveraging this internal success.
- To obtain the support of the company's senior management, provide a set of quantifiable goals.
Westpac correctly recognises that quantifying the aims and outcomes of data-centric projects in order to improve productivity and profit enhances the likelihood that certain projects will be approved by the board and funded.
- Enhance IT and business cooperation.
"Lost in translation" problems can be avoided if IT and business people work together effectively.
References
.png)
MITS5003 Wireless Networks and Communication Case Study Sample
Introduction
In this assessment you are required to explore the given case study and provide a solution, employing the latest wireless communication techniques. The assessment will help in developing an understanding of communication in wireless networks and the limitations and challenges.
Case Study: Penrith City Council Unwires
Penrith City Council’s charter is to equitably provide community services and facilities to the city of Penrith in Sydney’s west. To do this, the council employs some 1000 full-time and contract staff, who carry out a wide range of roles. While about half of them fulfil management and administration roles in the head office complex, the remainder do not work in the office and many also work outside of regular business hours; these include road maintenance staff, building inspectors, general repairers, and parking officers. With multiple department buildings, a mobile workforce, and a geographically diverse community to serve, the council was looking to improve their communications network to enable them to operate more efficiently by streamlining communication, lowering costs, and boosting productivity. Faced with a flourishing community, limited budgets and ever-increasing demands for services and information, Penrith City Council realised its existing IT infrastructure was holding them back. At the time, the three buildings to be connected by wireless were connected via ISDN at a 64K data transmission rate. With rapidly growing information needs, these links were proving unworkable due to network connectivity problems, unreliable response and speed issues hampering productivity. To share information between departments across the offices, staff were burning large files onto CDs and manually transferring the data, because sending information via the network or email was unreliable and slow. The decision to move to a wireless network was a strategic one for the council, as Richard Baczelis their IT Manager explains; “Located among thick bushland and separated by a river, networking our office buildings has always been a challenge. To solve this, I saw the huge potential of wireless technology; not only to help us today but also to position us well for the future.”
The scope of this report is to develop a wireless network solution for building 1 of the three buildings. The building structure is given in figure 1. The building already has broadband connectivity installed and the scope of the solution will be constrained. The building contains several wireless devices (Printer, Laptop, CCTV) that require high-speed Internet connectivity.
The proposed solution must consider the following criteria:
• Any area where the employee wishes to use the laptop should be less than 100 meters (almost 300 feet) away from the access point.
• Interference is generated by the cordless phone, CCTV, and microwave.
• The proposed network should be cost-effective and,
• The network should be secure.
• Other users on the office network
Solution
Introduction
The city council of Penrith, which has a staff of 1,000 contractual and permanent staff members, is the main administrative body in charge of carrying out numerous social functions and offering resources to a local. Here, network disruption is a serious threat to GSM online services because it affects the standard of communication, which creates and lowers revenue. For Assignment Help, The city council of Penrith decided to switch to the Wi-Fi network in terms of improving communication between the operational buildings and assure the network's integrity so that information may be transferred safely instead of manually because a requirement for local services grows. Therefore, the goal of the Penrith City Council will be to similarly distribute resources and facilities to the traditional western Sydney of Penrith city. On the other hand, the impact of the Wi-Fi network in the Penrith city council will be discussed. After that, the network design will be developed to modify the existing Penrith city council hardware and site design. However, a critical analysis of the network design will be illustrated properly in this report.
Impact of the Wireless network in the Penrith City Council
The impact of Wi-Fi network infrastructure will undoubtedly assist Penrith's city council with enhancing staff mobility and productivity, two factors that are crucial for effective social service. With the development of a protected Wi-Fi network, that will guarantee the confidentiality of the information transmitted via electronic mail as well as other methods of obtaining the company's database, the second major requirement—the ability to move information among various business units be resolved. The appropriate network improvement also guarantees the capability of the city commission personnel to perform their jobs, since the Wi-Fi network enables a broad range of users to access the network, ensuring a better method of offering the service to the neighborhood [2]. The goal of Penrith City Council will be to allocate equally the goods and services to the municipal govt. of a western Sydney of Penrith. The authority employs roughly 1000 permanent and contractual workers to carry out different responsibilities to achieve this. Since most highway repair staff, safety inspectors, general repairers, as well as registration officials operators are outside of regular business days, only about 50% of staff can do administrative and managerial tasks in the main office building.
Furthermore, due to a developing city, limited financial capabilities, and increasing need for data and support, Penrith City Council realized that its existing IT infrastructure was holding back commerce. The three buildings that would subsequently be linked and already have been attached by ISDN, which operates at a 64K bandwidth for data transmission. In order to offer complex approaches for disturbances control inside the parameters of a 5G connectivity system, it is necessary to analyze the advantages of UE methods and learn about recent advancements in internet information concepts. The challenges and effects of these challenges connected to the execution of the proposed disruption control plan have been investigated, with a focus on the growth of the 5G technology. The suggested Wi-Fi structure will also guarantee a cost-effective as well as productive way to deliver a secure server in addition to more options for the network's upcoming improvement and expansion.
Network Design
A network design is crucial to comprehend to obtain a general understanding of the needs that had to be put in place in terms of establishing a service provider database that wouldn't only safeguard the business resources but also guarantee work performance throughout the existing network. This approach demands to be significantly modified in this part since the unregistered spectrum involves specific implementation expertise and measurement equipment than wireless connections. In order to demonstrate some modifications that may be made to improve the safety of the municipal council network system, the customization of the current network architecture for the city council of Penrith has been shown [1]. By allowing them to effectively interact with one another, the established network structure will allow the administrative team and all the employees who support the city council in performing the social service. There is a network design that illustrates how well the city council of Penrith's system has now been updated as follows:
.png)
Figure 1: Modified Network Design
(Source: Author)
Furthermore, to illustrate the change that occurred in the city council's existing network, both a secure and a changed network model have been shown in the following design. The network structure of the city council's complete structure has been depicted in the layout, with the required machines including a gateway, switch, and database systems, as well as the deployment of the firewalls to prevent any data theft—being applied in-depth. The considerations when establishing a Wi-Fi technology. Therefore, Wi-Fi networks experience signal loss when passing via solid surfaces. They may have trouble communicating with each other because of disruption from loud routers. Weather conditions may skew wireless communications. Power issues: Consistent electricity is required for routers to operate effectively.
Critical Analysis
This proposed research conducted a variety of cases based on which it deduced the potential efficiency and effectiveness of the proposed methods. The methods have always been used as a method to solve the relative maximization of non-convex feature problems in the two presented frameworks. The design evaluation is an important step in the creation of a coherent and useful network. The proposed architecture, which would improve the existing network of the city council of Penrith, has already been demonstrated in this study. A firewall has now been incorporated into the network structure to improve data protection and safeguard all equipment from issues with theft and phishing [4]. According to this, firewalls were used in the municipal council tower to control how the networks are distributed throughout each level of the structure, enabling all network-connected devices to operate more easily. It describes developing a decentralized network to achieve power regulation while also effectively developing an equitable technique for system resource efficiency with a confined collaboration amongst flying units. For the integration of the following systems, the first study enhanced the currently used models as well as techniques for network congestion.
The report has highlighted how the chosen designs can influence the evolution of 5G networks as well as the actual challenges associated with their implementation. However, looking at the prospective advantages helps readers comprehend the situations in which the recommended approaches might be helpful. Unfortunately, the paper only employs a few extra studies and focuses on knowledge derived through quantitative information; therefore, there is no proof of the survey's relevance or credibility regarding theories put forth by prior academics. There are staff workers who had to physically carry large files across departments throughout the buildings as well as put them onto CDs while sending data via the internet or e-mails were slow as well as inefficient [5]. These two publications discussed identity verification and innovative system proposals that could help cell network wireless carriers reduce network disruption issues in a communication network. They made a substantial contribution to the advancement of approaches, ideas, and frameworks for network congestion. However, the first component doesn't specifically evaluate the recommended and offered data's relevance and validity to that obtained from previous literary and scientific investigations.
On the other hand, the second section runs multiple models to show the feasibility as well as the relevance of the study's goals and to verify and confirm the information that has been offered. In order to maintain network connectivity for all hardware linked to a similar network or to prevent any conflicts with additional machines that are on the equivalent network, routers including Wi-Fi routers have also been installed on any floors of a city council tower [3]. By adding a Wi-Fi router, the existing network is better able to deliver a variety of network services, which will enable the executive team to handle all the requirements and assist individuals or community leaders in organizing the system of facility provision.
Conclusion
An overview of, "Penrith's City Council Unwires" is the administrative body's responsibility of looking after community assets and rendering numerous functions to the city council of Penrith. Approximately 1000 employees have been employed by Penrith City Council to finish the social service project in this case, with 500 of them being responsible for management-related duties. The city council of Penrith recognized that stronger IT architecture was required to create a better and more efficient network for staff to increase effectiveness as the requirement for community services increased. As a result, Penrith City Council upgraded its network as well as decided to migrate to a Wi-Fi connection to strengthen network connectivity between operational structures and to ensure data protection so that data has been transmitted securely rather than through a manual procedure. This paper has covered the value of Wi-Fi connectivity in securing growth and satisfying city council standards. The categorization of different hardware required for the development, along with a site design to alter the current network architecture used by Penrith's city council, have now been demonstrated in this assessment.
Reference
.png)
BDA60 Big Data and Analytics Sample
Case Study
Big Retail is an online retail shop in Adelaide, Australia. Its website, at which its users can explore different products and promotions and place orders, has more than 100,000 visitors per month. During checkout, each customer has three options: 1) to login to an existing account; 2) to create a new account if they have not already registered; or 3) to checkout as a guest. Customers’ account information is maintained by both the sales and marketing departments in their separate databases. The sales department maintains records of the transactions in their database. The information technology (IT) department maintains the website.
Every month, the marketing team releases a catalogue and promotions, which are made available on the website and emailed to the registered customers. The website is static; that is, all the customers see the same content, irrespective of their location, login status or purchase history.
Recently, Big Retail has experienced a significant slump in sales, despite its having a cost advantage over its competitors. A significant reduction in the number of visitors to the website and the conversion rate (i.e., the percentage of visitors who ultimately buy something) has also been observed. To regain its market share and increase its sales, the management team at Big Retail has decided to adopt a data-driven strategy. Specifically, the management team wants to use big data analytics to enable a customised customer experience through targeted campaigns, a recommender system and product association.
The first step in moving towards the data-driven approach is to establish a data pipeline. The essential purpose of the data pipeline is to ingest data from various sources, integrate the data and store the data in a ‘data lake’ that can be readily accessed by both the management team and the data scientists.
Task Instructions
Critically analyse the above case study and write a 1,500-word report. In your report, ensure that you:
• Identify the potential data sources that align with the objectives of the organisation’s data-driven strategy. You should consider both the internal and external data sources. For each data source identified, describe its characteristics. Make reasonable assumptions about the fields and format of the data for each of the sources;
• Identify the challenges that will arise in integrating the data from different sources and that must be resolved before the data are stored in the ‘data lake.’ Articulate the steps necessary to address these issues;
• Describe the ‘data lake’ that you designed to store the integrated data and make the data available for efficient retrieval by both the management team and data scientists. The system should be designed using a commercial and/or an open-source database, tools and frameworks. Demonstrate how the ‘data lake’ meets the big data storage and retrieval requirements.
• Provide a schematic of the overall data pipeline. The schematic should clearly depict the data sources, data integration steps, the components of the ‘data lake’ and the interactions among all the entities.
Solution
1 INTRODUCTION
Big Data and Analytics have become one the most important technology for the online marketplace. The online market is fully dependent upon the review and feedback of the customer who frequently visits the website. To gain more customers, the organization needs to analyze the overall data regarding the review, sales, profit, user rating etc. to the customers to attract them (Ahmed & Kapadia, 2017). For Assignment Help, Thus, data storing and analysing are important tasks in business intelligence. To conduct these tasks, the organization need to organize the data pipelining for the data effective data management by employing suitable design. In this paper, then big data and the underlying aspects will be discussed for Big Retail using the Data Lake Design and Pipelining (Lytvyn, Vysotska, Veres, Brodyak, & Oryshchyn, 2017).
2 CASE STUDY OVERVIEW
2.1 OVERVIEW OF ORGANIZATION
Big Retain is one of the online retails shops in Adelaide, Australia. It has a large number of products which can be explored by the customer by visiting the website. The organization has detected that they have in an average of 100000 visitors per month who visit and explore the products there. On that website, customers can find various products and they can purchase those by paying the amount. The organization uses to publish the updated catalogue of the products and mail that to the registered users and keep that available on the website. So, the customer can visit the website and can view the available products. They also make the price of the products reasonable compared to the competitors in the market to attract more customers. Their website is maintained by the Information Technology department of the organization.
2.2 PRESENT CONDITION AND PROBLEM
Big Retails has a good number of products that it uses to sell to customers at a reasonable price. However, in recent days, they have faced a big challenge for the significant reduction in the number of customers. They primarily suspect the non-maintenance or non-adoption of the data-driven strategy by which they should have visualized the purchase, sales and marketing scenario of the organization (Lv, Iqbal, & Chang, 2018). To overcome the problem, they have decided to adopt the data-driven strategy for the betterment of the future business. So, they are now interested in the application of Bid Data Analytics so that they can obtain a customised customer experience and the recommender system for attractive more customers towards their business.
3 BIG DATA AND ANALYTICS
3.1 POTENTIAL DATA SOURCES
Big Retails had maintained their data in the server without which the data cannot be managed. As the number of customers was about 100000 per month, the transaction is expected to be huge in terms of website hit, website visit and product purchase. Those customers who purchase the products used to provide the review and rating on their website. So, apart from the business data like sales, profit, marketing etc. they need to maintain those reviews, ratings etc. data as well (Husamaldin & Saeed, 2019). Additionally, those data are also helpful in getting insight into the views and demands of customers regarding the products. So, the data like reviews, ratings etc. in addition to the data like sales, profit, marketing etc. will be required to be maintained and managed in the Bog Data Environment, As the big data environment can be managed for the particularization of the data sources, thus, the organization need to identify the data source (Batvia, 2017). Hence, the data sources for Big
Retail are as follows:
1. Data through Transaction: Big Retails can get the data from the transaction of the customers. It can be achievable concerning the purchase scenario and the website visit by the customers. When the customers will visit the website, and purchase some products, the data should be stored in the Big Data (Subudhi, Rout, & Ghosh, 2019).
2. Data for Customer Demand: When the customer will purchase some product, that product may satisfy or dissatisfy the customers. According to the satisfaction level, customers use to provide their product review and rating for the same products. This kind of data is essential for data analytics and to show the present demand of the products of the customer (Liang, Guo, & Shen, 2018).
3. Data through Machine: Apart from the two sources of data that are mentioned earlier. Another type of data comes from the system of the organizations. This kind of data may contain the historical records of the sales, profits or loss, marketing, campaigns etc.
3.2 CHALLENGES IN DATA INTEGRATION
Data Integration is a sensitive issue in Big Data Analytics. As Big Retail has a large volume of data and they wish to adopt big data analytics, they should be focused on the mitigation policies of the challenges that can be faced by then in the maintenance of the big data (Anandakumar, Arulmurugan, & Onn, 2019). Hence, there is a number of challenges that can be faced by Big Retail. The possible challenges of the Big Data Analytics that may be faced by Big Retails are as follows:
1. Data Quality: When Big Retail will adopt big data analytics for their business, the data should, be collected and stored in real-time by fetching those from the website. To control and maintain the huge volume of data, the quality of data places a significant impact. One of the greatest issues that can be generated during the maintenance of the data quality is the missing data (Anandakumar, Arulmurugan, & Onn, 2019). If the data contains missing values, the data will not be suitable for analytical work and so, the organization cannot operate of data. To get suitable data, the data sources and the data quality both need to be maintained.
2. Wrong Integration Process: The data integration process can connect the big data with the software ecosystem. A trigger-based data integration process allows the integration of the data with several applications that are aligned together. However, this process does not allow the integration of historical data which can be resolved by applying the Two-Way Integration System (Lytvyn, Vysotska, Veres, Brodyak, & Oryshchyn, 2017).
3. Data Overflow: Data should be collected by Big Retails based on the importance. If too much data will be collected regarding features, data can be overflown which is not expected for big data analytics.
3.3 DATA LAKE
A Data Lake can be defined by the repository of data that can accommodate a large amount of data of different formats such as structured data, semi-structured data and unstructured data. The greatest advantage of the application of data lake is that it allows the storage of the data without any limit. In this context, the data storage capacity is made flexible. It also facilitates the organization to store the data with high quality and with data integration (Liang, Guo, & Shen, 2018). These facilities increase the performance of data analytics on the big data which should be the expected scenario of Big Retail when they will adopt Big Data Analytics. Another advantage of the data lake is that it allows the storage of the data in real-time and while storing the data, the process is automated.
The data lake that can be proposed for Big Retail for making the business process smooth and faster is as follows:
.png)
Fig-1: Data Lake Design for Big Retail
3.4 DATA PIPELINE
The design of the data lake has been shown in the last section. The data pipelining can be addressed and demonstrated by emphasizing the data lake model for Big Retail. The process of data pipelining will follow the sequential operation of the data lake architecture (Ahmed & Kapadia, 2017). The data pipelining is discussed below:
1. Data Sources: Big Retail can gather the data by selecting the data source such as its website. Ads the data will be collected from the website, so the data may be the combined format of structured, unstructured or semi-structured.
2. Ingestion Tier: The data can be loaded in the data lake architecture in real-time or through batches as per the requirement (Lv, Iqbal, & Chang, 2018).
3. Unified Operations Tier: The data and the entire data management process will be controlled in this tier. it may also include the subordinate system that can manage the data, the workflow of the data collection and integration etc.
4. Processing Tier: After the data has been processed to the system of Big Retail, the analytics will be applied in this tier. This will facilitate the analysis process of the collected data so that the data insight can be generated (Batvia, 2017).
5. Distillation Tier: In the processing layer, the data of Big Retail will be analyzed using the employed algorithms. However, the processing time for the analytics is faster in the case of structured data. This tier is employed in the data lake to convert the collected unstructured and semi-structured data into structured one for faster analytics (Anandakumar, Arulmurugan, & Onn, 2019).
6. Insights Tier: The architecture of the data lake will employ the database queries on the data for the purpose of data analysis. It will help to compute the customer-based scenario such as sales per period, type of products with higher and lower sales etc.
7. Action: Finally, the architecture will produce visual insight into the data. In most cases, the visual insight may contain the analysis such as Review word cloud, Rating analysis, purchase statistics etc.
4 CONCLUSION
In this paper, big data analytics has been discussed for Big Retail through the implication of data lake and data pipelining. These measures have been seen to be effective in data management and analytics. As the number of customers is consistently decreasing for Big Retail, this architecture will help them grow their future business.
5 REFERENCES
ITC561 Business Requirements Report Sample
TASK
Read the Regional Gardens case study in the Resources section of Interact 2 before attempting this assignment help.
You are an ICT Cloud consultant and you have been approached by Regional Gardens (RG) to advise them on how to improve their data centre and move into the Cloud. The Managing Director (MD) is still unsure that this is the best approach for his company as he feels that his company is "not really big enough to be thinking about moving to the Cloud" and that any money should be spent on their garden design and product development rather than ICT. But both the Design manager and the Sales Manager are both concerned that if the company's data centre isn't improved then the company will not be able to expand.
The company has recently upgraded their display garden and also added a series of new product lines to their nursery store as a result. The Sales Manager is concerned that the current order system will be inadequate to handle the expected large increase in orders that is likely to come from these upgrades. The online sales system is currently running on the RG web services infrastructure, which has not been updated for a considerable amount of time. RG uses their own custom-designed garden design platform that runs on SharePoint 2013.
This allows them to enable a number of designers to work on individual customer designs or to collaborate on larger designs. This platform allows them to access the design software from the office, but also allows the possibility of remote access. The Design Manager would really like to enable the remote working capability, but has concerns that the SharePoint infrastructure is also quite dated and may not support an increase in the level of demand or for remote work.
The company is quite reluctant to put more capital into ICT infrastructure as the MD, correctly, reasons that this capital will be needed to support sales, design and distribution. The MD has read that the company can set up ICT infrastructure on Amazon Web Services (AWS) for no capital cost and reasonable monthly payments for the use of their infrastructure. The Regional Gardens MD is not entirely convinced that this is a valid approach as the company has always purchased and owned its own infrastrastructure so that it is not reliant on other organisations. But in the current circumstances, a Cloud approach now has to be investigated.
Regional Gardens Case Study
Regional Gardens Ltd is a company that runs a number of related gardening enterprises. It has a large display garden that it opens for public inspection a number of times a year. These enterprises include the Regional Gardens Nursery which sells plants and garden supplies to the public, and Regional Garden Planners which provides garden advice, design and consultancy services.
Regional Gardens Ltd has a small data centre at its main site in Bathurst where the company’s servers and data storage is located. The company has the following server infrastructure:
• 2 x Active Directory domain controllers on Windows Server 2012 R2;
• 2 x SQL Server 2008 R2 database servers on Windows Server 2012;
• 1 x Exchange 2010 email server on Windows Server 2012 R2;
• 4 x Windows Server 2012 File and Print servers;
• 2 x Windows SharePoint 2013 servers on Windows server 2012 R2;
• 2 x Red Hat Enterprise 5 Linux servers running Apache and TomCat (2 x Xeon 2.8GHZ, 16GB RAM, 140GB HDD).
• 1 x Cisco ASA 5512-X firewall running v9.6 ASA software.
This infrastructure has not been updated for some time and the Regional Gardens Board is concerned that a full upgrade may now cost them more than it is worth. The Board is now considering moving some, or all, of their current infrastructure into the Cloud. The Board sees this as a strategic move to future-proof the company.
Regional Gardens has engaged you as a consultant to advise them on the use of Cloud Computing in their daily operations. They have some 70 garden design, horticultural and support staff that work on different projects for clients in New South Wales. They have been advised that a move to using a Cloud based infrastructure would be an advantage to them.
Solution
Cloud discussion:
Advantages of Web Services:
Interoperability: Web service mainly works outside of any private networks and provides some important non-proprietary route to mitigate all issues of servers. Developers have enough priority to set up their programming language to communicate with authentic users. It can also determine as an independent platform.
Usability: Web service provides some business logic to expose through the web page. Web service helps the user to choose their application as per their preference. This type of approach can enhance the overall service and produces some useful code with different languages (Li et al., 2020).
Deployability: Web service is mainly used through standard Internet technologies. Web service is used in different firewalls to the servers for completing the internet connection. Community standard also depends on the webserver.
A regional garden can become more helpful by the deployment of the web server in the cloud security storage. It can also create a user-friendly atmosphere.
The disadvantage of web service:
Storage capacity: Web service protocol mainly followed plain text format. Therefore, this format occupied a large space than binary methods. Large spaces with low internet connections are strictly affected by the regional garden's organization resources. It is one of the significant drawbacks of the webserver (Ullah et al., 2020).
HTTP server: Comparing the core web protocols and web services, HTTP is mainly grown-up for the long-term session. Browser mainly uses this HTTP connection for providing some web pages and images. On the other hand, the webserver can establish the connection for a long-term period and sent the data periodic manner. Web service process has become quite difficult for the clients of Regional Garden Ltd company.
The server provides some unique identification to the client for accessing the server. This kind of unique identification process provides the further request to the server. The server mainly depends on the timeout mechanism. If the server did not get any response from the customer side, they usually remove the data. It can become an extra load for the Web service. Cloud infrastructure of the regional garden will be getting a random threat from the service provider to store ant information for future use.
Advantages of share point:
Advantages for Business growth:
SharePoint architecture helps the user to gather any important information about the portal and it can easily be accessible by the authentic user of such an organization. The regional garden must implement this activity to install data from various sources Like EXCEL. Microsoft SQL. This can enhance the business process of Regional Garden Pvt. Ltd.
Cloud-based framework: Share point can access the progress of any project at any time with the help of a web browser. Authentic users of the company can use their data and resource as per the company's requirements.
Security in cloud solution: The security of the company is mainly determined by the business data of any renowned organization. SharePoint helps the user to arrange any data with the help of the firewall security process. Unauthorized members or outsiders of the organization can hardly access the information. Cloud solution helps to improve the confidentiality of any documents.
Disadvantages of SharePoint:
Integration requires developmental effort: Sharepoint integration issue is recognized as a very important aspect. All user mainly invest their time and cost to creates any project. If the project has become fail, then it is determined as a wastage of time and money.
Poor capability: SharePoint is a traditional approach. User can not get their information in a few seconds. It will take some time to display the information on the screen.
Though Share pointer has some good qualities, the traditional approach and the low developmental process can restrict the growth of the Regional garden.
.png)
Source: (Mahloo et al., 2017)
Web service infrastructure:
Deploying RG web service into AWS cloud:
Amazon web service is determined as a comprehensive platform that consists of three different types of services like IaaS, Platform as a service, and Packaged software as a service model. Cloud deployment has been created with four different architectures like public cloud, private cloud, hybrid cloud, community cloud. Few processes will be introduced in this section to deploy the AWS cloud service.
1. RG private limited company use this service to make available the service and resources
2. AWS mainly helps to manage customers' data for different authenticated users. Consumers are managing all application stacks and also make logging information authorized(Abbasi et al., 2019).
3. After that patching the information and gives a backup plan to use the data as per the organization's requirement.
4. The provider gives the Host and VM installation process.
5. The server provides network service and storage capacity.
6. In a PaaS environment, the virtual server is installed to make a readymade environment (Zhang et al., 2019).
RG web service deployed in the public subnet and AWS service used to protect RG web service:
RG web service has taken a few steps or methods to install the AWS service model architecture. These processes are like production VPC, UAT vpc, and DEV vpc.
1. In the production subnet method private and public subnets are used to rout in a particular table. The proxy server will be available here for 24*7 hours. It can share the database and log storage by the VPG method.
2. In UAT internet access, a public subnet will be deployed with the help of a router and proxy server. VPG method is used here to share the database snapshot and log storage services.
3. Router table, virtual private gateway helps to deploy the web server into public subnet model. It can also access the data or services.
Public access to the web service:
1. When the webserver is allowing for the users, intruders are always ready to create a log file for stealing all personal information of the Real Garden PVT. Ltd. Company. Therefore a DNS server should be installed here to pollute the cache of the server. It can give some questions to the transmission control protocol. This can also help to build up protection against the cache protocol system.
2. To restrict the malicious user it is very important to disable the recursion of the DNS server. The service provider should give the information to ISP for restricting the similar attack of DNS server.
These are the required method to make the web server for public access in RG Pvt. Ltd.
Remote access for the authorized web users: The main problem of secure remote access is internal webserver from the outsides of the firewall security system. In the meantime, unauthorized users have enough opportunities to get access the sensitive information. The main goal of the Real Garden infrastructure cloud is to implement a one-time password solution for accessing all documents of RG. Pvt Ltd. A secure socket layer is also used here. These components are needed to be implemented here in such a way as to improve the security, performance, and availability scale.
2.Another process is the main component of the system has two subcomponents. Proxy has one subcomponent behind the firewall. Another component is present behind the firewall.
.png)
3.Push web machine is used inside the machine, another machine absent is used outside. When a web request comes from DWT, absent uses control connection statement to initiate actual communication with authorized users. Push web server only helps to establish a connection.
.png)
Source: (Pacevic & Kaceniauskas, 2017)
Share point design Platform:
Process of SharePoint infrastructure in AWS cloud:
Share point infrastructure can increase the security and high availability of the system in AWS cloud storage. Few steps should be followed here with the help of AWS cloud Formation template, multiple servers, and single server topologies. This deployment option included some specific categories like a single server and multiple server share points to form a virtual private cloud (Hodson et al., 2017).
1. Public subnet and private subnet mask are used here to make a static internet activity. In virtual private cloud storage, the Public subnet has two categories like NAT gateway and RD gateway.
2. Private subnet consists of 4 different categories like Frontend server, app server, database server, and directory server.
3. Network address translation gateway used here to allow outbound internet access for the required private subnets.
Private subnet: Application load balancer is used within the AWS server. Amazon EC2 instance is also added to the front-end device. Two amazon EC2 instances serve as Microsoft SQL servers needed to be deployed in the Amazon web server application (Yu et al., 2020).
4. A remote desktop gateway in the auto-scaling group allows the remote desktop protocol to Amazon elastic compute system. It can make the connection between private and public subnets.
These methods are required here to install SharePoint infrastructure in the AWS cloud(Varghese & Buyya, 2018).
SharePoint uses private subnet and AWS to protect RG web service:
According to the AWS configuration, VPC configuration has been used to place internet and non-internet servers in particular positions. This can also help to restrict direct access from the other instances of the internet.
1. Hybrid architecture is one of the useful methods to extend private policy and it can also enhance the Active directory infrastructure.
2. Private subnet made up with the help of application load balancer.
3. A network load balancer is used here for the SharePoint application server.
4. Two Amazon electric compute systems serve Microsoft SharePoint as an application server (Waguia & Menshchikov, 2021).
5. Amazon EC2 is also used here as a Windows failover file share witness.
6. At last SQL server is also used in RG infrastructure Pvt. Ltd to create a high available cluster.
7. These are the main components mainly used to set up the RG Pvt. Ltd company by implementing Amazon web server cloud architectural system.
Protection to RG web service: AWS server continuously helps to protect the data, information, and threats by improving the encryption, key management, and threat detection system. These concepts will be discussed in this section:
Threat identification and monitoring: AWS server is constantly monitoring threats in any system or network activity. As a result, it can detect any suspicious behavior within the cloud environment.
Identity access management: AWS identity constantly helps to make a secure management identity, resources, and permission within a particular scale. AWS has its identity service in the workforce and customer-facing applications. AWS constantly trying to manage its application (Mete & Yomralioglu, 2021).
Compliance status: AWS service constantly checking the comprehensive view of any compliance status. Not only that but also Monitoring the whole environment with the help of an automatic compliance checkup process.
In this way RG Pvt. Ltd can store the data in a safe, secure area. Implementing the above items or rules RG web service infrastructure will be protected.
Remote access share point for authorized users:
Share point is one of the significant document management platforms which is strictly used in different organizations, It can also produce near about 1 billion in revenue. SharePoint also helps to allow the organization and makes information confidential behind of corporate firewall system.
1.SharePoint intranet is mainly added with the users. The external use of this site can also have enough priority to get the internal information of Real Garden Pvt Ltd.
2. Self-hosted share point is one of the keys used to access internal information without using any virtual private network system.
3. It is also very important to create an application with the help of an application proxy. External and internal URLs will be used here to access the share point. There are few steps added here like internal URL, pre-authenticate URL, translation of the URL.
These are the required process needs to be implemented in RG Pvt Ltd for maintaining the remote access to the shared pointer.
5. After the process, the Sign-On mode and Internal application SPN model are used here to make a delegate login identity. User's domain has been checked continuously and select on-premises user names().
.png)
(Source: Kisimov et al., 2020)
Desktop architecture:
Approach to improve the desktop experience for staff:
Virtual desktop is defined as an innovative approach for any company to access the application from anywhere of the company. The desktop cloud can enhance the work from home opportunity. Covid-19 pandemic is gradually increasing the requirement of the virtual desktop category. In this report, few methods will be discussed to improve the desktop experience in the future (Chaignon et al., 2018).
Secure working environment: A hosted desktop solution offers Windows 10 and Windows Server from the different internet-based connected locations. It can make the data or information of the employee more secure. The virtual desktop experience is more comfortable than the office desktop experience.
Reduced cost in virtual desktop: Cloud virtual desktop has their expenditure for actual business. On the other hand, a physical desktop needs a huge amount of hardware, licensing, and management systems.
Consistent productivity: A hosted desktop solution remove the quality of the physical server on an individual site. This virtual desktop platform can also decrease the downtime system. An advance plan is also getting prepared in favor of employees’ satisfaction in RG Pvt. Ltd. Low downtime operation provides efficient operation and generates huge economic revenue (Sen & Skrobot, 2021).
Simplified IT infrastructure: Virtual desktop environments can create simple architecture to connect their 70 stores in one platform. An automation process can increase the quality of any users and running the program insecure manner. A simple and efficient process helps to make the IT team less worried than the previous project. It can also increase productivity within the organization.
Therefore as a researcher, it has been coming out that virtual desktop solution is more efficient for the staff of RG Pvt Ltd.
Amazon workspace vs. Goggle G suits for existing desktop:
Advantages and disadvantages of Amazon workspace and Google G Suite:
Advantages:
a)Amazon workspace is recognized as a virtual private network. Users can also get the advantages of encrypted storage volume from the AWS cloud service. It can also integrate the AWS key management service. Amazon workspace providers can improve the user data and risk service area.
b). Amazon workspace is also very helpful to save the time of operation which multiple computers needed. Amazon workspace is also defined as a cost-effective structure and provides various CPU, memory, and storage configuration.
c). Amazon workspace provides quality cloud infrastructure and manages the global deployment model.
Google G suits advantages:
a). It is very hard for the business owner of the RG Pvt Ltd company to visit multiple places for managing the tools. G Suite admin console helps to solve the issues by managing all devices, security change, and custom domain performance.
b) Google G suit helps to make the data protection capabilities which can preserve the sensitive information stored. Users can access the data as per the requirement.
c). Google G space has enough storage capacity which is restricted by the authenticated user within any organization. The administration head of the organization can send important mail to those people who are bounded within any particular organization.
d) G suit has enough tools like Google hangout chat, Google hangout meet, Google form and google slide. If any employee within the organization can not able to manage the data, the admin can remotely access the data. Then he can make changes to some additional issues.
Disadvantages:
1. When a remote official meeting has happened, G suit had never maintained the picture resolution within the screen. Therefore it can create a barrier within the organization.
2. A single workspace is too difficult for the users’ to manage. As a result, multiple google spaces are required for improving the user access movement.
The disadvantage of Amazon workspace:
a). Though the amazon marketplace is great, it is hard to make a subscription and activate the instance.
b). Tools of the amazon workspace are quite higher than any other software.
c). Experienced users can only identify the correct configuration of the Amazon workspace. Therefore it is very important to use user-friendly software for making the function easier (Damianou et al., 2019).
Analyzing the above advantages and disadvantages of the Google G suite, amazon workspace, the G suit is quite acceptable for employees within the Real garden Pvt. Ltd. Multiple tools are used here to secure the data privacy system. Apart from this thing, remote access to the desktop can be easily done by this software.
Online Blog architecture:
Developing cloud edge solution:
IoT system is one of the useful platforms to connect global users in the market with the help of cloud service. According to the analytics, the business organization has depended on three different resources like Data analytics and cloud computing model (Solozabal, et al., 2018).
The edge computing model is being created with the help of advanced technology and LAN or WAN connection. IoT gateway devices are giving adequate support to improve the cloud computing operation within the system (Dreibholz et al., 2019).
When the edge device is combined with cloud computing technology strength of the local storage and processing capacity will be increased in a rapid manner. Edge computing architecture consists of different materials s which have been discussed in this section. The first thing is distributed computing system, the application process, Different device nodes, Rapid increment of data volume, and increasing traffic. Network connectivity has played a vital role by completing the sliced network and bandwidth management system. These are the required components needs to implement in Regional Garden company to provide better service in favor of customers’ requirement.
Advantages and disadvantages to the regional garden:
Advantages:
Cost reduction: Cloud edge solutions bring the opportunity to reduce the cost structure of any organization or firm. Cloud computing services can only charge the amount at the time of installing the software. RG company should only pay at the server time or space in that use(Cao et al., 2017).
Security: Cloud edge solutions is also become helpful to secure customer information. When a customer placed an order, authenticate user can only access those data or information. Cloud providers are always trying to make software updated. Therefore hackers can not able to access the bank account number or purchasing detail of the consumer (Zhang et al., 2018).
Disadvantages:
Downtime: Cloud edge solutions don’t have any cache memory to store the data when there is any power cut. Sometimes mobiles do have not enough power to complete the order in a cloud secure system. Then RG PVT. Ltd should give additional steps to fix such a problem.
Connection scheduling: Scheduling tasks has become challenging for different nodes. Scheduling tasks should be progressed to execute data processing and maintaining the information in a gentle way.
These benefits and limitations had become faced by the regional garden Pvt. Ltd.
Reference:
.png)
.png)
MIS500 Foundations of Information Systems Case Study Sample
Task Summary
In groups of 3-5, you are to act as consultants hired by the company the case study is based on, to research, investigate and propose an information system for your client.
Part A: In response to the case study provided, your group will produce a report explaining the information system plan you develop for your client. The report should be no more than 3000 words.
Part A Group report
1. Fibre Fashion – Case Study
To complete this assessment task you are required to design an information system for Fibre Fashion to assist with their business. You have discussed Porter’s Value Chain in class and you should understand the primary and support activities within businesses. For this assessment you need to concentrate on Marketing and Sales only.
2. Watch the case study video about Fibre Fashion (link below). This video will allow you to understand the business and where you, as consultants, can add value by improving their information systems in marketing and sales.
4. For further details about current information systems of Fibre Fashion, please see the Assessment 2 Database document and the Fibre Sales Figures Contacts spreadsheet in the Assessment 2 area of Blackboard.
5. Based on the information provided as well as your own research (reading!) into information systems for SMEs (small to medium enterprise), write a report for Fibre Fashion to assist them in using Business Intelligence (BI) to develop insights for their marketing and sales.
Solution
Introduction: Student 1
The main aim of the report is to propose the Advanced Business Intelligence Information System to assist the business of the Fibre Fashion Company. For Assignment Help, The report discussed the issues regarding the business information recording system of the Fibre Fashion Company. The first section of the report identified the main issue regarding the recording system of marketing and sales data of the company. It also identified the research questions for further research regarding the advanced marketing and sales data analysis system for the Fibre Fashion Company. The second section of the report reviewed the different journals and articles regarding the importance of the marketing and sales data analysis for Small and Medium Enterprises and available updated the Business Intelligence system for meeting the need of marketing and sales data analysis of the SMEs. The Final Section proposed a recommendation about the business intelligence information system that will assist the business record and marketing and sales data analysis system of the Fibre Fashion Company.
Background of the issue: Student 1
Fibre Fashion Company has been an effective and consistent presence in the wholesale fashion industry of Melbourne for over 20 years. The fledgling business of the Fibre Fashion Company has evolved with colour, flourish, embellishments and accents of the pure boutique. The main issue of the Fibre Fashion Company is their inefficient Excel Spreadsheet recording System of the company for recording details of the client and business sales per brand of the boutique. Moreover, the order placing system and invoice creation system of the company also is inefficient. The company uses a simple database system for placing the order and creating an invoice for the order that only contains the style number, category of the product, the colour of the product, and total cost of the product. The company also does not enter the other details of the product in the record like delivery date, pattern, job number, manufacturer details, etc. The Company also uses a simple database to keep the record regarding the simple information of customers including the contact details, customer code, customer address, mail details, credit and discount details and product purchase price details. The Company uses a simple Excel spreadsheet for keeping the details of the clients of the company. It contains the name of the retailer details and location details of the retailer. It contains the details of all open and closed retailer details in the excel spreadsheet. It removes the close retailer name by striking on the name of the retailer. It contains the details regarding “new client details”, “viewed but didn’t place order”, “Placed, then cancelled”, “Sale or return”, “viewed look book”, “Sent pack”, “Appt”, “cancelled appt”, “not interested to view”, “Order to come” etc. details regarding the client appointment and the order details of the product in a numerical format. It is very inefficient in nature for handling bulk data of marketing and sales information of the Fibre Fashion Company.
The report aims to review the needs of marketing and sales data analysis for SMEs and the range of updated Business Intelligent Systems for handling these needs. The report also aims to propose a better BI Information System for Fibre Fashion Business to assist their marketing and sales data.
Following are the objectives:
- To investigate the needs of the marketing and data analysis for SMEs.
- To identify the range of BI systems for meeting marketing and data analysis for SMEs.
- To propose a better BI information system for Fibre Fashion Company to handle their client and sales data.
Research Questions: Student 1
What are the needs of marketing and sales data analysis for SMEs and the range of updated Business Intelligent Systems for handling these needs?
Analysis and Review: Student 2 and Student 3
Identification of the issue:
According to the case study, The Fibre Fashion Company maintains a simple excel spreadsheet and database for handling and keeping records regarding the client details and sales details per brand of the company. Storing and keeping the data in the excel spreadsheet is not easy for data visualisation and it increases the chances of the error. Moreover, there is no particular indication regarding “who are the clients”, “what they order” and “when” etc. It is quite painful for reporting regarding the details of the client and sales per brand for the company. It can increase the chances of fraud and corruption and also it is difficult to troubleshoot and test. It is sometimes not possible to interrelate the spreadsheet data across the workstations on different locations. Lack of security and control issue is the major problem. It is not user-friendly and the excel round-off the large numbers using imprecise calculation. It reduces the accuracy of the data. Excel spreadsheet is not efficient for managing the advanced pricing rules. Moreover, the simple database system is not sufficient for handling the advanced pricing strategies like quantity based pricing, psychological pricing, handling pricing based on the market and different geographic locations, and attribute-based pricing etc. It is unfit for agile business practices. Maintaining and keeping the record in the excel spreadsheet is quite painful for extracting the marketing and sales data from different departments and retailers, consolidating those data and summarising the entire information is also painful for the management of the company. It is incapable of supporting the company to make a quick decision and because keeping the record and extracting the data from the spreadsheet is a time-consuming process. It is also totally unsuitable for the continuation of the business. It is required to use the updated BI information system to develop the new insights for the company’s marketing and sales data.
Importance and needs of the marketing and Sales data analysis for SMEs: Student 2
In the view of Jena & Panda (2017), sales and marketing data analysis is essential for unlocking the relevant commercial business insights. It helps to increase the profitability and revenue of SMEs. It also improves brand perception. It helps in uncovering new audience and customer niches, new markets and areas for future market development It helps SMEs to reach different segments of the market via the different channels that are working and not working. It helps SMEs to take all the necessary information regarding the market for building an effective marketing plan. It focuses on the internal and external environmental factors. It considers the weaknesses and strengths of the SMEs by gathering the data of all marketing channels of the SMEs. Marketing data analysis helps SMEs to analyse the current market and helps them to understand the market more efficiently (Chiang, Liang & Zhang, 2018). Sales data analysis helps SMEs to understand the behaviour of customers, the products that maximum customer select and the reason behind selecting the product and behaviour of the product.
Mikalef, Pappas, Krogstie & Giannakos (2018) stated that marketing and sales data analytics helps in predicting the behaviour of consumers, improves the SMEs decision-making process and determine the best path for increasing the return of investment based on the marketing efforts of the SMEs. It helps them to protect their market share. The study stated that big data technology to analyse the marketing and sales data of the business is important for increasing the business efficiency, reduces the operational cost, marketing and sales cost of the company. It helps in identifying the failures and weaknesses of the SMEs. It helps in conducting a review of customers and design the new services and products for SMEs for increasing the marketing and sales of their product. It helps in identifying the fraud while keeping the record of clients’ data and sales records of SMEs. It prevents fraudulent activities and helps SMEs to make smarter decisions for enhancing their business. It helps the owners of small businesses to meet their business goals. It helps the sourcing the marketing sales information for analysis the marketing and sales data from different sources such as sales receipts, email marketing reports, publicly available data, website data and social media data.
Based on the research by Grover, Chiang, Liang & Zhang (2018), the use of marketing and sales data analysis increases the chance of return on investments while taking any marketing initiatives in SMEs. It helps SMEs to make proper decisions for providing proper service to their customers to retain them (Becker & Gould, 2019). A real-time data analysis facility helps SMEs to provide critical meaningful insights to the decision-makers in real-time to make a proper decision regarding further steps. Data analysis system helps SMEs to grow their business by allowing them to develop an update and fine-tune marketing strategies and search engine strategies (SMEs who have their online websites) (Cortez & Johnston, 2017). It helps SMEs to determine the right mix (product, price, place and promotion strategy) strategy for optimising the sales of the product. It helps to store the sales data in one place to improve the performance of sales. It determines the areas that need modification by determining the facts and relevant data regarding the marketing and sales.
BI System for meeting marketing and data analysis needs of SMEs: Student 3
In the view of Anshari, Almunawar, Lim & Al-Mudimigh (2019), Business Intelligence is the advanced technology that enables the business processes to analyse, organise and contextualise the business data from the company. BI also includes multiple techniques and data to transform the raw data into actionable and meaningful information. The BI system has mainly four parts that include 1) The data warehouse stores that help in gathering a variety of sources in an accessible and centralised location. 2) Data management tools and Business Analytics Tools analyse and mine the data in the data warehouse system. 3) Business Performance Management Tools for analysing and monitoring the data. It helps SMEs to progress their business towards the goals of the business. 4) User Interface tools and interactive dashboards with the facility of data visualisation reporting tools that helps in quick access of the business information. Business Intelligence tools offer a wide variety of techniques and tools for supporting accurate and reliable decision making for progressing the business performance. BI based and data-driven process of decision making helps SMEs to stay competitive and relevant.
As an example, Lotte.com the leading and renowned shopping mall in Korea uses the BI Information system for understanding customer behaviour and uses that information to develop marketing strategies. It increases the sales of the product of the company. Stitch Fix Company provides online personal accessory and clothing styling services uses data science and recommended algorithms of BI Tools throughout their buying process to personalised their products as per the requirements (Ryan Ayers. 2020). Netflix also uses the information and data using BI software to get more people and engage them with their content. Walmart uses BI software to influence in-store and online activity. They analyse simulations to understand the purchasing patterns of customers. It helps them to increase the marketing and sales of products of the company.
Followings are some examples of advanced and updated Business Intelligence Software:
Power BI is the Business Intelligence Tools and it is serviced by the Microsoft Company. It provides interactive visualisations of data and provides the proper services for enhancing the business intelligence capabilities through the simple interface for creating the own business reports and dashboards. It brings the raw data from different sources also from a simple spreadsheet to cloud base data. It helps in sharing powerful insights by analysing the marketing and sales data.
Oracle Analytics Cloud is a Business intelligence Software system that is embedded with the machine learning facility (Oracle.com. 2021). It helps the organisations to discover effective and unique new business insights faster with the facility of a Business intelligence system and automation system.
Qlik Sense is another Business Intelligence Information System that helps SMEs and other companies to create interactive dashboards and tools based on marketing and sales data, operational data and data from different departments of the company (Qlik. 2021). It helps in creating stunning graphs and charts to make relevant business decisions.
SAS BI is also a cloud-based distribution model to deliver business analytics services like business reports and dashboards (Sas.com. 2021). It analyses the business data using modern cloud BI technology.
Tableau Business Intelligence uses the ad hoc analysis process to improve the ability to better see and understand the business data across every department of the company for better decision making (Carlisle, 2018).
Recommendation: Student 4
Based on the overall analysis, it is recommended that Fibre Fashion Company can use the Power BI Software to develop the business insights for marketing and sales of the company. Power BI will help the company to meet the enterprise business intelligence needs and self-service needs. It is the largest and fastest-growing business intelligence information system. It creates and shares effective and interactive data visualisations across the entire global data centre. It also includes the national clouds to meet the regulation and compliance needs of the Company (Powerbi.microsoft.com. 2021). Power BI Desktop, Power BI Service and Power BI Mobile Apps these three elements are the total package by Microsoft to provide an effective Business Intelligence Information system for the SMEs and also other leading companies. The Cost-effective plans and high-quality data analysis facility increases the demand for this product. Moreover, the Power BI Report server allows the company to publish the reports of the Power BI to the on-premises remote server after the report has been created in the Power BI Desktop. Iqbal et al. (2018) stated that the BI system drives the business decision based on the current, historical and potential future data. Predictive analytics system uses predictive modelling, data mining and machine learning system for making the projections and assumptions of future business events. It also helps in assessing the likelihood of particular events. Prescriptive analytics helps in revealing the actual reason for taking the particular action and initiative for enhancing the business performance. It enables the simulation and optimization of the marketing and sales data and uses the decision modelling system to provide the best possible business actions and decisions for the growth of SMEs. BI Tools helps marketers track the campaign metrics from the company’s central digital space. It helps SMEs in real-time campaign tracking that helps in measuring the performance of each effort and develop a plan for future business campaigns. It gives the marketing teams of the company more visibility into the overall business performance. BI Tools helps the sales team to quickly access complex information like customer profitability information, discount analysis information and information regarding the lifetime value for customers (Chiang, Liang & Zhang, 2018). It helps the sales managers to monitor sales performance, revenue targets with the real-time status of the sales pipeline using BI Dashboards with data visualizations and real-time business reports.
The main Key Features of the Power BI are:
.png)
Fig : Overview of Power BI information system
Source: (Powerbi.microsoft.com. 2021)
1. Power Query allows the transformation and integration of the company’s business data into the web service of Power BI. The company can shred the data across multiple users and multiple retailers in different geographic locations. The company can also model this data for enhanced data visualisation (Powerbi.microsoft.com. 2021).
2. The Common model of the database allows the company to use extensible database schemas and construction.
3. The Hybrid Development Support helps the tool of business intelligence to connect to the different data sources. It allows automatic data analytics application to information by creating the subsets of data through the use of quick insight feature.
4. The customisation feature can help the company to change the appearance of data visualisation tools. It also helps in importing new business intelligence tools into the platform.
5. The Dashboard of Power BI embedded in other appropriate software products through the use of APIs.
6. Complex data Models can also be divided into small and separate diagrams by using the modelling view common properties. It can be set, modified and viewed the data as per the requirements.
7. Cortana integration facility allows the employees and users of the company to query for any data verbally by using natural languages. It provides a digital assistant facility. The Power BI System helps in easily and quickly sharing the relevant data and meaningful insights after analysing the marketing and sales data across all system such as IOS, Windows and Android (Powerbi.microsoft.com. 2021).
Fig : Sales Performance Report
Source: (Powerbi.microsoft.com. 2021)
It will help the company to protect their marketing and sales data details by using the Power BI security facility with the other facilities like Azure Private Link, Service tags and Azure Virtual Network. It will help the company to prevent data loss. Power BI Desktop is also free for clients to use and the Pro level of the Power BI Information system is also available at a low monthly price per user. Moreover, the weekly and monthly updates of the Power BI improve the marketing and sales data analysis capability. It will help the Fibre Fashion Company to develop better decisions for enhancing the sales of the product. It will help the Company to get self-service analytics reports at an enterprise scale. It reduces the complexity, added cost and data security risks of recording the marketing and sales data and details clients, and sales per brand details that scales data from the individual level to the organisation level as a whole (nabler.com. 2021). It uses Smart tools, facility of data visualizations, tight integration of excel, prebuilt data connectors and custom data connectors and built-in AI Capabilities helps in providing strong outcomes for helping management of the company to make better decisions. Moreover, end-to-end encryption of the data, sensitivity labelling and Access monitoring system in real-time will increase the data security of the marketing and sales data, clients’ data and details of sales per brand of the company (Becker & Gould, 2019).
Fig : Transforming Excel data into Power BI
Source: (Powerbi.microsoft.com. 2021)
Power BI will allow the company to correlate the marketing data and metrics from the different business sources. It also removes the maximum possibility of having false positives from the marketing data. The Company can easily connect the data models, excel queries and other reports regarding the sales data to the Power BI Dashboards. It helps the company to gather the sales data of the company, analyse the data, publish and share the outcomes and business data in excel in new ways (Carlisle, 2018). It will help the company get new insights from the data and use the effective business insights for making the appropriate business decision for enhancing the business activities of the Fibre Fashion Company. It will help the company to track the record of their products in their inner-city warehouse of company. The use of the Power BI Software will enhance the skills and knowledge of the staff in providing unique services to the clients of the company. It will help them to maintain error-free transactions and ordering activities with their clients (Wright & Wernecke, 2020). It will help the fibre fashion Company to develop a loyal and trustworthy relationship with their clients that will help them to expand their business in the broader market.
Conclusion: Student 1
It concluded that the Fibre Fashion Company can use the Power BI Information System to get more meaningful business insights by analysing the marketing and sales data of the Company. The Power BI software will help the company to improve the security of their recorded data in the database system. It will help the company to enhance the privacy of the clients’ data and details of the sales record per brand. It will help the company to develop new business insights for improving the marketing and sales figure of the Fibre Fashion Company. It will help the company to take the appropriate decision for improving the market share of the company. It will help the company to track the record of their products per brand in the warehouse. It will help the company to develop a fruitful business relationship with their clients that will help them to increase their sales and marketing profitability in future. The report also discussed the importance of data analysis for SMEs for the enhancement of their business in the market. It revealed that the use of the data analysis facility helps SMEs to achieve their business goals and objectives.
References:
.png)
.png)
MIS605 Systems Analysis and Design Case Study 2 Sample
Task Summary
Based on your responses to Assessment 1 – Written assessment, perform process and data modelling and develop and document a number of design diagrams using UML (including Context Diagram, Level 0 and Level 1 Data Flow Diagram, Entity Relationship Diagram).
Scenario (The Case)
Book reading is an extremely healthy activity. It has many benefits and above all, it is exciting, entertaining and a great way to release stress, anxiety and depression. These are not the only benefits. Above everything; book reading helps in mental stimulation; improvement of memory and it also helps in improving language skills. It also certainly allows an individual to help concentrate better. In short, the benefits are enormous.
In recent times we have been introduced to technologies such as laptops, cell phones, tablets and other technologies but to date, the conventional book reading is something that people cherish and enjoy in its own way. It is believed that a “book has no substitute” and book readers from all over the world firmly agree to this.
Cynthia, a young technopreneur and a book lover; plans to open an online lifestyle substitute business named ‘bookedbook.com’. This online business is Cynthia’s dream. Cynthia has formally registered her new company, everything is in place from a legal perspective and the company now has ample funds to develop an online website that would support Cynthia’s business idea. bookedbook.com would be an extremely interesting website. This website will require user registration. Children would also be able to register but their registration would be accompanied with some details of parents and their contacts. The website would only offer individual registrations and proof of ID would be a must when registering. bookedbook.com will offer quarterly, biannual and annual memberships.
The whole idea is very simple. Registered book readers would be able to launch the books that they own and which they would want to give away to other registered members. A book launch would require complete details of the book. It would also require the user to provide the address where the book is available. Once the book details are provided by the subscriber (registered book reader) the company’s content manager would approve the book launch request. Once approved, the book would be available for all users for them to review and/or acquire. The review process would allow all users to provide feedback and comments about the book and would also allow users to rate the book. The acquisition process would allow book readers to acquire the book from the book owner.
The users planning on acquiring the book, would make a request for book acquisition. This request would help facilitate book reader meetup and exchange books. Once the book would be acquired the book owner would have the option of removing the book.
Bookedbook.com will also allow users to interact with one another via messaging and chat rooms. Users will be given an option to decide the mode of communication that they would prefer. Off course all chat request, messages and acquisition request and all other messages are also provided to the user via email that is provided at the time of subscription.
The website would also provide a portal to the administrator for data analytics. Cynthia is keen to observe and analyse every type of data that is obtained at this website. For example, she wants to know which book is being exchanged mostly, she wants complete customer analytics, book
exchange analytics, analysis of book reviews and rating and other similar portals for data analysis.
As soon as the user registration would expire, all book launch requests would be halted by the system and the users interested in acquiring the book(s) placed by the user whose registration is about to expire would be sent an email that these book(s) are no longer available. Users would be asked to renew their subscription 15 days before the registration expiry date to ensure continuity of services.
Cynthia does not want this website to be a book exchange platform only. She also wants the website to provide a platform for all the users to arrange for an online and face to face meetup. She wants to ensure that any book meetup events that bookedbook.com plans should be available to its users.
Users should be able to register for these events which may be paid or unpaid. She feels that these meetups would be a great source of fun for book lovers and also a source of marketing for the company.
In order to ensure this website stays profitable Cynthia also wants this website to allow book authors from all around the world to advertise their books on bookedbook.com. This functionality, however, would not require book authors to register with bookedbook.com formally. Book authors would be able to just fill in a ‘book show request form’, provide their details, provide the details of their book and a credit/debit card number. They would also provide information about the time period for which they want their book to be advertised on the website. Advertisement requests would also be approved by the content manager. Once approved, the book authors would be charged and the advertisement would go live. The ad would be removed by the system automatically once it reaches the end date. bookedbook.com will only allow advertisement of up to 5 books at a time. All advertisement requests would be entertained by the system on a first come first serve basis. The advertisement functionality is also available for subscribers. In this case the fee for advertisement is very minimal.
Cynthia wants this website to be upgradable and secure. She wants simple and modern interfaces and also wants a mobile application version of this website.
Instructions
1. Please read case study provided with assessment 1. Please note that every piece of information provided in this case study serves a purpose.
2. Please complete the following tasks:
Task 1.
Create a Context Diagram for the given case study.
Task 2.
Create and document a Level 0 Data Flow Diagram (DFD). The Level 0 DFD should contain all
the major high-level processes of the System and how these processes are interrelated.
Task 3.
Select three important processes from Level 0 DFD, decompose each of the processes into a
more explicit Level 1 DFD.
Task 4.
For the given case study, provide an Entity Relationship Diagram (ERD).
For the given case study, identify the data stores including the files that are not part of ERD.
Task 6.
Translate the ERD you developed in Task 4 into a physical relational database design.
Document database tables and their relationship in MSWord file. Normalise your database design to the Third Normal Form (3NF).
Please note that your responses to the tasks above must relate to the case study provided.
Solution
Introduction
The case study deals with the online lifestyle substitute vision of young technopreneur named Cynthia. The bookedbook.com website is concise with features like user registration, advertisement, data analytics, review and book acquisition. The booked book. For Assignment Help com aims to serves as a platform for the book lovers all across the world. This website offers authenticity via series of procedures followed up for user registration. This platform allows the one user to interact with other via messaging and chat rooms. This assignment has designed the database to store the data precisely dealing with user, book, advertisement and other entities provided. The rest of the assignment is organized as such, context diagram, Level 0 Data Flow Diagram (DFD), Level 1 Data Flow Diagram (DFD), Entity Relational Diagram (ERD) and at last Schema design up to 3 Normal Form (NF).
1. Context Diagram
The context flow diagram is diagrammatic representation of the system (Sciore, 2020). The CFD has a centric bubble, drawn in the epicenter of the diagram. The rest of the interconnected processes encloses this context bubble. Arrow headed lines with labeling states the flow of information. CFD gives out the high-level view without going into the details of it. This is how data hiding is achieved via CFD. CFD unlike other diagram is not for technocrats or engineers. It is to be used by project stakeholder therefore should be designed as simple as possible. Pros and cons of the Context Flow Diagram are follows:
Pros:
• CFD makes error listing easy and handy.
• If helps to trace out the rough sketch of the project straightforwardly.
• There are no limitations to the shapes that are used to depict CFD. Any preferred symbols can also be used. No hard and fast rule exists.
• This do not ask for any technical skillset to understand.
Cons:
• Context flow diagram fails to lay down the sequence of the process happening. By the sequence it means parallel execution of the project processes or sequential processing of the project processes.
• CFD diagrams are erroneous. Since they are just a high-level depiction without venturing about the detailing of the process happening.
• Context flow diagram fails to display out the all the detailing involved in the process. Moreover, to present out the exact relationship in CFD is also very difficult. Therefore, the need for more explained ER diagrams were felt. Unlike other diagram CFD do not go for well-defined meaning for the geometric shapes used in it.
Context Flow diagram in respect of proffered case study is delineated in figure 1.
.png)
Fig 1. Context Diagram
2. Level 0 Data Flow Diagram
The Level 0 DFD (Harrington, 2016) depicts high-level processes of the system namely, advertisement, user registration, book acquisition, review and data analytics and others. The major components of DFD are listed below-
- Processes – It is represented by rounded rectangle.
- Data Flows - It can be represented by straight line with arrowhead. The direction of arrowhead represents the flow direction.
- Stored data – It can be represented by two horizontal and parallel lines including a label mentioning the database name.
- External Entities – It can be represented as a rectangle.
The diagrammatic representation is depicted in figure 2.
.png)
Fig 2. Level 0 DFD
a. Advertisement
In the context diagram advertisement process depicts the two types of labeled flow. Internal flow labeled as "Payment", towards the context bubble, ventures the payment revenue generated by the bookedbook.com via the advertisement displayed on the website. External flow labeled as "Provide slot", outwards the context bubble, asks for the time period for which their book has to be advertised on the website. The advertisement process allows the authors from all over the world to advertise their book on bookedbook.com. This process does not ask for the registration. Authors have to fill the 'book show request form' along with time period and payments.
b. User Registration
The website bookedbook.com offers its website visitors to get themselves registered. The user registration process asks users for ID proof in the return website gives registration number to the user. The arrow headed line pointing towards the context bubble labeled as "ID proof" depicts the ID proof requirement asked by bookedbook.com for the authentication purpose. The arrow headed line pointing outwards the context bubble labeled as "Provide Registration Number" depicts the allotment of registration number to the user via the portal. Children are also allowed to register. The nitty gritty for their registration process will also be the same. In addition, they will be asked for parents’ details and contact number. Registered book user is allowed to launch the book they own. The registered user can give away book to other registered members.
c. Book Acquisition
Book acquisition process allows the book reader to acquire the book from the book owner. The user has to make a request first for the book acquisition. This request facilitates the smooth meet-up and book exchange process to happen. The user can remove the book after the successful book acquisition. In the context diagram this process depicts the two types of labeled flow. Internal flow labeled as "Approval", towards the context bubble, marks the approval of the book. External flow labeled as "Details", outwards the context bubble, provides the details of the required book.
d. Data Analytics
In the context diagram Data Analytics process depicts the two types of labeled flow. Internal flow labeled as "Analysis Result", towards the context bubble, this provides the results, done on the given dataset to website administrator. The prerequisite for the results to be generated is dataset generated on the website. External flow labeled as "Data", outwards the context bubble, this provides the dataset for the analysis. The data is broadly centric to customer and book. This includes all possible type of data generated like whichever book is exchanged most, which one is reviewed best and other related information.
e. Review
The review bubble depicted in the context diagram and Level 0 data flow diagram allows the user to provide feedback and comments about the book. The rating of books is generated. This review mechanism serves the purpose for data analytics. In the context diagram Review process is presented inside the bubble. The two-arrow headed line one pointing outwards from the main context bubble, labeled as "Related Data" and other one pointing towards the main context bubble, labeled as "Feedback" depicts the types of functionalities happening.
3. Level 1 Data Flow Diagram
Three important processes from Level 0 DFD are decomposed further and stated below. The Level 1 DFD are presented as follows:
a. Level 1 DFD (Narayanan, 2016) for User Registration in accordance with the case study provided is depicted in figure 3a.
.png)
Fig. 3a. Level 1 DFD for User Registration
b. L Level 1 DFD (Narayanan, 2016) for Book Advertisement in accordance with the case study provided is depicted in figure 3b.
Fig. 3b. Level 1 DFD for Book Advertisement
c. Level 1 DFD (Narayanan, 2016) for Book Launch in accordance with the case study provided is depicted in figure 3c.
.png)
Fig. 3c. Level 1 DFD for Book Launch
In Level 1 DFD, the processes of level 0 DFD are further decomposed in sub-processes. It is used to show the internal processes of the major/trivial process of level 0 DFD.
4. Entity Relationship Diagram
ER diagram has three main components: Entity, Attribute and Relationship (Cooper, 2013). ER diagram uses several geometric shapes to portray out different meaning to entities involved. Unlike context diagram where the high-level functioning of the process is depicted, ER diagram lays down all the nitty gritty involved in relation with the process. The required entity relationship diagram for the given case study is depicted in figure 4.
.png)
Fig 4. ER Diagram
5. Schema design up to 3NF
ER diagram depicted in above figure is served as one of the fundamentals of physical relational database. Some of the relational schema (Date, 2019) is described below.
USER:
.png)
REVIEW:
BOOK:
.png)
ADVERTISEMENT:
BOOK ACQUISITION:
PR and FR stand primary key and foreign key respectively.
FIRST NORMAL FORM (1NF):
The relational schema is considered to be in first normal form if the attributes hold only the atomic values, i.e., no attribute may have multiple values. (Gordon, 2017). Basically, multivalued attribute is not allowed.
Example:
.png)
The following table is not in 1NF.
This can be converted into 1NF by arranging the data as in the following table.
.png)
SECOND NORMAL FORM (2NF):
The relational schema will be considered as in 2NF if and only if both the following conditions satisfies. The schema must be in 1NF (First normal form). There must be no non-prime attribute that is dependent on the any subset of candidate key of the schema.
A non-prime attribute can be defined as an attribute that is not the part of any candidate key.
Example: Consider the following table for example.
This table is in 1NF but not in 2NF, because ‘Age’ is non-prime attributes and is dependent on User ID, which is proper subset of candidate key. Thus, we can break the table in 2NF as-
And,
THIRD NORMAL FORM (3NF):
Schema to get into the third normal form must needs to be firstly observed in second normal form. Moreover, it should not hold transitive functionality. Transitive functionality reflects the dependency of non-primitive attribute on that of the super key.
Mentioned above are only necessary conditions for any relational schema to be considered as in third normal form.
Example: Consider the following table for example.
This table is in 2NF, but not in 3NF as the attributes Book ID and Book Name are transitively dependent on super key User ID. Thus, we can split the table as follows to make it in 3NF.
And,
References
.png)
MIS604 Requirement Engineering Case Study Sample
Task Summary
This final assessment requires you to respond to the given case study used in Assessment 1 and 2, so that you can develop insights into the different facets of Requirements Analysis in agile. In this assessment you are required to produce an individual report of 2000 words (+/-10%) detailing the following:
1. A Product Roadmap for the project
2. Product Backlog of coarse granularity including Epics and User stories
3. Personas who typifies the future system end user
4. Decomposition of Epics into User stories for first release
5. Minimum Viable Product (MVP) definition for first release
6. Story Mapping for MVP - ordering User stories according to priority and sophistication
7. Story elaboration of User stories for MVP to ensure that the User story is clear, along with the acceptance criteria for the elaborated stories to ensure the ‘definition of done’.
8. A paragraph detailing the similarities and differences between ‘traditional predictive’ and ‘Agile’ requirements analysis and management.
Please refer to the Task Instructions for details on how to complete this task.
Context
In the second assessment you would have developed capability in the areas of requirements analysis and requirements lifecycle management, which are well recognised Business Analysis skills and capabilities. However, Agile has become a recognised software development approach which is both adaptive and iterative in nature. This has necessitated the development of new and differentiated requirements analysis and management skills, techniques, and capabilities. This assessment aims to assist you in developing well-rounded skills as a Business Analyst who uses a spectrum tools and techniques. In doing so, you can draw irrespective of the approach your future employer may take to software development.
Task Instructions
1. Please read the attached MIS604_Assessment_Case Study
2. Write a 2000 words Agile Requirements Analysis & Management Report as a response to the case study provided.
3. Review your subject notes to establish the relevant area of investigation that applies to the case. Re- read any relevant readings.
4. Perform additional research and investigation and select five additional sources in the field of agile requirement specification, analysis, and management to add depth to your explanation of method selection.
5. Plan how you will structure your ideas for your report and write a report plan before you start writing.
6. The report DOES NOT require an executive summary or abstract.
Case Study
ABC Pty Ltd is a start-up tech company based in Adelaide Australia, who are currently seeking to develop an online delivery system named “ServicePlease”. The system aims to create a convenient platform to be used by service providers, customers, and supermarkets for home delivery of groceries to customer residents. The application will be available in both forms of website and mobile app, with separate views for service providers, supermarket, and customers. ABC Pty Ltd wants to launch this system to market in the next six months and have secured an investment for this. You have been hired by ABC Pty Ltd as the Business Analyst (BA) to help them with the requirement analysis for this project.
The “ServicePlease” application should provide the service providers to register with the system. During registration service providers will be asked to complete the background checking process. Criminal history or background will be checked through National Crime Check (NCC). Right – to – work will be checked through Visa Entitlement Verification Online (VEVO), which will confirm their citizenship, residency or visa status that allows them to work in Australia. All service providers will need to provide an Australian Business number (ABN), which will be checked through ABN Lookup. Service providers also need to give proof for delivery capability by car through driving license and vehicle registration certificate. Upon successful completion of registration, the service provider will be eligible and available for grocery delivery service in “ServicePlease”. Supermarkets can register with “ServicePlease” online delivery system. When registered, customers will be able to find the supermarket in “ServicePlease” system. Supermarkets can accept and prepare an order to be picked up by the service provider authorized by a customer. The system should enable supermarkets to rate service providers and certify as their preferred one. To use this service, resident customers need to sign-up first. Sign up can be verified with a valid mobile phone number and an email address. Customers need to set-up the payment method using credit card, debit card or PayPal, to pay for the service when used. While ordering, the application should enable customersto search and select a supermarket first (pick- up location). Then the customer needs to authorise a service provider from the available list (certified service providers will be shown at the top of this list, then based on rating) to pick up groceries from a selected supermarket and deliver to their residence (drop-off location). Once the job is completed, payment can be made securely through the app. Customer will get email confirmation after successful completion of an order. Customers also can rate and review the service provider, as well as the supermarket.
Solutions
Introduction
The report will discuss the different user stories and epics in developing a product, "ServicePlease", which is an online delivery system. The grocery stores can register in the system where the users can see the profile and order the products. A software system will require the development of user stories and product roadmap by developing personas from consumers' perspectives. For Assignment Help, The story mapping for the minimum viable product will be described in this report, where the sophistication of the design approach and priority of design according to the mapping of the product will be highlighted. The use of agile project management and the traditional predictive model will be discussed, where similarities and differences of each project management style will be examined.
Addressing the areas regarding case study
Product Roadmap for the project
ABC Pty Ltd aims to develop the "ServicePlease" online home delivery system based on the combination of website and mobile application. For that purpose, the roadmap to ensure efficient system development is needed to be considered. Release planning involved in product roadmap creates effective time management (Aguanno, & Schibi, 2018).
.png)
.png)
Table 1: Product Roadmap including releases and time
Source: (Developed by the author)
Product backlog including Epics and User stories
.png)
.png)
.png)
Table 2: Product backlog
Source: (Developed by the author)
Persona who typifies the future system end-user
.png)
Table 3: Persona engaged in satisfying end-users
Source: (Developed by the author)
Decomposition of Epics into User Stories for the first release
Requirements analysis for system development includes specific user stories which help to elicit the requirements for new systems in business (Stephens, 2015). The decomposition of epics into user stories will help specify the requirements and the tasks associated with each user story.
.png)
.png)
Table 4: (Epics decomposed into user stories)
Source: (Developed by the author)
Minimum Viable Product (MVP) definition for the first release
The first release will include several items which will increase the viability of the system. System design development through minimum viable products ensures basic operations within the software (John, Robert, & Stephen, 2015). The minimum viable products for the "ServicePlease" home delivery system may include a basic user interface design for registration, sign-up, and verification. The registration and sign-up processes will allow the users to enter into the system. Verification of the criminal history and other records of the service providers will help to maintain the safety of the residential customers and to appoint appropriate candidates as service providers. The interface will serve as a communication platform between the users and the system. The system will also include security check-up features like VCC, VEVO, ABN for the first release. The payment feature will also be developed during the first release. Apart from that, the "ServicePlease '' home delivery system will include the features like a search bar tool, navigation key, order desk, and feedback and review desk.
Story Mapping for MVP
The user stories related to the system development of "ServicePlease" in ABC Pty Ltd will be arranged systematically for identifying the priority level.
Priority 1
- The registration process in the first release is the most important step as it will ensure proper verification of the users' details.
- Inputting the criminal history, driving license, vehicle registration certificate, and citizenship proof, the service providers will register within the system.
- The security checking process helps to ensure authentication within the system (Liu et al. 2018).
Priority 2
- The sign-up process will help the customers to enter into the system by providing their email address, phone number, and basic details.
- Sign-up is essential for managing order placement and product search
Priority 3
- The payment option will help the resident customers to pay for the orders
- Information and transaction security during payment is essential (Serrano, Oliva, & Kraiselburd, 2018)
- The priority of the payment feature development in the first release is high
Priority 4
- Order preparation option will help the supermarkets to accept the orders of the customers.
- The priority of order desk creation in the first release is moderate
Priority 5
- The feedback and Review option will be generated after the first release, so the priority is low.
- The feedback process will help the customers to state their comments about the services.
Story elaboration of User Stories for MVP
.png)
.png)
Table 5: Story Elaboration of User Stories for MVP
Source: (Developed by the author)
Acceptance Criteria for elaborated stories
.png)
Table 6: Acceptance criteria
Source: (Developed by the author)
Similarities and differences between agile and traditional predictive analysis and management
Similarities:
The agile methodology delas with the development of user stories, roadmaps and develops product vision. It also helps to create user stories and develops a project management plan. Reasonable and marketable products are developed in an iteration due to which monitoring and creating the project development through a retrospective approach can be an easy approach. The primary focus of agile is to achieve targets and customer satisfaction. IT and software projects tend to prefer agile project management (El-Wakeel, 2019). On the other hand, Project charter development and the project plan is developed by developing sub-projects in the case of traditional project management. Also, interim deliverables are developed and the project control and execution are managed with predictive analysis. Following a waterfall model and each phase are planned at different stages of the product life cycle.
Differences
Agile focuses on planning, cost, scope and time with prominence with term work and customer collaboration. Considers customer feedback and constant development at each phase of iteration, preventing time consumption and improved customer satisfaction. The client involvement is high as interaction and requirements constantly change in every phase of development. Both current and predictable requirements are used where the waterfall model is considered. Agile project development of good quality, motivation in team performance and client satisfaction (Loiro et al. 2019). In the case of traditional predictive methodology, The project follows the same life cycle where every stage is fixed, like planning, design, building, production, testing and support. The requirements are fixed and do not change with time. The current and predictable requirements are considered as the product develops completely without any change in iterative phases. Coding is done at a single stage, and testing is not performed at every iteration.
Conclusion
The epic story and user identification help in developing the right product according to customer requirements. Minimum Viable Product design is important to initially develop the product outcomes and the features associated with the software design. Using an agile project approach will be helpful for the design of software as feedback at iterative stages can guide in user mapping based on requirements, and the final product can be justified in terms of the demand and identification of the probable consumers. The ordering of user stories according to priority is elaborated, which is helpful in developing the product. The definition of done is achieved by developing the product through story mapping based on user stories, and the persona development identifies the specific expectations related to consumer experiences and requirements associated with the product.
References
.png)
MIS609 Data Management and Analytics Case Study Sample
Task Summary
For this assignment, you are required to write a 1500-word report proposing data management solutions for the organisation presented in the case scenario.
Context
Module 1 and 2 explored the fundamentals of data management. This assignment gives you the opportunity to make use of these concepts and propose a data management solution (a pre- proposal) for the organisation presented in the case scenario. This assessment is largely inspired from Data Management Maturity (DMM)SM Model by CMMI (Capability Maturity Model Integration).
Task Instructions
1. Please read the attached case scenario.
2. Write a 1500-word data management pre-proposal for the organisation.
3. The pre-proposal should not only discuss the technical but also the managerial aspects (cost, manpower, resources, etc.). Please keep in mind that you are writing a pre-proposal and not a detailed proposal.
4. Please ensure that you remain objective when writing the pre-proposal.
5. Your pre-proposal should ideally answer (but not be limited to) the following questions:
a) What would the data management strategy be?
b) How would data communication be done?
c) Which kind of data would be managed by your organization and how?
d) How many staff members at your organization would manage data of this school; what would be the team hierarchy and what would their expertise be?
e) What resources would be required from the school?
f) What deliverables (hard and soft) would be provided to the school?
g) What would general data management operations look like?
h) How would data management policy be set and how would it be implemented?
i) How would metadata be managed?
j) How would data quality be managed?
k) How would data management practices be audited and how would quality be assessed?
l) How will user and business requirements be collected from the clients?
m) Which data architectures and platforms would be used?
n) How would legacy data be taken care of?
o) How would risks be managed?
p) What benefits would the school have as a result of outsourcing this service to your organisation?
q) What are the potential disadvantages that the school can face?
r) Others....
6. The questions mentioned above are written randomly, in no particular sequence. When addressing these questions in your pre-proposal, please ensure that you write in a systematic way. Make use of the web to find out what pre-proposals look like.
7. You are strongly advised to read the rubric, which is an evaluation guide with criteria for grading your assignment. This will give you a clear picture of what a successful pre-proposal looks like.
Solution
Section 1
Introduction
Westpac was formed in 1817 and is Australia's oldest bank and corporation. With its current market capitalization, Commonwealth Bank of Australia as well as New Zealand has become one of the world's top banks, including one of the the top ten global publicly traded enterprises (WestPac, 2021). For Assignment Help, Financial services offered by Westpac include retail, business & institutional financing, as well as a high-growth wealth advisory business. In terms of corporate governance and sustainability, Westpac seems to be a worldwide powerhouse. For the past six years, they have been placed top in the Dow Jones Sustainability Index (WestPac, 2021).
Reason for selection
Considering Westpac Group been around for a long period of time, it was a logical choice. Big customer-related knowledge has been a problem for the organisation in its efforts to use big data analytics to make better business decisions. Since the organisation faced hurdles and gained outcomes, it's best if one learn about how they used big data analytics techniques to overcome those obstacles given their massive database.
Business of Westpac
Westpac Group is a multinational corporation that operates in a number of countries throughout the world. Four customer-focused deals make up the banking group, all of which play a critical role in the company's operations. A wide variety of financial and banking services are offered by Westpac, encompassing wealth management, consumer banking, & institutional banking. Over the course of its global activities, Westpac Group employs about 40,000 people and serves approximately 14 million clients (Li & Wang 2019). Large retail franchise comprising 825 locations and 1,666 ATMs throughout Australia, offering mortgage & credit card and short-long-term deposits.
Section 2
Concepts of Big Data
Unstructured, structured, & semi-organized real-time data are all part of the "big data" idea, which encompasses all types of data. It has to cope with massive, complex data sets which are too large or complex for standard application software to handle. To begin with, it's designed to collect, store, analyse, and then distribute and show data. Professionals and commercial organisations gather useful information from a vast amount of data. Businesses utilise this information to help them make better decisions (Agarwal, 2016). Many major organisations use data to produce real-time improvements in business outcomes and to build a competitive edge in the marketplace among multiple firms. Analyzing data helps to establish frameworks for information management during decision-making. Consequently, company owners will be able to make more informed choices regarding their enterprises.
Business intelligence
The term "business intelligence" refers to a wide range of technologies that provide quick and simple access to information about an organization's present state based on the available data. BI uses services and tools to translate data into actionable information and help a firm make operational and strategic decisions. Tools for business intelligence access and analyse data sets and show analytical results or breakthroughs in dashboards, charts, reports, graphs, highlights and infographics in order to give users detailed information about the company situation to users (Chandrashekar et al., 2017). The term "business intelligence" refers to a wide range of techniques and concepts that are used to address business-related problems that are beyond the capabilities of human people. An specialist in business intelligence, on the other hand, should be well-versed in the methods, procedures, and technology used to collect and analyse business data. In order to use business intelligence to address problems, those in this position need analytical talents as well (Schoneveld et al., 2021).
Data warehousing
In the data warehousing idea, there are huge reservoirs of data for combining data from one or many sources into a single location. In a data warehouse, there are specific structures for data storage, processes, and tools that support data quality (Palanivinayagam & Nagarajan, 2020). Deduplication, data extraction, feature extraction, and data integration are only few of the techniques used to assure the integrity of data in the warehouse (Morgan, 2019). Data warehousing has several advantages in terms of technology. An organization's strategic vision and operational efficiency can be improved with the use of these technological advantages.
Data Mining Concept
Patterns may be discovered in enormous databases using the data mining idea. Knowledge of data management, database, and large data is required for data mining. It mostly aids in spotting anomalies in large datasets. It also aids in the understanding of relationships between variables using primary data. Furthermore, data mining aids in the finding of previously unnoticed patterns in large datasets. Data summaries and regression analysis also benefit from this tool (Hussain & Roy, 2016).
Section 3
Data Sources
A wide variety of external data sources were explored to gather the information needed for such an evaluation. The term "secondary data" refers to data gathered by anyone other than the recipient of the information. This material comes from a variety of sources, including the official site of the firm, journal papers, books, and lectures that are available throughout the web. A simpler overview is described below:
.png)
Problems Faced
There were a number of issues faced by Westpac Group when it came to collecting and storing data, managing marketing, goods, and services delivery, embezzlement and risk mitigation, absence of appropriate multiple channel experiences, inability to design adequate usage of information strategy, and sharing of data schemes (Cameron, 2014). There wasn't enough assistance from key players for the sector, particularly in terms of finance and board approval for initiatives. In addition to the foregoing, the following critical concerns were discovered:
• Report production or ad hoc queries were typically delayed since data generated by several programmes would have to be manually cleaned, reconciled, and manually coded. Owing to the duplication of work and data, there were also inefficiencies (Cameron, 2014).
• Inconsistent methods for data integration were employed (e.g., push of data into flat files, hand code,. This is also not future-proof because no concepts or approaches were employed to handle emerging Big Data prospects, such as data services as well as service-oriented architecture (SOA).
• There was an error in data handling and data security categories, which resulted in unwarranted risks and possible consequences.
Implementation of the Solution
The Westpac Group was aware that financial services businesses needed to advertise their services and products as a banking sector. When it came to serving consumers and managing customer data across numerous channels, the corporation realised that it had an obligation toward becoming a true, customer-centric organisation. That which was just stated implies that seamless multichannel experiences are available. It was only with the emergence or introduction of big data, notably in the realm of social media, that the bank was able to discover that channel strategies were not restricted to traditional banking channels alone. Before anything else, Westpac set out to establish an information management strategy that would assist them navigate the path of big data (Cameron, 2014). However, achieving such a feat was not without difficulty (WestPac, 2016).
It was determined that the Westpac bank needed better visibility into its data assets. Data warehouse senior System Manager, Mr. Torrance Mayberry recommended Informatica's solution. Torrance Mayberry, a specialist in the field, worked with the bank to help break down organisational barriers and foster a more open and collaborative environment for new ideas. Customer focus was still far off, but Westpac didn't stop exploring the vast possibilities data held, particularly on social media. There was a further increase in the bank's desire to understand its customers in depth. The bank included sentiment analysis within big data analytics as well.
Quddus (2020) said that IBM Banking DW (BDW) was used by Westpac for data warehousing, and that IBM changed the BDW model hybridized version, that was implemented in an Oracle RDBMS, to include the bank's best practises into its DW. As a result, IBM's BDW came to provide a fully standardised and comprehensive representation of the data requirements of said financial services sector. Informatica was the platform of choice for integrating and accessing data. Informatica Metadata Manager was also included in the implementation of Informatica PowerExchange. Informatica platform variant 8.6.1 was used by Westpac until it was updated to edition 9.1 (Quddus, 2020).
An EDW was used as the principal data warehouse architecture, serving as a central hub from which data was fed into a number of smaller data marts that were dependent on it. Analytical solutions for enabling and maximizing economic gain, marketing, including pricing were part of the supply of these data marts. As an example, financial products' price history was saved and managed in the DW, and then sent to the data mart in order to fulfil the analysis requirements for pricing rationalization. Informatica's platform gathered data from the bank's PRM system, that allowed this same bank to quickly refresh its knowledge of fraud and reduce individual risk. Data-driven decision-making at Westpac developed as a result of increased trust in the information provided by the DW, as well as the creation of new business links.
Section 4
Problems Faced in Implementation
Data warehousing (DW) was the first step in Westpac's road to Big Data. Similarly to other large corporations with data-intensive tasks, the Westpac Group has a large number of unconnected apps that were not meant to share information.
• There was a lack of data strategy. The lack of a single version of Westpac's products and clients because critical data was gathered and stored in silos, and dissimilar information utilisation and definitions were the norm; and the inability to obtain a single version of Westpac's products and clients because critical data was gathered and stored in silos, and dissimilar information utilisation and definitions were the norm (Cameron, 2014).
• Due to the laborious scrubbing, validation, and hand-coding of data from several systems, the response time for ad hoc or reporting production requests was sometimes delayed. In addition, there was a lack of efficiency due to the duplication of data and labour
• To integrate data, many methods were used, including pushing information into flat files and manually coding.
• Soa (service-oriented architecture) as well as data services didn't exist at the time; and there were no methodologies or ideas that might be used to handle new big data opportunities; Information security and data handling were classified wrongly, resulting in potentially harmful complications and hazards.
Benefits realization to WestPac
According to Quddus (2020), Westpac has reaped the benefits of the big data revolution in a variety of ways. According to Westpac's data warehouse, a large number of its business units (LOBs) are now able to get information as well as reports from it (DW). Westpac said that the bank's core business stakeholders started to realise the strategic importance of the bank's data assets therefore began to embrace Westpac DW acceleration. Financing, retail and commercial banking departments in both New Zealand and Australia as well as an insight team for risk analytics as well as customer service were all part of it. It was possible for Westpac to invest in the development of a comprehensive data strategy to guide business decisions by delivering relevant, accurate, comprehensive, on-time managed information and data through the implementation of this plan. Impacted quantifiable goals and results for securing top-level management help as a result of change. In Westpac's view, the project's goals and outcomes were viewed as data-driven. The chance of obtaining funds and board approval for such ventures grew in respect of profit and productivity.
Conclusion
Big data analytics have just placed the company in a functioning stage thanks to the potential future gains or expansions that may be derived from the examination of enormous amounts of data. The Westpac Group anticipates the big data analysis journey to help the banking industry obtain insights according to what clients are saying, what they are seeking for, or what kinds of issues they are facing. The bank will be able to create, advertise, and sell more effective services, programmes, and products as a result of this.
Recommendations
The following recommendations can be sought for
• These early victories are vital.
DW team at Westpac was able to leverage this accomplishment to involve key stakeholders as well as the (LOBS) or line of businesses, thereby increasing awareness of the problem for the company's data strategy by leveraging this internal success.
• To obtain the support of the company's senior management, provide a set of quantifiable goals.
Westpac correctly recognises that quantifying the aims and outcomes of data-centric projects in order to improve productivity and profit enhances the likelihood that certain projects will be approved by the board and funded.
• Enhance IT and business cooperation.
"Lost in translation" problems can be avoided if IT and business people work together effectively.
References
DATA4000 Introduction to Business Analytics Case Study 1 Sample
Your Task
Complete Parts A to C below by the due date.
Consider the rubric at the end of the assignment for guidance on structure and content.
Assessment Description
.png)
• You are to read case studies provided and answer questions in relation to the content, analytics theory and potential analytics professionals required for solving the business problems at hand.
• Learning outcomes 1 and 2 are addressed.
Assessment Instructions
Part A: Case Study Analysis (700 words, 10 marks)
Instructions: Read the following two case studies. For each case study, briefly describe:
a) The industry to which analytics has been applied
b) A potential and meaningful business problem to be solved
c) The type of analytics used, and how it was used to address that potential and meaningful business problem
d) The main challenge(s) of using this type of analytics to achieve your business objective (from part b)
e) Recommendations regarding how to be assist stakeholders with adapting these applications for their business.
Part B: The Role of Analytics in Solving Business Problems (500 words, 8 marks)
Instructions: Describe two different types of analytics (from Workshop 1) and evaluate how each could be used as part of a solution to a business problem with reference to ONE real-world case study of your own choosing for one type of analytics and a SECOND real-world case study of your choosing for the second type of analytics.
You will need to conduct independent research and consult resources provided in the subject.
Part C: Developing and Sourcing Analytics Capabilities
Instructions: You are the Chief Analytics Officer for a large multinational corporation in the communications sector with operations that span India, China, the Philippines and Australia.
The organization is undergoing significant transformations; it is scaling back operations in existing low revenue segments and ramping up investments in next generation products and services - 5G, cloud computing and Software as a Service (SaaS).
The business is keen to develop its data and analytics capabilities. This includes using technology for product innovation and for developing a large contingent of knowledge workers.
To prepare management for these changes, you have been asked review Accenture’s report
(see link below) and publish a short report of your own that addresses the following key points:
1. How do we best ingrain analytics into the organisation’s decision-making processes?
2. How do we organize and coordinate analytics capabilities across the organization?
3. How should we source, train and deploy analytics talent?
The report is prepared for senior management and the board of directors. It must reflect the needs of your organization and the sector you operate in (communications).
Solution
Part A
1. Netflix Predictive Analytics: Journey to 220Mn+ subscribers
a) The case study covers how predictive analytics are being used in a variety of sectors, such as e-commerce, insurance, and customer support.
b) Reducing client turnover is a possible and significant business issue that can be resolved with predictive analytics. Businesses may experience a serious issue with customer churn, which is the rate at which customers leave doing business with a company. It might lead to revenue loss and reputational harm for the business. For assignment help, Businesses may enhance customer retention and eventually boost revenue by identifying customers who are at danger of leaving and taking proactive measures to keep them.
c) Customer demands were predicted using predictive analytics, which also helped to decrease churn, increase productivity, better allocate resources, and deliver tailored marketing messages. Customer data was analyzed using machine learning algorithms to spot trends and forecast future behavior. Predictive analytics, for instance, was used to inform customer service professionals to take proactive measures to keep clients who were at risk of leaving based on their behavior (Fouladirad et al., 2018).
d) Having access to high-quality data is the biggest obstacle to employing predictive analytics to accomplish the business goal of reducing customer turnover. In order to produce precise forecasts, predictive analytics needs reliable and pertinent data. The forecasts won't be correct if the data is unreliable, erroneous, or out of date. Additionally, firms may have trouble locating the proper talent to create and maintain the predictive models because predictive analytics needs substantial computational resources.
e) It is advised to start with a specific business problem in mind and find the data necessary to address it in order to help stakeholders with designing predictive analytics solutions for their organization. Making sure the data is correct and pertinent to the issue being addressed is crucial. In order to create and maintain the predictive models, businesses should also invest in the appropriate computational tools and recruit qualified data scientists. To guarantee that the predictive models continue to be accurate and useful, organizations should regularly assess their effectiveness and make any necessary adjustments (Ryu, 2013).
2. Coca-Cola vs. Pepsi: The Sweet Fight For Data-Driven Supremacy
a) The article focuses on the food and beverage industry, particularly the competition between Pepsi and Coca-Cola in terms of leveraging data and analytics to create new products and enhance corporate processes.
b) Keeping up with shifting consumer preferences and tastes is one of the potential commercial challenges for Coca-Cola and Pepsi. The difficulty lies in creating new beverages that satisfy the changing market needs and offer a tailored client experience. This issue calls for a cutting-edge strategy that can use analytics and data to spot patterns and customer behavior instantly.
c) Coca-Cola and Pepsi have both utilized various types of data analytics to help in the development of new products. The Freestyle beverage fountain from Coca-Cola gathers information on the most popular flavor combinations that can be used to crowdsource new product ideas. In order to track long-term consumer behavior and use it to personalize marketing campaigns and customer experiences, Coca-Cola has also integrated AI, ML, and real-time analytics. As an alternative, Pepsi has validated new product ideas by using AI-powered food analytics technologies like Trendscope and Tastewise to forecast consumer preferences. In order to spot new trends and forecast customer demand, these technologies comb through billions of social media posts, interactions with recipes, and menu items.
d) The accuracy and dependability of the data is one of the key difficulties when employing data analytics to create new goods. There is a chance that goods will be developed that may not be commercially successful since the data may not always accurately reflect actual consumer preferences and behavior. The demand for qualified data scientists and analysts who can decipher the data and offer useful insights for business decision-making is also great.
e) It is critical for stakeholders to understand the business issue they are attempting to solve before they can adapt data analytics applications for that issue. In order to gain insights into client behavior and preferences, they should identify the pertinent data sources and analytics technologies. In order to evaluate the data and offer actionable insights for business decision-making, stakeholders need also invest in qualified data scientists and analysts. In order to spur innovation and maintain an edge over the competition, firms should also be open to experimenting with new technology and methods.
Part B
By offering data-driven insights that can guide decision-making, analytics plays a significant role in resolving complicated business problems. This section will go over the two forms of analytics that can be utilized to solve business issues in many industries, namely descriptive analytics and predictive analytics.
Descriptive Analytics
A type of analytics called descriptive analytics includes looking at past data to understand past performance. It is frequently used to summarize and comprehend data, spot trends, and respond to the query "what happened?" Businesses can gain a better understanding of their historical performance and pinpoint opportunities for development by utilizing descriptive analytics.
Walmart is one example of a real-world case study that shows the application of descriptive analytics (Hwang et al., 2016). To optimize its inventory levels, cut expenses, and enhance the customer experience, Walmart employs descriptive analytics to examine customer purchasing trends and preferences. To find patterns in customer behavior, Walmart's data analysts examine sales information from both physical shops and online shopping platforms. By stocking up on items that are in high demand and reducing inventory levels of items that are not selling well, the corporation can better utilize the knowledge gained from these analysis (Dapi, 2012).
Predictive Analytics
Contrarily, predictive analytics is a subset of analytics that uses previous data to forecast future outcomes. When analyzing data, it is frequently used to spot trends and connections, predict the future, and provide a solution to the question, "What will happen?" Businesses can use predictive analytics to make data-driven decisions that foresee potential trends and business possibilities in the future.
The ride-hailing service Uber serves as one example of a real-world case study that demonstrates the application of predictive analytics (Chen et al.,2021). Uber employs predictive analytics to forecast rider supply and demand in real-time, enabling it to give drivers more precise arrival times and shorten wait times for riders. The business's data experts estimate the demand and supply trends for riders by analyzing data from a variety of sources, including historical ride data, weather forecasts, and event calendars. Uber can deploy its drivers more effectively thanks to the information gained from these analytics, which decreases rider wait times and enhances the entire riding experience (Batat, 2020).
Challenges
There are issues with using descriptive and predictive analytics, despite the fact that they both provide useful information for enterprises. The fact that descriptive analytics can only be used to analyze past data, which might not be a reliable indicator of future trends, is one of the key drawbacks of this approach. Furthermore, descriptive analytics ignores outside variables that can affect future performance. Using predictive analytics, however, presents a number of difficulties because it depends on precise and trustworthy data inputs. Predictive analytics may not produce accurate forecasts if the data is unreliable or incomplete.
Part C
Introduction
As Chief Analytics Officer for a large multinational corporation operating in the communications sector, I have been asked to review Accenture's report on building analytics-driven organizations and provide recommendations on how our company can develop its data and analytics capabilities.
Ingraining Analytics into Decision-making Processes
We must first create a data-driven culture before integrating analytics into our decision-making procedures. This entails encouraging the application of data and analytics at every level of the business, from the C-suite to the shop floor. By assembling cross-functional teams including data scientists, business analysts, and subject matter experts, we can do this. Together, these teams should pinpoint business issues that data and analytics may help to address and create solutions that are simple to comprehend and put into practice.
Investing in technology that facilitates data-driven decision making is another method to integrate analytics into our decision-making processes. Investments in big data platforms, data visualization tools, and predictive analytics software all fall under this category. By utilizing these tools, we can make greater use of the data we gather and offer data-based, actionable insights to decision-makers.
Organizing and Coordinating Analytics Capabilities
We must create a clear analytics strategy that supports our business objectives in order to organize and coordinate analytics skills across the organization. This strategy should lay out our plans for using data and analytics to accomplish our corporate goals as well as the precise skills we'll need to build to get there.
Additionally, we must clearly define the roles and duties of our analytics teams. This entails outlining the functions of domain experts, business analysts, and data scientists as well as developing a clear career path for each of these positions. By doing this, we can make sure that our analytics teams are functioning well and effectively, and that we are utilizing all of our analytical expertise to its fullest potential (Akter et al., 2016).
Sourcing, Training, and Deploying Analytics Talent
We must first have a clear talent strategy before we can find, train, and deploy analytical talent. This plan should detail the talents and expertise we specifically need, as well as the methods we'll use to find and develop the talent we need. We may achieve this through collaborating with colleges and training facilities, providing internships and apprenticeships, and funding staff development and training programmers.
Using our current employees as a resource for analytics talent is another option. Employees that are interested in data and analytics can be identified, and we can offer them the chances for training and growth they require to become proficient data analysts or data scientists. By doing this, we can utilize the knowledge and talents of our current personnel.
Enhancing Collaboration and Communication
Encourage collaboration and communication amongst divisions in order to successfully incorporate analytics into the organization's decision-making processes. Data silos and communication obstacles might make it difficult to adopt analytics solutions successfully. In order for teams to collaborate and solve business problems, it is critical to develop cross-functional communication and collaboration.
Investing in Training and Development
It is important to invest in the training and development of personnel if you want to create and coordinate analytics capabilities across your organization. This involves giving opportunities for upskilling and reskilling as well as strengthening data literacy abilities. Businesses may make sure that their staff members have the knowledge and abilities to use analytics tools and make data-driven decisions by investing in their training and development (Fadler & Legner, 2021).
Partnering with External Experts
Organizations can think about partnering with external experts to hasten the development of analytics capabilities. To acquire the most recent research and insights, this may entail working with academic institutions or employing outside experts. Organizations can benefit from a new viewpoint and access to cutting-edge analytics tools by collaborating with external experts.
Adopting a Continuous Learning attitude
Organizations must embrace a continuous learning attitude in order to effectively find, train, and deploy analytical talent. This entails supporting a culture of learning among staff members as well as their ongoing skill and knowledge development. In order to keep the company competitive in the market, it is also crucial to stay up to speed with the most recent analytics trends and technology. By adopting a continuous learning mindset, organizations can create a dynamic workforce that is agile and responsive to changing business needs.
Conclusion
To transform into an analytics-driven organization, we must create a data-driven culture, invest in the technology that enables data-driven decision-making, develop a clear analytics strategy, define the roles and responsibilities of our analytics teams, and create a talent strategy that enables us to efficiently find, develop, and deploy analytics talent. By doing this, we can make sure that we are maximizing the use of the data we gather and utilizing data and analytics to promote corporate growth and success in the communications industry.
References
.png)
TECH1300 Information Systems in Business Case Study 2 Sample
Your Task
This assessment is to be completed individually. In this assessment, you will create a comprehensive requirements specification plan using Agile Modelling frameworks for a new online shopping platform that meets the specifications described in the case study.
Assessment Description
You have been hired as a consultant to design a set of IT project specifications for a new online shopping platform. The platform will allow customers to browse, select, and purchase items online, and will require the development of a database to manage inventory and orders. You will need to apply various IT modelling techniques to produce a requirements specification plan and create a use-case model and associated user stories of a sufficient calibre to be presented to various stakeholders. Your task will be to document and communicate the requirements to various stakeholders, including the development team.
Case Study:
You have been hired as a consultant to design a set of IT project specifications for a new online shopping platform called "ShopEZ". ShopEZ is an e-commerce platform that will allow customers to browse, select, and purchase items online. The platform will require the development of a database to manage inventory and orders, as well as integration with various payment and delivery systems. The stakeholders for this project include the development team, the project sponsor, and the end- users (i.e., the customers). The project sponsor has set a strict deadline for the launch of the platform, and the development team is working in an Agile environment using Scrum methodology.
To complete this assessment, you will need to apply the elements of an Information Systems
Development Methodology to evaluate the business requirements, explain the components of Agile methodology, and document and communicate the information systems requirements to the stakeholders. You will need to use various IT modelling techniques to produce a requirements specification plan, including the creation of a use-case model and associated user stories. You will also need to create UML diagrams for the use-case, class, and sequence.
This assessment aims to achieve the following subject learning outcomes:
LO1 Apply the elements of an Information Systems Development Methodology when evaluating business requirements.
LO2 Explain the components of an Agile methodology and how they can be applied in the modelling process.
LO4 Document and communicate information systems requirements to various stakeholders.
Assessment Instructions
• In this assessment, students must work individually to prepare report highlighting business requirements.
• The report structure is stated below as part of the submission instructions:
1. Develop a comprehensive requirements specification plan using Agile Modelling frameworks.
2. The plan must include a use-case model and associated user stories, as well as UML diagrams for the use-case, class, and sequence.
3. Your plan must clearly communicate the requirements to various stakeholders, including the development team.
4. You must provide a detailed explanation of how you applied Agile methodology in the modelling process.
5. Your assessment must be submitted in a professional report format, adhering to KBS guidelines.
6. References
• Provide at least ten (10) academic references in Kaplan Harvard style.
• Please refer to the assessment marking guide to assist you in completing all the assessment criteria.
Solution
Introduction
The flexible and iterative approach to software development known as agile modeling places an emphasis on adaptability, collaboration, and communication. It focuses on creating visual models that are easy to understand and can change as the project goes on. This report is made for ShopEZ another internet shopping stage that expects to furnish clients with a consistent and helpful shopping experience. For assignment help, Responsibility as a consultant is to create ShopEZ's IT project specifications taking into account the requirements of the development team, project sponsor, and end users. This report will evaluate the business requirements, explain the components of the Agile methodology, and use IT modeling techniques like use-case models and UML diagrams to document the information systems requirements in this assessment.
The project explanation using four Methodologies for ShopEZ
Evaluating the Business Requirements:
As a consultant, the first responsibility is to take a specific and suitable methodology from Agile Methodology. Regarding making the software easier ShopEZ is going to use Kanban but especially the Scrum methodology. Scrum methodology is a very well-known and suitable methodology for the project(Athapaththu et al ., 2022). The Scrum methodology basically focuses on the breakdown of one project into many parts. Scrum methodology has a scrum board that includes an owner, a master core, and a development team. For this project as a consultant, it is very suitable to use a scrum methodology to do this software development for this project.ShopEZ is an upcoming e-commerce company that wants to
.png)
Figure 1: Scrum Diagram
(Source: https://lh3.googleusercontent.com)
2. Requirement gathering techniques used:
Agile Procedure is a lot of values, principles, and practices that guide the improvement of an item thing. The key convictions of Apt consolidate correspondence, facilitated exertion, client fixation, and responsiveness(Daum ., 2022). The guidelines of Flexible consolidate iterative and consistent new development, self-figuring out gatherings, and things drew in headway.
Kanban is a visual administration framework that helps groups track and deal with their work really. Work items are displayed as cards as they progress through the various stages of the workflow on a Kanban board. It advances straightforwardness, empowers a force-based approach, and permits groups to recognize bottlenecks and enhance their work process.
Continuous integration and continuous delivery (CI/CD) is a set of methods for automating software delivery to production environments. Continuous Integration entails developers regularly merging their code changes into a shared repository, which initiates automated build and testing procedures.
At the conclusion of each sprint or project phase, structured meetings known as agile retrospectives are held. The object is to ponder the group's presentation, distinguish regions for development, and characterize noteworthy stages for future cycles.
Business requirements using the Agile
Coordinated technique underscore cooperation and iterative turn of events, and client stories work with this methodology by advancing compelling correspondence among partners and the improvement group. User stories ensure that the final product or service meets end users' expectations by focusing on their requirements and points of view.
The primary client story features the requirement for a client account creation include, empowering clients to get to customized highlights. The related acknowledgment measures frame the means engaged with making a record and the normal results.
The shopping experience is the focus of user stories three and four, which allow customers to add items to their cart, proceed to the checkout process, and receive email order confirmations.
Following request status is the focal point of the fifth client story, accentuating constant updates and permeability for clients. The need for a mobile user interface that is both responsive and optimized is emphasized in the sixth user story.
The seventh client story features the meaning of client input through audits and evaluations. The actions that customers can take.
Values of Agile Methodology:
The Agile Methodology procedure is portrayed by a bunch of values and rules that guide its execution. These qualities are framed in the Dexterous Declaration, which was made by a gathering of programming improvement specialists in 2001. The four basic beliefs of Deft are Working programming over exhaustive documentation: Light-footed focuses on conveying a functioning item or programming that offers some benefit to the client(Da Camara et al ., 2020). While documentation is essential, Deft underlines the need to find some kind of harmony between documentation and real advancement work. The objective is to make unmistakable results that can be tried and refined.
Principals of Agile Methodology:
Here are the critical standards of the Deft approach: Embrace change: Dexterous perceives that necessities and needs can change all through an undertaking(Fernández-Diego et al ., 2020). It supports embracing change and perspectives as an amazing chance to work on the item. Dexterous groups are adaptable and ready to adjust to evolving conditions, even late in the improvement cycle. Gradual and iterative turn of events: Lithe advances an iterative and steady way to deal with improvement. Rather than endeavoring to convey the whole item without a moment's delay, it breaks the work into little, sensible augmentations called emphases or runs. Every cycle creates a working, possibly shippable item increase.
UML diagram:
use case diagram
.png)
(Source: Self Created in Draw.io)
Class diagram
.png)
(Source: Self Created in Draw.io)
Sequences diagram 1
.png)
Figure 4: UML Diagram
(Source: Self Created in Draw.io)
Sequence diagram 2:
.png)
.png)
Figure 5: UML sequence diagram
(Source: Self Created in Draw.io)
Communication to the stakeholders:
"ShopEZ" web-based shopping stage project, the partners and improvement group assume essential parts in the progress of the task. Here is an outline of their jobs: Project Support: The undertaking support is the individual or gathering who starts and offers monetary help for the task. They are liable for defining the undertaking's objectives, financial plan, and courses of events The venture support goes about as a resource for the improvement group and guarantees that the task lines up with the association's essential targets. Advancement Group: The improvement group is liable for carrying out the specialized parts of the venture(Schulte et al ., 2019). In a Nimble climate utilizing the Scrum procedure, the advancement group regularly comprises of cross-utilitarian individuals who work cooperatively to convey additions to the item. The group might incorporate programming engineers, data set overseers, analyzers, UI/UX fashioners, and other pertinent jobs. They are engaged with all periods of the task, including necessities investigation, plan, advancement, testing, and organization. End-clients (Clients): The end-clients are the people or substances who will associate with and utilize the "ShopEZ" stage whenever it is sent off. In this situation, the clients are the end-clients of the web-based business stage. Their fulfillment and client experience are essential to the progress of the stage.
Conclusion
The assessment has outlined the steps for developing a comprehensive requirements specification plan using Agile Modelling frameworks for a new online shopping platform called "ShopEZ". This plan included a use-case model and associated user stories, as well as UML diagrams for the use-case, class, and sequence. The assessment also explained the components of Agile methodology and how they can be applied in the modeling process. Finally, the assessment discussed how to document and communicate the information systems requirements to the stakeholders.
Reference
.png)
MIS609 Data Management and Analytics Case Study 3 Sample
Assessment Task
For this assignment, you are required to write a 2000-word case study report proposing data management solutions for the organisation presented in the case scenario.
Context
Module 5 and 6 explored the fundamentals of data management. This assignment gives you the opportunity to make use of these concepts and propose a data management solution for the organisation presented in the case scenario.
Assessment Instructions
1. Read the case scenario provided in the assessment area.
2. Write a 2000-word enterprise data management solution for the company
3. The solution should discuss how it helps the company to solve the technical or operational complexity of handling data.
Eg1: problem of securely maintaining customer data can be solved by implementing data security practises, setting up a security framework that establishes right users to get access to the data, continuous audit will help to monitor any malpractice etc.
Eg2: poor data quality issues can be solved by implementing data quality measures
4. Remember not to deep dive into any topics, the solution is more at a conceptual level
5. Please address the below areas
• Identifying the business requirements and existing issues in data operations (explain techniques used collecting requirements)
• Data management operations relating to the various kinds of data that the company deals with.
• Data Architecture (provide example of a proposed architecture that will help in processing the data e.g. ETL(data warehousing or cloud solution)
• Data quality measures
• Metadata management
• Handling legacy data - Data migration
• Data archival
• Data governance measures
• Data privacy
• Expected benefits
6. The areas listed above are indicative and are in no sequence. When addressing this in the solution, please ensure you write in an orderly fashion. Also, any other data management areas not listed above can also be covered.
7. You are strongly advised to read the rubric, which is an evaluation guide with criteria for grading your assignment.
Solution
Business Requirements and Existing Issues
The Status of the retail bank this time exposes severe issues brought on by out-of-date IT systems, which impede efficient data management and reduce client satisfaction. The bank has a sizable client base and a desire to grow even more, but it fails to manage new demands effectively. For Assignment Help, The problem is made worse by the dependence on uncoordinated technologies like Excel, Access DB, and outdated Oracle DB, which slows the generation of reports as a result of dispersed and inconsistent data. Additionally, the bank's capacity to respond quickly to problems and raise client satisfaction is hampered by insufficient data storage and management of consumer complaints. Modernisation, centralisation, and improvement of data processing are obviously necessary.
An complete business data management system is suggested to handle these problems. This approach ensures effective data management and integrity by replacing obsolete systems with contemporary database technology. The implementation of a centralised data repository will improve data quality and compliance when combined with strong data governance and security measures. Advanced analytics technologies may also help with the analysis and quicker response of consumer complaints (Orazalin, 2019, p.493). Business users may concentrate on innovation rather than mundane administration by automating manual data processes. Overall, the bank will be able to manage its expanding client base and update its IT environment thanks to this solution's simpler processes, increased customer happiness and increased business agility.
Data Management Operations
The retail bank is facing major difficulties with data management and its related operations given the status of the industry. The bank has a long history that dates back to the 1970s, has amassed a sizeable client base, and has a good reputation throughout Australia. The bank's quick client expansion has, however, resulted in operational inefficiencies brought on by outmoded IT systems and data management procedures. As a consequence of the current method's reliance on Excel sheets, Access databases, and outdated Oracle databases, data processing is fragmented, report production takes a long time, and data integrity is compromised.
.png)
Figure 1: Data Management Operations in Banks
Source: (Recode Solutions, 2022)
By year's end, the bank hopes to have one million customers, thus an updated and comprehensive data management system is required. The shortcomings in the present system make it difficult to handle consumer complaints effectively, resolve problems quickly, and make data-driven decisions. Furthermore, the problems are made worse by a lack of adequate data governance and security procedures. In order to enable business users to concentrate on strategic development rather of being bogged down by manual data activities, the Chief Technology Officer is aware of the necessity for a complete data management plan.
To address these concerns, implementing an enterprise data management solution is paramount. This solution will streamline data collection, storage, processing, and reporting, resulting in enhanced operational efficiency, improved customer satisfaction through faster complaint resolution, and better-informed decision-making (Reis et al., 2022, p.20). Additionally, the solution will establish robust data governance and security protocols, ensuring data quality, privacy, and compliance. Ultimately, the holistic approach aims to facilitate data-driven growth, enabling the bank to achieve its customer expansion goals while maintaining operational excellence and reputation.
Data Quality Measures
The current state of the retail bank highlights several data-related challenges that need to be addressed through an effective data management solution. The bank, with a long-standing reputation and an expanding customer base, is undergoing IT modernization to accommodate growth. However, the existing data infrastructure comprising Excel sheets, Access DB, and an outdated Oracle DB poses significant obstacles. These range from inefficient handling of customer requests and operations management to compromised customer satisfaction due to delayed complaint resolution. Generating reports from disorganized and disparate datasets is time-consuming, primarily due to data integrity issues stemming from poor data quality (Grimes et al., 2022, p.108).
There are several advantages to using an enterprise data management system. First, more accurate reporting and analytics will be possible because to enhanced data quality and integrity, which will allow for more informed choices. Second, by immediately resolving concerns, simplified procedures and effective data processing will raise customer satisfaction. Sensitive data will also be protected by the solution's governance and security safeguards, guaranteeing compliance with data protection laws. In the end, this solution will relieve business users of the stress of repetitive data administration duties and allow them to concentrate on strategic projects, promoting innovation and development.
Metadata Management
Metadata management is crucial for addressing the data-related challenges faced by the retail bank. Currently, the bank's operations are hindered by outdated systems and processes, leading to inefficiencies in managing customer data and operations. The bank's customer base is rapidly growing, and the use of Excel sheets, Access databases, and an old version of Oracle DB is causing data disarray and integrity issues. Due to scattered data sets and low data quality, it is difficult to provide timely reports for decision-making. Inadequate data storage and analytics skills also make it difficult for the bank to manage and report consumer concerns (Grimes et al., 2022, p.104).
It is crucial to establish a strong metadata management system in order to prevent these problems. In order to manage data definitions, linkages, and provenance across systems, a central repository must be established. With the help of this solution, data consistency, quality, and reporting and analytics will all be improved. Implementing governance and security measures will also improve compliance and data protection. The system will encourage innovation and development by automating data administration duties and allowing business users to concentrate on their main responsibilities. In the end, this strategy will speed up the processing of client complaints, increasing customer happiness and loyalty while also putting the bank in a position to easily meet its objective of one million customers by year’s end.
Data Governance Measures
A strong data governance policy has to be built to deal with these issues. Modern database systems will be used to centralise data storage, along with procedures for data integration and data quality implementation, as well as the establishment of distinct roles and responsibilities for data ownership. Data security measures should also be implemented to safeguard sensitive consumer information and guarantee compliance with relevant legislation, such as data privacy laws.
.png)
Figure 2: Types of Data Governance Measures
Source: (Nero, 2018, December 7)
The bank will profit in several ways by using an enterprise data management system. A faster response of client complaints will increase customer happiness and retention, which is the first benefit of streamlining data procedures. Second, more accurate reporting made possible by enhanced data integrity will lead to better decisions. Last but not least, the decreased human labour required for data administration chores would free up business users to concentrate on innovation and growth efforts, leading to the creating of new business possibilities and income.
Handling Legacy Data - Data Migration
For the bank’s modernization efforts and operational effectiveness, it is crucial to adopt a complete data management solution given the situation of the company today and the associated data-related problems. The bank's antiquated Oracle DB and legacy systems, such as Excel spreadsheets, Access databases, and Access databases, are unable to handle the growing client base and new demands. As a result, creating reports takes a lot of time, the data's quality is poor, and client satisfaction is suffering. A solid data transfer plan is suggested as a solution to these problems. In this approach, the current data from historical systems is moved to a more sophisticated and scalable platform, such a contemporary relational database or a cloud-based solution (Roskladka et al., 2019, p.15).
This method of data movement has several advantages. The bank would be able to manage the projected increase in clients with ease since it would first guarantee a smoother transfer to contemporary technology. Second, by consolidating data into a single repository, creating reports would be more quickly and cost-effectively. Additionally, increased data integrity would increase analytics' accuracy, resulting in better decision-making. In the end, the data transfer approach will lessen the load of legacy systems, allowing business users to concentrate on core duties, innovation, and customer-centric initiatives instead of being bogged down in manual data administration responsibilities. This transition to effective data management creates the groundwork for a bank that is more adaptable, responsive, and customer-focused.
Data Architecture
In response to the current challenges faced by the bank, a proposed enterprise data management solution aims to address data-related issues while supporting growth objectives. Given the bank's outdated systems and processes coupled with a growing customer base, a robust solution is imperative.
To streamline data operations, a modern data architecture is recommended, leveraging cloud-based technologies. This architecture involves Extract, Transform, Load (ETL) processes to efficiently collect data from sources like Excel sheets, Access DB, and Oracle DB. The data will then be cleansed, transformed, and loaded into a centralized cloud-based data warehouse. This repository ensures real-time access to accurate and consolidated data, thereby enhancing reporting efficiency and maintaining data integrity.
.png)
Figure 3: Data Architecture of Bank
Source: (Fernandez, 2019, August 20)
Benefits of this solution include improved operational efficiency, expedited decision-making, and elevated customer satisfaction. By automating data processes, bank employees can redirect their focus towards innovative business initiatives. Swift access to reliable data aids in promptly addressing customer complaints and boosting overall satisfaction. Furthermore, this data management approach establishes robust governance and security measures, mitigating risks associated with data mishandling. In conclusion, this holistic solution aligns with the bank's modernization goals and supports the CTO's vision of utilizing data for strategic growth (Grimes et al., 2022, p.171).
Data Privacy
One of the critical issues is the inability to manage customer complaints effectively, impeding the bank's goal of swift complaint resolution and improved customer satisfaction. The absence of a well-structured data storage mechanism for complaints, coupled with poor data quality, hinders insightful reporting and analytics. Furthermore, the lack of defined governance and security measures exposes the bank to potential risks associated with data mishandling. To address these challenges, implementing an enterprise data management solution is imperative. This solution would streamline data processes, centralize data storage, and enhance data quality through standardized practices. The integration of modern data management tools and technologies would enable efficient report generation and analytics, aiding decision-making processes. Moreover, by enforcing proper governance and security measures, the bank can ensure data privacy and mitigate potential breaches (La Torre et al., 2021, p.14)
Benefits of this data management solution include enhanced customer satisfaction through quicker complaint resolution, optimized operational efficiency, and improved data privacy and security. By liberating business users from tedious data management tasks, they can focus more on innovation and value creation, aligning with the Chief Technology Officer's vision for the bank's growth and modernization.
Data Archival
An enterprise data management system is essential to optimise operations and assure future scalability in response to the existing conditions of the company and the data-related difficulties encountered by the retail bank. Excel sheets, Access databases, and out-of-date versions of Oracle DB are just a few of the systems and procedures the bank now uses that make it difficult to handle data effectively and keep up with the growth in its client base. This leads to operational inefficiencies and a poor response to client concerns.
These problems will be solved and a number of advantages will result from using an extensive data management system. First, a crucial part of this approach will be data archiving. The bank may free up space on its current systems and improve the speed and responsiveness of those systems by preserving past client data and transaction records. Second, centralised data integration and storage will enhance data integrity and quality, allowing for more rapid and precise reporting. Furthermore, clear governance and security policies will guarantee data compliance and protect sensitive data. Overall, this solution will relieve business users of data administration duties so they can concentrate on core company responsibilities and innovation. Additionally, increased complaint resolution and operational efficiency will increase customer satisfactions.
Expected Benefits
The first step of the strategy is to centralize data storage and switch from outdated Oracle DB and separate systems like excel and Access DB to a more up-to-date, integrated database architecture. This change will improve data integrity, decrease duplication, and promote effective data retrieval, enabling the creation of reports more quickly and accurately. Second, the system has sophisticated data analytics and reporting features that will enable the bank to examine data on customer complaints, spot patterns, and respond quickly to resolve problems—all of which are in line with their objective of raising customer happiness.
The suggested solution also incorporates strong data governance and security mechanisms that guarantee regulatory compliance and protect private consumer data. By doing this, the bank's data handling procedures will be in line with industry best practices, reducing the likelihood of data breaches. Overall, the data management solution will allow business users to concentrate on strategic development objectives instead of being burdened by manual data management duties, freeing up critical time from them to do so.
References
.png)
ICC104 Introduction to Cloud Computing Case Study 2 Sample
Context:
This assessment assesses student’s capabilities to identify key cloud characteristics, service models and deployment models.
During this assessment, students should go through the four case studies identified below and prepare a short report (250 words each) around the case studies as per the instructions.
Case Study 1: ExxonMobil moves to Cloud
“XTO Energy is a subsidiary of ExxonMobil and has major holdings in the Permian Basin, one of the world’s most important oil-producing regions. To overcome the challenges of monitoring and optimizing a vast number of widely dispersed field assets, XTO Energy has been digitalizing its Permian operations. By using Microsoft Azure IoT technologies to electronically collect data and then using Azure solutions to store and analyse it, XTO Energy gains new insights into good operations and future drilling possibilities”. (Microsoft, 2018)
Read the full Case study: https://customers.microsoft.com/en-us/story/exxonmobil-mining-oil-gasazure
Case Study 2: Autodesk Builds Unified Log Analytics Solution on AWS to Gain New Insights
“Autodesk, a leading provider of 3D design and engineering software, wants to do more than create and deliver software. It also wants to ensure its millions of global users have the best experience running that software. To make that happen, Autodesk needs to monitor and fix software problems as quickly as possible. Doing this was challenging, however, because the company’s previous application-data log solution struggled to keep up with the growing volume of data needing to be analyzed and stored.” (Amazon Web Services, n.d)
Read the full Case Study at https://aws.amazon.com/solutions/case-studies/autodesk-log analytics/
Case Study 3: ‘Pay by the Drink’ Flexibility Creates Major Efficiencies and Revenue for Coca-Cola’s
International Bottling Investments Group (BIG)
“BIG’s stated goal is to drive efficiencies, higher revenue, greater transparency and higher standards across all of its bottlers. But, the bottlers within BIG each faced very unique challenges inherent to their business and markets. Thus the challenge for the business was how to address the unique complexities and requirements of a very diverse group of bottlers with efficient infrastructure and standardized processes.” (Virtual Stream, n.d)
Read the full Case Study at https://www.virtustream.com/solutions/case-studies/coca-cola
Case Study 4: Rocketbots improves its systems availability in difficult regions while optimizing the cost.
“Since Rocketbots in its essence is a software solution built on the cloud, they needed the availability to give their customers their high-end solution at any time. For other providers giving Rocketbots the availability, they needed in Southeast Asia proved difficult. By leveraging Alibaba Cloud’s many data centers throughout Asia, Rocketbots was able to give their customers an optimized solution that would work well and more importantly was available when they needed it.“ (Alibaba Group, n.d)
Read the Complete Case Study: https://www.alibabacloud.com/customers/rocketbots
Instructions:
The assessment requires you to prepare a report based on the case studies mentioned above.
Report Instructions:
Start off with a short introduction (approximately 250 words) stating what the report is about and some basic information relevant to the case study. For example, you can provide background information including some context related to cloud computing. This section will be written in complete sentences and paragraphs. No tables, graphs, diagrams or dot points should be included.
The main body of the report should comprise of four different sections of 250 words each (one
section for each of the above mentioned case studies). With each section specifically addressing the following questions about the case study.
• Introduction of the case
• What was the challenge?
• How the challenge was solved?
• What were the different service models each utilized?
• What are the different deployment models each utilized?
• What services of public cloud providers each case study used?
• Reflection
Finally, write a conclusion (approximately 250 words) as a summary of your analysis of the case. This section brings together all of the information that you have presented in your report and should link to the purpose of the assessment as mentioned in the introduction. You can also discuss any areas which have been identified as requiring further investigation and how this will work to improve or change our understanding of the topic. This section does not introduce or discuss any new information specifically, and like the introduction, will be written in complete sentences and paragraphs. No tables, graphs, diagrams or dot points should be included.
Solutions
Introduction:
This report explores the transformative power of cloud computing through a compilation of four diverse case studies. Cloud computing has emerged as a technological game-changer, offering businesses access to scalable, flexible, and cost-effective solutions to various challenges. For Assignment Help, Public cloud providers, including Amazon Web Services (AWS), Microsoft Azure, Google Cloud, and Alibaba Cloud, have risen as industry leaders, offering various services to cater to businesses of all sizes and industries.
In the digital age, organisations face ever-increasing pressure to adapt and innovate to remain competitive. Cloud computing has driven this transformation, enabling businesses to modernise their IT infrastructure, improve operational efficiency, enhance data management and analytics, and deliver superior customer experiences.
Throughout the case studies, we will examine each company's unique challenges and how they utilised cloud solutions to overcome these obstacles. We will also explore each organisation's different service and deployment models and the specific cloud services provided by public cloud providers in each instance.
As we delve into the intricacies of each case, we will witness the diverse applications of cloud computing, from optimising mining operations and enhancing software development to modernising IT Infrastructure and streamlining customer engagement. These real-world examples will provide valuable insights into the potential of cloud technologies to drive innovation and shape the future of businesses across various sectors. In an ever-changing digital landscape, cloud computing is a strategic imperative for organisations seeking to thrive in the modern era.
Case Study 1:
• Introduction: ExxonMobil, a global oil and gas industry leader, faced a significant challenge in optimising its mining operations for increased efficiency and productivity. To tackle this issue, they sought a cutting-edge solution that could leverage modern technologies to streamline their processes and enhance their overall performance.
• Challenge: ExxonMobil's complex mining operations involved extensive data processing, analysis, and management. The vast amounts of data generated from their mining sites made it imperative to find a solution that could handle the volume, velocity, and variety of data while ensuring data security and compliance (Microsoft. 2018).
• Solution: Azure's advanced data analytics and machine learning tools enabled them to gain valuable insights from the data, facilitating better decision-making and predictive maintenance strategies.
• Service Models: ExxonMobil utilised various service models provided by Microsoft Azure to address different aspects of its mining operations. They leveraged Infrastructure as a Service (IaaS) for scalable and flexible computing resources to efficiently manage their mining data and applications. Platform as a Service (PaaS) was used to build and seamlessly deploy custom data analytics and machine learning solutions.
• Deployment Models: ExxonMobil employed a hybrid deployment model to ensure the best utilisation of resources and meet specific operational requirements.
• Public Cloud Services: In their collaboration with Microsoft Azure, ExxonMobil utilised various services, including Azure Virtual Machines, Azure Machine Learning, Azure Data Factory, and Azure Kubernetes Service.
• Reflection: ExxonMobil's adoption of Microsoft Azure's cloud services exemplifies how cutting-edge technologies can revolutionise traditional industries. By leveraging Azure's advanced tools and service models, ExxonMobil successfully tackled their challenges, improving operational efficiency and increasing its competitive advantage in the oil and gas sector.
Case Study 2:
• Introduction: Autodesk, a renowned software company specialising in 3D design, engineering, and entertainment software, faced a critical challenge in efficiently managing and analysing their vast amounts of log data.
• Challenge: Autodesk's diverse suite of software products generated a massive volume of log data from various sources. The challenge lay in processing, storing, and analysing this data in real time to identify and resolve issues, monitor application performance, and optimise software development.
• Solution: AWS provided Autodesk with an efficient and cost-effective solution to address its log analytics challenge. Autodesk could centralise and streamline its log data management by adopting AWS Cloud services. AWS offered highly scalable storage options and powerful data processing tools that allowed Autodesk to easily handle large volumes of log data (Amazon Web Services).
• Service Models: Autodesk utilised multiple service models provided by AWS to optimise their log analytics. They leveraged Infrastructure as a Service (IaaS) for scalable computing resources, enabling them to deploy log processing applications without managing underlying hardware.
• Deployment Models: To meet their specific requirements and ensure seamless integration, Autodesk employed a hybrid deployment model. They retained critical on-premises Infrastructure for certain sensitive data while migrating non-sensitive log data and analytics to the AWS cloud.
• Public Cloud Services: In their collaboration with AWS, Autodesk utilised a range of services, including Amazon S3 for cost-effective and scalable object storage, Amazon EC2 for resizable compute capacity, and Amazon CloudWatch for real-time monitoring and alerting of log data.
• Reflection: Autodesk's successful integration of AWS cloud services for log analytics exemplifies how public cloud solutions can revolutionise business data management and analysis. By adopting AWS's versatile service and deployment models, Autodesk overcame the challenges posed by the massive scale of log data and transformed its log analytics process. This case study illustrates the power of cloud-based solutions in enabling companies to harness the full potential of their data, make informed decisions, and enhance overall business performance.
Case Study 3:
• Introduction: Coca-Cola, the world-renowned beverage company, embarked on a transformative journey to migrate its IT Infrastructure to the cloud. To achieve this, they partnered with Amazon Web Services (AWS), a leading public cloud provider known for its robust and scalable solutions.
• Challenge: Coca-Cola faced the challenge of modernising its IT infrastructure to keep pace with rapidly evolving business needs. Their existing on-premises systems struggled to handle the increasing demands of data processing, storage, and global accessibility.
• Solution: AWS offered Coca-Cola a comprehensive cloud solution that addressed its challenges. By migrating to AWS Cloud, Coca-Cola could leverage various services to modernise its applications, streamline data management, and enhance overall agility.
• Service Models: Coca-Cola utilised various service models provided by AWS to meet its diverse requirements. They leveraged Infrastructure as a Service (IaaS) to flexibly manage their computing resources and storage needs (Atchison, 2020).
• Deployment Models: To ensure a smooth and secure migration, Coca-Cola adopted a hybrid deployment model. They moved some of their applications and workloads to the AWS cloud while retaining sensitive data and critical operations in their on-premises Infrastructure (AWS., 2014).
• Public Cloud Services: In their collaboration with AWS, Coca-Cola used a wide array of cloud services. These included Amazon EC2 for resizable compute capacity, Amazon S3 for secure and scalable object storage, Amazon RDS for managed relational databases, and Amazon Redshift for advanced data analytics.
• Reflection: Coca-Cola's successful migration to AWS Cloud showcases the potential of public cloud solutions in addressing modern business challenges. By embracing AWS's service and deployment models, Coca-Cola effectively modernised their IT infrastructure, gaining improved scalability, flexibility, and cost-efficiency. This case study is an excellent example of how cloud migration can empower businesses to stay competitive, foster innovation, and adapt to the ever-changing technological landscape.
Case Study 4:
• Introduction: Rocketbots, a leading customer engagement platform, faced a significant challenge in managing and analysing vast customer data while ensuring seamless interactions across various messaging channels.
• Challenge: Rocketbots needed to efficiently handle large volumes of customer data generated through multiple messaging platforms like WhatsApp, Facebook Messenger, and more.
• Solution: Alibaba Cloud provided Rocketbots with a powerful and scalable cloud infrastructure to address customer engagement needs. By leveraging Alibaba Cloud's robust computing resources and AI capabilities, Rocketbots could process and analyse customer data in real-time (Alibaba Group).
• Service Models: Rocketbots utilised various service models offered by Alibaba Cloud to bolster their customer engagement platform. They leveraged Infrastructure as a Service (IaaS) for scalable computing resources to efficiently handle data processing and analytics.
• Deployment Models: Rocketbots adopted a hybrid deployment model to cater to their specific requirements. They integrated Alibaba Cloud's services with their Infrastructure to maintain data privacy and compliance.
• Public Cloud Services: In their collaboration with Alibaba Cloud, Rocketbots utilised various services. These included Alibaba Cloud Elastic Compute Service (ECS) for flexible computing resources, Alibaba Cloud Machine Learning Platform for AI-driven insights, and Alibaba Cloud Object Storage Service (OSS) for secure and scalable data storage (Artificial Intelligence and Cloud Computing Conference 2018).
• Reflection: Rocketbots' successful partnership with Alibaba Cloud demonstrates the power of public cloud solutions in optimising customer engagement and data management. By embracing Alibaba Cloud's service and deployment models, Rocketbots achieved enhanced scalability, real-time data analytics, and personalised customer interactions.
Conclusion:
The case studies presented in this report highlight the significant impact of cloud computing on businesses across diverse industries. The transformative potential of cloud solutions is evident in the successful outcomes of ExxonMobil, Autodesk, Coca-Cola, and Rocketbots. By adopting cloud services, these companies improved operational efficiency, optimised data management, and enhanced customer engagement. The versatility and scalability of public cloud providers, such as AWS, Microsoft Azure, Google Cloud, and Alibaba Cloud, played a pivotal role in driving innovation and delivering exceptional results. As cloud computing continues to evolve, businesses must recognise its strategic importance and embrace this technology to stay competitive and thrive in the digital era. In the rapidly evolving digital landscape, cloud computing has emerged as a catalyst for business transformation. The case studies of ExxonMobil, Autodesk, Coca-Cola, and Rocketbots provide compelling evidence of how cloud solutions can revolutionize operations, data management, and customer engagement. These real-world examples demonstrate that cloud computing is no longer just a technological trend but a fundamental enabler of innovation and growth.
The scalability, flexibility, and cost-effectiveness offered by public cloud providers have empowered companies to modernize their IT infrastructure and optimize processes. The ability to harness massive amounts of data in real-time through cloud-based analytics and machine learning has allowed businesses to make data-driven decisions and gain a competitive edge. Moreover, the adoption of hybrid cloud models has enabled organizations to strike a balance between maintaining critical operations on-premises and leveraging the cloud's agility and scalability.
References
.png)
TECH5300 Bitcoin Case Study 1 Sample
Your Task
This assessment is to be completed individually. In this assessment, you will evaluate the purpose, structure, and design of base layer 1 of the Bitcoin network, which provides the security layer.
Assessment Description
This assessment aims to evaluate your ability to analyse, evaluate, and critically assess the purpose, structure, and design of the base layer 1 of the Bitcoin network, which serves as the security layer. Additionally, you are required to explore the principles and significance of public-key cryptography in the context of Bitcoin transactions. By completing this assessment, you will demonstrate your proficiency in comprehending complex concepts, conducting in-depth research, and presenting well-structured arguments.
Case Study
Case Study Scenario: You have been appointed as a Bitcoin consultant for a financial institution seeking to explore the potential of utilising Bitcoin as part of their operations. Your task is to evaluate the purpose, structure, and design of the Bitcoin layer 1 network, with a particular focus on its security layer. Furthermore, you are required to analyse the role and impact of public-key cryptography in securing Bitcoin transactions.
Your Task: In this case study, you are required to prepare a detailed report addressing the following aspects:
1. Evaluation of the Purpose, Structure, and Design of Bitcoin Layer 1 Network:
a. Analyse the purpose and significance of the base layer 1 in the Bitcoin network, emphasising its role as the security layer.
b. Evaluate the structural components of the Bitcoin layer 1 network, including its decentralised nature, consensus mechanism, and transaction processing.
c. Assess the design principles and mechanisms employed within the Bitcoin layer 1 network to ensure security, immutability, and transaction verification.
2. Exploration of Public-Key Cryptography in Bitcoin Transactions:
a. Explain the fundamental principles of public-key cryptography and its relevance in securing Bitcoin transactions.
b. Analyse the mechanisms and algorithms used in public-key cryptography to ensure transaction verification, non-repudiation, and confidentiality in the Bitcoin network.
c. Evaluate the strengths and weaknesses of public-key cryptography within the context of Bitcoin transactions, considering factors such as key management, quantum resistance, and regulatory implications.
3. Evaluation of Security Challenges and Mitigation Strategies:
a. Identify and analyse the major security challenges and vulnerabilities associated with the Bitcoin layer 1 network, including potential attack vectors, double-spending, and transaction malleability.
b. Evaluate existing mitigation strategies and countermeasures employed to address these security challenges.
4. Future Outlook and Recommendations:
a. Discuss emerging trends, advancements, or potential challenges related to the Bitcoin layer 1 network and public-key cryptography.
b. Provide recommendations to the financial institution regarding the integration of the
Bitcoin layer 1 network and public-key cryptography into their operations, considering the benefits, risks, and potential mitigations.
Solution
Introduction
"The Security, Cryptography, and Future Outlook of the Bitcoin Layer 1 Network. This in-depth examination explores the goal, composition, and architecture of the fundamental layer 1 network that underpins Bitcoin. For Assignment Help, It examines the use of public-key cryptography for transaction security, assesses security risks, and suggests defences. While offering tactical suggestions for handling the shifting market, the conversation gives insights into new trends and developments.
1. Evaluation of the Purpose, Structure and Design of Bitcoin Layer 1 Network
a. Purpose and significance of the base layer 1 in the Bitcoin network
The network's core architecture, which is primarily concerned with security, is Bitcoin's base layer 1. The Proof of Work (PoW) consensus process, aims to enable safe and decentralised transactions (Akbar et al., 2021). In order to validate transactions and add them to the blockchain, miners compete to solve challenging mathematical puzzles. This creates a tamper-resistant database. Due to its enormous processing capacity, this security mechanism has demonstrated resilience against threats, making Bitcoin very resistant to censorship and manipulation. Since its launch in 2009, the basic layer of Bitcoin has experienced uptime of over 99.98%, proving its reliability (Nguyen, 2019). The network's miners' dedication to network security is demonstrated by this astounding increase.
b. Structural components of the Bitcoin layer 1 network
Decentralisation, consensus through Proof of Work (PoW), and transaction processing are all embodied in the Layer 1 network of Bitcoin. Decentralisation is ensured via
the dispersion of global nodes, which improves security and resilience. PoW requires miners to validate transactions by solving complex puzzles. Every 10 minutes, blocks are created for transaction processing, placing security over speed (Kenny, 2019). This methodical pace provides immutability while limiting throughput. Layer 2 solutions balance speed, trust, and security at Layer 1. Layer 1 of Bitcoin emphasises decentralisation, PoW consensus, and purposeful processing, reaffirming its leadership position in the cryptocurrency industry (Tatos et al., 2019).
c. Design principles and mechanisms
The layer 1 network for Bitcoin is carefully designed to provide security, immutability, and transaction verification. Decentralisation enhances security and prevents isolated failures. In order to add blocks, Proof of Work (PoW) uses difficult solutions (Jabbar et al., 2020). This collective effort maintains data accuracy by resisting retroactive alterations. The consensus of the nodes prevents unauthorised acts and double spending by verifying transactions before they are included in blocks. These ideas strengthen the first layer of Bitcoin, which is crucial to its function as a reliable store of value and digital money, encapsulating security, historical integrity, and reliable transaction validation (Jacobetty and Orton-Johnson, 2023).
2. Exploration of Public-Key Cryptography in Bitcoin Transactions
a. Fundamental principles of public-key cryptography
Asymmetric encryption and the generation of a public-private key pair are the two underlying tenets of public-key cryptography. In this system, a user creates two sets of keys: a public key that is widely disseminated and a private key that is kept secret (Aydar et al., 2019). Secure communication is made possible by the fact that messages encrypted with one key can only be decoded with the other. These concepts are essential for transaction security in the context of Bitcoin. Each user has their own set of keys. A transaction output is encrypted by the sender using the recipient's public key, the output can only be decrypted using the recipient's private key. This makes sure that the money can only be accessed by the legitimate owner. The private key must be kept secret at all times; if it is compromised, the related cash will also be lost (Rezaeighaleh and Zou, 2019).
b. Mechanisms and algorithms used in public-key cryptography
The Bitcoin network uses a variety of techniques and algorithms, including public key cryptography, to guarantee transaction verification, non-repudiation, and secrecy.
Transaction Verification: Digital signatures and cryptographic hashes are used in Bitcoin. A transaction is signed with the sender's private key when a user starts it, yielding a distinctive digital signature (Krishnapriya and Sarath, 2020). The sender's public key is then used by nodes in the network to validate the signature. The transaction is regarded as confirmed and can be uploaded to the blockchain if the signature is legitimate.
Non-Repudiation: Non-repudiation is provided through digital signatures (Fang et al., 2020). A transaction can be authenticated using the associated public key once it has been signed with a private key. This improves accountability by preventing senders from downplaying their role in the transaction.
Confidentiality: Public keys used to generate Bitcoin addresses maintain secrecy. The names behind addresses are fictitious, despite the fact that transactions are recorded on a public blockchain (Bernabe et al., 2019). The money linked to an address can only be accessed by individuals possessing the private key, protecting ownership privacy.
c. Strengths and weaknesses of public-key cryptography
- Strengths: With public-key cryptography, Bitcoin is more secure and private. It enables secure ownership verification and ensures confidentiality with digital signatures and bogus addresses (Guo and Yu, 2022). Without the need for a competent middleman, peer-to-peer transactions are also made easier. Furthermore, keys' cryptographic nature provides robust defence against brute-force attacks.
- Weaknesses: Key management is difficult because losing a private key means that money is lost forever. Furthermore, the security of public key cryptography depends on the complexity of certain mathematical puzzles, and potential future developments like quantum computers might undermine its security (Fernandez Carames and Fraga Lamas, 2020).
3. Evaluation of Security Challenges and Mitigation Strategies
a. Major security challenges and vulnerabilities
The Bitcoin network's first layer has security flaws and problems. When someone spends the same amount of Bitcoin twice, there is a danger of double-spending. Although the consensus system prevents it, a strong actor may launch a 51% assault, allowing for double spending (Hacken and Bartosz, 2023). Transaction malleability is a problem since it permits changes to IDs prior to confirmation, which might be confusing. It affects ID-dependent processes even while security isn't immediately compromised. Attacks called Sybils take advantage of decentralisation by clogging the network with phoney nodes and upsetting stability. Eclipses control transactions and isolate nodes (Salman, Al Janabi and Sagheer, 2023). These difficulties highlight the necessity of constant attack detection, protocol improvements, and a variety of decentralised nodes to maintain the Layer 1 security and integrity of Bitcoin.
b. Existing mitigation strategies
In order to resolve the security issues in the Bitcoin layer 1 network, existing mitigation tactics and remedies are used (Tedeschi, Sciancalepore and Di Pietro, 2022). The decentralised consensus process prevents double spending by making such assaults prohibitively costly and necessitating a majority of honest miners. Furthermore, miners choose to confirm transactions with larger fees, decreasing the appeal of double-spending. Segregated witness (SegWit) was introduced to address transaction malleability (Kedziora et al., 2023). SegWit increases block capacity and reduces vulnerability to malleability attacks by separating signature data from transactions.
Strong network topology and peer discovery techniques are used to defend against Sybil assaults, assuring connections with a variety of nodes rather than being dominated by a single party (Madhwal and Pouwelse, 2023). Eclipse attacks may be thwarted by selecting peers carefully, employing multiple points of connection, and monitoring network activity to look for malicious actors. In order to address these security issues, Bitcoin uses a mix of protocol upgrades, financial incentives, and network architecture, assuring the stability and dependability of its layer 1 network (Lin et al., 2022).
4. Future Outlook and Recommendations
a. Emerging trends, advancements, or potential challenges
New developments and trends in public-key cryptography and layer 1 of the Bitcoin network provide both opportunities and difficulties. Layer 2 scaling solutions like the Lightning Network seek to solve Bitcoin's scalability problems by enabling quicker, lower cost off-chain transactions while retaining the layer 1 network's security (Dasaklis and Malamas, 2023). On the other hand, the security of conventional public key cryptography is in danger from quantum computing, which may have an effect on Bitcoin. In order to address this danger and uphold the network's security, researchers are investigating quantum-resistant cryptographic methods (Akter, 2023).
b. Recommendations
Opportunities exist for integrating public-key cryptography and the Bitcoin layer 1 network into the operations of financial institutions, but this requires careful design. First, consider adopting Bitcoin for cross-border payments to take advantage of its efficient and borderless nature. Public key cryptography may be used to improve security by assuring encrypted communication and safe transactions (Dijesh, Babu and Vijayalakshmi, 2020). Uncertain laws, volatile markets, and security concerns like key management are risks, nevertheless. For minimising these risks, use risk management strategies to cope with price changes, give solid key management processes top priority to prevent losing access to money, and do in-depth due diligence on compliance requirements.
Consider introducing Bitcoin services gradually to reduce risks and stay current with market movements. Consult with compliance and blockchain experts if there are any issues. Overall, financial institutions may be prepared for success in the changing environment by developing a well-thought-out plan that finds a balance between the benefits of Bitcoin, encryption, and risk-reduction strategies (Ekstrand and Musial, 2022).
Conclusion
The study of Bitcoin's Layer 1 network concludes by highlighting the importance of this network for security, decentralisation, and transaction verification. Public-key cryptography improves non-repudiation and secrecy. Although security issues still exist, the network's integrity is supported by current mitigating techniques including consensus mechanisms and network architecture. Future developments like quantum-resistant encryption and Layer 2 solutions present both possibilities and difficulties. Recommendations stress the integration of Bitcoin into financial institutions, led by strategic adoption and risk management, to ensure a strong basis for navigating the changing environment.
References
.png)
.png)
TECH5300 Bitcoin Case Study 2 Sample
Your Task
This assessment is to be completed individually. In this assessment, you will evaluate the purpose, structure, and design of base layer 1 of the Bitcoin network, which provides the security layer.
Assessment Description
This assessment aims to evaluate your ability to analyse, evaluate, and critically assess the purpose, structure, and design of the base layer 1 of the Bitcoin network, which serves as the security layer. Additionally, you are required to explore the principles and significance of public-key cryptography in the context of Bitcoin transactions. By completing this assessment, you will demonstrate your proficiency in comprehending complex concepts, conducting in-depth research, and presenting well-structured arguments.
Case Study
Case Study Scenario: You have been appointed as a Bitcoin consultant for a financial institution seeking to explore the potential of utilising Bitcoin as part of their operations. Your task is to evaluate the purpose, structure, and design of the Bitcoin layer 1 network, with a particular focus on its security layer. Furthermore, you are required to analyse the role and impact of public-key cryptography in securing Bitcoin transactions.
Your Task: In this case study, you are required to prepare a detailed report addressing the following aspects:
1. Evaluation of the Purpose, Structure, and Design of Bitcoin Layer 1 Network:
a. Analyse the purpose and significance of the base layer 1 in the Bitcoin network, emphasising its role as the security layer.
b. Evaluate the structural components of the Bitcoin layer 1 network, including its decentralised nature, consensus mechanism, and transaction processing.
c. Assess the design principles and mechanisms employed within the Bitcoin layer 1 network to ensure security, immutability, and transaction verification.
2. Exploration of Public-Key Cryptography in Bitcoin Transactions:
a. Explain the fundamental principles of public-key cryptography and its relevance in securing Bitcoin transactions.
b. Analyse the mechanisms and algorithms used in public-key cryptography to ensure transaction verification, non-repudiation, and confidentiality in the Bitcoin network.
c. Evaluate the strengths and weaknesses of public-key cryptography within the context of Bitcoin transactions, considering factors such as key management, quantum resistance, and regulatory implications.
3. Evaluation of Security Challenges and Mitigation Strategies:
a. Identify and analyse the major security challenges and vulnerabilities associated with the Bitcoin layer 1 network, including potential attack vectors, double-spending, and transaction malleability.
b. Evaluate existing mitigation strategies and countermeasures employed to address these security challenges.
4. Future Outlook and Recommendations:
a. Discuss emerging trends, advancements, or potential challenges related to the Bitcoin layer 1 network and public-key cryptography.
b. Provide recommendations to the financial institution regarding the integration of the
Bitcoin layer 1 network and public-key cryptography into their operations, considering the benefits, risks, and potential mitigations.
Solution
Introduction
"The Security, Cryptography, and Future Outlook of the Bitcoin Layer 1 Network. This in depth examination explores the goal, composition, and architecture of the fundamental layer 1 network that underpins Bitcoin. For Assignment Help, It examines the use of public key cryptography for transaction security, assesses security risks, and suggests defences. While offering tactical suggestions for handling the shifting market, the conversation gives insights into new trends and developments.
1. Evaluation of the Purpose, Structure and Design of Bitcoin Layer 1 Network
a. Purpose and significance of the base layer 1 in the Bitcoin network
The network's core architecture, which is primarily concerned with security, is Bitcoin's base layer 1. The Proof of Work (PoW) consensus process, aims to enable safe and decentralised transactions (Akbar et al., 2021). In order to validate transactions and add them to the blockchain, miners compete to solve challenging mathematical puzzles. This creates a tamper resistant database. Due to its enormous processing capacity, this security mechanism has demonstrated resilience against threats, making Bitcoin very resistant to censorship and manipulation. Since its launch in 2009, the basic layer of Bitcoin has experienced uptime of over 99.98%, proving its reliability (Nguyen, 2019). The network's miners' dedication to network security is demonstrated by this astounding increase.
b. Structural components of the Bitcoin layer 1 network
Decentralisation, consensus through Proof of Work (PoW), and transaction processing are all embodied in the Layer 1 network of Bitcoin. Decentralisation is ensured via the dispersion of global nodes, which improves security and resilience. PoW requires miners to validate transactions by solving complex puzzles. Every 10 minutes, blocks are created for transaction processing, placing security over speed (Kenny, 2019). This methodical pace provides immutability while limiting throughput. Layer 2 solutions balance speed, trust, and security at Layer 1. Layer 1 of Bitcoin emphasises decentralisation, PoW consensus, and purposeful processing, reaffirming its leadership position in the cryptocurrency industry (Tatos et al., 2019).
c. Design principles and mechanisms
The layer 1 network for Bitcoin is carefully designed to provide security, immutability, and transaction verification. Decentralisation enhances security and prevents isolated failures. In order to add blocks, Proof of Work (PoW) uses difficult solutions (Jabbar et al., 2020). This collective effort maintains data accuracy by resisting retroactive alterations. The consensus of the nodes prevents unauthorised acts and double spending by verifying transactions before they are included in blocks. These ideas strengthen the first layer of Bitcoin, which is crucial to its function as a reliable store of value and digital money, encapsulating security, historical integrity, and reliable transaction validation (Jacobetty and Orton-Johnson, 2023).
2. Exploration of Public Key Cryptography in Bitcoin Transactions
a. Fundamental principles of public key cryptography
Asymmetric encryption and the generation of a public private key pair are the two underlying tenets of public key cryptography. In this system, a user creates two sets of keys: a public key that is widely disseminated and a private key that is kept secret (Aydar et al., 2019). Secure communication is made possible by the fact that messages encrypted with one key can only be decoded with the other. These concepts are essential for transaction security in the context of Bitcoin. Each user has their own set of keys. A transaction output is encrypted by the sender using the recipient's public key, the output can only be decrypted using the recipient's private key. This makes sure that the money can only be accessed by the legitimate owner. The private key must be kept secret at all times; if it is compromised, the related cash will also be lost (Rezaeighaleh and Zou, 2019).
b. Mechanisms and algorithms used in public key cryptography
The Bitcoin network uses a variety of techniques and algorithms, including public key cryptography, to guarantee transaction verification, non-repudiation, and secrecy.
Transaction Verification: Digital signatures and cryptographic hashes are used in Bitcoin. A transaction is signed with the sender's private key when a user starts it, yielding a distinctive digital signature (Krishnapriya and Sarath, 2020). The sender's public key is then used by nodes in the network to validate the signature. The transaction is regarded as confirmed and can be uploaded to the blockchain if the signature is legitimate.
Non-Repudiation: Non-repudiation is provided through digital signatures (Fang et al., 2020). A transaction can be authenticated using the associated public key once it has been signed with a private key. This improves accountability by preventing senders from downplaying their role in the transaction.
Confidentiality: Public keys used to generate Bitcoin addresses maintain secrecy. The names behind addresses are fictitious, despite the fact that transactions are recorded on a public blockchain (Bernabe et al., 2019). The money linked to an address can only be accessed by individuals possessing the private key, protecting ownership privacy.
c. Strengths and weaknesses of public key cryptography
- Strengths: With public-key cryptography, Bitcoin is more secure and private. It enables secure ownership verification and ensures confidentiality with digital signatures and bogus addresses (Guo and Yu, 2022). Without the need for a competent middleman, peer-to-peer transactions are also made easier. Furthermore, keys' cryptographic nature provides robust defence against brute-force attacks.
- Weaknesses: Key management is difficult because losing a private key means that money is lost forever. Furthermore, the security of public key cryptography depends on the complexity of certain mathematical puzzles, and potential future developments like quantum computers might undermine its security (Fernandez Carames and Fraga Lamas, 2020).
3. Evaluation of Security Challenges and Mitigation Strategies
a. Major security challenges and vulnerabilities
The Bitcoin network's first layer has security flaws and problems. When someone spends the same amount of Bitcoin twice, there is a danger of double-spending. Although the consensus system prevents it, a strong actor may launch a 51% assault, allowing for double spending (Hacken and Bartosz, 2023). Transaction malleability is a problem since it permits changes to IDs prior to confirmation, which might be confusing. It affects ID dependent processes even while security isn't immediately compromised. Attacks called Sybils take advantage of decentralisation by clogging the network with phoney nodes and upsetting stability. Eclipses control transactions and isolate nodes (Salman, Al Janabi and Sagheer, 2023). These difficulties highlight the necessity of constant attack detection, protocol improvements, and a variety of decentralised nodes to maintain the Layer 1 security and integrity of Bitcoin.
b. Existing mitigation strategies
In order to resolve the security issues in the Bitcoin layer 1 network, existing mitigation tactics and remedies are used (Tedeschi, Sciancalepore and Di Pietro, 2022). The decentralised consensus process prevents double spending by making such assaults prohibitively costly and necessitating a majority of honest miners. Furthermore, miners choose to confirm transactions with larger fees, decreasing the appeal of double spending. Segregated witness (SegWit) was introduced to address transaction malleability (Kedziora et al., 2023). SegWit increases block capacity and reduces vulnerability to malleability attacks by separating signature data from transactions.
Strong network topology and peer discovery techniques are used to defend against Sybil assaults, assuring connections with a variety of nodes rather than being dominated by a single party (Madhwal and Pouwelse, 2023). Eclipse attacks may be thwarted by selecting peers carefully, employing multiple points of connection, and monitoring network activity to look for malicious actors. In order to address these security issues, Bitcoin uses a mix of protocol upgrades, financial incentives, and network architecture, assuring the stability and dependability of its layer 1 network (Lin et al., 2022).
4. Future Outlook and Recommendations
a. Emerging trends, advancements, or potential challenges
New developments and trends in public-key cryptography and layer 1 of the Bitcoin network provide both opportunities and difficulties. Layer 2 scaling solutions like the Lightning Network seek to solve Bitcoin's scalability problems by enabling quicker, lower-cost off chain transactions while retaining the layer 1 network's security (Dasaklis and Malamas, 2023). On the other hand, the security of conventional public key cryptography is in danger from quantum computing, which may have an effect on Bitcoin. In order to address this danger and uphold the network's security, researchers are investigating quantum resistant cryptographic methods (Akter, 2023).
b. Recommendations
Opportunities exist for integrating public key cryptography and the Bitcoin layer 1 network into the operations of financial institutions, but this requires careful design. First, consider adopting Bitcoin for cross border payments to take advantage of its efficient and borderless nature. Public key cryptography may be used to improve security by assuring encrypted communication and safe transactions (Dijesh, Babu and Vijayalakshmi, 2020). Uncertain laws, volatile markets, and security concerns like key management are risks, nevertheless. For minimising these risks, use risk management strategies to cope with price changes, give solid key management processes top priority to prevent losing access to money, and do in depth due diligence on compliance requirements.
Consider introducing Bitcoin services gradually to reduce risks and stay current with market movements. Consult with compliance and blockchain experts if there are any issues. Overall, financial institutions may be prepared for success in the changing environment by developing a well thought-out plan that finds a balance between the benefits of Bitcoin, encryption, and risk reduction strategies (Ekstrand and Musial, 2022).
Conclusion
The study of Bitcoin's Layer 1 network concludes by highlighting the importance of this network for security, decentralisation, and transaction verification. Public key cryptography improves non repudiation and secrecy. Although security issues still exist, the network's integrity is supported by current mitigating techniques including consensus mechanisms and network architecture. Future developments like quantum resistant encryption and Layer 2 solutions present both possibilities and difficulties. Recommendations stress the integration of Bitcoin into financial institutions, led by strategic adoption and risk management, to ensure a strong basis for navigating the changing environment.
References
.png)
.png)
BUS5VA Visual Analytics Case Study 2 Sample
Assignment Details
Case Study 1 - Bank Marketing Campaign for Intelligent Targeting
In this case study, envision yourself as a junior business analyst collaborating with the marketing team to analyse and determine the best campaign strategy for a bank aimed at attracting customers to open term deposits. Successful marketing campaigns are characterised by their focus on customer needs and overall satisfaction.
However, several variables play a pivotal role in determining the success of a marketing campaign. We must carefully consider the following variables when crafting a marketing campaign:
- Customer Segmentation: Identify the target population segment and justify your choice. This aspect is very important as it suggests which segment of the population is most likely to respond to the marketing campaign's message.
- Distribution Channels: Devise the most effective strategy for reaching customers. It is important to define the target population segment to address and select appropriate communication channels, such as telephones, TV, and social media, for disseminating the campaign's message.
- Pricing Strategy: Determine the optimal pricing strategy for potential clients. Note that in the context of the bank's marketing campaign, pricing may not be the primary concern, as the bank's primary objective is to encourage clients to open deposit accounts to support its operational activities.
- Promotional Strategy: Outline the strategy's execution and how potential clients will be engaged. This step should follow an in-depth analysis of past campaigns (if available) to gain insights from past mistakes and enhance the overall effectiveness of the marketing campaign.
Your task as a junior business analyst is to address the following questions from the marketing team by creating visualisations in Tableau:
Task 1.1 (5 Marks): Investigate whether there is a significant age distribution difference between clients who make a deposit and those who do not.
Task 1.2 (5 Marks): Analyse whether a client's job or career has an impact on their likelihood to make a deposit.
Task 1.3 (5 Marks): Explore how the duration of the last contact influences the campaign's success (i.e., the likelihood to make a deposit).
Task 1.4 (5 Marks): Identify at least four campaign strategies, such as who should be contacted, how to contact them, and when to contact them. Present your findings in the form of a dashboard in Tableau.
Case Study 2 - Sports Analytics for Informed Decision Making
In this case study, you will take on the role of an analyst consultant working closely with the manager of a soccer team. Your objective is to explore the Soccer Match Dataset (available on LMS) and help the team manager to make informed decisions. The Soccer Match Dataset is a comprehensive collection of spatio-temporal events that occur during an entire season of seven soccer competitions, including La Liga, Serie A, Bundesliga, Premier League, Ligue
1, FIFA World Cup 2018, and UEFA Euro Cup 2016. This dataset offers valuable insights into various aspects of soccer matches, such as passes, shots, fouls, and more, and contains information about position, time, outcome, player, and other characteristics. Your task is to conduct descriptive analytics on this dataset and create interactive Tableau visualisations to empower the team manager with insights into the datasets, enabling informed decision-making.
Task 2.1 (5 Marks): The manager is searching for a skilled goalkeeper to join the team. Generate visualisations ranking goalkeepers based on the number of save attempts they made and highlight the top 5 goalkeepers with the most save attempts. Your visualisations should enable users to access player attributes, including weight, height, full name, and nationality, by hovering over the players of interest.
Task 2.2 (5 Marks): Lionel Messi (wyId: 3359) and Cristiano Ronaldo (wyId: 3322) are two of the greatest soccer players. Compare the game performance (e.g., the number of shots and number of passes) and physical characteristics (e.g., height, weight, and dominant foot) of Lionel Messi and Cristiano Ronaldo, to aid the manager in deciding between the two legendary players for potential recruitment.
Task 2.3 (5 Marks): The manager is interested in the potential impact of players' physical characteristics on their game performance. Create visualisations to investigate the correlations between players' physical characteristics (e.g., height, weight, and dominant foot) and their game performance (e.g., the number of passes, number of shots, and number of free kick).
Task 2.4 (5 Marks): Develop a Tableau dashboard to be used by the manager for future reference. Your dashboard should enable the manager to (1) rank players based on a selected event type (focusing on Pass, Shot, Free Kick, Foul, Offside) and (2) compare game statistics between the first half (1H) and second half (2H) of matches, based on a selected event type (Pass, Shot, Free Kick, Foul, Offside).
Solution
Introduction
In today’s age of big data understanding and presenting data in an iterative manner is of essence is the ability that defines many analyses. Tableau is one of the most popular tools used for data visualization and it helps users to analyze data and create interactive visualizations for business intelligence. This report explores the application of Tableau in two distinct case studies: an advert produced by a bank that is in a marketing campaign that focuses on efficient promotions and sports statistical analysis focusing on soccer teams. Analyzing Tableau’s tools, the report shows that such visualizations enable discovering hidden patterns and characteristics, improve marketing and player performance strategies. Hypothesis targeting the age bracket of clients to be targeted based on job, impact of job to deposit like likelihood, goalkeeper performance analytic, and comparing icons soccer players will showcase how Tableau transforms data into insights. This exploration therefore emphasizes the centrality of data visualization in enabling strategic management and organizational performance.
Case 1: Bank Marketing Campaign for Intelligent Targeting
Task 1.1: Investigate Whether There Is a Significant Age Distribution Difference Between Clients
The first task sought to identify whether there is a skewed age difference between the clients who open the term deposit and those who did not (Mazlan, Sainan and Mohamed, 2023). To do this, a histogram with ages as the x-axis and frequency as the y-axis was made possible using Tableau with the option to segment results based on deposit status.
The findings of the Visualization indicated that the clients who are using term deposit were older than the other group who were not using the term deposit (Dewi, Nilawati. and Anandita, 2024). This was evident from the distribution where the age group of depositors ended up being dominated by older people (Park and Park, 2021). There is an apparent indication that trying to reach out to older clients might help in enhancing the probability of realizing future marketing initiatives. Additional quantization could entail splitting age into particular categories to capture niche markets more accurately.
.png)
Figure 1: Part of Significant age distribution difference between clients
(Source: Implemented by Tableau)
The shared visualization concerns a line graph that focuses on the distribution of clients by their age. The x axis is the age of the clients starting from 15 up to 95 while the y axis is the number of clients in that age group. The peak has arisen in the age group of 25-35, wherein the values are gradually decreasing with the increase in age for the assignment helpline.
Task 1.2: Analyse Whether a Client's Job or Career Has an Impact on Their Likelihood to Make a Deposit
To illustrate the correlation between job type and the propensity to make a deposit as observed from the client data, a bar chart was developed using Tableau as shown in Table 5. This chart made the degree of differentiation among job types and deposit rates comprehensible, as the number of deposit comparison has been established above. As the bar chart showed there were certain professions where higher deposit rates were found especially the management and technical jobs.
.png)
Figure 2: Bar Chart of Job Type on Deposit Likelihood
(Source: Implemented by Tableau)
This insight will be useful for the marketing team in the bank to know which job categories are likely to embrace deposit campaigns. They provide an avenue of targeting specific job categories eliminating the generality of marketing messages thus enhancing the prospects of achievement of campaign goals.
Task 1.3: Explore How the Duration of the Last Contact Influences the Campaign's Success
For this work, this visualization was created in Tableau, to analyze the connection between the length of the last interaction with the effectiveness of the campaign (Dent et al. 2021). The graph depicted contact duration on the amount of loan deposit with each dot or node referring to a particular client.
.png)
Figure 3: Visualization of the Duration of the Last Contact Influences the Campaign's Success
(Source: Implemented by Tableau)
The plot also unmasks an increasing trend of deposit rates with longer contact durations. This means that if the interaction with the clients is taken further, the likelihood of getting a deposit would be improved. This plot established this correlation further, to stress the necessity of extemporaneous communication at potential clients. From this insight, the marketing team may be in a position to modify its contact strategies with the view of enhancing the general impact of the campaigns.
Task 1.4: Dashboard Creation
The last activity entailed creating a dashboard in table of the results of the preceding tasks. Additionally, the dashboard included components that let users navigate to the content by applying various filters.
To synthesize, the dashboard united several components to offer an overall opinion about the marketing campaign. Firstly, it included the Age Distribution visualization that displayed the distribution of the number of clients by their ages and their deposit/ no deposit status. This element enabled the users to recognize relationships in the age segment with higher deposit ratio. Secondly, the Job Type Analysis component used a bar chart to show how likely a deposit was going to be made based on job type. This made it easy to identify which professions were more receptive to the marketing campaign hence helping in propagation efforts.
Figure 4: Dashboard Creation Part
(Source: Implemented by Tableau)
Finally, there was the Contact Duration Analysis which depicted the campaign success based on the duration of contact with the clients. This component helped to understand the positive effects of longer contact with clients by illustrating how deposit rates depended on contact duration. Altogether, such elements allowed considering various aspects of deposit behavior and identifying factors affecting them more carefully. Dynamic data visualization and its interactivity proved beneficial in gaining a broader perspective of how the campaign was performing and contributed to the fine-tuning of marketing efforts.
Case 2: Sports Analytics for Informed Decision Making
Task 2.1: Rank Goalkeepers Based on Save Attempts
This task aimed at defining and sorting a list of goalkeepers according to the number of save attempts. To compare the goalkeepers by the number of save attempts, a bar chart was created in Tableau with emphasis on the best performers.
The bar chart was very effective in displaying the save attempts for the five top goalkeepers, complete with tooltips that displayed the weight, height, full name, and nationality of each player.
Figure 5: The part of Identifying Goalkeepers based on Save Attempts
(Source: Implemented by Tableau)
On this account, this visualization is essential particularly for the team manager where they get to judge potential goalkeepers on their performance from a clear, comparative vantage. Because there is more information regarding hover one can make a better decision when selecting it.
Task 2.2: Compare Lionel Messi and Cristiano Ronaldo
To analyses the performance of the game and the body measurements between Lionel Messi and Cristiano Ronaldo, the following visualizations were developed (Stephens and Young, 2020). Two bar charts were used to track down their shots and passes and, on the other hand, a table contained the players physical characteristics like height, weight, and preferred foot.
.png)
Figure 6: Comparison Between Messi and Ronaldo using Bar Chart
(Source: Implemented by Tableau)
The bar charts above revealed that Cristiano Ronaldo made more shots than Messi did while Messi completed more passes. The table that was provided to me showed how they differ in height, weight and the preferred foot they use. This detailed comparison is beneficial for the manager to make the right decision about recruitment since it presents a clear view of every player’s qualities.
Task 2.3: Investigate Physical Characteristics and Game Performance
This task was to assess the correlation between the players physical properties and the performance on the game (Torres-Ronda and Curtis, 2022). In the context of data exploration affordances, charts was developed in Tableau to establish relationship patterns between height, weight and the side of the foot depending on various performance statistics including, the passes, the shots and the free kicks.
Figure 7: Visualization Part of Investigate Physical Characteristics and Game Performances
(Source: Implemented by Tableau)
The plots revealed that defensive effectiveness increased positively with height while weight was also positively and moderately associated with the number of shots attempted by the players. This information is crucial in analyzing how specific physical characteristics can somehow affect one’s performance on the game, and thus in assessment of players. For example, it will enable the team to know which player would be best suited for which role given his or her physical attributes of the team.
Task 2.4: Dashboard Creation
The last activity involved creating a detailed and all-encompassing dashboard that would help the manager in the assessment of players’ and match data. Some of the features were amusing and these included Player Ranking in which rankings for different event types were depicted and Half-Time Comparison in which comparison of game statistics between the first and the second half for selected event was depicted.
Figure 8: Dashboard Creation Part
(Source: Implemented by Tableau)
Some smaller elements like drop down menus and filter functionalities enabled the manager to select different event types and view statistics side-by-side. Thus, this dashboard can be used as a vital means that helps to control player performance and match characteristics for making better decisions.
Conclusion
The examples outlined above show how it is possible to use Tableau to analyze various sets of data and come up with useful information from the large chunks of information. In the case of bank marketing campaign, Tableau analysis pointed out important insights with regards to age, job type and contact duration which were rather helpful for fine tuning the existing and future marketing campaigns. In the sports analytics case, Tableau offered a clear comparison analysis between goalkeepers and famous players, and impact of physical attributes on the gamers. The use of interactive dashboards in both cases improved option for data and decisions Accent of the data and mechanics for the decisions. In general, Tableau has been of great help in transforming data into insights particularly in marketing and in managing sporting events.
References
.png)

.png)
.png)



.png)
~5.png)
.png)
~1.png)























































.png)






