Order Now
- Home
- About Us
-
Services
-
Assignment Writing
-
Academic Writing Services
- HND Assignment Help
- SPSS Assignment Help
- College Assignment Help
- Writing Assignment for University
- Urgent Assignment Help
- Architecture Assignment Help
- Total Assignment Help
- All Assignment Help
- My Assignment Help
- Student Assignment Help
- Instant Assignment Help
- Cheap Assignment Help
- Global Assignment Help
- Write My Assignment
- Do My Assignment
- Solve My Assignment
- Make My Assignment
- Pay for Assignment Help
-
Management
- Management Assignment Help
- Business Management Assignment Help
- Financial Management Assignment Help
- Project Management Assignment Help
- Supply Chain Management Assignment Help
- Operations Management Assignment Help
- Risk Management Assignment Help
- Strategic Management Assignment Help
- Logistics Management Assignment Help
- Global Business Strategy Assignment Help
- Consumer Behavior Assignment Help
- MBA Assignment Help
- Portfolio Management Assignment Help
- Change Management Assignment Help
- Hospitality Management Assignment Help
- Healthcare Management Assignment Help
- Investment Management Assignment Help
- Market Analysis Assignment Help
- Corporate Strategy Assignment Help
- Conflict Management Assignment Help
- Marketing Management Assignment Help
- Strategic Marketing Assignment Help
- CRM Assignment Help
- Marketing Research Assignment Help
- Human Resource Assignment Help
- Business Assignment Help
- Business Development Assignment Help
- Business Statistics Assignment Help
- Business Ethics Assignment Help
- 4p of Marketing Assignment Help
- Pricing Strategy Assignment Help
- Nursing
-
Finance
- Finance Assignment Help
- Do My Finance Assignment For Me
- Financial Accounting Assignment Help
- Behavioral Finance Assignment Help
- Finance Planning Assignment Help
- Personal Finance Assignment Help
- Financial Services Assignment Help
- Forex Assignment Help
- Financial Statement Analysis Assignment Help
- Capital Budgeting Assignment Help
- Financial Reporting Assignment Help
- International Finance Assignment Help
- Business Finance Assignment Help
- Corporate Finance Assignment Help
-
Accounting
- Accounting Assignment Help
- Managerial Accounting Assignment Help
- Taxation Accounting Assignment Help
- Perdisco Assignment Help
- Solve My Accounting Paper
- Business Accounting Assignment Help
- Cost Accounting Assignment Help
- Taxation Assignment Help
- Activity Based Accounting Assignment Help
- Tax Accounting Assignment Help
- Financial Accounting Theory Assignment Help
-
Computer Science and IT
- Operating System Assignment Help
- Data mining Assignment Help
- Robotics Assignment Help
- Computer Network Assignment Help
- Database Assignment Help
- IT Management Assignment Help
- Network Topology Assignment Help
- Data Structure Assignment Help
- Business Intelligence Assignment Help
- Data Flow Diagram Assignment Help
- UML Diagram Assignment Help
- R Studio Assignment Help
-
Law
- Law Assignment Help
- Business Law Assignment Help
- Contract Law Assignment Help
- Tort Law Assignment Help
- Social Media Law Assignment Help
- Criminal Law Assignment Help
- Employment Law Assignment Help
- Taxation Law Assignment Help
- Commercial Law Assignment Help
- Constitutional Law Assignment Help
- Corporate Governance Law Assignment Help
- Environmental Law Assignment Help
- Criminology Assignment Help
- Company Law Assignment Help
- Human Rights Law Assignment Help
- Evidence Law Assignment Help
- Administrative Law Assignment Help
- Enterprise Law Assignment Help
- Migration Law Assignment Help
- Communication Law Assignment Help
- Law and Ethics Assignment Help
- Consumer Law Assignment Help
- Science
- Biology
- Engineering
-
Humanities
- Humanities Assignment Help
- Sociology Assignment Help
- Philosophy Assignment Help
- English Assignment Help
- Geography Assignment Help
- Agroecology Assignment Help
- Psychology Assignment Help
- Social Science Assignment Help
- Public Relations Assignment Help
- Political Science Assignment Help
- Mass Communication Assignment Help
- History Assignment Help
- Cookery Assignment Help
- Auditing
- Mathematics
-
Economics
- Economics Assignment Help
- Managerial Economics Assignment Help
- Econometrics Assignment Help
- Microeconomics Assignment Help
- Business Economics Assignment Help
- Marketing Plan Assignment Help
- Demand Supply Assignment Help
- Comparative Analysis Assignment Help
- Health Economics Assignment Help
- Macroeconomics Assignment Help
- Political Economics Assignment Help
- International Economics Assignments Help
-
Academic Writing Services
-
Essay Writing
- Essay Help
- Essay Writing Help
- Essay Help Online
- Online Custom Essay Help
- Descriptive Essay Help
- Help With MBA Essays
- Essay Writing Service
- Essay Writer For Australia
- Essay Outline Help
- illustration Essay Help
- Response Essay Writing Help
- Professional Essay Writers
- Custom Essay Help
- English Essay Writing Help
- Essay Homework Help
- Literature Essay Help
- Scholarship Essay Help
- Research Essay Help
- History Essay Help
- MBA Essay Help
- Plagiarism Free Essays
- Writing Essay Papers
- Write My Essay Help
- Need Help Writing Essay
- Help Writing Scholarship Essay
- Help Writing a Narrative Essay
- Best Essay Writing Service Canada
-
Dissertation
- Biology Dissertation Help
- Academic Dissertation Help
- Nursing Dissertation Help
- Dissertation Help Online
- MATLAB Dissertation Help
- Doctoral Dissertation Help
- Geography Dissertation Help
- Architecture Dissertation Help
- Statistics Dissertation Help
- Sociology Dissertation Help
- English Dissertation Help
- Law Dissertation Help
- Dissertation Proofreading Services
- Cheap Dissertation Help
- Dissertation Writing Help
- Marketing Dissertation Help
- Programming
-
Case Study
- Write Case Study For Me
- Business Law Case Study Help
- Civil Law Case Study Help
- Marketing Case Study Help
- Nursing Case Study Help
- Case Study Writing Services
- History Case Study help
- Amazon Case Study Help
- Apple Case Study Help
- Case Study Assignment Help
- ZARA Case Study Assignment Help
- IKEA Case Study Assignment Help
- Zappos Case Study Assignment Help
- Tesla Case Study Assignment Help
- Flipkart Case Study Assignment Help
- Contract Law Case Study Assignments Help
- Business Ethics Case Study Assignment Help
- Nike SWOT Analysis Case Study Assignment Help
- Coursework
- Thesis Writing
- CDR
- Research
-
Assignment Writing
-
Resources
- Referencing Guidelines
-
Universities
-
Australia
- Asia Pacific International College Assignment Help
- Macquarie University Assignment Help
- Rhodes College Assignment Help
- APIC University Assignment Help
- Torrens University Assignment Help
- Kaplan University Assignment Help
- Holmes University Assignment Help
- Griffith University Assignment Help
- VIT University Assignment Help
- CQ University Assignment Help
-
Australia
- Experts
- Free Sample
- Testimonial
MITS4004 - IT Networking and Communication Assignment 2 Sample
Assignment Brief
Due Date: Session 9
Weightage: 10%
Individual Assignment
This assessment item relates to the unit learning outcomes as in the unit descriptors.
L01: Identify the operation of the protocols that are used inside the Internet and use the seven-layer model to classify networking topology, protocol and security needs.
LO2: Evaluate LAN technology issues, including routing and flow control. Explain the difference between switches and routers. Build and troubleshoot Ethernet, Wi-Fi and Leased line networks. Connect networks with routers.
Scenario:
You are a Network and Security Engineer for the ABC Consulting Private Limited, which is a leading network and security provider for the small and medium scaled offices.
Task 1: Your task is to propose a network design for the small scaled company and sketch a basic logical network diagram of the office with 5 departments. You are free to assume:
• Name of the Office and Departments
• Networking Hardware’s such as routers, switches, hubs, modems wireless access points, firewalls etc.
Task 2: Using your expert knowledge on TCP/IP Model and its layers, sketch the TCP/IP protocols and identify at least one protocol used by each layer.
Task 3: At each level of the TCP/IP model, there are security vulnerabilities and therefore, security prevention measures that can be taken to ensure that enterprise applications are protected. As a network and security engineer, your task is to identify the security threats and propose a solution on each layer.
The report should be prepared in Microsoft word and uploaded on to the LMS. The word limit of the report is 2000 words. The report should be a properly constructed as an academic report. The report should include references in IEEE style.
Submission Guidelines for assignment help
The report should have a consistent, professional, and well-organized appearance.
1. Your report should include the following:
? The word limit of the report is 2000 words.
? The cover page must identify student names and the ID numbers, unit details, and the assignment details.
? The assignment must use 12-point font size and at least single line spacing with appropriate section headings.
? In-text referencing in IEEE style must be cited in the text of the report and listed appropriately at the end in a reference list.
2. The report must be submitted in soft (electronic) copy as a Microsoft Word document on the LMS in Turnitin drop box. Assignments submitted on the LMS will only be accepted.
3. Late penalty applies on late submission, 10% per day would be deducted.
4. The assignments will go through Turnitin and plagiarism penalty will be applied.
The report must be submitted in soft (electronic) copy as a Microsoft Word document via the upload link available on Moodle.
Solution
Introduction
The design of the network of the company has 5 departments. The office “GLORE” situated in the US is the small Scale which has 5 departments and the designing of the network is to be done for them. This plan of the organization for the organization should have 5 offices. The workplace "GLORE" arranged in the US is a limited scale which has 5 divisions and the planning of the organization is to be accomplished for them. The report comprises of the organization name GLORE with 5 divisions that are account, innovative work, advertising, client care, and IT.
Furthermore, the availability is finished utilizing a modem, switch, LAN, frameworks, stockpiling framework, centre point, an organization switch, printers, PCs, and so on. For the organization, the requirement LAN network is required as indicated by the need. The availability was used by the utilization of different organization media such as switches, centre, switch, stockpiling worker, firewall, connector, and so on. What's more, preceding to it the managing of the organization beginning initiating from ISP moving to the client. Next, we examined the TCP/IP convention suite and the conventions of the layer along with their graph. And then we considered the security weakness at TCP/IP distinctive layer of TCP/IP, and it enforced us and then we thought of the safety efforts and answers for those weaknesses. TCP/IP convention suite that is layered engineering where every layer has its conventions which are utilized to do the usefulness of that layer. Also, at each degree of TCP/IP observations of security weaknesses were seen and they need safety efforts and afterward new layers of the suite TCP/IP convention suite aren’t secure also it has weaknesses than to have sure about them. The utilization of various controls was run which will lesson the odds of the danger of information misfortune, data spilling, and numerous different issues looked in conventions downside. This report is made in the wake of experiencing the distinctive accessible examination materials and data accessible.
Organizational network design
The planning of the organization is to be accomplished for an occasion overseeing organization "GLORE Events" which has 5 divisions, and every office requires web access for their expert. For their concern of worker's prerequisites and also for the planning of the organization, we require the availability just as the equipment and programming for its arrangement. The association needs to be established and for the installation, the introduction was initiated for receiving of an association from Internet Service Provider(ISP).
ISP provides a source that is the utilization of Modem also afterward utilizing the LAN (Local Area Network). It provides arrangement to receive the admittance to the public organization and interfacing Router along with it that requires introduction in the organization. It also posts that utilizes links, we will append an organization switch with it. And then afterward frameworks of every division will be associated with that Switch and will have the option to operate it through the data and added to the stage to speak with different frameworks. From the earliest starting point the establishment for the association is needed from the Internet Service Provider that is ISP. At that point to receive the network modem is associated utilizing the NIC and the available links which were getting the signs also the utilization of LAN installed preceding to the modem and traced with firewall. Router is also associated which is giving the availability utilizing Wi-Fi and through Ethernet is associated with switch/center also.
Router is also associated with the capacity worker for the handling of the correspondence. Also, as the organization GLORE Events has 5 offices so the Switch is associated with 6 frameworks through the link.
One for every division and one concerning the principle office sort of a worker and now the plan of the fundamental rational network association: [6]
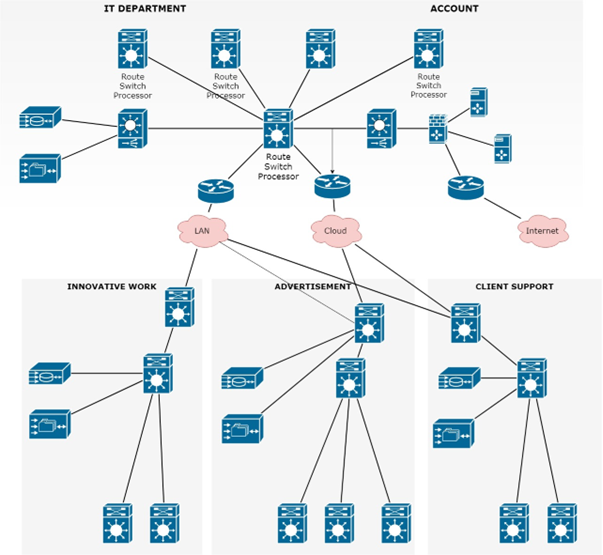
Figure 1 NETWORK LOGIC DIAGRAM
(Source: Self-developed)
The planning of the organization for the establishment of equipment is additionally thought of where the modem requires the installation where it was being designed and initiate it as a work. The five frameworks ought to be present at divisions of the organization and the switch ought to be set halfway such that in the event of any disappointment in any associations.
The framework can admittance to Wi-Fi also the individuals who expect the portability and don't lean toward the link and wires near them so they can without much of a stretch admittance to the availability.
The additional association that is the 6th ought to be put midway and ought to be utilized to teach the wide range of various frameworks.
In the same manner with a similar order can likewise be utilized as a reinforcement framework on the off chance that any of the frameworks isn't working or confronting any issue with the network. This sort of framework will make the moving simpler and as the situations are good then representatives will have the option to work productively thus it will be at last profit the organization.
TCP/IP model
As in an examination, it was indicated that correspondence between two frameworks is conceivable with the organization through convention suits. TCP/IP is one of the most generally utilized convention suite, additionally accessible without any problem. TCP/IP is the implementation of the OSI model (open system interconnection model). TCP/IP, the substitution of the convention isn't simple. TCP/IP convention is a structure of layers, and every layer posses with a particular use which is completed by the utilization of the convention. Every layer has conventions to complete its usefulness that is clung with the layer. TCP/IP convention suite consists of four layers:
Application layer: manages every layer ought to be independent and the tools that are of the first layer can secure the application information and probably not the data of TCP/IP as it is available in the next layers. The uppermost layer is an OSI and is distributed into 2 different layers and TCP/IP is the combination of 2 OSI layers. The protocols are Telnet, SMTP (Simple mail transfer protocol), HTTP (Hypertext transfer protocol), SNMP (Simple network management protocol), FTP (File transfer protocol).
Transport layer: it is the phase or layer which will ensure the information in one meeting of correspondence among the 2 communicators. As the Information Protocol data is raised in the organization phase and the layer isn't equipped for dealing with it. The layer that works as an intermediate and is properly oriented in the connection is also known as the connectionless or no connection layer. The protocols are UDP (User Datagram Protocol) and TCP (Transmission Control Protocol).
Organization layer: It is viewed as that the specific features of the organization layer could be shared by other layers and it will not create the hurdle as they are not specific with application explicit, which implies no change is needed in the insurance application. i.e. Another connectionless layer. The formation or transferring of the data is done in small units that have an address associated with them that is an IP address. The protocols are ISMP (Inter-Switch Message Protocol) and IP (Internet Protocol).
Datalink layer: The tools or managing are operated to the wide range of various layers and their controls committed circuits among the 2 communicators of an ISP. The management of data is done from the physical links and it is said that this gives the procedural and functional attributes to the data transferring. The protocols are ARP (Address Resolution Protocol), token ring, and Ethernet.
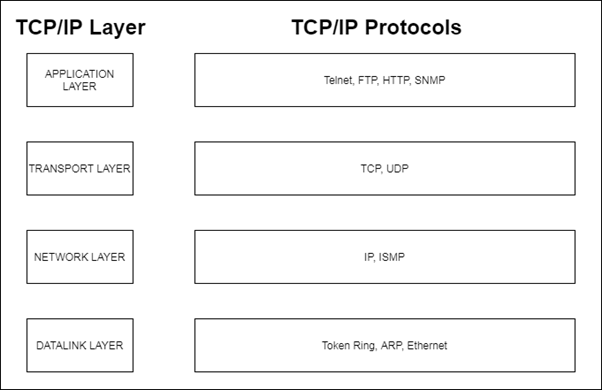
Figure 2 TCP/IP MODEL
(Source: self-developed)
Vulnerabilities
TCP/IP utilizes the location of the gadgets which are associated which fill the two or double that need to distinguishing the gadget also. As a result of this organization weakness is made and it will entirely noticeable and not contrasted with angry clients all through the globe. TCP/IP has 4 layers, as well as security concerns, that exist at every degree of the suite TCP/IP convention suite. TCP/IP information moves from the most elevated phase which is from the first Application layer and to the fourth layer which is named the Data link layer, at every next layer data is added. Along these lines, modes fitted on a more elevated phase cannot secure the previous phase, as the usefulness of the previous-level isn't distinguished from the preceding phase. Security controlling tools that are used at different layers and phase of TCP/IP convention suite available are: [1]
Application layer: manages of every phase ought to become independent and then the tools that are of the first layer phase can secure the first application information or data and probably not only the data of TCP/IP as this is available for the next layers of phase. The answer for being utilized for it ought to be level-based which can be utilized for quite a while, for instance, the utilization of Secure Multipurpose Internet Mail Extensions(S/MIME) that is continued because of the information that will be encoded in it. [2]
Transport layer: it is that of phase which will ensure the information in a meeting of correspondence among 2 communicators. Information Protocol data which was raised in any organization phase and also the layer isn't equipped for dealing with it. The layer is utilized to deal with the commotion of traffic created by the HTTP via the Transport Layer Security (TLS) convention. For utilizing Transport Layer Security (TLS) it is required that the application can uphold Transport Layer Security (TLS). In contrast with additional insurance to the first phase that is application layer utilizing or combining with the Transport Layer Security (TLS) is favored and considered safer. Transport Layer Security (TLS) will be utilized with SSL entryway VPNs.
Organization layer: displayed as that the specific features of the organization layer could be shared by other layers and it will not create the hurdle as they are not specific with application explicit, which implies no change is needed in the insurance application. In certain cases, the controlling is done by the Network layer of the IP Security (Internet Protocol security) is favored over different controls or the controls of different layers and the layers are transport and application layer. In this layer, information is ensured in parcels and the Internet
Protocol of every bundle is secured. [5]
Datalink layer: The tools or managing are operated to the wide range of various layers and their controls committed circuits among the 2 communicators of an ISP. The utilization of information encryptors is utilized to secure it. Although it does not provide help to the insurance from numerous lines thus it is viewed as basic in contrast with the different layer controls and it is simpler to execute. These conventions are utilized for the extra assurance for some particular connections that are least relied thus the utilization of these tools are finished. [3]
Conclusion
The entire report is on Network and beginning with the planning of the organization for an organization consists of 5 divisions. All the availability and connectivity and can be given by Local Area Network that is LAN since we have 3 kinds of organization that are WAN, LAN, and MAN.
Where LAN can be utilized for the structures or organization more than one spot for some clients yet MAN is used for intercity or state organization purposes and utilization of WAN is around the world. This report is set up in the wake of examining and experiencing sites and available books with network availability and their advantages.
At long last with which we thought of the answers for security weaknesses and portrayed the conventions and planned the organization for the organization GLORE Events. TCP/IP convention suite that is layered engineering where every layer has its conventions which are utilized to do the usefulness of that layer. Also, at each degree of TCP/IP, observations of weaknesses in security was seen. There is a need of safety efforts and afterward, new layers of the suite TCP/IP convention suite aren’t secure also it has weaknesses than to make sure about them. With the utilization of various controls was run which will lesson the odds of the danger of information misfortune, data spilling, and numerous different issues looked in conventions downside.
References
[1]
M. Ji, “Designing and Planning a Campus Wireless Local Area Network,” Theseus.fi, 2017, doi: URN:NBN:fi:amk-2017053011119. [Online]. Available: https://www.theseus.fi/handle/10024/130087. [Accessed: 12-Jan-2021]
[2]
M. Ji, “Designing and Planning a Campus Wireless Local Area Network,” Theseus.fi, 2017, doi: URN:NBN:fi:amk-2017053011119. [Online]. Available: https://www.theseus.fi/handle/10024/130087. [Accessed: 12-Jan-2021]
[3]
S. Francik, N. Pedryc, T. Hebda, and B. Brzychczyk, “Use of network planning methods in designing modernization of agri-food processing enterprise to improve organization of production: example of meat processing plant,” May 2018, doi: 10.22616/erdev2018.17.n426. [Online]. Available: http://www.tf.llu.lv/conference/proceedings2018/Papers/N426.pdf. [Accessed: 12-Jan-2021]
[4]
N. Zarbakhshnia, H. Soleimani, M. Goh, and S. S. Razavi, “A novel multi-objective model for green forward and reverse logistics network design,” Journal of Cleaner Production, vol. 208, pp. 1304–1316, Jan. 2019, doi: 10.1016/j.jclepro.2018.10.138. [Online]. Available: https://www.sciencedirect.com/science/article/abs/pii/S0959652618331548. [Accessed: 12-Jan-2021]
[5]
M. Mohammadi, S.-L. Jämsä-Jounela, and I. Harjunkoski, “Optimal planning of municipal solid waste management systems in an integrated supply chain network,” Computers & Chemical Engineering, vol. 123, pp. 155–169, Apr. 2019, doi: 10.1016/j.compchemeng.2018.12.022. [Online]. Available: https://www.sciencedirect.com/science/article/abs/pii/S0098135418302813. [Accessed: 12-Jan-2021]
[6]
B. Dey, K. Khalil, A. Kumar, and M. Bayoumi, “A Reversible-Logic based Architecture for Artificial Neural Network,” 2020 IEEE 63rd International Midwest Symposium on Circuits and Systems (MWSCAS), Aug. 2020, doi: 10.1109/mwscas48704.2020.9184662. [Online]. Available: https://ieeexplore.ieee.org/abstract/document/9184662. [Accessed: 13-Jan-2021]
[7]
“US20200264901A1 - Configuring programmable logic region via programmable network - Google Patents,” Google.com, 14-Feb-2019. [Online]. Available: https://patents.google.com/patent/US20200264901A1/en. [Accessed: 13-Jan-2021]
[8]
“US20200336588A1 - Device logic enhancement for network-based robocall blocking - Google Patents,” Google.com, 19-Apr-2019. [Online]. Available: https://patents.google.com/patent/US20200336588A1/en. [Accessed: 13-Jan-2021]
[9]
“A comparative analysis of surface roughness in robot spray painting using nano paint by Taguchi – fuzzy logic-neural network methods,” Australian Journal of Mechanical Engineering, 2020. [Online]. Available: https://www.tandfonline.com/doi/abs/10.1080/14484846.2020.1842157. [Accessed: 13-Jan-2021]

Download Samples PDF
Related Sample
- 3038IBA Business Case Assignment
- MKT744 Assessment Global Marketing and Sales Development Report
- ECON6001 Economic Principles Assignment
- MBA5003 Operations Plan Report 2
- MBA5008 Business Research Methods Report 3
- ACCT6003 Financial Accounting Processes Assignment
- Strategic Management Assignment
- HI6026 Audit Assurance and Compliance Assignment
- SHI104 Sociology of Health and Illness Assignment
- DATA4300 Data Security and Ethics Report 3
- MEM603 Engineering Strategy Report
- SPS201 Alcohol and Other Drugs Essay 1
- MITS5002 Software Engineering Methodology Assignment
- MBA505 Business Psychology Coaching and Mentoring Assignment
- COIT20248 Information System Analysis and Design Assignment
- MBAS905 Advanced Business Analytics Case Study 1
- IND301A Industry Consulting Project Assignment
- MIS609 Data Management and Analytics Case Study 1
- NRSG367 Transition to Professional Nursing Assignment
- NURBN2024 Mental Health Recovery Plan Case Study

Assignment Services
-
Assignment Writing
-
Academic Writing Services
- HND Assignment Help
- SPSS Assignment Help
- College Assignment Help
- Writing Assignment for University
- Urgent Assignment Help
- Architecture Assignment Help
- Total Assignment Help
- All Assignment Help
- My Assignment Help
- Student Assignment Help
- Instant Assignment Help
- Cheap Assignment Help
- Global Assignment Help
- Write My Assignment
- Do My Assignment
- Solve My Assignment
- Make My Assignment
- Pay for Assignment Help
-
Management
- Management Assignment Help
- Business Management Assignment Help
- Financial Management Assignment Help
- Project Management Assignment Help
- Supply Chain Management Assignment Help
- Operations Management Assignment Help
- Risk Management Assignment Help
- Strategic Management Assignment Help
- Logistics Management Assignment Help
- Global Business Strategy Assignment Help
- Consumer Behavior Assignment Help
- MBA Assignment Help
- Portfolio Management Assignment Help
- Change Management Assignment Help
- Hospitality Management Assignment Help
- Healthcare Management Assignment Help
- Investment Management Assignment Help
- Market Analysis Assignment Help
- Corporate Strategy Assignment Help
- Conflict Management Assignment Help
- Marketing Management Assignment Help
- Strategic Marketing Assignment Help
- CRM Assignment Help
- Marketing Research Assignment Help
- Human Resource Assignment Help
- Business Assignment Help
- Business Development Assignment Help
- Business Statistics Assignment Help
- Business Ethics Assignment Help
- 4p of Marketing Assignment Help
- Pricing Strategy Assignment Help
- Nursing
-
Finance
- Finance Assignment Help
- Do My Finance Assignment For Me
- Financial Accounting Assignment Help
- Behavioral Finance Assignment Help
- Finance Planning Assignment Help
- Personal Finance Assignment Help
- Financial Services Assignment Help
- Forex Assignment Help
- Financial Statement Analysis Assignment Help
- Capital Budgeting Assignment Help
- Financial Reporting Assignment Help
- International Finance Assignment Help
- Business Finance Assignment Help
- Corporate Finance Assignment Help
-
Accounting
- Accounting Assignment Help
- Managerial Accounting Assignment Help
- Taxation Accounting Assignment Help
- Perdisco Assignment Help
- Solve My Accounting Paper
- Business Accounting Assignment Help
- Cost Accounting Assignment Help
- Taxation Assignment Help
- Activity Based Accounting Assignment Help
- Tax Accounting Assignment Help
- Financial Accounting Theory Assignment Help
-
Computer Science and IT
- Operating System Assignment Help
- Data mining Assignment Help
- Robotics Assignment Help
- Computer Network Assignment Help
- Database Assignment Help
- IT Management Assignment Help
- Network Topology Assignment Help
- Data Structure Assignment Help
- Business Intelligence Assignment Help
- Data Flow Diagram Assignment Help
- UML Diagram Assignment Help
- R Studio Assignment Help
-
Law
- Law Assignment Help
- Business Law Assignment Help
- Contract Law Assignment Help
- Tort Law Assignment Help
- Social Media Law Assignment Help
- Criminal Law Assignment Help
- Employment Law Assignment Help
- Taxation Law Assignment Help
- Commercial Law Assignment Help
- Constitutional Law Assignment Help
- Corporate Governance Law Assignment Help
- Environmental Law Assignment Help
- Criminology Assignment Help
- Company Law Assignment Help
- Human Rights Law Assignment Help
- Evidence Law Assignment Help
- Administrative Law Assignment Help
- Enterprise Law Assignment Help
- Migration Law Assignment Help
- Communication Law Assignment Help
- Law and Ethics Assignment Help
- Consumer Law Assignment Help
- Science
- Biology
- Engineering
-
Humanities
- Humanities Assignment Help
- Sociology Assignment Help
- Philosophy Assignment Help
- English Assignment Help
- Geography Assignment Help
- Agroecology Assignment Help
- Psychology Assignment Help
- Social Science Assignment Help
- Public Relations Assignment Help
- Political Science Assignment Help
- Mass Communication Assignment Help
- History Assignment Help
- Cookery Assignment Help
- Auditing
- Mathematics
-
Economics
- Economics Assignment Help
- Managerial Economics Assignment Help
- Econometrics Assignment Help
- Microeconomics Assignment Help
- Business Economics Assignment Help
- Marketing Plan Assignment Help
- Demand Supply Assignment Help
- Comparative Analysis Assignment Help
- Health Economics Assignment Help
- Macroeconomics Assignment Help
- Political Economics Assignment Help
- International Economics Assignments Help
-
Academic Writing Services
-
Essay Writing
- Essay Help
- Essay Writing Help
- Essay Help Online
- Online Custom Essay Help
- Descriptive Essay Help
- Help With MBA Essays
- Essay Writing Service
- Essay Writer For Australia
- Essay Outline Help
- illustration Essay Help
- Response Essay Writing Help
- Professional Essay Writers
- Custom Essay Help
- English Essay Writing Help
- Essay Homework Help
- Literature Essay Help
- Scholarship Essay Help
- Research Essay Help
- History Essay Help
- MBA Essay Help
- Plagiarism Free Essays
- Writing Essay Papers
- Write My Essay Help
- Need Help Writing Essay
- Help Writing Scholarship Essay
- Help Writing a Narrative Essay
- Best Essay Writing Service Canada
-
Dissertation
- Biology Dissertation Help
- Academic Dissertation Help
- Nursing Dissertation Help
- Dissertation Help Online
- MATLAB Dissertation Help
- Doctoral Dissertation Help
- Geography Dissertation Help
- Architecture Dissertation Help
- Statistics Dissertation Help
- Sociology Dissertation Help
- English Dissertation Help
- Law Dissertation Help
- Dissertation Proofreading Services
- Cheap Dissertation Help
- Dissertation Writing Help
- Marketing Dissertation Help
- Programming
-
Case Study
- Write Case Study For Me
- Business Law Case Study Help
- Civil Law Case Study Help
- Marketing Case Study Help
- Nursing Case Study Help
- Case Study Writing Services
- History Case Study help
- Amazon Case Study Help
- Apple Case Study Help
- Case Study Assignment Help
- ZARA Case Study Assignment Help
- IKEA Case Study Assignment Help
- Zappos Case Study Assignment Help
- Tesla Case Study Assignment Help
- Flipkart Case Study Assignment Help
- Contract Law Case Study Assignments Help
- Business Ethics Case Study Assignment Help
- Nike SWOT Analysis Case Study Assignment Help
- Coursework
- Thesis Writing
- CDR
- Research


.png)
~5.png)
.png)
~1.png)























































.png)






